IT Security Management Report - Digital Forensics and Network Design
VerifiedAdded on 2023/06/10
|20
|5768
|442
Report
AI Summary
This IT Security Management report analyzes a digital forensic case investigation for a new start-up company. The report details the use of digital forensics tools, including the creation of virtual disk images using Magic ISO software. It also presents a network design for the company, including network topology, security assumptions, and challenges. The report explores authentication and authorization mechanisms, key management issues, intrusion detection systems, and firewall implementation. Furthermore, it measures the ROI on security and identifies potential security breaches. The report aims to provide a comprehensive understanding of IT security management principles and their practical application in a business context. The assignment covers topics such as digital forensics, network design, security solutions, virtual disk images, network topology, authentication, and authorization mechanisms, intrusion detection systems, firewalls, and DMZ.

IT SECURITY MANAGEMENT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction..............................................................................................................................2
Task -1 Digital Forensics.........................................................................................................2
1. Case Study Description.................................................................................................2
2. Virtual Disk Image........................................................................................................3
Task - 2 Network Design..........................................................................................................5
1. Network Topology.........................................................................................................6
2. Security Assumptions and Challenges........................................................................9
3. Authentication and Authorisation Mechanisms.........................................................9
4. Key Management Issues.............................................................................................11
5. IDS................................................................................................................................13
6. Security Issues.............................................................................................................14
7. Measure the ROI on Security.....................................................................................15
8. Security Breach...........................................................................................................16
Conclusion...............................................................................................................................16
References...............................................................................................................................17
1
Introduction..............................................................................................................................2
Task -1 Digital Forensics.........................................................................................................2
1. Case Study Description.................................................................................................2
2. Virtual Disk Image........................................................................................................3
Task - 2 Network Design..........................................................................................................5
1. Network Topology.........................................................................................................6
2. Security Assumptions and Challenges........................................................................9
3. Authentication and Authorisation Mechanisms.........................................................9
4. Key Management Issues.............................................................................................11
5. IDS................................................................................................................................13
6. Security Issues.............................................................................................................14
7. Measure the ROI on Security.....................................................................................15
8. Security Breach...........................................................................................................16
Conclusion...............................................................................................................................16
References...............................................................................................................................17
1

Introduction
This projects aims to analyse the digital forensic case investigation, which involves
network designing and security solutions for a new start-up company. This company
basically is a small medium enterprise and this company owned by Luton. Using E-
government model, in production and accounting records, Luton decided to encounter many
anomalies. This company has investigator and employed for digital forensics. So, investigator
needs to evaluate determine any form of malicious activities that take place in the network.
Provide prevention for the malware with the company system. All this will be analysed and
discussed in detail. The digital forensic tool needs to be analysed and discussed in detail.
Also the network security for this company will be analysed and discussed in detail. Further,
analysing the authentication and authorization mechanisms will be done. Key management
issues will be analysed and discussed. Measures on ROI security will be measured and
discussed in detail. Finally, the security breaches will be identified.
Task -1 Digital Forensics
1. Case Study Description
The new start-up company is a small medium enterprise and this company is owned
by Luton. In production and accounting records, Luton decided to encounter many anomalies,
using E-government model. Basically, this company begins with system check for the log
files, then it determines various suspicious entries along with various IP addresses. These
information is transferred outside the company with the help of firewall. The enterprise
system is also received and has encountered many complaints from the customers. It included
that a strange message is often displayed in the processing time and sometimes it leads to
redirect to the payment pages but it does not look relevant. So, this company faces hard
situation for ensuring uncompromised computer system in terms of enterprise’s system. This
company also contains investigator and is employed for digital forensic. Thus, the
investigator must perform evaluation of malicious activities that occur in the network. It
provides prevention for those malware with the company system.
2
This projects aims to analyse the digital forensic case investigation, which involves
network designing and security solutions for a new start-up company. This company
basically is a small medium enterprise and this company owned by Luton. Using E-
government model, in production and accounting records, Luton decided to encounter many
anomalies. This company has investigator and employed for digital forensics. So, investigator
needs to evaluate determine any form of malicious activities that take place in the network.
Provide prevention for the malware with the company system. All this will be analysed and
discussed in detail. The digital forensic tool needs to be analysed and discussed in detail.
Also the network security for this company will be analysed and discussed in detail. Further,
analysing the authentication and authorization mechanisms will be done. Key management
issues will be analysed and discussed. Measures on ROI security will be measured and
discussed in detail. Finally, the security breaches will be identified.
Task -1 Digital Forensics
1. Case Study Description
The new start-up company is a small medium enterprise and this company is owned
by Luton. In production and accounting records, Luton decided to encounter many anomalies,
using E-government model. Basically, this company begins with system check for the log
files, then it determines various suspicious entries along with various IP addresses. These
information is transferred outside the company with the help of firewall. The enterprise
system is also received and has encountered many complaints from the customers. It included
that a strange message is often displayed in the processing time and sometimes it leads to
redirect to the payment pages but it does not look relevant. So, this company faces hard
situation for ensuring uncompromised computer system in terms of enterprise’s system. This
company also contains investigator and is employed for digital forensic. Thus, the
investigator must perform evaluation of malicious activities that occur in the network. It
provides prevention for those malware with the company system.
