IT Security Report: Assessing Risks, Implementing Security Measures
VerifiedAdded on 2023/01/17
|17
|5127
|60
Report
AI Summary
This report examines IT security for Zapmeta, a retail food delivery company. It begins by defining IT security and its importance, outlining various security risks like accidental and deliberate threats, and vulnerabilities such as unauthorized access and malware. The report then details security procedures organizations should implement, including authorized access, limited access, password procedures, anti-virus measures, and router security. It further delves into methods for assessing IT security risks, emphasizing the use of strong passwords and access control. The core of the report discusses the impact of incorrect firewall configurations and third-party VPNs, highlighting potential data privacy issues and decreased processing speed. Finally, it explores the implementation of DMZ, static IP, and NAT to enhance network security, providing a comprehensive overview of IT security practices.
IT SECURITY
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................3
LO 1.................................................................................................................................................3
P1: Security Risks types...............................................................................................................3
P2: Security procedures of organisations.....................................................................................6
M1: Method to assess the IT security risks..................................................................................7
LO 2.................................................................................................................................................7
P3: Potential impact to IT security of incorrect configuration of firewall policies and third
party VPNs. .................................................................................................................................7
P4: Implement DMZ, static IP, NAT in a network, which can improve the security of network.
......................................................................................................................................................8
LO 3...............................................................................................................................................10
P5: Risk assessment procedures.................................................................................................10
M3: ISO 31000 risk management technology and its application.............................................11
P6: Data protection processes and regulations...........................................................................12
LO 4...............................................................................................................................................13
P7: Security Policy plan.............................................................................................................13
P8: List the main components of organisational disaster plan...................................................14
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................16
INTRODUCTION...........................................................................................................................3
LO 1.................................................................................................................................................3
P1: Security Risks types...............................................................................................................3
P2: Security procedures of organisations.....................................................................................6
M1: Method to assess the IT security risks..................................................................................7
LO 2.................................................................................................................................................7
P3: Potential impact to IT security of incorrect configuration of firewall policies and third
party VPNs. .................................................................................................................................7
P4: Implement DMZ, static IP, NAT in a network, which can improve the security of network.
......................................................................................................................................................8
LO 3...............................................................................................................................................10
P5: Risk assessment procedures.................................................................................................10
M3: ISO 31000 risk management technology and its application.............................................11
P6: Data protection processes and regulations...........................................................................12
LO 4...............................................................................................................................................13
P7: Security Policy plan.............................................................................................................13
P8: List the main components of organisational disaster plan...................................................14
CONCLUSION..............................................................................................................................15
REFERENCES..............................................................................................................................16

INTRODUCTION
IT security is process of protecting digital assets from unethical users and hackers. It is
process of managing risks associated with use of information technology and digital devices. It is
process of identifying, assessing and treating risks for the confidentiality to the organizational
assets. It comprises cyber-security strategies to protect unauthorized access of organizational
assets, networks, and devices. For an effective implementation of cyber security process there
must be proper coordination of efforts throughout organizational information system. Main
elements of cyber security are network security, data security, cloud security, identity
management. Challenging situation for IT security is ever-changing nature of IT risks. This is the
reason that now organizations provides more adaptive and practical practices. Here in this report
Zapmeta is taken as retail food Delivery Company. IT issues related to security of this company
is to be resolved. It is important to make proper arrangement of IT security because linkage of
payment gateways with it and efficient functioning of company.
LO 1
P1: Security Risks types.
Security can be defined as being free from any sort of danger or also refers as being safe.
In IT, security refers to the protection of information as well as information systems from the
unauthorised access. Information security is composed of communication security and computer
security. There are several risks associated with the organizations. With the advancement in
technology has also given rise to cyber threats which have made various businesses vulnerable to
security threats and even these threats are increasing in number.
IT security is process of protecting digital assets from unethical users and hackers. It is
process of managing risks associated with use of information technology and digital devices. It is
process of identifying, assessing and treating risks for the confidentiality to the organizational
assets. It comprises cyber-security strategies to protect unauthorized access of organizational
assets, networks, and devices. For an effective implementation of cyber security process there
must be proper coordination of efforts throughout organizational information system. Main
elements of cyber security are network security, data security, cloud security, identity
management. Challenging situation for IT security is ever-changing nature of IT risks. This is the
reason that now organizations provides more adaptive and practical practices. Here in this report
Zapmeta is taken as retail food Delivery Company. IT issues related to security of this company
is to be resolved. It is important to make proper arrangement of IT security because linkage of
payment gateways with it and efficient functioning of company.
LO 1
P1: Security Risks types.
Security can be defined as being free from any sort of danger or also refers as being safe.
