HNC Computing - Unit 5: Security Risks and Risk Management Report
VerifiedAdded on 2022/08/26
|11
|781
|13
Report
AI Summary
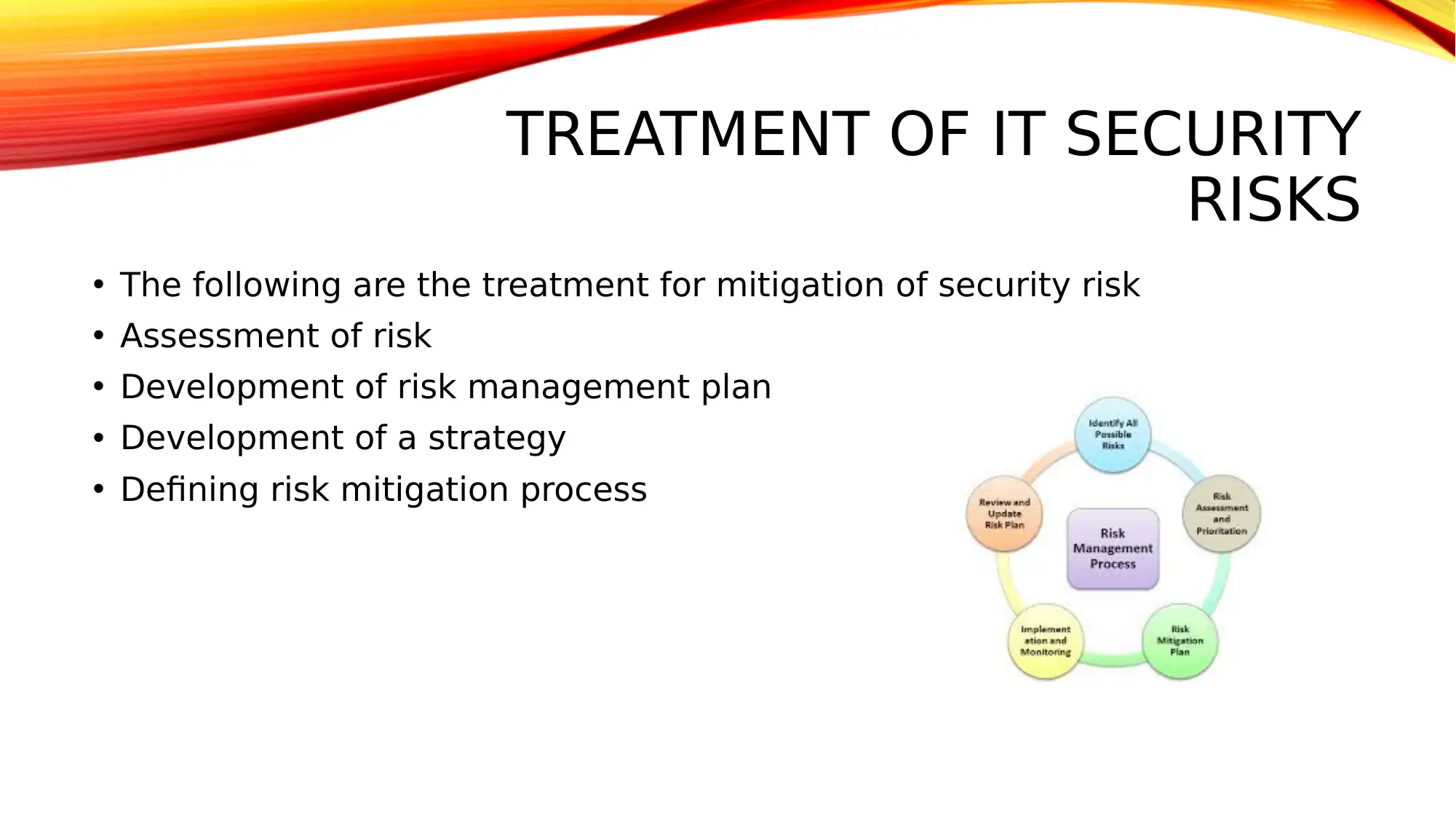
This report provides an overview of IT security risks and risk management strategies. It begins with an introduction to security systems, highlighting the importance of network security and the role of firewalls, DMZ zones, static IPs, and NAT in preventing attacks. The report then details various types of security risks, including computer viruses, rogue software, Trojan horses, adware, spyware, computer worms, DOS/DDOS attacks, phishing, rootkits, SQL injection attacks, and man-in-the-middle attacks. Each risk is described in detail, explaining its potential impact on an organization. The report further outlines organizational security procedures, such as authorization of security roles, user behavior expectations, and business continuity plans. It also discusses risk assessment methods, including asset listing, consequence identification, threat identification, vulnerability assessment, and risk treatment. Finally, the report covers the treatment for IT security risks, including risk assessment, the development of a risk management plan and strategy, and defining risk mitigation processes. The report concludes by emphasizing the importance of proactive security measures and offers insights into improving network security through various techniques. The bibliography provides a list of relevant research papers on the topic.
1 out of 11
















![[object Object]](/_next/static/media/star-bottom.7253800d.svg)