Implementing Cloud Services, COBIT, and Security: IT Strategy Plan
VerifiedAdded on 2023/06/03
|11
|2200
|274
Report
AI Summary
This report provides a detailed analysis of IT strategy and control, focusing on cloud service implementation, the COBIT framework, and security planning. It begins by exploring how cloud computing can enhance organizational performance, detailing the ITIL lifecycle phases and relevant metrics for performance improvement. The report then differentiates between COBIT 4.1 and COBIT 5, explaining the benefits of implementing a control framework within a business and highlighting the importance of an IT control framework. Furthermore, it presents a comprehensive security plan for a small law firm, addressing network security, risk assessment, and policy frameworks, along with physical and logical controls. Finally, the report addresses a service desk scenario, offering a decision tree to prioritize customer service effectively. Desklib provides students with access to past papers and solved assignments to aid their studies.

Running head: IT STRATEGY AND CONTROL
IT STRATEGY AND CONTROL
Name of the Student
Name of the University
Author Note
IT STRATEGY AND CONTROL
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT STRATEGY AND CONTROL
Answer to Question 1:
With the implementation of cloud computing, the performance of the organization
will get developed. Cloud service provides better way of storing the information with highest
security (Arpaci et al. 2015). The cloud computing decreases the cost and saves for every
organization. There are several architectures provided by the cloud service. According to the
need of customer, the organization can adopt cloud service. Moreover, cloud computing
offers their customer with the facility of paying as per their use. The organization can choose
PaaS architecture for their cloud service. This is designed for the companies that aims at
developing application or setting their application and aims at deploying these applications
within their cloud server (Bowers and Morse 2018). This is the best realistic strategy and will
help the organization in gaining more profit. With the help of IT service management
terminology, the organization can implement the cloud easily.
With the implementation of these five stages of ITIL, the organization can
implement the strategy. ITIL stands for information technology infrastructure library and this
has gained great importance in the managing the IT services (Al Mourad and Hussain 2014).
Thus, this strategy will eventually help the organization in storing and managing the
information well. There are total five stages of ITIL, this are as follows:
Service strategy
Service design
Service operation
Service transition
Continual service improvement
With the implementation off ITIL, there are some features offered by these and are
important. The metrics that will help to determine the better performance are as follows:
IT STRATEGY AND CONTROL
Answer to Question 1:
With the implementation of cloud computing, the performance of the organization
will get developed. Cloud service provides better way of storing the information with highest
security (Arpaci et al. 2015). The cloud computing decreases the cost and saves for every
organization. There are several architectures provided by the cloud service. According to the
need of customer, the organization can adopt cloud service. Moreover, cloud computing
offers their customer with the facility of paying as per their use. The organization can choose
PaaS architecture for their cloud service. This is designed for the companies that aims at
developing application or setting their application and aims at deploying these applications
within their cloud server (Bowers and Morse 2018). This is the best realistic strategy and will
help the organization in gaining more profit. With the help of IT service management
terminology, the organization can implement the cloud easily.
With the implementation of these five stages of ITIL, the organization can
implement the strategy. ITIL stands for information technology infrastructure library and this
has gained great importance in the managing the IT services (Al Mourad and Hussain 2014).
Thus, this strategy will eventually help the organization in storing and managing the
information well. There are total five stages of ITIL, this are as follows:
Service strategy
Service design
Service operation
Service transition
Continual service improvement
With the implementation off ITIL, there are some features offered by these and are
important. The metrics that will help to determine the better performance are as follows:

2
IT STRATEGY AND CONTROL
Services: this involves delivering a better product and service within the time.
Service management: this includes rules that will be followed by the employee while
delivering a product to their customers.
Value, utility and warranty: this is very much necessary to value customer’s feedback
and provide their services within the time. This is also necessary to utilize all the
rights assure by the organization towards their customer. Moreover, there is a
warranty provided towards the customers and it is the responsibility of the
organization to change or refund the product in case any problem occurs.
Capabilities: this is referred to the feature that involves organizing and adding value
to the resources generated by the organization.
