University IT Assignment: System Security, Privacy, Ethics, Copyright
VerifiedAdded on 2023/04/04
|9
|823
|463
Homework Assignment
AI Summary
This IT assignment delves into critical aspects of information technology, focusing on system security, privacy, ethics, and copyright. It begins with an explanation of organizational policies and procedures related to system security, emphasizing the importance of maintaining privacy and data integrity. The assignment then explores the security features of a server operating system, detailing how these features protect privacy, ethical considerations, and copyright information. Furthermore, it examines organizational communication processes and procedures necessary for upholding privacy, copyright, and ethical standards. The document identifies key areas for effective customer communication and concludes with an explanation of the ACS Code of Ethics and its role in the ICT industry, ensuring ethical practices within the field. This assignment provides a comprehensive overview of these crucial IT topics.

Running head: INFORMATION TECHNOLOGY
Information Technology
Name of the Student
Name of the University
Author’s Note:
Information Technology
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
INFORMATION TECHNOLOGY
Table of Contents
Question 6..................................................................................................................................3
Question 7..................................................................................................................................4
Question 8..................................................................................................................................5
Question 9..................................................................................................................................7
Question 10................................................................................................................................8
References..................................................................................................................................9
INFORMATION TECHNOLOGY
Table of Contents
Question 6..................................................................................................................................3
Question 7..................................................................................................................................4
Question 8..................................................................................................................................5
Question 9..................................................................................................................................7
Question 10................................................................................................................................8
References..................................................................................................................................9

3
INFORMATION TECHNOLOGY
Question 6
Explanation of an Organizational Policy or Procedure related to System Security for
Privacy and Data
i) Privacy: An organizational policy related to system security for privacy includes
maintenance of systems and other organizational equipment with the purpose of providing
high security and ensuring that these systems are working or functioning without any type of
complexity (Schwalbe 2015). Privacy ensures that controlling of unauthorized access to
organizational resources.
ii) Data: Organizational policy related to security of system for data includes data
content, classification, ownership and security. This type of security eventually compromises
about jeopardizing ability in providing services or loss of revenue through destruction of
confidential data and also reducing reputation and credibility with shareholders and
customers.
INFORMATION TECHNOLOGY
Question 6
Explanation of an Organizational Policy or Procedure related to System Security for
Privacy and Data
i) Privacy: An organizational policy related to system security for privacy includes
maintenance of systems and other organizational equipment with the purpose of providing
high security and ensuring that these systems are working or functioning without any type of
complexity (Schwalbe 2015). Privacy ensures that controlling of unauthorized access to
organizational resources.
ii) Data: Organizational policy related to security of system for data includes data
content, classification, ownership and security. This type of security eventually compromises
about jeopardizing ability in providing services or loss of revenue through destruction of
confidential data and also reducing reputation and credibility with shareholders and
customers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
INFORMATION TECHNOLOGY
Question 7
Discussion of Security Features of a Server Operating System and Process of their relation
to Protection of Privacy, Ethics and Copyright Information
The main security features of a server operating system with protection process fr
privacy, ethics and copyright information are as follows:
i) Credential Guard: A credential guard mainly relies on virtual secure mode and is
being designed for prevention of user credentials from getting compromised (Holtshouse
2013). Thus, it becomes easy to maintain ethics and copyright information for the
organization.
ii) Device Guard: This type of guard leverages virtual secure model and it includes
UEFI secure boot, VSM protected code integrity or platform and configurable code integrity
for prevention of malware infections. It ensures integrity and privacy by running at kernel
level.
iii) Host Guardian and Shielded Virtual Machines: This particular feature ensures
that virtualization administrator or storage administrator is prevented from copying hard disk
of virtual machine to the removable media. Since, these administrators cannot copy hard disk,
ethics and privacy of data are maintained.
INFORMATION TECHNOLOGY
Question 7
Discussion of Security Features of a Server Operating System and Process of their relation
to Protection of Privacy, Ethics and Copyright Information
The main security features of a server operating system with protection process fr
privacy, ethics and copyright information are as follows:
i) Credential Guard: A credential guard mainly relies on virtual secure mode and is
being designed for prevention of user credentials from getting compromised (Holtshouse
2013). Thus, it becomes easy to maintain ethics and copyright information for the
organization.
ii) Device Guard: This type of guard leverages virtual secure model and it includes
UEFI secure boot, VSM protected code integrity or platform and configurable code integrity
for prevention of malware infections. It ensures integrity and privacy by running at kernel
level.
