IT Security: Risk Assessment, Data Protection, Policy Design & Impact
VerifiedAdded on 2024/06/03
|18
|4231
|429
Report
AI Summary
This report provides a comprehensive analysis of IT security, beginning with risk assessment procedures and the application of ISO 31000 standards for effective risk management. It discusses data protection processes and regulations, including the Data Protection Act, Computer Misuse Act, and ISO 3001 standard. The report explores the potential impacts of IT security audits on organizational security, emphasizing user account security, policy configuration, server strengthening, security automation, and hardware maintenance. It also addresses the alignment of IT security with organizational policy, highlighting the security implications of misalignment. Furthermore, the report designs and implements a security policy, lists the main components of an organizational disaster recovery plan, and discusses the roles of stakeholders in implementing security audit recommendations. The evaluation of tools used in organizational policy concludes the analysis, providing a holistic view of IT security management.

IT SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction..................................................................................................................................................1
LO 3.............................................................................................................................................................2
P5 Discuss risk assessment procedures....................................................................................................2
P6 Explain data protection processes and regulations as applicable to an organization.........................3
M3 Summaries the ISO 31000 risk management methodology and its application in IT security.........4
M4 Discuss possible impacts to organizational security resulting from an IT security audit.................5
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact
of any misalignment................................................................................................................................6
LO 4.............................................................................................................................................................8
P7 Design and implement a security policy for an organization.............................................................8
P8. List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion...................................................................................................................................................9
M5. Discuss the roles of stakeholder in the organization to implement security audit recommendations
...............................................................................................................................................................10
D3 Evaluate the suitability of the tools used in an organizational policy..............................................11
Conclusion.................................................................................................................................................12
References..................................................................................................................................................13
Introduction..................................................................................................................................................1
LO 3.............................................................................................................................................................2
P5 Discuss risk assessment procedures....................................................................................................2
P6 Explain data protection processes and regulations as applicable to an organization.........................3
M3 Summaries the ISO 31000 risk management methodology and its application in IT security.........4
M4 Discuss possible impacts to organizational security resulting from an IT security audit.................5
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact
of any misalignment................................................................................................................................6
LO 4.............................................................................................................................................................8
P7 Design and implement a security policy for an organization.............................................................8
P8. List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion...................................................................................................................................................9
M5. Discuss the roles of stakeholder in the organization to implement security audit recommendations
...............................................................................................................................................................10
D3 Evaluate the suitability of the tools used in an organizational policy..............................................11
Conclusion.................................................................................................................................................12
References..................................................................................................................................................13

LIST OF FIGURES
Figure 1: Risk assessment process...............................................................................................................3
Figure 2: Principles, framework and process in ISO 31000........................................................................5
Figure 3: Wireshark for data analysis in network......................................................................................11
Figure 4: Nessus vulnerabilities scanner....................................................................................................12
Figure 1: Risk assessment process...............................................................................................................3
Figure 2: Principles, framework and process in ISO 31000........................................................................5
Figure 3: Wireshark for data analysis in network......................................................................................11
Figure 4: Nessus vulnerabilities scanner....................................................................................................12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Introduction
Information technology is widely spread and used in every field; particularly it is of great significance in
business operations. IT system helps to accomplish the various organizational tasks and objectives by
gathering the information and generation of decision making process. Security enables the growth and
competence of the organization in the market. Therefore, the report will discuss risk assessment
procedures with discussion of the ISO 31000 standards. Various impacts of the security audit process on
the security of the organization will be discussed along with data protection process and regulations.
Report will discuss the applicability of the standards and regulations in the business for the security
purpose. Report will design and implement the security policies, list the main components of the
organizational disaster recovery plan and discuss the role of stakeholders in the implementation of the
security audits. Also various tools for security policies will be focussed.
1
Information technology is widely spread and used in every field; particularly it is of great significance in
business operations. IT system helps to accomplish the various organizational tasks and objectives by
gathering the information and generation of decision making process. Security enables the growth and
competence of the organization in the market. Therefore, the report will discuss risk assessment
procedures with discussion of the ISO 31000 standards. Various impacts of the security audit process on
the security of the organization will be discussed along with data protection process and regulations.
Report will discuss the applicability of the standards and regulations in the business for the security
purpose. Report will design and implement the security policies, list the main components of the
organizational disaster recovery plan and discuss the role of stakeholders in the implementation of the
security audits. Also various tools for security policies will be focussed.
