IT Security Report: Risk Assessment and Policy Recommendations
VerifiedAdded on 2022/11/13
|14
|3006
|309
Report
AI Summary
This report provides a detailed analysis of IT security within an organization, focusing on risk assessment, disaster management, and the development of enhanced IT policies. The report begins with an introduction to risk assessment, defining it as a review of potential threats, both human-made and natural, and their impact on organizational operations. It emphasizes the importance of disaster management and the use of Geographical Information Systems in emergency situations. The discussion section delves into the growing significance of IT risk management, the automation of risk management programs, and the process of managing risks associated with information technology, including asset identification, vulnerability assessment, and threat analysis. The report outlines the steps for identifying assets, vulnerabilities, and threats, as well as implementing controls. It also explains the risk assessment process, risk treatment options (remediation, mitigation, transference, risk acceptance, and avoidance), and the importance of stakeholder involvement and accountability. The report concludes by emphasizing the roles of various stakeholders in the IT security process, from the finance team to the ISRM team and risk owners, ensuring smooth operation and the importance of clear responsibilities.

0Running head: IT SECURITY IN AN ORGANIZATION
IT SECURITY OF AN ORGANIZATION
Name of the Student
Name of the Organization
Author notes
IT SECURITY OF AN ORGANIZATION
Name of the Student
Name of the Organization
Author notes
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT SECURITY IN AN ORGANIZATION
Executive Summary
This report discusses regarding risk assessment related the Information Technology in an
organization. This report also discusses regarding the risk assessment related to the disaster
management and also the management plan. It also tells the set of the enhanced IT policies for
including the data protection, whistle blowing policy, Acceptance Use Policy, backup policy,
Staff training policy, and also the password policy.
Executive Summary
This report discusses regarding risk assessment related the Information Technology in an
organization. This report also discusses regarding the risk assessment related to the disaster
management and also the management plan. It also tells the set of the enhanced IT policies for
including the data protection, whistle blowing policy, Acceptance Use Policy, backup policy,
Staff training policy, and also the password policy.

2IT SECURITY IN AN ORGANIZATION
Table of Contents
Introduction:....................................................................................................................................3
Discussion........................................................................................................................................3
Conclusion.......................................................................................................................................9
References:....................................................................................................................................10
Table of Contents
Introduction:....................................................................................................................................3
Discussion........................................................................................................................................3
Conclusion.......................................................................................................................................9
References:....................................................................................................................................10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT SECURITY IN AN ORGANIZATION
Introduction:
The risk assessment of the information technology is a kind of document that is used to
review that has the possible threats that the company faces, human made and/or natural (Cardona
2013). These threats are weighted by the occurrence of the likelihood and after that it is affect the
operation section of the organization in the exponential manner. Disaster Management is a very
important part of the management of the emergency situation that enhanced the programme
which are developed and is implemented by using the analysis and the information of the IT
(Chang and Ramachandran m 2015). The majority of the Geographical Information System is
allowing the emergency situation for identifying the cause of the disaster. For this case, the size
and the scope of the emergency situation of that organization is very logically. The appropriate
steps regarding this matter should be taken very carefully. This report discusses regarding the
risk assessment regarding the IT services and also the related data (Cole et al. 2013). It also
discusses regarding the policy of the disaster management and also the recovery plan. This report
also discusses regarding the data protection, the whistle blowing policy, backup policy and also
the staff training policy and many others.
Discussion
In today’s world the risk management in the IT industry is gaining its popularity. The
tremendous compliance effort for dealing with many regulations in separate manner and audit
each regulation individually (Glendon and Clarke 2015). It may often distract the ability of the
company for identifying the risk exposure in the true manner. Different company offers the IT
risk management in automated form. It will provide the guidance and support for selecting,
Introduction:
The risk assessment of the information technology is a kind of document that is used to
review that has the possible threats that the company faces, human made and/or natural (Cardona
2013). These threats are weighted by the occurrence of the likelihood and after that it is affect the
operation section of the organization in the exponential manner. Disaster Management is a very
important part of the management of the emergency situation that enhanced the programme
which are developed and is implemented by using the analysis and the information of the IT
(Chang and Ramachandran m 2015). The majority of the Geographical Information System is
allowing the emergency situation for identifying the cause of the disaster. For this case, the size
and the scope of the emergency situation of that organization is very logically. The appropriate
steps regarding this matter should be taken very carefully. This report discusses regarding the
risk assessment regarding the IT services and also the related data (Cole et al. 2013). It also
discusses regarding the policy of the disaster management and also the recovery plan. This report
also discusses regarding the data protection, the whistle blowing policy, backup policy and also
the staff training policy and many others.
