IT Risk Management Report: IT Security, Models, and Risk Analysis
VerifiedAdded on 2020/02/19
|9
|1317
|106
Report
AI Summary
This report comprehensively addresses IT risk management, emphasizing the protection of data and information within organizations. It examines the evolving IT landscape and the critical importance of data privacy. The report delves into IT security models, particularly the Role-Based Access Control (RBAC) model, explaining its hierarchical structure and its role in managing access and mitigating cyber threats. It also provides an overview of IT threat and risk assessment, categorizing various risks such as human errors, non-human factors, and environmental threats. The report highlights the importance of updated security measures, including firewalls and anti-virus software, in preventing cyberattacks. It concludes by emphasizing the significance of a robust risk management process in maintaining data security and preventing data breaches, which can cause significant financial losses. The report references several academic sources to support its findings.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the Student
Name of the University
Author’s Note
IT Risk Management
Name of the Student
Name of the University
Author’s Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.
IT RISK MANAGEMENT
Executive Summary
This report deals with the UT security and risk assessment of the data and information in the
companies. There are many cases in which the data and information has been recovered by the
companies in the market. The use of the updated firewalls and anti-viruses software helps in
reducing the risks of cyber attacking the server of the company. The proper risk management has
helped in tracking these activities over the Internet and making the company free form the cyber-
attacks. The hackers are restricted ti enter into the security firewall of the server.

2
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................4
IT security and Technology landscape............................................................................................4
IT security models and access controls...........................................................................................5
IT security Threat and risk assessment............................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
IT RISK MANAGEMENT
Table of Contents
Introduction......................................................................................................................................4
IT security and Technology landscape............................................................................................4
IT security models and access controls...........................................................................................5
IT security Threat and risk assessment............................................................................................7
Conclusion.......................................................................................................................................8
References........................................................................................................................................9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
Introduction
The enhancement of the IT operations in the IT industry have enhanced the groeth in the market.
The protection of data and information in the business organization has been an integral part of
the business organization.
This report deals with the IT security models and controls, IT threat and risks management and
IT security landscape.
This report also outlines these three topics for helping in the development of the market. The
different techniques for starting the risk assessment process has been discussed in the report.
IT security and Technology landscape
The maintenance of the data and information of the business organization in the market has been
an important topic in the market. The data and information of the company in the market has
been an important asset for the company (Ackermann, 2012). Therefore, the privacy of the
da6abans information is important for the company. The cyber-insurance of the data and
information has been done by the company to receiver the data incase f any loss due to the cyber-
attacks. The cyber-attacks in the database server causes a huge loss of the data and information
loss in the company (Bojanc, & Jerman-Blažič, 2013). There are different security protocols
installed in the database server of the company that helped in maintaining the security of the data
and information of the company. On the other hand, Rieke et al., (2012) argued that the lost data
and info ration cannot be recovered. The total data and information of the company cannot be
regained. Therefore, the IT security protocols have focused on the maintenance of the data and
information of the company.
IT RISK MANAGEMENT
Introduction
The enhancement of the IT operations in the IT industry have enhanced the groeth in the market.
The protection of data and information in the business organization has been an integral part of
the business organization.
This report deals with the IT security models and controls, IT threat and risks management and
IT security landscape.
This report also outlines these three topics for helping in the development of the market. The
different techniques for starting the risk assessment process has been discussed in the report.
IT security and Technology landscape
The maintenance of the data and information of the business organization in the market has been
an important topic in the market. The data and information of the company in the market has
been an important asset for the company (Ackermann, 2012). Therefore, the privacy of the
da6abans information is important for the company. The cyber-insurance of the data and
information has been done by the company to receiver the data incase f any loss due to the cyber-
attacks. The cyber-attacks in the database server causes a huge loss of the data and information
loss in the company (Bojanc, & Jerman-Blažič, 2013). There are different security protocols
installed in the database server of the company that helped in maintaining the security of the data
and information of the company. On the other hand, Rieke et al., (2012) argued that the lost data
and info ration cannot be recovered. The total data and information of the company cannot be
regained. Therefore, the IT security protocols have focused on the maintenance of the data and
information of the company.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
IT security models and access controls
The various types of access control models has been used in he report that helps in maintaining
the security of the data and information in the company.
