IT Security: Risk Assessment, Policies, and Disaster Recovery
VerifiedAdded on 2024/06/03
|25
|6063
|108
Report
AI Summary
This report provides a comprehensive analysis of IT security within organizations, focusing on risk identification, assessment, and treatment. It details various security risks such as internet attacks, unauthorized access, hardware/software theft, and system failures, alongside organizational security procedures like risk assessment and corrective actions. The report also examines the potential impact of misconfigured firewall policies and VPNs, and how implementing DMZs, static IPs, and NAT can enhance network security. Furthermore, it discusses risk assessment procedures, data protection regulations, and the ISO 31000 risk management methodology, highlighting the importance of IT security audits and stakeholder roles. The report concludes with the design of a security policy and the main components of a disaster recovery plan, emphasizing the need for robust security measures to protect organizational assets and data. Desklib provides access to this and other solved assignments to aid students in their studies.

IT Security
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction..................................................................................................................................................1
LO 1.............................................................................................................................................................2
P1 Identify types of security risks to organisations.................................................................................2
P2 Describe organisational security procedures......................................................................................3
M1 Propose a method to assess and treat IT security risks......................................................................4
LO2..............................................................................................................................................................7
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and third-
party VPNs...............................................................................................................................................7
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a network can
improve Network Security.......................................................................................................................9
M2 Discuss three benefits to implement network monitoring systems with supporting reasons..........10
LO 3...........................................................................................................................................................12
P5 Discuss risk assessment procedures..................................................................................................12
P6 Explain data protection processes and regulations as applicable to an organisation........................13
M3 Summarise the ISO 31000 risk management methodology and its application in IT security.......13
M4 Discuss possible impacts to organisational security resulting from an IT security audit................15
LO 4...........................................................................................................................................................16
P7 Design and implement a security policy for an organisation...........................................................16
P8 List the main components of an organisational disaster recovery plan, justifying the reasons for
inclusion.................................................................................................................................................17
M5 roles of stakeholders in the organisation to implement security audit recommendations...............18
Conclusion.................................................................................................................................................19
References..................................................................................................................................................20
Introduction..................................................................................................................................................1
LO 1.............................................................................................................................................................2
P1 Identify types of security risks to organisations.................................................................................2
P2 Describe organisational security procedures......................................................................................3
M1 Propose a method to assess and treat IT security risks......................................................................4
LO2..............................................................................................................................................................7
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and third-
party VPNs...............................................................................................................................................7
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a network can
improve Network Security.......................................................................................................................9
M2 Discuss three benefits to implement network monitoring systems with supporting reasons..........10
LO 3...........................................................................................................................................................12
P5 Discuss risk assessment procedures..................................................................................................12
P6 Explain data protection processes and regulations as applicable to an organisation........................13
M3 Summarise the ISO 31000 risk management methodology and its application in IT security.......13
M4 Discuss possible impacts to organisational security resulting from an IT security audit................15
LO 4...........................................................................................................................................................16
P7 Design and implement a security policy for an organisation...........................................................16
P8 List the main components of an organisational disaster recovery plan, justifying the reasons for
inclusion.................................................................................................................................................17
M5 roles of stakeholders in the organisation to implement security audit recommendations...............18
Conclusion.................................................................................................................................................19
References..................................................................................................................................................20

LIST OF FIGURES
Figure 1:Type of security risk.....................................................................................................................2
Figure 2:Sercurity procedure.......................................................................................................................3
Figure 3: Risk as the function of vulnerabilities, threats and risks..............................................................5
Figure 4: phases for IT security risk assessment.........................................................................................5
Figure 5: Firewall.........................................................................................................................................7
Figure 6:VPNS.............................................................................................................................................8
Figure 7:DMZ Functioning..........................................................................................................................9
Figure 8:NAT functioning.........................................................................................................................10
Figure 9: ISO 31000 standard....................................................................................................................14
Figure 1:Type of security risk.....................................................................................................................2
Figure 2:Sercurity procedure.......................................................................................................................3
Figure 3: Risk as the function of vulnerabilities, threats and risks..............................................................5
Figure 4: phases for IT security risk assessment.........................................................................................5
Figure 5: Firewall.........................................................................................................................................7
Figure 6:VPNS.............................................................................................................................................8
Figure 7:DMZ Functioning..........................................................................................................................9
Figure 8:NAT functioning.........................................................................................................................10
Figure 9: ISO 31000 standard....................................................................................................................14
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
The project is based on the study of the security for the information technology to implement the new
technologies for the protection of the organisation. The Ramsac is the organisation that is used in the
project and the factors are implemented for the growth and development by reducing the safety
precaution in IT security. The type of security risk is explained along with the security procedure and IT
risk treatments. The project has provided the incorrect configuration of the VPNs and firewall that
provide the protection from the hackers and viruses. DMZ, Static IP and NAT network security is used
for the organisations security. The risk methodology is used in the project for the IT security and the
stakeholder audit and recommendation is explained in the project for the implementation of the new
technologies.
