IT Risk Management Report: IT Security, Models, and Threats
VerifiedAdded on 2020/03/04
|10
|1547
|47
Report
AI Summary
This report provides an extensive overview of IT risk management, focusing on data and information security within organizations. It explores the IT security landscape, models, and access controls, including the Role-Based Access Control (RBAC) model, and conducts a thorough IT security threat and risk assessment. The report identifies various risks, categorizing them into human and non-human threats, and discusses the importance of risk assessment policies, firewalls, and anti-virus software in mitigating cyber-attacks and protecting data. It emphasizes the need for continuous improvement in IT security to safeguard against data breaches and ensure the success of the company in the market. The report concludes that IT security plays a pivotal role in organizational success, highlighting the significance of proactive risk management strategies and the use of various models and theories in the risk assessment process.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author’s Note
IT Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.

2
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
IT security and technology landscape..............................................................................................3
IT security models and access controls...........................................................................................4
IT security threat and risk assessment.............................................................................................6
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................3
IT security and technology landscape..............................................................................................3
IT security models and access controls...........................................................................................4
IT security threat and risk assessment.............................................................................................6
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Introduction
The protection of data and information in the business organization is an integral part for
the development of the organization in the market. The privacy of the data has shown many
consequences in the organization.
This report deals with various risks and security threats of the data and information in the
organization. This report refers to three topics including IT security landscape, IT security
models and controls and IT threat and risk assessment.
This report outlines three topics in the IT risk management that helps in maintaining the
privacy of the data and information. There are different techniques discussed in the report for
managing the risks in the business organization.
IT security and technology landscape
The IT management in the organization have continuously enhancing the quality of the
products and services in the market. The data and information in the company are maintained in
the database of the company that helps in the progress of the company (Herath & Herath, 2014).
The use of the IoT has helped in maintaining the privacy of the data and information in the
company. The companies prefer to have a cyber-insurance of their data and information that has
helped in recovering the data in case of data loss. The security protocols involved in the
databases server of the company are helping in maintaining the privacy of the company. On the
other hand, Rieke et al., (2012) argued that the loss of the data and information cannot be
recovered totally as there is a huge data breach during the cyber-attacks. Therefore, the IT risk
assessment has been focusing on the reducing the threats of the cyber-attacks in the company.
IT RISK MANAGEMENT
Introduction
The protection of data and information in the business organization is an integral part for
the development of the organization in the market. The privacy of the data has shown many
consequences in the organization.
This report deals with various risks and security threats of the data and information in the
organization. This report refers to three topics including IT security landscape, IT security
models and controls and IT threat and risk assessment.
This report outlines three topics in the IT risk management that helps in maintaining the
privacy of the data and information. There are different techniques discussed in the report for
managing the risks in the business organization.
IT security and technology landscape
The IT management in the organization have continuously enhancing the quality of the
products and services in the market. The data and information in the company are maintained in
the database of the company that helps in the progress of the company (Herath & Herath, 2014).
The use of the IoT has helped in maintaining the privacy of the data and information in the
company. The companies prefer to have a cyber-insurance of their data and information that has
helped in recovering the data in case of data loss. The security protocols involved in the
databases server of the company are helping in maintaining the privacy of the company. On the
other hand, Rieke et al., (2012) argued that the loss of the data and information cannot be
recovered totally as there is a huge data breach during the cyber-attacks. Therefore, the IT risk
assessment has been focusing on the reducing the threats of the cyber-attacks in the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
The IT risk management has also been focusing in the process of retrieving the lost data and
information in the company.