Answer to Question 2:
COBIT aims at collecting the important information for an organization and providing
this information to the required one. The main objective is to manage the IT resources with
the help of a natural grouped process (Huygh et al. 2018). There are basically two types of
COBIT, this are COBIT 4.1 and COBIT 5. The difference between these two are as follows:
COBIT 4 is an IT Model whereas COBIT 5 is a IT governance and management
framework for IT enterprise.
COBIT 5 includes ITIL, COSO, TOGAF, ISO 27000, ISO 38500 and many more
where CBOIT 4 does not include this features.
COBIT 4 was introduced in 2004 and this was the early version with minimal features
and with the aim of providing and IT model to its users (Saputro, Utnami and Al Fatta
2018). The release of COBIT 5 has updated and removed all the problems faced while
working with COBIT 4.
IT STRATEGY AND CONTROL
Services: this involves delivering a better product and service within the time.
Service management: this includes rules that will be followed by the employee while
delivering a product to their customers.
Value, utility and warranty: this is very much necessary to value customer’s feedback
and provide their services within the time. This is also necessary to utilize all the
rights assure by the organization towards their customer. Moreover, there is a
warranty provided towards the customers and it is the responsibility of the
organization to change or refund the product in case any problem occurs.
Capabilities: this is referred to the feature that involves organizing and adding value
to the resources generated by the organization.
Answer to Question 2:
COBIT aims at collecting the important information for an organization and providing
this information to the required one. The main objective is to manage the IT resources with
the help of a natural grouped process (Huygh et al. 2018). There are basically two types of
COBIT, this are COBIT 4.1 and COBIT 5. The difference between these two are as follows:
COBIT 4 is an IT Model whereas COBIT 5 is a IT governance and management
framework for IT enterprise.
COBIT 5 includes ITIL, COSO, TOGAF, ISO 27000, ISO 38500 and many more
where CBOIT 4 does not include this features.
COBIT 4 was introduced in 2004 and this was the early version with minimal features
and with the aim of providing and IT model to its users (Saputro, Utnami and Al Fatta
2018). The release of COBIT 5 has updated and removed all the problems faced while
working with COBIT 4.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT STRATEGY AND CONTROL
These frameworks are effective for enterprises as these helps in meeting the needs of
the stakeholders and also strategies plan that will help in meeting the goal of enterprise. The
implementation COBIT within an organization is necessary as it helps to understand the
needs of stakeholders and also allows to set a generic goal for their customer. These goals set
by the enterprise can be developed with the help of a balanced scorecard dimensions. This
will help to understand and meet the goal. COBIT 5 is being developed based on the previous
version of COBIT that includes Val IT and Risk IT. This will help the organization to create
value for their stakeholders and will also create for governance objective (Nugraha, Winarno
and Al Fatta 2018). This is necessary for an organization to choose COBIT as these will help
to meet the goal set by the organization. This also ensures the needs of stakeholders and
prepares strategy to meet their needs and also monitors the activity of the stakeholders.
Management plans, runs, builds and monitors the activities that are set by the governance
body.
IT control framework is necessary for organization as this helps to manage the
traffics. It Control framework is exactly like a co-ordinated traffic light. This framework is in
form of data structure that is used to organize and categorize all the internal controls of
organization. This helps to minimize the risk and create more value towards the business.
Answer to Question 3:
Network security plan:
There is a need to develop a security plan that will protect the network from threats,
risks and intruders (Benson and Rahman 2015). The organization needs to develop a list of
points that will include points before entering into the network. The organization needs to
create a security policy and everyone associated with the network needs to follow this. There
is a need to include policy that will be used to maintain the confidentiality of the information
IT STRATEGY AND CONTROL
These frameworks are effective for enterprises as these helps in meeting the needs of
the stakeholders and also strategies plan that will help in meeting the goal of enterprise. The
implementation COBIT within an organization is necessary as it helps to understand the
needs of stakeholders and also allows to set a generic goal for their customer. These goals set
by the enterprise can be developed with the help of a balanced scorecard dimensions. This
will help to understand and meet the goal. COBIT 5 is being developed based on the previous
version of COBIT that includes Val IT and Risk IT. This will help the organization to create
value for their stakeholders and will also create for governance objective (Nugraha, Winarno
and Al Fatta 2018). This is necessary for an organization to choose COBIT as these will help
to meet the goal set by the organization. This also ensures the needs of stakeholders and
prepares strategy to meet their needs and also monitors the activity of the stakeholders.
