ITC571 Project: SCADA Based Cyber-security Management in IOT
VerifiedAdded on 2023/06/11
|12
|1125
|119
Project
AI Summary
This project proposal outlines a plan for researching SCADA-based cyber-security management in the Internet of Things (IoT). It addresses the increasing security threats and vulnerabilities in IoT systems, particularly those connected to critical infrastructure. The proposal includes a research background, motivation, aims and objectives, deliverables, timelines, and methodology, focusing on using a qualitative research approach with data collected through questionnaires and analyzed using snowball sampling. The goal is to develop a SCADA-enabled security architecture that enhances standardization and security in IoT networks, ultimately boosting user confidence and market value in IoT technology. The proposal also references existing research and literature to support the proposed approach.

Project
proposal and
plan
Student Name:
Student Number:
Course Name:
University Name:
SCADA based cyber-security management in IOT
proposal and
plan
Student Name:
Student Number:
Course Name:
University Name:
SCADA based cyber-security management in IOT
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

INTRODUCTION
Internet of things is a hot topic for research and
is continuously emerging as it maps the real
world entities in virtual world. Both entities, i.e.
digital and physical can be enhanced with
sensing, self-adapting and processing
capabilities to perform automated tasks by
making interaction using special addressing
schemes. Due to the highly interoperability
within the technology, it is not possible to offer
effective and standardized security parameters.
Internet of things is a hot topic for research and
is continuously emerging as it maps the real
world entities in virtual world. Both entities, i.e.
digital and physical can be enhanced with
sensing, self-adapting and processing
capabilities to perform automated tasks by
making interaction using special addressing
schemes. Due to the highly interoperability
within the technology, it is not possible to offer
effective and standardized security parameters.
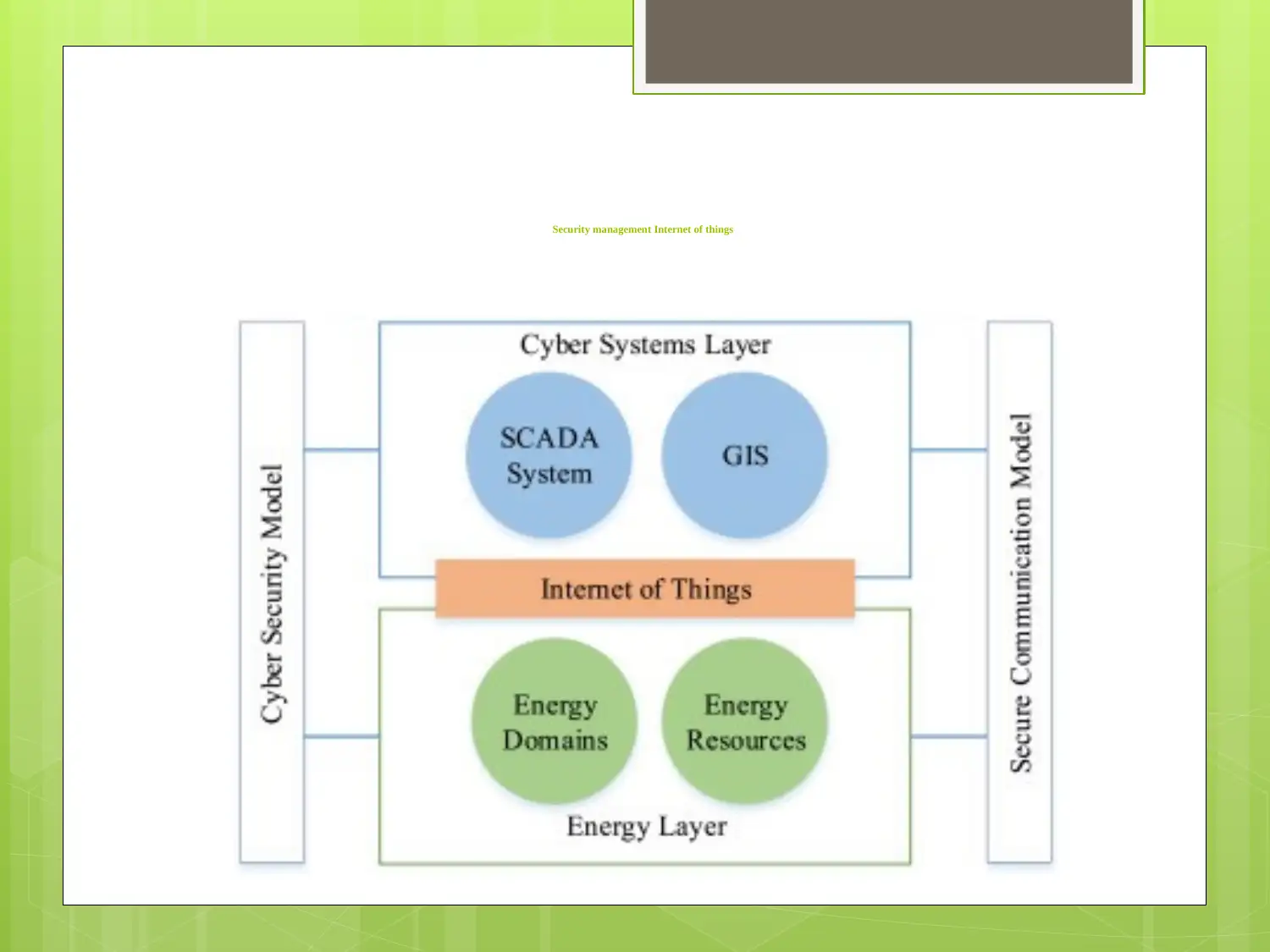
Security management Internet of things
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Need for Research
With the increasing security attacks and advancing
security threats to the IOT, user is being conscious
towards acquiring the potential services offered by
IOT technology and it is also damaging the market
value of the technology which raises the need for
researching a system architecture with strong
security parameters to boost the market value and
confidence of users in IOT as well
With the increasing security attacks and advancing
security threats to the IOT, user is being conscious
towards acquiring the potential services offered by
IOT technology and it is also damaging the market
value of the technology which raises the need for
researching a system architecture with strong
security parameters to boost the market value and
confidence of users in IOT as well
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Motivation for Research
Significant obstacles such as security
vulnerability and cyber attacks over Internet
of things can influence the development of
technology in insecure manner and can make
the technology vulnerable. Fake user profiling
is the major issue reported in IOT technology
which limits the use of IOT technology within
users as Sensors and other devices acquires
data in large amount and attackers can gain
access to their routine data and can make
fake profiles for business profits. Black market
is another issue which purchases the stolen
information for enhancing their business value
and processes.
Significant obstacles such as security
vulnerability and cyber attacks over Internet
of things can influence the development of
technology in insecure manner and can make
the technology vulnerable. Fake user profiling
is the major issue reported in IOT technology
which limits the use of IOT technology within
users as Sensors and other devices acquires
data in large amount and attackers can gain
access to their routine data and can make
fake profiles for business profits. Black market
is another issue which purchases the stolen
information for enhancing their business value
and processes.