In IT, security refers to the protection of information as well as information systems from the
unauthorised access. Information security is composed of communication security and computer
security. There are several risks associated with the organizations. With the advancement in
technology has also given rise to cyber threats which have made various businesses vulnerable to
security threats and even these threats are increasing in number.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
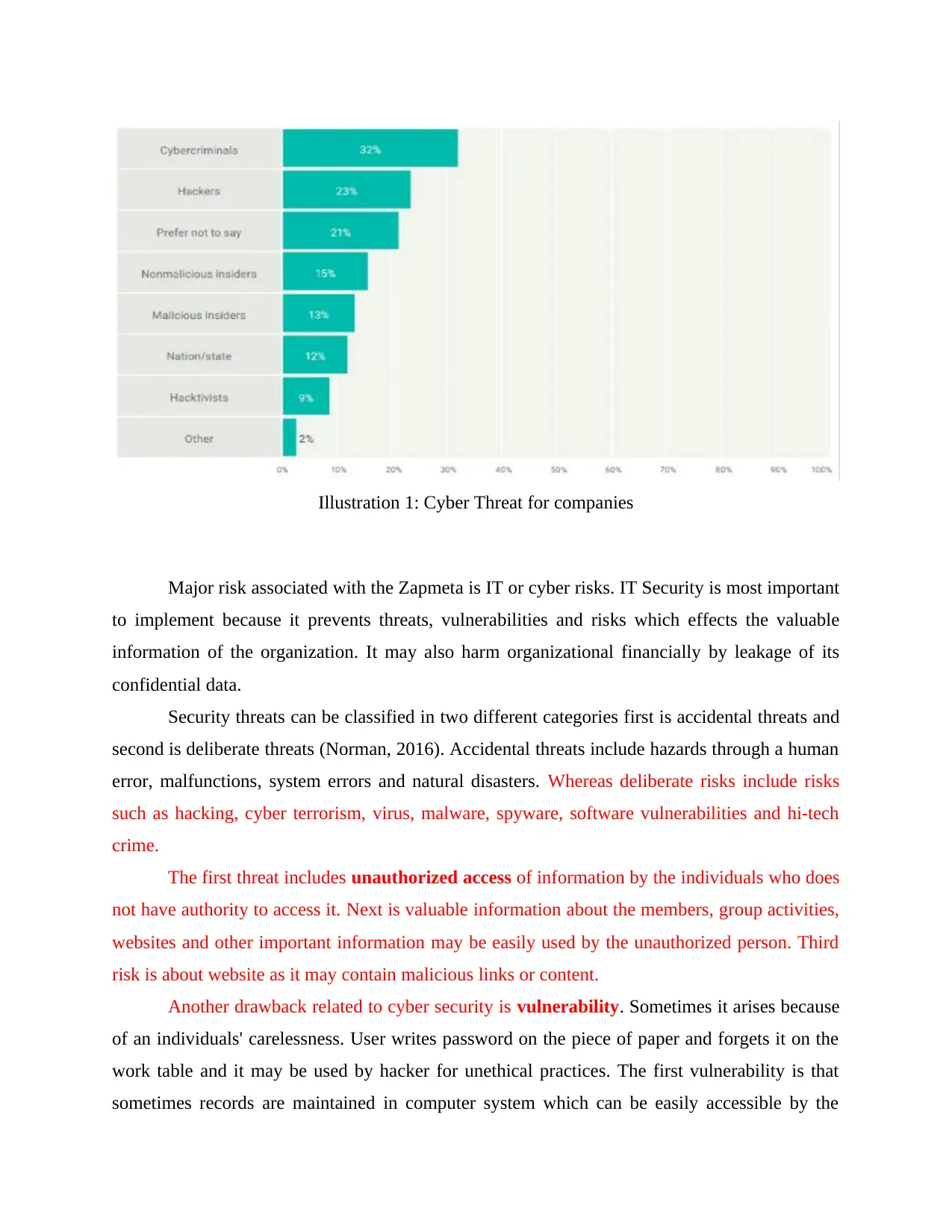
Illustration 1: Cyber Threat for companies
Major risk associated with the Zapmeta is IT or cyber risks. IT Security is most important
to implement because it prevents threats, vulnerabilities and risks which effects the valuable
information of the organization. It may also harm organizational financially by leakage of its
confidential data.
Security threats can be classified in two different categories first is accidental threats and
second is deliberate threats (Norman, 2016). Accidental threats include hazards through a human
error, malfunctions, system errors and natural disasters. Whereas deliberate risks include risks
such as hacking, cyber terrorism, virus, malware, spyware, software vulnerabilities and hi-tech
crime.
The first threat includes unauthorized access of information by the individuals who does
not have authority to access it. Next is valuable information about the members, group activities,
websites and other important information may be easily used by the unauthorized person. Third
risk is about website as it may contain malicious links or content.
Another drawback related to cyber security is vulnerability. Sometimes it arises because
of an individuals' carelessness. User writes password on the piece of paper and forgets it on the
work table and it may be used by hacker for unethical practices. The first vulnerability is that
sometimes records are maintained in computer system which can be easily accessible by the
Major risk associated with the Zapmeta is IT or cyber risks. IT Security is most important
to implement because it prevents threats, vulnerabilities and risks which effects the valuable
information of the organization. It may also harm organizational financially by leakage of its
confidential data.
Security threats can be classified in two different categories first is accidental threats and
second is deliberate threats (Norman, 2016). Accidental threats include hazards through a human
error, malfunctions, system errors and natural disasters. Whereas deliberate risks include risks
such as hacking, cyber terrorism, virus, malware, spyware, software vulnerabilities and hi-tech
crime.
