IT Security Assignment: Protecting Information Systems
VerifiedAdded on 2023/06/10
|8
|1360
|274
Homework Assignment
AI Summary
This assignment delves into various aspects of IT security, beginning with an examination of protective measures for new online businesses, including threat assessment, data confidentiality, and the importance of authentication and access controls. It then outlines essential information security policies, such as Acceptable Use, Confidential Data, Email, Authentication, Network Security, and Physical Security policies. The assignment further discusses methods for protecting information in computer systems, emphasizing the role of cryptography, secure password practices, access control lists, and regular data backups. Finally, it analyzes the business use of 2-key triple DES, comparing its benefits and vulnerabilities, and recommending the use of 3DES for enhanced security. The document references several sources to support the discussed concepts.

IT Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1 | P a g e I T S e c u r i t y
Table of Contents
Answer to question1-Protective measures.................................................................................2
Answer to question2- Information Security Policy....................................................................2
Answer to question3- Protecting information in computer system............................................3
Answer to question 4- Business use 2-key triple DES...............................................................4
References..................................................................................................................................5
Table of Contents
Answer to question1-Protective measures.................................................................................2
Answer to question2- Information Security Policy....................................................................2
Answer to question3- Protecting information in computer system............................................3
Answer to question 4- Business use 2-key triple DES...............................................................4
References..................................................................................................................................5

2 | P a g e I T S e c u r i t y
Answer to question1-Protective measures
When a company starts up a new online business there are various things that need to
be measured. The first phase includes threat assessment in which all the natural as well as
third party attacks are analysed. This asset takes care of all the threats that could breach the
security of information. The information that is stored online of the business need to be kept
confidential and integrity thus for that protective measures are taken so that it do not cause
loss to the company. The other risk of online business can be that competitors are using the
data or some information is getting leaked through side door. Thus it is recommended that
before starting the business online various security issues like proper authentication an access
controls are assigned (Ncsc, 2016). Apart from that all the assets that are used by the business
should be upgraded to latest technology so that vulnerabilities can be managed. The data and
information that is provided by the business should have a proper access otherwise it will led
to privacy issue (Safa, Von Solms & Furnell, 2016). Most important while the business is
incorporate online the copyright should be used so that no one else can copy their unique idea
and plan.
The business mostly follows the framework to manage the business risk by assessing
the possible risk and then establishing a proper management plan. Information security
Answer to question1-Protective measures
When a company starts up a new online business there are various things that need to
be measured. The first phase includes threat assessment in which all the natural as well as
third party attacks are analysed. This asset takes care of all the threats that could breach the
security of information. The information that is stored online of the business need to be kept
confidential and integrity thus for that protective measures are taken so that it do not cause
loss to the company. The other risk of online business can be that competitors are using the
data or some information is getting leaked through side door. Thus it is recommended that
before starting the business online various security issues like proper authentication an access
controls are assigned (Ncsc, 2016). Apart from that all the assets that are used by the business
should be upgraded to latest technology so that vulnerabilities can be managed. The data and
information that is provided by the business should have a proper access otherwise it will led
to privacy issue (Safa, Von Solms & Furnell, 2016). Most important while the business is
incorporate online the copyright should be used so that no one else can copy their unique idea
and plan.
The business mostly follows the framework to manage the business risk by assessing
the possible risk and then establishing a proper management plan. Information security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3 | P a g e I T S e c u r i t y
planning is vital for implementing and maintains a secure environment. While starting the
business online there are various measures that need to be undertaken to make sure that all
the assets and threats are measured and protective steps are taken.
Answer to question2- Information Security Policy
To make sure that a company is free from security breaches various policies need to
be used.
Acceptable Use Policy- This policy is important for every business as it allow only valid
user to access the data (Nordquist. 2016)
. It prohibits the access of unauthorized users which assures that all the
resources are secured.
Confidential Data Policy- This is important for every company as it assures
that data is kept confidential and can be handled by only valid users.
Email Policy- Company faces most of the threats due to emails as it affects
the liability factor of an organisation. This policy takes into account all the
gateways of emails so that network of the business is not hacked.