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
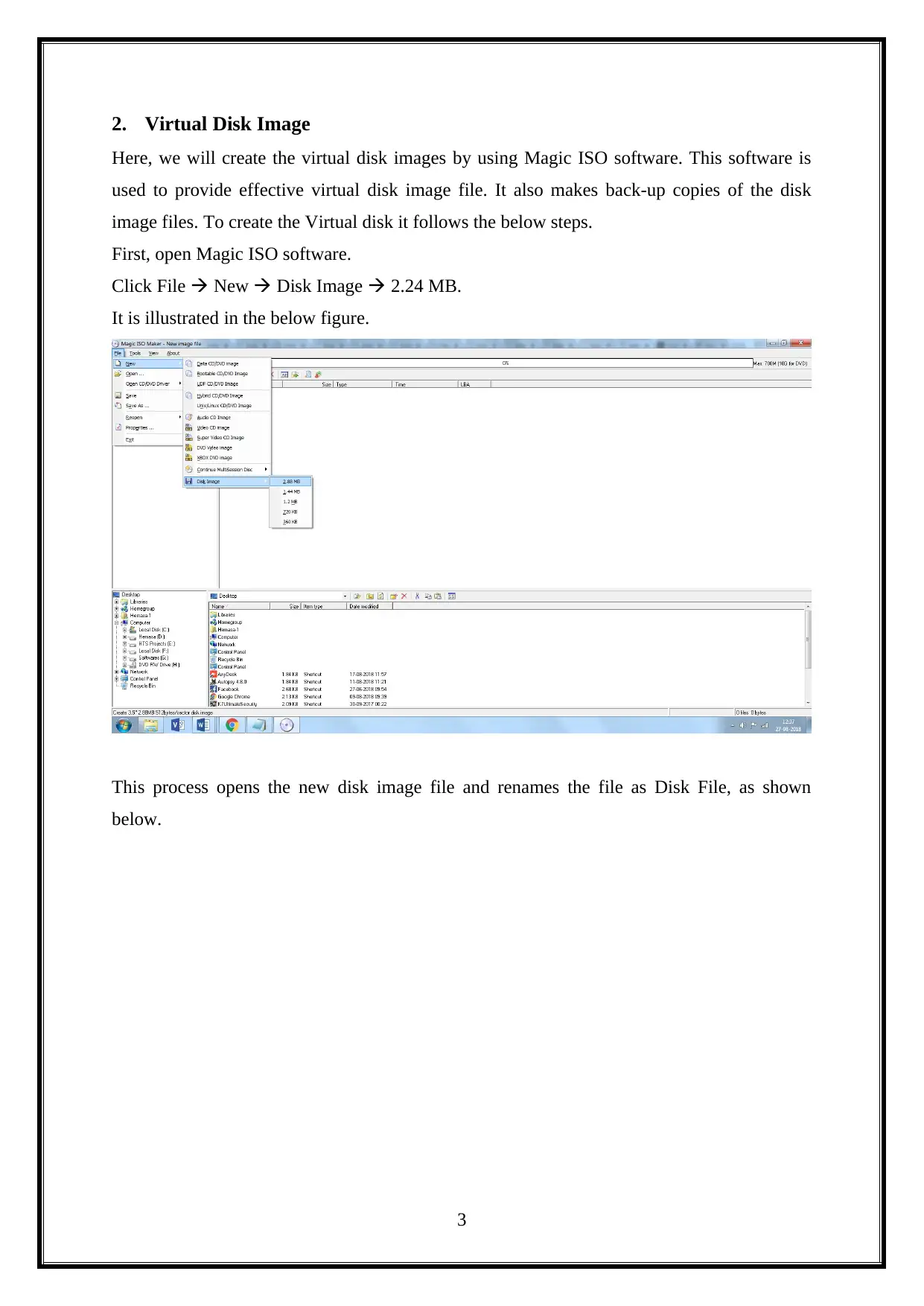
2. Virtual Disk Image
Here, we will create the virtual disk images by using Magic ISO software. This software is
used to provide effective virtual disk image file. It also makes back-up copies of the disk
image files. To create the Virtual disk it follows the below steps.
First, open Magic ISO software.
Click File New Disk Image 2.24 MB.
It is illustrated in the below figure.
This process opens the new disk image file and renames the file as Disk File, as shown
below.
3
Here, we will create the virtual disk images by using Magic ISO software. This software is
used to provide effective virtual disk image file. It also makes back-up copies of the disk
image files. To create the Virtual disk it follows the below steps.
First, open Magic ISO software.
Click File New Disk Image 2.24 MB.
It is illustrated in the below figure.
