IT Security Management Assignment Solutions - Workshops 1-12
VerifiedAdded on 2023/01/10
|35
|11232
|87
Homework Assignment
AI Summary
This document presents a comprehensive solution to an IT Security Management assignment, encompassing detailed responses to workshops and case studies. The assignment covers a wide range of topics, including the application of the CNSS model and McCumber Cube for information protection, analysis of the Australian Privacy Principles, and the implications of the Assistance and Access Act. It delves into physical security measures, risk assessments, and the development of IT security policies. The assignment also includes a case study on John Dough Pizza, analyzing its security management issues, compliance with ISM, and incident response strategies. Furthermore, the document explores job hunting websites, required qualifications, and the role of AI, data lakes, and blockchain in cybersecurity. The solutions provided offer insights into secured software development and the defense against trespassing, along with asset identification and incident management.

IT Security
Management
Management
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Table of Contents
Workshop 1......................................................................................................................................1
Exercise 1.........................................................................................................................................1
Brief statement for addressing 27 cells of CNSS model........................................................1
Exercise 2.........................................................................................................................................3
Impact if information in system is compromised...................................................................3
Workshop 2......................................................................................................................................4
Exercise 1.........................................................................................................................................4
Brief statements for producing whether firm needs new policies in context of new Assistance
and Access law.......................................................................................................................4
If Technical Assistance Request is provided to intercept message, will you comply it.........4
Compare technical assistance request, technical capability notice and technical assistance
notice......................................................................................................................................4
Which needs to have quick actions by firm............................................................................5
Exercise 2.........................................................................................................................................5
Choose 3 principles from Australian Privacy Principles for on-line game that are utilised by
school children........................................................................................................................5
Exercise 3.........................................................................................................................................6
Approaches for improvisation of staff awareness..................................................................6
Workshop 3......................................................................................................................................6
1. Define physical security................................................................................................6
2. List issues that can take place while managing physical security of art gallery...........6
a. Creation of 5 issues.......................................................................................................6
3. Carry out risk assessment for issue identified...............................................................7
a. Probable risks associated with issue.............................................................................7
4. Legal & ethical issues while developing new policies.................................................7
a. Concerns related with legal as well as ethical concerns...............................................7
5. Develop physical security policies................................................................................7
6. Formulate structure of policy document from SANS policies......................................8
1. Illustrate new security policies......................................................................................8
Workshop 1......................................................................................................................................1
Exercise 1.........................................................................................................................................1
Brief statement for addressing 27 cells of CNSS model........................................................1
Exercise 2.........................................................................................................................................3
Impact if information in system is compromised...................................................................3
Workshop 2......................................................................................................................................4
Exercise 1.........................................................................................................................................4
Brief statements for producing whether firm needs new policies in context of new Assistance
and Access law.......................................................................................................................4
If Technical Assistance Request is provided to intercept message, will you comply it.........4
Compare technical assistance request, technical capability notice and technical assistance
notice......................................................................................................................................4
Which needs to have quick actions by firm............................................................................5
Exercise 2.........................................................................................................................................5
Choose 3 principles from Australian Privacy Principles for on-line game that are utilised by
school children........................................................................................................................5
Exercise 3.........................................................................................................................................6
Approaches for improvisation of staff awareness..................................................................6
Workshop 3......................................................................................................................................6
1. Define physical security................................................................................................6
2. List issues that can take place while managing physical security of art gallery...........6
a. Creation of 5 issues.......................................................................................................6
3. Carry out risk assessment for issue identified...............................................................7
a. Probable risks associated with issue.............................................................................7
4. Legal & ethical issues while developing new policies.................................................7
a. Concerns related with legal as well as ethical concerns...............................................7
5. Develop physical security policies................................................................................7
6. Formulate structure of policy document from SANS policies......................................8
1. Illustrate new security policies......................................................................................8

a. Specify policy name......................................................................................................8
b. What is policy based on................................................................................................8
c. How much existent policies can be reused...................................................................8
d. Risks that will be addressed by policy..........................................................................8
e. Success of policy...........................................................................................................8
Discuss that IT security policies taken are enough that can be adapted within distinct security
environment............................................................................................................................9
Workshop 4......................................................................................................................................9
2. Identification of peculiar security management issues that prevails in JOHN DOUGH9
3. Identify types of controls within chapter....................................................................10
4. Statement that summarizes current levels for compliance with Government.............10
5. What immediate action is required by JOHN DOUGH to improvise security...........10
The controls illustrated are reasonable for business or they overkill...................................11
How firm can comply with ISM...........................................................................................11
How to prove compliance with ISM....................................................................................11
Workshop 5....................................................................................................................................12
1. By usage of internet identify job hunting website......................................................12
There are various websites which are being utilized by individuals for identification of
appropriate job as per their qualification. They are: Adzuna, CareerOne, CareerJet, Gumtree,
Indeed Australia, JobActive powered by JobSearch, GradConnection, Job Seeker and many
more that aids people to have jobs as per their requirements. There are various job roles with
reference to IT and individuals can apply for them as per their qualifications....................12
2. List 10 titles which are advertised...............................................................................12
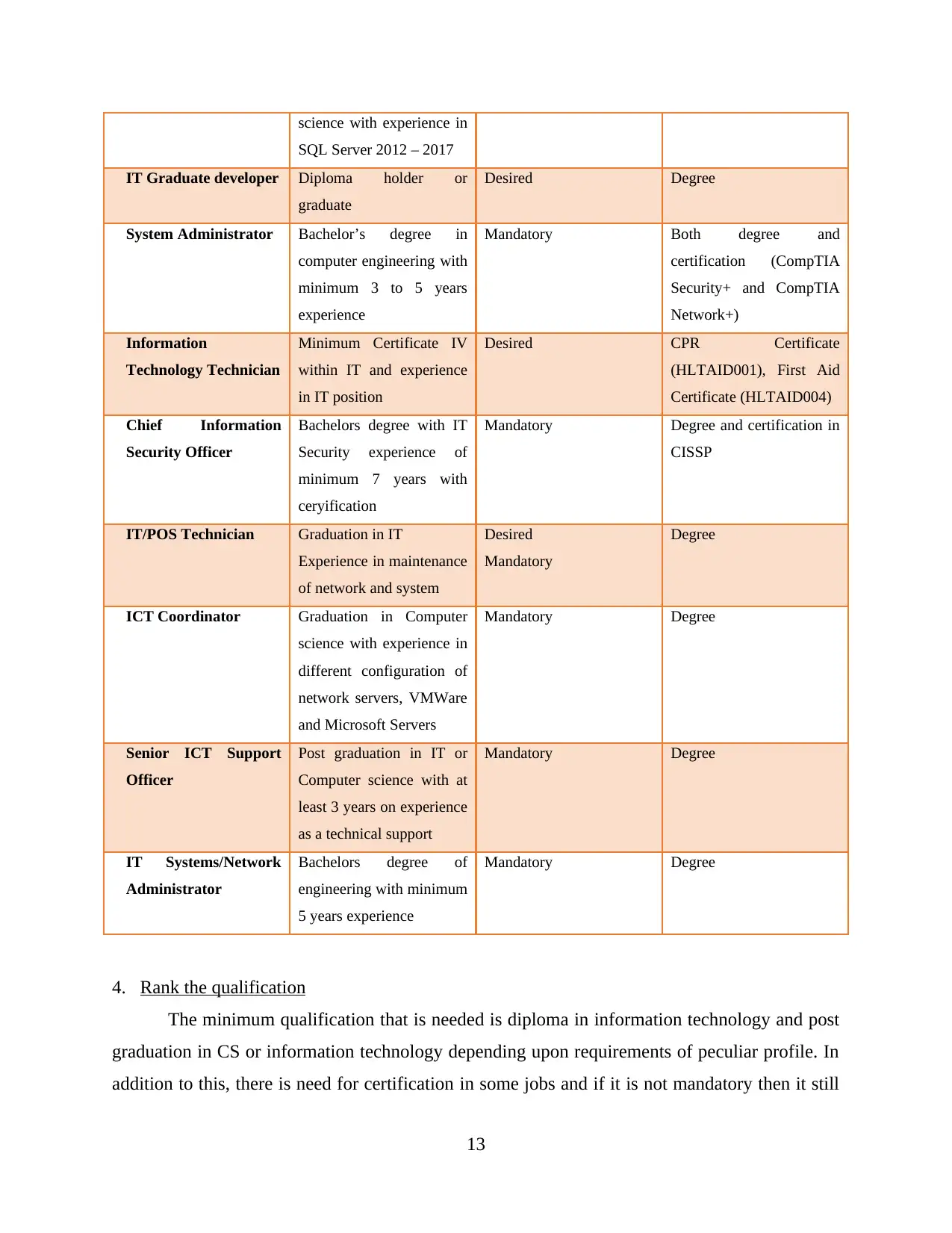
3. Identify qualification needed for job...........................................................................12
A, b, c Qualification, desired or mandatory and Industry certification or degree................12
4. Rank the qualification.................................................................................................14
5. Identification of 3 required industry certification.......................................................14
6. Write description of ideal candidate...........................................................................15
1. Identify role that has to be fulfilled.............................................................................15
a. Specify role of title......................................................................................................15
2. Illustrate what other firms are doing in reference to needs of role with identical title15
b. What is policy based on................................................................................................8
c. How much existent policies can be reused...................................................................8
d. Risks that will be addressed by policy..........................................................................8
e. Success of policy...........................................................................................................8
Discuss that IT security policies taken are enough that can be adapted within distinct security
environment............................................................................................................................9
Workshop 4......................................................................................................................................9
2. Identification of peculiar security management issues that prevails in JOHN DOUGH9
3. Identify types of controls within chapter....................................................................10
4. Statement that summarizes current levels for compliance with Government.............10
5. What immediate action is required by JOHN DOUGH to improvise security...........10
The controls illustrated are reasonable for business or they overkill...................................11
How firm can comply with ISM...........................................................................................11
How to prove compliance with ISM....................................................................................11
Workshop 5....................................................................................................................................12
1. By usage of internet identify job hunting website......................................................12
There are various websites which are being utilized by individuals for identification of
appropriate job as per their qualification. They are: Adzuna, CareerOne, CareerJet, Gumtree,
Indeed Australia, JobActive powered by JobSearch, GradConnection, Job Seeker and many
more that aids people to have jobs as per their requirements. There are various job roles with
reference to IT and individuals can apply for them as per their qualifications....................12
2. List 10 titles which are advertised...............................................................................12
3. Identify qualification needed for job...........................................................................12
A, b, c Qualification, desired or mandatory and Industry certification or degree................12
4. Rank the qualification.................................................................................................14
5. Identification of 3 required industry certification.......................................................14
6. Write description of ideal candidate...........................................................................15
1. Identify role that has to be fulfilled.............................................................................15
a. Specify role of title......................................................................................................15
2. Illustrate what other firms are doing in reference to needs of role with identical title15

3. Qualification that is expected......................................................................................15
4. Explicate ideal Job in context of job advertisement read............................................16
Workshop 7....................................................................................................................................16
1. List IT security programme for evaluation. List 5organisation and programmes
identified...............................................................................................................................16
2, 3. Identification of goals of programme and Illustrate 5 words for programme..............16
4. Illustrate one programme in depth..............................................................................18
5. Evaluate programme...................................................................................................18
1. Write introduction on IT security programme that is being examined.......................19
2. Goals of programme....................................................................................................19
3. Why programme is evaluated.....................................................................................19
4. Create a logic map for programme.............................................................................19
5. Formulate evaluation questions..................................................................................20
6. Write short statements.................................................................................................20
Discussions....................................................................................................................................21
What questions would assist within evaluation of IT security programmes........................21
Illustrate difficulties encountered while carrying out research on IT security programmes 21
Workshop 8....................................................................................................................................22
Identify ways in which secured software development assist John Dough Pizza................22
Workshop 9....................................................................................................................................22
Task 1: What kind of devices will be used for defending trespassing?................................22
Task 2: Why halon-based fire technologies are not helpful?...............................................23
Task 3: How fire triangle is adequate within IT security.....................................................23
Workshop 11..................................................................................................................................24
1. Illustrate 5 assets for John Dough Pizza.....................................................................24
2. Specify major incident that create influence on asset.................................................24
3. Illustrate impact of incident........................................................................................25
4. Take into account “incident response actions” if incidence takes place:....................25
a. How to recognise that incident is taking place...........................................................25
b. Illustrate steps that can be taken when incident takes place.......................................26
c. Specify steps needed for recovering incident.............................................................26
4. Explicate ideal Job in context of job advertisement read............................................16
Workshop 7....................................................................................................................................16
1. List IT security programme for evaluation. List 5organisation and programmes
identified...............................................................................................................................16
2, 3. Identification of goals of programme and Illustrate 5 words for programme..............16
4. Illustrate one programme in depth..............................................................................18
5. Evaluate programme...................................................................................................18
1. Write introduction on IT security programme that is being examined.......................19
2. Goals of programme....................................................................................................19
3. Why programme is evaluated.....................................................................................19
4. Create a logic map for programme.............................................................................19
5. Formulate evaluation questions..................................................................................20
6. Write short statements.................................................................................................20
Discussions....................................................................................................................................21
What questions would assist within evaluation of IT security programmes........................21
Illustrate difficulties encountered while carrying out research on IT security programmes 21
Workshop 8....................................................................................................................................22
Identify ways in which secured software development assist John Dough Pizza................22
Workshop 9....................................................................................................................................22
Task 1: What kind of devices will be used for defending trespassing?................................22
Task 2: Why halon-based fire technologies are not helpful?...............................................23
Task 3: How fire triangle is adequate within IT security.....................................................23
Workshop 11..................................................................................................................................24
1. Illustrate 5 assets for John Dough Pizza.....................................................................24
2. Specify major incident that create influence on asset.................................................24
3. Illustrate impact of incident........................................................................................25
4. Take into account “incident response actions” if incidence takes place:....................25
a. How to recognise that incident is taking place...........................................................25
b. Illustrate steps that can be taken when incident takes place.......................................26
c. Specify steps needed for recovering incident.............................................................26
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

