IT Risk Management Report: Assessing Security Risks for VIC Government
VerifiedAdded on 2020/03/01
|15
|3514
|86
Report
AI Summary
This report provides a comprehensive analysis of IT risk management within the VIC government, exploring current security risks and concerns. It begins with an illustration of these risks, followed by a detailed diagram analysis and risk classification, identifying both internal and external threats such as data theft, system errors, and privacy concerns. The report then compares and ranks these threats, differentiating between accidental and deliberate threats, and categorizing risks based on their exposure areas (high, medium, low). It further delves into the security challenges faced by the VIC information system, including modeling, system, data, organizational, and regulatory challenges. The report also discusses the differences between risk and uncertainty, and concludes with a discussion of risk mitigation and management strategies to enhance the security posture of the VIC government's information system. The analysis includes references to relevant literature and provides a structured approach to understanding and addressing IT security vulnerabilities.

Running head: IT RISK MANAGEMENT
IT Risk Management
Name of the student:
Student ID:
Name of the University:
Author’s note:
IT Risk Management
Name of the student:
Student ID:
Name of the University:
Author’s note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1IT RISK MANAGEMENT
Table of Contents
1. Illustration of Current Security Risks and Concerns of VIC Government..................................2
2. Diagram Analysis and Risk Classification..................................................................................3
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram........................3
2.2 Classification of the Risk and Identifying their Exposure Area............................................5
3. Comparison and Ranking of Threats...........................................................................................7
3.1 Comparing the Accidental and Deliberate Threats................................................................7
3.2 Ranking Threats for VIC Information System......................................................................8
4. Security Challenges of VIC information system.........................................................................9
5. Risk vs. Uncertainty in VIC information system.......................................................................11
6. Risk Mitigation and Management in VIC Information System.................................................12
References......................................................................................................................................14
Table of Contents
1. Illustration of Current Security Risks and Concerns of VIC Government..................................2
2. Diagram Analysis and Risk Classification..................................................................................3
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram........................3
2.2 Classification of the Risk and Identifying their Exposure Area............................................5
3. Comparison and Ranking of Threats...........................................................................................7
3.1 Comparing the Accidental and Deliberate Threats................................................................7
3.2 Ranking Threats for VIC Information System......................................................................8
4. Security Challenges of VIC information system.........................................................................9
5. Risk vs. Uncertainty in VIC information system.......................................................................11
6. Risk Mitigation and Management in VIC Information System.................................................12
References......................................................................................................................................14