Discussion
In today’s world the risk management in the IT industry is gaining its popularity. The
tremendous compliance effort for dealing with many regulations in separate manner and audit
each regulation individually (Glendon and Clarke 2015). It may often distract the ability of the
company for identifying the risk exposure in the true manner. Different company offers the IT
risk management in automated form. It will provide the guidance and support for selecting,
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT SECURITY IN AN ORGANIZATION
integrating and also automating the multiple types of the risk management programs with the IT
governance in the centralized form and also the risk and the compliance platform.
Information security risk management is the process of the managing different kinds of
the risk which is associated with the use of the information technology (Hopkin 2018). It
includes the identification, assessing, treating of the different kinds of the risk for the
confidentiality of the information, integrity and the availability of the information are the assets
of the organization (Lam 2014). The ultimate goal of this process is to take the risk such a way
that organization can tolerate the risk (Patil and Seshadri 2014). The businesses should not
expect the elimination of all risks. Being a security manager of that organization that person
should follow some stages for doing the ISRM:
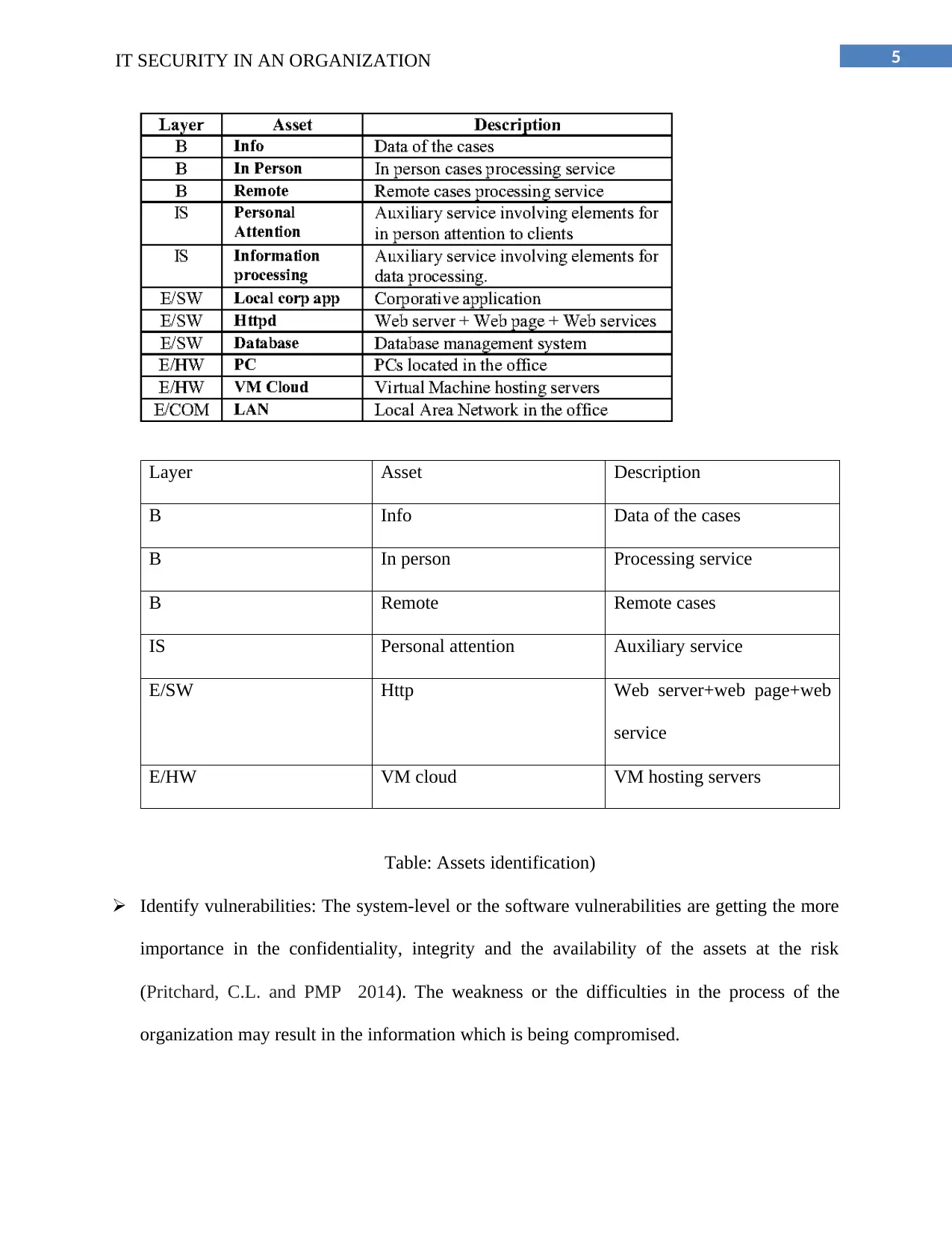
Identify assets: First of all, the security manager should identify that which assets would have
the significance on that organization if the confidentiality, integrity, or availability is
compromised (Peltier, 2013). It is not very difficult to check the reason behind the
importance of the social security numbers and the intellectual property. If the business falls
under the regulatory system of the ISO27001 then there will not be a major problem in the
reporting of the financial data that may be result in the huge cost (Peltier 2016). The
organization is doing the transaction of the for the online payment is debit card, if the server
is not available for the payment then the company may lose the large number of the
customers.
