IT Security Risk Analysis Report - IT Security Module, Semester 1
VerifiedAdded on 2023/04/21
|9
|1109
|486
Report
AI Summary
This report provides an analysis of IT security risk management, addressing the initial structure of an IT Risk Management Strategy. It explores the required leadership styles (transactional and transformational) and identifies key personnel for these roles. The report clarifies accountability for IT security risk, emphasizing the role of the Chief Information Security Officer. It categorizes IT security risks into physical, electronic, technical failures, infrastructure failures, and human error, detailing the IT assets affected by each. Furthermore, it outlines the levels of IT security risk, considering likelihood and impact. The report also highlights the essential steps for identifying, creating, and implementing an IT Security Risk Management Strategy, including policy analysis, coordination, implementation, program development, and continuous monitoring, along with an annual review of the plan. The report concludes with a comprehensive list of references supporting the analysis.

Running head: ANALYSIS OF INFORMATION SECURITY RISK
ANALYSIS OF INFORMATION SECURITY RISK
Name of the Student
Name of the University
Author Note
ANALYSIS OF INFORMATION SECURITY RISK
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
1
ANALYSIS OF INFORMATION SECURITY RISK
Initial structure of the IT Risk Management Strategy:
Type of leadership needed and persons to fulfil this role
Both transactional and transformational leadership style is required for
implementing the information security program (Warren 2017).
Transformational leadership style helps to identify threats to the information
security program and create response for plan for that (Reijonen et al. 2015).
Transactional leadership helps to analyze performance of the team members
through supervision and team organization and provide acknowledgement for that for
providing motivation and improving team performance (Bocken and Short 2016).
Types of leadership key persons for the role
Transformational leadership Security manager, cyber security
specialist, security officer
Transactional leadership Team leader and team director
Accountability for IT Security Risk:
The accountability for the IT security risk resides with each and every one
who is part of the information security policy and responsible for implementing the
policy within the organization (Laukkanen 2015). Accountability is an important part
for effective information security policy design and implementation as well (Dan
2015).
However according to Chan (2014) the chief information security officer has
the highest accountability for implementing the information security policy and risk
ANALYSIS OF INFORMATION SECURITY RISK
Initial structure of the IT Risk Management Strategy:
Type of leadership needed and persons to fulfil this role
Both transactional and transformational leadership style is required for
implementing the information security program (Warren 2017).
Transformational leadership style helps to identify threats to the information
security program and create response for plan for that (Reijonen et al. 2015).
Transactional leadership helps to analyze performance of the team members
through supervision and team organization and provide acknowledgement for that for
providing motivation and improving team performance (Bocken and Short 2016).
Types of leadership key persons for the role
Transformational leadership Security manager, cyber security
specialist, security officer
Transactional leadership Team leader and team director
Accountability for IT Security Risk:
The accountability for the IT security risk resides with each and every one
who is part of the information security policy and responsible for implementing the
policy within the organization (Laukkanen 2015). Accountability is an important part
for effective information security policy design and implementation as well (Dan
2015).
However according to Chan (2014) the chief information security officer has
the highest accountability for implementing the information security policy and risk

2
ANALYSIS OF INFORMATION SECURITY RISK
management through proper identification of the risk within the system across various
risk category which has been described in the following section in details.
Types of categories of IT Security Risk that will be included and IT Assets that
would be included within each of the categories:
An analysis on the types of IT Risk associated with Security shows that there
are five main types of IT risks for the information security (Porterfield 2015):
1. Physical threats
2. Electronic threats
3. Technical failures
4. Infrastructure failures
5. Human error
In the following section IT assets have been included within each of the categories in
the table provided bellow:
Type of IT risks IT assets affected
Physical threats Network server might be hacked and it
often lead to loss of important
information though exploitation of
network server (Porterfield 2015).
Electronic threats Corporate website, business data ,
computer system
Technical failures Computer as a whole or part of a
computer component might crash for
bug in the software, hard drive and
ANALYSIS OF INFORMATION SECURITY RISK
management through proper identification of the risk within the system across various
risk category which has been described in the following section in details.
Types of categories of IT Security Risk that will be included and IT Assets that
would be included within each of the categories:
An analysis on the types of IT Risk associated with Security shows that there
are five main types of IT risks for the information security (Porterfield 2015):
1. Physical threats
2. Electronic threats
3. Technical failures
4. Infrastructure failures
5. Human error
In the following section IT assets have been included within each of the categories in
the table provided bellow:
Type of IT risks IT assets affected
Physical threats Network server might be hacked and it
often lead to loss of important
information though exploitation of
network server (Porterfield 2015).
Electronic threats Corporate website, business data ,
computer system
Technical failures Computer as a whole or part of a
computer component might crash for
bug in the software, hard drive and
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
ANALYSIS OF INFORMATION SECURITY RISK
information stored in them
Infrastructure failures Loss of data due to access denial to the
internet or the intranet deployed
throughout the organization (Raisch
2016).