Research signifiance
The car owner gets ‘paid’ by other users, so they incur
minimal or no expenses in fuel and maintenance. The
other commuters save themselves the fuel cost to get
them to work. The most important benefit will be the
ability to reach their workplaces on time because the
system will remove almost a third (as a minimum) of the
personal vehicular traffic from the roads. The other
benefit will be a general reduction in the overall fossil
fuel use and consequently, a significant reduction in the
amount of pollution generated as a result of a significant
number of cars being removed from the roads, especially
at peak hours when people are rushing to work
The car owner gets ‘paid’ by other users, so they incur
minimal or no expenses in fuel and maintenance. The
other commuters save themselves the fuel cost to get
them to work. The most important benefit will be the
ability to reach their workplaces on time because the
system will remove almost a third (as a minimum) of the
personal vehicular traffic from the roads. The other
benefit will be a general reduction in the overall fossil
fuel use and consequently, a significant reduction in the
amount of pollution generated as a result of a significant
number of cars being removed from the roads, especially
at peak hours when people are rushing to work
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Aim and objectives
This research paper aims to offer SCADA
based security parameters which will offer a
standardized security mechanism to tackle
the cyber attacks over the IOT nodes by
offering flexible yet standardized interaction
between several nodes with the objective
making interaction between IOT enabled
nods even flexible and secure to enhance the
business value of IOT technology and
encourage further research on Internet of
Things [6].
This research paper aims to offer SCADA
based security parameters which will offer a
standardized security mechanism to tackle
the cyber attacks over the IOT nodes by
offering flexible yet standardized interaction
between several nodes with the objective
making interaction between IOT enabled
nods even flexible and secure to enhance the
business value of IOT technology and
encourage further research on Internet of
Things [6].
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Research deliverables
Following are the deliverables of the research:
This research is expected to deliver SCADA
enabled security architecture which will
enforce standardization within the
networking and computing for flexible
computing and communication capabilities
in a secure manner [4].
This research aims to deliver the several
cyber-security issues being faced by IOT by
using Security attacks tree model to
represent effective information about
different security attacks.
Following are the deliverables of the research:
This research is expected to deliver SCADA
enabled security architecture which will
enforce standardization within the
networking and computing for flexible
computing and communication capabilities
in a secure manner [4].
This research aims to deliver the several
cyber-security issues being faced by IOT by
using Security attacks tree model to
represent effective information about
different security attacks.