5 How incident reports will decline the influence to asset............................................26
6 Specify 3 steps that can lead to minimise influence of incident.................................26
Discussion......................................................................................................................................27
Specify incident along with overview of response actions..................................................27
How effectively incident response plan diminish influence of JOHN DOUGH..................27
Workshop 12..................................................................................................................................27
1. Role of AI in cyber security........................................................................................27
2. Role of data lakes in cyber eco-system.......................................................................28
3. Key challenges within deployment of blockchain......................................................28
4. Will you prefer edge computing above cloud.............................................................28
References......................................................................................................................................30
6 Specify 3 steps that can lead to minimise influence of incident.................................26
Discussion......................................................................................................................................27
Specify incident along with overview of response actions..................................................27
How effectively incident response plan diminish influence of JOHN DOUGH..................27
Workshop 12..................................................................................................................................27
1. Role of AI in cyber security........................................................................................27
2. Role of data lakes in cyber eco-system.......................................................................28
3. Key challenges within deployment of blockchain......................................................28
4. Will you prefer edge computing above cloud.............................................................28
References......................................................................................................................................30

Workshop 1
Exercise 1
Brief statement for addressing 27 cells of CNSS model
McCumber Cube also referred to as cybersecurity cube which is developed for
management of protecting domain, internet and network. This has three dimensions which are
based on information security, states of information and identification of expertise needed for
protection (Brunner, Mussmann and Breu, 2019). The 27 cells of cube are specified below:
1. Confidentiality/Policy/Storage: This can be attained by formulation of policies assist
students within having access to peculiar course content and access their own
information, grades and class work.
2. Confidentiality/Policy/Processing: Develop policies through which students can alter
their confidential data like user ID, password, user profile and many more aspects.
3. Confidentiality/Policy/Transmission: This involves policy that will restrict uploading as
well as downloading of personal documents and class work for peculiar authorized users
along with professor.
4. Confidentiality/Education/Storage: It has to be ensured that students go via orientation
that will teach them the ways they can secure their information by keeping their
credentials with them only (Chen and Zhu, 2019).
5. Confidentiality/Education/Processing: Educating professor and student related with
their confidential data private so that third person do not access or can alter the work.
6. Confidentiality/Education/Transmission: Illustrating students the ways in which they can
upload and download information from class as well as ensure that any kind of sensitive
information is not uploaded like assignment solution is not uploaded in discussion forum.
7. Confidentiality/Technology/Storage: Adequate security like firewall aids registered
professors and students for accessing class documents and data within peculiar access
ports.
8. Confidentiality/Technology/Processing: Ensuring that virus protection and firewall
assist professors and students within altering their personal information like profile and
User ID (Cockcroft, 2020).
1
Exercise 1
Brief statement for addressing 27 cells of CNSS model
McCumber Cube also referred to as cybersecurity cube which is developed for
management of protecting domain, internet and network. This has three dimensions which are
based on information security, states of information and identification of expertise needed for
protection (Brunner, Mussmann and Breu, 2019). The 27 cells of cube are specified below:
1. Confidentiality/Policy/Storage: This can be attained by formulation of policies assist
students within having access to peculiar course content and access their own
information, grades and class work.
2. Confidentiality/Policy/Processing: Develop policies through which students can alter
their confidential data like user ID, password, user profile and many more aspects.
3. Confidentiality/Policy/Transmission: This involves policy that will restrict uploading as
well as downloading of personal documents and class work for peculiar authorized users
along with professor.
4. Confidentiality/Education/Storage: It has to be ensured that students go via orientation
that will teach them the ways they can secure their information by keeping their
credentials with them only (Chen and Zhu, 2019).
5. Confidentiality/Education/Processing: Educating professor and student related with
their confidential data private so that third person do not access or can alter the work.
6. Confidentiality/Education/Transmission: Illustrating students the ways in which they can
upload and download information from class as well as ensure that any kind of sensitive
information is not uploaded like assignment solution is not uploaded in discussion forum.
7. Confidentiality/Technology/Storage: Adequate security like firewall aids registered
professors and students for accessing class documents and data within peculiar access
ports.
8. Confidentiality/Technology/Processing: Ensuring that virus protection and firewall
assist professors and students within altering their personal information like profile and
User ID (Cockcroft, 2020).
1

9. Confidentiality/Technology/Transmission: Malware software and virus runs scans on all
the information that has been uploaded on canvas servers.
10. Integrity/Policy/Storage: Creation of policies will lead to ensure that each users information
cannot be altered by third person intentionally or unintentionally (Dotsenko and et. al,
2019). Only peculiar users will be rendered access to it.
11. Integrity/Policy/Processing: Formulation of policies that will lead them to ensure that
users need to follow certain format when altering personal information like password.
12. Integrity/Policy/Transmission: Creation of rules which will assist authorized users for
making changes within personal information into canvas site.
13. Integrity/Education/Storage: Educating professors and students with reference to ways
in which they cannot cause any security issues while storage of information.
14. Integrity/Education/Processing: This involves educating people with reference to what,
how and where alterations can be made within canvas environment.
15. Integrity/Education/Transmission: This involves that while transmitting information
integrity is maintained and is not altered by intruder.
16. Integrity/Technology/Storage: Setting up technology through which all the uploaded
files within canvas site are complete and cannot be modified when uploaded (Dotsenko
and et. al, 2019).
17. Integrity/Technology/Processing: It has to be ensured that firewall allow alteration to
class data when it is required like being able to make post when it is needed.
18. Integrity/Technology/Transmission: Setting up installed technologies so that entire data
which is transmitted is attained completely.
19. Availability/Policy/Storage: Policies needed to enact so that information which is stored
within can be accessed by everyone in class but each must have their own credentials and a
peculiar format agreed upon.
20. Availability/Policy/Processing: Policies are liable for restricting editing of information
for enrolled professors and students.
21. Availability/Policy/Transmission: Creation of policies which will ensure that data is
being available for authorized users and they can only make downloads as well as make
upload when needed (Gangawane and et. al, 2019).
2
the information that has been uploaded on canvas servers.
10. Integrity/Policy/Storage: Creation of policies will lead to ensure that each users information
cannot be altered by third person intentionally or unintentionally (Dotsenko and et. al,
2019). Only peculiar users will be rendered access to it.
11. Integrity/Policy/Processing: Formulation of policies that will lead them to ensure that
users need to follow certain format when altering personal information like password.
12. Integrity/Policy/Transmission: Creation of rules which will assist authorized users for
making changes within personal information into canvas site.
13. Integrity/Education/Storage: Educating professors and students with reference to ways
in which they cannot cause any security issues while storage of information.
14. Integrity/Education/Processing: This involves educating people with reference to what,
how and where alterations can be made within canvas environment.
15. Integrity/Education/Transmission: This involves that while transmitting information
integrity is maintained and is not altered by intruder.
16. Integrity/Technology/Storage: Setting up technology through which all the uploaded
files within canvas site are complete and cannot be modified when uploaded (Dotsenko
and et. al, 2019).
17. Integrity/Technology/Processing: It has to be ensured that firewall allow alteration to
class data when it is required like being able to make post when it is needed.
18. Integrity/Technology/Transmission: Setting up installed technologies so that entire data
which is transmitted is attained completely.
19. Availability/Policy/Storage: Policies needed to enact so that information which is stored
within can be accessed by everyone in class but each must have their own credentials and a
peculiar format agreed upon.
20. Availability/Policy/Processing: Policies are liable for restricting editing of information
for enrolled professors and students.
21. Availability/Policy/Transmission: Creation of policies which will ensure that data is
being available for authorized users and they can only make downloads as well as make
upload when needed (Gangawane and et. al, 2019).
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

22. Availability/Education/Storage: Educate each professor and student related with how
and where information can be stored as well as accessed whenever this is needed.
Furthermore, they should not allow others to access their information.
23. Availability/Education/Processing:Students and teachers must be educated with respect
to ways in which they can change their information by making use of relevant
authorization and its availability (Gutta, 2019).
24. Availability/Education/Transmission: Adequate knowledge must be imparted to entities so
that they can transmit information to relevant areas and even do not cause any serious issues
accidentally.
25. Availability/Technology/Storage: This involves ensuring that technologies for setup that
will assist authorized users for having access to relevant information as per requirements.
26. Availability/Technology/Processing: Technology can be set up through which authorized
individuals like professors and students can alter their private information at any instance
of time.
27. Availability/Technology/Transmission: This involves ensuring that technology is being
installed that will not restrict authorized users from having access to downloads as well as
uploaded documents within the class site (Huang and et. al, 2019).
Exercise 2
Impact if information in system is compromised
This has been experienced by me and found that identity theft is a serious that has to be
taken into consideration. Identity theft is defined as fraudulent practice that involves making use
of name of other person and their personal information in order to have certain credits or carry
out any unauthorised practices. I have kept lots of personal information like some projects,
private photographs and office information but this will not be difficult for third person to steal
identity if they are able to get access within the system. Identity theft is one of the most serious
issues but a nightmare for dealing within context of social security issues. In case if information
present within my personal computer is compromised due to loss of credentials then someone
else can have access to my assignments and can pretend to be there by downloading them (Iwai
and et. al, 2020). In addition to this, if data within hard drive occurs then and it fails, in case if
3
and where information can be stored as well as accessed whenever this is needed.
Furthermore, they should not allow others to access their information.
23. Availability/Education/Processing:Students and teachers must be educated with respect
to ways in which they can change their information by making use of relevant
authorization and its availability (Gutta, 2019).
24. Availability/Education/Transmission: Adequate knowledge must be imparted to entities so
that they can transmit information to relevant areas and even do not cause any serious issues
accidentally.
25. Availability/Technology/Storage: This involves ensuring that technologies for setup that
will assist authorized users for having access to relevant information as per requirements.
26. Availability/Technology/Processing: Technology can be set up through which authorized
individuals like professors and students can alter their private information at any instance
of time.
27. Availability/Technology/Transmission: This involves ensuring that technology is being
installed that will not restrict authorized users from having access to downloads as well as
uploaded documents within the class site (Huang and et. al, 2019).
Exercise 2
Impact if information in system is compromised
This has been experienced by me and found that identity theft is a serious that has to be
taken into consideration. Identity theft is defined as fraudulent practice that involves making use
of name of other person and their personal information in order to have certain credits or carry
out any unauthorised practices. I have kept lots of personal information like some projects,
private photographs and office information but this will not be difficult for third person to steal
identity if they are able to get access within the system. Identity theft is one of the most serious
issues but a nightmare for dealing within context of social security issues. In case if information
present within my personal computer is compromised due to loss of credentials then someone
else can have access to my assignments and can pretend to be there by downloading them (Iwai
and et. al, 2020). In addition to this, if data within hard drive occurs then and it fails, in case if
3

there is no backup then i will lose my hard work for which I have given time. Furthermore,
memories will also be lost and everything that is present within the system.
Workshop 2
Exercise 1
Brief statements for producing whether firm needs new policies in context of new Assistance and
Access law
New policies can be introduced by CISO and CTO with reference to new law as it has
brought in some major reforms that will assist agencies within having intelligence as well as
evidence that they may aid them within delivering their operations. This involves enhancement
within industry cooperation law enforcement as well as security agencies (Jin and Wang, 2019).
It will also improvise computer access powers. This will assist
awesomeonlinegamethatkidslove.com to have surveillance activities that will enable them to
amplify the security levels related with activities carried out by them. It will enable them to have
enhanced obligations of business by rendering adequate interaction to services that will assist
agencies.
If Technical Assistance Request is provided to intercept message, will you comply it
When any TAR is provided then depending upon the situations that are being
experienced by business then it can be complied with. It will enable business to have civil
immunity with respect to services carried out by them with adequate assistance. The civil
immunity will be provided to them in case they comply with request as assistance.
Compare technical assistance request, technical capability notice and technical assistance notice
The voluntary request that is being issued from head of interception agency, ASIO
(Australian Security Intelligence Organisation), ASD (Australian Signals Directorate) or ASIS
(Australian Secret Intelligence Agency) for prescribed purpose is referred to as TAR (technical
assistance request).
Technical assistance notice denotes a compulsory notice that is being issued via ASIO or
head of interception agency, if a communication provider is requested to render assistance if
there capabilities permit them to do so (Johnson and et. al, 2020). With reference to this, provider
needs not to develop capabilities which are not possessed by them for complying with TAN.
4
memories will also be lost and everything that is present within the system.
Workshop 2
Exercise 1
Brief statements for producing whether firm needs new policies in context of new Assistance and
Access law
New policies can be introduced by CISO and CTO with reference to new law as it has
brought in some major reforms that will assist agencies within having intelligence as well as
evidence that they may aid them within delivering their operations. This involves enhancement
within industry cooperation law enforcement as well as security agencies (Jin and Wang, 2019).
It will also improvise computer access powers. This will assist
awesomeonlinegamethatkidslove.com to have surveillance activities that will enable them to
amplify the security levels related with activities carried out by them. It will enable them to have
enhanced obligations of business by rendering adequate interaction to services that will assist
agencies.
If Technical Assistance Request is provided to intercept message, will you comply it
When any TAR is provided then depending upon the situations that are being
experienced by business then it can be complied with. It will enable business to have civil
immunity with respect to services carried out by them with adequate assistance. The civil
immunity will be provided to them in case they comply with request as assistance.
Compare technical assistance request, technical capability notice and technical assistance notice
The voluntary request that is being issued from head of interception agency, ASIO
(Australian Security Intelligence Organisation), ASD (Australian Signals Directorate) or ASIS
(Australian Secret Intelligence Agency) for prescribed purpose is referred to as TAR (technical
assistance request).
Technical assistance notice denotes a compulsory notice that is being issued via ASIO or
head of interception agency, if a communication provider is requested to render assistance if
there capabilities permit them to do so (Johnson and et. al, 2020). With reference to this, provider
needs not to develop capabilities which are not possessed by them for complying with TAN.
4

