Project Implementation Report: IT Virtualization on VMware Analysis
VerifiedAdded on 2020/01/23
|15
|2883
|56
Report
AI Summary
This report details a project implementing IT virtualization using VMware, specifically focusing on the LOGIIC initiative, which assessed cybersecurity in the oil and gas sector. The project evaluated virtualization solutions within an operational environment, aiming to create guidelines for securing virtual environments across multiple process control network layers. The report presents technical findings, vulnerabilities identified during assessments, and recommendations for secure virtualization in IACS environments. Key areas of focus include security considerations across hardware, software, and implementation, including role-based access control, password management, and patch management. The report emphasizes the importance of understanding automation vendor practices, layered security, and the need for strong technical skills for design, setup, and management. It highlights the critical role of patching and system support in mitigating vulnerabilities and ensuring the stability of the virtualized environment. The findings underscore the importance of a proactive approach to security, including physical access controls, and comprehensive life-cycle planning.

Running head: IT VIRTUALIZATION ON VMWARE
1
Project implementation
Name
Institution Affiliation
1
Project implementation
Name
Institution Affiliation
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1.1 Introduction
Virtualization is a software technology that make bit possible to run multiple syatems and a
applications on the same server at the same time. VMware company has embraced the use of this
technology that has several benefits. The report covers show the a project under the vmwares
known as the LOGIIC. It was a program introduced to review and study cybersecurity issues as
they concern the oil and gas sector. The LOGIIC initiatives are applicable to numerous industries
with control systems
The project concentrates on the use of virtualization solutions in the operational environment.
The primary project goal was to evaluate and test current automation vendor industry practices to
generate guidelines and reference architectures that present techniquesfor securing virtual
environments that spans multiple process control network layers. LOGIIC directed a progression
of exploration reviews and studies to distinguish item offerings in the commercial center, their
materialness the IACS environment, and their digital security abilities. Hands-on evaluation
exercises directed in an IACS situation distinguished the security capacities of virtualization
arrangements and the effects connected with their utilization in an operational setting. This report
presents conclusions on the utilization of virtualization in an IACS domain. These
determinations are a consequence of specialized appraisal and investigation. The target of this
report is to pass on critical variables that should be weighed while considering virtualization in
an IACS situation and to bolster a discourse between resource proprietors and mechanization
vendors. The target group for this report is the IACS specialized and security groups, and
computerization and security vendors.
1.2 Objectives
Virtualization is a software technology that make bit possible to run multiple syatems and a
applications on the same server at the same time. VMware company has embraced the use of this
technology that has several benefits. The report covers show the a project under the vmwares
known as the LOGIIC. It was a program introduced to review and study cybersecurity issues as
they concern the oil and gas sector. The LOGIIC initiatives are applicable to numerous industries
with control systems
The project concentrates on the use of virtualization solutions in the operational environment.
The primary project goal was to evaluate and test current automation vendor industry practices to
generate guidelines and reference architectures that present techniquesfor securing virtual
environments that spans multiple process control network layers. LOGIIC directed a progression
of exploration reviews and studies to distinguish item offerings in the commercial center, their
materialness the IACS environment, and their digital security abilities. Hands-on evaluation
exercises directed in an IACS situation distinguished the security capacities of virtualization
arrangements and the effects connected with their utilization in an operational setting. This report
presents conclusions on the utilization of virtualization in an IACS domain. These
determinations are a consequence of specialized appraisal and investigation. The target of this
report is to pass on critical variables that should be weighed while considering virtualization in
an IACS situation and to bolster a discourse between resource proprietors and mechanization
vendors. The target group for this report is the IACS specialized and security groups, and
computerization and security vendors.
1.2 Objectives

The project key aim was to assess and test current mechanization seller industry practices to
produce rules and reference structures that show strategies for securing virtual situations that
traverse various procedure control system layers.
The project also aims in creating confidence in security, maintainability, implementation, and
optimization prior to expanding the use of virtualization in their organizations.
1.3 Specifications for the agreed project
It was considered in the following the ways:
Access to and development of information between security zones
Management of legacy frameworks and applications
Historization
Factory acknowledgment testing
Training and support/administrator capacities
Lab and reproduction situations
Utility frameworks that backing the BPCS
HMI workstations and servers
Footprint lessening
Advanced control applications
Calculation programs
Domain controllers
Optimization frameworks
Database frameworks
produce rules and reference structures that show strategies for securing virtual situations that
traverse various procedure control system layers.
