ITC-596 IT Risk Management: IoT Vulnerability & Threat Assessment
VerifiedAdded on 2024/07/01
|20
|6776
|405
Report
AI Summary
This report, prepared for Gigantic Corporation, details an IT risk assessment focused on Internet of Things (IoT) applications. It identifies vulnerabilities and threats through methods like interviews and Delphi techniques, using tools such as probability and impact matrices for risk prioritization. The report classifies risks as high, medium, and low, emphasizing mitigation strategies for high and medium risks to prevent data theft and breaches. Recommendations include using the latest firewall and malware protection, periodic software upgrades, developing standard internet usage guidelines, and implementing strict password policies. The report also highlights the importance of data backups, employee training, regular audits, and monitoring systems. By implementing these measures, Gigantic Corporation can enhance its IT infrastructure security, build stakeholder trust, and ensure the effective and safe use of IoT in its operations.

Assessment Item: 3
SUBJECT: ITC-596 IT RISK MANAGEMENT –
INTERNET OF THINGS
1
SUBJECT: ITC-596 IT RISK MANAGEMENT –
INTERNET OF THINGS
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Executive Summary
This report has been prepared and presented to the management of Gigantic Corporation
regarding the findings and vulnerabilities identified by the “IT Risk Assessment Lead Consultant
– Internet of Things”. The report has been prepared for enabling the management to take vital
decisions regarding technical risks associated while using IoT-based applications in its
operations. The report contains the major IT-related issues that have been identified by
conducting vulnerabilities and threats assessment and the recommendations have been provided
accordingly. These findings will help the management to develop appropriate IT policies and
procedures which enable to protect the vital information; both personal information of the
employees as well as corporate data.
In order to arrive at appropriate conclusions, the methods such as conducting interviews, Delphi
technique, and brainstorming were used for analysing the possible threats of using the current
policies that are employed for managing and controlling the data while using IoT-based
applications. The views and opinion provided by the experts provided an insight regarding the
vulnerabilities of the current IT infrastructure developed by Gigantic Corporation and the extent
of the risk associated while using the Internet of Things in various operations.
The tools and techniques such as probability and impact matrix, risk data quality assessment and
quantitative risk analysis were used for determining the immediate threats that have to be
mitigated by the organisation. These tools and techniques also enabled to ascertain the threats
and threat agents and the ways in which the loop-holes can be identified and mitigated.
The vulnerabilities and threats have been identified and presented separately along with
illustrating the ratings of these risks which have been classified as high, medium, and low. The
report concentrates on providing the solutions for mitigating high and medium risks as these
risks have the potential of hampering the smooth flow of operations. The high and medium risks
have to be immediately resolved for preventing the instances of threats such as data theft and
data breach. The recommendations have been provided based on the issues identified and the
best possible ways in which these risks can be mitigated effectively.
The report provides the following recommendations based on the findings and which should be
implemented by the management for protecting the organisation from facing serious
consequences, which include:
Using the latest firewall and malware protection software in all IoT-based applications
and server.
Using a firewall in the network which is used for communicating with the customers and
vendors.
Upgrading the applications and software periodically.
Developing and implementing the standard guidelines for using the internet and the
procedure that has to be followed while using software and application.
Developing standard procedures that have to be implemented while dealing with threats.
Strict adherence to the password policies and the sharing of information.
Providing the access to the application and software based on the job role of the user.
Using administrator credentials in all the computers and devices and restricting the user
from using external storage devices such as pen drives.
Restricting the movement of personnel to certain locations such as server rooms.
Using strong passwords for all the applications and software that are being used.
Maintaining a log of users and the type of software and applications they use for better
control.
2
This report has been prepared and presented to the management of Gigantic Corporation
regarding the findings and vulnerabilities identified by the “IT Risk Assessment Lead Consultant
– Internet of Things”. The report has been prepared for enabling the management to take vital
decisions regarding technical risks associated while using IoT-based applications in its
operations. The report contains the major IT-related issues that have been identified by
conducting vulnerabilities and threats assessment and the recommendations have been provided
accordingly. These findings will help the management to develop appropriate IT policies and
procedures which enable to protect the vital information; both personal information of the
employees as well as corporate data.
