Research Proposal: Addressing IT Security Challenges in Digital Era
VerifiedAdded on 2022/11/13
|15
|3990
|426
Report
AI Summary
This research proposal addresses the significant IT security challenges faced by organizations in the modern digital landscape. It highlights the increasing reliance on data management and the associated vulnerabilities to malicious attacks. The proposal identifies the problem of inadequate IT security as a major concern, leading to data breaches and financial losses. The research aims to explore the impact of collaboration, innovation, and government cooperation on enhancing IT security. The methodology involves surveys and both qualitative and quantitative data analysis. The research expects to yield tangible outputs such as standards, guidelines, and software prototypes, alongside new knowledge about the impact of robust IT security on customer relations and organizational performance. The study will take three months and involve five researchers, focusing on a comprehensive analysis of the IT security landscape to provide practical solutions.

1
Running head: MANAGEMENT
IT security in the market today is the major challenge to organizations in the market today
Name
Institution
Author’s Note
Running head: MANAGEMENT
IT security in the market today is the major challenge to organizations in the market today
Name
Institution
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
MANAGEMENT
Problem statement
In this modern world, quit a number of organizations have decided to put much focus on
digitizing all their data platforms. Appropriate data management acts as one of the most
fundamental parameters within the boundaries of information technology and is known to have
the capability of focusing on the offering of advanced forms of protection against quite a number
of malicious attacks that are likely to emerge from the external sources (Birkinshaw, Bresman &
Håkanson, 2016). Currently, quite a number of organizations have been able to encounter IT
security problems as a major challenge in the market today. This is a problem that has been on
the verge and is known to be increasing over the past years thus causing a serious nightmare to
most of the organizations that are known to be carrying out a vast range of operations across
different platforms. As far as the understanding of this problem is concerned in this current
society, quite a number of essential data across various organizations have been penetrated into
where most of them have also ended being manipulated. This is a scenario that has been able to
emerge as a result of poor implementation of different forma of information security across these
organizations. At the same time, the problem has made quite a number of organizations to
encounter serious losses thereby preventing them from moving forward towards the direction of
their goals and objectives (Guest, 2011). According to statistics, the challenge attached to the IT
security in the market today has been able to emerge as a result of various factors with the major
one being the recruitment of the employees who are not well versed in the area of information
technology. It is therefore necessary to carry out a research into solving this problem because if
the whole issue is not well taken care of, it is likely to rise to greater levels in the coming future
where it will not be easy to solve it. As a result, one of the essential new knowledge that will be
able to emerge is the implementation of quite a number of strategies that will be geared towards
solving the entire situation by eradicating its occurrence as much as possible.
MANAGEMENT
Problem statement
In this modern world, quit a number of organizations have decided to put much focus on
digitizing all their data platforms. Appropriate data management acts as one of the most
fundamental parameters within the boundaries of information technology and is known to have
the capability of focusing on the offering of advanced forms of protection against quite a number
of malicious attacks that are likely to emerge from the external sources (Birkinshaw, Bresman &
Håkanson, 2016). Currently, quite a number of organizations have been able to encounter IT
security problems as a major challenge in the market today. This is a problem that has been on
the verge and is known to be increasing over the past years thus causing a serious nightmare to
most of the organizations that are known to be carrying out a vast range of operations across
different platforms. As far as the understanding of this problem is concerned in this current
society, quite a number of essential data across various organizations have been penetrated into
where most of them have also ended being manipulated. This is a scenario that has been able to
emerge as a result of poor implementation of different forma of information security across these
organizations. At the same time, the problem has made quite a number of organizations to
encounter serious losses thereby preventing them from moving forward towards the direction of
their goals and objectives (Guest, 2011). According to statistics, the challenge attached to the IT
security in the market today has been able to emerge as a result of various factors with the major
one being the recruitment of the employees who are not well versed in the area of information
technology. It is therefore necessary to carry out a research into solving this problem because if
the whole issue is not well taken care of, it is likely to rise to greater levels in the coming future
where it will not be easy to solve it. As a result, one of the essential new knowledge that will be
able to emerge is the implementation of quite a number of strategies that will be geared towards
solving the entire situation by eradicating its occurrence as much as possible.

