IT Risk Management Report: Risks and Mitigation in VIC Government
VerifiedAdded on 2020/03/04
|19
|3163
|41
Report
AI Summary
This report examines IT risk management within the Victorian government, focusing on the establishment of a monitoring system to secure confidential information. The introduction highlights the government's objectives, including identifying information ownership, assessing information value, managing data security risks, and fostering a positive security culture. The report identifies current security risks across various domains such as governance, information, personnel, and ICT. It provides a comparison between deliberate and accidental threats, outlining the challenges faced by the government in managing information security, including issues with information value, security framework application, and incident management. The report differentiates between risks and uncertainty, detailing approaches for risk control and mitigation through a security management framework, security policies, access management, security obligations, training, incident management, business continuity, contracted service providers, government services, and security plans. The report emphasizes the importance of proactive measures to protect sensitive data and ensure the effective functioning of the government.
IT Risk Management
2017
2017
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management
Contents
Introduction:..........................................................................................................................................4
Current security risks in the VIC government:......................................................................................4
1
Contents
Introduction:..........................................................................................................................................4
Current security risks in the VIC government:......................................................................................4
1
IT Risk Management
....5
Identification of the areas of risks exposure:.........................................................................................6
Comparison between Deliberate and accidental threats exposure:.........................................................6
2
Risk Associated
with the current
working of the
victorian
government
Policies and
operational
responsibilities
Understanding
of the
information
values
Security
culture and
monitoring
system
Cost associated
with the
project
Security in
Governance
Security of
information
Security of
Personal
ICT security
Physical
infrastructure
security
....5
Identification of the areas of risks exposure:.........................................................................................6
Comparison between Deliberate and accidental threats exposure:.........................................................6
2
Risk Associated
with the current
working of the
victorian
government
Policies and
operational
responsibilities
Understanding
of the
information
values
Security
culture and
monitoring
system
Cost associated
with the
project
Security in
Governance
Security of
information
Security of
Personal
ICT security
Physical
infrastructure
security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

IT Risk Management
Challenges faced by the VIC government:............................................................................................7
Difference between risks and uncertainty:.............................................................................................7