Technical capability notice is being issued as a compulsory order jointly by Minister for
Communication and Attorney General, at request of ASIO. In case any provider is requested to
render assistance with reference to TCN then they must provide relevant assistance that
comprises of formulation of capabilities for providing adequate services.
Which needs to have quick actions by firm
Both TCN and TAN needs quick actions as it involves compulsory orders to which
communication providers have to comply to (Karimi and Peikar, 2019). But with reference to
TCN it becomes a time consuming process as in this case capabilities have to be developed that
will utilised for rendering assistance.
Exercise 2
Choose 3 principles from Australian Privacy Principles for on-line game that are utilised by
school children
There are 13 principles which can be utilised as per the requirements and to ensure the
security of information. With reference to on-line game, they are specified below:
Open and transparent management of personal information (APP 1): This is liable for
outlining requirements of APP entity for management of their personal information.
With reference to this, entity is liable for taking up reasonable steps for execution of
practices, systems and procedures. The entity must have up to date APP with reference
to ways in which personal information is being managed by them.
Collection of solicited personal information (APP3): This is liable for collecting
solicited personal information. The entity can only have information in case it is
reasonably crucial or is directly associated with activities or functionalities of
organization (Kaušpadienė, Ramanauskaitė and Čenys, 2019). The sensitive information
can be only gathered if the specification illustrated above is met and precise consent
from individual is attained. This must be collected in fair and lawful manner.
Security of personal information (APP 11): The entity needs to take relevant and
reasonable steps for protecting personal information that is being possessed by them
from any kind of interference, loss misuse, unauthorized access disclosure or
modification. With reference to this, entity need to make sure that information is de-
identified (Sennewald and Baillie, 2020).
5
Communication and Attorney General, at request of ASIO. In case any provider is requested to
render assistance with reference to TCN then they must provide relevant assistance that
comprises of formulation of capabilities for providing adequate services.
Which needs to have quick actions by firm
Both TCN and TAN needs quick actions as it involves compulsory orders to which
communication providers have to comply to (Karimi and Peikar, 2019). But with reference to
TCN it becomes a time consuming process as in this case capabilities have to be developed that
will utilised for rendering assistance.
Exercise 2
Choose 3 principles from Australian Privacy Principles for on-line game that are utilised by
school children
There are 13 principles which can be utilised as per the requirements and to ensure the
security of information. With reference to on-line game, they are specified below:
Open and transparent management of personal information (APP 1): This is liable for
outlining requirements of APP entity for management of their personal information.
With reference to this, entity is liable for taking up reasonable steps for execution of
practices, systems and procedures. The entity must have up to date APP with reference
to ways in which personal information is being managed by them.
Collection of solicited personal information (APP3): This is liable for collecting
solicited personal information. The entity can only have information in case it is
reasonably crucial or is directly associated with activities or functionalities of
organization (Kaušpadienė, Ramanauskaitė and Čenys, 2019). The sensitive information
can be only gathered if the specification illustrated above is met and precise consent
from individual is attained. This must be collected in fair and lawful manner.
Security of personal information (APP 11): The entity needs to take relevant and
reasonable steps for protecting personal information that is being possessed by them
from any kind of interference, loss misuse, unauthorized access disclosure or
modification. With reference to this, entity need to make sure that information is de-
identified (Sennewald and Baillie, 2020).
5
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Exercise 3
Approaches for improvisation of staff awareness
Employees are greatest assets as well as risk within each organisation in context of cyber
security. One intentional or unintentional click by staff member can destroy entire network.
Thereby improvisation of staff awareness is essential and must be a priority for each firm
(Subramanian, Neelakanteshwar and Purushothaman, 2020). Some of the approaches as per
ACSC site are mentioned beneath:
Promotion of processes and documentation
Designing a program
Utilizes examples to illustrate risk caused by any particular activity of staff
Keep it adequate
Board level buy in
Involve employees and get competitive
Promote safe behavior towards customers
Extension of training to suppliers
Measure the outcome.
Workshop 3
1. Define physical security
The protection of physical assets, property and people from actions as well as events that
can lead to loss or damage is referred to as physical security. This involves networks, data,
hardware and software from any kind of loss (Turel, Xu and Guo, 2020). It also comprises of
protecting firm or agency from vandalism, natural disaster, fire, terrorism, theft and burglary.
2. List issues that can take place while managing physical security of art gallery
a. Creation of 5 issues
The art gallery is vulnerable to following physical security issues, they are mentioned
below:
Unauthorized access to storeroom
Accidental damage of art work
Weak control over keys
6
Approaches for improvisation of staff awareness
Employees are greatest assets as well as risk within each organisation in context of cyber
security. One intentional or unintentional click by staff member can destroy entire network.
Thereby improvisation of staff awareness is essential and must be a priority for each firm
(Subramanian, Neelakanteshwar and Purushothaman, 2020). Some of the approaches as per
ACSC site are mentioned beneath:
Promotion of processes and documentation
Designing a program
Utilizes examples to illustrate risk caused by any particular activity of staff
Keep it adequate
Board level buy in
Involve employees and get competitive
Promote safe behavior towards customers
Extension of training to suppliers
Measure the outcome.
Workshop 3
1. Define physical security
The protection of physical assets, property and people from actions as well as events that
can lead to loss or damage is referred to as physical security. This involves networks, data,
hardware and software from any kind of loss (Turel, Xu and Guo, 2020). It also comprises of
protecting firm or agency from vandalism, natural disaster, fire, terrorism, theft and burglary.
2. List issues that can take place while managing physical security of art gallery
a. Creation of 5 issues
The art gallery is vulnerable to following physical security issues, they are mentioned
below:
Unauthorized access to storeroom
Accidental damage of art work
Weak control over keys
6

Lack of reports
Inadequate passwords within system to prevent loss
3. Carry out risk assessment for issue identified
The major risk upon which art gallery need to think on is inadequate passwords in
their system.
a. Probable risks associated with issue
Within each organisation there are some aspects in terms of private or confidential
information like employee’s details, customers information, strategies, stakes, stakeholders,
financial assets and many more which adds value to ways in which operations are being carried
out by art gallery (Wang, Che and Jing, 2019). But in case if this information is compromised
then what impact will it have on their functions. For an example, if third person get access to
their information then there is higher probability that they will misuse this. Thus, it is important
to acknowledge that they have strong passwords in their system so that it becomes difficult for
intruder to access their confidential information.
4. Legal & ethical issues while developing new policies
The legal aspects associated with issue are that personal information about company or
their assets must not be compromised due to the mistakes of organisation or due to internal
personnel. The ethics comprises of right and wrong which must be taken into consideration while
formulation of policies (Killer, Rodrigues and Stiller, 2019). An example can be taken to
understand this aspect like if weak passwords like admin or name of person is used then it will be
not a difficult task to get into the system of art gallery.
a. Concerns related with legal as well as ethical concerns
These issues can be controlled by opting for usage of precise and adequate security
policies that will assist to minimise overall impact which will be created. Legal and ethical
aspects have to be taken into consideration by art gallery to ensure that their information is not
vulnerable to any external or internal threats. The major concern is hacking, identity theft and
malicious attacks which can take place due to weak passwords easily.
5. Develop physical security policies
Systems are vulnerable to attacks which make it important to assess vulnerabilities that
have to be remediated (Kirti and et. al, 2020). The purpose of policy is to illustrate assessments
7
Inadequate passwords within system to prevent loss
3. Carry out risk assessment for issue identified
The major risk upon which art gallery need to think on is inadequate passwords in
their system.
a. Probable risks associated with issue
Within each organisation there are some aspects in terms of private or confidential
information like employee’s details, customers information, strategies, stakes, stakeholders,
financial assets and many more which adds value to ways in which operations are being carried
out by art gallery (Wang, Che and Jing, 2019). But in case if this information is compromised
then what impact will it have on their functions. For an example, if third person get access to
their information then there is higher probability that they will misuse this. Thus, it is important
to acknowledge that they have strong passwords in their system so that it becomes difficult for
intruder to access their confidential information.
4. Legal & ethical issues while developing new policies
The legal aspects associated with issue are that personal information about company or
their assets must not be compromised due to the mistakes of organisation or due to internal
personnel. The ethics comprises of right and wrong which must be taken into consideration while
formulation of policies (Killer, Rodrigues and Stiller, 2019). An example can be taken to
understand this aspect like if weak passwords like admin or name of person is used then it will be
not a difficult task to get into the system of art gallery.
a. Concerns related with legal as well as ethical concerns
These issues can be controlled by opting for usage of precise and adequate security
policies that will assist to minimise overall impact which will be created. Legal and ethical
aspects have to be taken into consideration by art gallery to ensure that their information is not
vulnerable to any external or internal threats. The major concern is hacking, identity theft and
malicious attacks which can take place due to weak passwords easily.
5. Develop physical security policies
Systems are vulnerable to attacks which make it important to assess vulnerabilities that
have to be remediated (Kirti and et. al, 2020). The purpose of policy is to illustrate assessments
7

within Art Gallery System assessments are conducted for identification of weaknesses as an
outcome of weak authentication, sensitive information leakage, mis-configuration and many
more. Identification and subsequent mitigation of issues will restrict attack surface of Art gallery
both internally as well as externally and satisfy compliance with adequate policies.
6. Formulate structure of policy document from SANS policies
1. Illustrate new security policies
The new policy will protect system of art gallery from unauthenticated access via third
person and even the employees of organisation (Ključnikov¹, Mura, and Sklenár, 2019). This can
be attained by formulating policies with respect to what can be accessed by whom with respect to
their roles and responsibilities in the gallery.
a. Specify policy name
System security policy
b. What is policy based on
It will be based on securing the assets of art gallery by making use of strong
passwords and having certain access restrictions depending upon operations that have to be
carried out by employees of art gallery.
c. How much existent policies can be reused
There are certain extents up to which policy can be reused as password aspects were
specified. For an example employees were told to use strong passwords so that they can be
cracked easily but they used same for their systems (Kordestani, Chaibakhsh and Saif, 2020).
Thus for having restrictions the system programming can be altered that would only take
alphanumeric passwords as it will be difficult to break them. It will lead to prevent attacks
like brute force, hit and trail and even dictionary attacks.
d. Risks that will be addressed by policy
The policy will address the major risk associated with weak password and
unauthenticated access within the systems.
e. Success of policy
By making use of access controls and alphanumeric passwords up to some extent
security attacks can be prevented by ensuring that third person do not get access into system.
8
outcome of weak authentication, sensitive information leakage, mis-configuration and many
more. Identification and subsequent mitigation of issues will restrict attack surface of Art gallery
both internally as well as externally and satisfy compliance with adequate policies.
6. Formulate structure of policy document from SANS policies
1. Illustrate new security policies
The new policy will protect system of art gallery from unauthenticated access via third
person and even the employees of organisation (Ključnikov¹, Mura, and Sklenár, 2019). This can
be attained by formulating policies with respect to what can be accessed by whom with respect to
their roles and responsibilities in the gallery.
a. Specify policy name
System security policy
b. What is policy based on
It will be based on securing the assets of art gallery by making use of strong
passwords and having certain access restrictions depending upon operations that have to be
carried out by employees of art gallery.
c. How much existent policies can be reused
There are certain extents up to which policy can be reused as password aspects were
specified. For an example employees were told to use strong passwords so that they can be
cracked easily but they used same for their systems (Kordestani, Chaibakhsh and Saif, 2020).
Thus for having restrictions the system programming can be altered that would only take
alphanumeric passwords as it will be difficult to break them. It will lead to prevent attacks
like brute force, hit and trail and even dictionary attacks.
d. Risks that will be addressed by policy
The policy will address the major risk associated with weak password and
unauthenticated access within the systems.
e. Success of policy
By making use of access controls and alphanumeric passwords up to some extent
security attacks can be prevented by ensuring that third person do not get access into system.
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Furthermore, if more than 3 attempts will be made to logging into systems then IT
department will have information about that and the account or system will be locked for
preventing any kind of harm to network.
Discuss that IT security policies taken are enough that can be adapted within distinct security
environment
With the advancement in technology the attackers are finding out new ways to get into
system so to say that respective security policy is enough to prevent system form attacks is
enough then it will be wrong (White,, Hewitt and Kruck, 2019). The manner in which attackers
alter their ways to get into the system similarly policies must be modified or something new must
be added within them so that systems can be prevented from attack. For an example if dictionary
attack will not help them to crack the passwords then they opt for hit and trial or dictionary and
even use Trojan horse to enter into the system. So by taking into consideration all the aspects
policies must be made and altered with time so that systems do not get vulnerable.
Workshop 4
2. Identification of peculiar security management issues that prevails in JOHN DOUGH
JOHN DOUGH facing various issues related with security, they are specified below:
In 2014, the disgruntled franchisee has deleted all orders from database and all sales
history.
2015, the PC of management was stolen from franchise at the time of burglary. This
contained financial information, software along with configuration files.
In 2016, accidentally email was sent by manager of firm to the entire customer by making
use of automated newsletter script that is liable for copy paste into email client as well as
sends the message without making use of BCC.
2017, the company that was doing marketing for firm (JOHN DOUGH) was provided
will credentials for customer database. This was suspected that the copy of them was
taken up by one of the employees and have attained by scammers.
In 2018, power outage occurred for 6 hours, the UPS were installed but they also
maintained operations of technical staff for around 30 minutes.
9
department will have information about that and the account or system will be locked for
preventing any kind of harm to network.
Discuss that IT security policies taken are enough that can be adapted within distinct security
environment
With the advancement in technology the attackers are finding out new ways to get into
system so to say that respective security policy is enough to prevent system form attacks is
enough then it will be wrong (White,, Hewitt and Kruck, 2019). The manner in which attackers
alter their ways to get into the system similarly policies must be modified or something new must
be added within them so that systems can be prevented from attack. For an example if dictionary
attack will not help them to crack the passwords then they opt for hit and trial or dictionary and
even use Trojan horse to enter into the system. So by taking into consideration all the aspects
policies must be made and altered with time so that systems do not get vulnerable.
Workshop 4
2. Identification of peculiar security management issues that prevails in JOHN DOUGH
JOHN DOUGH facing various issues related with security, they are specified below:
In 2014, the disgruntled franchisee has deleted all orders from database and all sales
history.
2015, the PC of management was stolen from franchise at the time of burglary. This
contained financial information, software along with configuration files.
In 2016, accidentally email was sent by manager of firm to the entire customer by making
use of automated newsletter script that is liable for copy paste into email client as well as
sends the message without making use of BCC.
2017, the company that was doing marketing for firm (JOHN DOUGH) was provided
will credentials for customer database. This was suspected that the copy of them was
taken up by one of the employees and have attained by scammers.
In 2018, power outage occurred for 6 hours, the UPS were installed but they also
maintained operations of technical staff for around 30 minutes.
9

