Guidebook: IT Security Risks, Technologies, and Endpoint Integrity
VerifiedAdded on 2023/03/30
|14
|3538
|185
Report
AI Summary
This assignment is a comprehensive IT security guidebook designed to train junior staff members on identifying and assessing IT security risks, along with the organizational policies needed to protect business-critical data and equipment. The report is divided into three main sections: Risk and security processes, Security technologies, and Monitoring and endpoint integrity. The first section details various security risks, including computer viruses, rogue security tools, Trojan horses, phishing attacks, and malware, along with organizational security procedures and methods for assessing and treating IT security risks. The second section focuses on security technologies, such as firewalls, discussing the impact of incorrect configurations and implementing DMZ, static IPs, and NAT. The final section addresses monitoring networks and endpoint integrity, covering methods to improve network security, gain ROI, and fix issues faster. The guidebook emphasizes the importance of understanding and mitigating IT security threats to improve overall productivity and performance, with references to support the information presented.

COMPUTER INFORMATION SYSTEM 0
Computer Information System
Computer Information System
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER INFORMATION SYSTEM 1
Table of Contents
Introduction...........................................................................................................................................2
Task 1: Risk and security processes.......................................................................................................2
Various kinds of security risk.............................................................................................................2
Computer viruses..............................................................................................................................2
Rogue security tools..........................................................................................................................3
Trojan horse......................................................................................................................................3
Phishing attack...................................................................................................................................3
Malware attack..................................................................................................................................4
Organizational security procedures...................................................................................................4
Methods to assess and treat IT security risks....................................................................................5
Task 2: Security technologies................................................................................................................5
The potential impact of incorrect configuration of firewall...............................................................5
Implementing DMZ, static IP and NAT...............................................................................................6
DMZ...............................................................................................................................................6
Static IP..........................................................................................................................................7
NAT................................................................................................................................................8
Task 3: Monitoring and endpoint integrity............................................................................................8
Monitoring networks.........................................................................................................................8
Fix issues faster..............................................................................................................................9
Gain immediate ROI.......................................................................................................................9
Improve the security of networks..................................................................................................9
Trusted network..............................................................................................................................10
Conclusion...........................................................................................................................................10
References...........................................................................................................................................12
Table of Contents
Introduction...........................................................................................................................................2
Task 1: Risk and security processes.......................................................................................................2
Various kinds of security risk.............................................................................................................2
Computer viruses..............................................................................................................................2
Rogue security tools..........................................................................................................................3
Trojan horse......................................................................................................................................3
Phishing attack...................................................................................................................................3
Malware attack..................................................................................................................................4
Organizational security procedures...................................................................................................4
Methods to assess and treat IT security risks....................................................................................5
Task 2: Security technologies................................................................................................................5
The potential impact of incorrect configuration of firewall...............................................................5
Implementing DMZ, static IP and NAT...............................................................................................6
DMZ...............................................................................................................................................6
Static IP..........................................................................................................................................7
NAT................................................................................................................................................8
Task 3: Monitoring and endpoint integrity............................................................................................8
Monitoring networks.........................................................................................................................8
Fix issues faster..............................................................................................................................9
Gain immediate ROI.......................................................................................................................9
Improve the security of networks..................................................................................................9
Trusted network..............................................................................................................................10
Conclusion...........................................................................................................................................10
References...........................................................................................................................................12

COMPUTER INFORMATION SYSTEM 2
Introduction
In this generation, the use of information technology is increasing very fast which is
now used in many organizations for controlling their computer devices. IT systems
provide a platform to the companies for improving the overall productivity of their
businesses and also maintain the performance of computer networks (AlZain, Pardede,
Soh, and Thom, 2012). Security is a major concern associated with the information
technology which also increases the data breach and security risks in the organizations.
The aim of this report is to describe the security risks faced by the organizations and
evaluate security or privacy related technologies used by the companies. For any
organization, it is very important to train their staff members for handling security-
related issues and problems. In order to understand the key factors linked with the
information technology, this report will create an engaging guidebook which contains
the security risks, their impacts and mitigation tools. Mainly, this report is divided into
major three tasks which include, risk and security processes, security technologies and
monitoring and endpoint integrity.
Task 1: Risk and security processes
Various kinds of security risks
This section will identify and describe numerous types of security threats and risks
which impact on the performance of an organization. It is identified that security of data
is a very complex task for every organization which increase by increasing numbers of
IT systems (Baskerville, Spagnoletti, and Kim, 2014). In the last few years, the rate of
cyber-crimes and attacks has increased by 60% worldwide and the numbers of
companies are facing data breach related issues while using information technologies.