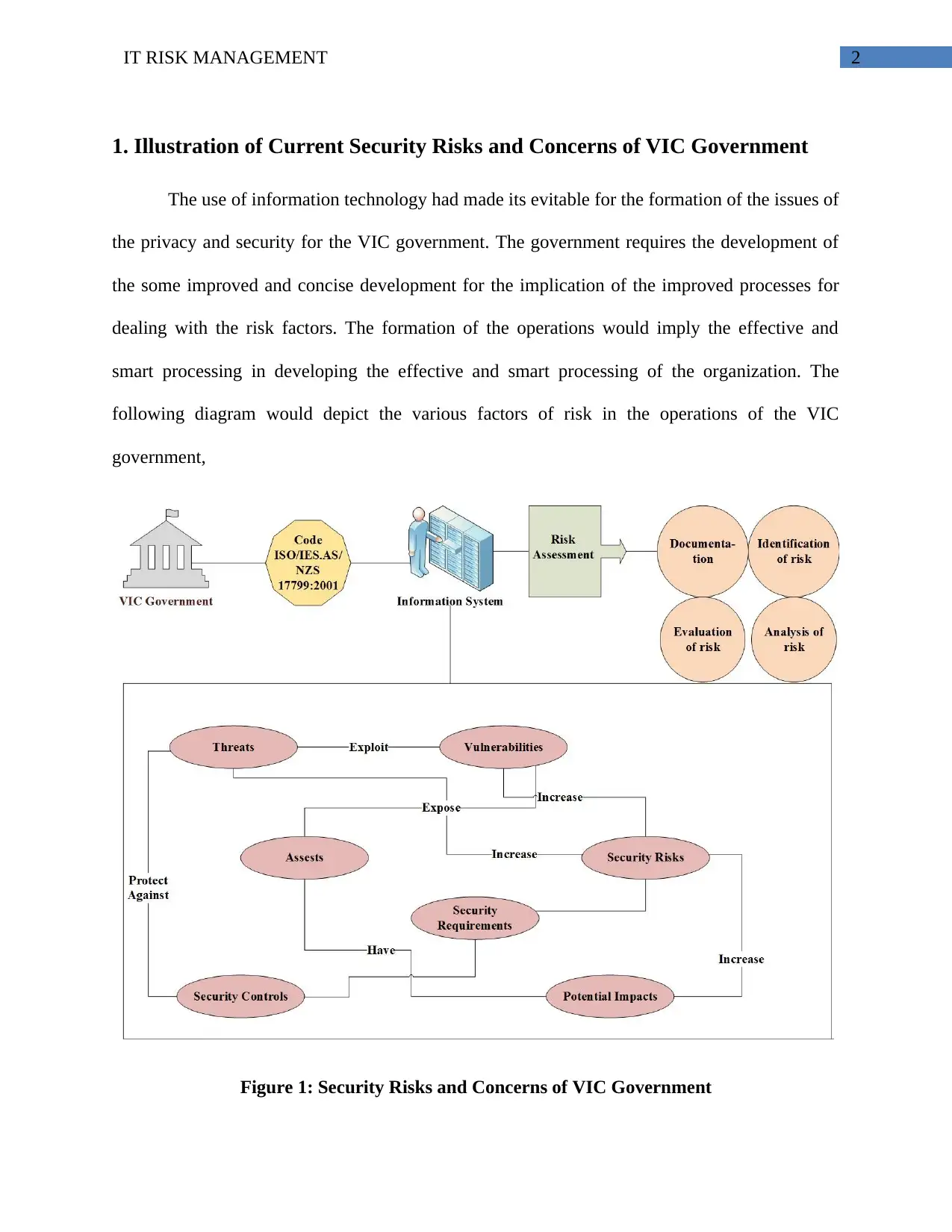
2IT RISK MANAGEMENT
1. Illustration of Current Security Risks and Concerns of VIC Government
The use of information technology had made its evitable for the formation of the issues of
the privacy and security for the VIC government. The government requires the development of
the some improved and concise development for the implication of the improved processes for
dealing with the risk factors. The formation of the operations would imply the effective and
smart processing in developing the effective and smart processing of the organization. The
following diagram would depict the various factors of risk in the operations of the VIC
government,
Figure 1: Security Risks and Concerns of VIC Government
1. Illustration of Current Security Risks and Concerns of VIC Government
The use of information technology had made its evitable for the formation of the issues of
the privacy and security for the VIC government. The government requires the development of
the some improved and concise development for the implication of the improved processes for
dealing with the risk factors. The formation of the operations would imply the effective and
smart processing in developing the effective and smart processing of the organization. The
following diagram would depict the various factors of risk in the operations of the VIC
government,
Figure 1: Security Risks and Concerns of VIC Government
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3IT RISK MANAGEMENT
(Source: Created by the author in Ms-Visio)
2. Diagram Analysis and Risk Classification
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram
The diagram for the risk and concern analysis for VIC government had shown the use of
the simple IT information system for the management of the information and implication of the
advanced processes. The components of the VIC diagram are information system, risk
assessment, threats, vulnerabilities, security controls, and security requirements.
VIC Government: The VIC government represents the users and members of the
government board that uses the information system and it would be implied for increasing the
efficiency of the operations. The system development would ease the operations of the
organization and its implication would form performance improvement for the organization.
Information System: The information system would be implied for integrating the
development of the operations for forming the effective information processing. The processing
of the system would result in employing the advanced processing of the data and information to
guide the effective flow of information. The system processing had been implied for forming the
faster data processing and development.
Risk Factors: There are a number of risk factors that affect the processing of the
information over the network of the organization. The threat and vulnerabilities would result in
integrating the development of the issues for the operations of the organization. The security
control system for the VIC government information processing would include the formation of
the systematic control over the errors and issues. The various vulnerabilities and the threats have
sincere impact on the development of the issues on the operations of VIC government. The
(Source: Created by the author in Ms-Visio)
2. Diagram Analysis and Risk Classification
2.1 Analysis of the Security Risks and Concerns of VIC Government Diagram
The diagram for the risk and concern analysis for VIC government had shown the use of
the simple IT information system for the management of the information and implication of the
advanced processes. The components of the VIC diagram are information system, risk
assessment, threats, vulnerabilities, security controls, and security requirements.
VIC Government: The VIC government represents the users and members of the
government board that uses the information system and it would be implied for increasing the
efficiency of the operations. The system development would ease the operations of the
organization and its implication would form performance improvement for the organization.