2019, the malware infection within the network permitted unidentified hacker for having
access to their systems. This involved remote access tool as well as key logger but it is
not known that for how long this occurred.
3. Identify types of controls within chapter
The security documentation is taken into consideration so that relevant consideration can
be regarded with respect to operations carried out by JOHN DOUGH while delivering their
services (Yang and et. al, 2019). The controls mentioned within this are:
Strategies for cyber security
Security documentation and its maintenance
Relevant system security plan
Incident response plan
Continuous monitoring plan
Security assessment report
Plan of actions along with milestones
4. Statement that summarizes current levels for compliance with Government
JOHN DOUGH do not have any such policy for securing their system or operations that
are carried out by them and that is the probable reasons that each year they face one or the other
issue related with their working (Kumah, Yaokumah, and Okai, 2019). Though they have
systems, Proprietary JOHN DOUGH Systems and Stock & ingredients management system
which are managed by back or head office but they pretend that they are completely automated
but as per employees they are manually maintained.
5. What immediate action is required by JOHN DOUGH to improvise security
It is necessary for firm to take some actions with respect to problems they are going
through so that affirmative implications can be attained. The quick action that can be taken up
involves formulation of security policies with respect to operations that are carried out by them
instead of expanding their operations (Lander, and Sondhi, 2019). The major aspect that they can
emphasize is that their ordering system is build by making use of legacy code but it is becoming
un-maintainable so it has to be maintained before it becomes vulnerable to any kind of attacks.
All with this they need to update their systems as they have not been updated from years which
makes them more vulnerable to attacks.
10
access to their systems. This involved remote access tool as well as key logger but it is
not known that for how long this occurred.
3. Identify types of controls within chapter
The security documentation is taken into consideration so that relevant consideration can
be regarded with respect to operations carried out by JOHN DOUGH while delivering their
services (Yang and et. al, 2019). The controls mentioned within this are:
Strategies for cyber security
Security documentation and its maintenance
Relevant system security plan
Incident response plan
Continuous monitoring plan
Security assessment report
Plan of actions along with milestones
4. Statement that summarizes current levels for compliance with Government
JOHN DOUGH do not have any such policy for securing their system or operations that
are carried out by them and that is the probable reasons that each year they face one or the other
issue related with their working (Kumah, Yaokumah, and Okai, 2019). Though they have
systems, Proprietary JOHN DOUGH Systems and Stock & ingredients management system
which are managed by back or head office but they pretend that they are completely automated
but as per employees they are manually maintained.
5. What immediate action is required by JOHN DOUGH to improvise security
It is necessary for firm to take some actions with respect to problems they are going
through so that affirmative implications can be attained. The quick action that can be taken up
involves formulation of security policies with respect to operations that are carried out by them
instead of expanding their operations (Lander, and Sondhi, 2019). The major aspect that they can
emphasize is that their ordering system is build by making use of legacy code but it is becoming
un-maintainable so it has to be maintained before it becomes vulnerable to any kind of attacks.
All with this they need to update their systems as they have not been updated from years which
makes them more vulnerable to attacks.
10

The controls illustrated are reasonable for business or they overkill
The controls which are illustrated above are adequate with respect to JOHN DOUGH as
the firm do not have any security plan in case if any problem occurs then it is necessary to have a
backup through which risks associated can be mitigated. Incident response plan will assist firm
to respond in an adequate manner with respect to situation that will occur within working
environment (Lee, Han and Yoo, 2019). With reference to this, it will comprise the likeability of
incidents which may occur in future and formulate respective response for same. A simple
example can be taken to acknowledge this aspect like it is predicted that dictionary attack may
occur in future as a response they can formulae the policy that words from dictionary should not
used as a password within the system.
How firm can comply with ISM
The organisation has not opted for any precise policy, they aims at expanding their
operations instead of updating or maintaining their operations. Thus, it will be difficult for JOHN
DOUGH to comply with information security management. It will be a time consuming process
as for this management need to identify all the critical aspects related with their operations and
even minute details must be taken into consideration. This is the only way they can have secured
system and ensure that security aspects are not compromised.
How to prove compliance with ISM
Information security management can be ensured by following strict policies by
monitoring their activities while they are making use of network. In addition to this, if they do
not comply with them then there should be serious penalties like by clicking on unauthenticated
networks they make their system prone to attacks (Li, Liu and Spini, 2019). The small steps can
be taken up by JOHN DOUGH to ensure that they comply with the ISM and also update their
system on continuous basis to eliminate any kind of vulnerabilities within them.
11
The controls which are illustrated above are adequate with respect to JOHN DOUGH as
the firm do not have any security plan in case if any problem occurs then it is necessary to have a
backup through which risks associated can be mitigated. Incident response plan will assist firm
to respond in an adequate manner with respect to situation that will occur within working
environment (Lee, Han and Yoo, 2019). With reference to this, it will comprise the likeability of
incidents which may occur in future and formulate respective response for same. A simple
example can be taken to acknowledge this aspect like it is predicted that dictionary attack may
occur in future as a response they can formulae the policy that words from dictionary should not
used as a password within the system.
How firm can comply with ISM
The organisation has not opted for any precise policy, they aims at expanding their
operations instead of updating or maintaining their operations. Thus, it will be difficult for JOHN
DOUGH to comply with information security management. It will be a time consuming process
as for this management need to identify all the critical aspects related with their operations and
even minute details must be taken into consideration. This is the only way they can have secured
system and ensure that security aspects are not compromised.
How to prove compliance with ISM
Information security management can be ensured by following strict policies by
monitoring their activities while they are making use of network. In addition to this, if they do
not comply with them then there should be serious penalties like by clicking on unauthenticated
networks they make their system prone to attacks (Li, Liu and Spini, 2019). The small steps can
be taken up by JOHN DOUGH to ensure that they comply with the ISM and also update their
system on continuous basis to eliminate any kind of vulnerabilities within them.
11
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.
Workshop 5
1. By usage of internet identify job hunting website
There are various websites which are being utilized by individuals for identification of
appropriate job as per their qualification. They are: Adzuna, CareerOne, CareerJet, Gumtree,
Indeed Australia, JobActive powered by JobSearch, GradConnection, Job Seeker and many more
that aids people to have jobs as per their requirements. There are various job roles with reference
to IT and individuals can apply for them as per their qualifications.
2. List 10 titles which are advertised
They are specified below:
1. IT Systems Administrator
2. DBA MS SQL
3. IT Graduate developer
4. System Administrator
5. Information Technology Technician
6. IT Support Technician
7. IT/POS Technician
8. IT Salesperson
9. Senior ICT Support Officer
10. IT Systems/Network Administrator
3. Identify qualification needed for job
A, b, c Qualification, desired or mandatory and Industry certification or degree
Role Qualification Mandatory or Desired Degree or Certification
IT Systems
Administrator
Minimum diploma in IT
system administrations
Working experience in
window OS, networking
systems, basic proficiency
with bash commands in
Linux
Mandatory Degree
DBA MS SQL Bachelors in Computer Mandatory Degree
12
1. By usage of internet identify job hunting website
There are various websites which are being utilized by individuals for identification of
appropriate job as per their qualification. They are: Adzuna, CareerOne, CareerJet, Gumtree,
Indeed Australia, JobActive powered by JobSearch, GradConnection, Job Seeker and many more
that aids people to have jobs as per their requirements. There are various job roles with reference
to IT and individuals can apply for them as per their qualifications.
2. List 10 titles which are advertised
They are specified below:
1. IT Systems Administrator
2. DBA MS SQL
3. IT Graduate developer
4. System Administrator
5. Information Technology Technician
6. IT Support Technician
7. IT/POS Technician
8. IT Salesperson
9. Senior ICT Support Officer
10. IT Systems/Network Administrator
3. Identify qualification needed for job
A, b, c Qualification, desired or mandatory and Industry certification or degree
Role Qualification Mandatory or Desired Degree or Certification
IT Systems
Administrator
Minimum diploma in IT
system administrations
Working experience in
window OS, networking
systems, basic proficiency
with bash commands in
Linux
Mandatory Degree
DBA MS SQL Bachelors in Computer Mandatory Degree
12
science with experience in
SQL Server 2012 – 2017
IT Graduate developer Diploma holder or
graduate
Desired Degree
System Administrator Bachelor’s degree in
computer engineering with
minimum 3 to 5 years
experience
Mandatory Both degree and
certification (CompTIA
Security+ and CompTIA
Network+)
Information
Technology Technician
Minimum Certificate IV
within IT and experience
in IT position
Desired CPR Certificate
(HLTAID001), First Aid
Certificate (HLTAID004)
Chief Information
Security Officer
Bachelors degree with IT
Security experience of
minimum 7 years with
ceryification
Mandatory Degree and certification in
CISSP
IT/POS Technician Graduation in IT
Experience in maintenance
of network and system
Desired
Mandatory
Degree
ICT Coordinator Graduation in Computer
science with experience in
different configuration of
network servers, VMWare
and Microsoft Servers
Mandatory Degree
Senior ICT Support
Officer
Post graduation in IT or
Computer science with at
least 3 years on experience
as a technical support
Mandatory Degree
IT Systems/Network
Administrator
Bachelors degree of
engineering with minimum
5 years experience
Mandatory Degree
4. Rank the qualification
The minimum qualification that is needed is diploma in information technology and post
graduation in CS or information technology depending upon requirements of peculiar profile. In
addition to this, there is need for certification in some jobs and if it is not mandatory then it still
13
SQL Server 2012 – 2017
IT Graduate developer Diploma holder or
graduate
Desired Degree
System Administrator Bachelor’s degree in
computer engineering with
minimum 3 to 5 years
experience
Mandatory Both degree and
certification (CompTIA
Security+ and CompTIA
Network+)
Information
Technology Technician
Minimum Certificate IV
within IT and experience
in IT position
Desired CPR Certificate
(HLTAID001), First Aid
Certificate (HLTAID004)
Chief Information
Security Officer
Bachelors degree with IT
Security experience of
minimum 7 years with
ceryification
Mandatory Degree and certification in
CISSP
IT/POS Technician Graduation in IT
Experience in maintenance
of network and system
Desired
Mandatory
Degree
ICT Coordinator Graduation in Computer
science with experience in
different configuration of
network servers, VMWare
and Microsoft Servers
Mandatory Degree
Senior ICT Support
Officer
Post graduation in IT or
Computer science with at
least 3 years on experience
as a technical support
Mandatory Degree
IT Systems/Network
Administrator
Bachelors degree of
engineering with minimum
5 years experience
Mandatory Degree
4. Rank the qualification
The minimum qualification that is needed is diploma in information technology and post
graduation in CS or information technology depending upon requirements of peculiar profile. In
addition to this, there is need for certification in some jobs and if it is not mandatory then it still
13

counts within experience that will further lead to enhancement within their knowledge as well as
have hike in their salaries.
5. Identification of 3 required industry certification
Certifications enhances the value of CV as it denotes that candidate have relevant
knowledge with reference to job profile they have applied for. The 3 certifications are illustrated
below:
1. CPR Certificate HLTAID001
2. CompTIA Security+
3. CompTIA Network+
6. Write description of ideal candidate
The candidate who possesses both desired as well as mandatory qualification will serve
as an ideal candidate but if they have some certifications with respect to particular role then they
can easily grab the particular job easily.
1. Identify role that has to be fulfilled
With respect to JOHN DOUGH, the crucial details are specified below:
a. Specify role of title
Chief Information Security Officer
2. Illustrate what other firms are doing in reference to needs of role with identical title
Each firm is looking forward to have a best candidate for peculiar job role as it will
enable them to carry out their operations as per requirements of organization. In case they
arebale to identify the ideal candidate then they will be able to have risk as well as management
that will enable firm like JOHN DOUGH to manage security services alleviate and automate
applications. They can also foresee the security challenges as well as risk management
(Циклаури and et. al, 2019). They will also enable organisation to have architecture
development, remote and mobile management, network security and many more. To have all the
critical assets and prevent their firm from any kind of security issues, it is necessary that
adequate measures are being taken to identify probable candidate for the position of CISO.
3. Qualification that is expected
The minimum requirement for role of Chief Information Security Officer is bachelor’s
degree in Cyber Security, Computer Science or any other related domain. Employees also
14
have hike in their salaries.
5. Identification of 3 required industry certification
Certifications enhances the value of CV as it denotes that candidate have relevant
knowledge with reference to job profile they have applied for. The 3 certifications are illustrated
below:
1. CPR Certificate HLTAID001
2. CompTIA Security+
3. CompTIA Network+
6. Write description of ideal candidate
The candidate who possesses both desired as well as mandatory qualification will serve
as an ideal candidate but if they have some certifications with respect to particular role then they
can easily grab the particular job easily.
1. Identify role that has to be fulfilled
With respect to JOHN DOUGH, the crucial details are specified below:
a. Specify role of title
Chief Information Security Officer
2. Illustrate what other firms are doing in reference to needs of role with identical title
Each firm is looking forward to have a best candidate for peculiar job role as it will
enable them to carry out their operations as per requirements of organization. In case they
arebale to identify the ideal candidate then they will be able to have risk as well as management
that will enable firm like JOHN DOUGH to manage security services alleviate and automate
applications. They can also foresee the security challenges as well as risk management
(Циклаури and et. al, 2019). They will also enable organisation to have architecture
development, remote and mobile management, network security and many more. To have all the
critical assets and prevent their firm from any kind of security issues, it is necessary that
adequate measures are being taken to identify probable candidate for the position of CISO.
3. Qualification that is expected
The minimum requirement for role of Chief Information Security Officer is bachelor’s
degree in Cyber Security, Computer Science or any other related domain. Employees also
14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