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO 3
P5 Discuss risk assessment procedures
The risk assessment procedure of the organization has involvement of the two processes. First, risk
identification in which the risk is identified from the analysis of the systems and network resources
whereas in second, risk evaluation, the impact and potential solutions of the identified through the
organizational controls and standards. Risk assessment procedure is foundation for the risk management
risks so that the organization can handle the risk effectively with the proper understanding and
knowledge with the risk, impacts and sources. Risk assessment procedure in the organization has five
major steps:
The organization can use the already gained knowledge and experience to understand the risks
with the information technology system. The process is further supported with the engagement
and communication of the employees. The step has role to define and identify the risk in the
organization.
Later the organization can focus on the controls those are working on the business. It contains
system and environmental controls in which risk in impacting the security. Controls are the
major considerable factors of the IT systems those can bring strength or weaknesses (Clir.org,
2018). Therefore, it is essential to define the controls and then determine the weaker controls to
handle the risks.
Risk assessment can be done through the consideration of the various techniques. For example,
risk matrices and impact analysis can be used to assess the risk. The objective of the risk
assessment is to uncover the security risks along with their source.
Risk analysis process has consideration of the sources associated with the risk and then
evaluates the solutions for the security. The stage has role to justify the solution for the security
purpose in the information technology system (Bahr, 2014).
Later the organization has to make the plan for the risk testing and document the results to
provide the understanding and knowledge in the future for such events and actions.
2
P5 Discuss risk assessment procedures
The risk assessment procedure of the organization has involvement of the two processes. First, risk
identification in which the risk is identified from the analysis of the systems and network resources
whereas in second, risk evaluation, the impact and potential solutions of the identified through the
organizational controls and standards. Risk assessment procedure is foundation for the risk management
risks so that the organization can handle the risk effectively with the proper understanding and
knowledge with the risk, impacts and sources. Risk assessment procedure in the organization has five
major steps:
The organization can use the already gained knowledge and experience to understand the risks
with the information technology system. The process is further supported with the engagement
and communication of the employees. The step has role to define and identify the risk in the
organization.
Later the organization can focus on the controls those are working on the business. It contains
system and environmental controls in which risk in impacting the security. Controls are the
major considerable factors of the IT systems those can bring strength or weaknesses (Clir.org,
2018). Therefore, it is essential to define the controls and then determine the weaker controls to
handle the risks.
Risk assessment can be done through the consideration of the various techniques. For example,
risk matrices and impact analysis can be used to assess the risk. The objective of the risk
assessment is to uncover the security risks along with their source.
Risk analysis process has consideration of the sources associated with the risk and then
evaluates the solutions for the security. The stage has role to justify the solution for the security
purpose in the information technology system (Bahr, 2014).
Later the organization has to make the plan for the risk testing and document the results to
provide the understanding and knowledge in the future for such events and actions.
2

Figure 1: Risk assessment process
(Source: clir.org, 2018)
P6 Explain data protection processes and regulations as applicable to an organization
Data protection means to protect the information with high accuracy and consistency and ensure that it is
safe from the unwanted use or sharing. The organizations can follow the various processes to achieve
the data protection. Also the regulations can be enforced in the business process to achieve the data
security as it constraints the users for the operations and sharing on the data.
Data protection act: The act has guideline how the personal information can be used in the
organizations, governments and business. According to the act, the owner of the information has to
acquire the knowledge where the information has been used or shared in the organizations. It enforces
the organization to manage the individual’s privacy and confidentiality. It ensures that information is
used fairly and lawfully for the specific purpose (Sauerwein and Linnemann, 2016). Also information
should be handled effectively according to the rights and permissions of the owner.
Computer misuse act: The act has enforced the use of the computer resources in the lawful manner so
that users of the organizations are not allowed to use the system for the personal purpose. For example,
the users are not allowed to do the personal work at workplace and they cannot use the systems to store
3
(Source: clir.org, 2018)
P6 Explain data protection processes and regulations as applicable to an organization
Data protection means to protect the information with high accuracy and consistency and ensure that it is
safe from the unwanted use or sharing. The organizations can follow the various processes to achieve
the data protection. Also the regulations can be enforced in the business process to achieve the data
security as it constraints the users for the operations and sharing on the data.
Data protection act: The act has guideline how the personal information can be used in the
organizations, governments and business. According to the act, the owner of the information has to
acquire the knowledge where the information has been used or shared in the organizations. It enforces
the organization to manage the individual’s privacy and confidentiality. It ensures that information is
used fairly and lawfully for the specific purpose (Sauerwein and Linnemann, 2016). Also information
should be handled effectively according to the rights and permissions of the owner.