Approaches for risk control and mitigation:..........................................................................................8
Conclusion:..........................................................................................................................................16
References...........................................................................................................................................17
3
Challenges faced by the VIC government:............................................................................................7
Difference between risks and uncertainty:.............................................................................................7
Approaches for risk control and mitigation:..........................................................................................8
Conclusion:..........................................................................................................................................16
References...........................................................................................................................................17
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management
Introduction:
The Victorian government wants to establish a monitoring system to provide security to the
confidential information. The objective is to determine the ownership for identifying the
information, assessment of the information value, identification and management of the data
security risks, application of the security measures, creating the positive organization culture
for imposing security, and increasing the methods for providing data security. “The company
is working hard to provide the assurance actions for mitigating from the associated security
risks” (Venkatesh, 2015). The Victorian government requires a protective security policy
framework to enhance the working of the government in national interest. The information
security procedures should be created to cope up with the new threats, updated threats, and
the occurrence of vulnerabilities. The management of the information helps in overcoming
the problem seen in the disruption occurs in the business objectives. The positive security
culture in the organization helps in the deployment of continuous improvement plan which
helps in enhancing the functions performed by the Victorian government for the betterment
of the nation. “The application of the Victorian government depends on the value of the
information” (Lebanidze, 2014)). The proper security procedures should be indulge to create
the positive information value for the good will of the nation.
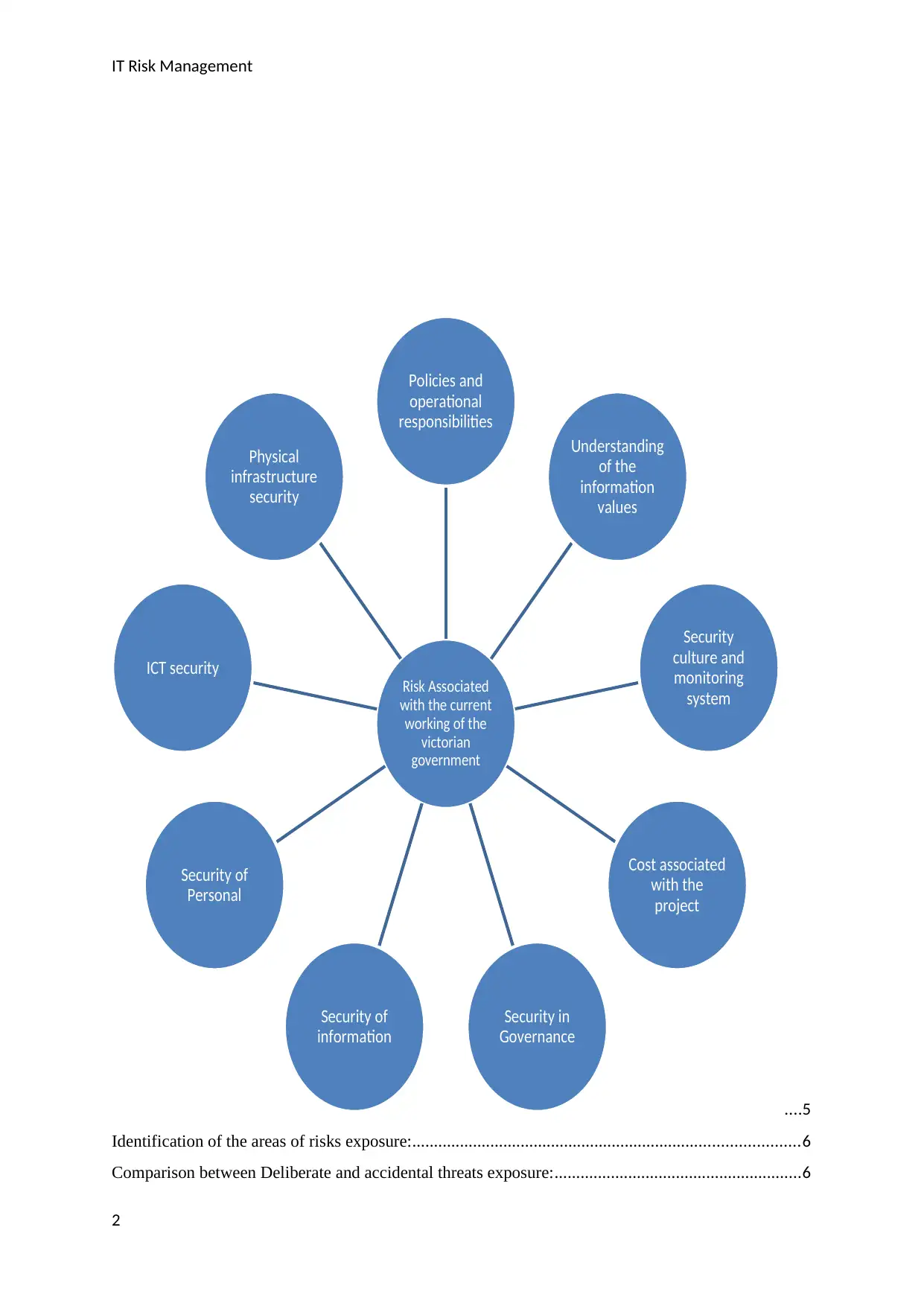
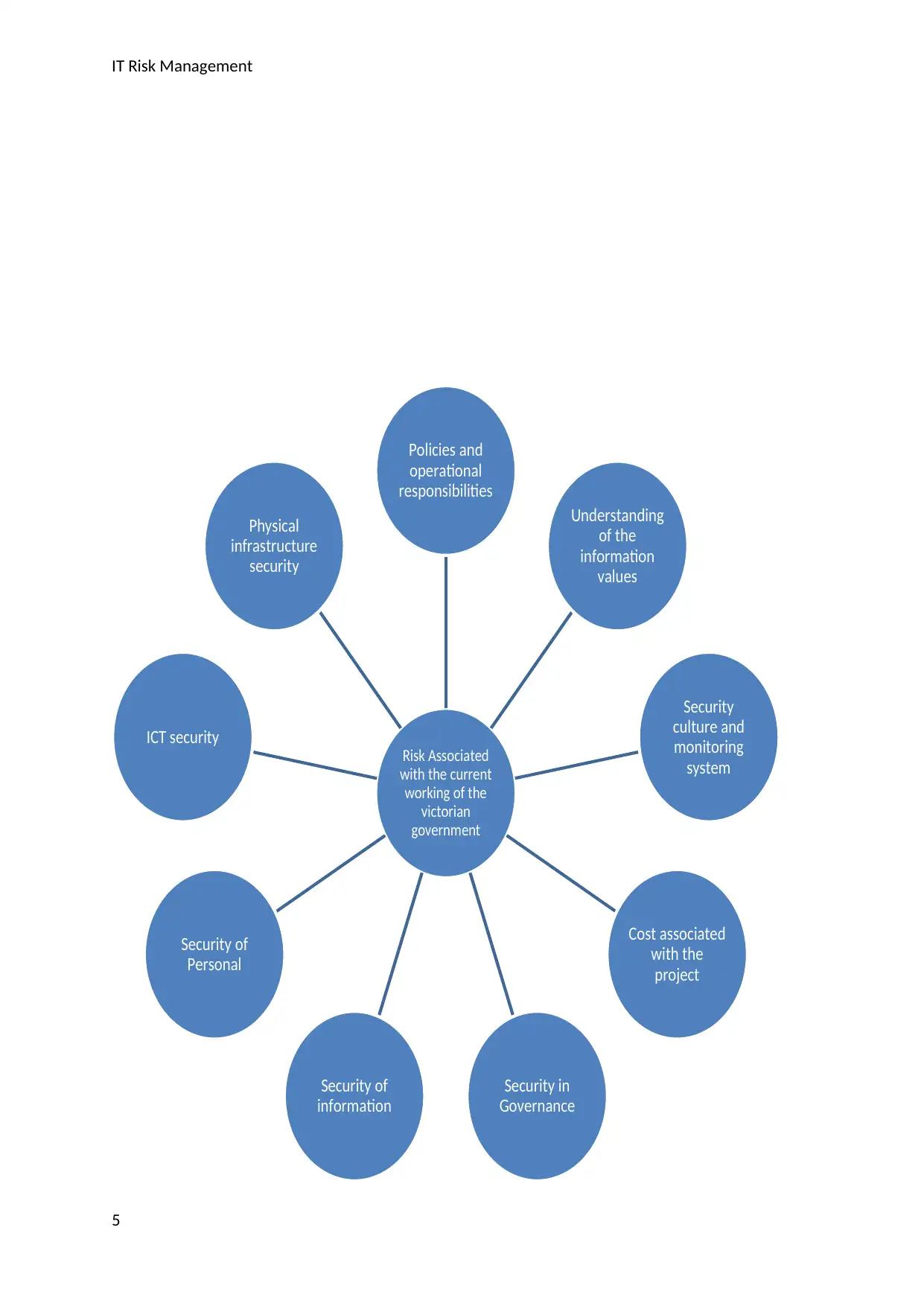
Current security risks in the VIC government:
“The analysis of the risks associated with the working of the government helps in enhancing
the decision making capability and providing priority to the security efforts which are
undertaken by the government” (Brezeanu, 2011). The government is working in the
direction to protect the domains which are named as security to governance, security to
information, security to personnel, security to information and communication technology,
and provides physical security. The current working of the Victorian government is equipped
with the risks equipped in the information sharing, assessment of information, management
of information, inclusion of personal life cycle, security plans, business continuity plan, and
information values.