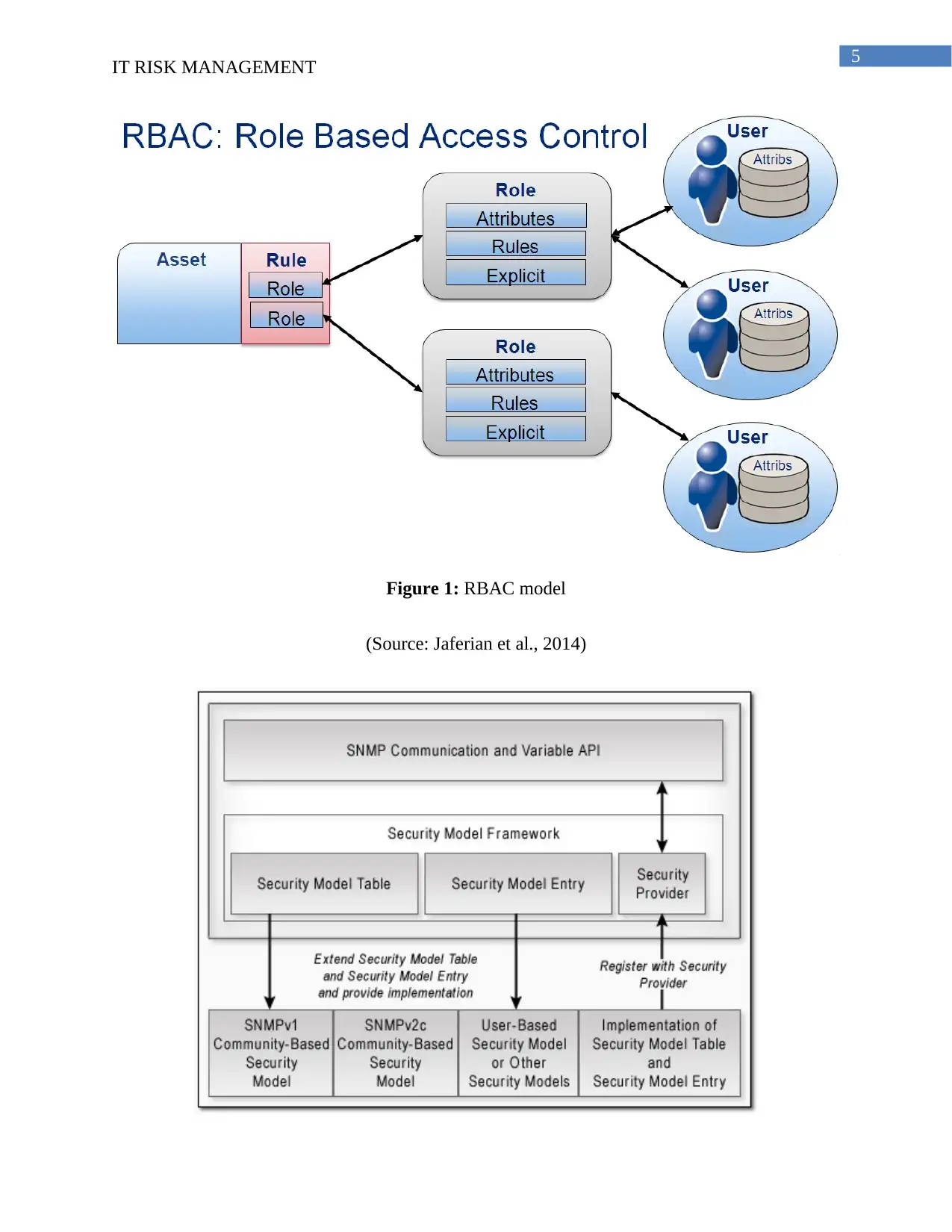
Role-based Access control
The Role-based Control (RBAC) model functions the roles for helping the users in finding their
respective jobs in the server of the company. The model was developed for overcoming the
problems in the administration encountered in the big commercial companies. The main part of
the decision making process is managed by the RBAC model (Jaferian et al., 2014). This model
has a hierarchical concept that helps in analyzing each step of the decision-making process
model. The main role of the RBAC model is to maintaining a systematic approach of analyzing
the data and information of the companying the market. This model relates with the cost benefit
analysis of the company in the market. The data security and privacy has been maintained by the
hierarchical approach of the model. The model helps in maintaining the cyber-attacks and its
prevention policy. On the other hand, Rieke et al., (2012) argued that due to the collection of the
huge data and information, the model is unable ti handle this data and there are gaps in the
security and privacy of the data. Therefore, the hackers can easily penetrate into the cyber the
entire database server of the company. This causes a huge loss of data and information of the
company.
IT RISK MANAGEMENT
IT security models and access controls
The various types of access control models has been used in he report that helps in maintaining
the security of the data and information in the company.