Computer misuse act: The act has enforced the use of the computer resources in the lawful manner so
that users of the organizations are not allowed to use the system for the personal purpose. For example,
the users are not allowed to do the personal work at workplace and they cannot use the systems to store
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

their personal data (Fafinski, 2013). Also they cannot use the system in the criminal or unwanted
activities according to the policies and rules of the organization.
ISO 3001 standard: According to the standard, the risk management process can be simplified and
accomplished easily. The organization can use the principles, guidelines and framework to identify and
assess the risk effectively. The standard has focus on the utilization of the assets and resources in the
systematic manner to handle the risks and reduce the impacts (Lalonde and Boiral, 2012).
M3 Summaries the ISO 31000 risk management methodology and its application in IT security.
The standard has supported the organizations to design, implement and manage the risk management
activities in the effective manner. The organizations can use the methodology with the proper
integration of the stakeholders and business operations. The standard has following major principles
related to the risk management:
The process of risk management creates values for the organizations and it is the integral part of
the operations.
It is effective to address the uncertainly in the business and help in the decision making process.
It is based on the available information but well structured and systematic to meet the security
goals.
It is tailored and considers the human and cultural factors with high transparency and inclusion.
It is highly flexible and responsive to adopt the changes and supports improvements over time.
The standard has simple concept to handle the risks as shown in the framework of the standard
(Ernawati and Nugroho, 2012). The standard focus on the identification of the risks, implements the risk
management plan, monitor the plan and then improve it over the time.
4
activities according to the policies and rules of the organization.
ISO 3001 standard: According to the standard, the risk management process can be simplified and
accomplished easily. The organization can use the principles, guidelines and framework to identify and
assess the risk effectively. The standard has focus on the utilization of the assets and resources in the
systematic manner to handle the risks and reduce the impacts (Lalonde and Boiral, 2012).
M3 Summaries the ISO 31000 risk management methodology and its application in IT security.
The standard has supported the organizations to design, implement and manage the risk management
activities in the effective manner. The organizations can use the methodology with the proper
integration of the stakeholders and business operations. The standard has following major principles
related to the risk management:
The process of risk management creates values for the organizations and it is the integral part of
the operations.
It is effective to address the uncertainly in the business and help in the decision making process.
It is based on the available information but well structured and systematic to meet the security
goals.
It is tailored and considers the human and cultural factors with high transparency and inclusion.
It is highly flexible and responsive to adopt the changes and supports improvements over time.