4
Introduction:
The Victorian government wants to establish a monitoring system to provide security to the
confidential information. The objective is to determine the ownership for identifying the
information, assessment of the information value, identification and management of the data
security risks, application of the security measures, creating the positive organization culture
for imposing security, and increasing the methods for providing data security. “The company
is working hard to provide the assurance actions for mitigating from the associated security
risks” (Venkatesh, 2015). The Victorian government requires a protective security policy
framework to enhance the working of the government in national interest. The information
security procedures should be created to cope up with the new threats, updated threats, and
the occurrence of vulnerabilities. The management of the information helps in overcoming
the problem seen in the disruption occurs in the business objectives. The positive security
culture in the organization helps in the deployment of continuous improvement plan which
helps in enhancing the functions performed by the Victorian government for the betterment
of the nation. “The application of the Victorian government depends on the value of the
information” (Lebanidze, 2014)). The proper security procedures should be indulge to create
the positive information value for the good will of the nation.
Current security risks in the VIC government:
“The analysis of the risks associated with the working of the government helps in enhancing
the decision making capability and providing priority to the security efforts which are
undertaken by the government” (Brezeanu, 2011). The government is working in the
direction to protect the domains which are named as security to governance, security to
information, security to personnel, security to information and communication technology,
and provides physical security. The current working of the Victorian government is equipped
with the risks equipped in the information sharing, assessment of information, management
of information, inclusion of personal life cycle, security plans, business continuity plan, and
information values.
4
IT Risk Management
5
Risk Associated
with the current
working of the
victorian
government
Policies and
operational
responsibilities
Understanding
of the
information
values
Security
culture and
monitoring
system
Cost associated
with the
project
Security in
Governance
Security of
information
Security of
Personal
ICT security
Physical
infrastructure
security
5
Risk Associated
with the current
working of the
victorian
government
Policies and
operational
responsibilities
Understanding
of the
information
values
Security
culture and
monitoring
system
Cost associated
with the
project
Security in
Governance
Security of
information
Security of
Personal
ICT security
Physical
infrastructure
security
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Risk Management
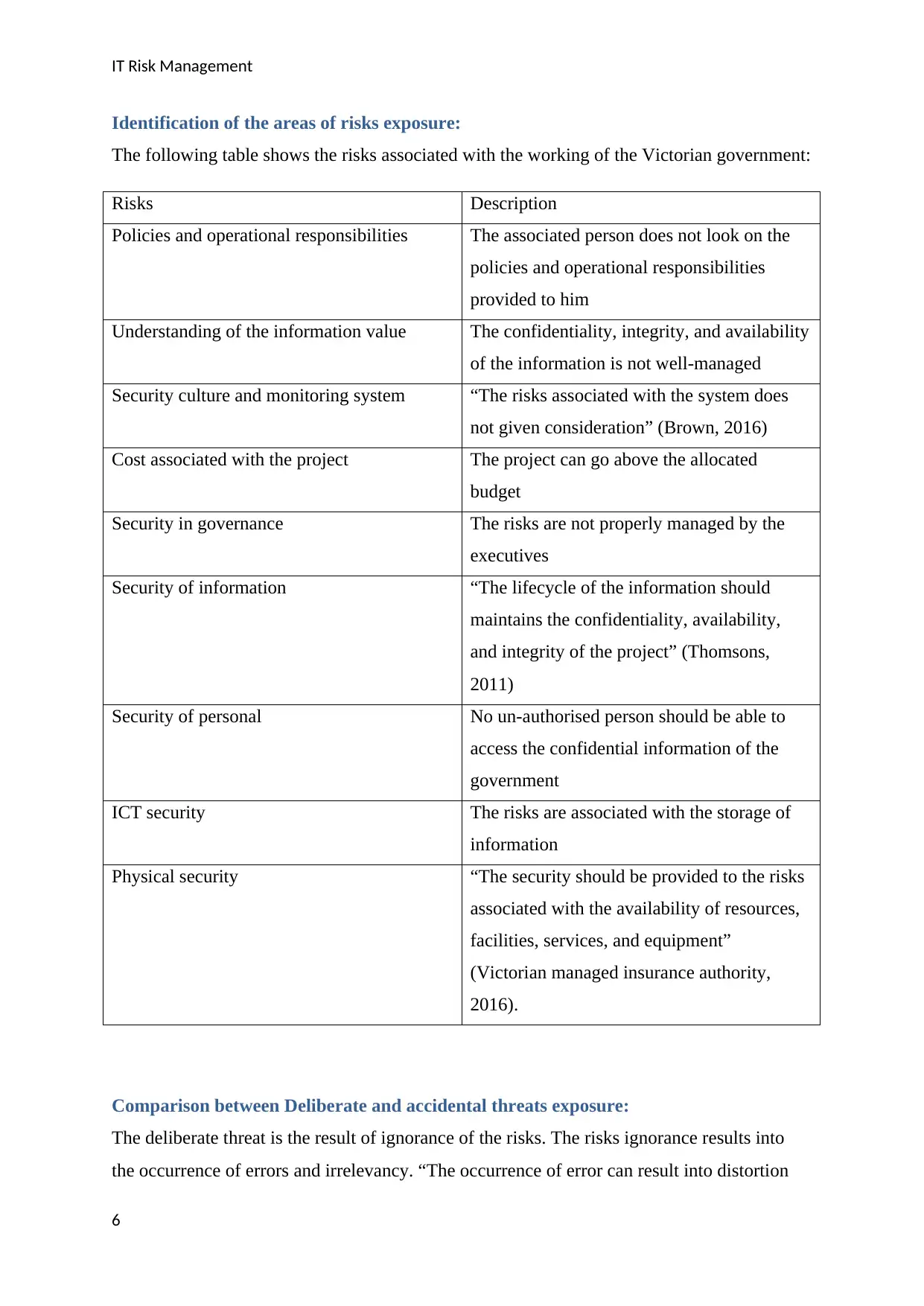
Identification of the areas of risks exposure:
The following table shows the risks associated with the working of the Victorian government:
Risks Description
Policies and operational responsibilities The associated person does not look on the
policies and operational responsibilities
provided to him
Understanding of the information value The confidentiality, integrity, and availability
of the information is not well-managed
Security culture and monitoring system “The risks associated with the system does
not given consideration” (Brown, 2016)
Cost associated with the project The project can go above the allocated
budget
Security in governance The risks are not properly managed by the
executives
Security of information “The lifecycle of the information should
maintains the confidentiality, availability,
and integrity of the project” (Thomsons,
2011)
Security of personal No un-authorised person should be able to
access the confidential information of the
government
ICT security The risks are associated with the storage of
information
Physical security “The security should be provided to the risks
associated with the availability of resources,
facilities, services, and equipment”
(Victorian managed insurance authority,
2016).