Management plans, runs, builds and monitors the activities that are set by the governance
body.
IT control framework is necessary for organization as this helps to manage the
traffics. It Control framework is exactly like a co-ordinated traffic light. This framework is in
form of data structure that is used to organize and categorize all the internal controls of
organization. This helps to minimize the risk and create more value towards the business.
Answer to Question 3:
Network security plan:
There is a need to develop a security plan that will protect the network from threats,
risks and intruders (Benson and Rahman 2015). The organization needs to develop a list of
points that will include points before entering into the network. The organization needs to
create a security policy and everyone associated with the network needs to follow this. There
is a need to include policy that will be used to maintain the confidentiality of the information
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT STRATEGY AND CONTROL
stored within the organizations database (Obio and Mutale 2015). These is very much
necessary to understand the importance of the information and process accordingly this will
help the network to maintain the security and the data will not get breached. Different type of
network security available are (Shin, Wang and Gu 2015):
Access control
Application security
Behavioural analytics
Data loss prevention
Email security
Firewalls
Intrusion prevention system.
Risk assessment plan:
Risk assessment plant includes a document that contains a project manager and
prepare a document that will contain a foresee risks, defines responses towards the issues
raised, estimates the impacts. This also includes a risk assessment matrix. Risk is referred to
an uncertain event or condition that will create a negative impact on the organization. Thus,
this is very much necessary to develop a plan that will help to mitigate the risks. In addition
to this, the risk management plans also include matrices. There are four potential strategies
that are offered by risk management plans. This includes:
Avoid risk: the plan made by the project manager can be changed when subjected to
any kind of risks.
Control or mitigate risk: the risks can be mitigated or the impacts can be reduced
with the use of intermediate steps.
IT STRATEGY AND CONTROL
stored within the organizations database (Obio and Mutale 2015). These is very much
necessary to understand the importance of the information and process accordingly this will
help the network to maintain the security and the data will not get breached. Different type of
network security available are (Shin, Wang and Gu 2015):
Access control
Application security
Behavioural analytics
Data loss prevention
Email security
Firewalls
Intrusion prevention system.
Risk assessment plan:
Risk assessment plant includes a document that contains a project manager and
prepare a document that will contain a foresee risks, defines responses towards the issues
raised, estimates the impacts. This also includes a risk assessment matrix. Risk is referred to
an uncertain event or condition that will create a negative impact on the organization. Thus,
this is very much necessary to develop a plan that will help to mitigate the risks. In addition
to this, the risk management plans also include matrices. There are four potential strategies
that are offered by risk management plans. This includes:
Avoid risk: the plan made by the project manager can be changed when subjected to
any kind of risks.
Control or mitigate risk: the risks can be mitigated or the impacts can be reduced
with the use of intermediate steps.

5
IT STRATEGY AND CONTROL
Accept risk: after knowing the risk, the organization can take a chance so that they
can work according with the budget.
Transfer risk: outsourcing the risk to the third party will help in managing the risk.
Policy framework
A policy framework is in the form of document that offers a set of goals or procedures
that are used by the organization. This is used to negotiate or to make decision with a detailed
set of policies and also helps in providing maintenance towards the organization’s policies.
The main aim of having a policy framework is that it sets boundaries for the workers within
the organization. The developed guidelines are needed to be followed by the organization.
These offers a clear communication within the employees and also sets rules for their
behaviour.
Physical and logical controls
There are two types of controls this are physical and logical controls. The physical
access control includes limiting the access of buildings, areas, rooms and IT assets. Whereas
the logical access control is used to limit the connection of computer networks, data and
system files. The main difference between these two are the physical controls is used to
describe that the user can react to the computer’s hardware at any time. On the other hand the
logical control involves the use of computer from different rooms.
