ITC596: Risk Assessment of Cloud Security Project - Gigantic Corp
VerifiedAdded on 2023/06/04
|17
|3863
|237
Report
AI Summary
This report provides a comprehensive risk assessment of a cloud security project, specifically a DDoS detection and prevention system, for Gigantic Corporation. It identifies various threats and vulnerabilities, including unauthenticated data utilization, compromised APIs, reduced data visibility, credential theft, insider threats, and data deletion. The assessment categorizes these risks by level and outlines their consequences based on an IT control framework. The report recommends utilizing virtual private networks and parallel networking to enhance cloud security. Mitigation techniques, such as deploying antivirus software with regular updates and implementing firewalls, are discussed to address identified risks. The document concludes by emphasizing the importance of these measures for safeguarding sensitive information and maintaining the integrity of the cloud environment. Desklib offers a variety of resources for students, including similar past papers and solved assignments.

Running head: IT RISK MANAGEMENT
IT Risk Management: Cloud Security
Name of the Student
Name of the University
Author’s Note:
IT Risk Management: Cloud Security
Name of the Student
Name of the University
Author’s Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1
IT RISK MANAGEMENT
Table of Contents
Executive Summary...................................................................................................................2
Cloud Security........................................................................................................................2
DDoS Detection and Prevention System...............................................................................3
Attacks in Cloud Computing..................................................................................................3
Introduction................................................................................................................................4
Risk Assessment.........................................................................................................................4
Various Threats and Vulnerabilities for the Cloud Security in Gigantic Corporation...........4
Risk Assessment on the Identified Risks for the Cloud Security...........................................6
Consequences of the Identified Risks derived from IT Control Framework.........................6
Recommendations for this Project.........................................................................................7
Mitigation of Risks and Major Impact on the System...........................................................8
Literature Review.......................................................................................................................9
Protection Mechanisms Required for Information Security in this Project...........................9
Conclusion................................................................................................................................12
References................................................................................................................................14
IT RISK MANAGEMENT
Table of Contents
Executive Summary...................................................................................................................2
Cloud Security........................................................................................................................2
DDoS Detection and Prevention System...............................................................................3
Attacks in Cloud Computing..................................................................................................3
Introduction................................................................................................................................4
Risk Assessment.........................................................................................................................4
Various Threats and Vulnerabilities for the Cloud Security in Gigantic Corporation...........4
Risk Assessment on the Identified Risks for the Cloud Security...........................................6
Consequences of the Identified Risks derived from IT Control Framework.........................6
Recommendations for this Project.........................................................................................7
Mitigation of Risks and Major Impact on the System...........................................................8
Literature Review.......................................................................................................................9
Protection Mechanisms Required for Information Security in this Project...........................9
Conclusion................................................................................................................................12
References................................................................................................................................14

2
IT RISK MANAGEMENT
Executive Summary
The main objective of the report is to do a risk assessment on the case of an enterprise,
known as Gigantic Corporation. The enterprise is executing a significant project on the cloud
security, called the DDoS detection and prevention system. The management of this
company has eventually recruited their risk assessment lead consultant for information
technology and information systems. The most significant responsibility of this particular risk
consultant is that he will have to provide the basic interface within the business related
stakeholders like owners and customers and even the respective technologists and even for
the major task to translate the various potential technology oriented difficulties or issues to
the risk language for this major reason of facilitation of the efficient as well as effective
process of decision making by each and every stakeholder.
Cloud Security
Cloud security refers to the significant collection of controls, technologies and policies that
are to be deployed for the proper protection of data, related infrastructure and the applications
of the specific technology of cloud computing. This cloud security is the sub domain of
network security, information security and data security. Several important and significant
issues related to security are eventually present that are closely linked to the storage providers
and cloud computing. This technology of cloud computing is considered as the fastest and the
most effective service that is helpful for the purpose of providing few of the significant
functionalities that are same as this traditional security of information technology. The
various important and noteworthy functionalities of cloud computing subsequently involve
the proper protection of any critical and sensitive information from all types of data theft,
data leakage as well as data deletion. Safety and security are the two important benefits of
this cloud security.