Information System: The information system would be implied for integrating the
development of the operations for forming the effective information processing. The processing
of the system would result in employing the advanced processing of the data and information to
guide the effective flow of information. The system processing had been implied for forming the
faster data processing and development.
Risk Factors: There are a number of risk factors that affect the processing of the
information over the network of the organization. The threat and vulnerabilities would result in
integrating the development of the issues for the operations of the organization. The security
control system for the VIC government information processing would include the formation of
the systematic control over the errors and issues. The various vulnerabilities and the threats have
sincere impact on the development of the issues on the operations of VIC government. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4IT RISK MANAGEMENT
security requirements have been sincerely caused errors on the development of the effective and
smart operations. The threats exploit the vulnerabilities for forming the security issues in the
development of the effective and smart operations within the development of the operations. The
data theft, system errors and privacy hindrance are the factors of security threats in the
organizational development. The deployment of the effective and improved processes has been
largely influenced due to the hindrances of risk factors.
Internal and External Risk: The threats, risk, and vulnerabilities would form the
development of issues in forming the effective operations of the organization. There are many
risks in the information system of VIC and they can be broadly classified into internal and
external risks. The internal risks are developed from internal errors and vulnerabilities and some
of them are technical risks, denial of service, spamming, design flaws, and unauthorized entrance
in the information system. These risk factors would imply the errors and technical vulnerabilities
in the system of operations for the organization. The external risk factor is aroused from the
development of the some outside errors and issues. The external risk include user generated
errors and cyber criminal activities. These errors are generated outside of the system and it
results in forming the major threat to the system development.
Risk Assessment: The risk assessment is implied for forming the development of the
security risk management. The risk management is implied for developing the smart risk analysis
for forming the effective and smart processing of the information. The risk assessment consists
of documentation, analysis, evaluation, and identification of the risk. The risk assessment
consists of the development of the some strategies for the implication of the improved processes.
The risk assessment would imply the development of monitoring process for the system analysis
security requirements have been sincerely caused errors on the development of the effective and
smart operations. The threats exploit the vulnerabilities for forming the security issues in the
development of the effective and smart operations within the development of the operations. The
data theft, system errors and privacy hindrance are the factors of security threats in the
organizational development. The deployment of the effective and improved processes has been
largely influenced due to the hindrances of risk factors.
Internal and External Risk: The threats, risk, and vulnerabilities would form the
development of issues in forming the effective operations of the organization. There are many
risks in the information system of VIC and they can be broadly classified into internal and
external risks. The internal risks are developed from internal errors and vulnerabilities and some
of them are technical risks, denial of service, spamming, design flaws, and unauthorized entrance
in the information system. These risk factors would imply the errors and technical vulnerabilities
in the system of operations for the organization. The external risk factor is aroused from the
development of the some outside errors and issues. The external risk include user generated
errors and cyber criminal activities. These errors are generated outside of the system and it
results in forming the major threat to the system development.
Risk Assessment: The risk assessment is implied for forming the development of the
security risk management. The risk management is implied for developing the smart risk analysis
for forming the effective and smart processing of the information. The risk assessment consists
of documentation, analysis, evaluation, and identification of the risk. The risk assessment
consists of the development of the some strategies for the implication of the improved processes.
The risk assessment would imply the development of monitoring process for the system analysis
5IT RISK MANAGEMENT
and design. The analysis and evaluation of the risk factors would help in forming the integrated
operations of the organization.
2.2 Classification of the Risk and Identifying their Exposure Area
The risk has been broadly classified into internal and external risk factors and it has helped in
developing an independent analysis of the risk assessment. The VIC government had deployed
the information processing for forming the improved processes of the data processing. However,
the organization had to face some issues and risk factors for integration and development. The
various risks of VIC government are security risk, vulnerabilities, potential risk, malware,
phishing, data theft, technical errors, unauthorized entry, spamming, denial of service, suer
generated errors, and social engineering errors. These risks can be categorized into high,
medium, medium-low, and low risk exposure areas.
Risk Type Description Example
High risk
exposure
areas
The high risk exposure areas have crucial and
significant impact on the development of the
operations in the organization. The risk factors would
form the major influence on the development of the
operations. The high risk exposure areas would be
given highest priority for being treated and rectified
in the operations of the project.