1
The project is based on the study of the security for the information technology to implement the new
technologies for the protection of the organisation. The Ramsac is the organisation that is used in the
project and the factors are implemented for the growth and development by reducing the safety
precaution in IT security. The type of security risk is explained along with the security procedure and IT
risk treatments. The project has provided the incorrect configuration of the VPNs and firewall that
provide the protection from the hackers and viruses. DMZ, Static IP and NAT network security is used
for the organisations security. The risk methodology is used in the project for the IT security and the
stakeholder audit and recommendation is explained in the project for the implementation of the new
technologies.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO 1
P1 Identify types of security risks to organisations.
The organisation main aim is to protect the operation of the system so that the records and data can be
keep safe and secure. The organisation faces the various aspects of problem and difficulties in terms of
the security. The types of security risk that affect the organisation is explained below:
Figure 1:Type of security risk
(Source: Self created)
Internet and network attack: The internet and network occur the huge level of the viruses and threats
while transferring the information from one path to other. The organisation cannot keep the internet
isolated it has to be used in all the way so must be used in such a way that cannot break the security of
the organisation (Eriksson, 2017).
Unauthorized access and use: The organisation must keep the security strong so that the unauthorized
user cannot hack the confidential data and record. It is most increasing risk type in field of the security
as the third person easily breaks the security so it should be protected.
2
Internet and network attack
unathorized access and use
Hardware / Software theft
Information theft
system failure
P1 Identify types of security risks to organisations.
The organisation main aim is to protect the operation of the system so that the records and data can be
keep safe and secure. The organisation faces the various aspects of problem and difficulties in terms of
the security. The types of security risk that affect the organisation is explained below:
Figure 1:Type of security risk
(Source: Self created)
Internet and network attack: The internet and network occur the huge level of the viruses and threats
while transferring the information from one path to other. The organisation cannot keep the internet
isolated it has to be used in all the way so must be used in such a way that cannot break the security of
the organisation (Eriksson, 2017).
Unauthorized access and use: The organisation must keep the security strong so that the unauthorized
user cannot hack the confidential data and record. It is most increasing risk type in field of the security
as the third person easily breaks the security so it should be protected.
2
Internet and network attack
unathorized access and use
Hardware / Software theft
Information theft
system failure
Hardware and software theft: The security level can be break or hacked by the unauthorized user by
damaging the software and hardware of the operating system. The Ramsac organization can configure
the high level of software and hardware so that it can be keep safe and secure from the hacker and thefts.
System Failure: The system protection is major source of risk security the hacker and theft make the
system track stop the functioning of the system operation. The user can make the system recheck so that
the system failure problem cannot arise in the computers. The authentication can make the strong so that
the system can be protected from the theft and viruses. The system failure cause by the large no of
viruses by using the internet and network as these carries viruses in no of amount that can affect the
working of the system.
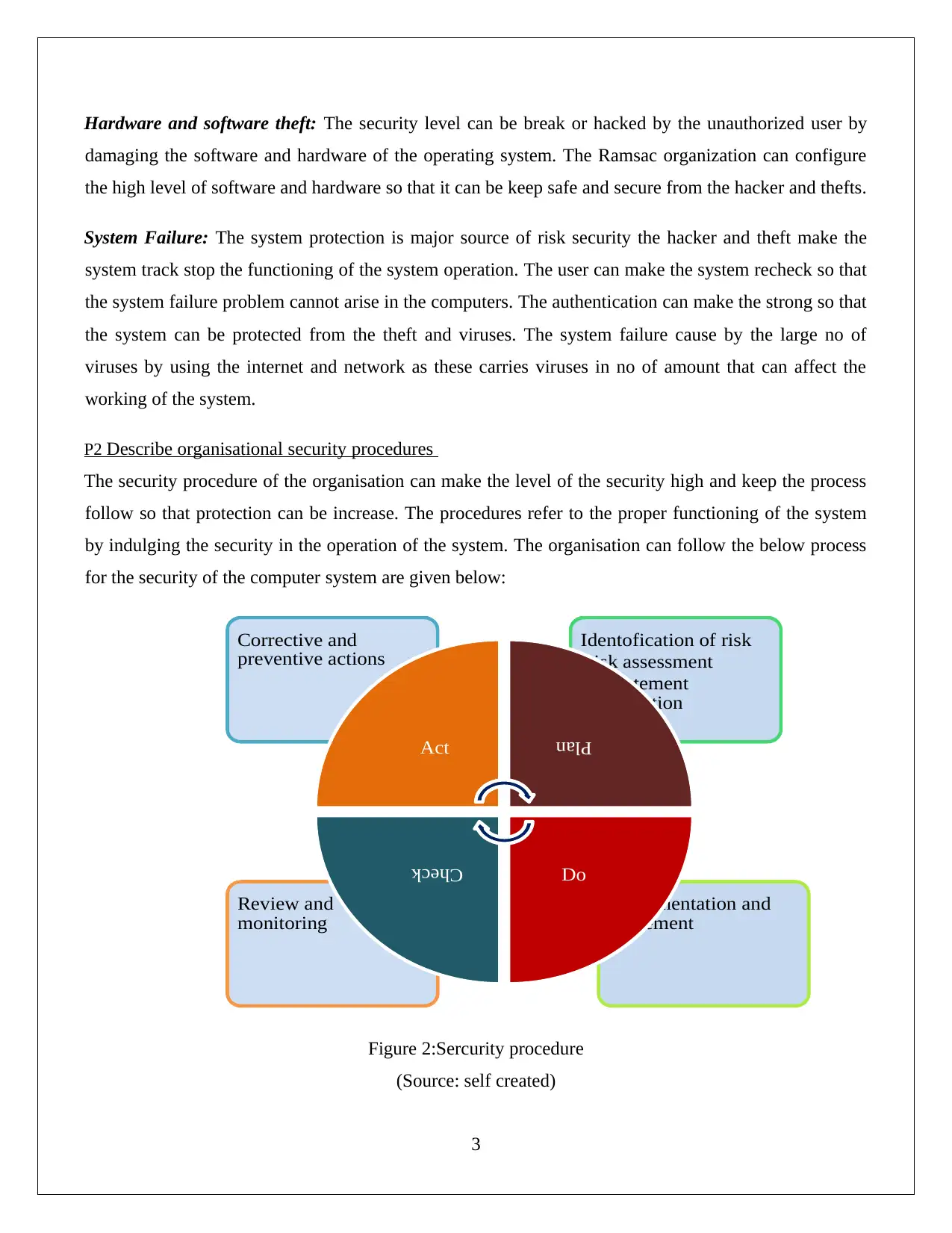
P2 Describe organisational security procedures
The security procedure of the organisation can make the level of the security high and keep the process
follow so that protection can be increase. The procedures refer to the proper functioning of the system