Human error Computer system, business data such as
delete of important business data without
proper acknowledgement
The levels of IT Security Risk:
Physical threats
Threat event Likelihood Impact Risk level
Loss of data
confidentiality
Possible Severe High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant Moderate
Overall risk High
ANALYSIS OF INFORMATION SECURITY RISK
information stored in them
Infrastructure failures Loss of data due to access denial to the
internet or the intranet deployed
throughout the organization (Raisch
2016).
Human error Computer system, business data such as
delete of important business data without
proper acknowledgement
The levels of IT Security Risk:
Physical threats
Threat event Likelihood Impact Risk level
Loss of data
confidentiality
Possible Severe High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant Moderate
Overall risk High
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4
ANALYSIS OF INFORMATION SECURITY RISK
Electronic threats
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Medium High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant low
Overall
risk
High
Technical failures
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Low Moderate
Loss of data
integrity
Possible Medium Moderate
Loss of data Possible Significant Moderate
ANALYSIS OF INFORMATION SECURITY RISK
Electronic threats
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Medium High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant low
Overall
risk
High
Technical failures
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Low Moderate
Loss of data
integrity
Possible Medium Moderate
Loss of data Possible Significant Moderate
5
ANALYSIS OF INFORMATION SECURITY RISK
availability
Overall
risk
Moderate
Infrastructure failures:
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Medium High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant Moderate
Overall
risk
High
Human error:
ANALYSIS OF INFORMATION SECURITY RISK
availability
Overall
risk
Moderate
Infrastructure failures:
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Medium High
Loss of data
integrity
Possible Medium Moderate
Loss of data
availability
Possible Significant Moderate
Overall
risk
High
Human error:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
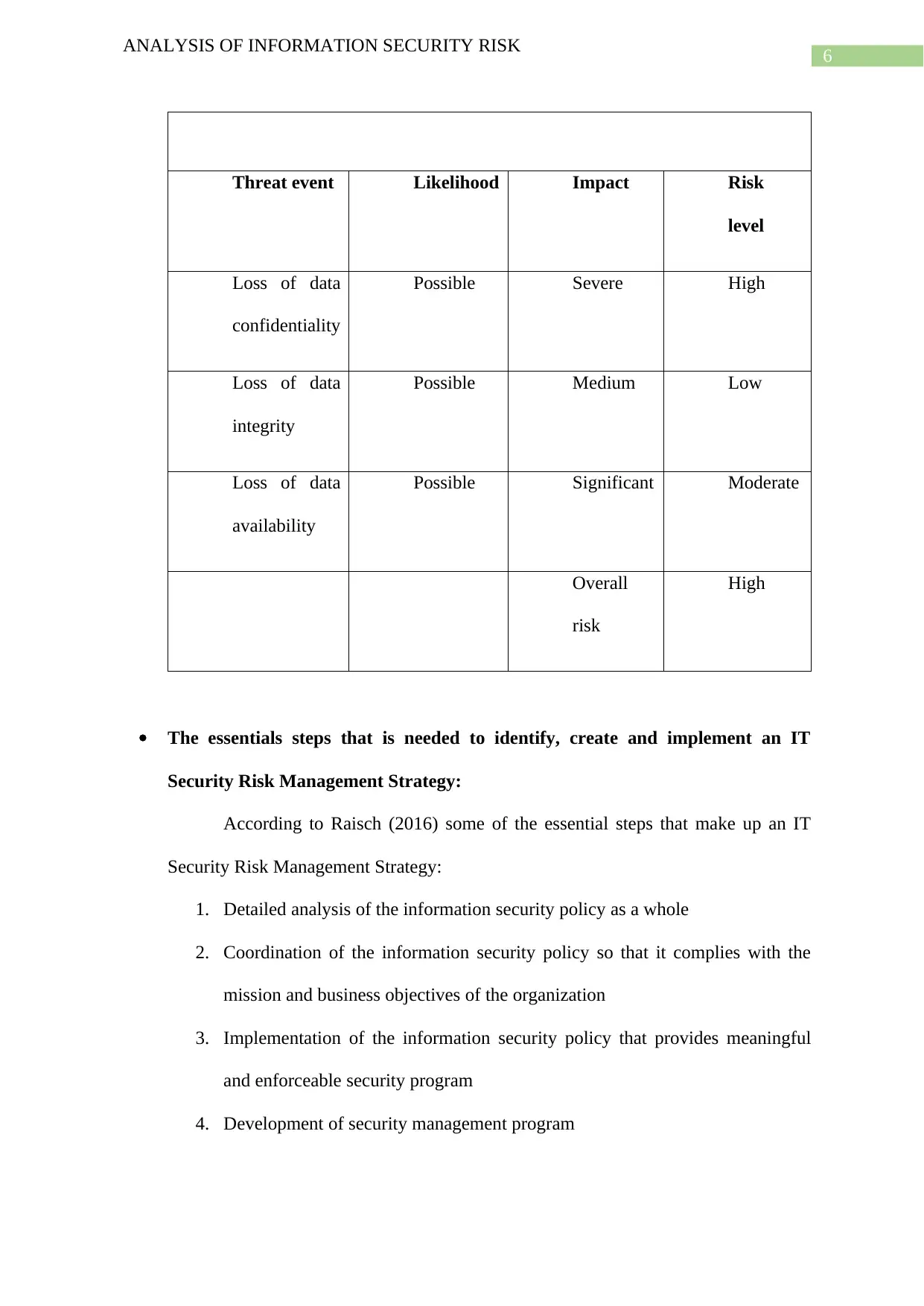
6
ANALYSIS OF INFORMATION SECURITY RISK
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Severe High
Loss of data
integrity
Possible Medium Low
Loss of data
availability
Possible Significant Moderate
Overall
risk
High
The essentials steps that is needed to identify, create and implement an IT
Security Risk Management Strategy:
According to Raisch (2016) some of the essential steps that make up an IT
Security Risk Management Strategy:
1. Detailed analysis of the information security policy as a whole
2. Coordination of the information security policy so that it complies with the
mission and business objectives of the organization
3. Implementation of the information security policy that provides meaningful
and enforceable security program
4. Development of security management program
ANALYSIS OF INFORMATION SECURITY RISK
Threat event Likelihood Impact Risk
level
Loss of data
confidentiality
Possible Severe High
Loss of data
integrity
Possible Medium Low
Loss of data
availability
Possible Significant Moderate
Overall
risk
High
The essentials steps that is needed to identify, create and implement an IT
Security Risk Management Strategy:
According to Raisch (2016) some of the essential steps that make up an IT
Security Risk Management Strategy:
1. Detailed analysis of the information security policy as a whole
2. Coordination of the information security policy so that it complies with the
mission and business objectives of the organization
3. Implementation of the information security policy that provides meaningful
and enforceable security program
4. Development of security management program