Theft of data, Privacy
concerns, and Security
vulnerabilities are
example of high risk
exposure areas
Medium
risk
exposure
The medium risk exposure areas would be formed for
the risk factors that have medium impact on the
operations of the information system. These types of
Malwares, Intrusion,
Design errors, and
technical errors are the
and design. The analysis and evaluation of the risk factors would help in forming the integrated
operations of the organization.
2.2 Classification of the Risk and Identifying their Exposure Area
The risk has been broadly classified into internal and external risk factors and it has helped in
developing an independent analysis of the risk assessment. The VIC government had deployed
the information processing for forming the improved processes of the data processing. However,
the organization had to face some issues and risk factors for integration and development. The
various risks of VIC government are security risk, vulnerabilities, potential risk, malware,
phishing, data theft, technical errors, unauthorized entry, spamming, denial of service, suer
generated errors, and social engineering errors. These risks can be categorized into high,
medium, medium-low, and low risk exposure areas.
Risk Type Description Example
High risk
exposure
areas
The high risk exposure areas have crucial and
significant impact on the development of the
operations in the organization. The risk factors would
form the major influence on the development of the
operations. The high risk exposure areas would be
given highest priority for being treated and rectified
in the operations of the project.
Theft of data, Privacy
concerns, and Security
vulnerabilities are
example of high risk
exposure areas
Medium
risk
exposure
The medium risk exposure areas would be formed for
the risk factors that have medium impact on the
operations of the information system. These types of
Malwares, Intrusion,
Design errors, and
technical errors are the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6IT RISK MANAGEMENT
areas risk exposure areas are given moderate priority for
sorting and developing plan for contingency. The
medium risk exposure areas are treated for decreasing
the impact on the operations of the information
system of VIC Government.
medium risk exposure
areas
Medium
low risk
exposure
areas
The medium low risk exposure areas do not have
major influence on the operations of information
system of the VIC organization. These risk exposure
areas is not supportive for the integration of the
information processing. These risk exposure areas
would be give less priority in being delivered of the
solution and processing.
The spamming, denial of
service, and some minor
issues are the medium
low risk exposure areas.
Low risk
exposure
areas
The low risk exposure areas are the least influential
factor for impacting the operations of the information
processing of VIC government. The processing of
these risk factors would take the least amount of time
and their impact on the VIC organization is least. The
low risk exposure areas would be given least priority
for being sorted and solved.
The Social engineering
generated errors and the
user generated errors are
the low risk exposure
areas.
areas risk exposure areas are given moderate priority for
sorting and developing plan for contingency. The
medium risk exposure areas are treated for decreasing
the impact on the operations of the information
system of VIC Government.
medium risk exposure
areas
Medium
low risk
exposure
areas
The medium low risk exposure areas do not have
major influence on the operations of information
system of the VIC organization. These risk exposure
areas is not supportive for the integration of the
information processing. These risk exposure areas
would be give less priority in being delivered of the
solution and processing.
The spamming, denial of
service, and some minor
issues are the medium
low risk exposure areas.
Low risk
exposure
areas
The low risk exposure areas are the least influential
factor for impacting the operations of the information
processing of VIC government. The processing of
these risk factors would take the least amount of time
and their impact on the VIC organization is least. The
low risk exposure areas would be given least priority
for being sorted and solved.
The Social engineering
generated errors and the
user generated errors are
the low risk exposure
areas.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7IT RISK MANAGEMENT
3. Comparison and Ranking of Threats
3.1 Comparing the Accidental and Deliberate Threats
Alcorn, Good and Pain (2013) have explained that the accidental threats have no specific
reason or motive for the operations of the organization. The accidental threats are formed due to
some mistakes or errors caused unintentionally. The accidental threats can be sorted by any
preplanned operations as the occurrence of the accidental threats is not in scope for the
operations of the information processing at VIC government. The accidental threats are
moreover can be caused due to internal issues or by any external involvement. On the contrary,
Ali et al. (2014) argued that the deliberate threats are caused due to involving of the external
influence or agent. The external deliberate threat is intentionally done either for benefitting the
attacker or harming the user of the system. The deliberate threat is caused due to the use of
improved technology for harming the flow of operations. The deliberate threat includes the cyber
criminal activities and hacking technology used purposely for harming VIC government.