The project also aims in creating confidence in security, maintainability, implementation, and
optimization prior to expanding the use of virtualization in their organizations.
1.3 Specifications for the agreed project
It was considered in the following the ways:
Access to and development of information between security zones
Management of legacy frameworks and applications
Historization
Factory acknowledgment testing
Training and support/administrator capacities
Lab and reproduction situations
Utility frameworks that backing the BPCS
HMI workstations and servers
Footprint lessening
Advanced control applications
Calculation programs
Domain controllers
Optimization frameworks
Database frameworks
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The goals of the undertaking's appraisal centered around noting key specialized inquiries
identified with the utilization of virtualization in an operational situation.
1.4 Project plan
Test situation
Test situations were created to deliver results that reply specialized inquiries identifying with
execution, outline, particular use cases; and to give contribution to essential conclusions with
respect to the utilization of virtualization when all is said in done.
As defined by LOGIIC, the following scenarios in Figure 1 were within the scope.
identified with the utilization of virtualization in an operational situation.
1.4 Project plan
Test situation
Test situations were created to deliver results that reply specialized inquiries identifying with
execution, outline, particular use cases; and to give contribution to essential conclusions with
respect to the utilization of virtualization when all is said in done.
As defined by LOGIIC, the following scenarios in Figure 1 were within the scope.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
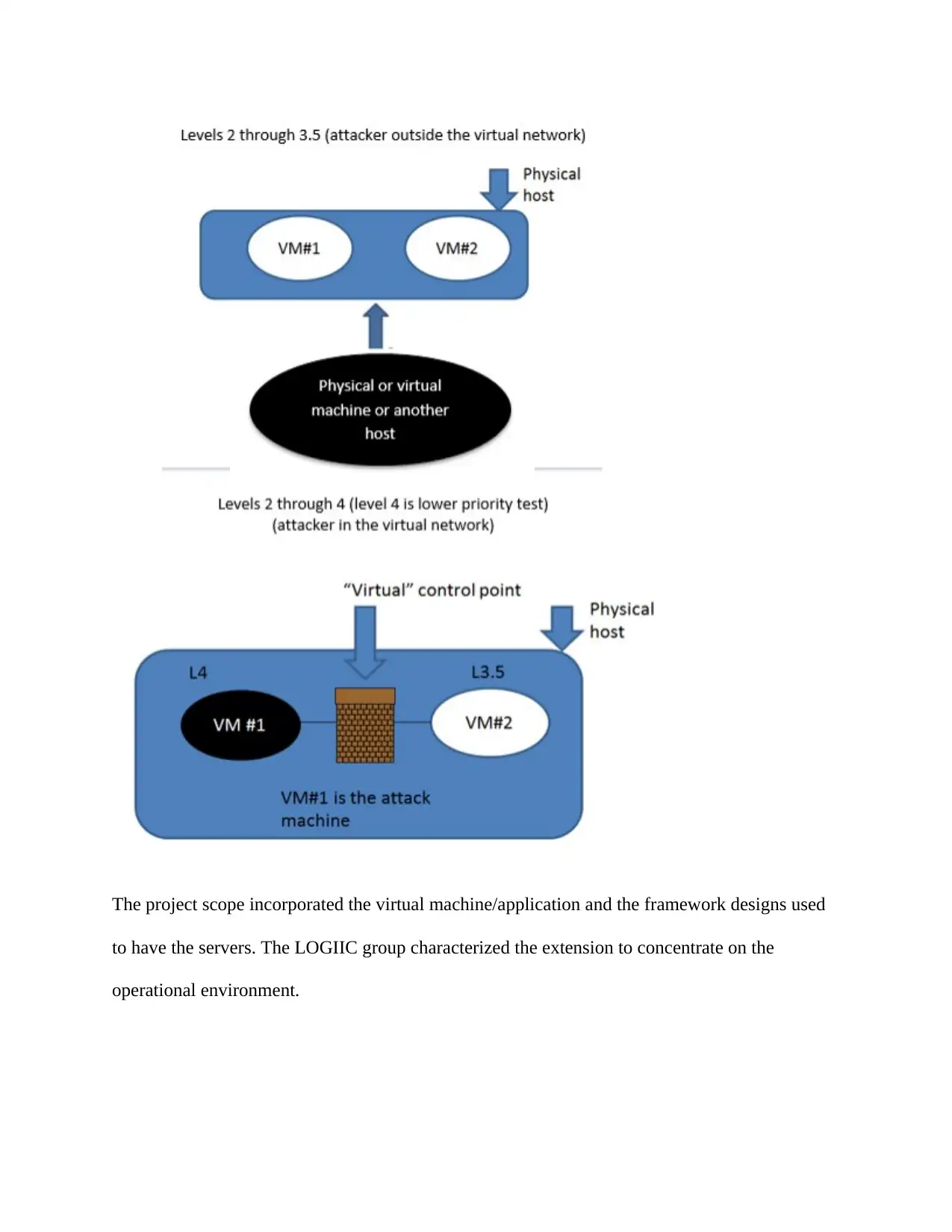
The project scope incorporated the virtual machine/application and the framework designs used
to have the servers. The LOGIIC group characterized the extension to concentrate on the
operational environment.