by indulging the security in the operation of the system. The organisation can follow the below process
for the security of the computer system are given below:
Figure 2:Sercurity procedure
(Source: self created)
3
Implementation and
treatement
Review and
monitoring
Identofication of risk
Risk assessment
Treamtement
identifcation
Corrective and
preventive actions
Act
Plan
Do Check
damaging the software and hardware of the operating system. The Ramsac organization can configure
the high level of software and hardware so that it can be keep safe and secure from the hacker and thefts.
System Failure: The system protection is major source of risk security the hacker and theft make the
system track stop the functioning of the system operation. The user can make the system recheck so that
the system failure problem cannot arise in the computers. The authentication can make the strong so that
the system can be protected from the theft and viruses. The system failure cause by the large no of
viruses by using the internet and network as these carries viruses in no of amount that can affect the
working of the system.
P2 Describe organisational security procedures
The security procedure of the organisation can make the level of the security high and keep the process
follow so that protection can be increase. The procedures refer to the proper functioning of the system
by indulging the security in the operation of the system. The organisation can follow the below process
for the security of the computer system are given below:
Figure 2:Sercurity procedure
(Source: self created)
3
Implementation and
treatement
Review and
monitoring
Identofication of risk
Risk assessment
Treamtement
identifcation
Corrective and
preventive actions
Act
Plan
Do Check
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Planning: The first procedure of the security is to plan the risk in two different ways such as
identification of the risk, risk assessment and treatment identification. The organisation first finds out
the operation so that the risk can be identified after that it can be easy for the risk treatment.
Do: After the planning of the risk and its identification the implementation can be applied for the
security of the computer and its operation. The do phase of the security procedure make the business
more reliable as it identified the functional activities (Peltier, 2016).
Check: The third step of the security procedure is to check the risk such as to review the threats and
viruses and its occurrence so that it can be rectified or correctives by the experts and professionals. The
checking of the system must be in the proper way so that virus expansion can be stop by the experts and
experienced person of the organisation.
Action: The action is the last step of the security procedure under this process the threats and viruses
can be finished by implementing the new techniques and tools in the operation of the computer. For the
security of the IT the configuration of high quality of hardware and software can be used so that the
level of the security can be increased. The main purpose of the security is to keep the level more reliable
and secure while action the function in system.
M1 Propose a method to assess and treat IT security risks
Risk assessment for the organization is the snapshot of the current risks those are impacting the
performance or security. The risk assessment process of the organization can contain the following
phases:
Threat identification: Threats on IT systems and security should be identified in the phase with the help
of the stakeholders and the proven evidence from the activities. It has analysis of the threats,
vulnerabilities and assets related to the threat.
Threat characterisation: The phase has role to identify the impacts and the likelihood of the threats in
the organization. Threats are characterised for the impacts on business security.
Exposure assessment: It means to assess the exposure of the threats on the assets of the organization. It
helps to understand the risks and their impacts on the organization. It determines which assets are at
risks or exposed to the unauthenticated users (ENISA security procedure, 2018).
4
identification of the risk, risk assessment and treatment identification. The organisation first finds out
the operation so that the risk can be identified after that it can be easy for the risk treatment.