integrating and also automating the multiple types of the risk management programs with the IT
governance in the centralized form and also the risk and the compliance platform.
Information security risk management is the process of the managing different kinds of
the risk which is associated with the use of the information technology (Hopkin 2018). It
includes the identification, assessing, treating of the different kinds of the risk for the
confidentiality of the information, integrity and the availability of the information are the assets
of the organization (Lam 2014). The ultimate goal of this process is to take the risk such a way
that organization can tolerate the risk (Patil and Seshadri 2014). The businesses should not
expect the elimination of all risks. Being a security manager of that organization that person
should follow some stages for doing the ISRM:
Identify assets: First of all, the security manager should identify that which assets would have
the significance on that organization if the confidentiality, integrity, or availability is
compromised (Peltier, 2013). It is not very difficult to check the reason behind the
importance of the social security numbers and the intellectual property. If the business falls
under the regulatory system of the ISO27001 then there will not be a major problem in the
reporting of the financial data that may be result in the huge cost (Peltier 2016). The
organization is doing the transaction of the for the online payment is debit card, if the server
is not available for the payment then the company may lose the large number of the
customers.
5IT SECURITY IN AN ORGANIZATION
Layer Asset Description
B Info Data of the cases
B In person Processing service
B Remote Remote cases
IS Personal attention Auxiliary service
E/SW Http Web server+web page+web
service
E/HW VM cloud VM hosting servers
Table: Assets identification)
Identify vulnerabilities: The system-level or the software vulnerabilities are getting the more
importance in the confidentiality, integrity and the availability of the assets at the risk
(Pritchard, C.L. and PMP 2014). The weakness or the difficulties in the process of the
organization may result in the information which is being compromised.