Information disclosure schedule
Disclosure schedule contains all the information that are needed by the acquisition
agreement. This includes listing the important contracts, employee information, intellectual
property and other material matters. This contains all the necessary details and representation
of these details along with the warranty provided by the selling company.
IT STRATEGY AND CONTROL
Accept risk: after knowing the risk, the organization can take a chance so that they
can work according with the budget.
Transfer risk: outsourcing the risk to the third party will help in managing the risk.
Policy framework
A policy framework is in the form of document that offers a set of goals or procedures
that are used by the organization. This is used to negotiate or to make decision with a detailed
set of policies and also helps in providing maintenance towards the organization’s policies.
The main aim of having a policy framework is that it sets boundaries for the workers within
the organization. The developed guidelines are needed to be followed by the organization.
These offers a clear communication within the employees and also sets rules for their
behaviour.
Physical and logical controls
There are two types of controls this are physical and logical controls. The physical
access control includes limiting the access of buildings, areas, rooms and IT assets. Whereas
the logical access control is used to limit the connection of computer networks, data and
system files. The main difference between these two are the physical controls is used to
describe that the user can react to the computer’s hardware at any time. On the other hand the
logical control involves the use of computer from different rooms.
Information disclosure schedule
Disclosure schedule contains all the information that are needed by the acquisition
agreement. This includes listing the important contracts, employee information, intellectual
property and other material matters. This contains all the necessary details and representation
of these details along with the warranty provided by the selling company.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6
IT STRATEGY AND CONTROL
The biggest security challenge that can be faced by the organization is with the
information getting leaked. As the organization stores important information and confidential
information of every customer. Thus, these data needs to be stored with highest security so
that no one can tamper this information’s. These is the main threat that is likely to be faced
by the organization. This is necessary to maintain the confidentiality of the information.
Answer to question 4:
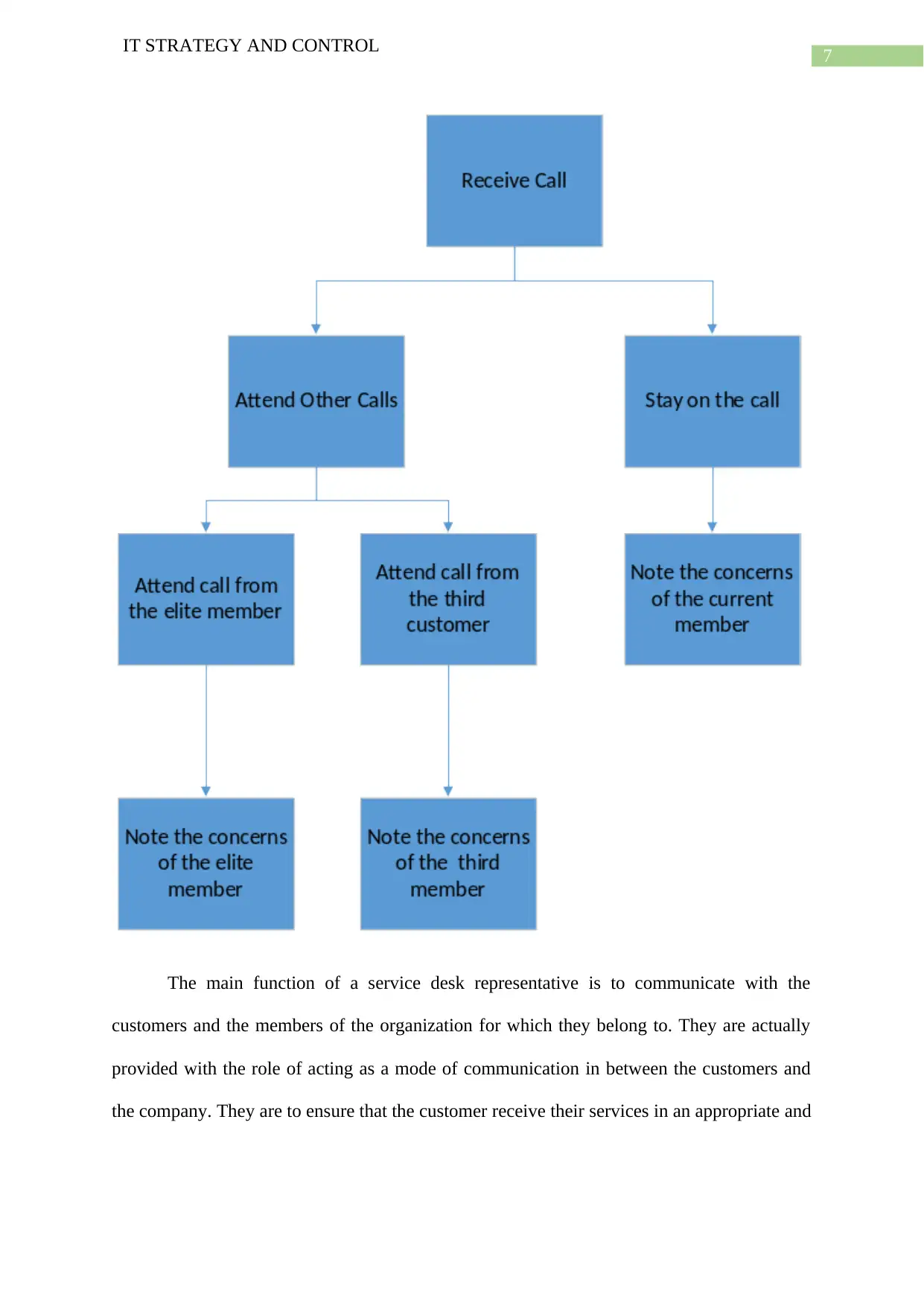
In the provided situation the service desk representative is already attending a call and
two more calls come in (Smith and Wong 2016). Hence, it is very important that the service
