School of Computing and Maths - ITC506 Ethics Case Study Analysis
VerifiedAdded on 2021/04/17
|6
|2080
|21
Case Study
AI Summary
This case study, submitted by a student, analyzes an ethical dilemma within the Willis Project, focusing on the pressure to deliver software ahead of schedule by foregoing essential security measures. The student applies the 'Doing Ethics Technique' to dissect the situation, identifying key facts, non-ethical and ethical issues, and stakeholders affected by the decision to potentially release software without encryption. The analysis explores the implications of prioritizing profit and deadlines over data security, evaluating various options, and ultimately recommending the best course of action to protect the interests of all parties involved. The assignment also considers the ethical responsibilities of the project team, project director, and CIO, while referencing relevant literature to support the arguments. The student concludes that the project director should prioritize ethical considerations and convince the CIO to maintain encryption, avoiding potential damage to the company's reputation and client security.

SCHOOL OF COMPUTING AND MATHS, Charles Sturt University
Title of your case study/scenario
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:
Title of your case study/scenario
Assignment 1: Doing Ethics Technique
Your Name
Student Number
Word Count:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Title of you case study/scenario
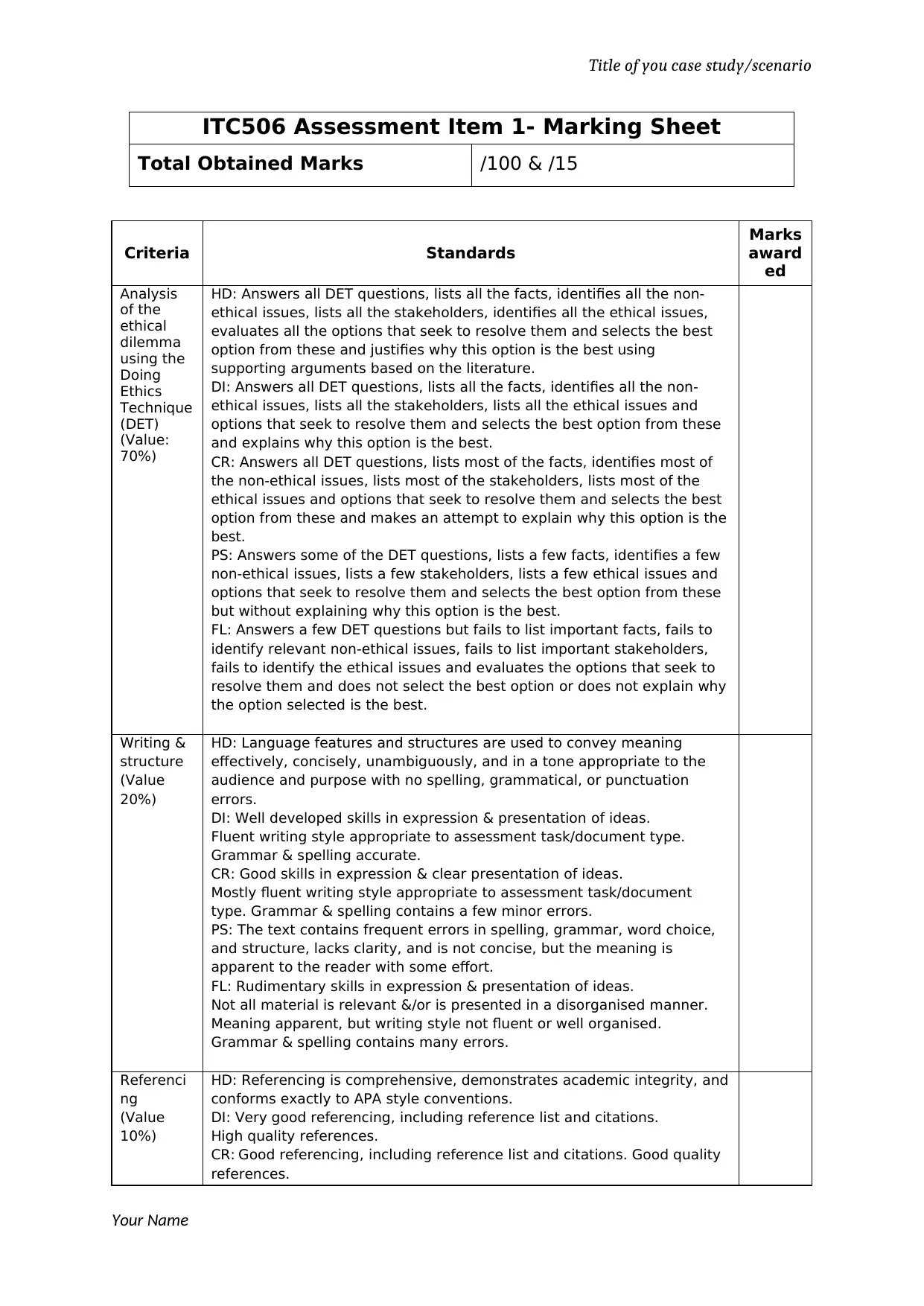
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
ITC506 Assessment Item 1- Marking Sheet
Total Obtained Marks /100 & /15
Criteria Standards
Marks
award
ed
Analysis
of the
ethical
dilemma
using the
Doing
Ethics
Technique
(DET)
(Value:
70%)
HD: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, identifies all the ethical issues,
evaluates all the options that seek to resolve them and selects the best
option from these and justifies why this option is the best using
supporting arguments based on the literature.
DI: Answers all DET questions, lists all the facts, identifies all the non-
ethical issues, lists all the stakeholders, lists all the ethical issues and
options that seek to resolve them and selects the best option from these