Comparison between Deliberate and accidental threats exposure:
The deliberate threat is the result of ignorance of the risks. The risks ignorance results into
the occurrence of errors and irrelevancy. “The occurrence of error can result into distortion
6
Identification of the areas of risks exposure:
The following table shows the risks associated with the working of the Victorian government:
Risks Description
Policies and operational responsibilities The associated person does not look on the
policies and operational responsibilities
provided to him
Understanding of the information value The confidentiality, integrity, and availability
of the information is not well-managed
Security culture and monitoring system “The risks associated with the system does
not given consideration” (Brown, 2016)
Cost associated with the project The project can go above the allocated
budget
Security in governance The risks are not properly managed by the
executives
Security of information “The lifecycle of the information should
maintains the confidentiality, availability,
and integrity of the project” (Thomsons,
2011)
Security of personal No un-authorised person should be able to
access the confidential information of the
government
ICT security The risks are associated with the storage of
information
Physical security “The security should be provided to the risks
associated with the availability of resources,
facilities, services, and equipment”
(Victorian managed insurance authority,
2016).
Comparison between Deliberate and accidental threats exposure:
The deliberate threat is the result of ignorance of the risks. The risks ignorance results into
the occurrence of errors and irrelevancy. “The occurrence of error can result into distortion
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

IT Risk Management
and incompleteness of deploying the security framework in the working culture of the
Victorian government” (Perkins, 2014). The major impact of ignorance can be seen in the
working of the Victorian government to take initatives for securing the information in terms
of confusion, uncertainty, inaccuracy, unavailability, loss of confidential information, and
fuzziness.
“The accidental threats are not known in advance. They can occur by chance” (Wuest, 2013).
The complete working of the Victorian government can get affected with the exposure of
accidental threats because the government is not proactive to face such a situation which can
change the current scenario of the government. “The accidental threats can be categorised as
non-availability of resources, flow of communication breakdown, and etc.” (Stoneburner,
2014).
Challenges faced by the VIC government:
In managing the security of the information, the Victorian government has to face many
challenges and have to developed many mitigation programs to cope up with the challenges
and issues in managing confidentiality and integrity of the information. The Victorian
government facing problems in managing value of the information, in the application of the
security framework, selecting and certifying security measures which should be specified for
developing the framework, management of response associated with the security incident,
monitoring and reviewing of implementing security framework, updating of security working
programs, reflecting changing in the business operations, conducting external monitoring of
activities, and others.
Difference between risks and uncertainty:
“The risks can be defined as the probability of losing or gaining something in carrying out the
procedures of the Victorian government” (Bansal, 2013). The uncertainty can be defined as
the situation arises when the Victorian government have to take instant steps to face the
situation for the betterment of the nation. The situation is not known before its existence.
“The risks associated with the securing the information of the Victorian government can be
identified and managed” (Bemile, 2012). The risks associated with the project can be
measured. The uncertainty arises for managing the information of the Victorian government
to prevent its confidentiality, integrity, and availability. The uncertainty cannot be measured
before its occurrence. The outcome of the risks identification and management process is
7
and incompleteness of deploying the security framework in the working culture of the
Victorian government” (Perkins, 2014). The major impact of ignorance can be seen in the
working of the Victorian government to take initatives for securing the information in terms
of confusion, uncertainty, inaccuracy, unavailability, loss of confidential information, and
fuzziness.
“The accidental threats are not known in advance. They can occur by chance” (Wuest, 2013).
The complete working of the Victorian government can get affected with the exposure of
accidental threats because the government is not proactive to face such a situation which can
change the current scenario of the government. “The accidental threats can be categorised as
non-availability of resources, flow of communication breakdown, and etc.” (Stoneburner,
2014).
Challenges faced by the VIC government:
In managing the security of the information, the Victorian government has to face many
challenges and have to developed many mitigation programs to cope up with the challenges
and issues in managing confidentiality and integrity of the information. The Victorian
government facing problems in managing value of the information, in the application of the
security framework, selecting and certifying security measures which should be specified for
developing the framework, management of response associated with the security incident,
monitoring and reviewing of implementing security framework, updating of security working
programs, reflecting changing in the business operations, conducting external monitoring of
activities, and others.
Difference between risks and uncertainty:
“The risks can be defined as the probability of losing or gaining something in carrying out the
procedures of the Victorian government” (Bansal, 2013). The uncertainty can be defined as
the situation arises when the Victorian government have to take instant steps to face the
situation for the betterment of the nation. The situation is not known before its existence.