3
MANAGEMENT
Research questions
There are quite a number of research questions where the entire study will be capable of putting
much focus on. The following are among the major types of research questions;
(1) To what extent do you think that the collaboration among various organizations when it
comes to addressing of IT security challenges will be able to enhance issues associated
with cyber security?
(2) In what ways will innovation play an essential role when it comes to supporting the entire
IT security?
Answering the research question is likely to contribute towards solving the research
problem through the provision of adequate and reliable information that can be used in the
analysis of the entire situation (Guest, 2011). Moreover, by answering the research question,
it will make it much possible to carry out an analysis of quite a number of variables thereby
making sure that the entire research problem is appropriately solved. This is a question that
has not been answered before since quite a number of organizations have still been able to
raise a lot of complaints in relation to the problems that they have been facing within the
boundaries of information technology security.
MANAGEMENT
Research questions
There are quite a number of research questions where the entire study will be capable of putting
much focus on. The following are among the major types of research questions;
(1) To what extent do you think that the collaboration among various organizations when it
comes to addressing of IT security challenges will be able to enhance issues associated
with cyber security?
(2) In what ways will innovation play an essential role when it comes to supporting the entire
IT security?
Answering the research question is likely to contribute towards solving the research
problem through the provision of adequate and reliable information that can be used in the
analysis of the entire situation (Guest, 2011). Moreover, by answering the research question,
it will make it much possible to carry out an analysis of quite a number of variables thereby
making sure that the entire research problem is appropriately solved. This is a question that
has not been answered before since quite a number of organizations have still been able to
raise a lot of complaints in relation to the problems that they have been facing within the
boundaries of information technology security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4
MANAGEMENT
Research methodology
Taking good care of research methodology is one condition that is likely to determine the
final outcome associated with a given research. Tis research will therefore make sure that quite a
number of data collection methods are put into consideration thus coming up with one of the
most relevant results so far (Hofacker & Belanche, 2016). As a result of this, the overall strategy
for answering all the research questions will fully depend of the use of surveys across different
regions in order to obtain a vast range of information that will be more appropriate in the future
analysis of the entire situation. A good number of information technology research that have
been carried out over the past three years have been able to explore the use of surveys thus
providing them with one of the most appropriate chances to carry out an exploration of quite a
number of issues associated with their research questions thus making sure that they stay relevant
as much as possible (Birdi et al ., 2016).
There are quite a number of individual steps that will be fully involved to undertake the
entire research and as a result of this; the steps will be carried out with a lot of care without
making any assumptions at all. This is to make sure that accuracy is guaranteed throughout the
entire research process by eradicating any confusion related situations as much as possible. Some
of the major steps that will be fully involved in undertaking the whole research mainly include
the following;
Problem identification- This step will involve a full identification of the problem in order
to make the whole research to be clear as much as possible. Once the problem is
identified at this stage, it will be much easier to undertake the remaining parts of the
research project.
MANAGEMENT
Research methodology
Taking good care of research methodology is one condition that is likely to determine the
final outcome associated with a given research. Tis research will therefore make sure that quite a
number of data collection methods are put into consideration thus coming up with one of the
most relevant results so far (Hofacker & Belanche, 2016). As a result of this, the overall strategy
for answering all the research questions will fully depend of the use of surveys across different
regions in order to obtain a vast range of information that will be more appropriate in the future
analysis of the entire situation. A good number of information technology research that have
been carried out over the past three years have been able to explore the use of surveys thus
providing them with one of the most appropriate chances to carry out an exploration of quite a
number of issues associated with their research questions thus making sure that they stay relevant
as much as possible (Birdi et al ., 2016).