and explains why this option is the best.
CR: Answers all DET questions, lists most of the facts, identifies most of
the non-ethical issues, lists most of the stakeholders, lists most of the
ethical issues and options that seek to resolve them and selects the best
option from these and makes an attempt to explain why this option is the
best.
PS: Answers some of the DET questions, lists a few facts, identifies a few
non-ethical issues, lists a few stakeholders, lists a few ethical issues and
options that seek to resolve them and selects the best option from these
but without explaining why this option is the best.
FL: Answers a few DET questions but fails to list important facts, fails to
identify relevant non-ethical issues, fails to list important stakeholders,
fails to identify the ethical issues and evaluates the options that seek to
resolve them and does not select the best option or does not explain why
the option selected is the best.
Writing &
structure
(Value
20%)
HD: Language features and structures are used to convey meaning
effectively, concisely, unambiguously, and in a tone appropriate to the
audience and purpose with no spelling, grammatical, or punctuation
errors.
DI: Well developed skills in expression & presentation of ideas.
Fluent writing style appropriate to assessment task/document type.
Grammar & spelling accurate.
CR: Good skills in expression & clear presentation of ideas.
Mostly fluent writing style appropriate to assessment task/document
type. Grammar & spelling contains a few minor errors.
PS: The text contains frequent errors in spelling, grammar, word choice,
and structure, lacks clarity, and is not concise, but the meaning is
apparent to the reader with some effort.
FL: Rudimentary skills in expression & presentation of ideas.
Not all material is relevant &/or is presented in a disorganised manner.
Meaning apparent, but writing style not fluent or well organised.
Grammar & spelling contains many errors.
Referenci
ng
(Value
10%)
HD: Referencing is comprehensive, demonstrates academic integrity, and
conforms exactly to APA style conventions.
DI: Very good referencing, including reference list and citations.
High quality references.
CR: Good referencing, including reference list and citations. Good quality
references.