IT security models and access controls
Different types of access control models of the IT has been mentioned below:
Role Based Access control
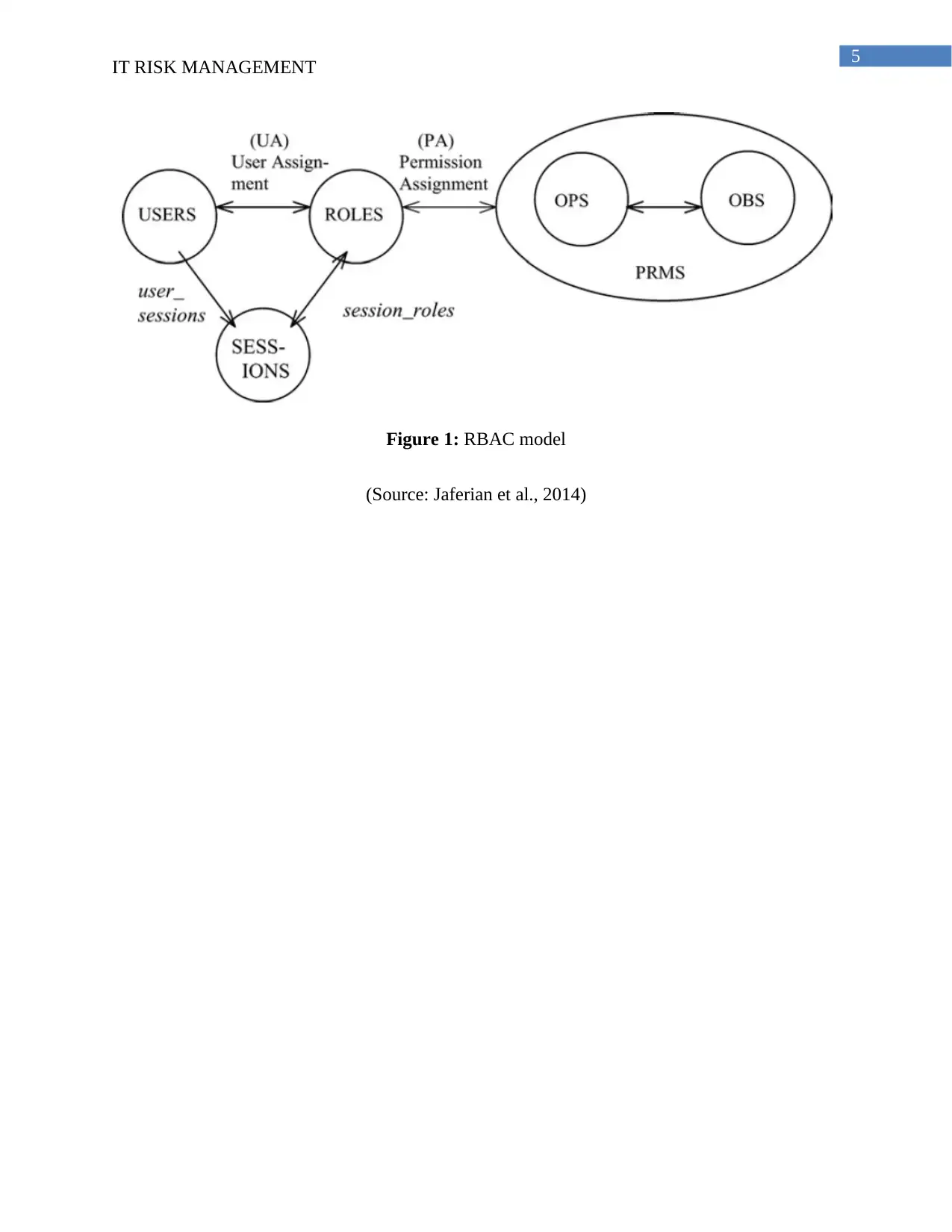
The Role based access control (RBAC) model contains all the roles for permitting
different types of tasks to the users in the organization. This model was developed for
maintaining the administration of the company and handle the administrative challenges of the
organization (Jaferian et al., 2014). There are various types of discussion roles are played in the
DAC model that help in proper decision-making process of the company. This hierarchical
model helps in reviewing each step in the decision-making process. The IT risks are properly
analyzed in the RBAC model that helps in minimizing the cyber-attacks in the company
(Kimwele, 2014). On the other hand, Rieke et al., (2012) argued that this model is unable to
control the cyber-attacks as the model has no updating in the recent world. Therefore, various
types’ viruses and malwares present in the server. This model has also recurring the process of
securing the server of the data and information. The hierarchical order has put forward an
opportunity for enriching the performance of model in market.
IT RISK MANAGEMENT
The IT risk management has also been focusing in the process of retrieving the lost data and
information in the company.
IT security models and access controls
Different types of access control models of the IT has been mentioned below:
Role Based Access control
The Role based access control (RBAC) model contains all the roles for permitting
different types of tasks to the users in the organization. This model was developed for
maintaining the administration of the company and handle the administrative challenges of the
organization (Jaferian et al., 2014). There are various types of discussion roles are played in the
DAC model that help in proper decision-making process of the company. This hierarchical
model helps in reviewing each step in the decision-making process. The IT risks are properly
analyzed in the RBAC model that helps in minimizing the cyber-attacks in the company
(Kimwele, 2014). On the other hand, Rieke et al., (2012) argued that this model is unable to
control the cyber-attacks as the model has no updating in the recent world. Therefore, various
types’ viruses and malwares present in the server. This model has also recurring the process of
securing the server of the data and information. The hierarchical order has put forward an
opportunity for enriching the performance of model in market.