The first threat includes unauthorized access of information by the individuals who does
not have authority to access it. Next is valuable information about the members, group activities,
websites and other important information may be easily used by the unauthorized person. Third
risk is about website as it may contain malicious links or content.
Another drawback related to cyber security is vulnerability. Sometimes it arises because
of an individuals' carelessness. User writes password on the piece of paper and forgets it on the
work table and it may be used by hacker for unethical practices. The first vulnerability is that
sometimes records are maintained in computer system which can be easily accessible by the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

employee. Next is information about the habits and organizational motives which can be used by
the individuals who are not authorised to access or use the information (Baikalov and et.al ,
2017). Third vulnerability is that there is no firewall between the website server and internet.
Without firewall preventing unauthorized access makes computer system vulnerable to attacks.
The vulnerability will result in risk and thus will damage the system of organizations.
Risk related to payment gateways is also a major risk for an organization. Hackers may
use confidential payment details and access organizational bank details in unauthorized way.
Malware is unauthorized windows running behind the desktop without the users'
knowledge. Virus works by replicating and inserting themselves within computer which can
make system slower and can destroy the data, disable software and deletes the file. It can be
infected by the means of email or file download from virus affected downloading.
Spyware collects the information and transfers it to some unauthorized access. It is
embedded and undetectable (Tsohou, Karyda, and Kokolakis, 2015). It is not able to be detected
but have symptoms of slowing the computer systems. Unpatched server and software
vulnerabilities are another type of cyber risk that allows access via unpatched server and
software.
These risk can be assessed and can be treated. Key steps of Risk assessment are as
follows:-
Identify information assets:- These are those assets which are vulnerable to business and
contains valuable data for the company.
Identify the owners of assets:-Identification of the department whom assets are being at
risk.
Identification of risks to confidentiality and availability of information assets.
Identification of the risk owners to the risk.
Analysing the identified risk:-The identified risk is analysed at this stage.
Determination of the levels of risk (Peltier, 2016).
Prioritization of risks is done among the alternate risks associated with aim to eliminate
that risk.
the individuals who are not authorised to access or use the information (Baikalov and et.al ,
2017). Third vulnerability is that there is no firewall between the website server and internet.
Without firewall preventing unauthorized access makes computer system vulnerable to attacks.
The vulnerability will result in risk and thus will damage the system of organizations.
Risk related to payment gateways is also a major risk for an organization. Hackers may
use confidential payment details and access organizational bank details in unauthorized way.
Malware is unauthorized windows running behind the desktop without the users'
knowledge. Virus works by replicating and inserting themselves within computer which can
make system slower and can destroy the data, disable software and deletes the file. It can be
infected by the means of email or file download from virus affected downloading.
Spyware collects the information and transfers it to some unauthorized access. It is
embedded and undetectable (Tsohou, Karyda, and Kokolakis, 2015). It is not able to be detected
but have symptoms of slowing the computer systems. Unpatched server and software
vulnerabilities are another type of cyber risk that allows access via unpatched server and
software.
These risk can be assessed and can be treated. Key steps of Risk assessment are as
follows:-
Identify information assets:- These are those assets which are vulnerable to business and
contains valuable data for the company.
Identify the owners of assets:-Identification of the department whom assets are being at
risk.
Identification of risks to confidentiality and availability of information assets.
Identification of the risk owners to the risk.
Analysing the identified risk:-The identified risk is analysed at this stage.
Determination of the levels of risk (Peltier, 2016).
Prioritization of risks is done among the alternate risks associated with aim to eliminate
that risk.

P2: Security procedures of organisations
Organisations have huge amount of sensitive data related to their businesses and thus
they must have security policies at their workplace. For preventing the data of company there are
specific rules and procedures. Zapmeta should possess the security procedures like:
Authorised access: The person who is authorised to access the information in the company is
required to follow an authentication method in which login ID and Passwords are required so
that authenticity of the person can be verified (Safa, Von Solms and Furnell, 2016).
Limited Access: Person who is authorised to access the system, can also have access to
particular section in which they can be made changes or access the information. Like system
have limited data accessing rights for the person which are view, modify, add, delete etc. all
these rights need permissions from the information owner so that necessary restrictions can be
imposed against making unauthorised changes. It provides the prevention of destruction of data.
Password Procedures: all the employees in the organisation should maintain and select the
passwords in their systems. System level passwords such as those of systems of administration,
root and application accounts of admin must be changed. Next user level passwords must be
changes according to the policies of company (Soomro, Shah and Ahmed, 2016). Passwords
should be saved in encrypted form. Organisation can also use hash key function for saving the
passwords.
Anti-Virus Procedures: organisation must include the effective virus detection software in the
connected network of the systems. Anti-virus should be installed on each system, its supportive
application and next they should update the anti-virus time to time. If any user outside the
organisation tries to access the company's data then it is protected through anti-virus which is
licensed and approved so that it keeps the data safe.
Router security procedures: this involves routers and switches which are used to connect the
production network in the company. Configuration standards for routers and authentication of
user are necessary so router must use the TACACS+, or similar standards (Safa and Von Solms,
2016). Password must be secured in encrypted form. Routers installed in the network of the
organisation should have similar password which are in encrypted form for enabling user
accounts so, unauthorised access may prohibited on the network device.