“The risks associated with the securing the information of the Victorian government can be
identified and managed” (Bemile, 2012). The risks associated with the project can be
measured. The uncertainty arises for managing the information of the Victorian government
to prevent its confidentiality, integrity, and availability. The uncertainty cannot be measured
before its occurrence. The outcome of the risks identification and management process is
7
IT Risk Management
known before its existence whereas the outcome of the uncertainty cannot be predicted before
its existence. The risks can be minimized by deploying the risks mitigation policies but the
uncertainty cannot be reduced because it is an instant action. The probabilities of risks
occurrence can be assigned but the probabilities of uncertainty cannot be predicted. The
priority of risks management can be assigned with the prediction of the risks but the same is
not applicable for uncertainty because it is uncontrollable.
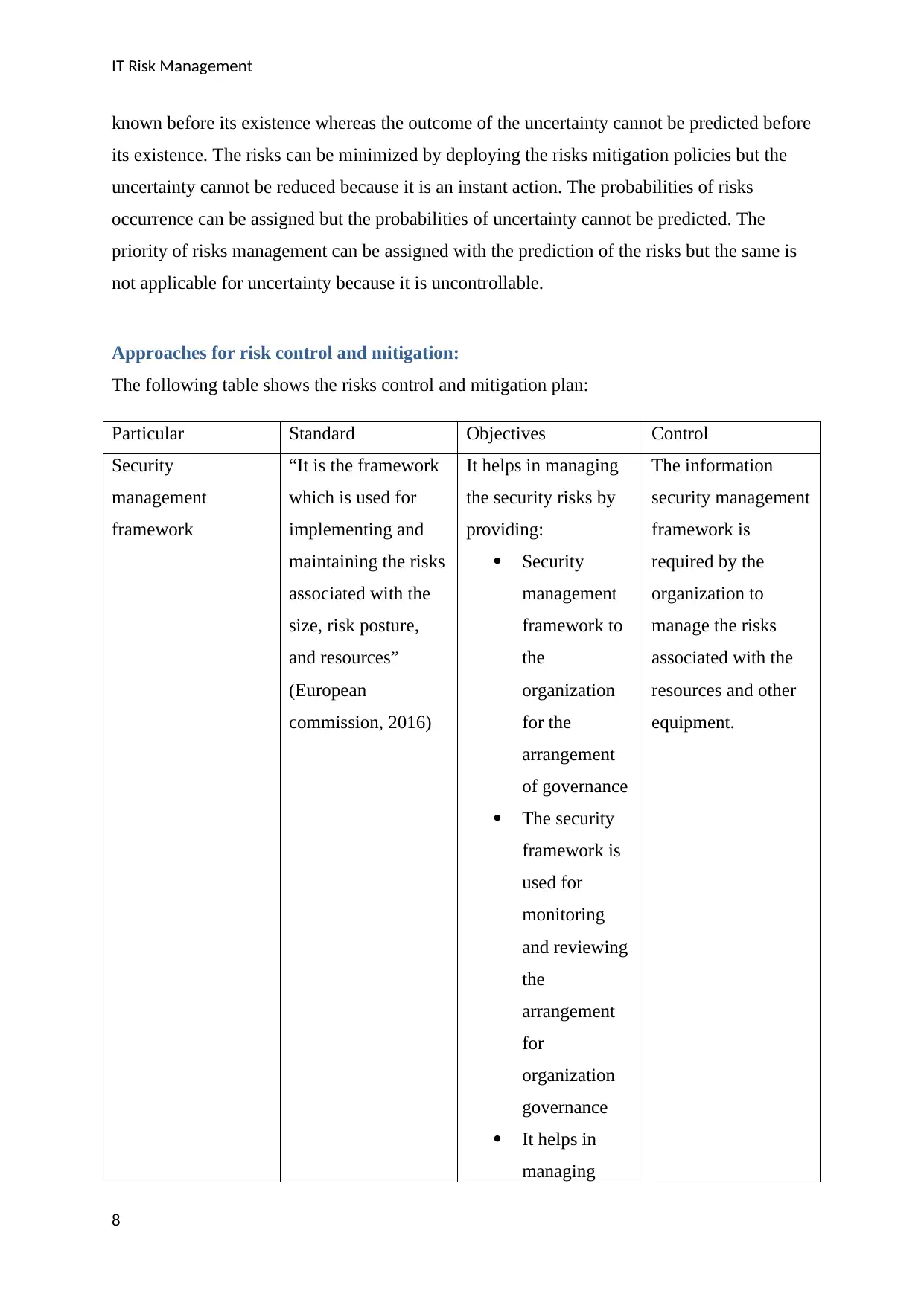
Approaches for risk control and mitigation:
The following table shows the risks control and mitigation plan:
Particular Standard Objectives Control
Security
management
framework
“It is the framework
which is used for
implementing and
maintaining the risks
associated with the
size, risk posture,
and resources”
(European
commission, 2016)
It helps in managing
the security risks by
providing:
Security
management
framework to
the
organization
for the
arrangement
of governance
The security
framework is
used for
monitoring
and reviewing
the
arrangement
for
organization
governance
It helps in
managing
The information
security management
framework is
required by the
organization to
manage the risks
associated with the
resources and other
equipment.
8
known before its existence whereas the outcome of the uncertainty cannot be predicted before
its existence. The risks can be minimized by deploying the risks mitigation policies but the
uncertainty cannot be reduced because it is an instant action. The probabilities of risks
occurrence can be assigned but the probabilities of uncertainty cannot be predicted. The
priority of risks management can be assigned with the prediction of the risks but the same is
not applicable for uncertainty because it is uncontrollable.
