HND Computing Unit 5: IT Security Report on Risks and Implementation
VerifiedAdded on 2023/02/01
|18
|1181
|61
Report
AI Summary
This report delves into the realm of IT security, focusing on various aspects crucial for organizational protection. It begins by evaluating different types of security risks, including computer viruses, malware, and DOS/DDOS attacks, emphasizing their potential impact. The report then examines organizational security procedures, highlighting their role in safeguarding sensitive information and ensuring consistent implementation of security controls. Furthermore, it explores the potential impact of incorrect firewall configurations and third-party VPNs on IT security. Finally, the report discusses the implementation of DMZ, static IP, and NAT in a network, providing insights into how these technologies enhance security. The report is well-structured, citing relevant references, and providing a comprehensive overview of IT security concepts and their practical applications within a retail business scenario.

IT SECURITY
LO 1 & LO 2
LO 1 & LO 2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
■ INTRODUCTION
■ LO1
■ P1 Evaluating the types of security risks to organization
■ P2 Examining the organizational security procedure
■ LO2
■ P3 Potential impact of IT security with respect to the incorrect configuration of firewall
policies and third party VPN
■ P4 Implementation of DMZ, Static IP and NAT in a network
■ CONCLUSION
■ INTRODUCTION
■ LO1
■ P1 Evaluating the types of security risks to organization
■ P2 Examining the organizational security procedure
■ LO2
■ P3 Potential impact of IT security with respect to the incorrect configuration of firewall
policies and third party VPN
■ P4 Implementation of DMZ, Static IP and NAT in a network
■ CONCLUSION

INTRODUCTION
■ IT security is a set of cyber-security strategies that prevents unauthorised access to
organizational assets which includes computer, network and data.
■ IT security mainly maintains the integrity and confidentiality of sensitive information,
blocking the access to sophisticated hackers.
■ IT security is a set of cyber-security strategies that prevents unauthorised access to
organizational assets which includes computer, network and data.
■ IT security mainly maintains the integrity and confidentiality of sensitive information,
blocking the access to sophisticated hackers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P1 Evaluating the types of security risks to
organization
■ Security risk to the system is generally performed by the unauthorised
users in order to gain access of the confidential data for the purpose of
attempting cyber-attack.
■ This is a illegal practice which is mostly performed by the cyber
criminals with the intention of stealing the private data from the retail
organization in London.
organization
■ Security risk to the system is generally performed by the unauthorised
users in order to gain access of the confidential data for the purpose of
attempting cyber-attack.
■ This is a illegal practice which is mostly performed by the cyber
criminals with the intention of stealing the private data from the retail
organization in London.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
CONTINUE…..
Different types of security risks are as follows:
■ Computer Virus
■ Malware
■ Trojan Horse
■ DOS and DDOS attacks
■ Computer worm
Different types of security risks are as follows:
■ Computer Virus
■ Malware
■ Trojan Horse
■ DOS and DDOS attacks
■ Computer worm

CONTINUE…..
Computer Virus
■ This is a small piece of software which is mainly designed to infect, corrupt, steal or
delete the data from the system. This can be easily spread from one computer system to
another in it uses the computer programs such as emails and messages to attack the
system. Viruses are also known as Spam messages.
Malware
■ It is termed as a Malicious software which can be created through the variety of forms
such as hostile, intrusive or annoying software program codes and software.
Computer Virus
■ This is a small piece of software which is mainly designed to infect, corrupt, steal or
delete the data from the system. This can be easily spread from one computer system to
another in it uses the computer programs such as emails and messages to attack the
system. Viruses are also known as Spam messages.
Malware
■ It is termed as a Malicious software which can be created through the variety of forms
such as hostile, intrusive or annoying software program codes and software.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