Your Name
Title of you case study/scenario
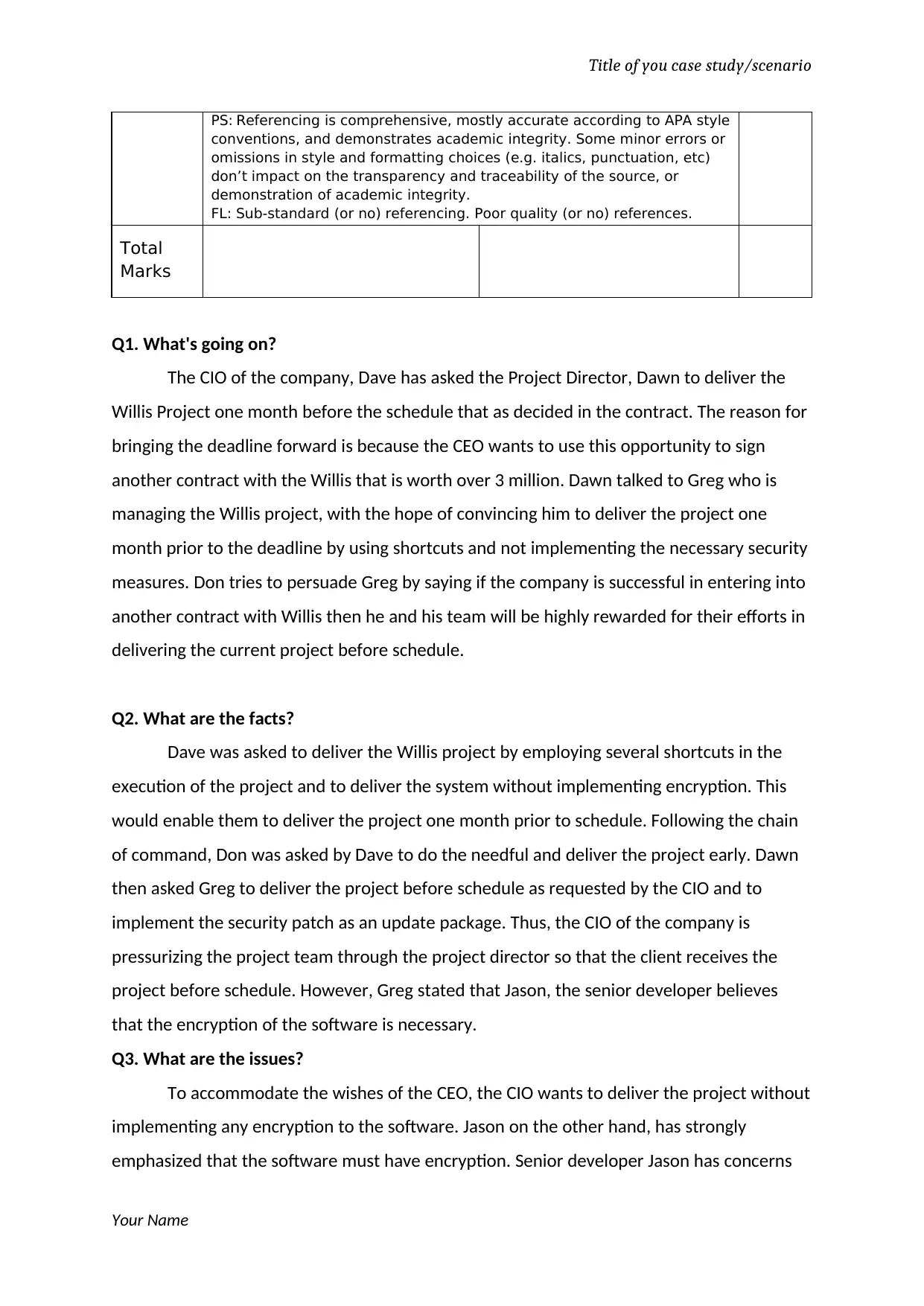
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
The CIO of the company, Dave has asked the Project Director, Dawn to deliver the
Willis Project one month before the schedule that as decided in the contract. The reason for
bringing the deadline forward is because the CEO wants to use this opportunity to sign
another contract with the Willis that is worth over 3 million. Dawn talked to Greg who is
managing the Willis project, with the hope of convincing him to deliver the project one
month prior to the deadline by using shortcuts and not implementing the necessary security
measures. Don tries to persuade Greg by saying if the company is successful in entering into
another contract with Willis then he and his team will be highly rewarded for their efforts in
delivering the current project before schedule.