Layer Asset Description
B Info Data of the cases
B In person Processing service
B Remote Remote cases
IS Personal attention Auxiliary service
E/SW Http Web server+web page+web
service
E/HW VM cloud VM hosting servers
Table: Assets identification)
Identify vulnerabilities: The system-level or the software vulnerabilities are getting the more
importance in the confidentiality, integrity and the availability of the assets at the risk
(Pritchard, C.L. and PMP 2014). The weakness or the difficulties in the process of the
organization may result in the information which is being compromised.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6IT SECURITY IN AN ORGANIZATION
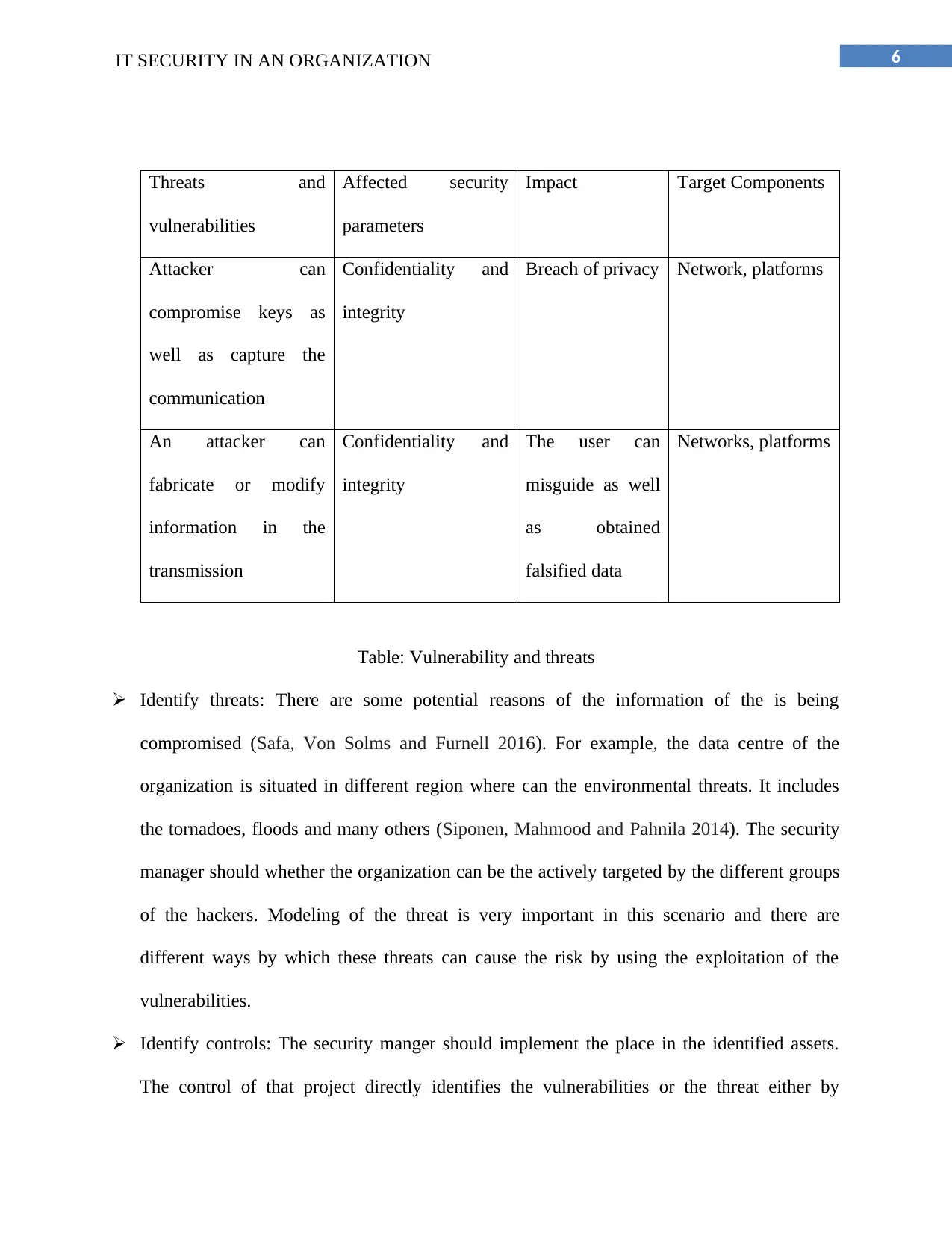
Threats and
vulnerabilities
Affected security
parameters
Impact Target Components
Attacker can
compromise keys as
well as capture the
communication
Confidentiality and
integrity
Breach of privacy Network, platforms
An attacker can
fabricate or modify
information in the
transmission
Confidentiality and
integrity
The user can
misguide as well
as obtained
falsified data
Networks, platforms
Table: Vulnerability and threats
Identify threats: There are some potential reasons of the information of the is being
compromised (Safa, Von Solms and Furnell 2016). For example, the data centre of the
organization is situated in different region where can the environmental threats. It includes
the tornadoes, floods and many others (Siponen, Mahmood and Pahnila 2014). The security
manager should whether the organization can be the actively targeted by the different groups
of the hackers. Modeling of the threat is very important in this scenario and there are
different ways by which these threats can cause the risk by using the exploitation of the
vulnerabilities.