IT RISK MANAGEMENT
Executive Summary
The main objective of the report is to do a risk assessment on the case of an enterprise,
known as Gigantic Corporation. The enterprise is executing a significant project on the cloud
security, called the DDoS detection and prevention system. The management of this
company has eventually recruited their risk assessment lead consultant for information
technology and information systems. The most significant responsibility of this particular risk
consultant is that he will have to provide the basic interface within the business related
stakeholders like owners and customers and even the respective technologists and even for
the major task to translate the various potential technology oriented difficulties or issues to
the risk language for this major reason of facilitation of the efficient as well as effective
process of decision making by each and every stakeholder.
Cloud Security
Cloud security refers to the significant collection of controls, technologies and policies that
are to be deployed for the proper protection of data, related infrastructure and the applications
of the specific technology of cloud computing. This cloud security is the sub domain of
network security, information security and data security. Several important and significant
issues related to security are eventually present that are closely linked to the storage providers
and cloud computing. This technology of cloud computing is considered as the fastest and the
most effective service that is helpful for the purpose of providing few of the significant
functionalities that are same as this traditional security of information technology. The
various important and noteworthy functionalities of cloud computing subsequently involve
the proper protection of any critical and sensitive information from all types of data theft,
data leakage as well as data deletion. Safety and security are the two important benefits of
this cloud security.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
IT RISK MANAGEMENT
DDoS Detection and Prevention System
The organization has hired their risk assessment leading consultant regarding the information
technology to properly identify as well as prevent the most significant risks related to
information technology in the subsequent project of making the system of detection and
prevention of distributed denial of service attacks. The specific system is the basic collection
of techniques as well as tools, which are helpful for resisting and preventing the total impact
of the several attacks on the cloud and cloud services, which are attached with the
connectivity of Internet either by protecting their target or by simply securing the networks.
The respective normal conditions could be recognized for each and every type of network
traffic after perfectly defining the several patterns of the network traffic. The specified system
of this distributed denial of service detection or prevention also requires the major
identification or recognition of the incoming and outgoing network traffic to separate this
traffic from bots and also from the hacked web browsers. There is a major process that is to
be completed either by the signature comparison and the examination of the network traffic
attributes such as IP addresses, cookie variations, HTTP headers and even Javascript
footprints.
Attacks in Cloud Computing
The DDoS attack is the most vulnerable attack in cloud computing and for the cloud security.
The particular company of Gigantic Corporation selected the project of distributed denial of
service attack detection as well as prevention system within the core area of this cloud
security. Some other important and popular types of risks and threats within cloud computing
are the blocking of the respective IP addresses of any authenticated user and the lack of
proper synchronization of the SYN packets that are sent to their targeted system. The report
has assessed the risks and various mitigation and the various protection mechanisms are also
provided here.
IT RISK MANAGEMENT
DDoS Detection and Prevention System
The organization has hired their risk assessment leading consultant regarding the information
technology to properly identify as well as prevent the most significant risks related to
information technology in the subsequent project of making the system of detection and
prevention of distributed denial of service attacks. The specific system is the basic collection
of techniques as well as tools, which are helpful for resisting and preventing the total impact
of the several attacks on the cloud and cloud services, which are attached with the
connectivity of Internet either by protecting their target or by simply securing the networks.
The respective normal conditions could be recognized for each and every type of network
traffic after perfectly defining the several patterns of the network traffic. The specified system
of this distributed denial of service detection or prevention also requires the major
identification or recognition of the incoming and outgoing network traffic to separate this
traffic from bots and also from the hacked web browsers. There is a major process that is to
be completed either by the signature comparison and the examination of the network traffic
attributes such as IP addresses, cookie variations, HTTP headers and even Javascript
footprints.
Attacks in Cloud Computing
The DDoS attack is the most vulnerable attack in cloud computing and for the cloud security.
The particular company of Gigantic Corporation selected the project of distributed denial of
service attack detection as well as prevention system within the core area of this cloud
security. Some other important and popular types of risks and threats within cloud computing
are the blocking of the respective IP addresses of any authenticated user and the lack of
proper synchronization of the SYN packets that are sent to their targeted system. The report
has assessed the risks and various mitigation and the various protection mechanisms are also
provided here.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4
IT RISK MANAGEMENT
Introduction
The cloud security could be defined as the significant security as well as protection of
any specific type of sensitive or confidential information, which is being stored online (Rong,
Nguyen & Jaatun, 2013). Some of the most significant and important risks and threats are
present for this specific type of cloud security, which majorly includes the loss of data,
intercepting the network traffics, insecure application program interfaces or APIs, sensitive
data or information breaching, lack of options for the several providers of the cloud storages,
shared technology and many more. The company of Gigantic Corporation has subsequently
taken the core decision of execution a distinct project of the distributed denial of service
detection and prevention system within the cloud security (Almorsy, Grundy & Müller,
2016). This report will be describing a detailed discussion about this particular organization
as well as the project they have decided to execute. A proper assessment of risks is being
completed for each and every identified risk as well as the respective consequences of these
risks as per a respective control framework of information technology. Moreover, some
protection mechanisms will be provided here.