iii) Host Guardian and Shielded Virtual Machines: This particular feature ensures
that virtualization administrator or storage administrator is prevented from copying hard disk
of virtual machine to the removable media. Since, these administrators cannot copy hard disk,
ethics and privacy of data are maintained.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
INFORMATION TECHNOLOGY
Question 8
Organizational Communication Processes and Procedures needed for Privacy, Copyright
and Ethics
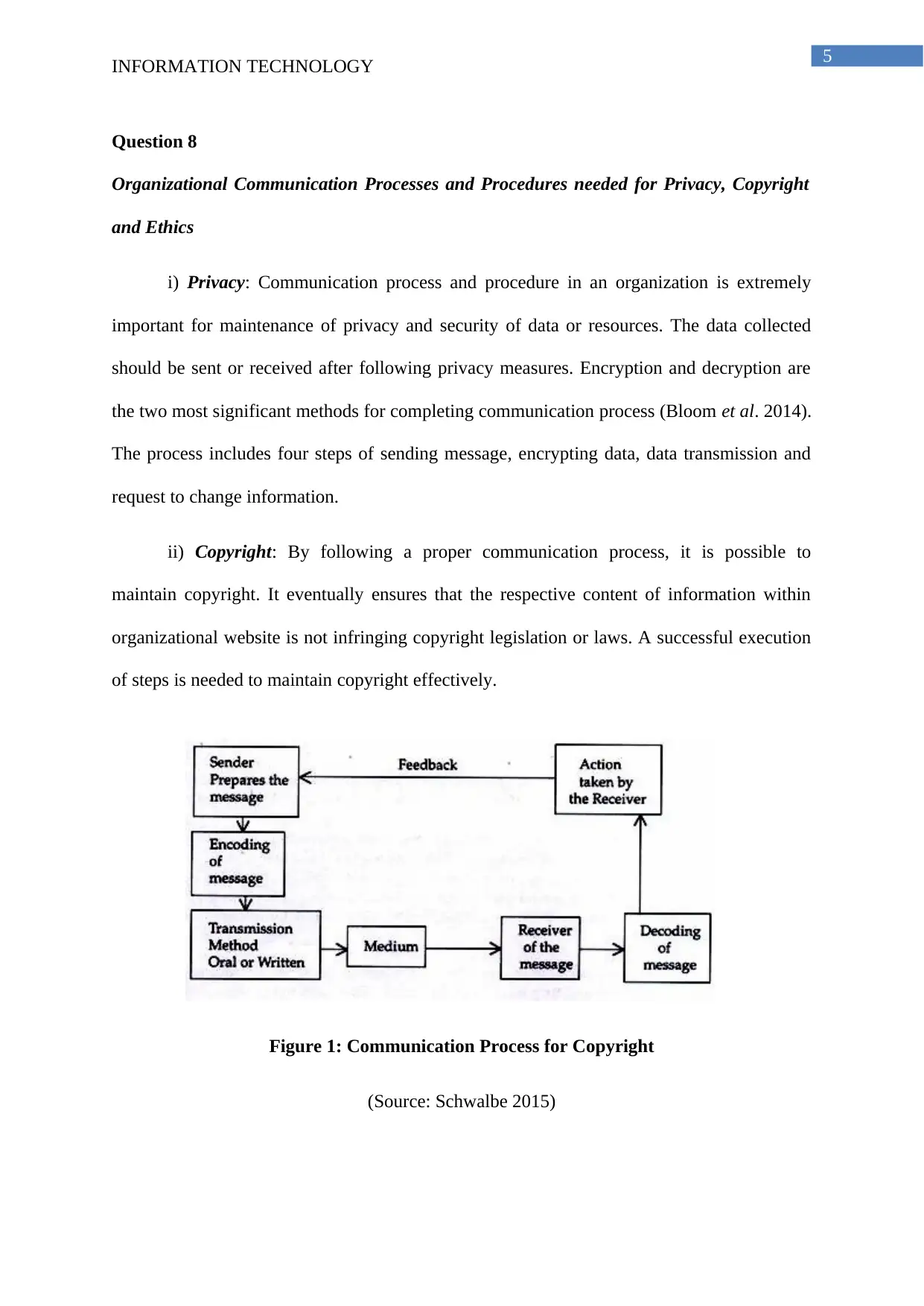
i) Privacy: Communication process and procedure in an organization is extremely
important for maintenance of privacy and security of data or resources. The data collected
should be sent or received after following privacy measures. Encryption and decryption are
the two most significant methods for completing communication process (Bloom et al. 2014).
The process includes four steps of sending message, encrypting data, data transmission and
request to change information.
ii) Copyright: By following a proper communication process, it is possible to
maintain copyright. It eventually ensures that the respective content of information within
organizational website is not infringing copyright legislation or laws. A successful execution
of steps is needed to maintain copyright effectively.
Figure 1: Communication Process for Copyright
(Source: Schwalbe 2015)
INFORMATION TECHNOLOGY
Question 8
Organizational Communication Processes and Procedures needed for Privacy, Copyright
and Ethics
i) Privacy: Communication process and procedure in an organization is extremely
important for maintenance of privacy and security of data or resources. The data collected
should be sent or received after following privacy measures. Encryption and decryption are
the two most significant methods for completing communication process (Bloom et al. 2014).