Identify controls: The security manger should implement the place in the identified assets.
The control of that project directly identifies the vulnerabilities or the threat either by
Threats and
vulnerabilities
Affected security
parameters
Impact Target Components
Attacker can
compromise keys as
well as capture the
communication
Confidentiality and
integrity
Breach of privacy Network, platforms
An attacker can
fabricate or modify
information in the
transmission
Confidentiality and
integrity
The user can
misguide as well
as obtained
falsified data
Networks, platforms
Table: Vulnerability and threats
Identify threats: There are some potential reasons of the information of the is being
compromised (Safa, Von Solms and Furnell 2016). For example, the data centre of the
organization is situated in different region where can the environmental threats. It includes
the tornadoes, floods and many others (Siponen, Mahmood and Pahnila 2014). The security
manager should whether the organization can be the actively targeted by the different groups
of the hackers. Modeling of the threat is very important in this scenario and there are
different ways by which these threats can cause the risk by using the exploitation of the
vulnerabilities.
Identify controls: The security manger should implement the place in the identified assets.
The control of that project directly identifies the vulnerabilities or the threat either by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT SECURITY IN AN ORGANIZATION
resolving this one completely (Von Solms and Van Niekerk 2013). For example, if the
company has the identified risk for the users for continuing the task that have the access to
the specific application. Control could be the process that removes this one automatically
from the application of the users f or the termination. A control related to the compensation is
the safe way for controlling the indirect access of the risk (Warkentin and Baskerville 2013).
A compensating control may the access quarterly in a certain year for the review process
related to the data security (Xu et al. 2014). During this kind of the review the application of
the customer is cross referenced with the user directory available at the office of the company
and the list of the termination is to find the users with the unwarranted access and then it can
be removed from the insecure access when this type of the resource will be found.
Assessment: This is the process of the combination of the information that the security
manager has gathered regarding the assets, vulnerabilities, and also the controls for defining
the risk. There are many platforms available for doing this. The equation for calculating the
risk includes:
Risk= (threat*vulnerabilities (exploit likelihood*exploit impact) * asset value) – security
controls.
Treatment: Once the risk has been identified and also analyzed in detail. The company
should select the different treatment options:
Remediation: Implementing the different control measures for the different security
issues related to the information technology industry (Yang, Shieh, and Tzeng 2013).
For example, the security manager has detected an issue related to the vulnerability
on the server of the company and he/she can apply for the software patch for that
particular vulnerability.
resolving this one completely (Von Solms and Van Niekerk 2013). For example, if the
company has the identified risk for the users for continuing the task that have the access to
the specific application. Control could be the process that removes this one automatically
from the application of the users f or the termination. A control related to the compensation is
the safe way for controlling the indirect access of the risk (Warkentin and Baskerville 2013).
A compensating control may the access quarterly in a certain year for the review process
related to the data security (Xu et al. 2014). During this kind of the review the application of
the customer is cross referenced with the user directory available at the office of the company
and the list of the termination is to find the users with the unwarranted access and then it can
be removed from the insecure access when this type of the resource will be found.
Assessment: This is the process of the combination of the information that the security
manager has gathered regarding the assets, vulnerabilities, and also the controls for defining
the risk. There are many platforms available for doing this. The equation for calculating the
risk includes:
Risk= (threat*vulnerabilities (exploit likelihood*exploit impact) * asset value) – security
controls.
Treatment: Once the risk has been identified and also analyzed in detail. The company
should select the different treatment options:
Remediation: Implementing the different control measures for the different security
issues related to the information technology industry (Yang, Shieh, and Tzeng 2013).
For example, the security manager has detected an issue related to the vulnerability
on the server of the company and he/she can apply for the software patch for that
particular vulnerability.

8IT SECURITY IN AN ORGANIZATION
Mitigation: The security manager must understand the risk related to different
information and data security applications (Zhang 2018). For example, the security
manager is already identified the vulnerability issues in the server where the different
a firewall rules have to be implemented. There are some specific systems by which
the communication can be established by using the vulnerable service.