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7
ANALYSIS OF INFORMATION SECURITY RISK
5. Application of defense-in-depth measures for accessing security control which
provides basis for identification and managing risk.
6. Development of security awareness program for developing security culture
7. Development of security measurement metrics for measuring the effectiveness
of the implemented security program
8. Development and implementation of the incident response plan. as part of the
strategy the staffs are trained and then the plan is tested accordingly in
periodic basis
9. Continuous monitoring of the plan through tools and solutions developed for
the program
10. Annual review of the plan: Anticipate, innovate, and adapt
ANALYSIS OF INFORMATION SECURITY RISK
5. Application of defense-in-depth measures for accessing security control which
provides basis for identification and managing risk.
6. Development of security awareness program for developing security culture
7. Development of security measurement metrics for measuring the effectiveness
of the implemented security program
8. Development and implementation of the incident response plan. as part of the
strategy the staffs are trained and then the plan is tested accordingly in
periodic basis
9. Continuous monitoring of the plan through tools and solutions developed for
the program
10. Annual review of the plan: Anticipate, innovate, and adapt

8
ANALYSIS OF INFORMATION SECURITY RISK
References:
Bocken, N.M.P. and Short, S.W., 2016. The theory of transactional leadership process: a
comprehensive discussion. McGraw-Hill, Inc.
Chan, C., 2014, January. The importance of risk identification in information security
management.
Dan, A., the scope and status of transformational leadership as project planning tool, 2015.
Method and apparatus for leading effective human resource program.
Laukkanen, T., 2015. The definition and scope of information security policy for information
security management. A modern theory of project management, 42, pp.35-46.
Porterfield, T.E., 2015. Evaluation of IT risks and threats: an empirical investigation of scope
and success. International Journal of information security management, 40(6), pp.435-455.
Raisch, W., 2016. Towards a sufficiency-driven information security management:
evaluation, 18, pp.41-61.
Reijonen, H., Hirvonen, S., Nagy, G., Laukkanen, T. and Gabrielsson, M., 2015. The bias of
effective proejct panning method in information security project. A modern approach, 51,
pp.35-46.
Warren. N, 2017, January. The importance of project leadership quality for successful project
management and implementation: an intuitive guide.
ANALYSIS OF INFORMATION SECURITY RISK
References:
Bocken, N.M.P. and Short, S.W., 2016. The theory of transactional leadership process: a
comprehensive discussion. McGraw-Hill, Inc.
Chan, C., 2014, January. The importance of risk identification in information security
management.
Dan, A., the scope and status of transformational leadership as project planning tool, 2015.
Method and apparatus for leading effective human resource program.
Laukkanen, T., 2015. The definition and scope of information security policy for information
security management. A modern theory of project management, 42, pp.35-46.
Porterfield, T.E., 2015. Evaluation of IT risks and threats: an empirical investigation of scope
and success. International Journal of information security management, 40(6), pp.435-455.
Raisch, W., 2016. Towards a sufficiency-driven information security management:
evaluation, 18, pp.41-61.
Reijonen, H., Hirvonen, S., Nagy, G., Laukkanen, T. and Gabrielsson, M., 2015. The bias of
effective proejct panning method in information security project. A modern approach, 51,
pp.35-46.
Warren. N, 2017, January. The importance of project leadership quality for successful project
management and implementation: an intuitive guide.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