Risk Assessment
Various Threats and Vulnerabilities for the Cloud Security in Gigantic Corporation
The respective cloud computing technology is one of the most important and a
noteworthy technology that is responsible for safe and secured data transfer. However, in
spite of having of such important advantages and benefits, few of the threats, vulnerabilities
and threats are subsequently present for this particular technology that are quite dangerous
and risky for the company of Gigantic Corporation (Aljawarneh, 2013). Amongst them, the
major risks are provided below:
IT RISK MANAGEMENT
Introduction
The cloud security could be defined as the significant security as well as protection of
any specific type of sensitive or confidential information, which is being stored online (Rong,
Nguyen & Jaatun, 2013). Some of the most significant and important risks and threats are
present for this specific type of cloud security, which majorly includes the loss of data,
intercepting the network traffics, insecure application program interfaces or APIs, sensitive
data or information breaching, lack of options for the several providers of the cloud storages,
shared technology and many more. The company of Gigantic Corporation has subsequently
taken the core decision of execution a distinct project of the distributed denial of service
detection and prevention system within the cloud security (Almorsy, Grundy & Müller,
2016). This report will be describing a detailed discussion about this particular organization
as well as the project they have decided to execute. A proper assessment of risks is being
completed for each and every identified risk as well as the respective consequences of these
risks as per a respective control framework of information technology. Moreover, some
protection mechanisms will be provided here.
Risk Assessment
Various Threats and Vulnerabilities for the Cloud Security in Gigantic Corporation
The respective cloud computing technology is one of the most important and a
noteworthy technology that is responsible for safe and secured data transfer. However, in
spite of having of such important advantages and benefits, few of the threats, vulnerabilities
and threats are subsequently present for this particular technology that are quite dangerous
and risky for the company of Gigantic Corporation (Aljawarneh, 2013). Amongst them, the
major risks are provided below:

5
IT RISK MANAGEMENT
i) Unauthenticated Utilization of Data: The most significant threat for the cloud
security within the company of Gigantic Corporation is the unauthorized and unauthenticated
utilization of sensitive information and data (Krasnyanskaya & Tylets, 2015). The newer
services can be promptly provisioned and thus all the aspects of the on demand self servicing
that would be help the staffs of this organization for the purpose of enabling the various
services without even taking consent of IT experts.
ii) Compromise in the Internet Accessible Management APIs: Another important
and significant risk for the cloud security for the company of Gigantic Corporation is the
respective compromise within the accessible or manageable APIs. A collection of the
application programming interface can easily manage or interact with various cloud services
and hence few issues are being faced here (Chou, 2013).
iii) Reduction in the Visibility and Control of Data: This is the next popular and
noteworthy risk within cloud security in the company of Gigantic Corporation. The hacker
often reduces the major visibility as well as control of the confidential or sensitive data. This
type of issue could even bring out the casualties in the data.
iv) Stealing of the Credentials: The various credentials are often stolen by this threat
in cloud security and hence this particular risk is to be mitigated eventually within the
company of Gigantic Corporation (Zhao, Li & Liu, 2014).
v) Insiders Threats: The staffs or the employees of the company of Gigantic
Corporation could also bring out major vulnerabilities either intentionally or unintentionally.
vi) Deletion of Data: When the sensitive data is being deleted within the company of
Gigantic Corporation, the sensitive data is lost subsequently (Mishra et al., 2013). This
IT RISK MANAGEMENT
i) Unauthenticated Utilization of Data: The most significant threat for the cloud
security within the company of Gigantic Corporation is the unauthorized and unauthenticated
utilization of sensitive information and data (Krasnyanskaya & Tylets, 2015). The newer
services can be promptly provisioned and thus all the aspects of the on demand self servicing
that would be help the staffs of this organization for the purpose of enabling the various
services without even taking consent of IT experts.