There are quite a number of individual steps that will be fully involved to undertake the
entire research and as a result of this; the steps will be carried out with a lot of care without
making any assumptions at all. This is to make sure that accuracy is guaranteed throughout the
entire research process by eradicating any confusion related situations as much as possible. Some
of the major steps that will be fully involved in undertaking the whole research mainly include
the following;
Problem identification- This step will involve a full identification of the problem in order
to make the whole research to be clear as much as possible. Once the problem is
identified at this stage, it will be much easier to undertake the remaining parts of the
research project.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

5
MANAGEMENT
Review of the literature- This will be the second step that will be implemented to
undertake the research problem. After the identification of the problem, the researcher
will be able to learn much about the whole topic that will be under investigation thereby
providing him with a foundational knowledge that is strongly related to the whole
problem (Hofacker & Belanche, 2016). Moreover, the review of literature as a second
step will also be able to educate the researcher regarding the type of studies that have
always been conducted over the past together with how these studies were conducted and
all the conclusions that they were able to come up with.
Clarification of the problem- This that will be used to undertake the research will fully
involve he clarification of the entire research problem that will be majorly carried out by
the researcher thus trying as much as possible to make sure that the entire scope of study
is also narrowed down. This step will only be carried out right after the literature has
been reviewed. All the knowledge that will be obtained from the entire literature review
will be able to offer an appropriate guidance to the researcher during the clarification
process and narrowing of the research project.
Data collection- This is one of the most fundamental steps that will require much
attention. Right after the completion of the instrumental plan, the next step that will be
taken into consideration by the study is data collection. This is a critical step that will be
used in the provision of information that is required in order to give a relent answer to the
entire research question.
Data analysis- This is the final individual step that will be involved in the undertaking of
the research project (Hudson, Huang, Roth & Madden, 2016). At this step, the researcher
shall have obtained an appropriate and reliable set of data that will be used for analysis so
MANAGEMENT
Review of the literature- This will be the second step that will be implemented to
undertake the research problem. After the identification of the problem, the researcher
will be able to learn much about the whole topic that will be under investigation thereby
providing him with a foundational knowledge that is strongly related to the whole
problem (Hofacker & Belanche, 2016). Moreover, the review of literature as a second
step will also be able to educate the researcher regarding the type of studies that have
always been conducted over the past together with how these studies were conducted and
all the conclusions that they were able to come up with.
Clarification of the problem- This that will be used to undertake the research will fully
involve he clarification of the entire research problem that will be majorly carried out by
the researcher thus trying as much as possible to make sure that the entire scope of study
is also narrowed down. This step will only be carried out right after the literature has
been reviewed. All the knowledge that will be obtained from the entire literature review
will be able to offer an appropriate guidance to the researcher during the clarification
process and narrowing of the research project.
Data collection- This is one of the most fundamental steps that will require much
attention. Right after the completion of the instrumental plan, the next step that will be
taken into consideration by the study is data collection. This is a critical step that will be
used in the provision of information that is required in order to give a relent answer to the
entire research question.
Data analysis- This is the final individual step that will be involved in the undertaking of
the research project (Hudson, Huang, Roth & Madden, 2016). At this step, the researcher
shall have obtained an appropriate and reliable set of data that will be used for analysis so

6
MANAGEMENT
that the research question can be answered to its maximum level. Moreover, the
researcher will be able to appropriately analyze the data according to the plan that was
created at the initial step.
Analysis applied to the raw data collected
The analysis that will be applied to the entire collected raw data will mainly involve will majorly
involve the use of both the qualitative and quantitative analysis to make sure that an appropriate
outcome is met. The qualitative method of analysis will majorly involve the use of scientific
methods of observation in order to gather different types of non-numerical data. One of the major
reasons as to why this mode of analysis will be put into consideration is simply because most of
the data that is obtained from qualitative analysis is based on human experience and different
types of observations. On the other hand, quantitative research that will be used will majorly
focus on the objective measurements together with the statistical analysis of the entire collected
data.