In order to arrive at appropriate conclusions, the methods such as conducting interviews, Delphi
technique, and brainstorming were used for analysing the possible threats of using the current
policies that are employed for managing and controlling the data while using IoT-based
applications. The views and opinion provided by the experts provided an insight regarding the
vulnerabilities of the current IT infrastructure developed by Gigantic Corporation and the extent
of the risk associated while using the Internet of Things in various operations.
The tools and techniques such as probability and impact matrix, risk data quality assessment and
quantitative risk analysis were used for determining the immediate threats that have to be
mitigated by the organisation. These tools and techniques also enabled to ascertain the threats
and threat agents and the ways in which the loop-holes can be identified and mitigated.
The vulnerabilities and threats have been identified and presented separately along with
illustrating the ratings of these risks which have been classified as high, medium, and low. The
report concentrates on providing the solutions for mitigating high and medium risks as these
risks have the potential of hampering the smooth flow of operations. The high and medium risks
have to be immediately resolved for preventing the instances of threats such as data theft and
data breach. The recommendations have been provided based on the issues identified and the
best possible ways in which these risks can be mitigated effectively.
The report provides the following recommendations based on the findings and which should be
implemented by the management for protecting the organisation from facing serious
consequences, which include:
Using the latest firewall and malware protection software in all IoT-based applications
and server.
Using a firewall in the network which is used for communicating with the customers and
vendors.
Upgrading the applications and software periodically.
Developing and implementing the standard guidelines for using the internet and the
procedure that has to be followed while using software and application.
Developing standard procedures that have to be implemented while dealing with threats.
Strict adherence to the password policies and the sharing of information.
Providing the access to the application and software based on the job role of the user.
Using administrator credentials in all the computers and devices and restricting the user
from using external storage devices such as pen drives.
Restricting the movement of personnel to certain locations such as server rooms.
Using strong passwords for all the applications and software that are being used.
Maintaining a log of users and the type of software and applications they use for better
control.
2

Creating unique Ids and passwords with strong login credentials for using software and
applications.
Installing CCTV cameras at appropriate locations for monitoring the activities performed
by the users and preventing intrusions in the restricted locations.
Separating the personal information of the employees and staff with that of corporate
information.
Taking a regular back-up of the data in a cloud set-up.
Providing training to the employees and staff regarding the ways in which the
applications and software are to be used.
Communicating the possible threats of using the internet to the employees and staff and
the risk associated with accessing websites other than the recommended sites.
Conducting third-party audits regularly.
Periodic assessment of vulnerabilities and threats for ascertaining the effectiveness of
implementing preventive measures.
Using firewall/filters at the server for detecting malwares/ransomware and for identifying
risky websites.
The report also provides a detailed explanation regarding the possible consequences that may
have to be faced if proper control mechanisms are not implemented. Due to the increasing use of
the Internet of Things, the company is too much dependent on the applications and software, it is
necessary to understand the risks associated with using these applications. These details will help
the management to modify the current procedures that are being followed and the measures that
can be taken for enhancing the safety and security of the data. The results of the assessment
provide a clear understanding as to the importance of identifying threat agents and the ways in
which the vulnerabilities can be exploited by the threat agents for accessing the information.
The merits of this project are as given below:
By using firewall and anti-malware, the possible cyber attacks can be prevented thereby
safeguarding the vital information of the company.
Using strong login credentials ensures that the issues related to data theft and data breach
can be eliminated.
Upgrading the applications and software regularly helps the company from possible
malware attacks as the latest versions of the applications are assumed to be safe.
Formulating appropriate guidelines will help the management to implement appropriate
control measures enhancing the existing security of the IT infrastructure.
Communicating the possible risks associated with using the applications and software
enables to implement the policies effectively.