Role-based Access control
The Role-based Control (RBAC) model functions the roles for helping the users in finding their
respective jobs in the server of the company. The model was developed for overcoming the
problems in the administration encountered in the big commercial companies. The main part of
the decision making process is managed by the RBAC model (Jaferian et al., 2014). This model
has a hierarchical concept that helps in analyzing each step of the decision-making process
model. The main role of the RBAC model is to maintaining a systematic approach of analyzing
the data and information of the companying the market. This model relates with the cost benefit
analysis of the company in the market. The data security and privacy has been maintained by the
hierarchical approach of the model. The model helps in maintaining the cyber-attacks and its
prevention policy. On the other hand, Rieke et al., (2012) argued that due to the collection of the
huge data and information, the model is unable ti handle this data and there are gaps in the
security and privacy of the data. Therefore, the hackers can easily penetrate into the cyber the
entire database server of the company. This causes a huge loss of data and information of the
company.
5
IT RISK MANAGEMENT
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
IT RISK MANAGEMENT
Figure 1: RBAC model
(Source: Jaferian et al., 2014)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT RISK MANAGEMENT
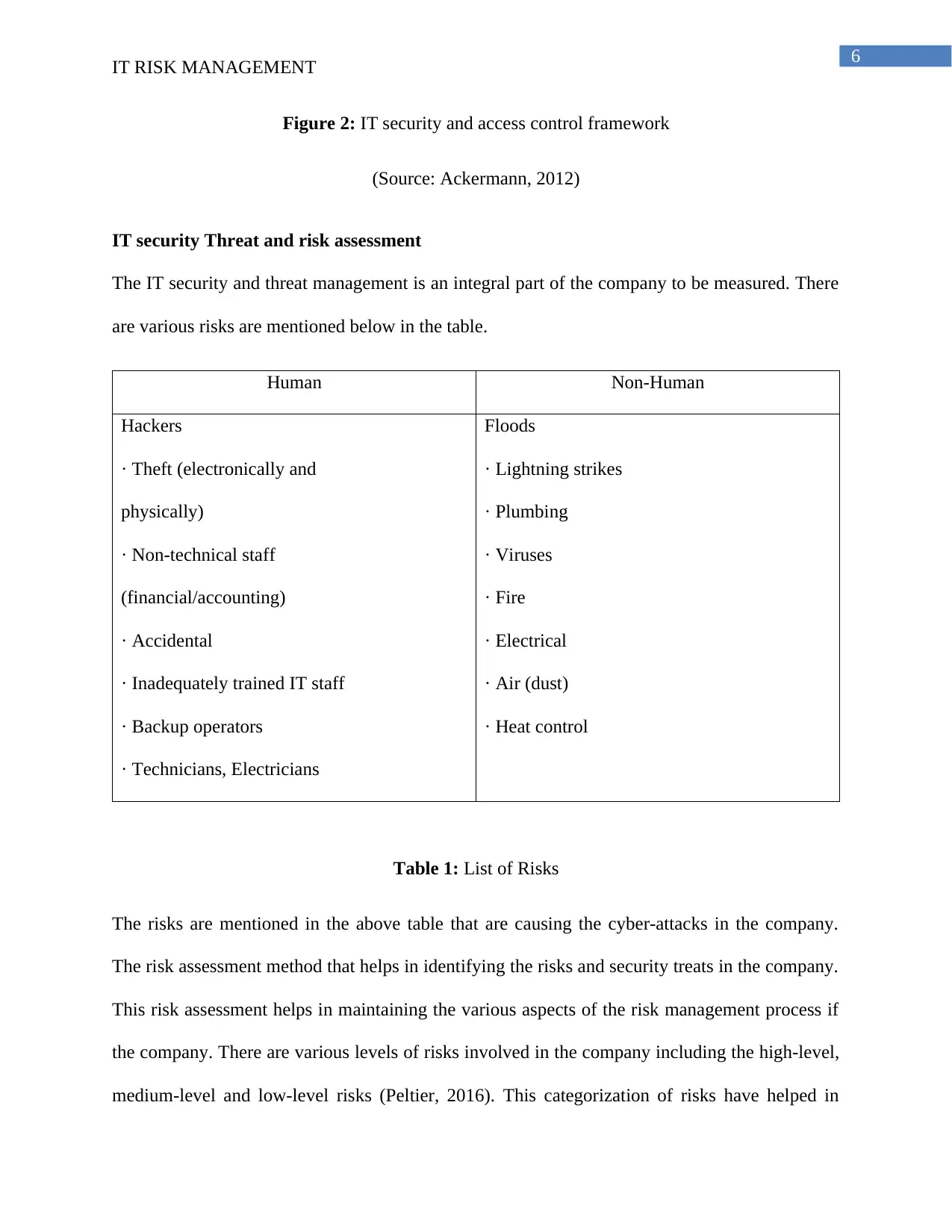
Figure 2: IT security and access control framework
(Source: Ackermann, 2012)
IT security Threat and risk assessment
The IT security and threat management is an integral part of the company to be measured. There
are various risks are mentioned below in the table.