This process opens the new disk image file and renames the file as Disk File, as shown
below.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
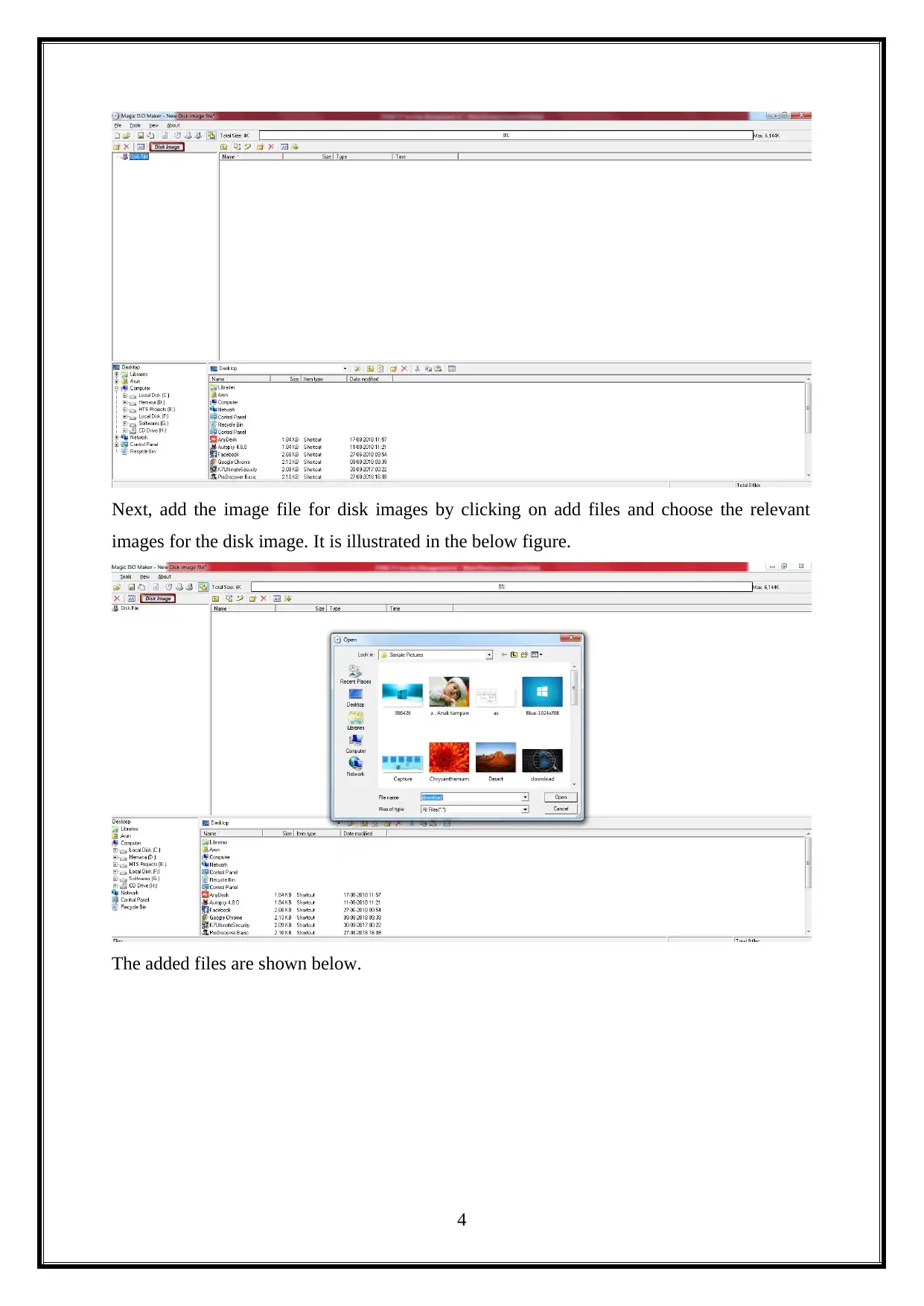
Next, add the image file for disk images by clicking on add files and choose the relevant
images for the disk image. It is illustrated in the below figure.
The added files are shown below.
4
images for the disk image. It is illustrated in the below figure.
The added files are shown below.
4
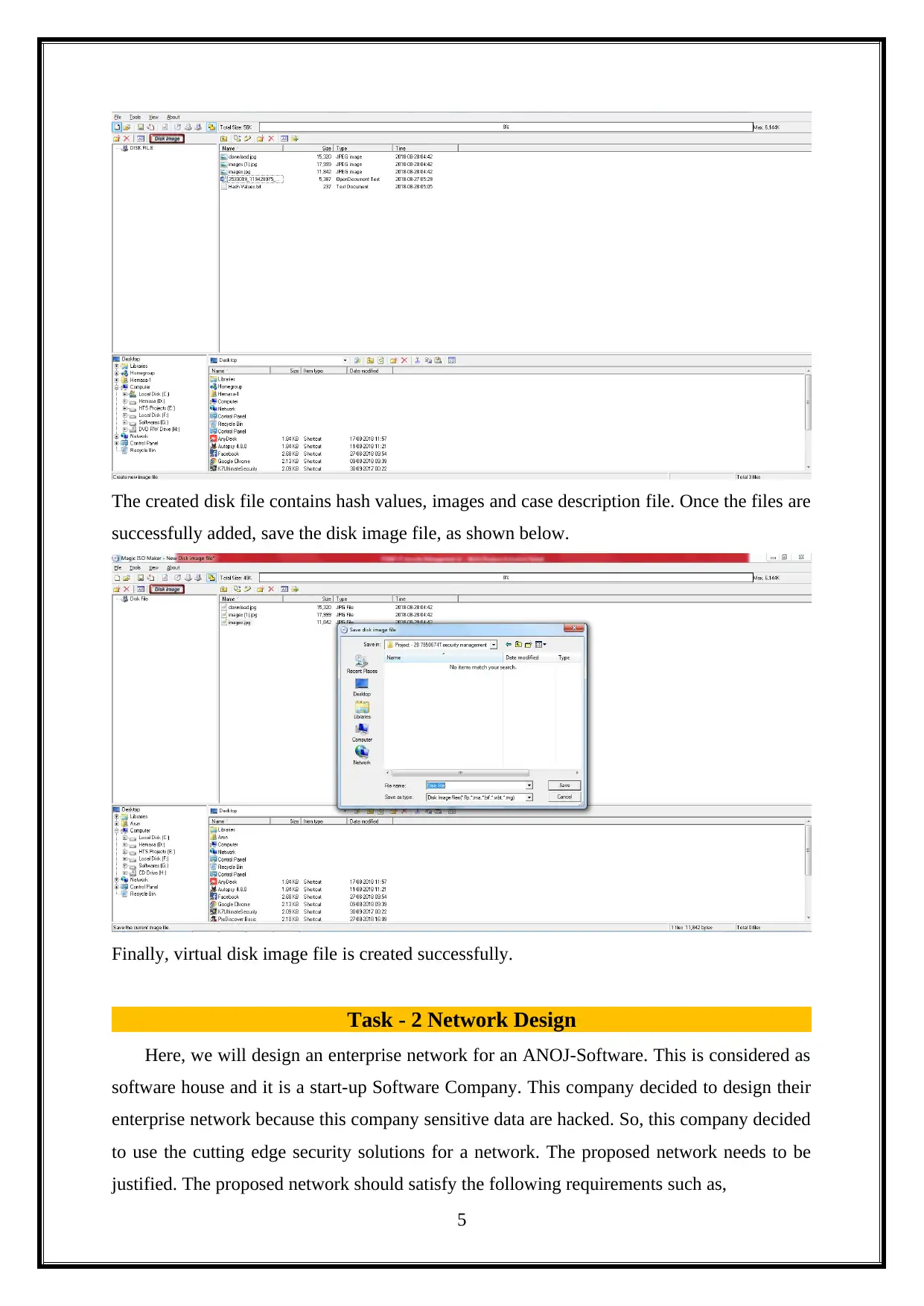
The created disk file contains hash values, images and case description file. Once the files are
successfully added, save the disk image file, as shown below.
Finally, virtual disk image file is created successfully.
Task - 2 Network Design
Here, we will design an enterprise network for an ANOJ-Software. This is considered as
software house and it is a start-up Software Company. This company decided to design their
enterprise network because this company sensitive data are hacked. So, this company decided
to use the cutting edge security solutions for a network. The proposed network needs to be
justified. The proposed network should satisfy the following requirements such as,
5
successfully added, save the disk image file, as shown below.
Finally, virtual disk image file is created successfully.
Task - 2 Network Design
Here, we will design an enterprise network for an ANOJ-Software. This is considered as
software house and it is a start-up Software Company. This company decided to design their
enterprise network because this company sensitive data are hacked. So, this company decided
to use the cutting edge security solutions for a network. The proposed network needs to be
justified. The proposed network should satisfy the following requirements such as,
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Use internal email server
Use two web servers. One for external users and another for the internal users.
Use internal CVS server and it only grants the internal access.
Also, use the anonymous CVS server for remote teams to download the source
code.
1. Network Topology
Network Diagrams are basics for guaranteeing you have an entire comprehension of how