ii) Compromise in the Internet Accessible Management APIs: Another important
and significant risk for the cloud security for the company of Gigantic Corporation is the
respective compromise within the accessible or manageable APIs. A collection of the
application programming interface can easily manage or interact with various cloud services
and hence few issues are being faced here (Chou, 2013).
iii) Reduction in the Visibility and Control of Data: This is the next popular and
noteworthy risk within cloud security in the company of Gigantic Corporation. The hacker
often reduces the major visibility as well as control of the confidential or sensitive data. This
type of issue could even bring out the casualties in the data.
iv) Stealing of the Credentials: The various credentials are often stolen by this threat
in cloud security and hence this particular risk is to be mitigated eventually within the
company of Gigantic Corporation (Zhao, Li & Liu, 2014).
v) Insiders Threats: The staffs or the employees of the company of Gigantic
Corporation could also bring out major vulnerabilities either intentionally or unintentionally.
vi) Deletion of Data: When the sensitive data is being deleted within the company of
Gigantic Corporation, the sensitive data is lost subsequently (Mishra et al., 2013). This
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6
IT RISK MANAGEMENT
particular risk can also cause some of the basic infrastructure issues for the organization and
hence an important significance is required here.
Risk Assessment on the Identified Risks for the Cloud Security
The risk assessment of all the identified risks for this cloud security is provided below
(Salah et al., 2013):
Serial Number Identified Risks Level of Risk
1. Unauthenticated Utilization of Data High
2. Compromise in the Internet Accessible
Management APIs
Low
3. Reduction in the Visibility and Control
of Data
Moderate
4. Stealing of Credentials High
5. Insiders’ Threat Low
6. Deletion of Data Moderate
Consequences of the Identified Risks derived from IT Control Framework
This IT control framework has the ability of organizing and categorizing the
organizational internal controls within the organization to create business values and
reduction of risks (Sachdev & Bhansali, 2013). Several policies and procedures are present
here. The consequences of identified risks, which are derived according to the IT control
framework, are provided below:
Serial Number Identified Risks Consequences of Risks
1. Unauthenticated Utilization of Data Major
2. Compromise in the Internet Accessible Major
IT RISK MANAGEMENT
particular risk can also cause some of the basic infrastructure issues for the organization and
hence an important significance is required here.
Risk Assessment on the Identified Risks for the Cloud Security
The risk assessment of all the identified risks for this cloud security is provided below
(Salah et al., 2013):
Serial Number Identified Risks Level of Risk
1. Unauthenticated Utilization of Data High
2. Compromise in the Internet Accessible
Management APIs
Low
3. Reduction in the Visibility and Control
of Data
Moderate
4. Stealing of Credentials High
5. Insiders’ Threat Low
6. Deletion of Data Moderate
Consequences of the Identified Risks derived from IT Control Framework
This IT control framework has the ability of organizing and categorizing the
organizational internal controls within the organization to create business values and
reduction of risks (Sachdev & Bhansali, 2013). Several policies and procedures are present
here. The consequences of identified risks, which are derived according to the IT control
framework, are provided below:
Serial Number Identified Risks Consequences of Risks
1. Unauthenticated Utilization of Data Major
2. Compromise in the Internet Accessible Major
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7
IT RISK MANAGEMENT
Management APIs
3. Reduction in the Visibility and Control
of Data
Moderate
4. Stealing of Credentials Major
5. Insiders’ Threat Minor
6. Deletion of Data Moderate
Recommendations for this Project
The project of distributed denial of service detection and prevention system is
considered as one of the major and a basic project that would be much effective and efficient
for the organization of Gigantic Corporation (Tari, 2014). However, with the help of some
recommendations, the cloud security would be eventually benefitted and secured. The two
suitable recommendations for the cloud security in this company are provided below:
i) Utilizing Virtual Private Networks: The most important recommendation for
Gigantic Corporation is to use the VPN or virtual private network within their information
systems (Tirthani & Ganesan, 2014). It is the private network, which eventually enables all
the users to send as well as receive the confidential data within the public and shared
networks.
ii) Utilizing Parallel Networking: Another significant suggestion for the cloud
security in this company is using parallel networking (Kalaiprasath, Elankavi & Udayakumar,
2017). This particular network has ability of easily detecting the significant problem of the
attacks of distributed denial of service and hence the issues could be eventually mitigated
without many complexities.