Authentication policy- this is essential to showcase who can read, write and
modify the business data. It covers the right that need to be given to the users
(Nordquist. 2016).
Network Security Policy- this is the main policy that very business should
follow as it assure that the data will be kept in an integrated manner and the
chances of security risk would be mitigated. It also controls the path through
which communication exists.
Physical Security Policy- It is not only important to protect the network but
all the assets owned by company should be kept protected.
planning is vital for implementing and maintains a secure environment. While starting the
business online there are various measures that need to be undertaken to make sure that all
the assets and threats are measured and protective steps are taken.
Answer to question2- Information Security Policy
To make sure that a company is free from security breaches various policies need to
be used.
Acceptable Use Policy- This policy is important for every business as it allow only valid
user to access the data (Nordquist. 2016)
. It prohibits the access of unauthorized users which assures that all the
resources are secured.
Confidential Data Policy- This is important for every company as it assures
that data is kept confidential and can be handled by only valid users.
Email Policy- Company faces most of the threats due to emails as it affects
the liability factor of an organisation. This policy takes into account all the
gateways of emails so that network of the business is not hacked.
Authentication policy- this is essential to showcase who can read, write and
modify the business data. It covers the right that need to be given to the users
(Nordquist. 2016).
Network Security Policy- this is the main policy that very business should
follow as it assure that the data will be kept in an integrated manner and the
chances of security risk would be mitigated. It also controls the path through
which communication exists.
Physical Security Policy- It is not only important to protect the network but
all the assets owned by company should be kept protected.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4 | P a g e I T S e c u r i t y
Answer to question3- Protecting information in computer system
To protect the information in the computer system there are many ways.
Cryptography is often considered an important tool for protecting information in
computer system as even if the data is leaked by third part user they will not be able to read
the actual data. As in cryptography the data packets are encoded in the language that is not
readable by human that is chipper text. Thus it is the best way to protect the data over the
network. On the other hand it is always recommended that data and files should not be
downloaded from unauthorized sources (Siponen & Vance, 2014). The passwords used in
business should be strong enough so that it is not breached by some third party.
To protect the information on computer system important approach is access control
list that address the list of names who are allowed to access the information. From this policy
no unauthorised user will be able to access the information. To protect the information over
the network it is recommended that regular backups should be taken so that in case of site
failure data could be recovered. Security of information is important thus to maintain
integrity, confidentially and availability various measures are undertaken. The best way is
cryptography as it stores the data and transmits to only those who can read and process it
Answer to question3- Protecting information in computer system
To protect the information in the computer system there are many ways.
Cryptography is often considered an important tool for protecting information in
computer system as even if the data is leaked by third part user they will not be able to read
the actual data. As in cryptography the data packets are encoded in the language that is not
readable by human that is chipper text. Thus it is the best way to protect the data over the
network. On the other hand it is always recommended that data and files should not be
downloaded from unauthorized sources (Siponen & Vance, 2014). The passwords used in
business should be strong enough so that it is not breached by some third party.
To protect the information on computer system important approach is access control
list that address the list of names who are allowed to access the information. From this policy
no unauthorised user will be able to access the information. To protect the information over
the network it is recommended that regular backups should be taken so that in case of site
failure data could be recovered. Security of information is important thus to maintain
integrity, confidentially and availability various measures are undertaken. The best way is
cryptography as it stores the data and transmits to only those who can read and process it

5 | P a g e I T S e c u r i t y
(Bauer & Bernroider, 2017). The main objective of this technique is that it maintains
confidentiality, integrity, authentication and non-repudiation of the information. Thus
information needs to be protected so that all the sensitive data remains confidential and
available to valid users.