your network topology is interconnected and can give you an overhead perspective of what’s
going ahead in the system. Commonly, it will enable you to imagine where your foundation
is missing and what should be overhauled/supplanted.
Having a legitimately recorded schematic of your whole system and associations can
likewise guarantee you can investigate issues in a deliberate request when they emerge. A
portion of these product bundles even naturally refreshes your system topology, then outlines
new gadgets included or expelled from the system, which truly eliminates by physically
removing them.
With their ability for demonstrating how arrange parts collaborate, organize, the outlines can
fill an assortment of needs, including the following:
Arranging the structure of a home or expert system.
Organizing updates to a current system.
Detailing and investigating system issues.
To follow PCI or different prerequisites.
As documentation for outside correspondence, on boarding, and so forth.
To monitor parts that send important data to a seller for a RFP (ask for proposition)
without unveiling private data.
Pitching a system proposition to monetary partners.
Proposing abnormal state, syslog framework changes.
Remembering the final goal for outlining and constructing the highly anchored
arrangement, numerous elements should be considered. For instance, host’s topology and
position within an organization, equipment determining, then programming innovations as
well as the careful arrangement of each segment.
Topology and Architecture
The basic development in outlining this system is to characterize the topology of the
system. Topology is considered as physical and sensible system format. On the physical side,
6
Use two web servers. One for external users and another for the internal users.
Use internal CVS server and it only grants the internal access.
Also, use the anonymous CVS server for remote teams to download the source
code.
1. Network Topology
Network Diagrams are basics for guaranteeing you have an entire comprehension of how
your network topology is interconnected and can give you an overhead perspective of what’s
going ahead in the system. Commonly, it will enable you to imagine where your foundation
is missing and what should be overhauled/supplanted.