to have the servers. The LOGIIC group characterized the extension to concentrate on the
operational environment.
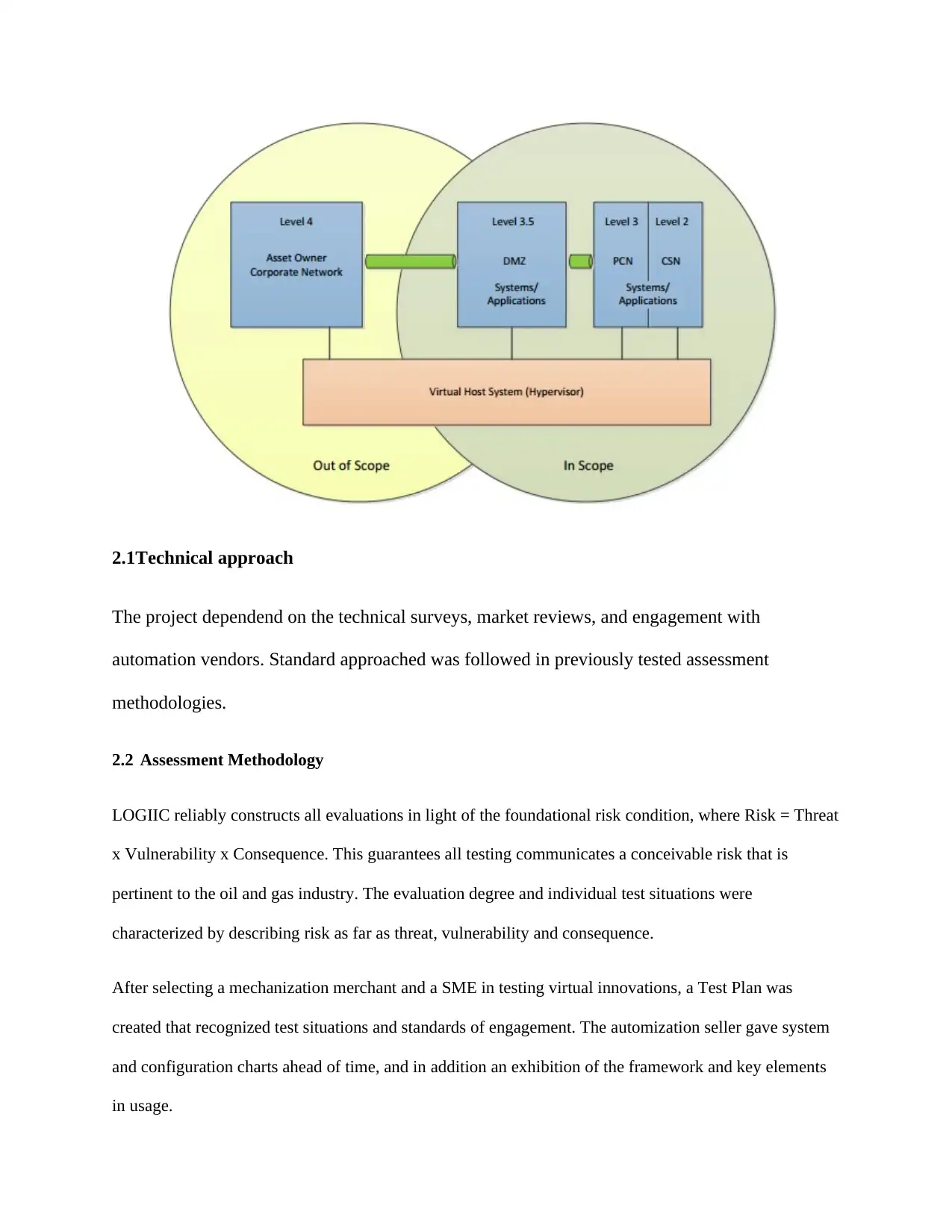
2.1Technical approach
The project dependend on the technical surveys, market reviews, and engagement with
automation vendors. Standard approached was followed in previously tested assessment
methodologies.