demand that CISO must have Master’s degree within IT security. MBA degree is also pursued by
candidates but there has to be knowledge about principles along with practices (Limba and et. al,
2019). MBA with certification in IT Forensics, IT and Cyber Security can also be taken. Along
with this there are various certification programs which must have been acquired by potential
candidates; they are CCISO, CISSP, CISM, OSCP, CISA, CEH, CGIET and GSLC. Apart from
this, role of CISO cannot be attained if there is no relevant experience with reference to
technical foundation, it is minimum 7 years.
4. Explicate ideal Job in context of job advertisement read
JOHN DOUGH is working as a locally owned chain for pizza stores who have 3
company stores and are looking forward to expand their operations. They are one of the
recognized pizza delivery services (Limba and et. al, 2019). We need CISO for interim basis for
development of security strategies that involves processes, technology and people.
Responsibilities
Formulate as well as render security strategies at global level for monitoring, cultural
awareness and GRC.
Collaborate with vendors to have best services and tools for rendering relevant
operations.
Develop foundation for security team that will comprise of hybrid SOC model by
working closely with monitoring partners.
Key Skills
Enterprise level cybersecurity knowledge at higher levels
Ability to interact with C-suite level executives and technical teams.
Acknowledge inhouse along with outsourced SOCs
Workshop 7
1. List IT security programme for evaluation. List 5organisation and programmes identified
The different organisations along with their programs are specified below:
EIT Digital: Cyber Security Program
CyberSecOp: Security Program Risk Management
15
candidates but there has to be knowledge about principles along with practices (Limba and et. al,
2019). MBA with certification in IT Forensics, IT and Cyber Security can also be taken. Along
with this there are various certification programs which must have been acquired by potential
candidates; they are CCISO, CISSP, CISM, OSCP, CISA, CEH, CGIET and GSLC. Apart from
this, role of CISO cannot be attained if there is no relevant experience with reference to
technical foundation, it is minimum 7 years.
4. Explicate ideal Job in context of job advertisement read
JOHN DOUGH is working as a locally owned chain for pizza stores who have 3
company stores and are looking forward to expand their operations. They are one of the
recognized pizza delivery services (Limba and et. al, 2019). We need CISO for interim basis for
development of security strategies that involves processes, technology and people.
Responsibilities
Formulate as well as render security strategies at global level for monitoring, cultural
awareness and GRC.
Collaborate with vendors to have best services and tools for rendering relevant
operations.
Develop foundation for security team that will comprise of hybrid SOC model by
working closely with monitoring partners.
Key Skills
Enterprise level cybersecurity knowledge at higher levels
Ability to interact with C-suite level executives and technical teams.
Acknowledge inhouse along with outsourced SOCs
Workshop 7
1. List IT security programme for evaluation. List 5organisation and programmes identified
The different organisations along with their programs are specified below:
EIT Digital: Cyber Security Program
CyberSecOp: Security Program Risk Management
15
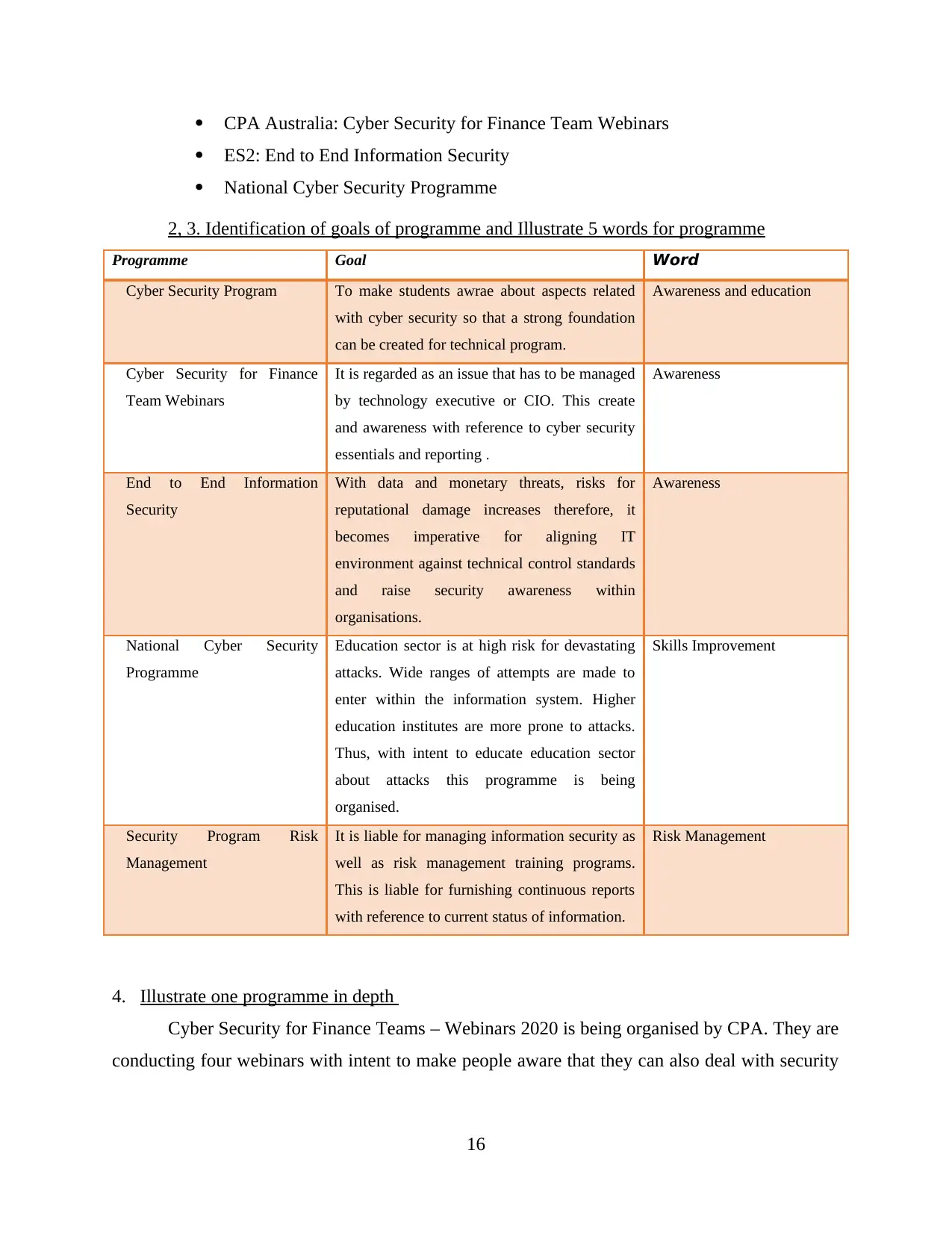
CPA Australia: Cyber Security for Finance Team Webinars
ES2: End to End Information Security
National Cyber Security Programme
2, 3. Identification of goals of programme and Illustrate 5 words for programme
Programme Goal Word
Cyber Security Program To make students awrae about aspects related
with cyber security so that a strong foundation
can be created for technical program.
Awareness and education
Cyber Security for Finance
Team Webinars
It is regarded as an issue that has to be managed
by technology executive or CIO. This create
and awareness with reference to cyber security
essentials and reporting .
Awareness
End to End Information
Security
With data and monetary threats, risks for
reputational damage increases therefore, it
becomes imperative for aligning IT
environment against technical control standards
and raise security awareness within
organisations.
Awareness
National Cyber Security
Programme
Education sector is at high risk for devastating
attacks. Wide ranges of attempts are made to
enter within the information system. Higher
education institutes are more prone to attacks.
Thus, with intent to educate education sector
about attacks this programme is being
organised.
Skills Improvement
Security Program Risk
Management
It is liable for managing information security as
well as risk management training programs.
This is liable for furnishing continuous reports
with reference to current status of information.
Risk Management
4. Illustrate one programme in depth
Cyber Security for Finance Teams – Webinars 2020 is being organised by CPA. They are
conducting four webinars with intent to make people aware that they can also deal with security
16
ES2: End to End Information Security
National Cyber Security Programme
2, 3. Identification of goals of programme and Illustrate 5 words for programme
Programme Goal Word
Cyber Security Program To make students awrae about aspects related
with cyber security so that a strong foundation
can be created for technical program.
Awareness and education
Cyber Security for Finance
Team Webinars
It is regarded as an issue that has to be managed
by technology executive or CIO. This create
and awareness with reference to cyber security
essentials and reporting .
Awareness
End to End Information
Security
With data and monetary threats, risks for
reputational damage increases therefore, it
becomes imperative for aligning IT
environment against technical control standards
and raise security awareness within
organisations.
Awareness
National Cyber Security
Programme
Education sector is at high risk for devastating
attacks. Wide ranges of attempts are made to
enter within the information system. Higher
education institutes are more prone to attacks.
Thus, with intent to educate education sector
about attacks this programme is being
organised.
Skills Improvement
Security Program Risk
Management
It is liable for managing information security as
well as risk management training programs.
This is liable for furnishing continuous reports
with reference to current status of information.
Risk Management
4. Illustrate one programme in depth
Cyber Security for Finance Teams – Webinars 2020 is being organised by CPA. They are
conducting four webinars with intent to make people aware that they can also deal with security
16

threats and it is not only responsibility of technical executives (Logan, 2020). The webinars are
specified below:
Significance of cybersecurity: This will render three major key reasons that is being
played by finance team within protection of organization and what they can do for
protecting information assets of firm.
Cybersecurity essentials for finance team: This will provide an overview of common
cyber as well as information threats that are being faced by finance team and ways in
which they can processes their activities for reducing the overall risk.
Building culture of cybersecurity in finance team: To minimize risk, organizations
need to formulate as well as embrace enterprise wide security culture and finance team
must not be an exception (McCoy, 2019). Within this team will eb provided with more
secured working culture.
Cyber Security reporting for finance team: The CFO might find them reporting to board
with reference finance items along with financial risk, cyber insurance which results from
cyber threat as this pertains to certain finance.
5. Evaluate programme
The program can be evaluated with reference to performance attained by employees
while delivering their services within organisation and ways in which they dealt with issues that
occurred (Brunner, Mussmann and Breu, 2019). Along with this, it will enable to identify any
event which may occur while delivering their services and they will also make sure that they will
not click on any unauthenticated link as it may have malicious program. Some questions have
been specified beneath:
What is the objective of program?
What are the needs of population that have been targeted?
Where the problem lies?
How the program is executed?
Is there any alternative method to deliver the program?
1. Write introduction on IT security programme that is being examined
The AISEP (Australasian Information Security Evaluation Program) is liable for
evaluation of products for protecting their systems along with information against any kind of
cyber threats which takes place (Chen and Zhu, 2019). Then these evaluation activities will be
17
specified below:
Significance of cybersecurity: This will render three major key reasons that is being
played by finance team within protection of organization and what they can do for
protecting information assets of firm.
Cybersecurity essentials for finance team: This will provide an overview of common
cyber as well as information threats that are being faced by finance team and ways in
which they can processes their activities for reducing the overall risk.
Building culture of cybersecurity in finance team: To minimize risk, organizations
need to formulate as well as embrace enterprise wide security culture and finance team
must not be an exception (McCoy, 2019). Within this team will eb provided with more
secured working culture.
Cyber Security reporting for finance team: The CFO might find them reporting to board
with reference finance items along with financial risk, cyber insurance which results from
cyber threat as this pertains to certain finance.
5. Evaluate programme
The program can be evaluated with reference to performance attained by employees
while delivering their services within organisation and ways in which they dealt with issues that
occurred (Brunner, Mussmann and Breu, 2019). Along with this, it will enable to identify any
event which may occur while delivering their services and they will also make sure that they will
not click on any unauthenticated link as it may have malicious program. Some questions have
been specified beneath:
What is the objective of program?
What are the needs of population that have been targeted?
Where the problem lies?
How the program is executed?
Is there any alternative method to deliver the program?
1. Write introduction on IT security programme that is being examined
The AISEP (Australasian Information Security Evaluation Program) is liable for
evaluation of products for protecting their systems along with information against any kind of
cyber threats which takes place (Chen and Zhu, 2019). Then these evaluation activities will be
17
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