The standard has simple concept to handle the risks as shown in the framework of the standard
(Ernawati and Nugroho, 2012). The standard focus on the identification of the risks, implements the risk
management plan, monitor the plan and then improve it over the time.
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
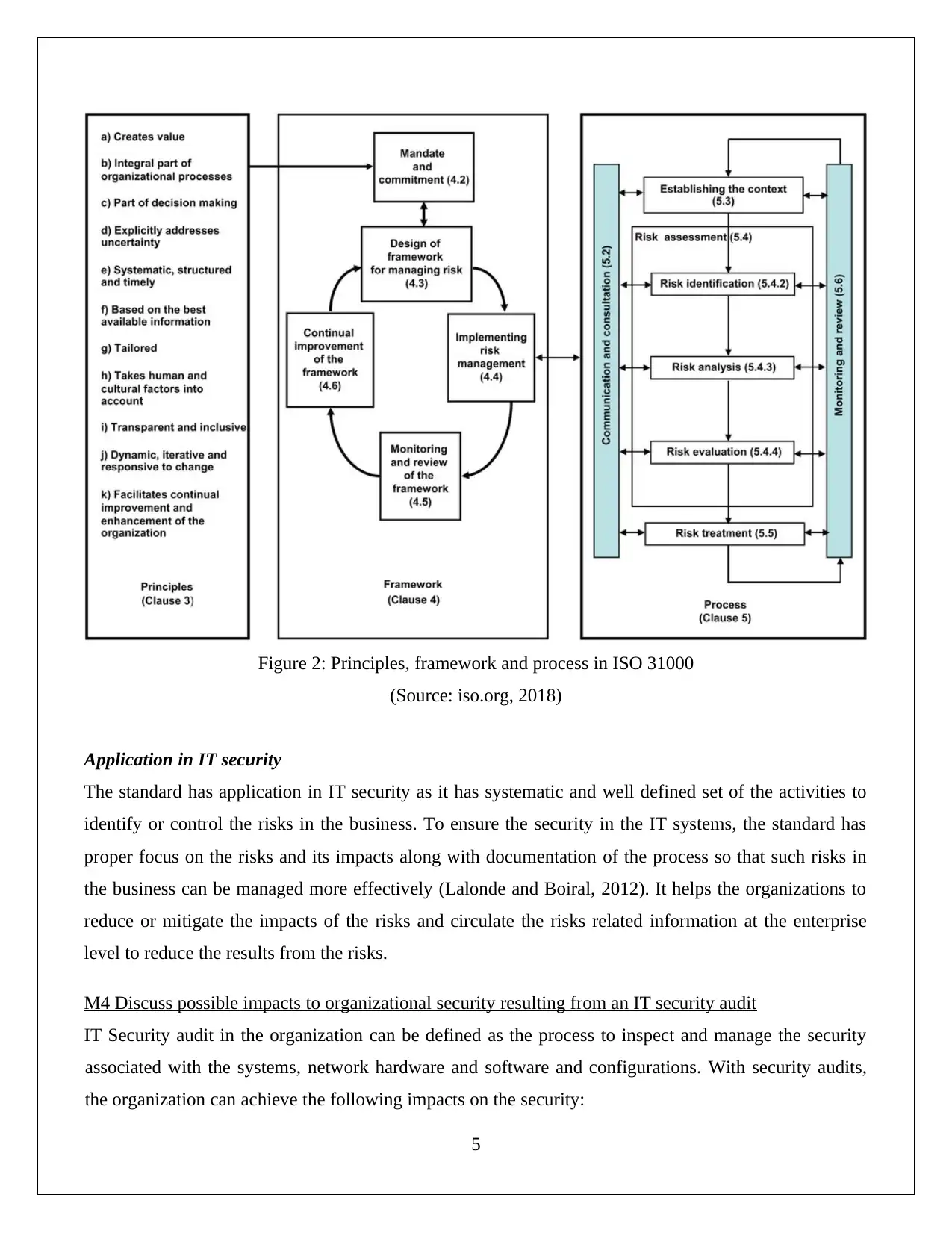
Figure 2: Principles, framework and process in ISO 31000
(Source: iso.org, 2018)
Application in IT security
The standard has application in IT security as it has systematic and well defined set of the activities to
identify or control the risks in the business. To ensure the security in the IT systems, the standard has
proper focus on the risks and its impacts along with documentation of the process so that such risks in
the business can be managed more effectively (Lalonde and Boiral, 2012). It helps the organizations to
reduce or mitigate the impacts of the risks and circulate the risks related information at the enterprise
level to reduce the results from the risks.
M4 Discuss possible impacts to organizational security resulting from an IT security audit
IT Security audit in the organization can be defined as the process to inspect and manage the security
associated with the systems, network hardware and software and configurations. With security audits,
the organization can achieve the following impacts on the security:
5
(Source: iso.org, 2018)
Application in IT security
The standard has application in IT security as it has systematic and well defined set of the activities to
identify or control the risks in the business. To ensure the security in the IT systems, the standard has
proper focus on the risks and its impacts along with documentation of the process so that such risks in
the business can be managed more effectively (Lalonde and Boiral, 2012). It helps the organizations to
reduce or mitigate the impacts of the risks and circulate the risks related information at the enterprise
level to reduce the results from the risks.
M4 Discuss possible impacts to organizational security resulting from an IT security audit
IT Security audit in the organization can be defined as the process to inspect and manage the security
associated with the systems, network hardware and software and configurations. With security audits,
the organization can achieve the following impacts on the security:
5

User account security: The organization can monitor the security on the use accounts with the help of
security audit. It can uncover the user accounts those have weaker authentication method or pass phrase
or lacking two-factor authentication. It can help to determine the user responsibilities and roles in the
network and configure the user actions and permissions in the system.
Configure security policies: System security is implemented through the proper configuration of the
system, user accounts, and network hardware and software. It improves security policies and
implements the protocols required for security.
Strengthen server configuration: It can monitor the server for the configuration and provide the high
performance and security (Synergyintegrations.com.au, 2018). It can be protected from the risks and
threats on the data storages. The provisioning of servers can deliver reliable configuration toward
desired security status.
Security automation: It can review the physical security of the system and can provide the automation
in the security. Commercial alarm systems and smart locks can be configured for their automated
operations in the system.