5
IT RISK MANAGEMENT
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
IT RISK MANAGEMENT
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT RISK MANAGEMENT
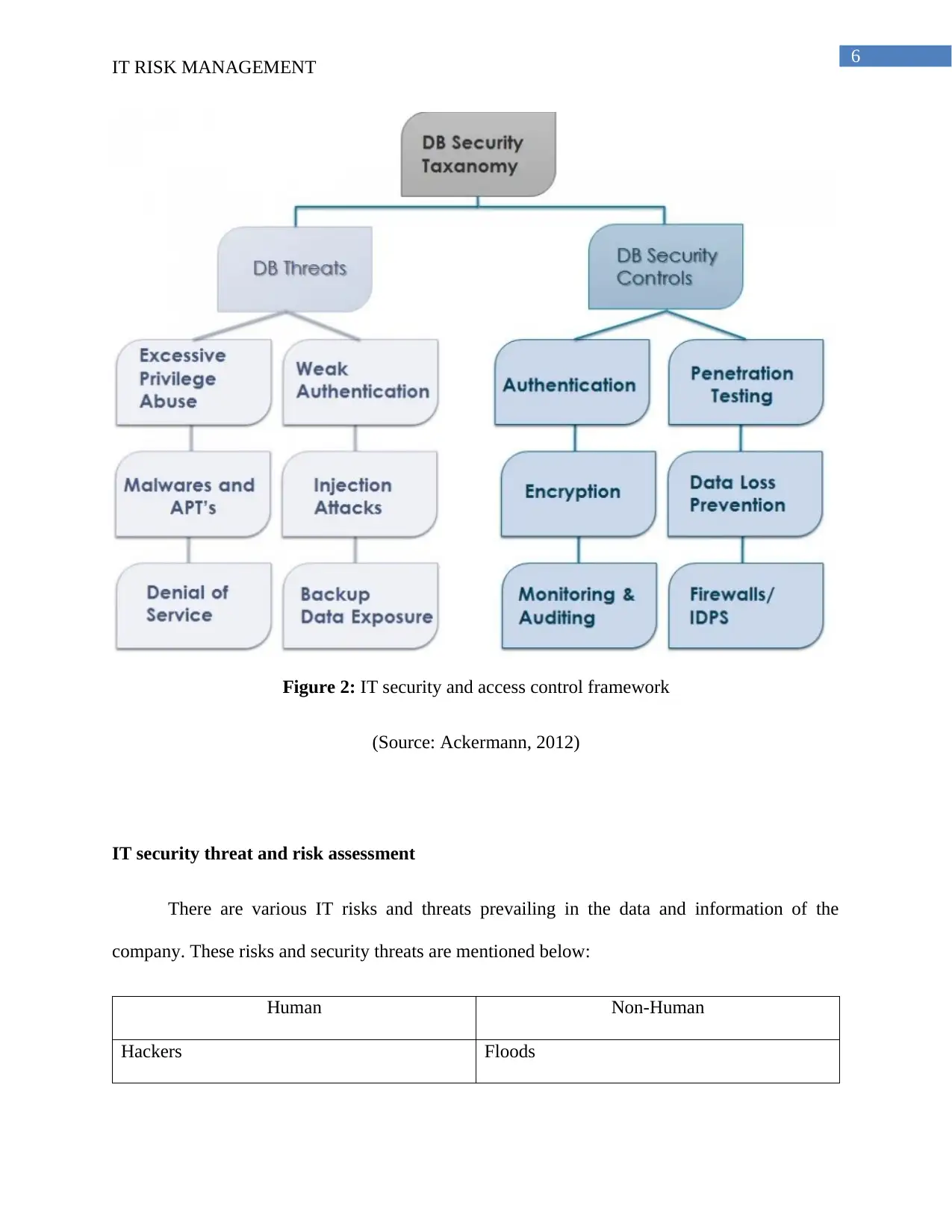
Figure 2: IT security and access control framework
(Source: Ackermann, 2012)
IT security threat and risk assessment
There are various IT risks and threats prevailing in the data and information of the
company. These risks and security threats are mentioned below:
Human Non-Human
Hackers Floods
IT RISK MANAGEMENT
Figure 2: IT security and access control framework
(Source: Ackermann, 2012)
IT security threat and risk assessment
There are various IT risks and threats prevailing in the data and information of the
company. These risks and security threats are mentioned below:
Human Non-Human
Hackers Floods
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
These risks are arising in the normal conditions in the organization. Therefore, these risks
are properly maintained in the companies for protecting their data and information (Angst et al.,
2017). The risk assessment policies are developed in the organization for analyzing these risks in
the company and find a proper solution for them (Vacca, 2012). Therefore, the risk assessment
process helps in identification of the risks and developing strategies for mitigating it. There are
three levels in the risks including high-level, medium-level and low-level (Bojanc, & Jerman-
Blažič, 2013). These categorization of risks helps in identification of the strategies for
minimizing the risks and security threats in the organization. The vulnerability of security threats
helps in maintaining a proper risk assessment process in the organization.