certified via ACA (Australasian Certification Authority). CCRA (Common Criteria Recognition
Arrangement) is an international partner that is certification authority that mutually recognises
certified products of one other.
2. Goals of programme
Organisation looks forward for purchasing products that will enable them to decide
whether independent assurance is required for security features of products. The purchasers can
examine data that is available within CPL like Security Target and Certification Report for each
product that is intended to be purchased. When ACA will be will be requested then draft version
will be provided of Security Target to probable New Zealand or Australian purchasers while
product is under evaluation.
3. Why programme is evaluated
It is assessed to identify the features rendered by the programme. It will enable them to
evaluate flaw with reference to remediation process that will render enhanced levels of
continuing assurance which is not offered by those products. The AISEF (Australasian
Information Security Evaluation Facility) illustrates a commercial facility that is being licensed
for carrying out evaluation (Cockcroft, 2020). This assists within identification of success of
earlier steps that are involved within policy development cycle. This will lead to ensure that
policy will lead to attain desired results or not. It also assists within identification that whether
things can been carried out in better manner in future.
4. Create a logic map for programme
The tool that is utilised for illustrating how program have to work is referred to as
program logic map. Basically, it unpacks logic underpinning the ways in which program is being
evaluated that aids team within considering the ways in which enhanced outcomes can be
attained for articulation of precise narrative for initiative choice (Dotsenko and et. al, 2019). It
illustrates diagram sequence that will illustrate sequence of anticipated consequences.
18
Arrangement) is an international partner that is certification authority that mutually recognises
certified products of one other.
2. Goals of programme
Organisation looks forward for purchasing products that will enable them to decide
whether independent assurance is required for security features of products. The purchasers can
examine data that is available within CPL like Security Target and Certification Report for each
product that is intended to be purchased. When ACA will be will be requested then draft version
will be provided of Security Target to probable New Zealand or Australian purchasers while
product is under evaluation.
3. Why programme is evaluated
It is assessed to identify the features rendered by the programme. It will enable them to
evaluate flaw with reference to remediation process that will render enhanced levels of
continuing assurance which is not offered by those products. The AISEF (Australasian
Information Security Evaluation Facility) illustrates a commercial facility that is being licensed
for carrying out evaluation (Cockcroft, 2020). This assists within identification of success of
earlier steps that are involved within policy development cycle. This will lead to ensure that
policy will lead to attain desired results or not. It also assists within identification that whether
things can been carried out in better manner in future.
4. Create a logic map for programme
The tool that is utilised for illustrating how program have to work is referred to as
program logic map. Basically, it unpacks logic underpinning the ways in which program is being
evaluated that aids team within considering the ways in which enhanced outcomes can be
attained for articulation of precise narrative for initiative choice (Dotsenko and et. al, 2019). It
illustrates diagram sequence that will illustrate sequence of anticipated consequences.
18
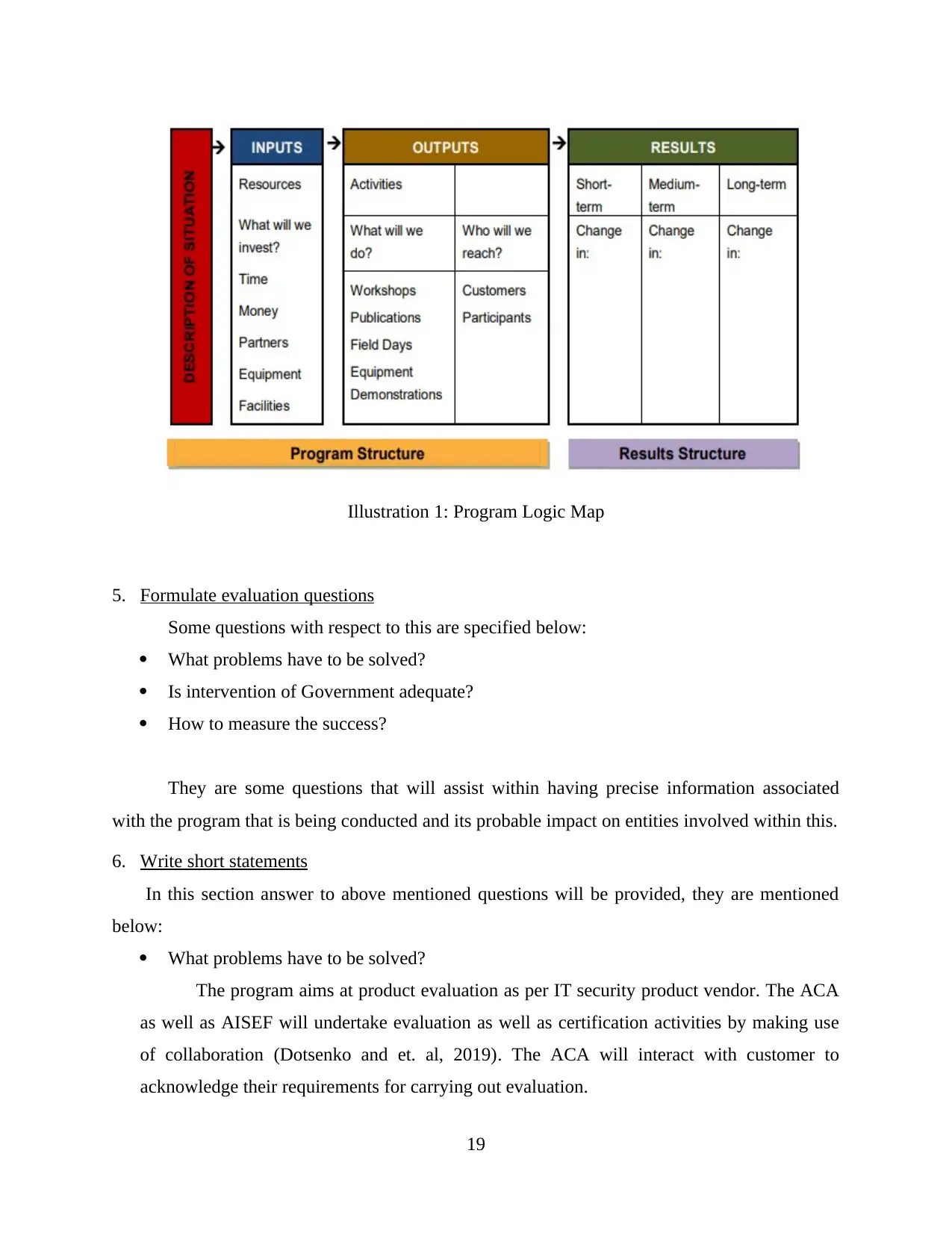
Illustration 1: Program Logic Map
5. Formulate evaluation questions
Some questions with respect to this are specified below:
What problems have to be solved?
Is intervention of Government adequate?
How to measure the success?
They are some questions that will assist within having precise information associated
with the program that is being conducted and its probable impact on entities involved within this.
6. Write short statements
In this section answer to above mentioned questions will be provided, they are mentioned
below:
What problems have to be solved?
The program aims at product evaluation as per IT security product vendor. The ACA
as well as AISEF will undertake evaluation as well as certification activities by making use
of collaboration (Dotsenko and et. al, 2019). The ACA will interact with customer to
acknowledge their requirements for carrying out evaluation.
19
5. Formulate evaluation questions
Some questions with respect to this are specified below:
What problems have to be solved?
Is intervention of Government adequate?
How to measure the success?
They are some questions that will assist within having precise information associated
with the program that is being conducted and its probable impact on entities involved within this.
6. Write short statements
In this section answer to above mentioned questions will be provided, they are mentioned
below:
What problems have to be solved?
The program aims at product evaluation as per IT security product vendor. The ACA
as well as AISEF will undertake evaluation as well as certification activities by making use
of collaboration (Dotsenko and et. al, 2019). The ACA will interact with customer to
acknowledge their requirements for carrying out evaluation.
19

Is intervention of Government adequate?
The intervention from is adequate as all the stakeholders involved within this are
government organizations and agencies who will furnish relevant services. The Government
is liable for development of PP’s for technical groups.
How to measure the success?
The DSD (Defence Signals Directorate) certifies that outcome of evaluation tasks that
are being carried under program. These certification services are furnished via DSD to
government. The successful completion of certification will be published on EPL (Evaluated
Products List) within DSD website.
Discussions
What questions would assist within evaluation of IT security programmes
There are various questions that will aid within having precise and relevant information
related with the program. They are mentioned below:
What are the problems that have to be solved?
Where the problem lies?
What is adequate plan of action for addressing problems?
How to recognize success?
Are the activities that are being delivered are intended?
Is there any alternative method for delivering activities?
What are net effects created by program?
What will be the influence of cessation?
They are some questions that can assist within formulation of program and ensure the
ways in which it can executed. Along with alternative methods should also be regarded
(Gangawane and et. al, 2019).
Illustrate difficulties encountered while carrying out research on IT security programmes
It is not easy to identify which organisations are carrying out which programme until and
unless some outsiders are allowed to be the part of it. Along with this, there were various
program which were conducted but the one that involves cyber security was critical to identify as
20
The intervention from is adequate as all the stakeholders involved within this are
government organizations and agencies who will furnish relevant services. The Government
is liable for development of PP’s for technical groups.
How to measure the success?
The DSD (Defence Signals Directorate) certifies that outcome of evaluation tasks that
are being carried under program. These certification services are furnished via DSD to
government. The successful completion of certification will be published on EPL (Evaluated
Products List) within DSD website.
Discussions
What questions would assist within evaluation of IT security programmes
There are various questions that will aid within having precise and relevant information
related with the program. They are mentioned below:
What are the problems that have to be solved?
Where the problem lies?
What is adequate plan of action for addressing problems?
How to recognize success?
Are the activities that are being delivered are intended?
Is there any alternative method for delivering activities?
What are net effects created by program?
What will be the influence of cessation?
They are some questions that can assist within formulation of program and ensure the
ways in which it can executed. Along with alternative methods should also be regarded
(Gangawane and et. al, 2019).
Illustrate difficulties encountered while carrying out research on IT security programmes
It is not easy to identify which organisations are carrying out which programme until and
unless some outsiders are allowed to be the part of it. Along with this, there were various
program which were conducted but the one that involves cyber security was critical to identify as
20
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

all the information was not available like goal, purpose and intent behind carrying out the
program.
Workshop 8
Identify ways in which secured software development assist John Dough Pizza
For this software development lifecycle can be utilised by the firm to ensure that all the
aspects work in an adequate manner as per desired security standards. But while execution of
SDLC and ensure that success is attained security measures must be implemented within them
(Gutta, 2019). This can be attained by incorporating industry standard security model within the
requirement phase of SDLC, personnel must be educated with reference to software security
within the same phase, as per this training rendered responsibilities must be assigned. Security
focused requirement collection must be performed by establishing comprehensive risk
management processes. Within design phase of SDLC, architecture review can be performed
along with threat modelling and code reviews can be conducted while execution. This is the
phase in which peculiar requirements for setting up password can be implemented (like
minimum length and alphanumeric words). Within the verification stage, test plans can be
conducted, perform penetration test and also make certain attacks to get into the system. When
testing is completed successfully software can be deployed within working environment of
JOHN DOUGH. This will enable organisation to have secured system.
Workshop 9
Task 1: What kind of devices will be used for defending trespassing?
The computer crime which involves unlawful access for systems possessed by an
organisation or individual is referred to as trespassing. It refers to accessing computer without
authentication for gaining financial information or any other data related with entity which is
protected within system. Though there are various devices that can be utilised for preventing
trespassing, they are gats, signs, trees and fence (Huang and et. al, 2019). With respect to
defending casual trespassing, fencing is an appropriate option. It denotes process associated with
isolation of nodes present within computer cluster or protection of shared resources when it
appears within malfunctioning. When number of nodes present in cluster increases then the
likelihood associated with their failure also increases at one or other time frame. The failed node
possess control above shared resources that must be reclaimed and in case node acts erratically
21
program.
Workshop 8
Identify ways in which secured software development assist John Dough Pizza
For this software development lifecycle can be utilised by the firm to ensure that all the
aspects work in an adequate manner as per desired security standards. But while execution of
SDLC and ensure that success is attained security measures must be implemented within them
(Gutta, 2019). This can be attained by incorporating industry standard security model within the
requirement phase of SDLC, personnel must be educated with reference to software security
within the same phase, as per this training rendered responsibilities must be assigned. Security
focused requirement collection must be performed by establishing comprehensive risk
management processes. Within design phase of SDLC, architecture review can be performed
along with threat modelling and code reviews can be conducted while execution. This is the
phase in which peculiar requirements for setting up password can be implemented (like
minimum length and alphanumeric words). Within the verification stage, test plans can be
conducted, perform penetration test and also make certain attacks to get into the system. When
testing is completed successfully software can be deployed within working environment of
JOHN DOUGH. This will enable organisation to have secured system.
Workshop 9
Task 1: What kind of devices will be used for defending trespassing?
The computer crime which involves unlawful access for systems possessed by an
organisation or individual is referred to as trespassing. It refers to accessing computer without
authentication for gaining financial information or any other data related with entity which is
protected within system. Though there are various devices that can be utilised for preventing
trespassing, they are gats, signs, trees and fence (Huang and et. al, 2019). With respect to
defending casual trespassing, fencing is an appropriate option. It denotes process associated with
isolation of nodes present within computer cluster or protection of shared resources when it
appears within malfunctioning. When number of nodes present in cluster increases then the
likelihood associated with their failure also increases at one or other time frame. The failed node
possess control above shared resources that must be reclaimed and in case node acts erratically
21

then rest of system has to be secured. Fencing is liable for either disabling nodes or disallowing
the shared access storage for maintaining integrity of data.
Task 2: Why halon-based fire technologies are not helpful?
Halon 1301 was used as fire suppressants within high value assets can be damaged by
making use of traditional sprinkler systems. But in 1989, it was identified that it is liable for
depletion of ozone layer and after this US Environmental Protection Agency banned
manufacturing of Halon 1301 in 1994 (Iwai and et. al, 2020). It went well with information
technology as this was utilised within data centres, museums, surgical suites, data centres and
various other locations where water dependent suppressants can cause damage electronics or
within archival collections. These were replaced by halocarbon compounds, clean agents, water
mist system and inert gas.
Task 3: How fire triangle is adequate within IT security
The way in which security controls can be prioritized is referred to as data breach triangle
or fire triangle. This involves three major entities, if any one of these is eradicated then breach
can be prevented (Jin and Wang, 2019). The entities are:
Data: This is equivalent to fuel, data that can be misused or stolen.
Exploit: The aggregation of an exploit or vulnerability that assist attacker within having
unapproved access for information stored within the system.
Egress: The path through which information can leave firm. This can be digital like
physical such as stolen hard drive or portable storage.
Illustration 2: Fire Triangle
22
the shared access storage for maintaining integrity of data.
Task 2: Why halon-based fire technologies are not helpful?
Halon 1301 was used as fire suppressants within high value assets can be damaged by
making use of traditional sprinkler systems. But in 1989, it was identified that it is liable for
depletion of ozone layer and after this US Environmental Protection Agency banned
manufacturing of Halon 1301 in 1994 (Iwai and et. al, 2020). It went well with information
technology as this was utilised within data centres, museums, surgical suites, data centres and
various other locations where water dependent suppressants can cause damage electronics or
within archival collections. These were replaced by halocarbon compounds, clean agents, water
mist system and inert gas.
Task 3: How fire triangle is adequate within IT security
The way in which security controls can be prioritized is referred to as data breach triangle
or fire triangle. This involves three major entities, if any one of these is eradicated then breach
can be prevented (Jin and Wang, 2019). The entities are:
Data: This is equivalent to fuel, data that can be misused or stolen.
Exploit: The aggregation of an exploit or vulnerability that assist attacker within having
unapproved access for information stored within the system.
Egress: The path through which information can leave firm. This can be digital like
physical such as stolen hard drive or portable storage.
Illustration 2: Fire Triangle
22

The security controls need to be mapped with triangle and if one side is broken then
breach can be prevented. For an instance data masking or encryption removes information.
Proactive and patch management controls can be used for preventing exploits. Portable devices
or egress filtering is liable for preventing egress (Johnson and et. al, 2020). When high –value
networks are involved then egress filtering furnish key for control to eradicate exploits.
Workshop 11
1. Illustrate 5 assets for John Dough Pizza
The major assets of organisation are: Automated Stock Management System, Ordering
system, Proprietary system, database and network connections.
2. Specify major incident that create influence on asset
The occurrences of events that create an influence on assets are mentioned below:
Automated Stock Management System: The system has not been updated by years this
means that it is highly exploitable.
Ordering system: If any of the employees share their details either intentionally or
unintentionally or become prone to shoulder surfing attack then the possibility of identity
theft can take place.
Proprietary system: The system faced maintenance issues, there is a probability that they
may lose the entire information stored within.
Database: It is the critical asset which have to be maintained as if third person gets an
access to their database then all the details related with inventory, warehouse, customers,
employees, suppliers and other information will be accessed by them which will lead to
creation of worse impact (Kaušpadienė, Ramanauskaitė and Čenys, 2019).
Network Connections: The single wrong click made by employees will make entire
network vulnerable to attacks that means one system is compromised then there will be
higher probability that all the systems will be affected.
Network connection is one of the major asset which if compromised will make each asset
vulnerable to attacks.
23
breach can be prevented. For an instance data masking or encryption removes information.
Proactive and patch management controls can be used for preventing exploits. Portable devices
or egress filtering is liable for preventing egress (Johnson and et. al, 2020). When high –value
networks are involved then egress filtering furnish key for control to eradicate exploits.
Workshop 11
1. Illustrate 5 assets for John Dough Pizza
The major assets of organisation are: Automated Stock Management System, Ordering
system, Proprietary system, database and network connections.
2. Specify major incident that create influence on asset
The occurrences of events that create an influence on assets are mentioned below:
Automated Stock Management System: The system has not been updated by years this
means that it is highly exploitable.
Ordering system: If any of the employees share their details either intentionally or
unintentionally or become prone to shoulder surfing attack then the possibility of identity
theft can take place.
Proprietary system: The system faced maintenance issues, there is a probability that they
may lose the entire information stored within.
Database: It is the critical asset which have to be maintained as if third person gets an
access to their database then all the details related with inventory, warehouse, customers,
employees, suppliers and other information will be accessed by them which will lead to
creation of worse impact (Kaušpadienė, Ramanauskaitė and Čenys, 2019).
Network Connections: The single wrong click made by employees will make entire
network vulnerable to attacks that means one system is compromised then there will be
higher probability that all the systems will be affected.
Network connection is one of the major asset which if compromised will make each asset
vulnerable to attacks.
23
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