2.2 Assessment Methodology
LOGIIC reliably constructs all evaluations in light of the foundational risk condition, where Risk = Threat
x Vulnerability x Consequence. This guarantees all testing communicates a conceivable risk that is
pertinent to the oil and gas industry. The evaluation degree and individual test situations were
characterized by describing risk as far as threat, vulnerability and consequence.
After selecting a mechanization merchant and a SME in testing virtual innovations, a Test Plan was
created that recognized test situations and standards of engagement. The automization seller gave system
and configuration charts ahead of time, and in addition an exhibition of the framework and key elements
in usage.
The project dependend on the technical surveys, market reviews, and engagement with
automation vendors. Standard approached was followed in previously tested assessment
methodologies.
2.2 Assessment Methodology
LOGIIC reliably constructs all evaluations in light of the foundational risk condition, where Risk = Threat
x Vulnerability x Consequence. This guarantees all testing communicates a conceivable risk that is
pertinent to the oil and gas industry. The evaluation degree and individual test situations were
characterized by describing risk as far as threat, vulnerability and consequence.
After selecting a mechanization merchant and a SME in testing virtual innovations, a Test Plan was
created that recognized test situations and standards of engagement. The automization seller gave system
and configuration charts ahead of time, and in addition an exhibition of the framework and key elements
in usage.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The accompanying high level state steps were taken after amid the appraisal for every gadget or
arrangement of gadgets:
1. Reconnaissance
2. Data Capture/Data Retrieval Attempts
3.Targeted Attack
Similarly as with the standard LOGIIC evaluation approach, attacks were just viewed as reasonable on
the off chance that they were traceable and reproducible. While specialized exercises, for example,
surveillance and assault, frame the premise for a large portion of the evaluation, discoveries, perceptions
about collaborations with gadgets, setup, and investigating can give important data for the LOGIIC group.
Execution of security elements, versatility, and power were measured by specialized results and by
general perceptions amid the appraisal.
2.3 Assessment Approach
The main virtualization product is the VMware serve as the basis for approximately all vitualisation
solutions presently offered by automatic vendors. Implementation of the product was tested during a
single assessment period. Test vectors were created by the LOGIIC group, and by the SME, to answer
key inquiries of particular enthusiasm to the LOGIIC individuals. These test vectors, recorded
underneath, were used by the SME to create more extensive test situations and select appropriate devices.
The SME employed reconnaissance and attack techniques that included the following ways.
arrangement of gadgets:
1. Reconnaissance
2. Data Capture/Data Retrieval Attempts
3.Targeted Attack
Similarly as with the standard LOGIIC evaluation approach, attacks were just viewed as reasonable on
the off chance that they were traceable and reproducible. While specialized exercises, for example,
surveillance and assault, frame the premise for a large portion of the evaluation, discoveries, perceptions
about collaborations with gadgets, setup, and investigating can give important data for the LOGIIC group.
Execution of security elements, versatility, and power were measured by specialized results and by
general perceptions amid the appraisal.
2.3 Assessment Approach
The main virtualization product is the VMware serve as the basis for approximately all vitualisation
solutions presently offered by automatic vendors. Implementation of the product was tested during a
single assessment period. Test vectors were created by the LOGIIC group, and by the SME, to answer
key inquiries of particular enthusiasm to the LOGIIC individuals. These test vectors, recorded
underneath, were used by the SME to create more extensive test situations and select appropriate devices.
The SME employed reconnaissance and attack techniques that included the following ways.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

i. Under the reconnaissance there were the following things.
Survey the architecture
Identification of unnecessary services
Surveying and verification encryption.