Research Timelines
Acquiring background information: existing research and information on
Internet of things and challenges acquired it will be acquired first.
Literature survey: several conference, research and journal papers will be
reviewed to acquire the sufficient data for conducting research.
Defining limitations: limitations will be defined before initializing the
actual research for defining the alternatives to the acquired limitations.
Formulating research questions: a common domain will be specified to
perform the research efficiently in a specific domain only.
Research Conceptual model: methodology along with the several steps
required to perform the research effectively should be mapped in a
graphical representation.
Acquiring background information: existing research and information on
Internet of things and challenges acquired it will be acquired first.
Literature survey: several conference, research and journal papers will be
reviewed to acquire the sufficient data for conducting research.
Defining limitations: limitations will be defined before initializing the
actual research for defining the alternatives to the acquired limitations.
Formulating research questions: a common domain will be specified to
perform the research efficiently in a specific domain only.
Research Conceptual model: methodology along with the several steps
required to perform the research effectively should be mapped in a
graphical representation.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Research timeliness
Research methodology: depending upon the descriptive nature of the
technology, research will be performed using qualitative research
methodology.
Collecting data using questionnaire: for the effective collection of data for
supposed end users, questionnaires will be distributed amongst them.
Sampling data using convenience sampling: collected data will be sampled
depending upon the several categorization of the data including age,
requirements, domain, expectations etc.
Analyzing sampled data: Sampled data will be analyzed using snowball
sampling technique for relevant sampling.
Collecting results: results will be measured and collected using effective
methods to eliminate the inconsistencies within collected data.
Evaluating results: results will be evaluated for its correctness and
effectiveness.
Research Closure: after acquiring the expected results, research paper will
be documented and research will be terminated.
Research methodology: depending upon the descriptive nature of the
technology, research will be performed using qualitative research
methodology.
Collecting data using questionnaire: for the effective collection of data for
supposed end users, questionnaires will be distributed amongst them.
Sampling data using convenience sampling: collected data will be sampled
depending upon the several categorization of the data including age,
requirements, domain, expectations etc.
Analyzing sampled data: Sampled data will be analyzed using snowball
sampling technique for relevant sampling.
Collecting results: results will be measured and collected using effective
methods to eliminate the inconsistencies within collected data.
Evaluating results: results will be evaluated for its correctness and
effectiveness.
Research Closure: after acquiring the expected results, research paper will
be documented and research will be terminated.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

References
[1]H. Ning and H. Liu, "Cyber-Physical-Social Based Security Architecture for
Future Internet of Things", Advances in Internet of Things, vol. 02, no. 01, pp. 1-
7, 2012.
[2]A. Sajid, H. Abbas and K. Saleem, "Cloud-Assisted IoT-Based SCADA Systems
Security: A Review of the State of the Art and Future Challenges", IEEE Access,
vol. 4, pp. 1375-1384, 2016.
[3]J. Pacheco and S. Hariri, "IoT Security Framework for Smart Cyber
Infrastructures", 2016 IEEE 1st International Workshops on Foundations and
Applications of Self* Systems (FAS*W), 2016.
[4]H. Suo, J. Wan, C. Zou and J. Liu, "Security in the Internet of Things: A
Review", 2012 International Conference on Computer Science and Electronics
Engineering, 2012.
[5]A. Sadeghi, C. Wachsmann and M. Waidner, "Security and privacy challenges
in industrial internet of things", Proceedings of the 52nd Annual Design
Automation Conference on - DAC '15, 2015.
[6]M. Chiang and T. Zhang, "Fog and IoT: An Overview of Research
Opportunities", IEEE Internet of Things Journal, vol. 3, no. 6, pp. 854-864, 2016.
[7]R. Mahmoud, T. Yousuf, F. Aloul and I. Zualkernan, "Internet of things (IoT)
security: Current status, challenges and prospective measures", 2015 10th
International Conference for Internet Technology and Secured Transactions
(ICITST), 2015.
[8]C. Bekara, "Security Issues and Challenges for the IoT-based Smart
[1]H. Ning and H. Liu, "Cyber-Physical-Social Based Security Architecture for
Future Internet of Things", Advances in Internet of Things, vol. 02, no. 01, pp. 1-
7, 2012.
[2]A. Sajid, H. Abbas and K. Saleem, "Cloud-Assisted IoT-Based SCADA Systems
Security: A Review of the State of the Art and Future Challenges", IEEE Access,
vol. 4, pp. 1375-1384, 2016.
[3]J. Pacheco and S. Hariri, "IoT Security Framework for Smart Cyber
Infrastructures", 2016 IEEE 1st International Workshops on Foundations and
Applications of Self* Systems (FAS*W), 2016.
[4]H. Suo, J. Wan, C. Zou and J. Liu, "Security in the Internet of Things: A
Review", 2012 International Conference on Computer Science and Electronics
Engineering, 2012.
[5]A. Sadeghi, C. Wachsmann and M. Waidner, "Security and privacy challenges
in industrial internet of things", Proceedings of the 52nd Annual Design
Automation Conference on - DAC '15, 2015.
[6]M. Chiang and T. Zhang, "Fog and IoT: An Overview of Research
Opportunities", IEEE Internet of Things Journal, vol. 3, no. 6, pp. 854-864, 2016.
[7]R. Mahmoud, T. Yousuf, F. Aloul and I. Zualkernan, "Internet of things (IoT)
security: Current status, challenges and prospective measures", 2015 10th
International Conference for Internet Technology and Secured Transactions
(ICITST), 2015.
[8]C. Bekara, "Security Issues and Challenges for the IoT-based Smart

⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