3. Illustrate impact of incident
The influence that is caused by incident will be worse. This has already taken place in
2019 where network assisted unidentified hacker to enter within system of JOHN DOUGH. This
can take place again as employees are not provided with adequate training with reference to what
they have to do and are not aware about cyber security. For this, at least they must know the fact
that unauthenticated links must not be clicked as it will lead third person to have access to entire
information (Karimi and Peikar, 2019). But along with this, there has to be a firewall installed so
that such mails are not attained and if this happens they must be filtered. If network will be
compromised then all the systems associated with this will be hacked along with this, the
confidential information will be in the hands of intruder who may utilised this carrying out
illegal practices or sell it to their competitors.
4. Take into account “incident response actions” if incidence takes place:
a. How to recognise that incident is taking place
It will be difficult for employees to access it but if any link is blocked by system but
again and again they are trying to get into system them it must be informed to technical
department of organisation. In addition to this, the CISO must render adequate training to
employees so that they can have its details (Sennewald and Baillie, 2020). Furthermore, technical
team of JOHN DOUGH must monitor all the activities that take place within the network.
b. Illustrate steps that can be taken when incident takes place
The initial step to prevent network attack is to amke use of strong passwords within the
system and furnishes adequate training to employees that will enable them to acknowledge some
activities are being carried out within their system. In addition to this, the login credentials must
be changed on continuous basis and it must be strong enough so that they cannot be cracked
through usage of hit and trail or dictionary attack (Subramanian, Neelakanteshwar and
Purushothaman, 2020). The technical need to ensure that when messages are transmitted then
they is in an encrypted form so that even if third person gets an access to system then also they
are not able to have access to the information.
c. Specify steps needed for recovering incident
This involves various steps, they are specified below:
Verification of attack that has taken place on the network.
24
The influence that is caused by incident will be worse. This has already taken place in
2019 where network assisted unidentified hacker to enter within system of JOHN DOUGH. This
can take place again as employees are not provided with adequate training with reference to what
they have to do and are not aware about cyber security. For this, at least they must know the fact
that unauthenticated links must not be clicked as it will lead third person to have access to entire
information (Karimi and Peikar, 2019). But along with this, there has to be a firewall installed so
that such mails are not attained and if this happens they must be filtered. If network will be
compromised then all the systems associated with this will be hacked along with this, the
confidential information will be in the hands of intruder who may utilised this carrying out
illegal practices or sell it to their competitors.
4. Take into account “incident response actions” if incidence takes place:
a. How to recognise that incident is taking place
It will be difficult for employees to access it but if any link is blocked by system but
again and again they are trying to get into system them it must be informed to technical
department of organisation. In addition to this, the CISO must render adequate training to
employees so that they can have its details (Sennewald and Baillie, 2020). Furthermore, technical
team of JOHN DOUGH must monitor all the activities that take place within the network.
b. Illustrate steps that can be taken when incident takes place
The initial step to prevent network attack is to amke use of strong passwords within the
system and furnishes adequate training to employees that will enable them to acknowledge some
activities are being carried out within their system. In addition to this, the login credentials must
be changed on continuous basis and it must be strong enough so that they cannot be cracked
through usage of hit and trail or dictionary attack (Subramanian, Neelakanteshwar and
Purushothaman, 2020). The technical need to ensure that when messages are transmitted then
they is in an encrypted form so that even if third person gets an access to system then also they
are not able to have access to the information.
c. Specify steps needed for recovering incident
This involves various steps, they are specified below:
Verification of attack that has taken place on the network.
24

Take the network down but this will also hamper the operations of organization
along with their positioning within the marketplace.
Clean all the systems which have been attacked as well as restore them.
Close the vulnerabilities which were liable for giving access to the network of
JOHN DOUGH.
5 How incident reports will decline the influence to asset
The actions that have been specified above are enough to minimise the impact that is
being created. For an instance if firewall will be installed then the unauthenticated person will be
restricted. Even in case they get access to system then strong passwords will block them to have
access to information stored within the computer (White,, Hewitt and Kruck, 2019).
Furthermore, if passwords are cracked then also encryption will prevent them from accessing
information. When various attempts are being made intruder then, the technical department will
be able to identify that malicious activities are conducted within peculiar system. But employees
need to ensure that they do not click on any unauthenticated link.
6 Specify 3 steps that can lead to minimise influence of incident
Make use of firewall and antivirus
Ensure that each system have alphanumeric password that comprises of 8 bits
Make use of encryption to store and transmit information
Discussion
Specify incident along with overview of response actions
When incident occurred then system was switched though it created a negative impact on
organisation but it also prevented from loose of information due to compromise in network
(Yang and et. al, 2019). After this, all the systems are cleaned for elimination of any trace of
virus or any malicious activity that can lead to hamper the operations of JOHN DOUGH again.
How effectively incident response plan diminish influence of JOHN DOUGH
Though it cannot be measured that how much information have been compromised but in
case attack has been identified at earliest then there will be hardly any lose that firm have to bear.
But when the entire network will go down then there will be impact on their position within the
marketplace and there may be trust issues among customers as once there have been an attempt
to access their information, this can take place again (Kumah, Yaokumah, and Okai, 2019).
25
along with their positioning within the marketplace.
Clean all the systems which have been attacked as well as restore them.
Close the vulnerabilities which were liable for giving access to the network of
JOHN DOUGH.
5 How incident reports will decline the influence to asset
The actions that have been specified above are enough to minimise the impact that is
being created. For an instance if firewall will be installed then the unauthenticated person will be
restricted. Even in case they get access to system then strong passwords will block them to have
access to information stored within the computer (White,, Hewitt and Kruck, 2019).
Furthermore, if passwords are cracked then also encryption will prevent them from accessing
information. When various attempts are being made intruder then, the technical department will
be able to identify that malicious activities are conducted within peculiar system. But employees
need to ensure that they do not click on any unauthenticated link.
6 Specify 3 steps that can lead to minimise influence of incident
Make use of firewall and antivirus
Ensure that each system have alphanumeric password that comprises of 8 bits
Make use of encryption to store and transmit information
Discussion
Specify incident along with overview of response actions
When incident occurred then system was switched though it created a negative impact on
organisation but it also prevented from loose of information due to compromise in network
(Yang and et. al, 2019). After this, all the systems are cleaned for elimination of any trace of
virus or any malicious activity that can lead to hamper the operations of JOHN DOUGH again.
How effectively incident response plan diminish influence of JOHN DOUGH
Though it cannot be measured that how much information have been compromised but in
case attack has been identified at earliest then there will be hardly any lose that firm have to bear.
But when the entire network will go down then there will be impact on their position within the
marketplace and there may be trust issues among customers as once there have been an attempt
to access their information, this can take place again (Kumah, Yaokumah, and Okai, 2019).
25

Workshop 12
1. Role of AI in cyber security
Firms pay attention for their network security and are aware about the fact that even a
small cyber attack can lead to massive impact. For securing infrastructure firms makes use of
wide range of multiple lines of defence (Turel, Xu and Guo, 2020). The initial is firewall and
other is antivirus software for elimination of malicious codes. AI will enable firms to have
peculiar features in context of cyber security.
Firms can track as well as respond to adequate security incidents by making use of
advanced tools.
It will detect malicious activities as well as prevent systems from any kind of cyber
attacks which may occur within the system.
Artificial intelligence will improvise human analysis which involves detection of
malicious attack that varies till protection of endpoints where information is being
utilized.
Automating mundane security tasks will be used and there will be not be even a single
zero day vulnerability (Wang, Che and Jing, 2019).
2. Role of data lakes in cyber eco-system
The repository which is designed for storing large amount of information within the
native form is referred to as Data Lake. It can be in unstructured, semi-structured or in structured
format that comprises of system logs, tables, text files and many more (Lander, and Sondhi,
2019) (Lee, Han and Yoo, 2019). The key capabilities that can be attained by usage of Data Lake
within cyber eco-system are specified below:
Automated Collection: With wide range of networking, security, mobile devices and
computer types within firms, automated gathering process furnish practical way for
keeping data up to date. When data will be attained then this will be parsed. For this
large parser library is necessary so that it can support enhanced range of security
protocols within networking devices, security applications, devices and computers.
Security context: The security data lake assists within organization of log files as well as
enrich within contextual data. When intruder will logging from unknown system then it
26
1. Role of AI in cyber security
Firms pay attention for their network security and are aware about the fact that even a
small cyber attack can lead to massive impact. For securing infrastructure firms makes use of
wide range of multiple lines of defence (Turel, Xu and Guo, 2020). The initial is firewall and
other is antivirus software for elimination of malicious codes. AI will enable firms to have
peculiar features in context of cyber security.
Firms can track as well as respond to adequate security incidents by making use of
advanced tools.
It will detect malicious activities as well as prevent systems from any kind of cyber
attacks which may occur within the system.
Artificial intelligence will improvise human analysis which involves detection of
malicious attack that varies till protection of endpoints where information is being
utilized.
Automating mundane security tasks will be used and there will be not be even a single
zero day vulnerability (Wang, Che and Jing, 2019).
2. Role of data lakes in cyber eco-system
The repository which is designed for storing large amount of information within the
native form is referred to as Data Lake. It can be in unstructured, semi-structured or in structured
format that comprises of system logs, tables, text files and many more (Lander, and Sondhi,
2019) (Lee, Han and Yoo, 2019). The key capabilities that can be attained by usage of Data Lake
within cyber eco-system are specified below:
Automated Collection: With wide range of networking, security, mobile devices and
computer types within firms, automated gathering process furnish practical way for
keeping data up to date. When data will be attained then this will be parsed. For this
large parser library is necessary so that it can support enhanced range of security
protocols within networking devices, security applications, devices and computers.
Security context: The security data lake assists within organization of log files as well as
enrich within contextual data. When intruder will logging from unknown system then it
26
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
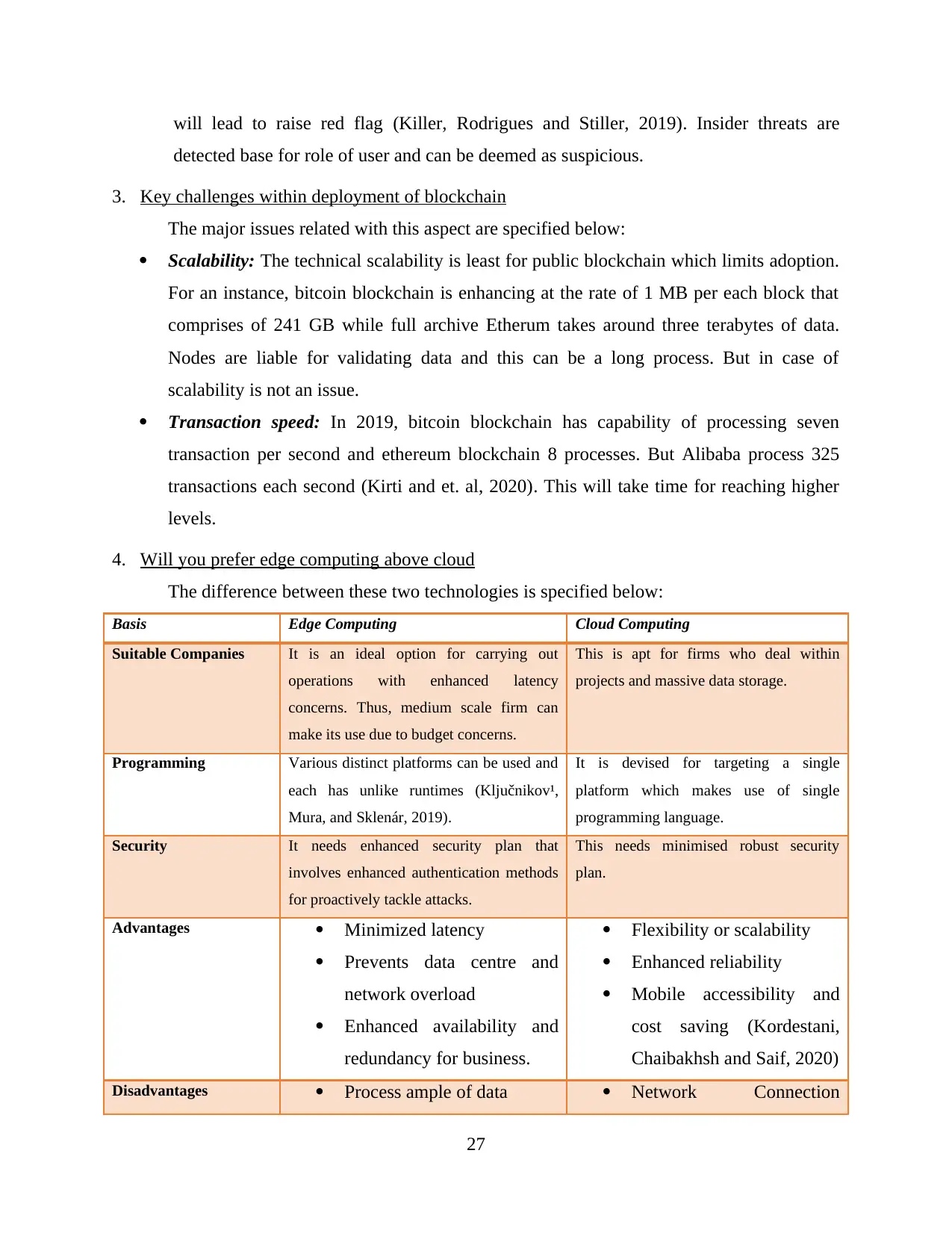
will lead to raise red flag (Killer, Rodrigues and Stiller, 2019). Insider threats are
detected base for role of user and can be deemed as suspicious.
3. Key challenges within deployment of blockchain
The major issues related with this aspect are specified below:
Scalability: The technical scalability is least for public blockchain which limits adoption.
For an instance, bitcoin blockchain is enhancing at the rate of 1 MB per each block that
comprises of 241 GB while full archive Etherum takes around three terabytes of data.
Nodes are liable for validating data and this can be a long process. But in case of
scalability is not an issue.
Transaction speed: In 2019, bitcoin blockchain has capability of processing seven
transaction per second and ethereum blockchain 8 processes. But Alibaba process 325
transactions each second (Kirti and et. al, 2020). This will take time for reaching higher
levels.
4. Will you prefer edge computing above cloud
The difference between these two technologies is specified below:
Basis Edge Computing Cloud Computing
Suitable Companies It is an ideal option for carrying out
operations with enhanced latency
concerns. Thus, medium scale firm can
make its use due to budget concerns.
This is apt for firms who deal within
projects and massive data storage.
Programming Various distinct platforms can be used and
each has unlike runtimes (Ključnikov¹,
Mura, and Sklenár, 2019).
It is devised for targeting a single
platform which makes use of single
programming language.
Security It needs enhanced security plan that
involves enhanced authentication methods
for proactively tackle attacks.
This needs minimised robust security
plan.
Advantages Minimized latency
Prevents data centre and
network overload
Enhanced availability and
redundancy for business.
Flexibility or scalability
Enhanced reliability
Mobile accessibility and
cost saving (Kordestani,
Chaibakhsh and Saif, 2020)
Disadvantages Process ample of data Network Connection
27
detected base for role of user and can be deemed as suspicious.
3. Key challenges within deployment of blockchain
The major issues related with this aspect are specified below:
Scalability: The technical scalability is least for public blockchain which limits adoption.
For an instance, bitcoin blockchain is enhancing at the rate of 1 MB per each block that
comprises of 241 GB while full archive Etherum takes around three terabytes of data.
Nodes are liable for validating data and this can be a long process. But in case of
scalability is not an issue.
Transaction speed: In 2019, bitcoin blockchain has capability of processing seven
transaction per second and ethereum blockchain 8 processes. But Alibaba process 325
transactions each second (Kirti and et. al, 2020). This will take time for reaching higher
levels.
4. Will you prefer edge computing above cloud
The difference between these two technologies is specified below:
Basis Edge Computing Cloud Computing
Suitable Companies It is an ideal option for carrying out
operations with enhanced latency
concerns. Thus, medium scale firm can
make its use due to budget concerns.
This is apt for firms who deal within
projects and massive data storage.
Programming Various distinct platforms can be used and
each has unlike runtimes (Ključnikov¹,
Mura, and Sklenár, 2019).
It is devised for targeting a single
platform which makes use of single
programming language.
Security It needs enhanced security plan that
involves enhanced authentication methods
for proactively tackle attacks.
This needs minimised robust security
plan.
Advantages Minimized latency
Prevents data centre and
network overload
Enhanced availability and
redundancy for business.
Flexibility or scalability
Enhanced reliability
Mobile accessibility and
cost saving (Kordestani,
Chaibakhsh and Saif, 2020)
Disadvantages Process ample of data Network Connection
27