Do: After the planning of the risk and its identification the implementation can be applied for the
security of the computer and its operation. The do phase of the security procedure make the business
more reliable as it identified the functional activities (Peltier, 2016).
Check: The third step of the security procedure is to check the risk such as to review the threats and
viruses and its occurrence so that it can be rectified or correctives by the experts and professionals. The
checking of the system must be in the proper way so that virus expansion can be stop by the experts and
experienced person of the organisation.
Action: The action is the last step of the security procedure under this process the threats and viruses
can be finished by implementing the new techniques and tools in the operation of the computer. For the
security of the IT the configuration of high quality of hardware and software can be used so that the
level of the security can be increased. The main purpose of the security is to keep the level more reliable
and secure while action the function in system.
M1 Propose a method to assess and treat IT security risks
Risk assessment for the organization is the snapshot of the current risks those are impacting the
performance or security. The risk assessment process of the organization can contain the following
phases:
Threat identification: Threats on IT systems and security should be identified in the phase with the help
of the stakeholders and the proven evidence from the activities. It has analysis of the threats,
vulnerabilities and assets related to the threat.
Threat characterisation: The phase has role to identify the impacts and the likelihood of the threats in
the organization. Threats are characterised for the impacts on business security.
Exposure assessment: It means to assess the exposure of the threats on the assets of the organization. It
helps to understand the risks and their impacts on the organization. It determines which assets are at
risks or exposed to the unauthenticated users (ENISA security procedure, 2018).
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
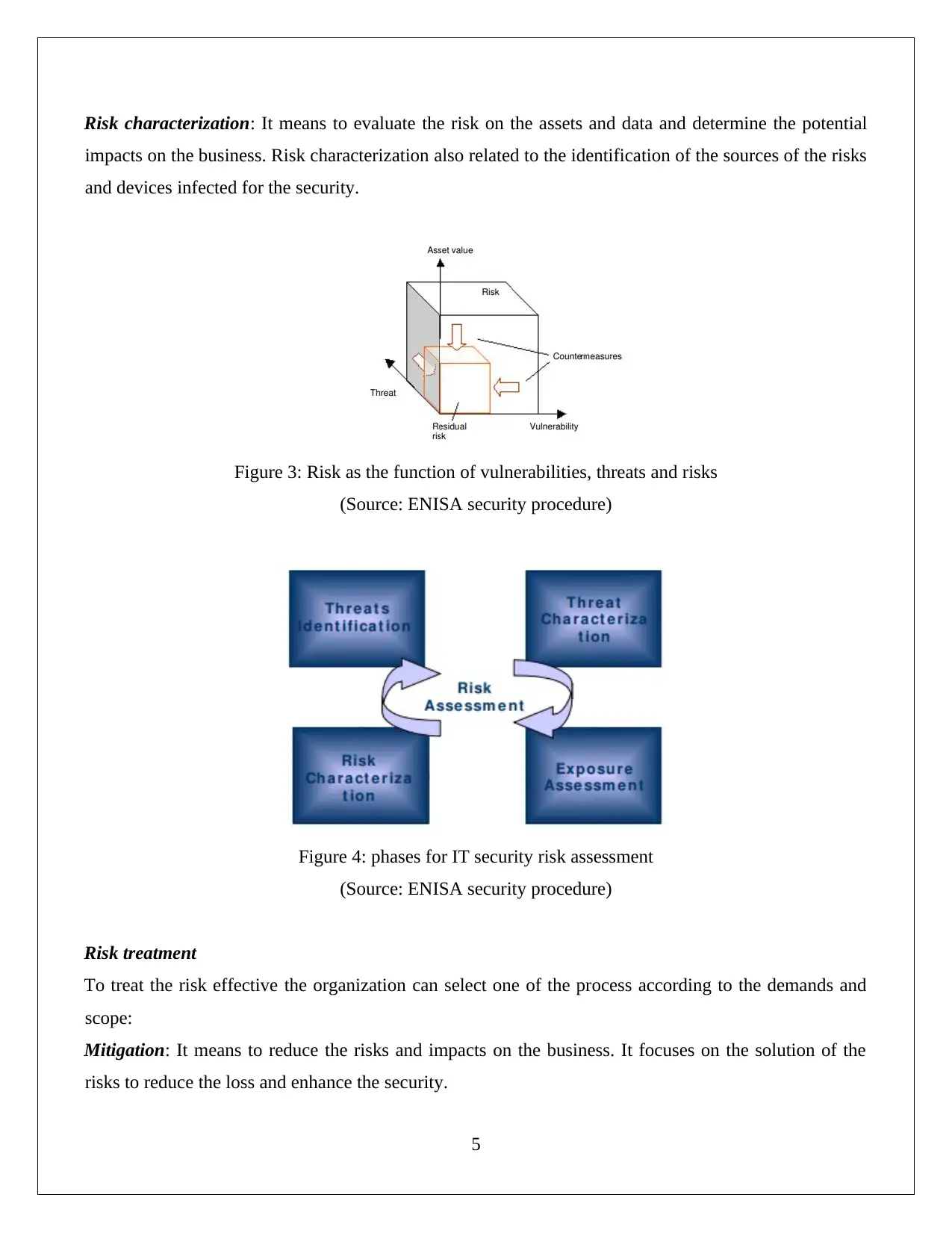
Risk characterization: It means to evaluate the risk on the assets and data and determine the potential
impacts on the business. Risk characterization also related to the identification of the sources of the risks
and devices infected for the security.