Organisations have huge amount of sensitive data related to their businesses and thus
they must have security policies at their workplace. For preventing the data of company there are
specific rules and procedures. Zapmeta should possess the security procedures like:
Authorised access: The person who is authorised to access the information in the company is
required to follow an authentication method in which login ID and Passwords are required so
that authenticity of the person can be verified (Safa, Von Solms and Furnell, 2016).
Limited Access: Person who is authorised to access the system, can also have access to
particular section in which they can be made changes or access the information. Like system
have limited data accessing rights for the person which are view, modify, add, delete etc. all
these rights need permissions from the information owner so that necessary restrictions can be
imposed against making unauthorised changes. It provides the prevention of destruction of data.
Password Procedures: all the employees in the organisation should maintain and select the
passwords in their systems. System level passwords such as those of systems of administration,
root and application accounts of admin must be changed. Next user level passwords must be
changes according to the policies of company (Soomro, Shah and Ahmed, 2016). Passwords
should be saved in encrypted form. Organisation can also use hash key function for saving the
passwords.
Anti-Virus Procedures: organisation must include the effective virus detection software in the
connected network of the systems. Anti-virus should be installed on each system, its supportive
application and next they should update the anti-virus time to time. If any user outside the
organisation tries to access the company's data then it is protected through anti-virus which is
licensed and approved so that it keeps the data safe.
Router security procedures: this involves routers and switches which are used to connect the
production network in the company. Configuration standards for routers and authentication of
user are necessary so router must use the TACACS+, or similar standards (Safa and Von Solms,
2016). Password must be secured in encrypted form. Routers installed in the network of the
organisation should have similar password which are in encrypted form for enabling user
accounts so, unauthorised access may prohibited on the network device.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

M1: Method to assess the IT security risks.
To lower the IT security risks Zapmeta must install anti-virus in the systems of company
which are connected through router. Also, they can use the access of information in terms of
granting the permission to all employees according to their positions. Company can use the
security procedure like strong password allocations, routers procedures, anti-virus procedure
which help them to minimise the access of important information of company by hackers.
LO 2
P3: Potential impact of incorrect configuration of firewall and third party VPNs
Firewall is designed to protect the system from unauthorised access from private
networks. It is used for network monitoring as well. It can be implemented in both forms either
hardware or software to restrict the use of private network by the unauthorised user. Firewall are
basically three types which are packet filtering, stateful firewall and application firewall (Dorca
and et.al., 2016). It exhibits the filtration of data according to the need. Firewall policies means
that the policies or rules applied to the access of user to private network. It gives the information
of the address which is used by user to access the network. For example particular user can be
identified by tracing IP addresses under firewall policy. Organisation can also make some
mistakes in terms of configuring firewall. As the traffic on the private network may increase but
only specific traffic is allowed to access the services. Malicious traffic is not allowed to access
the organisational information otherwise, it may result in data loss of Zapmeta. It may be wrong
implemented that they would not allow the specified IP addresses sources, which may be
harmful for the company. Identification of IP address of the destination specific port addresses is
also not identified.
Bad configuration-
Permit to any IP: It is wrong when it comes to access rule of controlling. It allows any source to
access any port for reaching specific destination, leading to data privacy issues.
Permit IP any WEB-SERVER1: it allows to access the web server of the company by all traffic
(Jayanthi, 2017). It gains the more traffic at server which slows the speed of processing for other
specific users of company.
VPN (Virtual Private Network) provides the organisation's their private network to access the
internet in their organisation which are UUNET and concentric networks. This allows the
To lower the IT security risks Zapmeta must install anti-virus in the systems of company
which are connected through router. Also, they can use the access of information in terms of
granting the permission to all employees according to their positions. Company can use the
security procedure like strong password allocations, routers procedures, anti-virus procedure
which help them to minimise the access of important information of company by hackers.
LO 2
P3: Potential impact of incorrect configuration of firewall and third party VPNs
Firewall is designed to protect the system from unauthorised access from private
networks. It is used for network monitoring as well. It can be implemented in both forms either
hardware or software to restrict the use of private network by the unauthorised user. Firewall are
basically three types which are packet filtering, stateful firewall and application firewall (Dorca
and et.al., 2016). It exhibits the filtration of data according to the need. Firewall policies means
that the policies or rules applied to the access of user to private network. It gives the information
of the address which is used by user to access the network. For example particular user can be
identified by tracing IP addresses under firewall policy. Organisation can also make some
mistakes in terms of configuring firewall. As the traffic on the private network may increase but
only specific traffic is allowed to access the services. Malicious traffic is not allowed to access
the organisational information otherwise, it may result in data loss of Zapmeta. It may be wrong
implemented that they would not allow the specified IP addresses sources, which may be
harmful for the company. Identification of IP address of the destination specific port addresses is
also not identified.
Bad configuration-
Permit to any IP: It is wrong when it comes to access rule of controlling. It allows any source to
access any port for reaching specific destination, leading to data privacy issues.
Permit IP any WEB-SERVER1: it allows to access the web server of the company by all traffic
(Jayanthi, 2017). It gains the more traffic at server which slows the speed of processing for other
specific users of company.