There are following security risks and issues are facing the organizations:
Computer viruses
It is observed that computer viruses are one of the simple types of security risk which
occurred in the computing devices used by an organization. The data of previous studies
show that the rate of computer virus is increasing day by day and around 33% of
companies were suffered from such kind of security issues in last two years ( Chen, and
Zhao, 2012). It is analysed the term computer virus is defined as the security threat
Introduction
In this generation, the use of information technology is increasing very fast which is
now used in many organizations for controlling their computer devices. IT systems
provide a platform to the companies for improving the overall productivity of their
businesses and also maintain the performance of computer networks (AlZain, Pardede,
Soh, and Thom, 2012). Security is a major concern associated with the information
technology which also increases the data breach and security risks in the organizations.
The aim of this report is to describe the security risks faced by the organizations and
evaluate security or privacy related technologies used by the companies. For any
organization, it is very important to train their staff members for handling security-
related issues and problems. In order to understand the key factors linked with the
information technology, this report will create an engaging guidebook which contains
the security risks, their impacts and mitigation tools. Mainly, this report is divided into
major three tasks which include, risk and security processes, security technologies and
monitoring and endpoint integrity.
Task 1: Risk and security processes
Various kinds of security risks
This section will identify and describe numerous types of security threats and risks
which impact on the performance of an organization. It is identified that security of data
is a very complex task for every organization which increase by increasing numbers of
IT systems (Baskerville, Spagnoletti, and Kim, 2014). In the last few years, the rate of
cyber-crimes and attacks has increased by 60% worldwide and the numbers of
companies are facing data breach related issues while using information technologies.
There are following security risks and issues are facing the organizations:
Computer viruses
It is observed that computer viruses are one of the simple types of security risk which
occurred in the computing devices used by an organization. The data of previous studies
show that the rate of computer virus is increasing day by day and around 33% of
companies were suffered from such kind of security issues in last two years ( Chen, and
Zhao, 2012). It is analysed the term computer virus is defined as the security threat
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER INFORMATION SYSTEM 3
which is designed and implemented by the hackers from the perspective of hacking.
Mainly, it is developed by the attackers and transfer from one computer to another
which are connected to each other. These types of signals impact on the performance of
computer devices and companies may suffer from the data breach related problems.
Rogue security tools
The term rogue security tool refers to the malicious software which is designed by the
attackers for obtaining the data of companies and users. It is an advanced version of
computer viruses where criminals attack the computer networks and servers used by
an organization and reduce their performance for entering into their data sets. Such
kinds of tools are free to access and numbers of employees install in their devices which
create a problem of a security breach in the companies (Chou, 2013).
Trojan horse
A recent study identified that a Trojan horse is defined as the security issue or tricking
someone by allowing hackers to access their personal computer devices. it is a kind of
hacking algorithm that has the ability for blocking the private computer devices used by
an organization (Fischer, and Geßner, 2012). Mainly, hackers use email as a platform for
transferring such kinds of codes from one computer to another and it also affects the
productivity of an organization. It is evaluated the Trojan horses are enough capable of
producing data breach and hacking and they can easily collect the passwords of
computer devices.
Phishing attack
It is a very common kind of cyber-attack which can impact on the performance of an
organization and community. A recent study identified that most of cyber-attacks and
security breaches are performed with the help of phishing attack where the criminals
send the fraud and spam emails to the employees and users (Ghosh, Gajar, and Rai,
2013). After that consumers click on these unwanted links and emails which help the
criminals for accessing the private details of their accounts along with the user’s
computer devices. In the last few years, the rate of phishing attack has increased by
67% because numbers of consumers access the fraud emails and links which are
developed by hackers.
which is designed and implemented by the hackers from the perspective of hacking.
Mainly, it is developed by the attackers and transfer from one computer to another
which are connected to each other. These types of signals impact on the performance of
computer devices and companies may suffer from the data breach related problems.
Rogue security tools
The term rogue security tool refers to the malicious software which is designed by the
attackers for obtaining the data of companies and users. It is an advanced version of
computer viruses where criminals attack the computer networks and servers used by
an organization and reduce their performance for entering into their data sets. Such
kinds of tools are free to access and numbers of employees install in their devices which
create a problem of a security breach in the companies (Chou, 2013).
Trojan horse
A recent study identified that a Trojan horse is defined as the security issue or tricking
someone by allowing hackers to access their personal computer devices. it is a kind of
hacking algorithm that has the ability for blocking the private computer devices used by
an organization (Fischer, and Geßner, 2012). Mainly, hackers use email as a platform for
transferring such kinds of codes from one computer to another and it also affects the
productivity of an organization. It is evaluated the Trojan horses are enough capable of
producing data breach and hacking and they can easily collect the passwords of
computer devices.