Hardware maintenance: Performance of the IT system has root in the configuration and installation of
the hardware. Security audit can boost the security with proper installation and recommendation of the
hardware components in the network and system to achieve the goal (Steinbart et al, 2012).
In this manner, security audit in the organization can help to achieve security to the next level where the
organization can provision the physical and logical security and protect the data and assets from the
misuse, theft or damage.
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact of
any misalignment
IT security can be achieved with the help of the organizational policies because the organizational
policies define the rules and regulations on the behaviour of the employees and promoted them to use
the resources effectively. Policies also make them aware about the losses and damages associated with
the misuse of the system and features against the organizational rules. It defines the roles and
responsibilities of the users so that security can be implemented easily. IT security can be made simple
with the help of the policies on the user accounts, user permissions, system placement and management
6
security audit. It can uncover the user accounts those have weaker authentication method or pass phrase
or lacking two-factor authentication. It can help to determine the user responsibilities and roles in the
network and configure the user actions and permissions in the system.
Configure security policies: System security is implemented through the proper configuration of the
system, user accounts, and network hardware and software. It improves security policies and
implements the protocols required for security.
Strengthen server configuration: It can monitor the server for the configuration and provide the high
performance and security (Synergyintegrations.com.au, 2018). It can be protected from the risks and
threats on the data storages. The provisioning of servers can deliver reliable configuration toward
desired security status.
Security automation: It can review the physical security of the system and can provide the automation
in the security. Commercial alarm systems and smart locks can be configured for their automated
operations in the system.
Hardware maintenance: Performance of the IT system has root in the configuration and installation of
the hardware. Security audit can boost the security with proper installation and recommendation of the
hardware components in the network and system to achieve the goal (Steinbart et al, 2012).
In this manner, security audit in the organization can help to achieve security to the next level where the
organization can provision the physical and logical security and protect the data and assets from the
misuse, theft or damage.
D2 Consider how IT security can be aligned with organizational policy, detailing the security impact of
any misalignment
IT security can be achieved with the help of the organizational policies because the organizational
policies define the rules and regulations on the behaviour of the employees and promoted them to use
the resources effectively. Policies also make them aware about the losses and damages associated with
the misuse of the system and features against the organizational rules. It defines the roles and
responsibilities of the users so that security can be implemented easily. IT security can be made simple
with the help of the policies on the user accounts, user permissions, system placement and management
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

of the network services (Siponen et al, 2014). Therefore, the security policies also have to consider the
integration of the legal framework to make them standard in the business operations.
However, misalignment of the policies for the IT security can lead the conflicts among the users for the
roles and security responsibility. Also the conflicts might be occurred among the law and regulations
and organizational policies for the differences in the implementation. Misalignment can damage the
security parameters in the organization and allow the users to extend the risk with authenticity on the
system and resources.
7
integration of the legal framework to make them standard in the business operations.
However, misalignment of the policies for the IT security can lead the conflicts among the users for the
roles and security responsibility. Also the conflicts might be occurred among the law and regulations
and organizational policies for the differences in the implementation. Misalignment can damage the
security parameters in the organization and allow the users to extend the risk with authenticity on the
system and resources.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

LO 4
P7 Design and implement a security policy for an organization
Security policy in the organization is a critical document which records the rules and processes those
must be integrated in the business operations so that security can be adhered. It must have to contain the
purpose and the sections for that the business wants to constraint the risks through security guidelines.
Design and implementation
Significance: The significance of the security policy in the organization is to empower the use of the
resources and services for the business purpose only and reduce the crime and failure risks through the
personal utilization of the network capabilities.
Use of systems
Users are allowed only to use the systems for the business purpose. They cannot accomplish
personal goals and objectives through the organizational assets.
Users are suggested to safe their data and user account through the eight character long and
complex passphrase.
Users are recommended to use the systems only in the defined permissions and timeframe so that
they can be authenticate on the system (Chen et al, 2012).
External connections and adding of the peripherals on the system is prohibited and user might be
marked for the misconducts.
Systems damaged or destructed during the user actions are the liabilities of the users and they
must have to report the issues to the management.
Use of mail services
Do not share the mail authentication details with others. It is the sole liability of the user to
ensure the security on the own mail account.
User cannot use the mail services to blackmail the others or to support the personal
communication over the internet.