The overall improvement in the IT infrastructure and enhanced security helps to build
trust and confidence among the stakeholders and customers thereby ensuring continuous
growth and development of the organisation.
The report concludes that the results of the risk analysis have been prepared by using appropriate
methods and techniques which enhances its accuracy. By implementing the measures stated in
the report, the organisation will be able to achieve the desired level of effectiveness while using
the Internet of Things in its operations.
3
applications.
Installing CCTV cameras at appropriate locations for monitoring the activities performed
by the users and preventing intrusions in the restricted locations.
Separating the personal information of the employees and staff with that of corporate
information.
Taking a regular back-up of the data in a cloud set-up.
Providing training to the employees and staff regarding the ways in which the
applications and software are to be used.
Communicating the possible threats of using the internet to the employees and staff and
the risk associated with accessing websites other than the recommended sites.
Conducting third-party audits regularly.
Periodic assessment of vulnerabilities and threats for ascertaining the effectiveness of
implementing preventive measures.
Using firewall/filters at the server for detecting malwares/ransomware and for identifying
risky websites.
The report also provides a detailed explanation regarding the possible consequences that may
have to be faced if proper control mechanisms are not implemented. Due to the increasing use of
the Internet of Things, the company is too much dependent on the applications and software, it is
necessary to understand the risks associated with using these applications. These details will help
the management to modify the current procedures that are being followed and the measures that
can be taken for enhancing the safety and security of the data. The results of the assessment
provide a clear understanding as to the importance of identifying threat agents and the ways in
which the vulnerabilities can be exploited by the threat agents for accessing the information.
The merits of this project are as given below:
By using firewall and anti-malware, the possible cyber attacks can be prevented thereby
safeguarding the vital information of the company.
Using strong login credentials ensures that the issues related to data theft and data breach
can be eliminated.
Upgrading the applications and software regularly helps the company from possible
malware attacks as the latest versions of the applications are assumed to be safe.
Formulating appropriate guidelines will help the management to implement appropriate
control measures enhancing the existing security of the IT infrastructure.
Communicating the possible risks associated with using the applications and software
enables to implement the policies effectively.
The overall improvement in the IT infrastructure and enhanced security helps to build
trust and confidence among the stakeholders and customers thereby ensuring continuous
growth and development of the organisation.
The report concludes that the results of the risk analysis have been prepared by using appropriate
methods and techniques which enhances its accuracy. By implementing the measures stated in
the report, the organisation will be able to achieve the desired level of effectiveness while using
the Internet of Things in its operations.
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table of Contents
Executive Summary.....................................................................................................................................1
Introduction.................................................................................................................................................4
Risk Management Overview....................................................................................................................... 5
Techniques used:.........................................................................................................................................6
Risk Assessment and Analysis:................................................................................................................... 7
Identification of the vulnerabilities.......................................................................................................... 8
Threats................................................................................................................................................... 10
Evaluation of the risks...............................................................................................................................11
Assessment Findings................................................................................................................................. 13
Risk Treatment and Response...................................................................................................................14
Findings based Recommendations.............................................................................................................14
Conclusion................................................................................................................................................. 17
References.................................................................................................................................................18
4
Executive Summary.....................................................................................................................................1
Introduction.................................................................................................................................................4
Risk Management Overview....................................................................................................................... 5
Techniques used:.........................................................................................................................................6
Risk Assessment and Analysis:................................................................................................................... 7
Identification of the vulnerabilities.......................................................................................................... 8
Threats................................................................................................................................................... 10
Evaluation of the risks...............................................................................................................................11
Assessment Findings................................................................................................................................. 13
Risk Treatment and Response...................................................................................................................14
Findings based Recommendations.............................................................................................................14
Conclusion................................................................................................................................................. 17
References.................................................................................................................................................18
4
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
This report has been prepared for providing a detailed analysis of implementing the applications
and software in Gigantic Corporation based on the concept of the Internet of Things. With the
increased usage of web-based interfaces, the various issues related to the security of the data as
well as the server is being faced by the company. The report has been prepared by conducting a
detailed vulnerability and threat analysis by using appropriate methods and techniques and the
possible consequences of these threats have also been explained in detail. The report also
provides the solution for resolving the issues and the ways in which the threats can be mitigated
have also been explained. Suitable recommendations have also been provided which can be used
by the management for safeguarding the vital information of the employees and customers.