Estimation of the required resources
Various types of resources will be required in order to make sure that the whole research
emerges as a success. As a result of this, the entire research will be expected to take an
approximated time frame of about 3 months in order to allow a humble time for the analysis
stage to be appropriately implemented in relation to the types of data that shall have been
acquired. On the other hand, a total of five different researchers would be required in the entire
process. One of the major equipment that will be needed will be a computer that will be majorly
used to store data and carry out advanced forms of analysis.
MANAGEMENT
that the research question can be answered to its maximum level. Moreover, the
researcher will be able to appropriately analyze the data according to the plan that was
created at the initial step.
Analysis applied to the raw data collected
The analysis that will be applied to the entire collected raw data will mainly involve will majorly
involve the use of both the qualitative and quantitative analysis to make sure that an appropriate
outcome is met. The qualitative method of analysis will majorly involve the use of scientific
methods of observation in order to gather different types of non-numerical data. One of the major
reasons as to why this mode of analysis will be put into consideration is simply because most of
the data that is obtained from qualitative analysis is based on human experience and different
types of observations. On the other hand, quantitative research that will be used will majorly
focus on the objective measurements together with the statistical analysis of the entire collected
data.
Estimation of the required resources
Various types of resources will be required in order to make sure that the whole research
emerges as a success. As a result of this, the entire research will be expected to take an
approximated time frame of about 3 months in order to allow a humble time for the analysis
stage to be appropriately implemented in relation to the types of data that shall have been
acquired. On the other hand, a total of five different researchers would be required in the entire
process. One of the major equipment that will be needed will be a computer that will be majorly
used to store data and carry out advanced forms of analysis.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
MANAGEMENT
The expected tangible outputs
There are quite a number of expected tangible outputs that are expected to emerge from the
entire research. All these tangible outputs are likely to determine the nature of the whole research
in the coming future in relation to its goals and objectives. One of the major outputs is the
standards and guidelines. This is a type of output that fully entails defining new ways of doing
things thus making sure that appropriate activities are well implemented under various conditions
(Birkinshaw, Bresman & Håkanson, 2016). Moreover, one of the major forms of this type of
derivable will be the written reports that will be obtained from various personalities and
organizations. Following the research methodology is capable of producing this output by
making sure that each and every step together with information is well taken into account. Other
expected tangible outputs will be the software prototypes that will be majorly produced with an
intention of allowing the capabilities of a particular proposed design to be well evaluated under
different conditions. The use of software will be one of the major forms attached to this kind of
derivable. Following the research methodology by appropriately analyzing the required data is
one of the major techniques that will make sure that this type of output is produced without
encountering any further complications (Hofacker et al., 2016).
The new knowledge
According to what is entailed in the entire research process, there is a high probability
that new knowledge is likely to emerge from the entire situation thereby coming up with quite a
number of benefits that will be felt across different sectors (Guest, 2011). One of the major
knowledge that is likely to be brought on board by the research is that is that the appropriate
MANAGEMENT
The expected tangible outputs
There are quite a number of expected tangible outputs that are expected to emerge from the
entire research. All these tangible outputs are likely to determine the nature of the whole research
in the coming future in relation to its goals and objectives. One of the major outputs is the
standards and guidelines. This is a type of output that fully entails defining new ways of doing
things thus making sure that appropriate activities are well implemented under various conditions
(Birkinshaw, Bresman & Håkanson, 2016). Moreover, one of the major forms of this type of
derivable will be the written reports that will be obtained from various personalities and
organizations. Following the research methodology is capable of producing this output by
making sure that each and every step together with information is well taken into account. Other
expected tangible outputs will be the software prototypes that will be majorly produced with an
intention of allowing the capabilities of a particular proposed design to be well evaluated under
different conditions. The use of software will be one of the major forms attached to this kind of
derivable. Following the research methodology by appropriately analyzing the required data is
one of the major techniques that will make sure that this type of output is produced without
encountering any further complications (Hofacker et al., 2016).