Phishing attack
It is a very common kind of cyber-attack which can impact on the performance of an
organization and community. A recent study identified that most of cyber-attacks and
security breaches are performed with the help of phishing attack where the criminals
send the fraud and spam emails to the employees and users (Ghosh, Gajar, and Rai,
2013). After that consumers click on these unwanted links and emails which help the
criminals for accessing the private details of their accounts along with the user’s
computer devices. In the last few years, the rate of phishing attack has increased by
67% because numbers of consumers access the fraud emails and links which are
developed by hackers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER INFORMATION SYSTEM 4
Malware attack
It is defined as computer software which is designed for controlling and managing the
private data of companies. It is observed that for performing a data breach most of the
hackers used such kind of software because of their ability to access the computer
devices used by employees in the organizations (Gonzalez, et al., 2012). Moreover, it can
impact on the productivity of an organization where criminals transfer a large number
of traffic signals and viruses to the user’s computer networks and block the security
systems used by the companies. By using such kind of security threats criminals can
easily control and store the private data of companies and users may lose their personal
information along with the accounts details.
Organizational security procedures
In this modern generation numbers of organizations are using information technologies
for improving their productivities and businesses. But, using IT systems also lead the
security risks and threats in the companies and they also lose their personal details. For
controlling and monitoring such kinds of issues companies adopt IT security specialist
that help them for identifying the risks factors linked with the computer systems.
Amazon, Google, Facebook and many more all these are real examples that faced the
security-related issues in the last few years (Jouini, Rabai, and Aissa, 2014).
For controlling and managing such kinds of issues they changed the IT infrastructure of
computer networks and also implemented security policies. Moreover, many companies
provide proper training and education to their junior staffs and employees in order to
reduce the security risks linked with the IT systems (Kashefi, Kassiri, M. and
Shahidinejad, 2013). Providing proper training is an effective approach that helps
companies for controlling the rate of security threats and management team can focus
on the computer networks used in information technologies. A recent study identified
that most of the business communities are using advanced computer networks and
security tools such as firewall, cryptography and so on. This method and tools help them
for reducing the rate of security threats and protect their personal data from criminals.
Methods to assess and treat IT security risks
In order to reduce the rate of security threats and risks from computer systems,
companies can adopt the information security risk process. There are several steps
includes in the risks assessment method, for example, identification, assessment, treat
Malware attack
It is defined as computer software which is designed for controlling and managing the
private data of companies. It is observed that for performing a data breach most of the
hackers used such kind of software because of their ability to access the computer
devices used by employees in the organizations (Gonzalez, et al., 2012). Moreover, it can
impact on the productivity of an organization where criminals transfer a large number
of traffic signals and viruses to the user’s computer networks and block the security
systems used by the companies. By using such kind of security threats criminals can
easily control and store the private data of companies and users may lose their personal
information along with the accounts details.
Organizational security procedures
In this modern generation numbers of organizations are using information technologies
for improving their productivities and businesses. But, using IT systems also lead the
security risks and threats in the companies and they also lose their personal details. For
controlling and monitoring such kinds of issues companies adopt IT security specialist
that help them for identifying the risks factors linked with the computer systems.
Amazon, Google, Facebook and many more all these are real examples that faced the
security-related issues in the last few years (Jouini, Rabai, and Aissa, 2014).
For controlling and managing such kinds of issues they changed the IT infrastructure of
computer networks and also implemented security policies. Moreover, many companies
provide proper training and education to their junior staffs and employees in order to
reduce the security risks linked with the IT systems (Kashefi, Kassiri, M. and
Shahidinejad, 2013). Providing proper training is an effective approach that helps
companies for controlling the rate of security threats and management team can focus
on the computer networks used in information technologies. A recent study identified
that most of the business communities are using advanced computer networks and
security tools such as firewall, cryptography and so on. This method and tools help them
for reducing the rate of security threats and protect their personal data from criminals.
Methods to assess and treat IT security risks
In order to reduce the rate of security threats and risks from computer systems,
companies can adopt the information security risk process. There are several steps
includes in the risks assessment method, for example, identification, assessment, treat

COMPUTER INFORMATION SYSTEM 5
the risks, integrate, and availability of an organization’s assists. Identification is the first
process of risk assessment approach which provides a platform to the organizations for
determining the risk factors linked with the IT system (Modi, et al., 2013).
The assessment is a kind of process which combines the data gathered from the risk
management and control systems. Moreover, a treatment process can help an
organization for handling security risks and threats linked with the IT system.
Therefore using such kind of risk assessment methods the organizations can control
and manage the level of security risks and they can easily secure their personal data
files from hackers (Montero, et al., 2015). There are numbers of laws and legislation
which can be involved and applied in the risk assessment process. These legislations
include The Data Protection Act 2018, data protection regulation 2016, General data
protection regulation 2016 and many more.
Task 2: Security technologies
The potential impact of incorrect configuration of the firewall
A firewall is a kind of computer software which is used in computer devices for
controlling and managing security risk and threats. Proper configuration of firewall is a
complex task for every organization which can impact on the overall security of
information technology. A recent study identified that incorrect configuration of firewall
software can provide a platform to the hackers for entering into the IT system and
devices (Ren, Wang, and Wang, 2012).