CONTINUE…..
DOS and DDOS attacks
■ This is generally arrived in case in which the website server gets overloaded with traffic
and simply crashes at the time when new story breaks out.
■ During the denial-of -Services, a malicious traffic overloaded which occurs at the time
when attacker over flood the website with traffic.
■ So in this situation, a website is unable to serve its content to visitor. This attack is
performed by machine and internet connection when large number of users sends the
multiple requests at the same time. A DDOS (Distributed Denial of services) attack is
more forceful as it is launched from the several computers and involve the range of IP
addresses.
DOS and DDOS attacks
■ This is generally arrived in case in which the website server gets overloaded with traffic
and simply crashes at the time when new story breaks out.
■ During the denial-of -Services, a malicious traffic overloaded which occurs at the time
when attacker over flood the website with traffic.
■ So in this situation, a website is unable to serve its content to visitor. This attack is
performed by machine and internet connection when large number of users sends the
multiple requests at the same time. A DDOS (Distributed Denial of services) attack is
more forceful as it is launched from the several computers and involve the range of IP
addresses.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

P2 Examining the organizational security
procedure
■ The main purpose of the information security is to Provide the
administrative, technical and physical safeguard to the operations and
data generated within the retailing business.
■ This is mainly used to protect the sensitive information from
unauthorised access, disclosure, corruption or destruction.
■ Security procedure is the detailed step-by-step instructions On enforcing
the security control within the organization.
■ This may consists of multitude of hardware and software components
which supports the secured business process.
procedure
■ The main purpose of the information security is to Provide the
administrative, technical and physical safeguard to the operations and
data generated within the retailing business.
■ This is mainly used to protect the sensitive information from
unauthorised access, disclosure, corruption or destruction.
■ Security procedure is the detailed step-by-step instructions On enforcing
the security control within the organization.
■ This may consists of multitude of hardware and software components
which supports the secured business process.

CONTINUE…..
■ In addition to this, The main purpose of the security procedure is to ensure the
consistency in implementation of the security control or execution of the security
relevant business process.
■ According to the scenario, Retail organization in London wants to expand the business
online so there is a huge requirement for the company to follow the security procedure
which meet the restricts the unauthorised access in gaining the control over the private
information of the business.
■ In addition to this, The main purpose of the security procedure is to ensure the
consistency in implementation of the security control or execution of the security
relevant business process.
■ According to the scenario, Retail organization in London wants to expand the business
online so there is a huge requirement for the company to follow the security procedure
which meet the restricts the unauthorised access in gaining the control over the private
information of the business.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