Q2. What are the facts?
Dave was asked to deliver the Willis project by employing several shortcuts in the
execution of the project and to deliver the system without implementing encryption. This
would enable them to deliver the project one month prior to schedule. Following the chain
of command, Don was asked by Dave to do the needful and deliver the project early. Dawn
then asked Greg to deliver the project before schedule as requested by the CIO and to
implement the security patch as an update package. Thus, the CIO of the company is
pressurizing the project team through the project director so that the client receives the
project before schedule. However, Greg stated that Jason, the senior developer believes
that the encryption of the software is necessary.
Q3. What are the issues?
To accommodate the wishes of the CEO, the CIO wants to deliver the project without
implementing any encryption to the software. Jason on the other hand, has strongly
emphasized that the software must have encryption. Senior developer Jason has concerns
Your Name
PS: Referencing is comprehensive, mostly accurate according to APA style
conventions, and demonstrates academic integrity. Some minor errors or
omissions in style and formatting choices (e.g. italics, punctuation, etc)
don’t impact on the transparency and traceability of the source, or
demonstration of academic integrity.
FL: Sub-standard (or no) referencing. Poor quality (or no) references.
Total
Marks
Q1. What's going on?
The CIO of the company, Dave has asked the Project Director, Dawn to deliver the
Willis Project one month before the schedule that as decided in the contract. The reason for
bringing the deadline forward is because the CEO wants to use this opportunity to sign
another contract with the Willis that is worth over 3 million. Dawn talked to Greg who is
managing the Willis project, with the hope of convincing him to deliver the project one
month prior to the deadline by using shortcuts and not implementing the necessary security
measures. Don tries to persuade Greg by saying if the company is successful in entering into
another contract with Willis then he and his team will be highly rewarded for their efforts in
delivering the current project before schedule.
Q2. What are the facts?
Dave was asked to deliver the Willis project by employing several shortcuts in the
execution of the project and to deliver the system without implementing encryption. This
would enable them to deliver the project one month prior to schedule. Following the chain
of command, Don was asked by Dave to do the needful and deliver the project early. Dawn
then asked Greg to deliver the project before schedule as requested by the CIO and to
implement the security patch as an update package. Thus, the CIO of the company is
pressurizing the project team through the project director so that the client receives the
project before schedule. However, Greg stated that Jason, the senior developer believes
that the encryption of the software is necessary.
Q3. What are the issues?
To accommodate the wishes of the CEO, the CIO wants to deliver the project without
implementing any encryption to the software. Jason on the other hand, has strongly
emphasized that the software must have encryption. Senior developer Jason has concerns
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Title of you case study/scenario
about the huge amount of time that they would require in the encryption of the Willis
system. Thus, delivering the Willis system without implementing the necessary encryption is
would create problems for the company, the Willis group and the customers of the Willis
group. These are the issues with the Willis project.
Q4. Who is affected?
The project team, the CIO, the Willis group and the customer associated with the
Willis Group are all affected by the activities in this scenario (Lawrence & Weber, 2014). In
the event of a successful release of the Willis system without implementing the needed
encryption and then the system gets hacked. The confidential data of the customers of the
customers would be stolen. Thus, the entire client base of the Willis group is affected, which
in turn damages the reputation of the Willis group and the level of security that they
provide to their customers. The company delivering the project then has to face the
repercussions as they were not only responsible for delivering the system on time, they
were also responsible for providing IT security for the system.
Q5. What are the ethical issues and their implications?
The CIO wants the project team to deliver the system without implementing
encryption. He wants the team to use shortcuts in order to achieve the designated goal at
the cost of quality. This means that even a small attack on the system is sufficient to steal all
the data of the customers that are stored by the Willis group (Conklin et al., 2015).