These processes has helped in analyzing proper strategies. The use of the firewalls and
anti-virus software have helped in providing security to the IP address of the computer and the
server of the company (Peltier, 2016). The database of the company in the server has been
protected by using the firewalls and anti-viruses. The firewalls helps in restricting the
unauthorized users and malwares from entering the server of the organization (Ackermann,
IT RISK MANAGEMENT
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
These risks are arising in the normal conditions in the organization. Therefore, these risks
are properly maintained in the companies for protecting their data and information (Angst et al.,
2017). The risk assessment policies are developed in the organization for analyzing these risks in
the company and find a proper solution for them (Vacca, 2012). Therefore, the risk assessment
process helps in identification of the risks and developing strategies for mitigating it. There are
three levels in the risks including high-level, medium-level and low-level (Bojanc, & Jerman-
Blažič, 2013). These categorization of risks helps in identification of the strategies for
minimizing the risks and security threats in the organization. The vulnerability of security threats
helps in maintaining a proper risk assessment process in the organization.
These processes has helped in analyzing proper strategies. The use of the firewalls and
anti-virus software have helped in providing security to the IP address of the computer and the
server of the company (Peltier, 2016). The database of the company in the server has been
protected by using the firewalls and anti-viruses. The firewalls helps in restricting the
unauthorized users and malwares from entering the server of the organization (Ackermann,

8
IT RISK MANAGEMENT
2012). A proper risk management in the organization has able to develop strategies that helps in
minimizing the risks and security threats in the organization. The tracking system of the
company has enhanced that helps in the maintaining the risks and security threats j the company.
The hackers continues to attack the database server of the canny and tries to breach into the data
and information. Therefore, the firewall help in restricting the hackers to breach into the cloud
server.
Conclusion
It can be concluded that risks and security threats are prevailing in the companies. The
security threats and risks in the management has gained a pivotal role in the organization. The
RBAC model has helped in hierarchical approach of the risk assessment process in the
organization. The three different topics in the IT security has able to analyses the vulnerabilities
of the IT risks and security issues in the organization. The use of different models and theories in
the risk assessment have helped in maintaining a positive approach for reducing the risks and
data loss from the server of the company. Therefore, the need of the IT security in the
organization is important for the success of the company in the market.
IT RISK MANAGEMENT
2012). A proper risk management in the organization has able to develop strategies that helps in
minimizing the risks and security threats in the organization. The tracking system of the
company has enhanced that helps in the maintaining the risks and security threats j the company.
The hackers continues to attack the database server of the canny and tries to breach into the data
and information. Therefore, the firewall help in restricting the hackers to breach into the cloud
server.
Conclusion
It can be concluded that risks and security threats are prevailing in the companies. The
security threats and risks in the management has gained a pivotal role in the organization. The
RBAC model has helped in hierarchical approach of the risk assessment process in the
organization. The three different topics in the IT security has able to analyses the vulnerabilities
of the IT risks and security issues in the organization. The use of different models and theories in
the risk assessment have helped in maintaining a positive approach for reducing the risks and
data loss from the server of the company. Therefore, the need of the IT security in the
organization is important for the success of the company in the market.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Angst, C. M., Block, E. S., D’Arcy, J., & Kelley, K. (2017). When do IT security investments
matter? Accounting for the influence of institutional factors in the context of healthcare
data breaches. MIS Quarterly.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Herath, H. S., & Herath, T. C. (2014). IT security auditing: A performance evaluation decision
model. Decision Support Systems, 57, 54-63.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Kimwele, M. W. (2014). Information technology (IT) security in small and medium enterprises
(SMEs). In Information Systems for Small and Medium-sized Enterprises (pp. 47-64).
Springer Berlin Heidelberg.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Angst, C. M., Block, E. S., D’Arcy, J., & Kelley, K. (2017). When do IT security investments
matter? Accounting for the influence of institutional factors in the context of healthcare
data breaches. MIS Quarterly.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Herath, H. S., & Herath, T. C. (2014). IT security auditing: A performance evaluation decision
model. Decision Support Systems, 57, 54-63.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Kimwele, M. W. (2014). Information technology (IT) security in small and medium enterprises
(SMEs). In Information Systems for Small and Medium-sized Enterprises (pp. 47-64).
Springer Berlin Heidelberg.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