Having a legitimately recorded schematic of your whole system and associations can
likewise guarantee you can investigate issues in a deliberate request when they emerge. A
portion of these product bundles even naturally refreshes your system topology, then outlines
new gadgets included or expelled from the system, which truly eliminates by physically
removing them.
With their ability for demonstrating how arrange parts collaborate, organize, the outlines can
fill an assortment of needs, including the following:
Arranging the structure of a home or expert system.
Organizing updates to a current system.
Detailing and investigating system issues.
To follow PCI or different prerequisites.
As documentation for outside correspondence, on boarding, and so forth.
To monitor parts that send important data to a seller for a RFP (ask for proposition)
without unveiling private data.
Pitching a system proposition to monetary partners.
Proposing abnormal state, syslog framework changes.
Remembering the final goal for outlining and constructing the highly anchored
arrangement, numerous elements should be considered. For instance, host’s topology and
position within an organization, equipment determining, then programming innovations as
well as the careful arrangement of each segment.
Topology and Architecture
The basic development in outlining this system is to characterize the topology of the
system. Topology is considered as physical and sensible system format. On the physical side,
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
one must ensure circulation to the workplaces or near structures where the presence of client
exists. For the servers, we should give network which includes the intranet, for the internet,
especially for the other organizational areas, then the remote clients who are interfacing via
phone lines etc. Consideration of intelligent topology is essential.
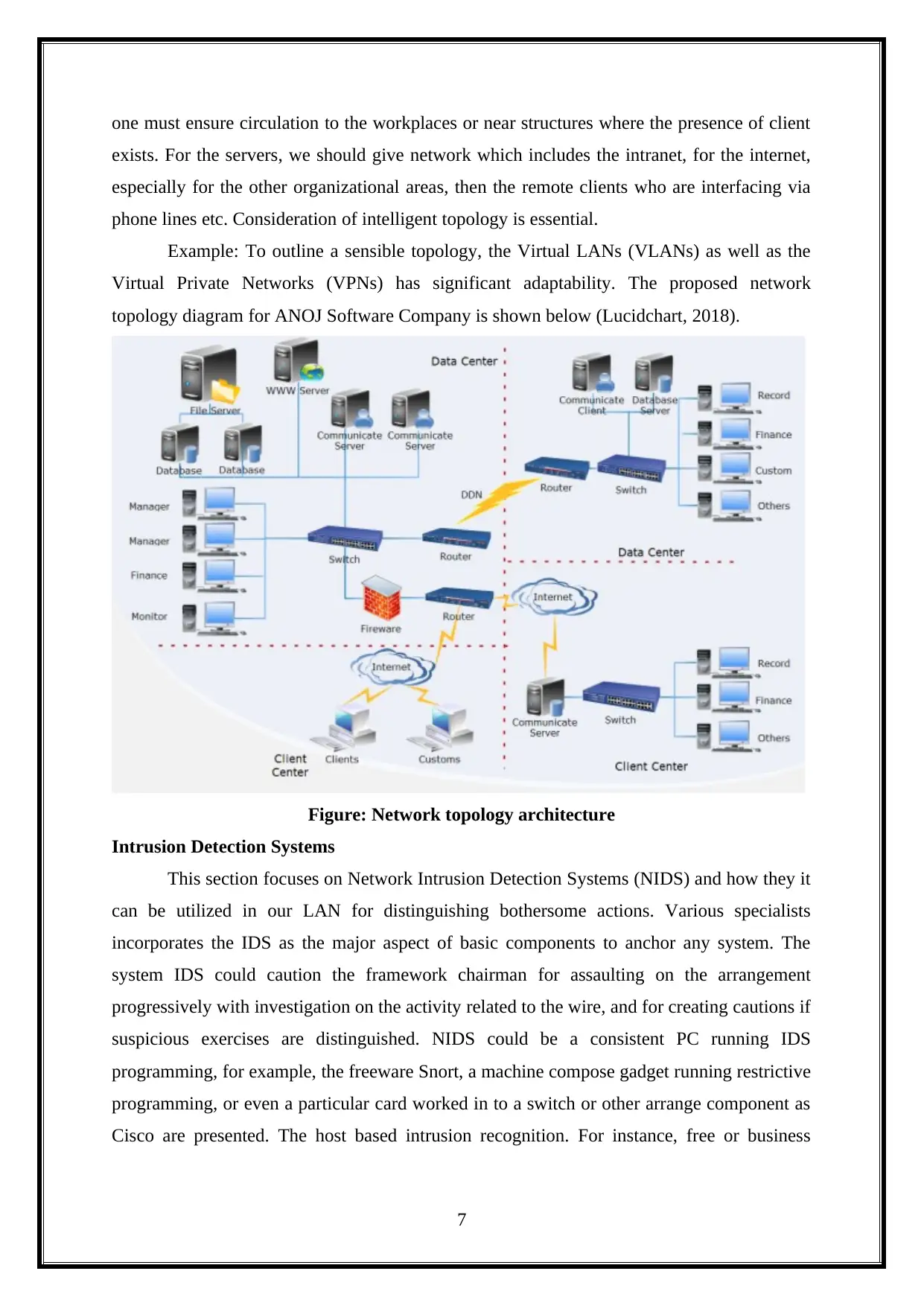
Example: To outline a sensible topology, the Virtual LANs (VLANs) as well as the
Virtual Private Networks (VPNs) has significant adaptability. The proposed network
topology diagram for ANOJ Software Company is shown below (Lucidchart, 2018).