Approaches for risk control and mitigation:
The following table shows the risks control and mitigation plan:
Particular Standard Objectives Control
Security
management
framework
“It is the framework
which is used for
implementing and
maintaining the risks
associated with the
size, risk posture,
and resources”
(European
commission, 2016)
It helps in managing
the security risks by
providing:
Security
management
framework to
the
organization
for the
arrangement
of governance
The security
framework is
used for
monitoring
and reviewing
the
arrangement
for
organization
governance
It helps in
managing
The information
security management
framework is
required by the
organization to
manage the risks
associated with the
resources and other
equipment.
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
IT Risk Management
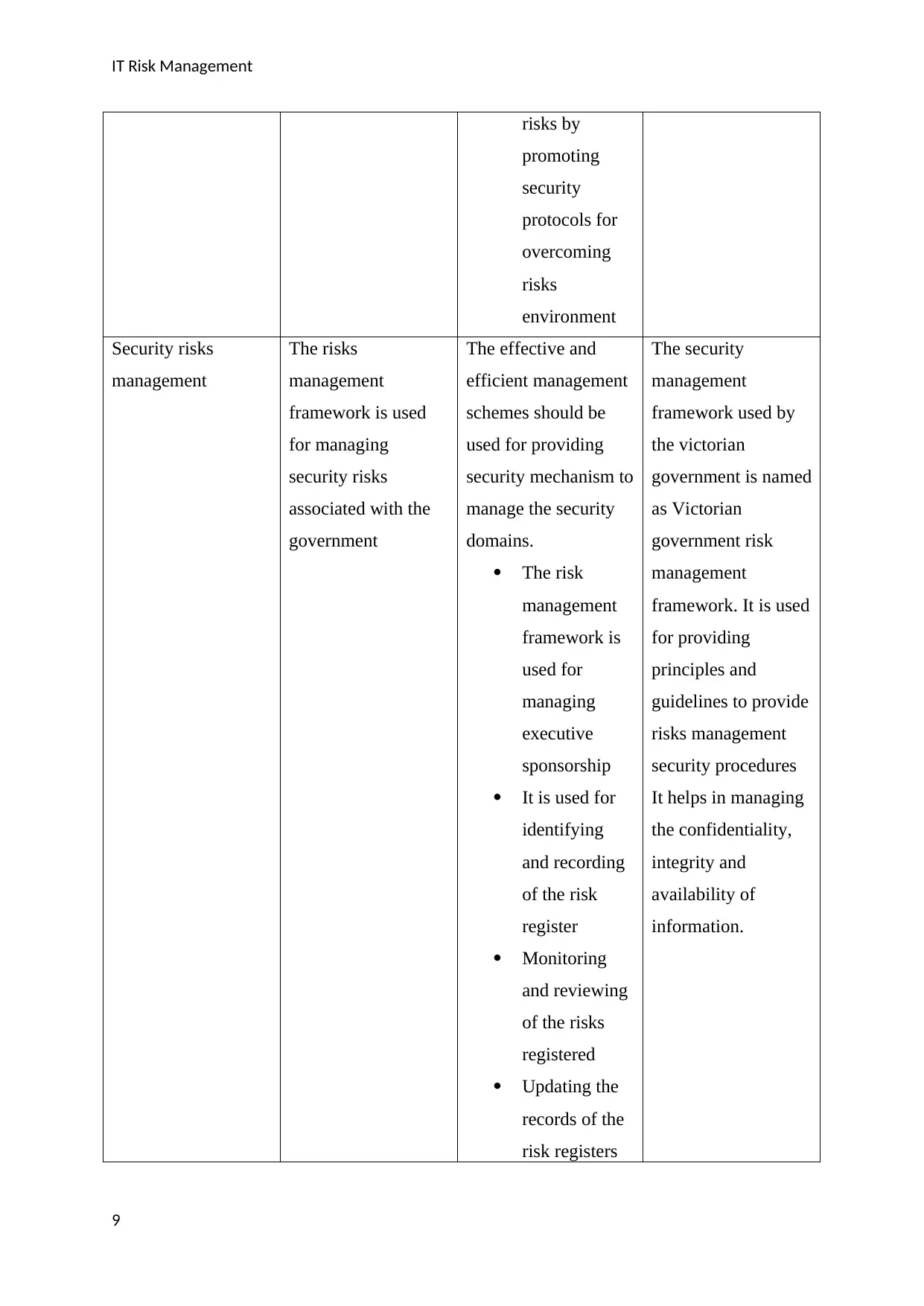
risks by
promoting
security
protocols for
overcoming
risks
environment
Security risks
management
The risks
management
framework is used
for managing
security risks
associated with the
government
The effective and
efficient management
schemes should be
used for providing
security mechanism to
manage the security
domains.
The risk
management
framework is
used for
managing
executive
sponsorship
It is used for
identifying
and recording
of the risk
register
Monitoring
and reviewing
of the risks
registered
Updating the
records of the
risk registers
The security
management
framework used by
the victorian
government is named
as Victorian
government risk
management
framework. It is used
for providing
principles and
guidelines to provide
risks management
security procedures
It helps in managing
the confidentiality,
integrity and
availability of
information.
9
risks by
promoting
security
protocols for
overcoming
risks
environment
Security risks
management
The risks
management
framework is used
for managing
security risks
associated with the
government
The effective and
efficient management
schemes should be
used for providing
security mechanism to
manage the security
domains.