desk representative at the airline company prioritises the work and the form an idea about the
process that is to be followed which would help in taking important decision in very urgent
situations. Hence a decision tree is formed for providing the service desk representative with
an efficient solution in the current scenario. the decision tree for the scenario is provided
below:
IT STRATEGY AND CONTROL
The biggest security challenge that can be faced by the organization is with the
information getting leaked. As the organization stores important information and confidential
information of every customer. Thus, these data needs to be stored with highest security so
that no one can tamper this information’s. These is the main threat that is likely to be faced
by the organization. This is necessary to maintain the confidentiality of the information.
Answer to question 4:
In the provided situation the service desk representative is already attending a call and
two more calls come in (Smith and Wong 2016). Hence, it is very important that the service
desk representative at the airline company prioritises the work and the form an idea about the
process that is to be followed which would help in taking important decision in very urgent
situations. Hence a decision tree is formed for providing the service desk representative with
an efficient solution in the current scenario. the decision tree for the scenario is provided
below:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT STRATEGY AND CONTROL
The main function of a service desk representative is to communicate with the
customers and the members of the organization for which they belong to. They are actually
provided with the role of acting as a mode of communication in between the customers and
the company. They are to ensure that the customer receive their services in an appropriate and
IT STRATEGY AND CONTROL
The main function of a service desk representative is to communicate with the
customers and the members of the organization for which they belong to. They are actually
provided with the role of acting as a mode of communication in between the customers and
the company. They are to ensure that the customer receive their services in an appropriate and

8
IT STRATEGY AND CONTROL
timely process. This would help in the enhancement of the of customer satisfaction towards
the organization.
IT STRATEGY AND CONTROL
timely process. This would help in the enhancement of the of customer satisfaction towards
the organization.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT STRATEGY AND CONTROL
References
Al Mourad, M.B. and Hussain, M., 2014. The impact of cloud computing on ITIL service
strategy processes. International Journal of Computer and Communication Engineering,
3(5), p.367.
Arpaci, I., Kilicer, K. and Bardakci, S., 2015. Effects of security and privacy concerns on
educational use of cloud services. Computers in Human Behavior, 45, pp.93-98.