Figure 3: Risk as the function of vulnerabilities, threats and risks
(Source: ENISA security procedure)
Figure 4: phases for IT security risk assessment
(Source: ENISA security procedure)
Risk treatment
To treat the risk effective the organization can select one of the process according to the demands and
scope:
Mitigation: It means to reduce the risks and impacts on the business. It focuses on the solution of the
risks to reduce the loss and enhance the security.
5
impacts on the business. Risk characterization also related to the identification of the sources of the risks
and devices infected for the security.
Figure 3: Risk as the function of vulnerabilities, threats and risks
(Source: ENISA security procedure)
Figure 4: phases for IT security risk assessment
(Source: ENISA security procedure)
Risk treatment
To treat the risk effective the organization can select one of the process according to the demands and
scope:
Mitigation: It means to reduce the risks and impacts on the business. It focuses on the solution of the
risks to reduce the loss and enhance the security.
5

Transfer: Risk can be transferred to the third party through the outsourcing and service providing so that
the organization can focus on the security and business operations. It helps to save the cost and time to
handle the risks and ensures maximum recovery from the lost.
Avoidance: Management can make the decisions on the risk handling. They can avoid the risk to focus
on the primary goals. However, there is threat that the organization can face more critical conditions if
risk exploit to more assets and data sources (Aljawarneh, 2013).
Retention of risks: The risks can be retained in the business with the proper planning and management
practices. It means to accept the risks and resolve with proper planning whereas the risks are solved over
the time. During the risk retention process, the organization insurances for the full or part of the risks to
recover the benefits. In it, the organization has no complete management plan for the risk and only focus
on the benefitted areas to attain the most of the returns.
6
the organization can focus on the security and business operations. It helps to save the cost and time to
handle the risks and ensures maximum recovery from the lost.
Avoidance: Management can make the decisions on the risk handling. They can avoid the risk to focus
on the primary goals. However, there is threat that the organization can face more critical conditions if