Human Non-Human
Hackers
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
Floods
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
The risks are mentioned in the above table that are causing the cyber-attacks in the company.
The risk assessment method that helps in identifying the risks and security treats in the company.
This risk assessment helps in maintaining the various aspects of the risk management process if
the company. There are various levels of risks involved in the company including the high-level,
medium-level and low-level risks (Peltier, 2016). This categorization of risks have helped in
IT RISK MANAGEMENT
Figure 2: IT security and access control framework
(Source: Ackermann, 2012)
IT security Threat and risk assessment
The IT security and threat management is an integral part of the company to be measured. There
are various risks are mentioned below in the table.
Human Non-Human
Hackers
· Theft (electronically and
physically)
· Non-technical staff
(financial/accounting)
· Accidental
· Inadequately trained IT staff
· Backup operators
· Technicians, Electricians
Floods
· Lightning strikes
· Plumbing
· Viruses
· Fire
· Electrical
· Air (dust)
· Heat control
Table 1: List of Risks
The risks are mentioned in the above table that are causing the cyber-attacks in the company.
The risk assessment method that helps in identifying the risks and security treats in the company.
This risk assessment helps in maintaining the various aspects of the risk management process if
the company. There are various levels of risks involved in the company including the high-level,
medium-level and low-level risks (Peltier, 2016). This categorization of risks have helped in
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
IT RISK MANAGEMENT
analyzing the severity of the risks in the company. The vulnerability of the risks in the company
can be measured with the help of risk assessment method. There are various methods to control
the cyber-attacks in the company. The use of the updated firewalls and anti-viruses software
helps in restricting the viruses and malwares form entering into the databases of the company.
The unauthorized users are blocked from entering into the firewall of the database of the
company (Vacca, 2012). A proper risk management process helps in maintaining the security of
the data and information of the company over the interest. The hackers are restricted from
entering the firewall and databases of the company.
Conclusion
It can be concluded that the use of the risk management process in the company helps in
mitigating with the risks involved in the company. The cyber security is an integral part of the
company for securing data and information. The data breach causes a huge loss to the company
in the market. The RBAC model has helped in maintaining the hierarchical order to analysis the
security level of the data and information in the company.
IT RISK MANAGEMENT
analyzing the severity of the risks in the company. The vulnerability of the risks in the company
can be measured with the help of risk assessment method. There are various methods to control
the cyber-attacks in the company. The use of the updated firewalls and anti-viruses software
helps in restricting the viruses and malwares form entering into the databases of the company.
The unauthorized users are blocked from entering into the firewall of the database of the
company (Vacca, 2012). A proper risk management process helps in maintaining the security of
the data and information of the company over the interest. The hackers are restricted from
entering the firewall and databases of the company.
Conclusion
It can be concluded that the use of the risk management process in the company helps in
mitigating with the risks involved in the company. The cyber security is an integral part of the
company for securing data and information. The data breach causes a huge loss to the company
in the market. The RBAC model has helped in maintaining the hierarchical order to analysis the
security level of the data and information in the company.

8
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
IT RISK MANAGEMENT
References
Ackermann, T. (2012). IT security risk management: perceived IT security risks in the context of
Cloud Computing. Springer Science & Business Media.
Bojanc, R., & Jerman-Blažič, B. (2013). A quantitative model for information-security risk
management. Engineering Management Journal, 25(2), 25-37.
Jaferian, P., Hawkey, K., Sotirakopoulos, A., Velez-Rojas, M., & Beznosov, K. (2014).
Heuristics for evaluating IT security management tools. Human–Computer Interaction,
29(4), 311-350.
Peltier, T. R. (2016). Information Security Policies, Procedures, and Standards: guidelines for
effective information security management. CRC Press.
Rieke, R., Coppolino, L., Hutchison, A., Prieto, E., & Gaber, C. (2012, October). Security and
Reliability Requirements for Advanced Security Event Management. In MMM-ACNS
(pp. 171-180).
Vacca, J. R. (2012). Computer and information security handbook. Newnes.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