VPN (Virtual Private Network) provides the organisation's their private network to access the
internet in their organisation which are UUNET and concentric networks. This allows the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

services by making an agreement at levels of contract with third party. It performs all the
operations in binary codes and data protection objective. VPN is used by Zapmeta for internet
access, which also encrypts the data of users for security purpose (Goodman, Straub and
Baskerville, 2016). Though it is secure but in case of bandwidth gaps to establish connection,
there are possibilities that attackers can access the account of the user in the organisation. It leads
to data insecurity.
If Zapmeta install the firewall configuration and VPN third party network at their
workplace they should focus on the rules and policies which are basic to be concerned. If there is
any mistake in any configuration policies then it may allow the attackers to hack the data which
is sensitive for the company. Also, it may decrease the speed of data processing as all traffic is
collected at their network.
P4: Implement DMZ, static IP, NAT in a network, for improving network security
Network security is very important in organisation and for ensuring network security
Zapmeta can use, DMZ, static IP, NAT. These are explained below:
DMZ
DMZ is demilitarised zone, also called screened sub network or perimeter network, it
separates the local area network (LAN) from the access of untrusted networks so it is logical or
physical subnet (Fakhri, Fahimah and Ibrahim, 2015).
operations in binary codes and data protection objective. VPN is used by Zapmeta for internet
access, which also encrypts the data of users for security purpose (Goodman, Straub and
Baskerville, 2016). Though it is secure but in case of bandwidth gaps to establish connection,
there are possibilities that attackers can access the account of the user in the organisation. It leads
to data insecurity.
If Zapmeta install the firewall configuration and VPN third party network at their
workplace they should focus on the rules and policies which are basic to be concerned. If there is
any mistake in any configuration policies then it may allow the attackers to hack the data which
is sensitive for the company. Also, it may decrease the speed of data processing as all traffic is
collected at their network.
P4: Implement DMZ, static IP, NAT in a network, for improving network security
Network security is very important in organisation and for ensuring network security
Zapmeta can use, DMZ, static IP, NAT. These are explained below:
DMZ
DMZ is demilitarised zone, also called screened sub network or perimeter network, it
separates the local area network (LAN) from the access of untrusted networks so it is logical or
physical subnet (Fakhri, Fahimah and Ibrahim, 2015).
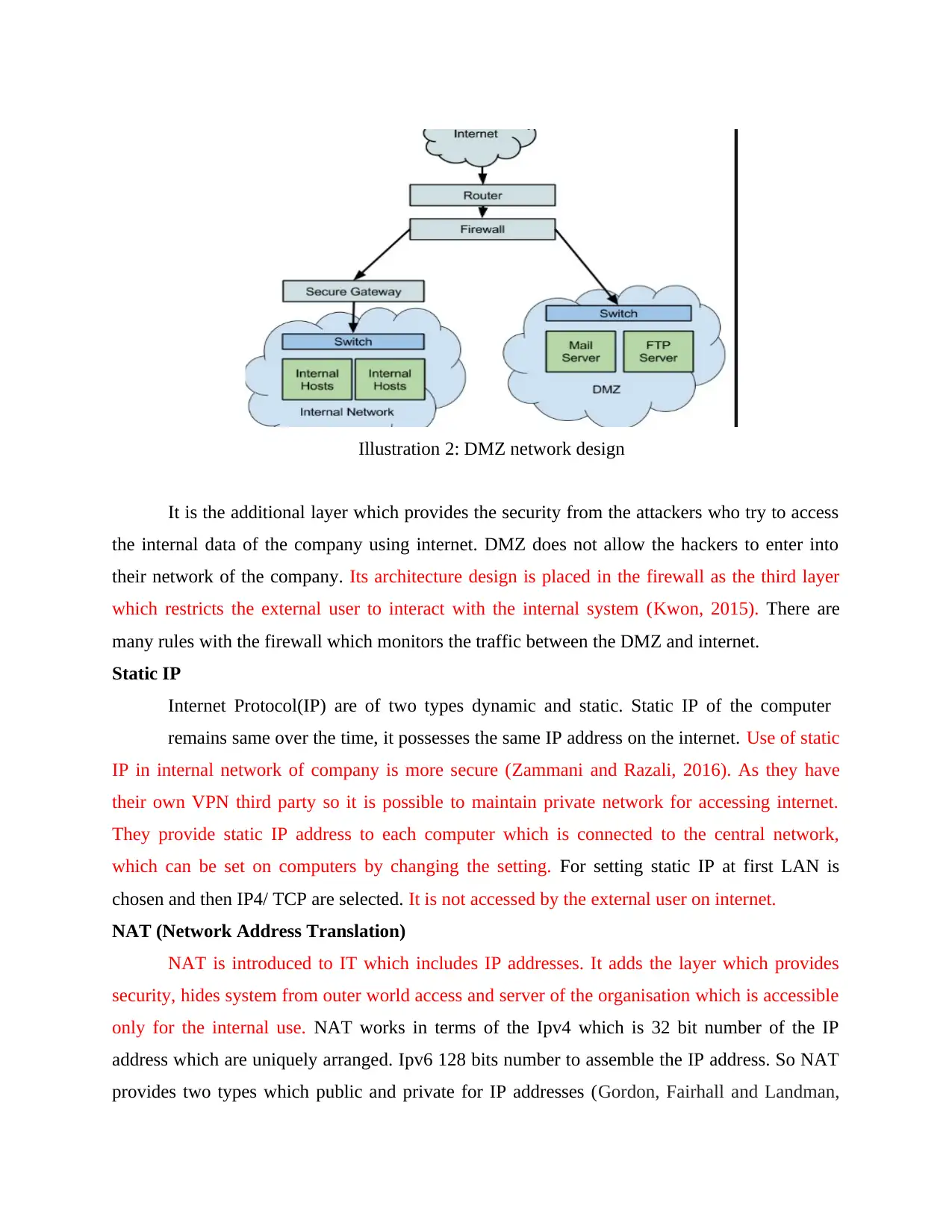
It is the additional layer which provides the security from the attackers who try to access
the internal data of the company using internet. DMZ does not allow the hackers to enter into
their network of the company. Its architecture design is placed in the firewall as the third layer
which restricts the external user to interact with the internal system (Kwon, 2015). There are
many rules with the firewall which monitors the traffic between the DMZ and internet.