Figure: Network topology architecture
Intrusion Detection Systems
This section focuses on Network Intrusion Detection Systems (NIDS) and how they it
can be utilized in our LAN for distinguishing bothersome actions. Various specialists
incorporates the IDS as the major aspect of basic components to anchor any system. The
system IDS could caution the framework chairman for assaulting on the arrangement
progressively with investigation on the activity related to the wire, and for creating cautions if
suspicious exercises are distinguished. NIDS could be a consistent PC running IDS
programming, for example, the freeware Snort, a machine compose gadget running restrictive
programming, or even a particular card worked in to a switch or other arrange component as
Cisco are presented. The host based intrusion recognition. For instance, free or business
7
exists. For the servers, we should give network which includes the intranet, for the internet,
especially for the other organizational areas, then the remote clients who are interfacing via
phone lines etc. Consideration of intelligent topology is essential.
Example: To outline a sensible topology, the Virtual LANs (VLANs) as well as the
Virtual Private Networks (VPNs) has significant adaptability. The proposed network
topology diagram for ANOJ Software Company is shown below (Lucidchart, 2018).
Figure: Network topology architecture
Intrusion Detection Systems
This section focuses on Network Intrusion Detection Systems (NIDS) and how they it
can be utilized in our LAN for distinguishing bothersome actions. Various specialists
incorporates the IDS as the major aspect of basic components to anchor any system. The
system IDS could caution the framework chairman for assaulting on the arrangement
progressively with investigation on the activity related to the wire, and for creating cautions if
suspicious exercises are distinguished. NIDS could be a consistent PC running IDS
programming, for example, the freeware Snort, a machine compose gadget running restrictive
programming, or even a particular card worked in to a switch or other arrange component as
Cisco are presented. The host based intrusion recognition. For instance, free or business
7

forms of Tripwire, or various types of proactive log observing programming, are
subsequently exceedingly, outside the extent of this paper (SearchSecurity, 2018).
Firewall
Firewall is a device that is introduced among inside system of the organization along
with what so ever the system contains. It intends forwarding some parcels as well as the other
channels. For example, the firewall might channel each single that approaches the bundle
bound for the particular host or a particular server like, HTTP or it might be utilized for
denying accessing for a specific host or administration in an organization. In the system, any
associated image portrays the establishment of firewall.
Working Architecture
The firewall is designed appropriately, its framework on one of its side is shielded from
the frameworks on its opposite side. The firewalls in most of the parts of the channel
movement are seen two techniques:
Firewall could permit the any movement with the exception that is limited. It is based
on the firewall type used, the source, then the goal addresses, and ports.
Firewall could deny any type of activity which don’t meet specific criteria referring to
the system layer where the firewall works.
The type of criteria utilized for deciding whether the activity should be allowed
differs beginning with a single kind and next to the other one.
The firewall could be concerned of the activity types or with the goal locations as well
as the ports.
The firewall could similarly use the complicated principles with respect to examining
the application information for deciding whether the movement should be permitted.
Demilitarized Zone (DMZ)
DMZ is fundamentally executed to anchor an inner system from collaboration with and
misuse and access by outside hubs and systems. DMZ can be a legitimate sub-organize, or a
physical system going about as a safe extension between an interior and outside system. A
DMZ organize has constrained access to the inward system, and the greater part of its
correspondence is filtered on a firewall before being exchanged inside. In the event that an
assailant plans to break or assault an association's system, a fruitful endeavour will just
outcome in the trade off of the DMZ arrange - not the center system behind it. DMZ is
viewed as more secure, more secure than a firewall, and can likewise fill in as an
intermediary server.
8
subsequently exceedingly, outside the extent of this paper (SearchSecurity, 2018).
Firewall
Firewall is a device that is introduced among inside system of the organization along
with what so ever the system contains. It intends forwarding some parcels as well as the other
channels. For example, the firewall might channel each single that approaches the bundle
bound for the particular host or a particular server like, HTTP or it might be utilized for
denying accessing for a specific host or administration in an organization. In the system, any
associated image portrays the establishment of firewall.
Working Architecture
The firewall is designed appropriately, its framework on one of its side is shielded from
the frameworks on its opposite side. The firewalls in most of the parts of the channel
movement are seen two techniques:
Firewall could permit the any movement with the exception that is limited. It is based
on the firewall type used, the source, then the goal addresses, and ports.
Firewall could deny any type of activity which don’t meet specific criteria referring to
the system layer where the firewall works.
The type of criteria utilized for deciding whether the activity should be allowed
differs beginning with a single kind and next to the other one.
The firewall could be concerned of the activity types or with the goal locations as well
as the ports.
The firewall could similarly use the complicated principles with respect to examining
the application information for deciding whether the movement should be permitted.