Mainly, hackers develop and implement third-party VPN networks for obtaining the
data of an organization and consumer configure such kinds of servers with their
computer devices which directly impact on the security of information technologies. It
is argued that 90% of security threats and attacks occurred due to lack of configuration
issues and VPN is the best platform by which hackers can easily enter into the
companies servers. It the secure connection does not complete in the system then
criminals can easily attack the computer networks and they can access the personal
data of an organization.
From previous studies, it is found that configuring firewall policies is a common
problem for every organization and it provides a way to the hackers for successfully
the risks, integrate, and availability of an organization’s assists. Identification is the first
process of risk assessment approach which provides a platform to the organizations for
determining the risk factors linked with the IT system (Modi, et al., 2013).
The assessment is a kind of process which combines the data gathered from the risk
management and control systems. Moreover, a treatment process can help an
organization for handling security risks and threats linked with the IT system.
Therefore using such kind of risk assessment methods the organizations can control
and manage the level of security risks and they can easily secure their personal data
files from hackers (Montero, et al., 2015). There are numbers of laws and legislation
which can be involved and applied in the risk assessment process. These legislations
include The Data Protection Act 2018, data protection regulation 2016, General data
protection regulation 2016 and many more.
Task 2: Security technologies
The potential impact of incorrect configuration of the firewall
A firewall is a kind of computer software which is used in computer devices for
controlling and managing security risk and threats. Proper configuration of firewall is a
complex task for every organization which can impact on the overall security of
information technology. A recent study identified that incorrect configuration of firewall
software can provide a platform to the hackers for entering into the IT system and
devices (Ren, Wang, and Wang, 2012).
Mainly, hackers develop and implement third-party VPN networks for obtaining the
data of an organization and consumer configure such kinds of servers with their
computer devices which directly impact on the security of information technologies. It
is argued that 90% of security threats and attacks occurred due to lack of configuration
issues and VPN is the best platform by which hackers can easily enter into the
companies servers. It the secure connection does not complete in the system then
criminals can easily attack the computer networks and they can access the personal
data of an organization.
From previous studies, it is found that configuring firewall policies is a common
problem for every organization and it provides a way to the hackers for successfully
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER INFORMATION SYSTEM 6
performing data breach and a security risk (Siponen, Mahmood, and Pahnila, 2014).
Firewalls are a fundamental piece of your system security, and a misconfigured firewall
can harm your association and give simple access to an assailant. However,
misconfigurations are alarmingly normal. There are major five most common firewall
configuration problems faced by an organization which is described below:
Broad policy configuration
Risky rogue services
Non-standard authorization process
Test system using production data
Logout from the security networks
Therefore, it is evaluated the misconfiguration of firewall policies can negatively impact
on the performance of an organization and IT security. Third party VPNs are mainly