3. Comparison and Ranking of Threats
3.1 Comparing the Accidental and Deliberate Threats
Alcorn, Good and Pain (2013) have explained that the accidental threats have no specific
reason or motive for the operations of the organization. The accidental threats are formed due to
some mistakes or errors caused unintentionally. The accidental threats can be sorted by any
preplanned operations as the occurrence of the accidental threats is not in scope for the
operations of the information processing at VIC government. The accidental threats are
moreover can be caused due to internal issues or by any external involvement. On the contrary,
Ali et al. (2014) argued that the deliberate threats are caused due to involving of the external
influence or agent. The external deliberate threat is intentionally done either for benefitting the
attacker or harming the user of the system. The deliberate threat is caused due to the use of
improved technology for harming the flow of operations. The deliberate threat includes the cyber
criminal activities and hacking technology used purposely for harming VIC government.

8IT RISK MANAGEMENT
Figure 2: Accidental Vs Deliberate Threats for VIC information system
(Source: Steinberg, 2016, pp.-334)
3.2 Ranking Threats for VIC Information System
The accidental threats can be sorted by any preplanned operations as the occurrence of
the accidental threats is not in scope for the operations of the information processing at VIC
government. The system flaws, unknown file deletion, accidental data compromise, and natural
disasters are the accidental threats of the information system implementation in VIC government.
The deliberate threat is caused due to the use of improved technology for harming the flow of
operations and used purposely for harming VIC government. The theft of storage system device,
hacking and cyber crimes, virus and malware attack, and deliberate data compromise are the
Threat
s
Accidental Data
Compromise
Natural
Disasters
Unknown File
Deletion
System Flaws
Hacking and
Cyber Crimes
Deliberate Data
Compromise
Virus and
Malware attack
Theft of Storage
system device
A
C
C
I
D
E
N
T
A
L
D
E
L
I
B
E
R
A
T
E
Figure 2: Accidental Vs Deliberate Threats for VIC information system
(Source: Steinberg, 2016, pp.-334)
3.2 Ranking Threats for VIC Information System
The accidental threats can be sorted by any preplanned operations as the occurrence of
the accidental threats is not in scope for the operations of the information processing at VIC
government. The system flaws, unknown file deletion, accidental data compromise, and natural
disasters are the accidental threats of the information system implementation in VIC government.
The deliberate threat is caused due to the use of improved technology for harming the flow of
operations and used purposely for harming VIC government. The theft of storage system device,
hacking and cyber crimes, virus and malware attack, and deliberate data compromise are the
Threat
s
Accidental Data
Compromise
Natural
Disasters
Unknown File
Deletion
System Flaws
Hacking and
Cyber Crimes
Deliberate Data
Compromise
Virus and
Malware attack
Theft of Storage
system device
A
C
C
I
D
E
N
T
A
L
D
E
L
I
B
E
R
A
T
E
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9IT RISK MANAGEMENT
deliberate threats of the information system implementation in VIC government. These two types
of threats have been ranked in the table below,
Rank: 1st
Threat Type: Deliberate
Examples: Theft of Storage System Device, Hacking and Cyber Crimes, Virus and Malware
Attack, and Deliberate Data Compromise
Explanation of the Rank: All of these risks are given highest priority due to their severe impact
on the information system processing at the VIC Government
Rank: 2nd
Threat Type: Accidental
Examples: System Flaws, Unknown File Deletion, Accidental Data Compromise, and Natural
Disasters
Explanation of the Rank: All these risks are give low priority due to the absence of any critical
impact on the operations of information system of VIC Government
Table 1: Threat ranking for VIC information system
(Source: Steinberg, 2016, pp.-340)
4. Security Challenges of VIC information system
The implementation of the information processing has to face many issues due to the risk
factors and it would form the generation of the some challenges for the VIC Government
deliberate threats of the information system implementation in VIC government. These two types
of threats have been ranked in the table below,
Rank: 1st
Threat Type: Deliberate
Examples: Theft of Storage System Device, Hacking and Cyber Crimes, Virus and Malware
Attack, and Deliberate Data Compromise
Explanation of the Rank: All of these risks are given highest priority due to their severe impact
on the information system processing at the VIC Government
Rank: 2nd
Threat Type: Accidental
Examples: System Flaws, Unknown File Deletion, Accidental Data Compromise, and Natural
Disasters
Explanation of the Rank: All these risks are give low priority due to the absence of any critical
impact on the operations of information system of VIC Government
Table 1: Threat ranking for VIC information system
(Source: Steinberg, 2016, pp.-340)
4. Security Challenges of VIC information system
The implementation of the information processing has to face many issues due to the risk
factors and it would form the generation of the some challenges for the VIC Government
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10IT RISK MANAGEMENT
(Sharma et al., 2013). The development of the effective and smart operations would be slacked
due to these issues and operations. The formation of the effective and imperative operation
would result in forming the major factors for the challenges to the VIC government (Mans et al.,
2013). The various factors of the challenges for VIC Government are modeling challenges,
system and data challenges, organizational challenges, and regulatory challenges.