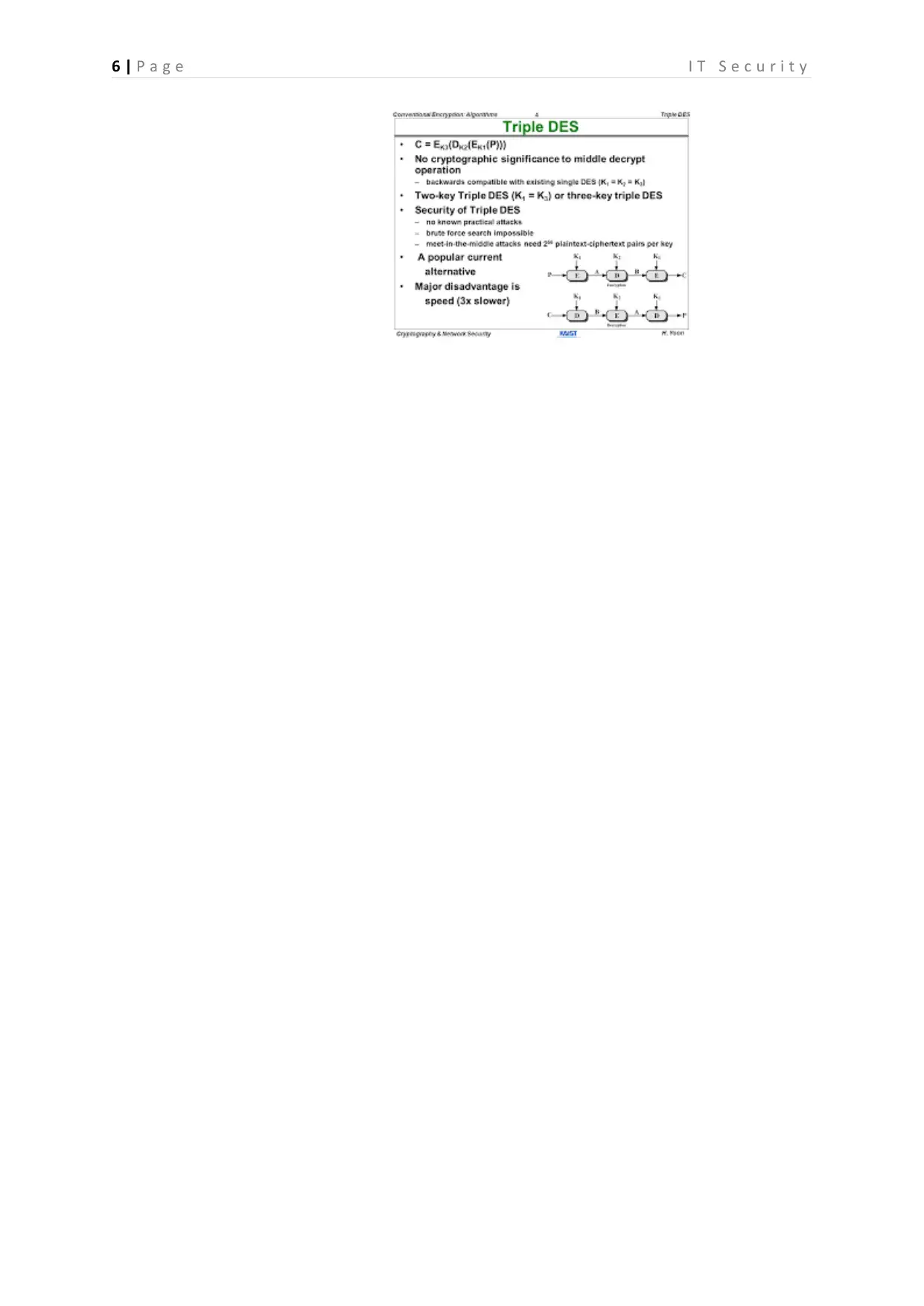
Answer to question 4- Business use 2-key triple DES
In today’s world business make use of 2-key DES rather than 3 DES strategies. 2-key
DES is also beneficial as it make use of 56 bit key that assures that brute force attack will not
impact the security of network. It is easy to be used as both encryption and decryption
follows same algorithm. In some cases it do not result appropriate result (Aleisa. 2016).
Thus it is recommended that business should use 3DES as 2-key DES is vulnerable to man in
the middle attack. It is much stronger than 2-key Des it has higher security measures. This is
highly secured as the scheme prevents the production of sub keys directly and also increases
the randomness in generating keys that leads to difficulty in hacking the information. the key
space is also extended in this case. The output generated by triple DES is slower but it is
highly secure and reliable (Aleisa. 2016). However, the power of computers is growing day
by day thus it is recommended that stronger algorithms are required to face hacker attacks.