Achieving profit for the organization does impact an employee’s career. However,
compromising the reputation of another company by jeopardizing the privacy of its clients
(Martin, Borah & Palmatier, 2017). The release of an insecure platform not only
demonstrates the ethical values of the decision maker at the project delivering company, it
also reflects the ethical values of the project team who followed the governing authority
and did not act against such unethical actions (Garegnani, Merlotti & Russo, 2015).
Q6. What could have been done about it?
Dave should have used his own analysis to convince the CEO that completing the
project one month in advance will compromise the quality of the system and in the long run
will affect the reputation of the company. The contract between two companies does not
include specific guidelines for measuring the quality at the time of product or service
delivery (Quinn, 2014). Thus, it is the responsibility of the delivering party to maintain the
standards of quality that suits the needs of the receiving client. The CIO must be capable of
Your Name
about the huge amount of time that they would require in the encryption of the Willis
system. Thus, delivering the Willis system without implementing the necessary encryption is
would create problems for the company, the Willis group and the customers of the Willis
group. These are the issues with the Willis project.
Q4. Who is affected?
The project team, the CIO, the Willis group and the customer associated with the
Willis Group are all affected by the activities in this scenario (Lawrence & Weber, 2014). In
the event of a successful release of the Willis system without implementing the needed
encryption and then the system gets hacked. The confidential data of the customers of the
customers would be stolen. Thus, the entire client base of the Willis group is affected, which
in turn damages the reputation of the Willis group and the level of security that they
provide to their customers. The company delivering the project then has to face the
repercussions as they were not only responsible for delivering the system on time, they
were also responsible for providing IT security for the system.
Q5. What are the ethical issues and their implications?
The CIO wants the project team to deliver the system without implementing
encryption. He wants the team to use shortcuts in order to achieve the designated goal at
the cost of quality. This means that even a small attack on the system is sufficient to steal all
the data of the customers that are stored by the Willis group (Conklin et al., 2015).
Achieving profit for the organization does impact an employee’s career. However,
compromising the reputation of another company by jeopardizing the privacy of its clients
(Martin, Borah & Palmatier, 2017). The release of an insecure platform not only
demonstrates the ethical values of the decision maker at the project delivering company, it
also reflects the ethical values of the project team who followed the governing authority
and did not act against such unethical actions (Garegnani, Merlotti & Russo, 2015).
Q6. What could have been done about it?
Dave should have used his own analysis to convince the CEO that completing the
project one month in advance will compromise the quality of the system and in the long run
will affect the reputation of the company. The contract between two companies does not
include specific guidelines for measuring the quality at the time of product or service
delivery (Quinn, 2014). Thus, it is the responsibility of the delivering party to maintain the
standards of quality that suits the needs of the receiving client. The CIO must be capable of
Your Name
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Title of you case study/scenario
understanding this before indicating any unethical delivery of the system that would
damage the reputation of the company and future elimination of any business prospects
with the Willis group.
Q7. What are the options?
There are three options to this scenario. The first is that the program director yields
to the pressure of the CIO and compels the project team to deliver the Willis project one
month before the scheduled time by not implementing the necessary encryption to the
system. The second option is that the program director does not approve of the
recommendations and concerns stated by project manager. Instead Dawn reports to Dave
about the insubordination of Greg and have him fired. In this option, Dave and Dawn want
to deliver the project at their own terms and would remove any one from their way to
achieve their goals. The third option is that the project director accepts the fact that
delivering a software without the proper encryption would not only harm their client the
Willis group, it would also damage the reputation of their own company. Thus, after
concluding this fact, he talks to the CIO about this particular decision that has been taken by
the team. Dawn tries to convince Dave about the repercussions that the company would
face in the event of a hack.
Q8. Which option is the best and why?
The third option where the project director, Dawn understands the problems of
delivering a software platform that is not encrypted is the best option in this scenario.