IT RISK MANAGEMENT
Management APIs
3. Reduction in the Visibility and Control
of Data
Moderate
4. Stealing of Credentials Major
5. Insiders’ Threat Minor
6. Deletion of Data Moderate
Recommendations for this Project
The project of distributed denial of service detection and prevention system is
considered as one of the major and a basic project that would be much effective and efficient
for the organization of Gigantic Corporation (Tari, 2014). However, with the help of some
recommendations, the cloud security would be eventually benefitted and secured. The two
suitable recommendations for the cloud security in this company are provided below:
i) Utilizing Virtual Private Networks: The most important recommendation for
Gigantic Corporation is to use the VPN or virtual private network within their information
systems (Tirthani & Ganesan, 2014). It is the private network, which eventually enables all
the users to send as well as receive the confidential data within the public and shared
networks.
ii) Utilizing Parallel Networking: Another significant suggestion for the cloud
security in this company is using parallel networking (Kalaiprasath, Elankavi & Udayakumar,
2017). This particular network has ability of easily detecting the significant problem of the
attacks of distributed denial of service and hence the issues could be eventually mitigated
without many complexities.
8
IT RISK MANAGEMENT
Mitigation of Risks and Major Impact on the System
Two significant techniques for mitigation for all the identified risks and threats within
the cloud devices are provided below:
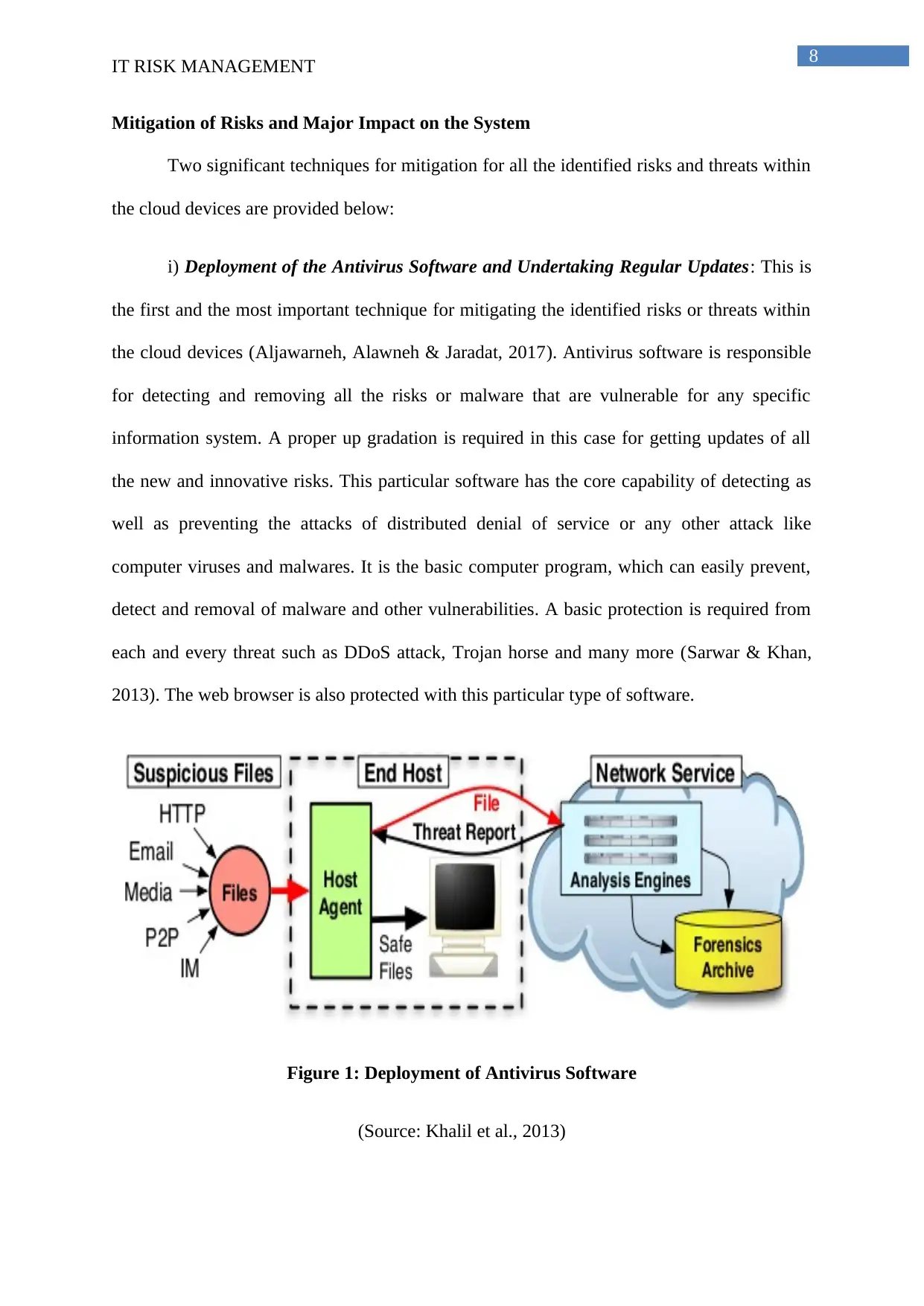
i) Deployment of the Antivirus Software and Undertaking Regular Updates: This is
the first and the most important technique for mitigating the identified risks or threats within
the cloud devices (Aljawarneh, Alawneh & Jaradat, 2017). Antivirus software is responsible
for detecting and removing all the risks or malware that are vulnerable for any specific
information system. A proper up gradation is required in this case for getting updates of all
the new and innovative risks. This particular software has the core capability of detecting as
well as preventing the attacks of distributed denial of service or any other attack like
computer viruses and malwares. It is the basic computer program, which can easily prevent,
detect and removal of malware and other vulnerabilities. A basic protection is required from
each and every threat such as DDoS attack, Trojan horse and many more (Sarwar & Khan,
2013). The web browser is also protected with this particular type of software.
Figure 1: Deployment of Antivirus Software
(Source: Khalil et al., 2013)
IT RISK MANAGEMENT
Mitigation of Risks and Major Impact on the System
Two significant techniques for mitigation for all the identified risks and threats within
the cloud devices are provided below:
i) Deployment of the Antivirus Software and Undertaking Regular Updates: This is
the first and the most important technique for mitigating the identified risks or threats within
the cloud devices (Aljawarneh, Alawneh & Jaradat, 2017). Antivirus software is responsible
for detecting and removing all the risks or malware that are vulnerable for any specific
information system. A proper up gradation is required in this case for getting updates of all
the new and innovative risks. This particular software has the core capability of detecting as
well as preventing the attacks of distributed denial of service or any other attack like
computer viruses and malwares. It is the basic computer program, which can easily prevent,
detect and removal of malware and other vulnerabilities. A basic protection is required from
each and every threat such as DDoS attack, Trojan horse and many more (Sarwar & Khan,
2013). The web browser is also protected with this particular type of software.
Figure 1: Deployment of Antivirus Software
(Source: Khalil et al., 2013)
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9
IT RISK MANAGEMENT
ii) Deployment of Firewall: The next significant technique to properly mitigate the
several threats in the cloud computing will be major deployment of the firewalls (Popa et al.,
2013). Since, this firewall is responsible for the proper detection as well as prevention of
several threats and risks; it could be easily utilized by the organization of Gigantic
Corporation. The incoming or the outgoing network traffics are easily monitored and
controlled after taking into consideration all the security regulations of IT control framework.
This deployment of firewalls will also be helpful in the establishment of the barrier within the
untrusted external network and the trusted internal network (Khan & Tuteja, 2015). Firewalls
should be implemented by this particular organization to reduce the various identified risks
and threats with perfection.
Figure 2: Deployment of Firewalls
(Source: Donald, Oli & Arockiam, 2013)
Literature Review
Protection Mechanisms Required for Information Security in this Project
As per Jouini and Rabai (2016), the protection of the various systems and devices
from each and every type of risks like data leakage, data theft and data deletion is possible by
IT RISK MANAGEMENT
ii) Deployment of Firewall: The next significant technique to properly mitigate the
several threats in the cloud computing will be major deployment of the firewalls (Popa et al.,
2013). Since, this firewall is responsible for the proper detection as well as prevention of
several threats and risks; it could be easily utilized by the organization of Gigantic
Corporation. The incoming or the outgoing network traffics are easily monitored and
controlled after taking into consideration all the security regulations of IT control framework.