P3 Potential impact of IT security with respect to the
incorrect configuration of firewall policies and third party
VPN
■ A firewall is a system that provides the network security for filtering incoming and
outgoing network traffic based on a set of user-defined rules.
■ The main purpose of the firewall is to reduce or eliminate the occurrence of the
unwanted network communications while allowing all legitimate communications to
flow freely.
■ It is as good as its policies and the security of its VPN connections.
incorrect configuration of firewall policies and third party
VPN
■ A firewall is a system that provides the network security for filtering incoming and
outgoing network traffic based on a set of user-defined rules.
■ The main purpose of the firewall is to reduce or eliminate the occurrence of the
unwanted network communications while allowing all legitimate communications to
flow freely.
■ It is as good as its policies and the security of its VPN connections.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
P4 Implementation of DMZ, Static IP and NAT
in a network
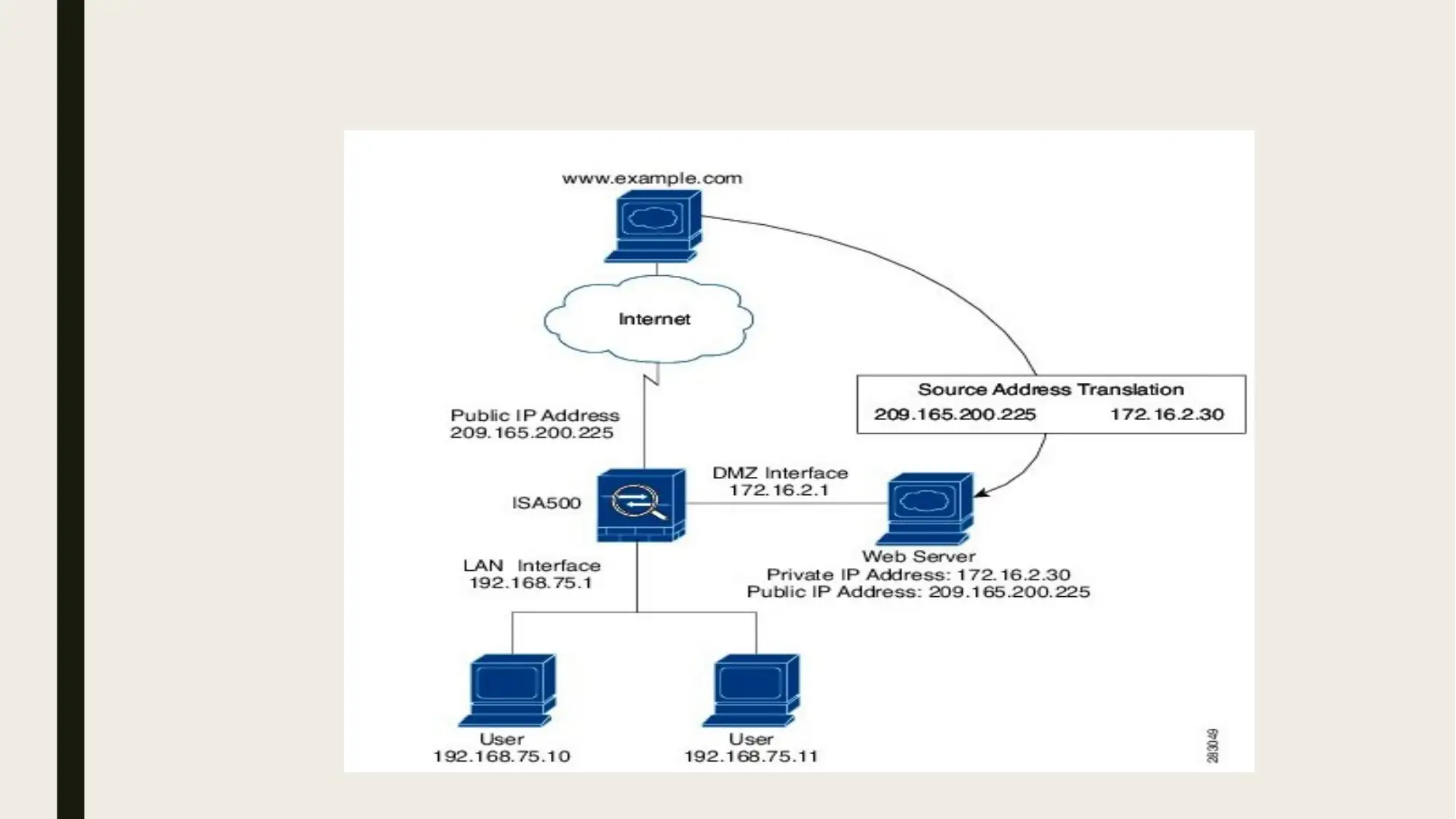
■ DMZ (Demilitarized Zones) are the network equivalent of the neutral ground. They provide
an isolated network segment for public-facing services such as mail servers and web services.
■ The Private net work in secured from such servers as the public accessibility makes them more
vulnerable to compromise. A standard DMZ approach mainly involves the use of Firewall
using three network interfaces.
■ A DMZ is basically a sub-network which is placed behind the firewall but open to the public.
This allows the public to use the services but it cannot penetrate the LAN.
in a network
■ DMZ (Demilitarized Zones) are the network equivalent of the neutral ground. They provide
an isolated network segment for public-facing services such as mail servers and web services.
■ The Private net work in secured from such servers as the public accessibility makes them more
vulnerable to compromise. A standard DMZ approach mainly involves the use of Firewall
using three network interfaces.
■ A DMZ is basically a sub-network which is placed behind the firewall but open to the public.
This allows the public to use the services but it cannot penetrate the LAN.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