8
P7 Design and implement a security policy for an organization
Security policy in the organization is a critical document which records the rules and processes those
must be integrated in the business operations so that security can be adhered. It must have to contain the
purpose and the sections for that the business wants to constraint the risks through security guidelines.
Design and implementation
Significance: The significance of the security policy in the organization is to empower the use of the
resources and services for the business purpose only and reduce the crime and failure risks through the
personal utilization of the network capabilities.
Use of systems
Users are allowed only to use the systems for the business purpose. They cannot accomplish
personal goals and objectives through the organizational assets.
Users are suggested to safe their data and user account through the eight character long and
complex passphrase.
Users are recommended to use the systems only in the defined permissions and timeframe so that
they can be authenticate on the system (Chen et al, 2012).
External connections and adding of the peripherals on the system is prohibited and user might be
marked for the misconducts.
Systems damaged or destructed during the user actions are the liabilities of the users and they
must have to report the issues to the management.
Use of mail services
Do not share the mail authentication details with others. It is the sole liability of the user to
ensure the security on the own mail account.
User cannot use the mail services to blackmail the others or to support the personal
communication over the internet.
8

Unwanted and intentional requests to the server to influence the performance are the subject of
misconduct in the operations.
It is highly recommended to avoid the financial transactions over the mail requests from the
anonymous. It is the liability of the user to report such actions to management (Neisse et al,
2014).
Prohibited or abusing words or sentences should not be used in the mail content. Such senders
might be blocked for the mail services on the basis of the complaints.
P8. List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion
During disaster organisation conquer with several problems related to their sensitive data and potential
resources which might get lost. At that time, the organisation cannot bear such data loss which can
affect the growth rate of the organisation which necessitates the need of recovering the lost data. By the
help of several recoveries plan organisation can recover the potential resources and information to
sustain the continuity of the business. Following are the components of recovery plan adopted by the
organisation:
Backup: Backup is the term which refers to the second copy of the data and information creation that
can be reloaded at the time of situation where organisation faces the disastrous loss of vital information.
This is done when the access to the primary data get lost. As this taking up of backup created by the
organisation is of great importance to recover the sensitive data in case of disastrous condition
(Snedaker, 2013). Accessing the incremental backup taking process only by considering the space to
save when the previous back up is not covered in the information.
Monitoring: After recovering the backup of the lost data and resources, monitoring and regulating of the
IT systems is required for the security purpose. This monitoring process is essentially required to
prevent the loss of the organisation by determining the possible sources and their possible solution at the
time of disastrous situation. Further this also helps to take decisions on time to minimize the loss at time
of disaster condition.
Redundancy: To manage or handling the data and connectivity between two devices organisation can
the redundant the organisational devices. For ensuring the continuity redundancy delivers the alternative
sources for the communication (Järveläinen, 2013). At the time of disastrous situation when
9
misconduct in the operations.
It is highly recommended to avoid the financial transactions over the mail requests from the
anonymous. It is the liability of the user to report such actions to management (Neisse et al,
2014).
Prohibited or abusing words or sentences should not be used in the mail content. Such senders
might be blocked for the mail services on the basis of the complaints.
P8. List the main components of an organizational disaster recovery plan, justifying the reasons for
inclusion
During disaster organisation conquer with several problems related to their sensitive data and potential
resources which might get lost. At that time, the organisation cannot bear such data loss which can
affect the growth rate of the organisation which necessitates the need of recovering the lost data. By the
help of several recoveries plan organisation can recover the potential resources and information to
sustain the continuity of the business. Following are the components of recovery plan adopted by the
organisation:
Backup: Backup is the term which refers to the second copy of the data and information creation that
can be reloaded at the time of situation where organisation faces the disastrous loss of vital information.
This is done when the access to the primary data get lost. As this taking up of backup created by the
organisation is of great importance to recover the sensitive data in case of disastrous condition
(Snedaker, 2013). Accessing the incremental backup taking process only by considering the space to
save when the previous back up is not covered in the information.
Monitoring: After recovering the backup of the lost data and resources, monitoring and regulating of the
IT systems is required for the security purpose. This monitoring process is essentially required to
prevent the loss of the organisation by determining the possible sources and their possible solution at the
time of disastrous situation. Further this also helps to take decisions on time to minimize the loss at time
of disaster condition.
Redundancy: To manage or handling the data and connectivity between two devices organisation can
the redundant the organisational devices. For ensuring the continuity redundancy delivers the alternative
sources for the communication (Järveläinen, 2013). At the time of disastrous situation when
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