The process includes four steps of sending message, encrypting data, data transmission and
request to change information.
ii) Copyright: By following a proper communication process, it is possible to
maintain copyright. It eventually ensures that the respective content of information within
organizational website is not infringing copyright legislation or laws. A successful execution
of steps is needed to maintain copyright effectively.
Figure 1: Communication Process for Copyright
(Source: Schwalbe 2015)

6
INFORMATION TECHNOLOGY
iii) Ethics: Ethical framework is required to be maintained to ensure cultural
awareness. Organizational cultural awareness helps to maintain ability to stand back from
issues in data communications and becoming aware of cultural value, perception and belief.
INFORMATION TECHNOLOGY
iii) Ethics: Ethical framework is required to be maintained to ensure cultural
awareness. Organizational cultural awareness helps to maintain ability to stand back from
issues in data communications and becoming aware of cultural value, perception and belief.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
INFORMATION TECHNOLOGY
Question 9
Identification of Five Areas and Explanation for Each Area during communication with
Customers
The five areas that are required to be aware of while communicating with the
customers over phone with relevant details are as follows:
i) Listening Carefully: Listening to problems of the customers is the first area that is
extremely important so that proper solutions could be provided.
ii) Crystal Clear Verbal Communication: There should no misinterpretation between
customer support and customers, hence it is needed to provide crystal clear verbal
communication (Holtshouse 2013).
iii) Ability to use Positive Language: Positive language is important for assuring
customers that IT help desk is understanding their issues and they would be getting proper
assistance.
iv) Knowledge of Organizational Services: The IT help should have knowledge of the
organizational services and products for assisting customers through communication.
v) Time Management Skills: Time management skills are also important for better
communication with customers.
INFORMATION TECHNOLOGY
Question 9
Identification of Five Areas and Explanation for Each Area during communication with
Customers
The five areas that are required to be aware of while communicating with the
customers over phone with relevant details are as follows:
i) Listening Carefully: Listening to problems of the customers is the first area that is
extremely important so that proper solutions could be provided.
ii) Crystal Clear Verbal Communication: There should no misinterpretation between
customer support and customers, hence it is needed to provide crystal clear verbal
communication (Holtshouse 2013).
iii) Ability to use Positive Language: Positive language is important for assuring
customers that IT help desk is understanding their issues and they would be getting proper
assistance.
iv) Knowledge of Organizational Services: The IT help should have knowledge of the
organizational services and products for assisting customers through communication.
v) Time Management Skills: Time management skills are also important for better
communication with customers.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
INFORMATION TECHNOLOGY
Question 10
Explanation of ACS Code of Ethics and its role in ICT Industry
The ACS code of ethics comprises of six codes, which are primacy of public interest,
enhancement of quality of life, honesty, competence, professional development and
professionalism (ACS Code of Ethics. 2019). All of these six codes have significant roles in
the ICT industry as they ensure that the respective organizational member or organization is
ethical and is following every code. It is being applied to every ACS member regardless of
the role and area of expertise within this industry.
INFORMATION TECHNOLOGY
Question 10
Explanation of ACS Code of Ethics and its role in ICT Industry
The ACS code of ethics comprises of six codes, which are primacy of public interest,
enhancement of quality of life, honesty, competence, professional development and
professionalism (ACS Code of Ethics. 2019). All of these six codes have significant roles in
the ICT industry as they ensure that the respective organizational member or organization is
ethical and is following every code. It is being applied to every ACS member regardless of
the role and area of expertise within this industry.

9
INFORMATION TECHNOLOGY
References
ACS Code of Ethics. 2019. [online]. Accessed from
https://www.acs.org.au/content/dam/acs/acs-documents/Code-of-Ethics.pdf [Accessed on 27
May 2019].
Bloom, N., Garicano, L., Sadun, R. and Van Reenen, J., 2014. The distinct effects of
information technology and communication technology on firm organization. Management
Science, 60(12), pp.2859-2885.
Holtshouse, D.K., 2013. Information technology for knowledge management. Springer
Science & Business Media.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
INFORMATION TECHNOLOGY
References
ACS Code of Ethics. 2019. [online]. Accessed from
https://www.acs.org.au/content/dam/acs/acs-documents/Code-of-Ethics.pdf [Accessed on 27
May 2019].
Bloom, N., Garicano, L., Sadun, R. and Van Reenen, J., 2014. The distinct effects of
information technology and communication technology on firm organization. Management
Science, 60(12), pp.2859-2885.
Holtshouse, D.K., 2013. Information technology for knowledge management. Springer
Science & Business Media.
Schwalbe, K., 2015. Information technology project management. Cengage Learning.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