The new knowledge
According to what is entailed in the entire research process, there is a high probability
that new knowledge is likely to emerge from the entire situation thereby coming up with quite a
number of benefits that will be felt across different sectors (Guest, 2011). One of the major
knowledge that is likely to be brought on board by the research is that is that the appropriate
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
MANAGEMENT
management of information security within an organization is capable of changing the
perspectives of quite a number of customers thus making them to be strongly attached to the
organization. This is simply because the shall have developed a perspective that handling of IT
security in a more advanced way will make sure that each and every essential data that is
associated with both the customer segments together with the organization will be well protected
from any external sources (Huang, Backman, Backman & Chang, 2016). Following the research
methodology by carrying out an appropriate data collection is likely to lead to the emergence of
this new knowledge across different organizations (Ferris & Judge, 2016).
On the other hand, another form of new knowledge is that when information security in
organizations is not given the first priority in organizations, then there is a high probability that it
will negatively impact on the performance of these organizations thus making them to encounter
quite a number of difficulties within different types of market platforms. By coming up with an
appropriate definition of the entire problem in relation to the research methodology is an
essential issue that will contribute towards the emergence of this kind of knowledge (Godey et
al., 2016)..
The above knowledge is likely to be useful in quite a number of situations since they are
capable of creating awareness of what is likely to occur in the coming future thus providing
different organizations and individuals to be able to come up with different types of conclusions
and recommendations pertaining how best they can be able to handle the entire situation.
Reflective statement
My engagement with the entire research involved a series of events that I was able to
encounter almost on a daily basis. In relation to all the weekly tasks that I was able to come
MANAGEMENT
management of information security within an organization is capable of changing the
perspectives of quite a number of customers thus making them to be strongly attached to the
organization. This is simply because the shall have developed a perspective that handling of IT
security in a more advanced way will make sure that each and every essential data that is
associated with both the customer segments together with the organization will be well protected
from any external sources (Huang, Backman, Backman & Chang, 2016). Following the research
methodology by carrying out an appropriate data collection is likely to lead to the emergence of
this new knowledge across different organizations (Ferris & Judge, 2016).
On the other hand, another form of new knowledge is that when information security in
organizations is not given the first priority in organizations, then there is a high probability that it
will negatively impact on the performance of these organizations thus making them to encounter
quite a number of difficulties within different types of market platforms. By coming up with an
appropriate definition of the entire problem in relation to the research methodology is an
essential issue that will contribute towards the emergence of this kind of knowledge (Godey et
al., 2016)..
The above knowledge is likely to be useful in quite a number of situations since they are
capable of creating awareness of what is likely to occur in the coming future thus providing
different organizations and individuals to be able to come up with different types of conclusions
and recommendations pertaining how best they can be able to handle the entire situation.
Reflective statement
My engagement with the entire research involved a series of events that I was able to
encounter almost on a daily basis. In relation to all the weekly tasks that I was able to come

9
MANAGEMENT
across, I was able to engage in them by providing them with the first priority to make sure that
all the tasks were solved according to the rules and regulations thus bringing one of the most
advanced outcomes so far. On the other hand, my engagement in the reflection of the research
process involved carrying out a deep analysis of the entire situation and also carrying out a
comparison between quite a numbers of conditions in order to come up with the correct results
that will be more in relation to the research. At the same time, discussing my work within my
tutorial group was one of the best experiences so far that I was able to attain. This is simply
because it provided me with one of the best opportunities to obtain new ideas that I had never
known before and also it let to the sharing of quite a number of ideas among the group members.
Moreover, discussing the work with my tutorial group provided a perfect opportunity to highlight
some of the mistakes that existed within the work thus making sure that it relevant as much as
possible.