developed by the attackers in order to control and manage the privacy of an
organization where a hacker uses botnet process for producing hacked VPNs. Mainly,
numbers of consumers use the low cost virtual private network which does not require
any private key for securing data and networks due to which the rate of security threats
also increases. However, both misconfiguration of firewall policies and third-party
virtual private networks can reduce the performance of information technologies and
break the security of IT devices which can increase the issue of cyber-attacks.
Implementing DMZ, static IP and NAT
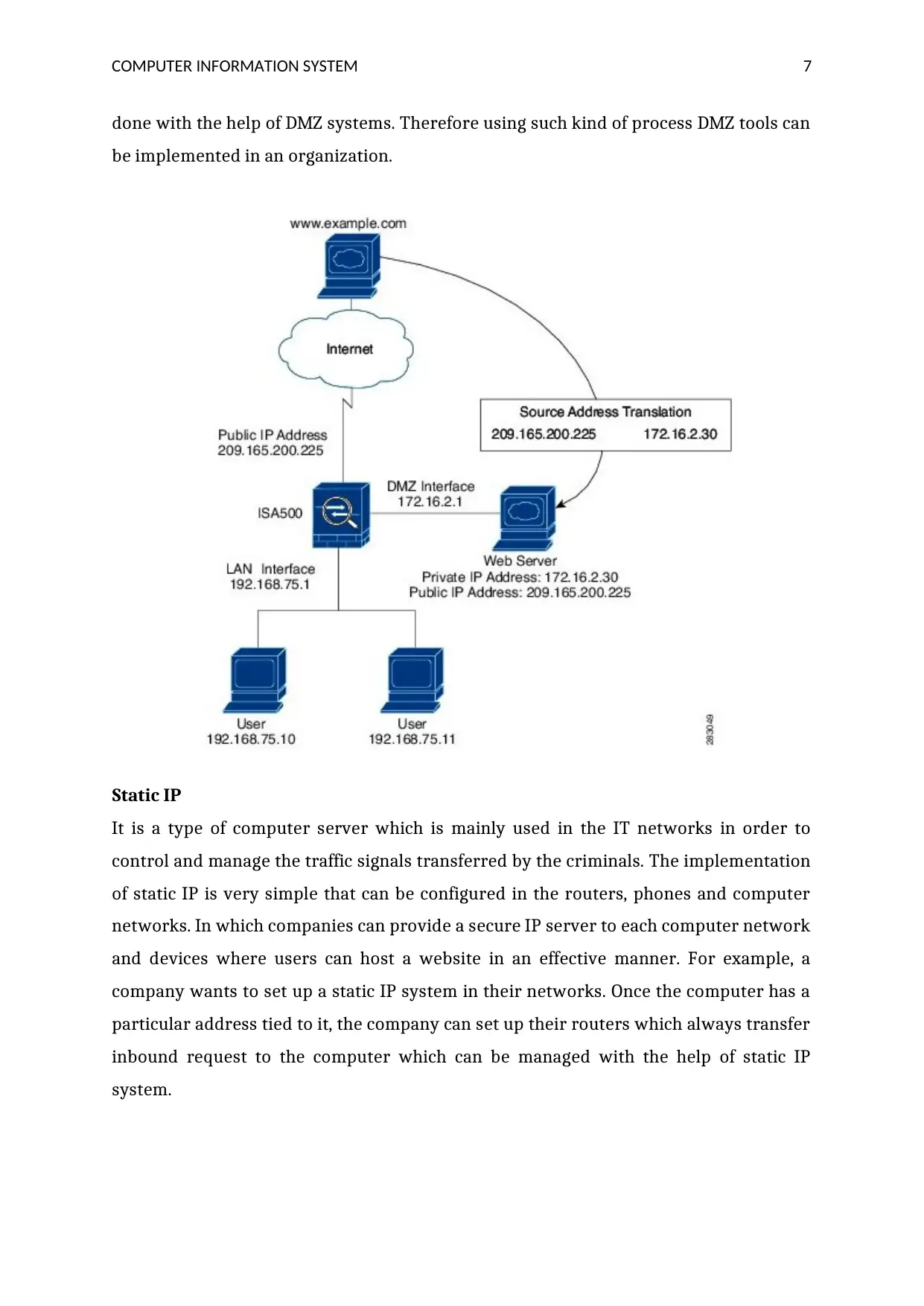
DMZ
DMZ is defined as a computer network which is mainly used in computer devices for
securing the personal data from hackers and criminals. It is an advanced version of
firewall which is a more secure system that has the ability for reducing the traffic
signals and unwanted links from the server. Implementing DMZ in the networks is an
effective strategy that can help the organizations for improving the overall security of
their networks. The implementation of DMZ can be done by making each portion of an
organization's networks sit on various IP networks (Zissis, and Lekkas, 2012). For
example, consumers have two accessible devices which deliver web hosting services
such as FTP and IRC system. Both these devices are completely based on the public
servers. For which a common LAN is used for separating their two servers and it can be
performing data breach and a security risk (Siponen, Mahmood, and Pahnila, 2014).
Firewalls are a fundamental piece of your system security, and a misconfigured firewall
can harm your association and give simple access to an assailant. However,
misconfigurations are alarmingly normal. There are major five most common firewall
configuration problems faced by an organization which is described below:
Broad policy configuration
Risky rogue services
Non-standard authorization process
Test system using production data
Logout from the security networks
Therefore, it is evaluated the misconfiguration of firewall policies can negatively impact
on the performance of an organization and IT security. Third party VPNs are mainly
developed by the attackers in order to control and manage the privacy of an
organization where a hacker uses botnet process for producing hacked VPNs. Mainly,
numbers of consumers use the low cost virtual private network which does not require
any private key for securing data and networks due to which the rate of security threats
also increases. However, both misconfiguration of firewall policies and third-party
virtual private networks can reduce the performance of information technologies and
break the security of IT devices which can increase the issue of cyber-attacks.
Implementing DMZ, static IP and NAT
DMZ
DMZ is defined as a computer network which is mainly used in computer devices for
securing the personal data from hackers and criminals. It is an advanced version of
firewall which is a more secure system that has the ability for reducing the traffic
signals and unwanted links from the server. Implementing DMZ in the networks is an
effective strategy that can help the organizations for improving the overall security of
their networks. The implementation of DMZ can be done by making each portion of an
organization's networks sit on various IP networks (Zissis, and Lekkas, 2012). For
example, consumers have two accessible devices which deliver web hosting services
such as FTP and IRC system. Both these devices are completely based on the public
servers. For which a common LAN is used for separating their two servers and it can be
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
COMPUTER INFORMATION SYSTEM 7
done with the help of DMZ systems. Therefore using such kind of process DMZ tools can
be implemented in an organization.