Transference: The risk transfer is another entity for that organization, so that it can
recover from the incurred costs of the risk which is realized (Yang, Shieh and Tzeng
2013). For example, the purchase that will cover the losses that would be affected if
the vulnerable systems are affected. This can be used to supplement the remediation
of the risk and also the mitigation but it is no replaced from that system altogether.
Risk acceptance: This is the appropriate in the cases where the risk which is clearly
low and the time and effort it takes for fixing the cost of the risk which is more than
any kind of risk.
Avoidance of the risk: Removing all the risks related to the information and the data
security can be avoided by taking some special measures (Xu et al. 2014). For
example, if the security manger detects those servers with the operating systems
which is about to the end-of-life then some security patches should receive from the
developer of the operating system. These servers are processing and also responsible
for storing the sensitive data that can be compromised (Xu et al. 2014). For avoiding
the above-mentioned risk there should be some kind of the protection of the sensitive
data. The security manager can quickly transfer the sensitive data to the new data and
also the server which can be patchable. The servers are able to continue for running
Mitigation: The security manager must understand the risk related to different
information and data security applications (Zhang 2018). For example, the security
manager is already identified the vulnerability issues in the server where the different
a firewall rules have to be implemented. There are some specific systems by which
the communication can be established by using the vulnerable service.
Transference: The risk transfer is another entity for that organization, so that it can
recover from the incurred costs of the risk which is realized (Yang, Shieh and Tzeng
2013). For example, the purchase that will cover the losses that would be affected if
the vulnerable systems are affected. This can be used to supplement the remediation
of the risk and also the mitigation but it is no replaced from that system altogether.
Risk acceptance: This is the appropriate in the cases where the risk which is clearly
low and the time and effort it takes for fixing the cost of the risk which is more than
any kind of risk.
Avoidance of the risk: Removing all the risks related to the information and the data
security can be avoided by taking some special measures (Xu et al. 2014). For
example, if the security manger detects those servers with the operating systems
which is about to the end-of-life then some security patches should receive from the
developer of the operating system. These servers are processing and also responsible
for storing the sensitive data that can be compromised (Xu et al. 2014). For avoiding
the above-mentioned risk there should be some kind of the protection of the sensitive
data. The security manager can quickly transfer the sensitive data to the new data and
also the server which can be patchable. The servers are able to continue for running
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT SECURITY IN AN ORGANIZATION
and the processing of the sensitive data when the plan is designed for attract them and
also for migrating from the non-sensitive data to the other servers.
The decision needs to be communicated within the organization of how the risk is being
treated. Stakeholders should understand the price of the treating or the non-treating of the risk
related to the information technology and there should be some reason behind the decision
(Warkentin and Baskerville 2013). Accountability and also the responsibility should be very
clear that can be defined and also associated with the individuals and also the teams within the
organization for ensuring the appropriate people that are involved at the correct times in the
process (Von Solms and Van Niekerk 2013). If the security manager chooses the payment
gateway for implementing the control, that needs to be seriously examined. He or she is very
likely for inserting the control into the system that is used to change over time. The ports of the
servers can be opened by the security manager, the code of the server can be changed, and also
the other factors can control for breaking down in the time span of the months and also the years,
which is used to follow the preliminary implementation (Siponen, Mahmood and Pahnila
2014.). There are many stakeholders which are in the ISRM processes and each of these have the
different responsibilities. The critical step of this is to conduct the process very smoothly.
Owner of the certain process: At the upper level, the company must have the finance
team or the audit team that is responsible to calculate the cost of Enterprise
Management Program, when the team of the Information Security will become the
owner of the program of the ISRM. It feeds into the ERM. Staffs of the ISRM team
need to be in the position of continuation of the program.
and the processing of the sensitive data when the plan is designed for attract them and
also for migrating from the non-sensitive data to the other servers.