I was able to come across quite a number of key processes where there were the one that
appeared quite interesting there are those that appeared to be challenging at some point. One of
the major key processes that appeared to be interesting is the identification of the problem. Since
I was much worried with the effects that quite a number of problems related to information
technology have been able to bring across different organizations, it was quite interesting to
identify these problems and be able to point out some of the major reasons that were able to
contribute towards their emergence. Moreover, another key process that I found to be quite
interesting is the review of the entire literature that made me to interact with quite a number of
sources and be able to highlight some of the issues that have been taking place across different
sectors. This key process was very interesting to such an extent that it enabled me to expand my
technical knowhow in relation to different issues attached to the topic of study. At the same time,
MANAGEMENT
across, I was able to engage in them by providing them with the first priority to make sure that
all the tasks were solved according to the rules and regulations thus bringing one of the most
advanced outcomes so far. On the other hand, my engagement in the reflection of the research
process involved carrying out a deep analysis of the entire situation and also carrying out a
comparison between quite a numbers of conditions in order to come up with the correct results
that will be more in relation to the research. At the same time, discussing my work within my
tutorial group was one of the best experiences so far that I was able to attain. This is simply
because it provided me with one of the best opportunities to obtain new ideas that I had never
known before and also it let to the sharing of quite a number of ideas among the group members.
Moreover, discussing the work with my tutorial group provided a perfect opportunity to highlight
some of the mistakes that existed within the work thus making sure that it relevant as much as
possible.
I was able to come across quite a number of key processes where there were the one that
appeared quite interesting there are those that appeared to be challenging at some point. One of
the major key processes that appeared to be interesting is the identification of the problem. Since
I was much worried with the effects that quite a number of problems related to information
technology have been able to bring across different organizations, it was quite interesting to
identify these problems and be able to point out some of the major reasons that were able to
contribute towards their emergence. Moreover, another key process that I found to be quite
interesting is the review of the entire literature that made me to interact with quite a number of
sources and be able to highlight some of the issues that have been taking place across different
sectors. This key process was very interesting to such an extent that it enabled me to expand my
technical knowhow in relation to different issues attached to the topic of study. At the same time,
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
MANAGEMENT
one of the major processes that I found to be quite challenging is data collection. There were
quite a number of barriers in terms of collecting the right data that would further be used in the
analysis stage.
One of the major decisions that I made in terms of leading up to this assignment is to stay
focused by making the entire research to remain relevant as much as possible in order to come up
with a more reliable results. I was able to overcome each and every obstacle by making sure that
all forms of ethical considerations were implemented to the maximum level. When it comes of
the approaching of similar tasks in the coming future, I will make sure that the implementation of
problem definition and clarification remains the same. At the same time, the only change that I