Static IP
It is a type of computer server which is mainly used in the IT networks in order to
control and manage the traffic signals transferred by the criminals. The implementation
of static IP is very simple that can be configured in the routers, phones and computer
networks. In which companies can provide a secure IP server to each computer network
and devices where users can host a website in an effective manner. For example, a
company wants to set up a static IP system in their networks. Once the computer has a
particular address tied to it, the company can set up their routers which always transfer
inbound request to the computer which can be managed with the help of static IP
system.
done with the help of DMZ systems. Therefore using such kind of process DMZ tools can
be implemented in an organization.
Static IP
It is a type of computer server which is mainly used in the IT networks in order to
control and manage the traffic signals transferred by the criminals. The implementation
of static IP is very simple that can be configured in the routers, phones and computer
networks. In which companies can provide a secure IP server to each computer network
and devices where users can host a website in an effective manner. For example, a
company wants to set up a static IP system in their networks. Once the computer has a
particular address tied to it, the company can set up their routers which always transfer
inbound request to the computer which can be managed with the help of static IP
system.
COMPUTER INFORMATION SYSTEM 8
NAT
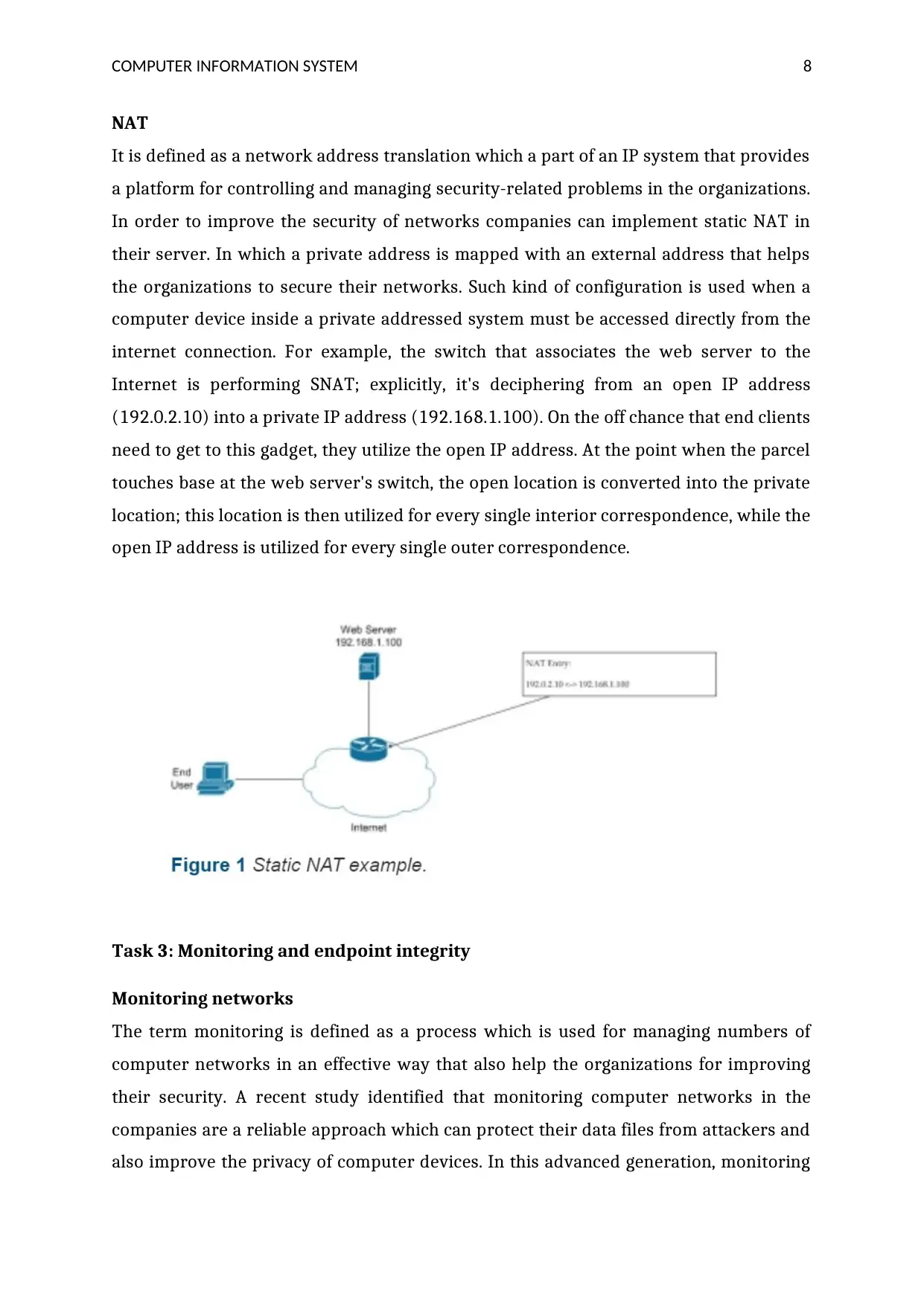
It is defined as a network address translation which a part of an IP system that provides
a platform for controlling and managing security-related problems in the organizations.