Real time processing Dependency
Loss of control
Both of them are two different approaches not substitutes. When they are utilised in
conjunction then edge and cloud computing assist the architecture within storing as well as
processing data in an efficacious manner.
28
Loss of control
Both of them are two different approaches not substitutes. When they are utilised in
conjunction then edge and cloud computing assist the architecture within storing as well as
processing data in an efficacious manner.
28

References
Books and Journals
Brunner, M., Mussmann, A. and Breu, R., 2019, April. Enabling change-driven workflows in
continuous information security management. In Proceedings of the 34th ACM/SIGAPP
Symposium on Applied Computing (pp. 1924-1933).
Chen, J. and Zhu, Q., 2019. Interdependent strategic security risk management with bounded
rationality in the internet of things. IEEE Transactions on Information Forensics and
Security, 14(11), pp.2958-2971.
Cockcroft, S., 2020. Securing the commercial Internet: Lessons learned in developing a
postgraduate course in information security management. Journal of Information Systems
Education, 13(3), p.7.
Dotsenko, S. and et. al, 2019. Integrated Security Management System for Enterprises in
Industry 4.0. Information & Security, 43(1), pp.294-304.
Dotsenko, S. and Kharchenko, et. al, 2019. Integrated Model of Knowledge Management for
Security of Information Technologies: Standards ISO/IEC 15408 and ISO/IEC
18045. Information & Security, 43(1), pp.305-317.
Gangawane, J.V. and et. al, 2019. Single logout functionality for a multi-tenant identity and data
security management cloud service. U.S. Patent 10,511,589.
Gutta, R.R., 2019. Managing Security Objectives for Effective Organizational Performance
Information Security Management (Doctoral dissertation, Walden University).
Huang, H.Y. and et. al, 2019. Security management for data systems. U.S. Patent Application
15/789,529.
Iwai, M. and et. al, 2020. Data security management based on device locations and connection
states. U.S. Patent 10,621,373.
Jin, Q. and Wang, L., 2019, July. Intranet User-Level Security Traffic Management with Deep
Reinforcement Learning. In 2019 International Joint Conference on Neural Networks
(IJCNN) (pp. 1-8). IEEE.
Johnson, R.A. and et. al, 2020. User interface features for enterprise security management. U.S.
Patent 10,652,280.
Karimi, Z. and Peikar, H.R., 2019. Information Security Management: The Impacts of
Organizational Commitment and Perceived Consequences of Security Breach on the
Intention of Patients’ Information Security Violation. Medical Ethics Journal, 13(44),
pp.1-10.
Kaušpadienė, L., Ramanauskaitė, S. and Čenys, A., 2019. Information security management
framework suitability estimation for small and medium enterprise. Technological and
Economic Development of Economy, 25(5), pp.979-997.
Killer, C., Rodrigues, B. and Stiller, B., 2019, May. Security Management and Visualization in a
Blockchain-based Collaborative Defense. In 2019 IEEE International Conference on
Blockchain and Cryptocurrency (ICBC) (pp. 108-111). IEEE.
Kirti, G. and et. al, 2020. Techniques for discovering and managing security of applications.
U.S. Patent 10,536,478.
Ključnikov¹, A., Mura, L. and Sklenár, D., 2019. Information security management in SMEs:
Factors of success.
Kordestani, M., Chaibakhsh, A. and Saif, M., 2020. SMS–A Security Management System for
Steam Turbines Using a Multisensor Array. IEEE Systems Journal.
29
Books and Journals
Brunner, M., Mussmann, A. and Breu, R., 2019, April. Enabling change-driven workflows in
continuous information security management. In Proceedings of the 34th ACM/SIGAPP
Symposium on Applied Computing (pp. 1924-1933).
Chen, J. and Zhu, Q., 2019. Interdependent strategic security risk management with bounded
rationality in the internet of things. IEEE Transactions on Information Forensics and
Security, 14(11), pp.2958-2971.
Cockcroft, S., 2020. Securing the commercial Internet: Lessons learned in developing a
postgraduate course in information security management. Journal of Information Systems
Education, 13(3), p.7.
Dotsenko, S. and et. al, 2019. Integrated Security Management System for Enterprises in
Industry 4.0. Information & Security, 43(1), pp.294-304.
Dotsenko, S. and Kharchenko, et. al, 2019. Integrated Model of Knowledge Management for
Security of Information Technologies: Standards ISO/IEC 15408 and ISO/IEC
18045. Information & Security, 43(1), pp.305-317.
Gangawane, J.V. and et. al, 2019. Single logout functionality for a multi-tenant identity and data
security management cloud service. U.S. Patent 10,511,589.
Gutta, R.R., 2019. Managing Security Objectives for Effective Organizational Performance
Information Security Management (Doctoral dissertation, Walden University).
Huang, H.Y. and et. al, 2019. Security management for data systems. U.S. Patent Application
15/789,529.
Iwai, M. and et. al, 2020. Data security management based on device locations and connection
states. U.S. Patent 10,621,373.
Jin, Q. and Wang, L., 2019, July. Intranet User-Level Security Traffic Management with Deep
Reinforcement Learning. In 2019 International Joint Conference on Neural Networks
(IJCNN) (pp. 1-8). IEEE.
Johnson, R.A. and et. al, 2020. User interface features for enterprise security management. U.S.
Patent 10,652,280.
Karimi, Z. and Peikar, H.R., 2019. Information Security Management: The Impacts of
Organizational Commitment and Perceived Consequences of Security Breach on the
Intention of Patients’ Information Security Violation. Medical Ethics Journal, 13(44),
pp.1-10.
Kaušpadienė, L., Ramanauskaitė, S. and Čenys, A., 2019. Information security management
framework suitability estimation for small and medium enterprise. Technological and
Economic Development of Economy, 25(5), pp.979-997.
Killer, C., Rodrigues, B. and Stiller, B., 2019, May. Security Management and Visualization in a
Blockchain-based Collaborative Defense. In 2019 IEEE International Conference on
Blockchain and Cryptocurrency (ICBC) (pp. 108-111). IEEE.
Kirti, G. and et. al, 2020. Techniques for discovering and managing security of applications.
U.S. Patent 10,536,478.
Ključnikov¹, A., Mura, L. and Sklenár, D., 2019. Information security management in SMEs:
Factors of success.
Kordestani, M., Chaibakhsh, A. and Saif, M., 2020. SMS–A Security Management System for
Steam Turbines Using a Multisensor Array. IEEE Systems Journal.
29
Secure Best Marks with AI Grader
Need help grading? Try our AI Grader for instant feedback on your assignments.

Kumah, P., Yaokumah, W. and Okai, E.S.A., 2019. A conceptual model and empirical
assessment of HR security risk management. Information & Computer Security.
Lander, V. and Sondhi, A., Oracle International Corp, 2019. Security Tokens for a Multi-Tenant
Identity and Data Security Management Cloud Service. U.S. Patent Application
16/247,461.
Lee, H., Han, C. and Yoo, T., 2019. The application of mistake-proofing to organisational
security management. Total Quality Management & Business Excellence, 30(9-10),
pp.1151-1166.
Li, L., Liu, F. and Spini, M., Huawei Technologies Co Ltd, 2019. Cyber security management
system, method, and apparatus. U.S. Patent Application 16/240,710.
Limba, T. and et. al, 2019. Peculiarities of cyber security management in the process of internet
voting implementation.
Limba, T. and et. al, 2019. Cyber security management model for critical infrastructure.
Logan, P.Y., 2020. Crafting an undergraduate information security emphasis within information
technology. Journal of Information Systems Education, 13(3), p.3.
McCoy, D.J., International Business Machines Corp, 2019. Key-based data security
management. U.S. Patent Application 16/278,303.
Sennewald, C.A. and Baillie, C., 2020. Effective security management. Butterworth-Heinemann.
Subramanian, E., Neelakanteshwar, M. and Purushothaman, R., Oracle International Corp,
2020. Tenant and service management for a multi-tenant identity and data security
management cloud service. U.S. Patent 10,616,224.
Turel, O., Xu, Z. and Guo, K., 2020. Organizational citizenship behavior regarding security:
Leadership approach perspective. Journal of Computer Information Systems, 60(1),
pp.61-75.
Wang, L., Che, R. and Jing, N., 2019, June. Research and Implementation of BDaaS Cloud
Platform for Security Industry. In Proceedings of the 2019 3rd High Performance
Computing and Cluster Technologies Conference (pp. 225-231).
White, G.L., Hewitt, B. and Kruck, S.E., 2019. Incorporating global information security and
assurance in IS education. Journal of Information Systems Education, 24(1), p.1.
Yang, R. and et. al, 2019. nLSALog: An Anomaly Detection Framework for Log Sequence in
Security Management. IEEE Access, 7, pp.181152-181164.
Циклаури, В.Ю. and et. al, 2019. Economic Security Management in Social Sphere.
In Education Excellence and Innovation Management through Vision 2020 (pp. 2561-
2570).
30
assessment of HR security risk management. Information & Computer Security.
Lander, V. and Sondhi, A., Oracle International Corp, 2019. Security Tokens for a Multi-Tenant
Identity and Data Security Management Cloud Service. U.S. Patent Application
16/247,461.
Lee, H., Han, C. and Yoo, T., 2019. The application of mistake-proofing to organisational
security management. Total Quality Management & Business Excellence, 30(9-10),
pp.1151-1166.
Li, L., Liu, F. and Spini, M., Huawei Technologies Co Ltd, 2019. Cyber security management
system, method, and apparatus. U.S. Patent Application 16/240,710.
Limba, T. and et. al, 2019. Peculiarities of cyber security management in the process of internet
voting implementation.
Limba, T. and et. al, 2019. Cyber security management model for critical infrastructure.
Logan, P.Y., 2020. Crafting an undergraduate information security emphasis within information
technology. Journal of Information Systems Education, 13(3), p.3.
McCoy, D.J., International Business Machines Corp, 2019. Key-based data security
management. U.S. Patent Application 16/278,303.
Sennewald, C.A. and Baillie, C., 2020. Effective security management. Butterworth-Heinemann.
Subramanian, E., Neelakanteshwar, M. and Purushothaman, R., Oracle International Corp,
2020. Tenant and service management for a multi-tenant identity and data security
management cloud service. U.S. Patent 10,616,224.
Turel, O., Xu, Z. and Guo, K., 2020. Organizational citizenship behavior regarding security:
Leadership approach perspective. Journal of Computer Information Systems, 60(1),
pp.61-75.
Wang, L., Che, R. and Jing, N., 2019, June. Research and Implementation of BDaaS Cloud
Platform for Security Industry. In Proceedings of the 2019 3rd High Performance
Computing and Cluster Technologies Conference (pp. 225-231).
White, G.L., Hewitt, B. and Kruck, S.E., 2019. Incorporating global information security and
assurance in IS education. Journal of Information Systems Education, 24(1), p.1.
Yang, R. and et. al, 2019. nLSALog: An Anomaly Detection Framework for Log Sequence in
Security Management. IEEE Access, 7, pp.181152-181164.
Циклаури, В.Ю. and et. al, 2019. Economic Security Management in Social Sphere.
In Education Excellence and Innovation Management through Vision 2020 (pp. 2561-
2570).
30
1 out of 35
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
© 2024 | Zucol Services PVT LTD | All rights reserved.