Application of proper analytical judgement by the project director would prevent the
company from delivering unsafe software (Moore, 2015). The CIO will not pay much
attention to the concerns of a project manager and thus it is the responsibility of the project
director to understand the situation and then convince the CIO to take the best possible
action that not only servers the interest of the company but is also ethical (Kian & Eastman,
2017).
References
Conklin, W. A., White, G., Cothren, C., Davis, R., & Williams, D. (2015). Principles of computer
security. McGraw-Hill Education Group.
Your Name
understanding this before indicating any unethical delivery of the system that would
damage the reputation of the company and future elimination of any business prospects
with the Willis group.
Q7. What are the options?
There are three options to this scenario. The first is that the program director yields
to the pressure of the CIO and compels the project team to deliver the Willis project one
month before the scheduled time by not implementing the necessary encryption to the
system. The second option is that the program director does not approve of the
recommendations and concerns stated by project manager. Instead Dawn reports to Dave
about the insubordination of Greg and have him fired. In this option, Dave and Dawn want
to deliver the project at their own terms and would remove any one from their way to
achieve their goals. The third option is that the project director accepts the fact that
delivering a software without the proper encryption would not only harm their client the
Willis group, it would also damage the reputation of their own company. Thus, after
concluding this fact, he talks to the CIO about this particular decision that has been taken by
the team. Dawn tries to convince Dave about the repercussions that the company would
face in the event of a hack.
Q8. Which option is the best and why?
The third option where the project director, Dawn understands the problems of
delivering a software platform that is not encrypted is the best option in this scenario.
Application of proper analytical judgement by the project director would prevent the
company from delivering unsafe software (Moore, 2015). The CIO will not pay much
attention to the concerns of a project manager and thus it is the responsibility of the project
director to understand the situation and then convince the CIO to take the best possible
action that not only servers the interest of the company but is also ethical (Kian & Eastman,
2017).
References
Conklin, W. A., White, G., Cothren, C., Davis, R., & Williams, D. (2015). Principles of computer
security. McGraw-Hill Education Group.
Your Name

Title of you case study/scenario
Garegnani, G. M., Merlotti, E. P., & Russo, A. (2015). Scoring firms’ codes of ethics: An explorative
study of quality drivers. Journal of Business Ethics, 126(4), 541-557.
Kian, L. A., & Eastman, S. D. (2017). Ethics and Information Technology. In Ethical Challenges in
Oncology (pp. 313-323).
Lawrence, A. T., & Weber, J. (2014). Business and society: Stakeholders, ethics, public policy.
Tata McGraw-Hill Education.
Martin, K. D., Borah, A., & Palmatier, R. W. (2017). Data privacy: Effects on customer and firm
performance. Journal of Marketing, 81(1), 36-58.
Moore, A. D. (2015). Privacy, Security and Accountability: Ethics, Law and Policy.
Quinn, M. J. (2014). Ethics for the information age. Boston, MA: Pearson.
Video link for Scenario 3: https://www.youtube.com/watch?v=v5M7ohdZ6qA.
Your Name
Garegnani, G. M., Merlotti, E. P., & Russo, A. (2015). Scoring firms’ codes of ethics: An explorative
study of quality drivers. Journal of Business Ethics, 126(4), 541-557.
Kian, L. A., & Eastman, S. D. (2017). Ethics and Information Technology. In Ethical Challenges in
Oncology (pp. 313-323).
Lawrence, A. T., & Weber, J. (2014). Business and society: Stakeholders, ethics, public policy.
Tata McGraw-Hill Education.
Martin, K. D., Borah, A., & Palmatier, R. W. (2017). Data privacy: Effects on customer and firm
performance. Journal of Marketing, 81(1), 36-58.
Moore, A. D. (2015). Privacy, Security and Accountability: Ethics, Law and Policy.
Quinn, M. J. (2014). Ethics for the information age. Boston, MA: Pearson.
Video link for Scenario 3: https://www.youtube.com/watch?v=v5M7ohdZ6qA.
Your Name
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 6
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