This deployment of firewalls will also be helpful in the establishment of the barrier within the
untrusted external network and the trusted internal network (Khan & Tuteja, 2015). Firewalls
should be implemented by this particular organization to reduce the various identified risks
and threats with perfection.
Figure 2: Deployment of Firewalls
(Source: Donald, Oli & Arockiam, 2013)
Literature Review
Protection Mechanisms Required for Information Security in this Project
As per Jouini and Rabai (2016), the protection of the various systems and devices
from each and every type of risks like data leakage, data theft and data deletion is possible by
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10
IT RISK MANAGEMENT
the incorporation of the several important and vital protection mechanisms. There are various
methodologies or techniques present that help to provide security and privacy within the
cloud like the tokenization, obfuscation, proper implementation of virtual private networks or
VPNs, significant implementation of firewalls as well as antivirus software, penetration
testing, basic avoidance of the use of the public connection of the Internet and many more.
According to Gordon et al. (2015), this cloud security can be termed as one of the vital or
important securities for every user, who is subsequently worried about the safety of their data
that are stored in those cloud services. It has been seen that this type of data is completely
safe and secured over the localized servicers and hence comprise of the explicit and major
control over the confidential data and information. However, this data that is being stored in
the cloud may be much more secured or safe as the providers of cloud service comprise of the
better security measure. There are some other threats also present for these cloud devices
such as social engineering attacks or the malware (Tari, 2014). DDoS detection and
prevention system project of Gigantic Corporation is responsible for mitigating all the
identified risks within the cloud services. The major protection mechanisms for the proper
reduction of each and every such issue in the cloud services and also to maintain the security
of the information are provided below:
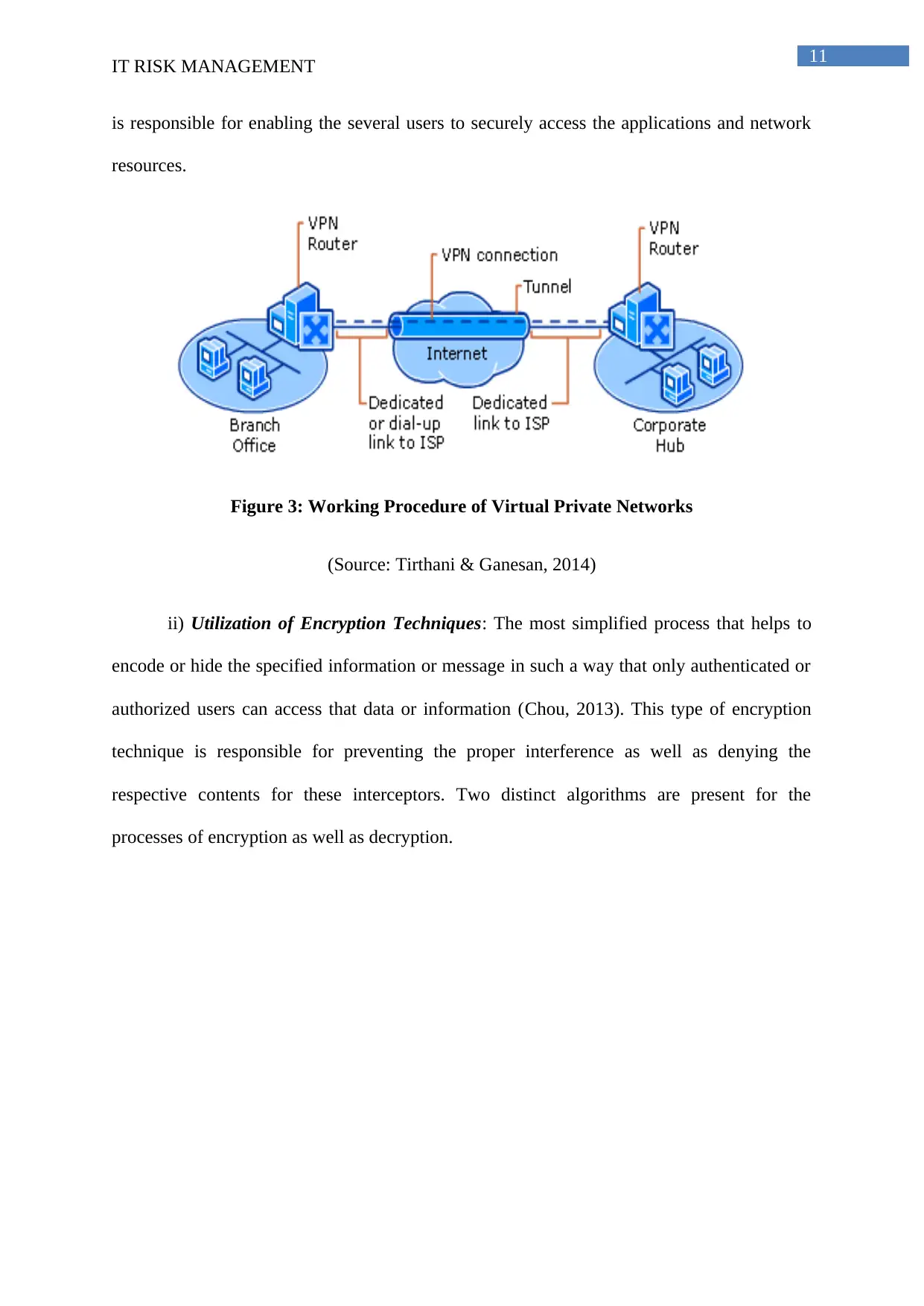
i) Deployment of the Virtual Private Networks: Salah et al. (2013) state that, the most
significant and important protection mechanism or methodology for the cloud security would
be significant implementation or deployment of several VPNs or virtual private network. This
specific virtual private network can be stated as the significant extension of the private
networks in a public network to enable their users for either sending or for receiving the
sensitive information in the shared or the public networks as the various computing devices
could be directly connected to the respective private networks. Hence, virtual private network
IT RISK MANAGEMENT
the incorporation of the several important and vital protection mechanisms. There are various
methodologies or techniques present that help to provide security and privacy within the
cloud like the tokenization, obfuscation, proper implementation of virtual private networks or
VPNs, significant implementation of firewalls as well as antivirus software, penetration