Modeling Challenges According to Mans et al. (2013), the modeling challenges are
caused due to the implication of the errors in the designing of the system and it had formed the
issue in performance and operational speed of the information processing. The information
system development would have to face the issue of system incompatibility and formation issues.
System and Data Challenges The system and data challenges would be implied for
the development of the information processing and it would be implied for the development of
the issues in the operations of the system data and challenges. According to Silbey (2013), the
data and system challenges would result in forming the issues of the information processing.
Organizational Challenges The system development would be implied for developing
the processes of the operational development. According to Sharma et al. (2013), the
organizational challenges would be developed for integrating the limited and temperament of the
operational processing. The development of the effective and smart operations would be slacked
due to these issues and operations.
Regulatory Challenges As opined by Varshney (2014), the regulatory issues of the
VIC information is important and crucial as the risk assessment is largely dependent on the
development for harming the issues of the integration and formation of the improved processes.
(Sharma et al., 2013). The development of the effective and smart operations would be slacked
due to these issues and operations. The formation of the effective and imperative operation
would result in forming the major factors for the challenges to the VIC government (Mans et al.,
2013). The various factors of the challenges for VIC Government are modeling challenges,
system and data challenges, organizational challenges, and regulatory challenges.
Modeling Challenges According to Mans et al. (2013), the modeling challenges are
caused due to the implication of the errors in the designing of the system and it had formed the
issue in performance and operational speed of the information processing. The information
system development would have to face the issue of system incompatibility and formation issues.
System and Data Challenges The system and data challenges would be implied for
the development of the information processing and it would be implied for the development of
the issues in the operations of the system data and challenges. According to Silbey (2013), the
data and system challenges would result in forming the issues of the information processing.
Organizational Challenges The system development would be implied for developing
the processes of the operational development. According to Sharma et al. (2013), the
organizational challenges would be developed for integrating the limited and temperament of the
operational processing. The development of the effective and smart operations would be slacked
due to these issues and operations.
Regulatory Challenges As opined by Varshney (2014), the regulatory issues of the
VIC information is important and crucial as the risk assessment is largely dependent on the
development for harming the issues of the integration and formation of the improved processes.

11IT RISK MANAGEMENT
The formation of the effective and imperative operation would result in forming the major
factors for the challenges to the VIC government.
5. Risk vs. Uncertainty in VIC information system
The VIC government had deployed the information processing for forming the improved
processes of the data processing. However, the organization had to face some risk and
uncertainty factors for integration and development. The VIC government have been facing
security risks and uncertainties. The comparison of risks and uncertainties have been given in the
table below,
Risk
Description: Risk can be defined as the factor that causes the uneven deviation of the
operational output from the expected outcome (Covello et al., 2013). The analysis had shown
that the risk plays a major role in the development of the operation for the VIC government.
Result: The outcome for the risk can be positive or negative depending upon the nature of the
operations.
System of control: The system of control is formed for integrating the development of the
operation and it would be formed by implying the risk management process. The risk
management would help in controlling the impact of the risk factors for the VIC Government.
Probability: High probability of occurrence and would have considerable impact on the
operations
Effect: Impact of the risk is divergent and can be positive and negative
The formation of the effective and imperative operation would result in forming the major
factors for the challenges to the VIC government.
5. Risk vs. Uncertainty in VIC information system
The VIC government had deployed the information processing for forming the improved
processes of the data processing. However, the organization had to face some risk and
uncertainty factors for integration and development. The VIC government have been facing
security risks and uncertainties. The comparison of risks and uncertainties have been given in the
table below,
Risk
Description: Risk can be defined as the factor that causes the uneven deviation of the
operational output from the expected outcome (Covello et al., 2013). The analysis had shown
that the risk plays a major role in the development of the operation for the VIC government.
Result: The outcome for the risk can be positive or negative depending upon the nature of the
operations.
System of control: The system of control is formed for integrating the development of the
operation and it would be formed by implying the risk management process. The risk
management would help in controlling the impact of the risk factors for the VIC Government.
Probability: High probability of occurrence and would have considerable impact on the
operations
Effect: Impact of the risk is divergent and can be positive and negative
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