Surveying the access control
Searching for the known vulnerabilities in the architecture
Identification of assets and keys
Performance of the auditing
Identification of attack and deanial of service vectors within the architecture.
ii. On the testing basis
Assess configuration
Evaluate arrangement against standard usage rehearses
Identify exploitable vulnerabilities
Image administration examination
Test update/patch usefulness
Test strength of framework
Virtual environment system setup assessment
VM OS confinement examination
Virtual environment application assessment
Pivot attacks
3.1. Evaluation technique and findings
Despite the fact that the evaluation concentrated on the security parts of utilizing virtualization
innovations as a part of the IACS environment, and any dangers connected with such a usage,
thought was additionally given amid the testing to simplicity of setup, support, information and
Survey the architecture
Identification of unnecessary services
Surveying and verification encryption.
Surveying the access control
Searching for the known vulnerabilities in the architecture
Identification of assets and keys
Performance of the auditing
Identification of attack and deanial of service vectors within the architecture.
ii. On the testing basis
Assess configuration
Evaluate arrangement against standard usage rehearses
Identify exploitable vulnerabilities
Image administration examination
Test update/patch usefulness
Test strength of framework
Virtual environment system setup assessment
VM OS confinement examination
Virtual environment application assessment
Pivot attacks
3.1. Evaluation technique and findings
Despite the fact that the evaluation concentrated on the security parts of utilizing virtualization
innovations as a part of the IACS environment, and any dangers connected with such a usage,
thought was additionally given amid the testing to simplicity of setup, support, information and

assets to keep up, and ease of use. The SME evaluation group, mechanization seller, and LOGIIC
specialized administration cooperated to shape more extensive conclusions.
3.2.Assessments Findings
The assessment offered numerous technical and operational findings.
Technical findings and vulnerabilities
During the assessment the SME conducted approximately the same number of test cases against
VMware architectures. Some test cases were direct exploit attempts, other cases focused on
information collection as building blocks for other attacks. Discoveries from every experiment
were looked into and positioned by outcome based seriousness and probability. Specialized
vulnerabilities were recognized in equipment, programming, and execution territories. These
vulnerabilities are gathered into more extensive danger classes recorded in the rest of this area.
Every range is important while considering the utilization of virtualization in an IACS situation,
and ought to be incorporated into the assessment, determination, and configuration process.
Likewise with any figuring ability actualized in an IACS situation, security must be considered
by any stretch of the imagination consistent layers of the arrangement and for the duration of the
life cycle. All standard security contemplations inside equipment, programming, execution, ease
of use, and execution affects that are normally said something another venture must be considered
with a virtualization arrangement. In any case, because of the decreased impression and potential
complexities of the framework, extra characteristics must be assessed. Security must be
incorporated with the configuration, counting measures past upkeep of the VMs. For instance, the
accompanying must be considered not just for visitor working frameworks and control
framework programming, additionally for hypervisors and virtualization administration
programming:
Role-based access control
specialized administration cooperated to shape more extensive conclusions.
3.2.Assessments Findings
The assessment offered numerous technical and operational findings.
Technical findings and vulnerabilities
During the assessment the SME conducted approximately the same number of test cases against
VMware architectures. Some test cases were direct exploit attempts, other cases focused on
information collection as building blocks for other attacks. Discoveries from every experiment
were looked into and positioned by outcome based seriousness and probability. Specialized
vulnerabilities were recognized in equipment, programming, and execution territories. These
vulnerabilities are gathered into more extensive danger classes recorded in the rest of this area.
Every range is important while considering the utilization of virtualization in an IACS situation,
and ought to be incorporated into the assessment, determination, and configuration process.
Likewise with any figuring ability actualized in an IACS situation, security must be considered
by any stretch of the imagination consistent layers of the arrangement and for the duration of the
life cycle. All standard security contemplations inside equipment, programming, execution, ease
of use, and execution affects that are normally said something another venture must be considered
with a virtualization arrangement. In any case, because of the decreased impression and potential
complexities of the framework, extra characteristics must be assessed. Security must be
incorporated with the configuration, counting measures past upkeep of the VMs. For instance, the
accompanying must be considered not just for visitor working frameworks and control
framework programming, additionally for hypervisors and virtualization administration
programming:
Role-based access control
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

User and managerial record administration
Password administration, for example, evacuation of default passwords, and necessities for least
multifaceted nature and lapse
Operating framework and programming redesigns and fixes
System log checking and interruption discovery
Standard parts of virtual arrangements, for example, regular administrations, ports, and web
components, may contain vulnerabilities that are not as a matter of course alleviated by
virtualization. Regular parts incorporate Remote Desktop Protocol (RDP), the Windows NT LAN
Manager (NTLM) utilized as the test/reaction convention, and normal credentialing frameworks.