The risk
management
framework is
used for
managing
executive
sponsorship
It is used for
identifying
and recording
of the risk
register
Monitoring
and reviewing
of the risks
registered
Updating the
records of the
risk registers
The security
management
framework used by
the victorian
government is named
as Victorian
government risk
management
framework. It is used
for providing
principles and
guidelines to provide
risks management
security procedures
It helps in managing
the confidentiality,
integrity and
availability of
information.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
IT Risk Management
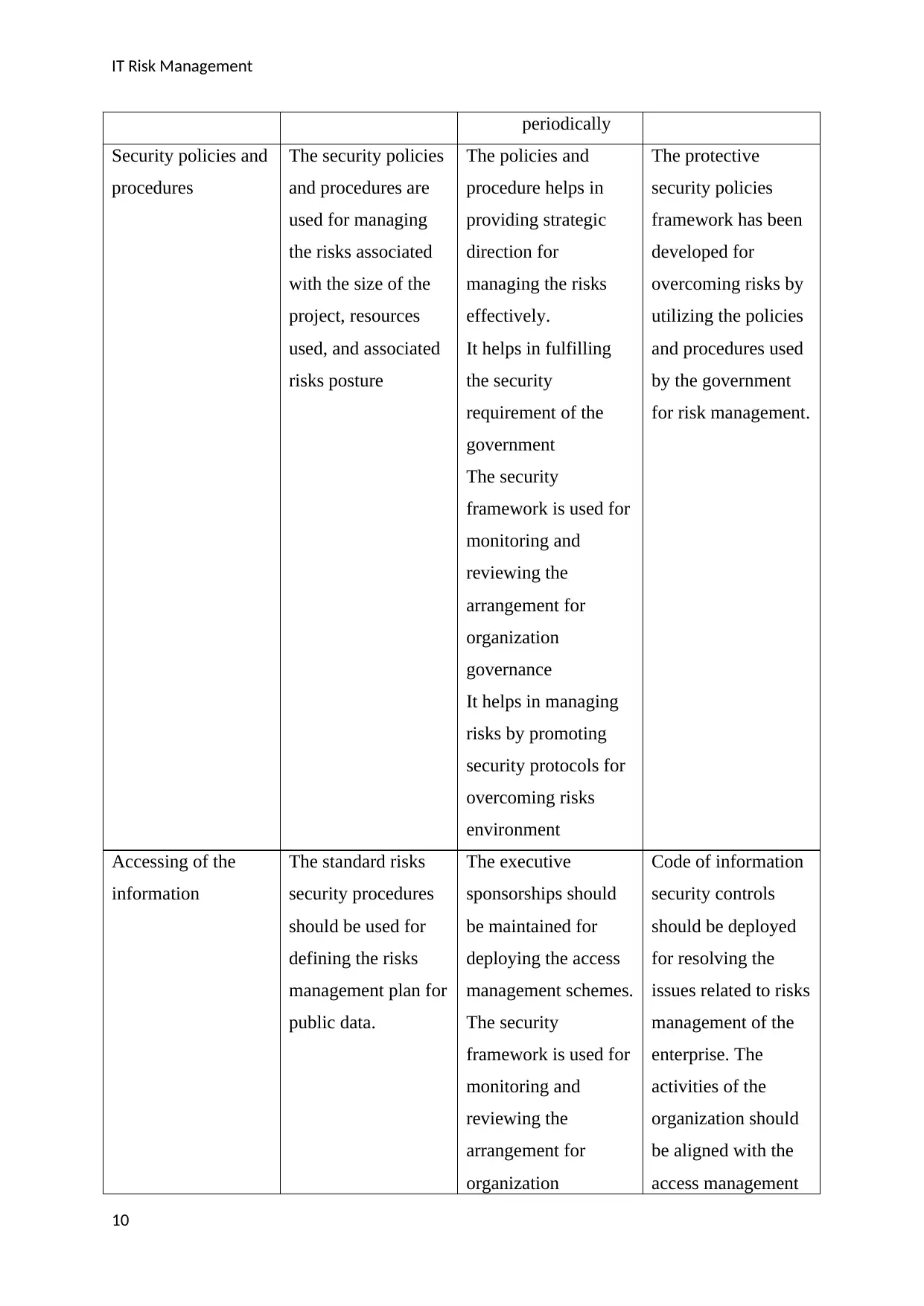
periodically
Security policies and
procedures
The security policies
and procedures are
used for managing
the risks associated
with the size of the
project, resources
used, and associated
risks posture
The policies and
procedure helps in
providing strategic
direction for
managing the risks
effectively.
It helps in fulfilling
the security
requirement of the
government
The security
framework is used for
monitoring and
reviewing the
arrangement for
organization
governance
It helps in managing
risks by promoting
security protocols for
overcoming risks
environment
The protective
security policies
framework has been
developed for
overcoming risks by
utilizing the policies
and procedures used
by the government
for risk management.
Accessing of the
information
The standard risks
security procedures
should be used for
defining the risks
management plan for
public data.
The executive
sponsorships should
be maintained for
deploying the access
management schemes.
The security
framework is used for
monitoring and
reviewing the
arrangement for
organization
Code of information
security controls
should be deployed
for resolving the
issues related to risks
management of the
enterprise. The
activities of the
organization should
be aligned with the
access management
10
periodically
Security policies and
procedures
The security policies
and procedures are
used for managing
the risks associated
with the size of the
project, resources
used, and associated
risks posture
The policies and
procedure helps in
providing strategic
direction for
managing the risks
effectively.
It helps in fulfilling
the security
requirement of the
government
The security
framework is used for
monitoring and
reviewing the
arrangement for
organization
governance
It helps in managing
risks by promoting
security protocols for
overcoming risks
environment
The protective
security policies
framework has been
developed for
overcoming risks by
utilizing the policies
and procedures used
by the government
for risk management.
Accessing of the
information
The standard risks
security procedures
should be used for
defining the risks
management plan for
public data.
The executive
sponsorships should
be maintained for
deploying the access
management schemes.