Aim
The purpose of the report is to analyse the possible threats that can be faced by Gigantic
Corporation while using applications and software based on the concept of the Internet of
Things. The threats and vulnerabilities are identified and the impact of these risks has also been
explained which can be utilised by the management while developing a risk mitigation plan.
Assessment Scope
The scope of the risk assessment contains the factors and elements associated with the internet of
things. The report explains the important factors; both internal and external, that has to be
considered while formulating policies and procedures for mitigating the issues related to the
Interne of Things. The safety and security of the data and the server has been given importance
as the organisation deals with a huge volume of data which is vital for the growth and
development of the organisation.
It is important to monitor and control the activities of the users since the company relies on the
various applications and software that are used for performing activities. The report provides
clear guidelines that have to be followed for preventing the instances of data theft and
unauthorised use of data. The importance of providing strong login credentials has also been
explained.
The recommendations that are provided in the last part of the report explain the possible ways of
resolving the issues related to access controls and safety and security of the information. The
findings-based recommendations enable the management to take appropriate measures for
implementing appropriate control measures which help to overcome the threats faced by
Gigantic Corporation.
5
This report has been prepared for providing a detailed analysis of implementing the applications
and software in Gigantic Corporation based on the concept of the Internet of Things. With the
increased usage of web-based interfaces, the various issues related to the security of the data as
well as the server is being faced by the company. The report has been prepared by conducting a
detailed vulnerability and threat analysis by using appropriate methods and techniques and the
possible consequences of these threats have also been explained in detail. The report also
provides the solution for resolving the issues and the ways in which the threats can be mitigated
have also been explained. Suitable recommendations have also been provided which can be used
by the management for safeguarding the vital information of the employees and customers.
Aim
The purpose of the report is to analyse the possible threats that can be faced by Gigantic
Corporation while using applications and software based on the concept of the Internet of
Things. The threats and vulnerabilities are identified and the impact of these risks has also been
explained which can be utilised by the management while developing a risk mitigation plan.
Assessment Scope
The scope of the risk assessment contains the factors and elements associated with the internet of
things. The report explains the important factors; both internal and external, that has to be
considered while formulating policies and procedures for mitigating the issues related to the
Interne of Things. The safety and security of the data and the server has been given importance
as the organisation deals with a huge volume of data which is vital for the growth and
development of the organisation.
It is important to monitor and control the activities of the users since the company relies on the
various applications and software that are used for performing activities. The report provides
clear guidelines that have to be followed for preventing the instances of data theft and
unauthorised use of data. The importance of providing strong login credentials has also been
explained.
The recommendations that are provided in the last part of the report explain the possible ways of
resolving the issues related to access controls and safety and security of the information. The
findings-based recommendations enable the management to take appropriate measures for
implementing appropriate control measures which help to overcome the threats faced by
Gigantic Corporation.
5

Risk Management Overview
The risk management is a process which involves identifying and managing the various risks
involved which may result in negatively impacting the operations of Gigantic Corporation. There
are various risks involved while developing a system based on the Internet of Things in which
the different functions of the organisation are connected through the Internet. The risks that are
involved while developing the system based on Internet of Things are system failures, instances
of data loss and data breach, natural disasters, and cyber attacks. These risks have to be mitigated
so that the organisation can overcome these issues and enhance the operational efficiencies and
protect the company from resulting losses (Biener, et. al., 2015).
It is very well established that it is important to protect the information as the competitors are
always looking for a way to extract confidential information for gaining an upper hand in the
market. Hence, it is essential that the key risks are identified so that a comprehensive plan can be
developed for protecting the server and the systems. The key factors have to be identified which
can be used for preventing any mishaps and the best possible ways of enhancing the cyber
security throughout the organisation.