Static IP
Internet Protocol(IP) are of two types dynamic and static. Static IP of the computer
remains same over the time, it possesses the same IP address on the internet. Use of static
IP in internal network of company is more secure (Zammani and Razali, 2016). As they have
their own VPN third party so it is possible to maintain private network for accessing internet.
They provide static IP address to each computer which is connected to the central network,
which can be set on computers by changing the setting. For setting static IP at first LAN is
chosen and then IP4/ TCP are selected. It is not accessed by the external user on internet.
NAT (Network Address Translation)
NAT is introduced to IT which includes IP addresses. It adds the layer which provides
security, hides system from outer world access and server of the organisation which is accessible
only for the internal use. NAT works in terms of the Ipv4 which is 32 bit number of the IP
address which are uniquely arranged. Ipv6 128 bits number to assemble the IP address. So NAT
provides two types which public and private for IP addresses (Gordon, Fairhall and Landman,
Illustration 2: DMZ network design
the internal data of the company using internet. DMZ does not allow the hackers to enter into
their network of the company. Its architecture design is placed in the firewall as the third layer
which restricts the external user to interact with the internal system (Kwon, 2015). There are
many rules with the firewall which monitors the traffic between the DMZ and internet.
Static IP
Internet Protocol(IP) are of two types dynamic and static. Static IP of the computer
remains same over the time, it possesses the same IP address on the internet. Use of static
IP in internal network of company is more secure (Zammani and Razali, 2016). As they have
their own VPN third party so it is possible to maintain private network for accessing internet.
They provide static IP address to each computer which is connected to the central network,
which can be set on computers by changing the setting. For setting static IP at first LAN is
chosen and then IP4/ TCP are selected. It is not accessed by the external user on internet.
NAT (Network Address Translation)
NAT is introduced to IT which includes IP addresses. It adds the layer which provides
security, hides system from outer world access and server of the organisation which is accessible
only for the internal use. NAT works in terms of the Ipv4 which is 32 bit number of the IP
address which are uniquely arranged. Ipv6 128 bits number to assemble the IP address. So NAT
provides two types which public and private for IP addresses (Gordon, Fairhall and Landman,
Illustration 2: DMZ network design
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2017). It helps private IP addresses within, the internal network and it can't be routed outside. It
allows to use the computer resources, severs and computers which have privately assigned
networks which help the organisation to be secured and protected from others. NAT used in
private network will hide the computer systems to access by the outer world.
Zapmeta can use these network security tolls to control and privatised the data. It gives
more security to company's network.
LO 3
P5: Risk assessment procedures.
Risk assessment is about analysis, estimation or evaluation of the possible risks in the
organisation which may occur during operations. In terms of IT security risk assessment is very
important for the company. Zapmeta should analyse the security of its information systems and
this procedure must include several things.
Firstly organisation must find all the assets which are valuable for the company like
websites, application, servers and customer’s data, company's data, payment gateways
information.
Secondly, Zapmeta must analyse the potential consequences, like financial losses which
can occurr due to asset damage (Pathan, 2016). It also includes data loss, legal consequence of
cybercrime, systems may face downtime.
In the next stage threats like viruses, malware, spyware, system failure, and possibilities
of unauthorised access by the attackers are identified. These threats may breach the security of
the computer in the organisation. Vulnerability analysis, helps to detect the threats which cause
harm to the systems.
Fifth assess the risks which can harm the systems, it provided managing the risks by
creating the risk management plan by collecting the data about the potential risks
RISK ASSESSMENT PLAN
Threats Vulnerabilities Asset and
consequences
Risk Solution
System
failure.
Firewall
configuration
Server High Proper
monitoring
allows to use the computer resources, severs and computers which have privately assigned
networks which help the organisation to be secured and protected from others. NAT used in
private network will hide the computer systems to access by the outer world.
Zapmeta can use these network security tolls to control and privatised the data. It gives
more security to company's network.
LO 3
P5: Risk assessment procedures.
Risk assessment is about analysis, estimation or evaluation of the possible risks in the
organisation which may occur during operations. In terms of IT security risk assessment is very
important for the company. Zapmeta should analyse the security of its information systems and
this procedure must include several things.