Demilitarized Zone (DMZ)
DMZ is fundamentally executed to anchor an inner system from collaboration with and
misuse and access by outside hubs and systems. DMZ can be a legitimate sub-organize, or a
physical system going about as a safe extension between an interior and outside system. A
DMZ organize has constrained access to the inward system, and the greater part of its
correspondence is filtered on a firewall before being exchanged inside. In the event that an
assailant plans to break or assault an association's system, a fruitful endeavour will just
outcome in the trade off of the DMZ arrange - not the center system behind it. DMZ is
viewed as more secure, more secure than a firewall, and can likewise fill in as an
intermediary server.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2. Security Assumptions and Challenges
The security problems that are present in the little to medium scrutinized LAN set for a
business or other foundation are inspected, and identifies a part of the procedures that are
accepted from the system architect’s point of view (Pkware.com, 2018). If the is no similarity
among the systems, a part of the commonplace complexities are looked by the organize
fashioner who incorporates the following:
From the internet propelled attacks, the systems are secured.
Internet confronting web, the DNS and the mail servers are secured.
Causing threat from the traded off frameworks, then counteracting the inside
propelled threats.
The securing of assets like, client databases, monetary records, exchange privileged
insights, etc.
For the executives to securely manage the arrangement, a structure is built.
For logging and intrusion recognition, frameworks are provided.
Prior to the commencement of procedure outlining, a security arrangement should be
set up. If not it must be refreshed so that the objectives of the organization can be identified.
Then, a sensible assessment of threats are managed, and the asset ID (labour, equipment, and
spending plan) which are accessible must be made. The process can begin, as the strategy for
organization security and accessible assets is identified.
3. Authentication and Authorisation Mechanisms
Authentication Mechanisms
When it is needed that the server should know who is taking their data, in such case
authentication is used by the server.
When any of the customer requires realizing that, the server refers to a framework and
when it acknowledges, then in such case, the customer use the Confirmation.
In Authentication, either client or the PC are required for personality demonstration
i.e., either for the customer or for the server.
As a rule, confirmation by a server contains the use of client name and password. For
validating various methods could be through like, voice acknowledgment, cards,
retina filters and the fingerprints.
From the customer verification rule, contains the server providing endorsement to the
customer where they are confided in the outsider. Example, Verisign or Thawte states
9
The security problems that are present in the little to medium scrutinized LAN set for a
business or other foundation are inspected, and identifies a part of the procedures that are
accepted from the system architect’s point of view (Pkware.com, 2018). If the is no similarity
among the systems, a part of the commonplace complexities are looked by the organize
fashioner who incorporates the following:
From the internet propelled attacks, the systems are secured.
Internet confronting web, the DNS and the mail servers are secured.
Causing threat from the traded off frameworks, then counteracting the inside
propelled threats.
The securing of assets like, client databases, monetary records, exchange privileged
insights, etc.
For the executives to securely manage the arrangement, a structure is built.
For logging and intrusion recognition, frameworks are provided.
Prior to the commencement of procedure outlining, a security arrangement should be
set up. If not it must be refreshed so that the objectives of the organization can be identified.
Then, a sensible assessment of threats are managed, and the asset ID (labour, equipment, and
spending plan) which are accessible must be made. The process can begin, as the strategy for
organization security and accessible assets is identified.
3. Authentication and Authorisation Mechanisms
Authentication Mechanisms
When it is needed that the server should know who is taking their data, in such case
authentication is used by the server.
When any of the customer requires realizing that, the server refers to a framework and
when it acknowledges, then in such case, the customer use the Confirmation.
In Authentication, either client or the PC are required for personality demonstration
i.e., either for the customer or for the server.
As a rule, confirmation by a server contains the use of client name and password. For
validating various methods could be through like, voice acknowledgment, cards,
retina filters and the fingerprints.
From the customer verification rule, contains the server providing endorsement to the
customer where they are confided in the outsider. Example, Verisign or Thawte states
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

which the server contains place with the element, like the bank that the customer
anticipates.
What type of tasks an individual could perform or what documents the person could
access cannot be figured out by confirmation. Authentication just recognizes and
assesses about the details of the individual and their framework.
User Authentication
User Validity-The popularly identified Authentication process refers to the Log-in ID.
Furthermore, the Password-based Access Log-in which recognizes an individual to the
framework with a concern on the end goal for acquiring to get it. The important use of
Personal Computer login strategy refers to validate the PC client’s personality or PC
programming endeavouring to know about the administration of PCs. The other mainstream
of Authentication process refers to IP Filtering or IP confirmation. Such a procedure is
considered as the parcel channel which dissects the bundles of TCP/IP. Web Cookie is
another procedure of client Authentication that could be helpful for the server for perceiving
the already confirmed clients. Web Proxy is another approach to validate. The confirmation
framework likewise plays out the same cryptographic process on the test and looks at its
outcome to the reaction from the customer. On the off chance that they coordinate, the
Authentication framework has checked that the client has the right watchword (InfoSec
Resources, 2018).
Authorization Mechanisms
The authorization is referred as a procedure using which the server takes decision
whether the customer contains any authorization for utilizing the asset or have access
to the document.
Typically, authorization is combined with confirmation so that the server contains
some idea about the customer who asks for it.
A sort of verification is needed for Authorization might change; the passwords could
be needed whenever required.
Whenever required, there exists no authorization; any client could use the asset or
they can access the record just with a request. on the Internet, most of the pages
doesn’t need any verification or Authorization.