The response to this is using 3DES so that all the hardware and software’s of the company
work correctly without any chances of information getting hacked. It might be possible that
use of 3DES is complicated but it is strongly secure.
(Bauer & Bernroider, 2017). The main objective of this technique is that it maintains
confidentiality, integrity, authentication and non-repudiation of the information. Thus
information needs to be protected so that all the sensitive data remains confidential and
available to valid users.
Answer to question 4- Business use 2-key triple DES
In today’s world business make use of 2-key DES rather than 3 DES strategies. 2-key
DES is also beneficial as it make use of 56 bit key that assures that brute force attack will not
impact the security of network. It is easy to be used as both encryption and decryption
follows same algorithm. In some cases it do not result appropriate result (Aleisa. 2016).
Thus it is recommended that business should use 3DES as 2-key DES is vulnerable to man in
the middle attack. It is much stronger than 2-key Des it has higher security measures. This is
highly secured as the scheme prevents the production of sub keys directly and also increases
the randomness in generating keys that leads to difficulty in hacking the information. the key
space is also extended in this case. The output generated by triple DES is slower but it is
highly secure and reliable (Aleisa. 2016). However, the power of computers is growing day
by day thus it is recommended that stronger algorithms are required to face hacker attacks.
The response to this is using 3DES so that all the hardware and software’s of the company
work correctly without any chances of information getting hacked. It might be possible that
use of 3DES is complicated but it is strongly secure.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6 | P a g e I T S e c u r i t y
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7 | P a g e I T S e c u r i t y
References
Aleisa. N. (2016). A Comparison of the 3DES and AES Encryption
Standards. Retrieved from http://www.sersc.org/journals/IJSIA/vol9_no7_2015/21.pdf.
Bauer, S., & Bernroider, E. W. (2017). From information security awareness to
reasoned compliant action: analyzing information security policy compliance in a large
banking organization. ACM SIGMIS Database: the DATABASE for Advances in Information
Systems, 48(3), 44-68.
Ncsc. (2016). MANAGE THE BUSINESS RISK. Retrieved from
https://www.ncsc.gov.uk/content/files/protected_files/guidance_files/SICS%20-%20Manage
%20The%20Business%20Risk%20Final%20v1%201_0.pdf.
Nordquist. C. (2016). 9 POLICIES YOUR IT SECURITY PLAN NEEDS TO
HAVE. Retrieved from https://www.annese.com/blog/how-to-create-your-it-security-policy.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy
compliance model in organizations. Computers & Security, 56, 70-82.
Siponen, M., & Vance, A. (2014). Guidelines for improving the contextual relevance
of field surveys: the case of information security policy violations. European Journal of
Information Systems, 23(3), 289-305.
References
Aleisa. N. (2016). A Comparison of the 3DES and AES Encryption
Standards. Retrieved from http://www.sersc.org/journals/IJSIA/vol9_no7_2015/21.pdf.
Bauer, S., & Bernroider, E. W. (2017). From information security awareness to
reasoned compliant action: analyzing information security policy compliance in a large
banking organization. ACM SIGMIS Database: the DATABASE for Advances in Information
Systems, 48(3), 44-68.
Ncsc. (2016). MANAGE THE BUSINESS RISK. Retrieved from
https://www.ncsc.gov.uk/content/files/protected_files/guidance_files/SICS%20-%20Manage
%20The%20Business%20Risk%20Final%20v1%201_0.pdf.
Nordquist. C. (2016). 9 POLICIES YOUR IT SECURITY PLAN NEEDS TO
HAVE. Retrieved from https://www.annese.com/blog/how-to-create-your-it-security-policy.
Safa, N. S., Von Solms, R., & Furnell, S. (2016). Information security policy
compliance model in organizations. Computers & Security, 56, 70-82.
Siponen, M., & Vance, A. (2014). Guidelines for improving the contextual relevance
of field surveys: the case of information security policy violations. European Journal of
Information Systems, 23(3), 289-305.
1 out of 8
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