The risk management process that has to be followed by Gigantic Corporation can be divided
into three steps:
Risk Assessment and Analysis: In this stage, the firm’s exposure to the potential risks and
uncertainties in the business and the resulting losses that may occur due to these risks. For
analysing the true nature of the risks, the company has to ascertain the market condition and the
objectives that are defined while developing the system based on the Internet of Things. This can
be explained by citing an example wherein the finance and sales functions are interconnected so
that the sales figures can be projected based on the actual sales target achieved by the team. In
this scenario, the potential risks that can be faced by Gigantic Corporation are; system failures in
finance, connectivity issues, data breach and data theft, and cyber attacks. Hence, the company
should identify the potential threats by assessing the risks involved in particular departments and
functions (Van Grembergen & De Haes).
Risk Evaluation: In this stage, the criteria are defined based on which the risks can be assessed
and the factors that have to be considered while evaluating the risks.
Risk Treatment and Response: The techniques and procedures are enlisted in this stage which
helps to mitigate the issues identified in the risk assessment stage.
Developing monitoring controls: It is essential for monitoring the systems and vulnerable
factors continuously so that the threats can be prevented and appropriate actions can be taken
quickly for mitigating the threats at the initial stage itself.
6
The risk management is a process which involves identifying and managing the various risks
involved which may result in negatively impacting the operations of Gigantic Corporation. There
are various risks involved while developing a system based on the Internet of Things in which
the different functions of the organisation are connected through the Internet. The risks that are
involved while developing the system based on Internet of Things are system failures, instances
of data loss and data breach, natural disasters, and cyber attacks. These risks have to be mitigated
so that the organisation can overcome these issues and enhance the operational efficiencies and
protect the company from resulting losses (Biener, et. al., 2015).
It is very well established that it is important to protect the information as the competitors are
always looking for a way to extract confidential information for gaining an upper hand in the
market. Hence, it is essential that the key risks are identified so that a comprehensive plan can be
developed for protecting the server and the systems. The key factors have to be identified which
can be used for preventing any mishaps and the best possible ways of enhancing the cyber
security throughout the organisation.
The risk management process that has to be followed by Gigantic Corporation can be divided
into three steps:
Risk Assessment and Analysis: In this stage, the firm’s exposure to the potential risks and
uncertainties in the business and the resulting losses that may occur due to these risks. For
analysing the true nature of the risks, the company has to ascertain the market condition and the
objectives that are defined while developing the system based on the Internet of Things. This can
be explained by citing an example wherein the finance and sales functions are interconnected so
that the sales figures can be projected based on the actual sales target achieved by the team. In
this scenario, the potential risks that can be faced by Gigantic Corporation are; system failures in
finance, connectivity issues, data breach and data theft, and cyber attacks. Hence, the company
should identify the potential threats by assessing the risks involved in particular departments and
functions (Van Grembergen & De Haes).
Risk Evaluation: In this stage, the criteria are defined based on which the risks can be assessed
and the factors that have to be considered while evaluating the risks.
Risk Treatment and Response: The techniques and procedures are enlisted in this stage which
helps to mitigate the issues identified in the risk assessment stage.
Developing monitoring controls: It is essential for monitoring the systems and vulnerable
factors continuously so that the threats can be prevented and appropriate actions can be taken
quickly for mitigating the threats at the initial stage itself.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 1: Risk Management Process
Source: (LucidChart, 2017)
Techniques used:
The techniques that are used for analysing the risk parameters are:
Documentation reviews:
The documents that are maintained by the organisations related to the assets, details of the
previous projects, and the results of the previous projects implemented are examined.
Interview: The interviews were conducted by preparing suitable questionnaires for ascertaining
the type of risks that are usually faced by the management. The participants were divided into
separate groups namely; employees, experts, and top-level executives.
Delphi Technique: In this technique, a list of questions was sent to the experts and stakeholders
for getting the responses on various topics and the results are sent back to them for arriving at a
common consensus.