The decision needs to be communicated within the organization of how the risk is being
treated. Stakeholders should understand the price of the treating or the non-treating of the risk
related to the information technology and there should be some reason behind the decision
(Warkentin and Baskerville 2013). Accountability and also the responsibility should be very
clear that can be defined and also associated with the individuals and also the teams within the
organization for ensuring the appropriate people that are involved at the correct times in the
process (Von Solms and Van Niekerk 2013). If the security manager chooses the payment
gateway for implementing the control, that needs to be seriously examined. He or she is very
likely for inserting the control into the system that is used to change over time. The ports of the
servers can be opened by the security manager, the code of the server can be changed, and also
the other factors can control for breaking down in the time span of the months and also the years,
which is used to follow the preliminary implementation (Siponen, Mahmood and Pahnila
2014.). There are many stakeholders which are in the ISRM processes and each of these have the
different responsibilities. The critical step of this is to conduct the process very smoothly.
Owner of the certain process: At the upper level, the company must have the finance
team or the audit team that is responsible to calculate the cost of Enterprise
Management Program, when the team of the Information Security will become the
owner of the program of the ISRM. It feeds into the ERM. Staffs of the ISRM team
need to be in the position of continuation of the program.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT SECURITY IN AN ORGANIZATION
Risk Owners: The risks related to the individual employees of that company who will
close the process by using the budget for the payment and also the fixing of the
problem (Safa, Von Solms and Furnell 2016). In the other way, owner of risk
assessment is auditable for ensuring the risks that can be treated. If the security
manager approves the budget, then he/she will be the owner of the risk. In addition to
this there will be different types of the stakeholders who will be either impacted by or
involved in the implementation. For example, the information security team of the
company is conducting the process stipulated by the ISRM. The risk of the
availability of the company’s customer relationship management system is to be
identified (Cardona 2013). With the help of the head of the IT team (who is also the
owner of the CRM team) and also the individual employee in the IT team who
manages this kind of the system on the day to day basis (who is the CRM system
administrator), helps the process owners for gathering the information related to the
assessment of the risk. The data available in the system of the company may become
unavailable will impact the reputation of the company. The risk owner should be able
to implement the different kinds of the different kinds of the treatment plan (Chang
and Ramachandran 2015). There are different kinds of the treatment plans are
implemented which can be offered by the information security team, system
administrators, system owners, and many others. They can accept any kind of the
risk. The system owner and system administrator can involve themselves again in this
kind of the process.
Risk Owners: The risks related to the individual employees of that company who will
close the process by using the budget for the payment and also the fixing of the
problem (Safa, Von Solms and Furnell 2016). In the other way, owner of risk
assessment is auditable for ensuring the risks that can be treated. If the security
manager approves the budget, then he/she will be the owner of the risk. In addition to
this there will be different types of the stakeholders who will be either impacted by or
involved in the implementation. For example, the information security team of the
company is conducting the process stipulated by the ISRM. The risk of the
availability of the company’s customer relationship management system is to be
identified (Cardona 2013). With the help of the head of the IT team (who is also the
owner of the CRM team) and also the individual employee in the IT team who
manages this kind of the system on the day to day basis (who is the CRM system
administrator), helps the process owners for gathering the information related to the
assessment of the risk. The data available in the system of the company may become
unavailable will impact the reputation of the company. The risk owner should be able
to implement the different kinds of the different kinds of the treatment plan (Chang
and Ramachandran 2015). There are different kinds of the treatment plans are
implemented which can be offered by the information security team, system
administrators, system owners, and many others. They can accept any kind of the
risk. The system owner and system administrator can involve themselves again in this
kind of the process.

11IT SECURITY IN AN ORGANIZATION
Conclusion
In this report it is discussed the importance of the information security in an organization
and also discusses briefly regarding the disaster management in organization. It also discusses
the risk assessment of the information and the data security. There are some legal issues related
to the IT security in an organization. The company should implement these legal issues related
the information and also the data security in that organization. This report concludes that for
protecting the information and the data of that organization the security manager, System
administrator, and also the other system engineers should take the strong step and the security
measure regarding this matter.
Conclusion
In this report it is discussed the importance of the information security in an organization
and also discusses briefly regarding the disaster management in organization. It also discusses
the risk assessment of the information and the data security. There are some legal issues related
to the IT security in an organization. The company should implement these legal issues related
the information and also the data security in that organization. This report concludes that for
protecting the information and the data of that organization the security manager, System
administrator, and also the other system engineers should take the strong step and the security
measure regarding this matter.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 14
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