These might be powerless against man-in-the-center (MITM) attacks, word reference attacks, and
other normal adventures. In this way, layered digital security that considers these dangers is vital
all through the configuration and usage.
3.3 Recommendation
Regardless of the division of VMs, the security and soundness effects of shared equipment and
systems administration must be considered. Hypervisors and virtualization administration parts
get to be basic, high-esteem resources.
I. A large number of the discoveries from the LOGIIC evaluation concentrated on the
significance of Hyper-V manager. The specialized discoveries prompted the conclusion
that setup is basic among these high-esteem parts. The Hyper-V® Manager controls all
VM activities, for example, beginning, ceasing, arrangement, creation, and erasure.
Lessening of dangers at setup and great administration practices can together alleviate
numerous vulnerabilities. For instance, these practices incorporate bans on single-client
records, normal fixing, bans on default passwords, and logging and observing. In like
Password administration, for example, evacuation of default passwords, and necessities for least
multifaceted nature and lapse
Operating framework and programming redesigns and fixes
System log checking and interruption discovery
Standard parts of virtual arrangements, for example, regular administrations, ports, and web
components, may contain vulnerabilities that are not as a matter of course alleviated by
virtualization. Regular parts incorporate Remote Desktop Protocol (RDP), the Windows NT LAN
Manager (NTLM) utilized as the test/reaction convention, and normal credentialing frameworks.
These might be powerless against man-in-the-center (MITM) attacks, word reference attacks, and
other normal adventures. In this way, layered digital security that considers these dangers is vital
all through the configuration and usage.
3.3 Recommendation
Regardless of the division of VMs, the security and soundness effects of shared equipment and
systems administration must be considered. Hypervisors and virtualization administration parts
get to be basic, high-esteem resources.
I. A large number of the discoveries from the LOGIIC evaluation concentrated on the
significance of Hyper-V manager. The specialized discoveries prompted the conclusion
that setup is basic among these high-esteem parts. The Hyper-V® Manager controls all
VM activities, for example, beginning, ceasing, arrangement, creation, and erasure.
Lessening of dangers at setup and great administration practices can together alleviate
numerous vulnerabilities. For instance, these practices incorporate bans on single-client
records, normal fixing, bans on default passwords, and logging and observing. In like
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

manner, vCenter™ Server records ought to likewise utilize part based access control
without default passwords. Both the vCenter™ Server and, Hyper-V® Manager can be
utilized with firewalls. These ought to be arranged and looked after likewise.
II. An asset proprietor's reasonable comprehension of the computerization vendor's
virtualization offering is critical in the configuration and execution of the item. Resource
proprietors ought to be completely mindful of the computerization seller's outline,
execution arrangement, risk moderation and patch administration blueprint. The
significance of life-cycle arranging and fix administration is noteworthy, and talked about
in further segments in point of interest. All in all, in any case, resource proprietors ought
to know that computerization seller practices ought to include:
Inherent layered security
Documented security proposals
Fault resilience, high accessibility, and failover choices
Good coding practices, for example, code confusion and no hard-coded passwords
Long term sensibility and versatility
Established procedures to oversee changing dangers with development
I. Another expansive outline and usage thought is risk and physical access. Insider
danger and physical access to equipment give various chances to misuse.
Physical access to the equipment gives a chance to bargain the framework, and it represents a
security risk that ought to be assessed and relieved with site security controls. This may
incorporate access to USB and other open ports with choices to get to the BIOS, console, and
logon screens. Specialized conclusions made by the SME show that physical access may
demonstrate full responsibility for framework.
In the same way as other innovations connected in the IACS environment, improving a procedure
or boosting advantage frequently requires interface with complex advances. Virtualization, in the
without default passwords. Both the vCenter™ Server and, Hyper-V® Manager can be
utilized with firewalls. These ought to be arranged and looked after likewise.