The security
framework is used for
monitoring and
reviewing the
arrangement for
organization
Code of information
security controls
should be deployed
for resolving the
issues related to risks
management of the
enterprise. The
activities of the
organization should
be aligned with the
access management
10
IT Risk Management
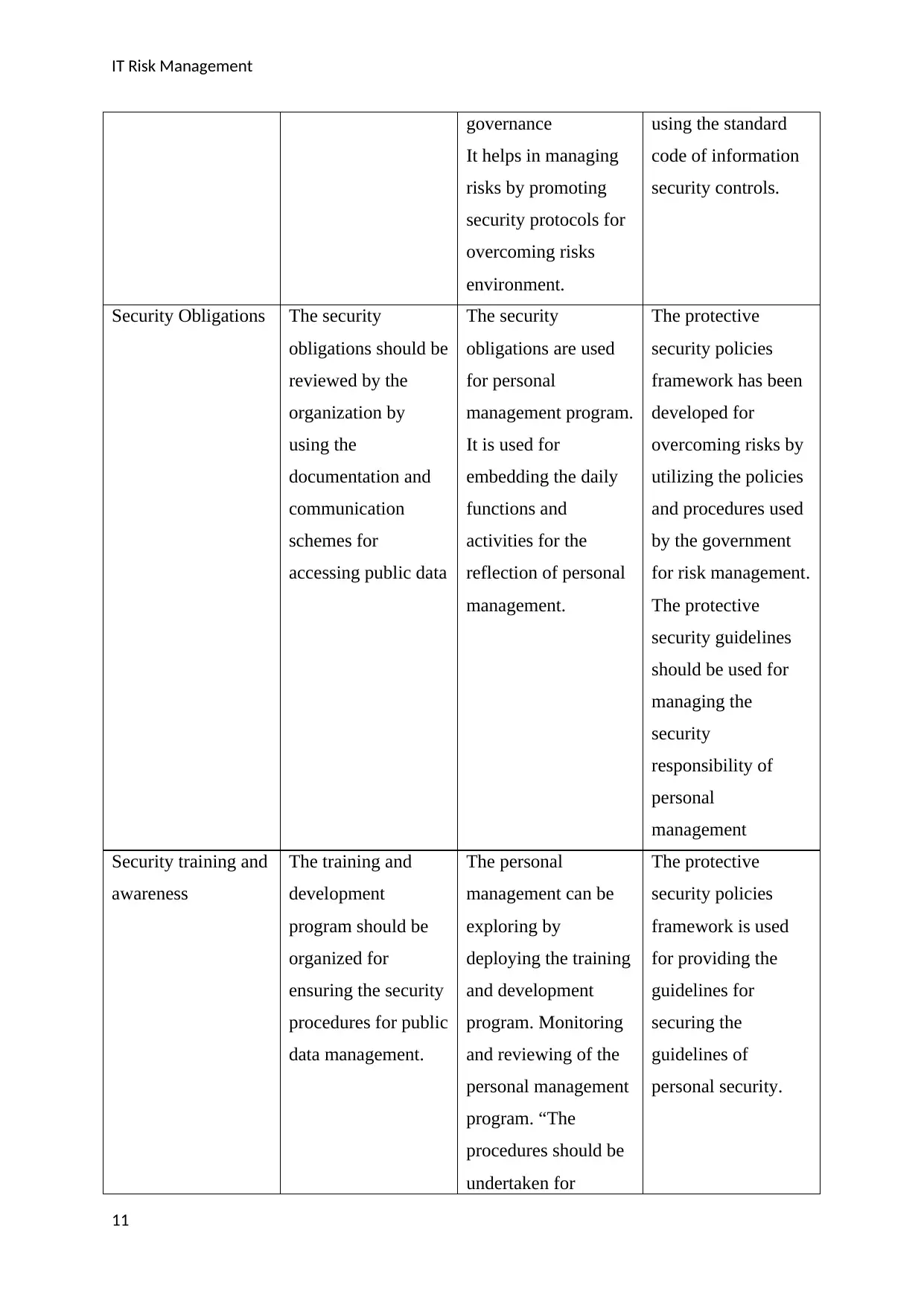
governance
It helps in managing
risks by promoting
security protocols for
overcoming risks
environment.
using the standard
code of information
security controls.
Security Obligations The security
obligations should be
reviewed by the
organization by
using the
documentation and
communication
schemes for
accessing public data
The security
obligations are used
for personal
management program.
It is used for
embedding the daily
functions and
activities for the
reflection of personal
management.
The protective
security policies
framework has been
developed for
overcoming risks by
utilizing the policies
and procedures used
by the government
for risk management.
The protective
security guidelines
should be used for
managing the
security
responsibility of
personal
management
Security training and
awareness
The training and
development
program should be
organized for
ensuring the security
procedures for public
data management.
The personal
management can be
exploring by
deploying the training
and development
program. Monitoring
and reviewing of the
personal management
program. “The
procedures should be
undertaken for
The protective
security policies
framework is used
for providing the
guidelines for
securing the
guidelines of
personal security.
11
governance
It helps in managing
risks by promoting
security protocols for
overcoming risks
environment.
using the standard
code of information
security controls.
Security Obligations The security
obligations should be
reviewed by the
organization by
using the
documentation and
communication
schemes for
accessing public data
The security
obligations are used
for personal
management program.
It is used for
embedding the daily
functions and
activities for the
reflection of personal
management.
The protective
security policies
framework has been
developed for
overcoming risks by
utilizing the policies
and procedures used
by the government
for risk management.
The protective
security guidelines
should be used for
managing the
security
responsibility of
personal
management
Security training and
awareness
The training and
development
program should be
organized for
ensuring the security
procedures for public
data management.
The personal
management can be
exploring by
deploying the training
and development
program. Monitoring
and reviewing of the
personal management
program. “The
procedures should be
undertaken for
The protective
security policies
framework is used
for providing the
guidelines for
securing the
guidelines of
personal security.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 19
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