Benson, K. and Rahman, S., 2015. Security Risks in Mechanical Engineering Industries.
arXiv preprint arXiv:1512.01730.
Bowers, D. and Morse, D., 2018. Including IT service management in the Computing
curriculum: a caricature approach.
Huygh, T., De Haes, S., Joshi, A. and Van Grembergen, W., 2018, January. Answering key
global IT management concerns through IT governance and management processes: A
COBIT 5 View. In Proceedings of the 51st Hawaii International Conference on System
Sciences.
Nugraha, T.R.T.P., Winarno, W.W. and Al Fatta, H., 2018. ANALISIS SISTEM
INFORMASI AKADEMIK MENGGUNAKAN DOMAIN DELIVERY AND SUPPORT
COBIT 5 PADA SMKN 4 YOGYAKARTA. Jurnal Ilmiah Teknologi Informasi, 8(1).
Obio, E.B. and Mutale, J., 2015, September. A comparative analysis of energy storage and N-
1 network security in transmission expansion planning. In Power Engineering Conference
(UPEC), 2015 50th International Universities (pp. 1-6). IEEE.
Saputro, F.E.N., Utami, E. and Al Fatta, H., 2018. Integrasi Framework COBIT 5 dan ITIL
V. 3 Untuk Membangun Model Tata Kelola Infrastruktur Teknologi Informasi. Konferensi
Nasional Sistem Informasi (KNSI) 2018.
IT STRATEGY AND CONTROL
References
Al Mourad, M.B. and Hussain, M., 2014. The impact of cloud computing on ITIL service
strategy processes. International Journal of Computer and Communication Engineering,
3(5), p.367.
Arpaci, I., Kilicer, K. and Bardakci, S., 2015. Effects of security and privacy concerns on
educational use of cloud services. Computers in Human Behavior, 45, pp.93-98.
Benson, K. and Rahman, S., 2015. Security Risks in Mechanical Engineering Industries.
arXiv preprint arXiv:1512.01730.
Bowers, D. and Morse, D., 2018. Including IT service management in the Computing
curriculum: a caricature approach.
Huygh, T., De Haes, S., Joshi, A. and Van Grembergen, W., 2018, January. Answering key
global IT management concerns through IT governance and management processes: A
COBIT 5 View. In Proceedings of the 51st Hawaii International Conference on System
Sciences.
Nugraha, T.R.T.P., Winarno, W.W. and Al Fatta, H., 2018. ANALISIS SISTEM
INFORMASI AKADEMIK MENGGUNAKAN DOMAIN DELIVERY AND SUPPORT
COBIT 5 PADA SMKN 4 YOGYAKARTA. Jurnal Ilmiah Teknologi Informasi, 8(1).
Obio, E.B. and Mutale, J., 2015, September. A comparative analysis of energy storage and N-
1 network security in transmission expansion planning. In Power Engineering Conference
(UPEC), 2015 50th International Universities (pp. 1-6). IEEE.
Saputro, F.E.N., Utami, E. and Al Fatta, H., 2018. Integrasi Framework COBIT 5 dan ITIL
V. 3 Untuk Membangun Model Tata Kelola Infrastruktur Teknologi Informasi. Konferensi
Nasional Sistem Informasi (KNSI) 2018.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT STRATEGY AND CONTROL
Shin, S., Wang, H. and Gu, G., 2015. A first step toward network security virtualization: from
concept to prototype. IEEE Transactions on Information Forensics and Security, 10(10),
pp.2236-2249.
Smith, L.C. and Wong, M.A. eds., 2016. Reference and Information Services: An
Introduction: An Introduction. ABC-CLIO.
IT STRATEGY AND CONTROL
Shin, S., Wang, H. and Gu, G., 2015. A first step toward network security virtualization: from
concept to prototype. IEEE Transactions on Information Forensics and Security, 10(10),
pp.2236-2249.
Smith, L.C. and Wong, M.A. eds., 2016. Reference and Information Services: An
Introduction: An Introduction. ABC-CLIO.
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