II. An asset proprietor's reasonable comprehension of the computerization vendor's
virtualization offering is critical in the configuration and execution of the item. Resource
proprietors ought to be completely mindful of the computerization seller's outline,
execution arrangement, risk moderation and patch administration blueprint. The
significance of life-cycle arranging and fix administration is noteworthy, and talked about
in further segments in point of interest. All in all, in any case, resource proprietors ought
to know that computerization seller practices ought to include:
Inherent layered security
Documented security proposals
Fault resilience, high accessibility, and failover choices
Good coding practices, for example, code confusion and no hard-coded passwords
Long term sensibility and versatility
Established procedures to oversee changing dangers with development
I. Another expansive outline and usage thought is risk and physical access. Insider
danger and physical access to equipment give various chances to misuse.
Physical access to the equipment gives a chance to bargain the framework, and it represents a
security risk that ought to be assessed and relieved with site security controls. This may
incorporate access to USB and other open ports with choices to get to the BIOS, console, and
logon screens. Specialized conclusions made by the SME show that physical access may
demonstrate full responsibility for framework.
In the same way as other innovations connected in the IACS environment, improving a procedure
or boosting advantage frequently requires interface with complex advances. Virtualization, in the

VMWare® environment, requires solid specialized abilities to outline, set up, and deal with the
framework, and to amplify the advantage of the innovation. Utilization of virtualization in the
IACS environment requires assessment of dangers to center frameworks. Recognizable proof and
alleviation of the dangers to center frameworks made by shared equipment, physical access, and
complex systems administration ought to happen in the outline stage. This assessment ought to
incorporate recognizable proof of any basic disappointment focuses and decide the requirements
for failover, adaptation to internal failure, and high accessibility. Early engagement with the
computerization seller is essential keeping in mind the end goal to determine the most relevant
outline preceding usage. Despite the fact that setup and usage might be performed fundamentally
by the automation vendor, it ought to be expected that the benefit proprietor will require solid
specialized assets accessible at their site to oversee and screen the virtual situations. These assets
ought to incorporate server, framework, and organizing aptitudes. As finished up by the testing,
usage mistakes or misconfigurations could prompt vulnerabilities, but may likewise destabilize
the framework.
Patching
Maybe the most imperative of the appraisal's operational discoveries is the requirement for fixing
and framework support. A considerable lot of the assaults succeed in light of the fact that the
framework was not completely fixed and a la mode at the time of testing. This demonstrates the
significance of breakthrough fixing. Unpatched frameworks have essentially
bigger assault surfaces. An essential thought is the way that Hyper-V® and VMWare® patches
may not be certify by the computerization seller, or may not be licensed instantly. This requires
the benefit proprietor to autonomously download and introduce qualified patches for VMWare®
and Hyper-V®. Some benefit proprietors might be hesitant to do this without robotization seller
framework, and to amplify the advantage of the innovation. Utilization of virtualization in the
IACS environment requires assessment of dangers to center frameworks. Recognizable proof and
alleviation of the dangers to center frameworks made by shared equipment, physical access, and
complex systems administration ought to happen in the outline stage. This assessment ought to
incorporate recognizable proof of any basic disappointment focuses and decide the requirements
for failover, adaptation to internal failure, and high accessibility. Early engagement with the
computerization seller is essential keeping in mind the end goal to determine the most relevant
outline preceding usage. Despite the fact that setup and usage might be performed fundamentally
by the automation vendor, it ought to be expected that the benefit proprietor will require solid
specialized assets accessible at their site to oversee and screen the virtual situations. These assets
ought to incorporate server, framework, and organizing aptitudes. As finished up by the testing,
usage mistakes or misconfigurations could prompt vulnerabilities, but may likewise destabilize
the framework.
Patching
Maybe the most imperative of the appraisal's operational discoveries is the requirement for fixing
and framework support. A considerable lot of the assaults succeed in light of the fact that the
framework was not completely fixed and a la mode at the time of testing. This demonstrates the
significance of breakthrough fixing. Unpatched frameworks have essentially
bigger assault surfaces. An essential thought is the way that Hyper-V® and VMWare® patches
may not be certify by the computerization seller, or may not be licensed instantly. This requires
the benefit proprietor to autonomously download and introduce qualified patches for VMWare®
and Hyper-V®. Some benefit proprietors might be hesitant to do this without robotization seller
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.