risk exploit to more assets and data sources (Aljawarneh, 2013).
Retention of risks: The risks can be retained in the business with the proper planning and management
practices. It means to accept the risks and resolve with proper planning whereas the risks are solved over
the time. During the risk retention process, the organization insurances for the full or part of the risks to
recover the benefits. In it, the organization has no complete management plan for the risk and only focus
on the benefitted areas to attain the most of the returns.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
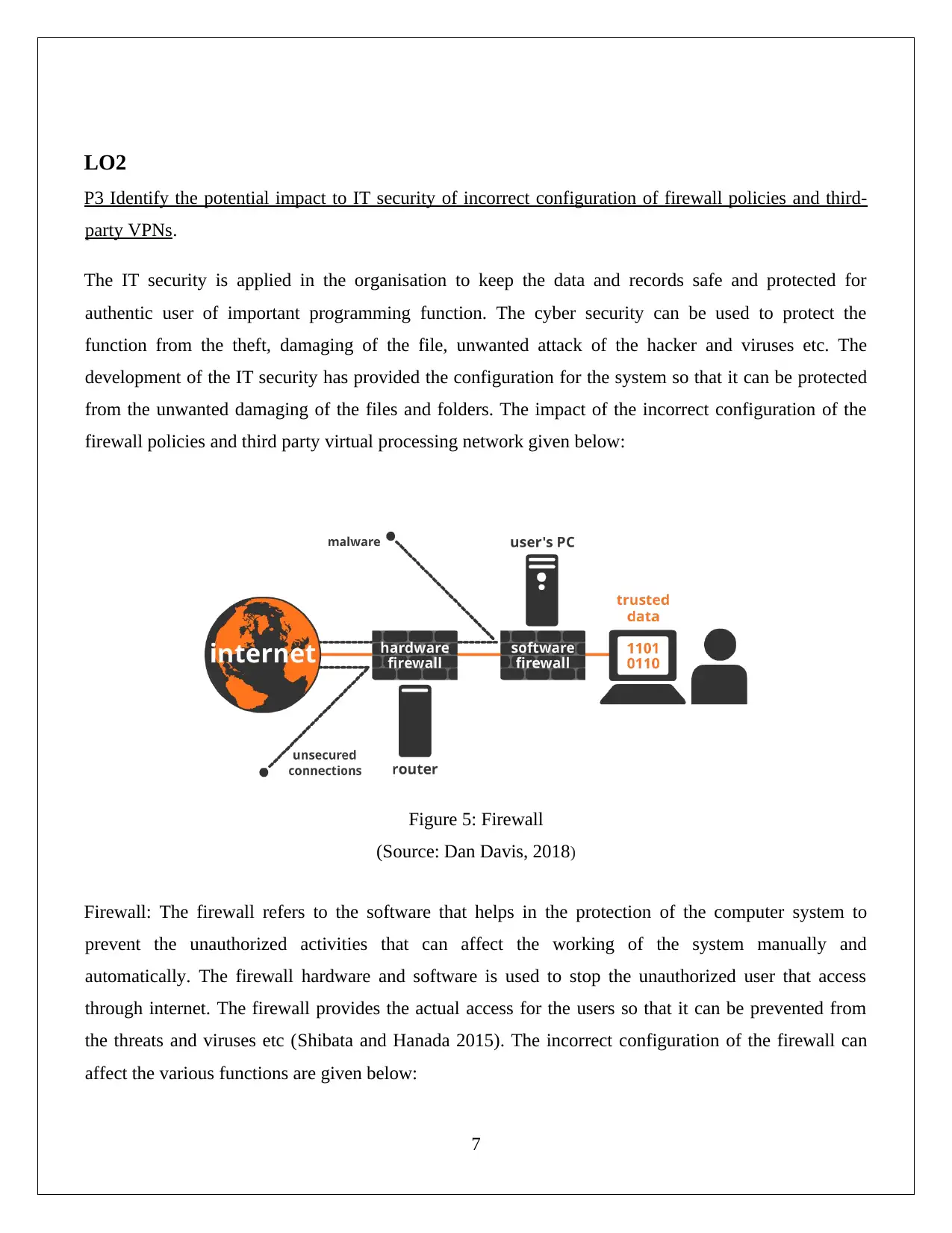
LO2
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and third-
party VPNs.
The IT security is applied in the organisation to keep the data and records safe and protected for
authentic user of important programming function. The cyber security can be used to protect the
function from the theft, damaging of the file, unwanted attack of the hacker and viruses etc. The
development of the IT security has provided the configuration for the system so that it can be protected
from the unwanted damaging of the files and folders. The impact of the incorrect configuration of the
firewall policies and third party virtual processing network given below:
Figure 5: Firewall
(Source: Dan Davis, 2018)
Firewall: The firewall refers to the software that helps in the protection of the computer system to
prevent the unauthorized activities that can affect the working of the system manually and
automatically. The firewall hardware and software is used to stop the unauthorized user that access
through internet. The firewall provides the actual access for the users so that it can be prevented from
the threats and viruses etc (Shibata and Hanada 2015). The incorrect configuration of the firewall can
affect the various functions are given below:
7
P3 Identify the potential impact to IT security of incorrect configuration of firewall policies and third-
party VPNs.
The IT security is applied in the organisation to keep the data and records safe and protected for
authentic user of important programming function. The cyber security can be used to protect the
function from the theft, damaging of the file, unwanted attack of the hacker and viruses etc. The
development of the IT security has provided the configuration for the system so that it can be protected
from the unwanted damaging of the files and folders. The impact of the incorrect configuration of the