Brainstorming: The brainstorming sessions were organised with the group of experts and top-
level executives for identifying the risks associated with the project.
SWOT Analysis: This is a management tool which can be used by the management for
ascertaining the strengths, and weaknesses of the firm and the opportunities that can be utilised
for overcoming the weaknesses.
The SWOT analysis of Gigantic Corporation for using the Internet of Things in various
operations is given below:
Strengths Weaknesses
Presence of well-established IT
infrastructure.
Using outdated applications and
software
7
Source: (LucidChart, 2017)
Techniques used:
The techniques that are used for analysing the risk parameters are:
Documentation reviews:
The documents that are maintained by the organisations related to the assets, details of the
previous projects, and the results of the previous projects implemented are examined.
Interview: The interviews were conducted by preparing suitable questionnaires for ascertaining
the type of risks that are usually faced by the management. The participants were divided into
separate groups namely; employees, experts, and top-level executives.
Delphi Technique: In this technique, a list of questions was sent to the experts and stakeholders
for getting the responses on various topics and the results are sent back to them for arriving at a
common consensus.
Brainstorming: The brainstorming sessions were organised with the group of experts and top-
level executives for identifying the risks associated with the project.
SWOT Analysis: This is a management tool which can be used by the management for
ascertaining the strengths, and weaknesses of the firm and the opportunities that can be utilised
for overcoming the weaknesses.
The SWOT analysis of Gigantic Corporation for using the Internet of Things in various
operations is given below:
Strengths Weaknesses
Presence of well-established IT
infrastructure.
Using outdated applications and
software
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
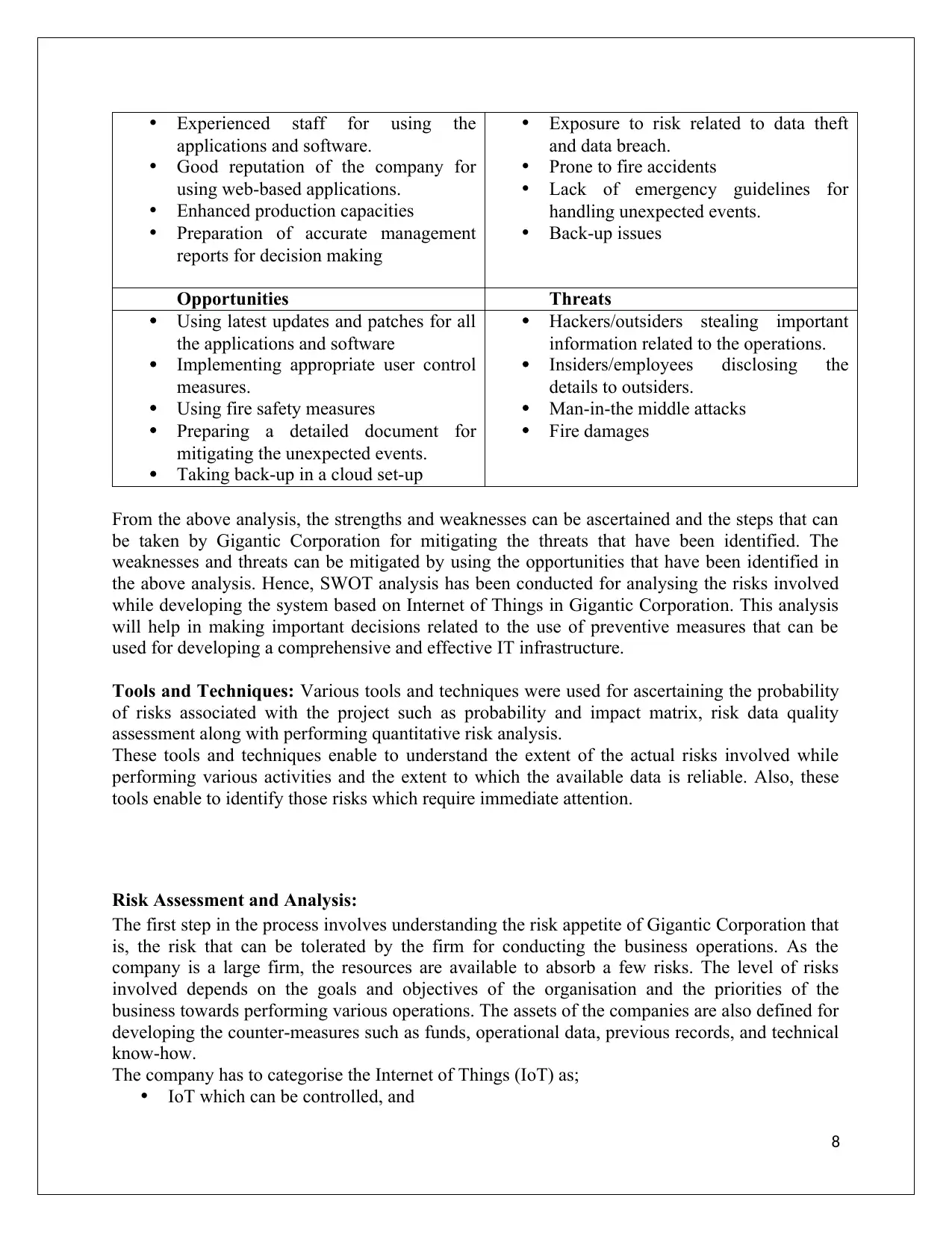
Experienced staff for using the
applications and software.
Good reputation of the company for
using web-based applications.
Enhanced production capacities
Preparation of accurate management
reports for decision making
Exposure to risk related to data theft
and data breach.
Prone to fire accidents
Lack of emergency guidelines for
handling unexpected events.
Back-up issues
Opportunities Threats
Using latest updates and patches for all
the applications and software
Implementing appropriate user control
measures.
Using fire safety measures
Preparing a detailed document for
mitigating the unexpected events.