In order to improve the security of networks companies can implement static NAT in
their server. In which a private address is mapped with an external address that helps
the organizations to secure their networks. Such kind of configuration is used when a
computer device inside a private addressed system must be accessed directly from the
internet connection. For example, the switch that associates the web server to the
Internet is performing SNAT; explicitly, it's deciphering from an open IP address
(192.0.2.10) into a private IP address (192.168.1.100). On the off chance that end clients
need to get to this gadget, they utilize the open IP address. At the point when the parcel
touches base at the web server's switch, the open location is converted into the private
location; this location is then utilized for every single interior correspondence, while the
open IP address is utilized for every single outer correspondence.
Task 3: Monitoring and endpoint integrity
Monitoring networks
The term monitoring is defined as a process which is used for managing numbers of
computer networks in an effective way that also help the organizations for improving
their security. A recent study identified that monitoring computer networks in the
companies are a reliable approach which can protect their data files from attackers and
also improve the privacy of computer devices. In this advanced generation, monitoring
NAT
It is defined as a network address translation which a part of an IP system that provides
a platform for controlling and managing security-related problems in the organizations.
In order to improve the security of networks companies can implement static NAT in
their server. In which a private address is mapped with an external address that helps
the organizations to secure their networks. Such kind of configuration is used when a
computer device inside a private addressed system must be accessed directly from the
internet connection. For example, the switch that associates the web server to the
Internet is performing SNAT; explicitly, it's deciphering from an open IP address
(192.0.2.10) into a private IP address (192.168.1.100). On the off chance that end clients
need to get to this gadget, they utilize the open IP address. At the point when the parcel
touches base at the web server's switch, the open location is converted into the private
location; this location is then utilized for every single interior correspondence, while the
open IP address is utilized for every single outer correspondence.
Task 3: Monitoring and endpoint integrity
Monitoring networks
The term monitoring is defined as a process which is used for managing numbers of
computer networks in an effective way that also help the organizations for improving
their security. A recent study identified that monitoring computer networks in the
companies are a reliable approach which can protect their data files from attackers and
also improve the privacy of computer devices. In this advanced generation, monitoring
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

COMPUTER INFORMATION SYSTEM 9
networks play a major contribution to the development of secure networks where
consumers can easily secure their personal data files.
There are many reasons which show the importance of monitoring process in the
organizations which includes, improve security, reduce security risks and threats, save
time and money, plan for change and manage computer networks in less time. it is
identified that a network monitoring process is more capable of detecting and capturing
failures of computer networks which increase the rate of cyber-crimes and attacks.
There are various benefits of monitoring system which are described below:
Fix issues faster
It is one of the major advantages of monitoring system where companies can identify
the risk factors linked with the computer networks and fix the security-related issues in
very less time. Moreover, such kind of approach makes problem-solving easier and
faster that help an organization for protecting their data from hackers.
Gain immediate ROI
It is observed that IT teams in the companies face heavy workloads which also impact
on the performance of computer devices. Such kinds of problems and issues can be
resolved with the help of a monitoring system which can provide immediate ROI. A
recent study argued that an effective monitoring system can help the organizations of
gaining immediate ROI which also reduce the level of traffic signals from the networks.
Improve the security of networks
It is an essential property of a monitoring process which is now used in the many
organizations for protecting information from criminals. It is identified that Amazon,
Google and so on are using such kind of process for managing large and complex
computer networks in an effective way. Mainly, it provides a secure strategy to the
companies which reduce the security threats and risks from the system and improve
the performance of computer networks. Therefore, it is suggested that companies
should adopt a monitoring process which effectively improves the security and privacy
of their networks and devices.
Trusted network
A trust network is defined as the secured network which is mainly used for controlling
and managing security risks associated with the computer devices. It is an effective
networks play a major contribution to the development of secure networks where
consumers can easily secure their personal data files.
There are many reasons which show the importance of monitoring process in the
organizations which includes, improve security, reduce security risks and threats, save
time and money, plan for change and manage computer networks in less time. it is
identified that a network monitoring process is more capable of detecting and capturing
failures of computer networks which increase the rate of cyber-crimes and attacks.
There are various benefits of monitoring system which are described below:
Fix issues faster
It is one of the major advantages of monitoring system where companies can identify
the risk factors linked with the computer networks and fix the security-related issues in
very less time. Moreover, such kind of approach makes problem-solving easier and
faster that help an organization for protecting their data from hackers.
Gain immediate ROI
It is observed that IT teams in the companies face heavy workloads which also impact
on the performance of computer devices. Such kinds of problems and issues can be
resolved with the help of a monitoring system which can provide immediate ROI. A
recent study argued that an effective monitoring system can help the organizations of
gaining immediate ROI which also reduce the level of traffic signals from the networks.