firewall policies and third party virtual processing network given below:
Figure 5: Firewall
(Source: Dan Davis, 2018)
Firewall: The firewall refers to the software that helps in the protection of the computer system to
prevent the unauthorized activities that can affect the working of the system manually and
automatically. The firewall hardware and software is used to stop the unauthorized user that access
through internet. The firewall provides the actual access for the users so that it can be prevented from
the threats and viruses etc (Shibata and Hanada 2015). The incorrect configuration of the firewall can
affect the various functions are given below:
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
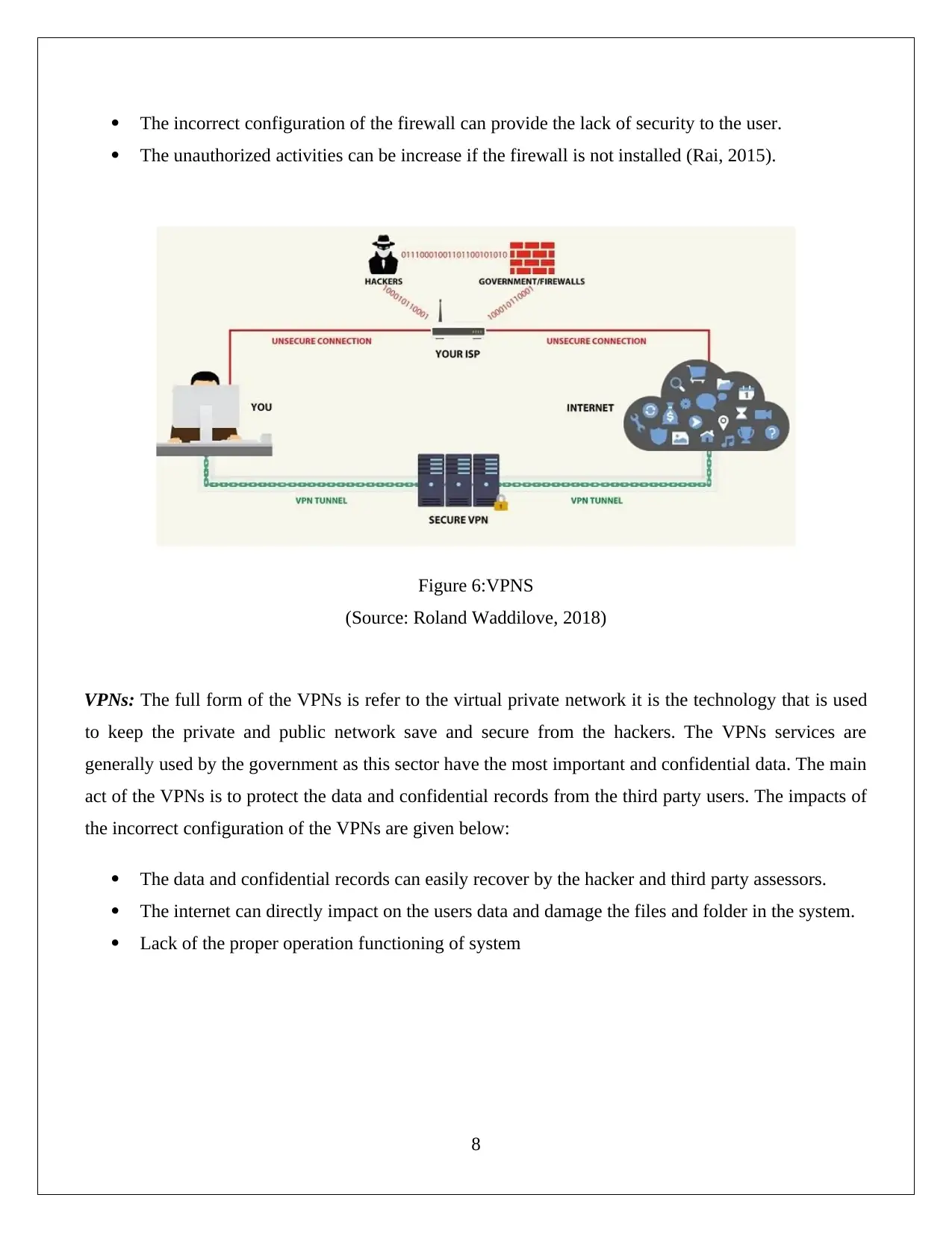
The incorrect configuration of the firewall can provide the lack of security to the user.
The unauthorized activities can be increase if the firewall is not installed (Rai, 2015).
Figure 6:VPNS
(Source: Roland Waddilove, 2018)
VPNs: The full form of the VPNs is refer to the virtual private network it is the technology that is used
to keep the private and public network save and secure from the hackers. The VPNs services are
generally used by the government as this sector have the most important and confidential data. The main
act of the VPNs is to protect the data and confidential records from the third party users. The impacts of
the incorrect configuration of the VPNs are given below:
The data and confidential records can easily recover by the hacker and third party assessors.
The internet can directly impact on the users data and damage the files and folder in the system.
Lack of the proper operation functioning of system
8
The unauthorized activities can be increase if the firewall is not installed (Rai, 2015).
Figure 6:VPNS
(Source: Roland Waddilove, 2018)
VPNs: The full form of the VPNs is refer to the virtual private network it is the technology that is used
to keep the private and public network save and secure from the hackers. The VPNs services are
generally used by the government as this sector have the most important and confidential data. The main
act of the VPNs is to protect the data and confidential records from the third party users. The impacts of
the incorrect configuration of the VPNs are given below:
The data and confidential records can easily recover by the hacker and third party assessors.
The internet can directly impact on the users data and damage the files and folder in the system.