will put into consideration is the use of different data collection techniques thus providing me
with an opportunity to be diverse.
MANAGEMENT
one of the major processes that I found to be quite challenging is data collection. There were
quite a number of barriers in terms of collecting the right data that would further be used in the
analysis stage.
One of the major decisions that I made in terms of leading up to this assignment is to stay
focused by making the entire research to remain relevant as much as possible in order to come up
with a more reliable results. I was able to overcome each and every obstacle by making sure that
all forms of ethical considerations were implemented to the maximum level. When it comes of
the approaching of similar tasks in the coming future, I will make sure that the implementation of
problem definition and clarification remains the same. At the same time, the only change that I
will put into consideration is the use of different data collection techniques thus providing me
with an opportunity to be diverse.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
MANAGEMENT
Technical part
How the problems of IT security has been able to affect organizations in the last
three years
Year 1 year 2 year 3
0%
10%
20%
30%
40%
50%
60%
70%
80%
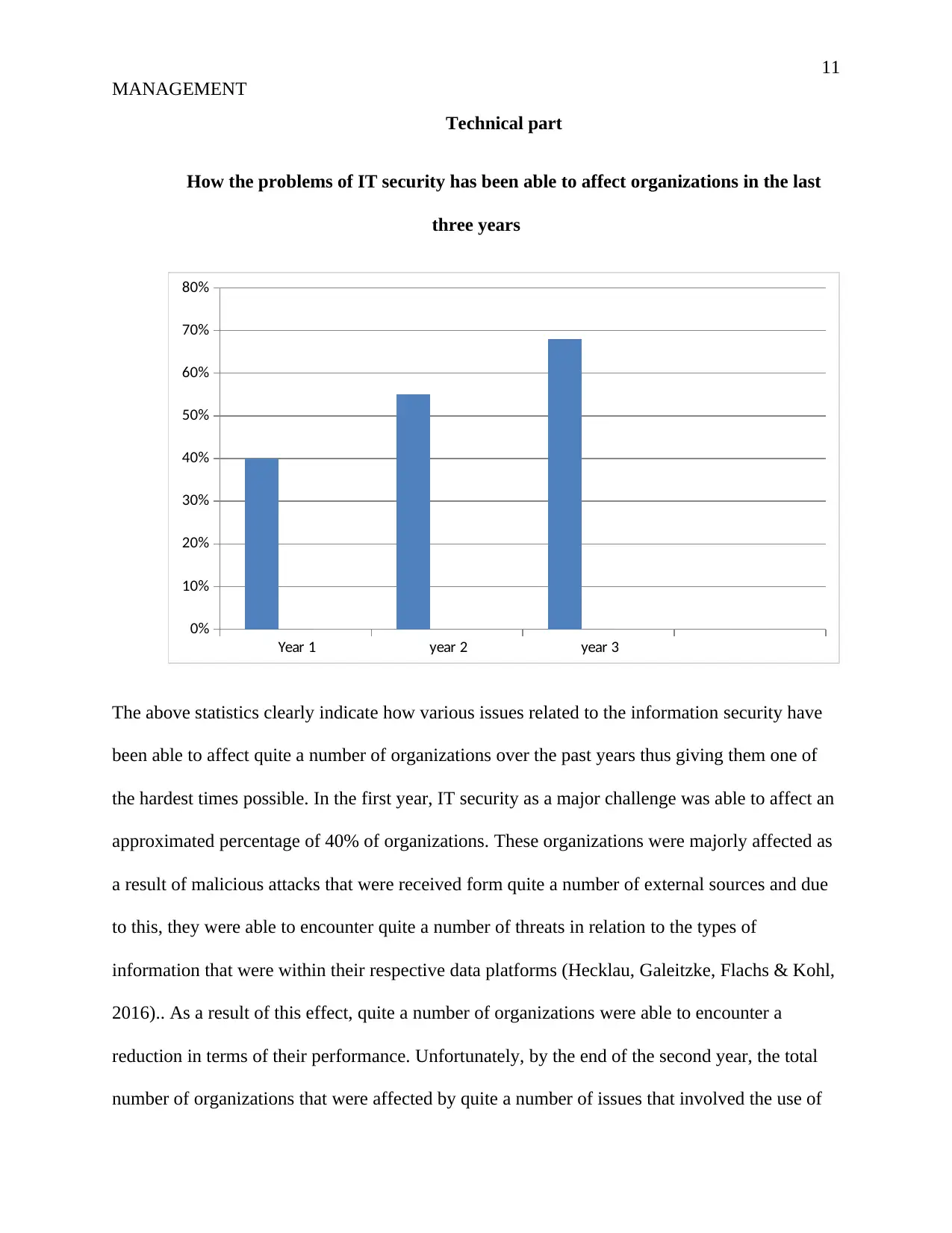
The above statistics clearly indicate how various issues related to the information security have
been able to affect quite a number of organizations over the past years thus giving them one of
the hardest times possible. In the first year, IT security as a major challenge was able to affect an
approximated percentage of 40% of organizations. These organizations were majorly affected as
a result of malicious attacks that were received form quite a number of external sources and due
to this, they were able to encounter quite a number of threats in relation to the types of
information that were within their respective data platforms (Hecklau, Galeitzke, Flachs & Kohl,
2016).. As a result of this effect, quite a number of organizations were able to encounter a
reduction in terms of their performance. Unfortunately, by the end of the second year, the total
number of organizations that were affected by quite a number of issues that involved the use of
MANAGEMENT
Technical part
How the problems of IT security has been able to affect organizations in the last
three years
Year 1 year 2 year 3
0%
10%
20%
30%
40%
50%
60%
70%
80%
The above statistics clearly indicate how various issues related to the information security have
been able to affect quite a number of organizations over the past years thus giving them one of
the hardest times possible. In the first year, IT security as a major challenge was able to affect an
approximated percentage of 40% of organizations. These organizations were majorly affected as
a result of malicious attacks that were received form quite a number of external sources and due
to this, they were able to encounter quite a number of threats in relation to the types of
information that were within their respective data platforms (Hecklau, Galeitzke, Flachs & Kohl,
2016).. As a result of this effect, quite a number of organizations were able to encounter a
reduction in terms of their performance. Unfortunately, by the end of the second year, the total
number of organizations that were affected by quite a number of issues that involved the use of

12
MANAGEMENT
information security moved to greater heights. The issue started to trigger different types of
questions that were raised by various organizations together with several other IT experts. At this
level, a lot of personal data that belonged to various organizations were penetrated into and the
data were really manipulated thus making all the organizations to encounter serious losses that
gave them one of the hardest times possible to work hard towards their dream lines. As a result