testing, basic avoidance of the use of the public connection of the Internet and many more.
According to Gordon et al. (2015), this cloud security can be termed as one of the vital or
important securities for every user, who is subsequently worried about the safety of their data
that are stored in those cloud services. It has been seen that this type of data is completely
safe and secured over the localized servicers and hence comprise of the explicit and major
control over the confidential data and information. However, this data that is being stored in
the cloud may be much more secured or safe as the providers of cloud service comprise of the
better security measure. There are some other threats also present for these cloud devices
such as social engineering attacks or the malware (Tari, 2014). DDoS detection and
prevention system project of Gigantic Corporation is responsible for mitigating all the
identified risks within the cloud services. The major protection mechanisms for the proper
reduction of each and every such issue in the cloud services and also to maintain the security
of the information are provided below:
i) Deployment of the Virtual Private Networks: Salah et al. (2013) state that, the most
significant and important protection mechanism or methodology for the cloud security would
be significant implementation or deployment of several VPNs or virtual private network. This
specific virtual private network can be stated as the significant extension of the private
networks in a public network to enable their users for either sending or for receiving the
sensitive information in the shared or the public networks as the various computing devices
could be directly connected to the respective private networks. Hence, virtual private network
11
IT RISK MANAGEMENT
is responsible for enabling the several users to securely access the applications and network
resources.
Figure 3: Working Procedure of Virtual Private Networks
(Source: Tirthani & Ganesan, 2014)
ii) Utilization of Encryption Techniques: The most simplified process that helps to
encode or hide the specified information or message in such a way that only authenticated or
authorized users can access that data or information (Chou, 2013). This type of encryption
technique is responsible for preventing the proper interference as well as denying the
respective contents for these interceptors. Two distinct algorithms are present for the
processes of encryption as well as decryption.
IT RISK MANAGEMENT
is responsible for enabling the several users to securely access the applications and network
resources.
Figure 3: Working Procedure of Virtual Private Networks
(Source: Tirthani & Ganesan, 2014)
ii) Utilization of Encryption Techniques: The most simplified process that helps to
encode or hide the specified information or message in such a way that only authenticated or
authorized users can access that data or information (Chou, 2013). This type of encryption
technique is responsible for preventing the proper interference as well as denying the
respective contents for these interceptors. Two distinct algorithms are present for the
processes of encryption as well as decryption.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




