Information Systems Security Report: Threats, Vulnerabilities, and IBM
VerifiedAdded on 2023/05/26
|5
|747
|57
Report
AI Summary
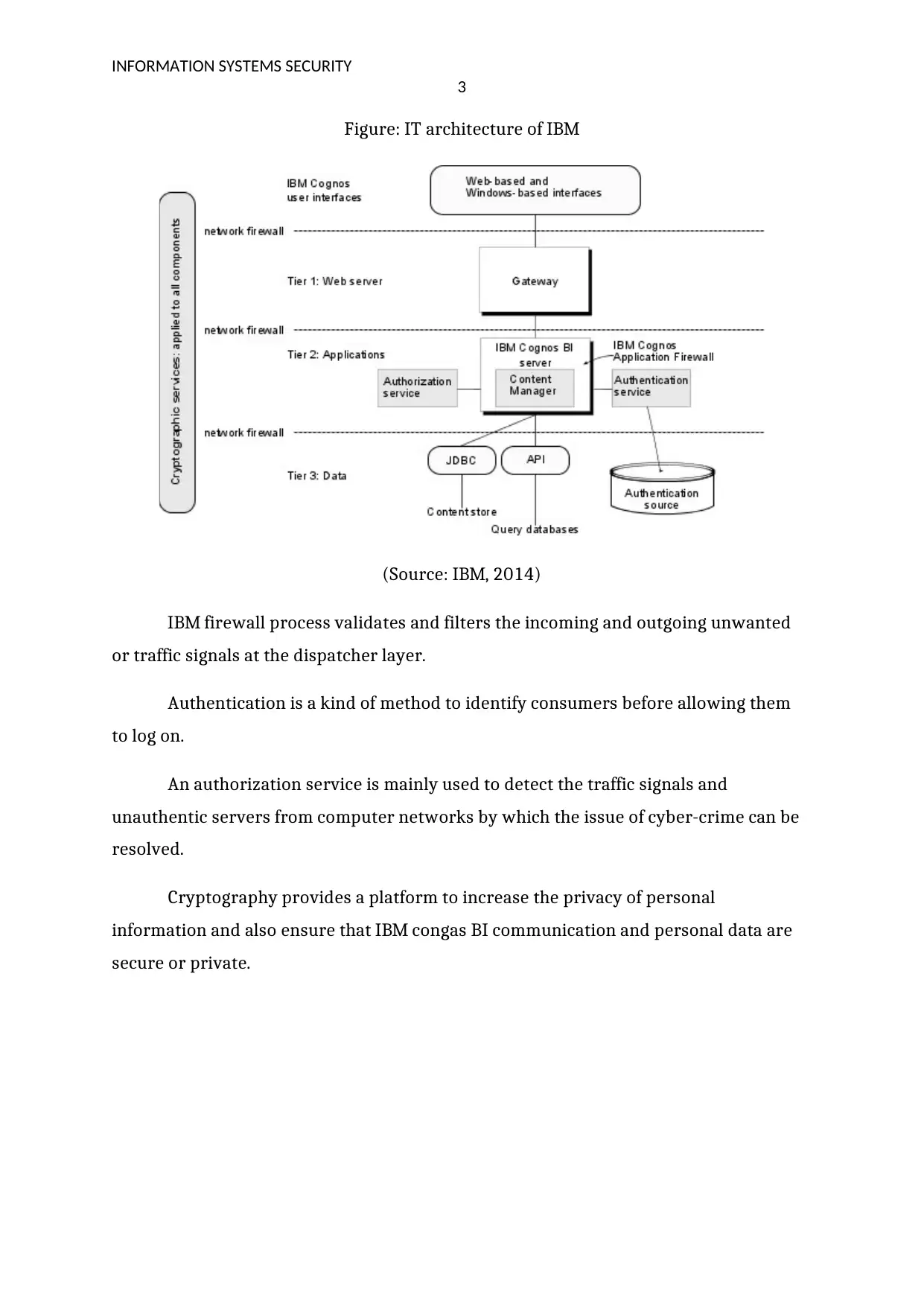
This report delves into the fundamental aspects of information systems security, highlighting the increasing rate of security threats and the importance of cybersecurity measures. It explores various IT security fundamentals such as threat analysis, auditing, vulnerability assessment, and risk assessment. The report identifies common vulnerabilities within IT infrastructures, including legacy software, DDOS attacks, malware, phishing, ransomware, and configuration conflicts. It recommends mitigation tools like firewalls, antivirus software, encryption, and regular software updates. Furthermore, the report analyzes IBM's security architecture, focusing on its authentication servers, authorization services, cryptographic technology, and firewall processes, to illustrate a robust approach to safeguarding information. Desklib provides this and other solved assignments to aid students in their studies.
1 out of 5










![[object Object]](/_next/static/media/star-bottom.7253800d.svg)