of this, most of the technical management teams decided to call serious meetings where they
could be able to share quite a number of brilliant ideas that they could best put into practice in
order to eradicate the occurrence of such ideas. Since appropriate and reliable measures had not
been taken into account by the end of the third year, the negative effect of the issue was able to
move higher to an approximated percentage of 68%. At this point, nearly all organizations were
affected across all boarders including the ones that were present at the local, national together
with the international level (Chuang & Liao, 2010). It was a reality check that made different
personalities to realize the importance of investing much in IT security thus preventing the
occurrence of quite a number of malicious actions that are targeted towards causing a lot of
destructions to different types of information that are fully attached to various organizations.
This is when different experts were able to develop the need of putting much focus into quite a
number of information security technologies through the utilization of quite a number of ideas
that were capable of coming up with one of the best outcomes so far. From the information
obtained from the above statistical data, it is now clear that this is an issue that was able to
emerge over the past and is known to have affected quite a number of organizations thereby
leading to serious complaints among various personalities. All the data that will be gathered
through the use of this research proposal will be used to carry out an analysis of the entire
situation in order to make sure that reasonable results are well obtained thereby contributing
MANAGEMENT
information security moved to greater heights. The issue started to trigger different types of
questions that were raised by various organizations together with several other IT experts. At this
level, a lot of personal data that belonged to various organizations were penetrated into and the
data were really manipulated thus making all the organizations to encounter serious losses that
gave them one of the hardest times possible to work hard towards their dream lines. As a result
of this, most of the technical management teams decided to call serious meetings where they
could be able to share quite a number of brilliant ideas that they could best put into practice in
order to eradicate the occurrence of such ideas. Since appropriate and reliable measures had not
been taken into account by the end of the third year, the negative effect of the issue was able to
move higher to an approximated percentage of 68%. At this point, nearly all organizations were
affected across all boarders including the ones that were present at the local, national together
with the international level (Chuang & Liao, 2010). It was a reality check that made different
personalities to realize the importance of investing much in IT security thus preventing the
occurrence of quite a number of malicious actions that are targeted towards causing a lot of
destructions to different types of information that are fully attached to various organizations.
This is when different experts were able to develop the need of putting much focus into quite a
number of information security technologies through the utilization of quite a number of ideas
that were capable of coming up with one of the best outcomes so far. From the information
obtained from the above statistical data, it is now clear that this is an issue that was able to
emerge over the past and is known to have affected quite a number of organizations thereby
leading to serious complaints among various personalities. All the data that will be gathered
through the use of this research proposal will be used to carry out an analysis of the entire
situation in order to make sure that reasonable results are well obtained thereby contributing
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