Improve the security of networks
It is an essential property of a monitoring process which is now used in the many
organizations for protecting information from criminals. It is identified that Amazon,
Google and so on are using such kind of process for managing large and complex
computer networks in an effective way. Mainly, it provides a secure strategy to the
companies which reduce the security threats and risks from the system and improve
the performance of computer networks. Therefore, it is suggested that companies
should adopt a monitoring process which effectively improves the security and privacy
of their networks and devices.
Trusted network
A trust network is defined as the secured network which is mainly used for controlling
and managing security risks associated with the computer devices. It is an effective
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

COMPUTER INFORMATION SYSTEM 10
network that has the capability for reducing the problem of a data breach, hacking and
security threats occurred in the computer networks. In the last few years, the use of
trusted networks has increased by 50% because of their ability to protect networks and
data of an organization in an effective manner.
From previous investigations, it is analysed that a trusted network is a process which is
used by the network administrator from the perspective of security and privacy.
Generally, it is a computer network where an IT team tries to secure and protect the
sensitive data of an organization. It is also said that the trusted network is within the
security perimeter which blocks the unwanted signals and networks from the system.
Therefore, it is very important for an organization to select trusted networks while
developing and implementing computer networks in IT devices.
It is suggested that trusted network may be a part of an IT security solution because of
their several advantages such as more effective and reliable, reduce security risks,
protect data from hackers, identify the risk factors and block traffic signals from the
devices. Moreover, such kinds of networks support administrator for controlling and
monitoring the rate of security attacks and improve the overall performance of
information technologies. Firewall, and VPN, both are the very best example of trusted
networks which are now used in computer devices for protecting data of users from
hackers.
In which firewall is software which is used in the computers for identifying the traffic
and unwanted signals from the system and improve the overall security of networks.
VPN is a virtual private network that controls and manage computer networks used by
an organization and reduces the rate of security threats and attacks more effectively. All
these evidenced shows that trusted network can be used as a security process and it is a
part of a security solution that can be adopted in an organization or community.
Conclusion
From the above observation, it is concluded that security is the biggest issue faced by an
organization while using information technology but it can be managed with the help of
firewall and other trusted networks. This report identified security risks and issues
faced by an organization and evaluated various security technologies. This engaging
network that has the capability for reducing the problem of a data breach, hacking and
security threats occurred in the computer networks. In the last few years, the use of
trusted networks has increased by 50% because of their ability to protect networks and
data of an organization in an effective manner.
From previous investigations, it is analysed that a trusted network is a process which is
used by the network administrator from the perspective of security and privacy.
Generally, it is a computer network where an IT team tries to secure and protect the
sensitive data of an organization. It is also said that the trusted network is within the
security perimeter which blocks the unwanted signals and networks from the system.
Therefore, it is very important for an organization to select trusted networks while
developing and implementing computer networks in IT devices.
It is suggested that trusted network may be a part of an IT security solution because of
their several advantages such as more effective and reliable, reduce security risks,
protect data from hackers, identify the risk factors and block traffic signals from the
devices. Moreover, such kinds of networks support administrator for controlling and
monitoring the rate of security attacks and improve the overall performance of
information technologies. Firewall, and VPN, both are the very best example of trusted
networks which are now used in computer devices for protecting data of users from
hackers.
In which firewall is software which is used in the computers for identifying the traffic
and unwanted signals from the system and improve the overall security of networks.
VPN is a virtual private network that controls and manage computer networks used by
an organization and reduces the rate of security threats and attacks more effectively. All
these evidenced shows that trusted network can be used as a security process and it is a
part of a security solution that can be adopted in an organization or community.
Conclusion
From the above observation, it is concluded that security is the biggest issue faced by an
organization while using information technology but it can be managed with the help of
firewall and other trusted networks. This report identified security risks and issues
faced by an organization and evaluated various security technologies. This engaging

COMPUTER INFORMATION SYSTEM 11
guidebook critically reviewed the IT security and analysed the risk factors associated
with computer networks. Implementing DMZ, static IP and NAT networks in an
organization can improve the security of IT devices and sensitive data. It is suggested
that companies should train their junior staff members and provide complete
information about security threats and attacks. Moreover, they should adopt only
secured networks and configure both firewall and VPN networks properly because
misconfiguration can lead to the issue of cyber-crimes.
guidebook critically reviewed the IT security and analysed the risk factors associated
with computer networks. Implementing DMZ, static IP and NAT networks in an
organization can improve the security of IT devices and sensitive data. It is suggested
that companies should train their junior staff members and provide complete
information about security threats and attacks. Moreover, they should adopt only
secured networks and configure both firewall and VPN networks properly because
misconfiguration can lead to the issue of cyber-crimes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