Firstly organisation must find all the assets which are valuable for the company like
websites, application, servers and customer’s data, company's data, payment gateways
information.
Secondly, Zapmeta must analyse the potential consequences, like financial losses which
can occurr due to asset damage (Pathan, 2016). It also includes data loss, legal consequence of
cybercrime, systems may face downtime.
In the next stage threats like viruses, malware, spyware, system failure, and possibilities
of unauthorised access by the attackers are identified. These threats may breach the security of
the computer in the organisation. Vulnerability analysis, helps to detect the threats which cause
harm to the systems.
Fifth assess the risks which can harm the systems, it provided managing the risks by
creating the risk management plan by collecting the data about the potential risks
RISK ASSESSMENT PLAN
Threats Vulnerabilities Asset and
consequences
Risk Solution
System
failure.
Firewall
configuration
Server High Proper
monitoring
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
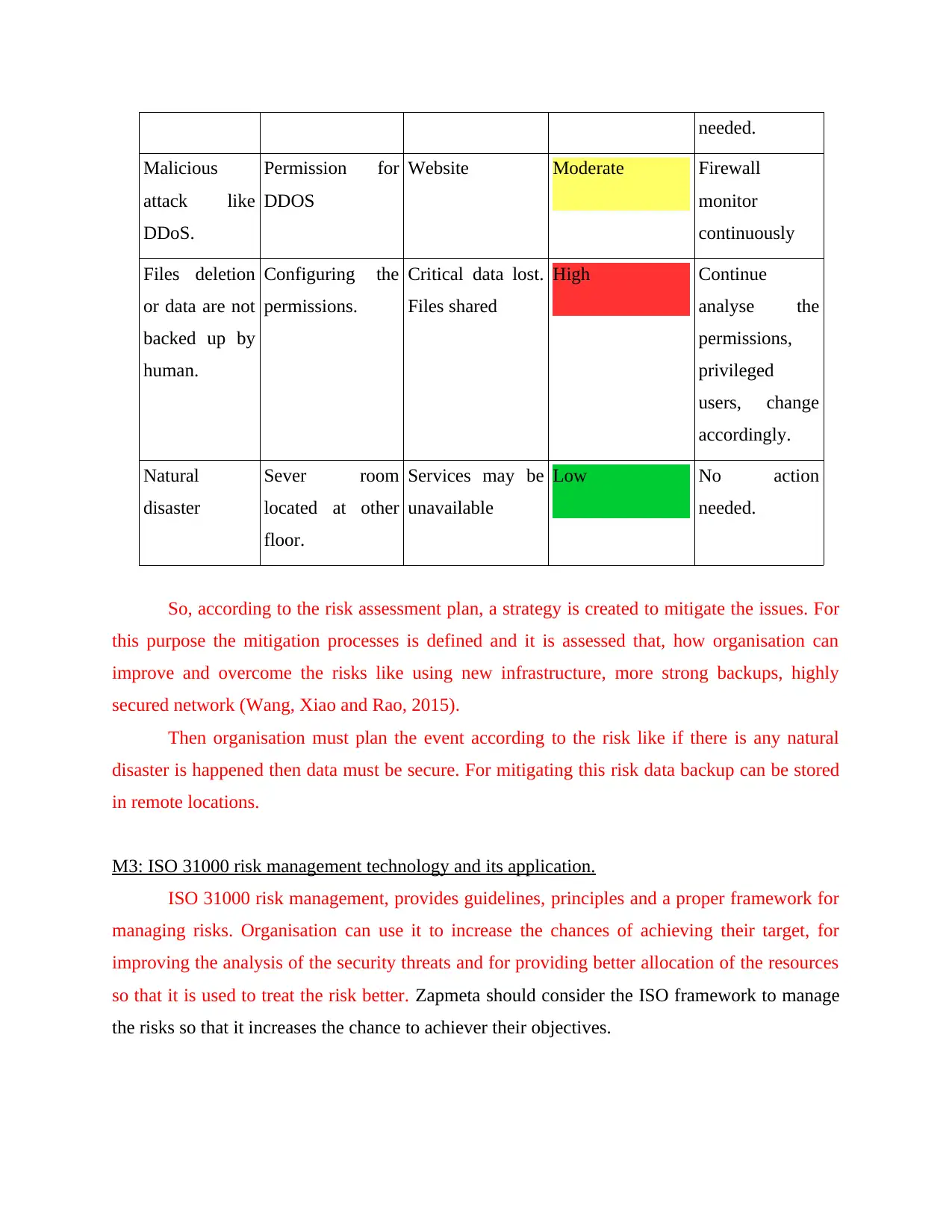
needed.
Malicious
attack like
DDoS.
Permission for
DDOS
Website Moderate Firewall
monitor
continuously
Files deletion
or data are not
backed up by
human.
Configuring the
permissions.
Critical data lost.
Files shared
High Continue
analyse the
permissions,
privileged
users, change
accordingly.
Natural
disaster
Sever room
located at other
floor.
Services may be
unavailable
Low No action
needed.