User Authorization
The Resource Access Permission-Authorization characterizes clients' consents as far as
access to computerized assets and degree of its utilization. In the Access Management
System, the authorization is allowed to the effectively confirm clients as per their rights on
10
anticipates.
What type of tasks an individual could perform or what documents the person could
access cannot be figured out by confirmation. Authentication just recognizes and
assesses about the details of the individual and their framework.
User Authentication
User Validity-The popularly identified Authentication process refers to the Log-in ID.
Furthermore, the Password-based Access Log-in which recognizes an individual to the
framework with a concern on the end goal for acquiring to get it. The important use of
Personal Computer login strategy refers to validate the PC client’s personality or PC
programming endeavouring to know about the administration of PCs. The other mainstream
of Authentication process refers to IP Filtering or IP confirmation. Such a procedure is
considered as the parcel channel which dissects the bundles of TCP/IP. Web Cookie is
another procedure of client Authentication that could be helpful for the server for perceiving
the already confirmed clients. Web Proxy is another approach to validate. The confirmation
framework likewise plays out the same cryptographic process on the test and looks at its
outcome to the reaction from the customer. On the off chance that they coordinate, the
Authentication framework has checked that the client has the right watchword (InfoSec
Resources, 2018).
Authorization Mechanisms
The authorization is referred as a procedure using which the server takes decision
whether the customer contains any authorization for utilizing the asset or have access
to the document.
Typically, authorization is combined with confirmation so that the server contains
some idea about the customer who asks for it.
A sort of verification is needed for Authorization might change; the passwords could
be needed whenever required.
Whenever required, there exists no authorization; any client could use the asset or
they can access the record just with a request. on the Internet, most of the pages
doesn’t need any verification or Authorization.
User Authorization
The Resource Access Permission-Authorization characterizes clients' consents as far as
access to computerized assets and degree of its utilization. In the Access Management
System, the authorization is allowed to the effectively confirm clients as per their rights on
10

data accessible. Additionally, authorization directs the obligation problems doled out for
various staff associated with advancement of a computerized storehouse/library and their
separate experts regarding expansion, erasure, altering and transferring of records into a
computerized gathering. Authorization refers to testing when compared to Authentication,
particularly to the appropriated computerized content suppliers. There are standard access
control models are listed below (Bu.edu, 2018).
a. Discretionary Access Control (DAC) - In a DAC Model, get to is represented by the
entrance rights allowed to the client or on the other hand client gatherings. An
association/executive/maker can distinguish an arrangement of activities and allocate
them to a protest and to an arrangement of clients.
b. Mandatory Access Control (MAC) - In MAC, the information proprietor has
restricted opportunity to settle on get to control. Data is arranged into various classes
and every classification is appointed a specific security level.
c. Role Based Access Control (RBAC) - RBAC is a generally utilized - and prevailing -
get to control display, and most get to control security items accessible in the market
today depend on this model since its destinations are compositional.
4. Key Management Issues
Due to the concern for guaranteeing the client information or for securing the
competitive innovations, various organizations alter their components just to exchange the
information using the Internet. Thus, there exists a number of interesting points during the
enhancement of information security exchange methodology, as follows:
User Authentication – FTP utilizes clear content passwords, which debilitates
security as there are possibilities that anyone could get the secret word which is
used, for gaining admittance to information.
The remote framework distinguishing proof confirmation for avoiding the capturing
of parcels by the framework.
Data protection (through encryption) with the goal that no transitional framework
could use the information.
Data security for averting change for the information, during its travel.
Preservation of information arrange. Distinctive working frameworks may store
information in diverse arrangements. When this is the case, it is attractive to have a
11
various staff associated with advancement of a computerized storehouse/library and their
separate experts regarding expansion, erasure, altering and transferring of records into a
computerized gathering. Authorization refers to testing when compared to Authentication,
particularly to the appropriated computerized content suppliers. There are standard access
control models are listed below (Bu.edu, 2018).
a. Discretionary Access Control (DAC) - In a DAC Model, get to is represented by the
entrance rights allowed to the client or on the other hand client gatherings. An
association/executive/maker can distinguish an arrangement of activities and allocate
them to a protest and to an arrangement of clients.
b. Mandatory Access Control (MAC) - In MAC, the information proprietor has
restricted opportunity to settle on get to control. Data is arranged into various classes
and every classification is appointed a specific security level.
c. Role Based Access Control (RBAC) - RBAC is a generally utilized - and prevailing -
get to control display, and most get to control security items accessible in the market
today depend on this model since its destinations are compositional.
4. Key Management Issues
Due to the concern for guaranteeing the client information or for securing the
competitive innovations, various organizations alter their components just to exchange the
information using the Internet. Thus, there exists a number of interesting points during the
enhancement of information security exchange methodology, as follows:
User Authentication – FTP utilizes clear content passwords, which debilitates
security as there are possibilities that anyone could get the secret word which is
used, for gaining admittance to information.
The remote framework distinguishing proof confirmation for avoiding the capturing
of parcels by the framework.
Data protection (through encryption) with the goal that no transitional framework
could use the information.
Data security for averting change for the information, during its travel.
Preservation of information arrange. Distinctive working frameworks may store
information in diverse arrangements. When this is the case, it is attractive to have a
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