Lack of the proper operation functioning of system
8
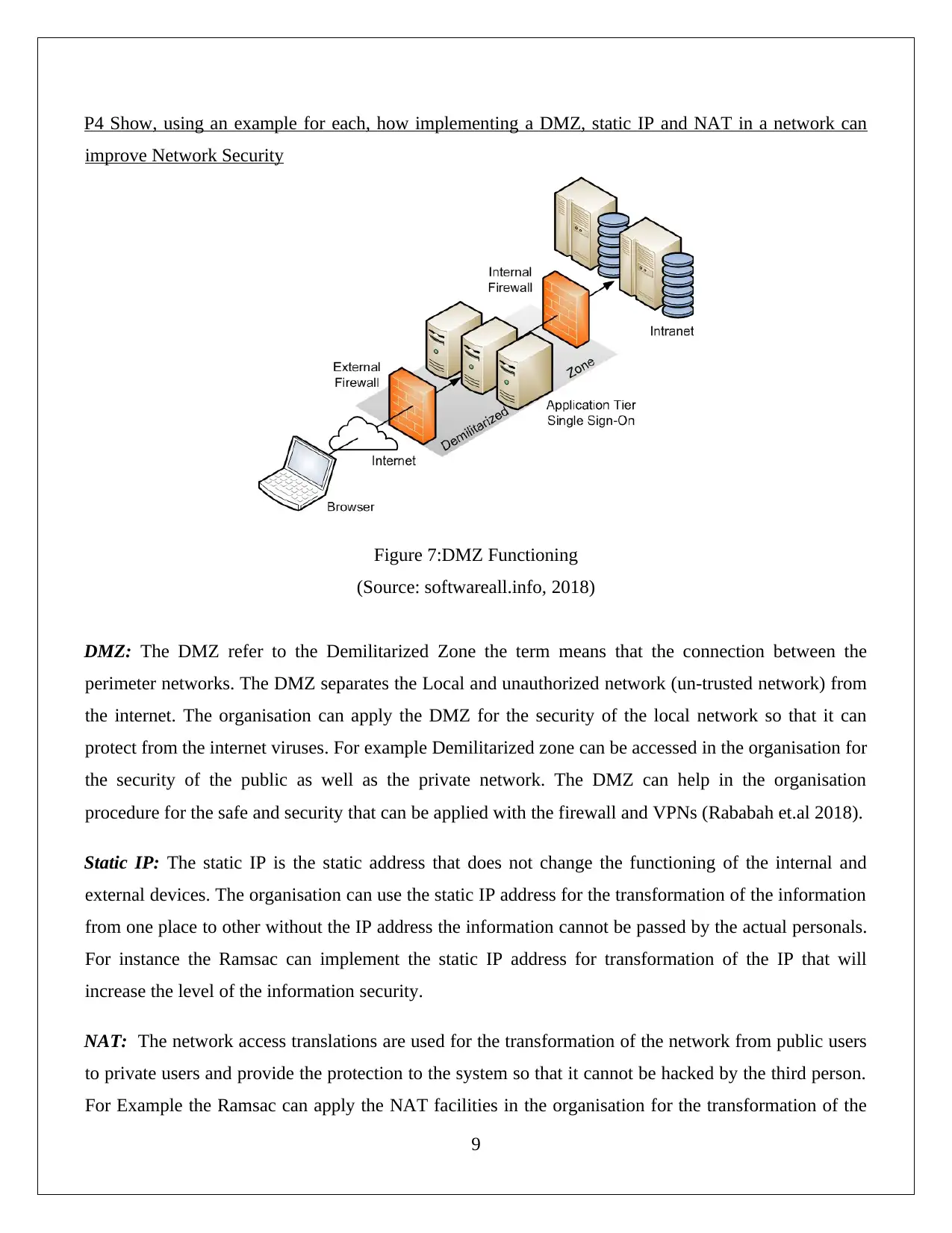
P4 Show, using an example for each, how implementing a DMZ, static IP and NAT in a network can
improve Network Security
Figure 7:DMZ Functioning
(Source: softwareall.info, 2018)
DMZ: The DMZ refer to the Demilitarized Zone the term means that the connection between the
perimeter networks. The DMZ separates the Local and unauthorized network (un-trusted network) from
the internet. The organisation can apply the DMZ for the security of the local network so that it can
protect from the internet viruses. For example Demilitarized zone can be accessed in the organisation for
the security of the public as well as the private network. The DMZ can help in the organisation
procedure for the safe and security that can be applied with the firewall and VPNs (Rababah et.al 2018).
Static IP: The static IP is the static address that does not change the functioning of the internal and
external devices. The organisation can use the static IP address for the transformation of the information
from one place to other without the IP address the information cannot be passed by the actual personals.
For instance the Ramsac can implement the static IP address for transformation of the IP that will
increase the level of the information security.
NAT: The network access translations are used for the transformation of the network from public users
to private users and provide the protection to the system so that it cannot be hacked by the third person.
For Example the Ramsac can apply the NAT facilities in the organisation for the transformation of the
9
improve Network Security
Figure 7:DMZ Functioning
(Source: softwareall.info, 2018)
DMZ: The DMZ refer to the Demilitarized Zone the term means that the connection between the
perimeter networks. The DMZ separates the Local and unauthorized network (un-trusted network) from
the internet. The organisation can apply the DMZ for the security of the local network so that it can
protect from the internet viruses. For example Demilitarized zone can be accessed in the organisation for
the security of the public as well as the private network. The DMZ can help in the organisation
procedure for the safe and security that can be applied with the firewall and VPNs (Rababah et.al 2018).
Static IP: The static IP is the static address that does not change the functioning of the internal and
external devices. The organisation can use the static IP address for the transformation of the information
from one place to other without the IP address the information cannot be passed by the actual personals.
For instance the Ramsac can implement the static IP address for transformation of the IP that will
increase the level of the information security.
NAT: The network access translations are used for the transformation of the network from public users
to private users and provide the protection to the system so that it cannot be hacked by the third person.
For Example the Ramsac can apply the NAT facilities in the organisation for the transformation of the
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 25
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.