So, according to the risk assessment plan, a strategy is created to mitigate the issues. For
this purpose the mitigation processes is defined and it is assessed that, how organisation can
improve and overcome the risks like using new infrastructure, more strong backups, highly
secured network (Wang, Xiao and Rao, 2015).
Then organisation must plan the event according to the risk like if there is any natural
disaster is happened then data must be secure. For mitigating this risk data backup can be stored
in remote locations.
M3: ISO 31000 risk management technology and its application.
ISO 31000 risk management, provides guidelines, principles and a proper framework for
managing risks. Organisation can use it to increase the chances of achieving their target, for
improving the analysis of the security threats and for providing better allocation of the resources
so that it is used to treat the risk better. Zapmeta should consider the ISO framework to manage
the risks so that it increases the chance to achiever their objectives.
Malicious
attack like
DDoS.
Permission for
DDOS
Website Moderate Firewall
monitor
continuously
Files deletion
or data are not
backed up by
human.
Configuring the
permissions.
Critical data lost.
Files shared
High Continue
analyse the
permissions,
privileged
users, change
accordingly.
Natural
disaster
Sever room
located at other
floor.
Services may be
unavailable
Low No action
needed.
So, according to the risk assessment plan, a strategy is created to mitigate the issues. For
this purpose the mitigation processes is defined and it is assessed that, how organisation can
improve and overcome the risks like using new infrastructure, more strong backups, highly
secured network (Wang, Xiao and Rao, 2015).
Then organisation must plan the event according to the risk like if there is any natural
disaster is happened then data must be secure. For mitigating this risk data backup can be stored
in remote locations.
M3: ISO 31000 risk management technology and its application.
ISO 31000 risk management, provides guidelines, principles and a proper framework for
managing risks. Organisation can use it to increase the chances of achieving their target, for
improving the analysis of the security threats and for providing better allocation of the resources
so that it is used to treat the risk better. Zapmeta should consider the ISO framework to manage
the risks so that it increases the chance to achiever their objectives.

P6: Data protection processes and regulations.
Data protection is about preventing the data which involves the collection and
dissemination of data. Thus it is taken as serious issue in the public and privately that data
privacy is must and all legal procedures are followed to maintain the data protection.
There are Data Protection Act 2018 and the General Data Protection Regulation (GDPR) for
serving the purpose of data protection legally. These are the primary laws which must regulate
the businesses, and protect the personal data (Papp and Buttyan, 2015). It is right and obligation
in terms to security of the data. It subjects for the storage, transmitting, processing the data.
Companies should compliances with GDPR, and it includes some privacy or protection of data
requirements
Data processing is the subject of consent, it is required.
Data collection is anonymous because of protecting the privacy.
Handling the data transfer across the border with safety.
Companies should appoint the officer for the data protection, which must ensure
that the GDPR is followed properly (Joshi and Singh, 2017).
It is applicable to all the citizens in the EU countries for the data protection. Otherwise
penalties are charged from them. Companies are also required to follow the GDPR and its
compliances includes
Reading the GDPR physically for ensuring and understanding the legislation.
Other organisations have to look the compliances of it to follow the GDPR.
Paying attention to the website, analyse the available data on the website, it may not
affect the privacy of the other people.
It provides the prevention from loss of data to the company.
Encryption of the data is properly managed so that it may not decrypted by the attacker, it
helps in that as well (Layton, 2016).
Third party risk management, GDPR compliance also obligates to play the active role in
protecting the data on processors. Controllers instruct them to process the data.
So the data protection processes and regulations provide controllability to company for
ensuring that all regulations related to data protection are followed. It helps in data privacy of the
companies, as they view the personal data of the public, and then they sue it for the business
Data protection is about preventing the data which involves the collection and
dissemination of data. Thus it is taken as serious issue in the public and privately that data
privacy is must and all legal procedures are followed to maintain the data protection.
There are Data Protection Act 2018 and the General Data Protection Regulation (GDPR) for
serving the purpose of data protection legally. These are the primary laws which must regulate
the businesses, and protect the personal data (Papp and Buttyan, 2015). It is right and obligation
in terms to security of the data. It subjects for the storage, transmitting, processing the data.
Companies should compliances with GDPR, and it includes some privacy or protection of data
requirements
Data processing is the subject of consent, it is required.
Data collection is anonymous because of protecting the privacy.
Handling the data transfer across the border with safety.
Companies should appoint the officer for the data protection, which must ensure
that the GDPR is followed properly (Joshi and Singh, 2017).
It is applicable to all the citizens in the EU countries for the data protection. Otherwise
penalties are charged from them. Companies are also required to follow the GDPR and its
compliances includes
Reading the GDPR physically for ensuring and understanding the legislation.
Other organisations have to look the compliances of it to follow the GDPR.
Paying attention to the website, analyse the available data on the website, it may not
affect the privacy of the other people.
It provides the prevention from loss of data to the company.
Encryption of the data is properly managed so that it may not decrypted by the attacker, it
helps in that as well (Layton, 2016).
Third party risk management, GDPR compliance also obligates to play the active role in
protecting the data on processors. Controllers instruct them to process the data.
So the data protection processes and regulations provide controllability to company for
ensuring that all regulations related to data protection are followed. It helps in data privacy of the
companies, as they view the personal data of the public, and then they sue it for the business
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