Taking back-up in a cloud set-up
Hackers/outsiders stealing important
information related to the operations.
Insiders/employees disclosing the
details to outsiders.
Man-in-the middle attacks
Fire damages
From the above analysis, the strengths and weaknesses can be ascertained and the steps that can
be taken by Gigantic Corporation for mitigating the threats that have been identified. The
weaknesses and threats can be mitigated by using the opportunities that have been identified in
the above analysis. Hence, SWOT analysis has been conducted for analysing the risks involved
while developing the system based on Internet of Things in Gigantic Corporation. This analysis
will help in making important decisions related to the use of preventive measures that can be
used for developing a comprehensive and effective IT infrastructure.
Tools and Techniques: Various tools and techniques were used for ascertaining the probability
of risks associated with the project such as probability and impact matrix, risk data quality
assessment along with performing quantitative risk analysis.
These tools and techniques enable to understand the extent of the actual risks involved while
performing various activities and the extent to which the available data is reliable. Also, these
tools enable to identify those risks which require immediate attention.
Risk Assessment and Analysis:
The first step in the process involves understanding the risk appetite of Gigantic Corporation that
is, the risk that can be tolerated by the firm for conducting the business operations. As the
company is a large firm, the resources are available to absorb a few risks. The level of risks
involved depends on the goals and objectives of the organisation and the priorities of the
business towards performing various operations. The assets of the companies are also defined for
developing the counter-measures such as funds, operational data, previous records, and technical
know-how.
The company has to categorise the Internet of Things (IoT) as;
IoT which can be controlled, and
8
applications and software.
Good reputation of the company for
using web-based applications.
Enhanced production capacities
Preparation of accurate management
reports for decision making
Exposure to risk related to data theft
and data breach.
Prone to fire accidents
Lack of emergency guidelines for
handling unexpected events.
Back-up issues
Opportunities Threats
Using latest updates and patches for all
the applications and software
Implementing appropriate user control
measures.
Using fire safety measures
Preparing a detailed document for
mitigating the unexpected events.
Taking back-up in a cloud set-up
Hackers/outsiders stealing important
information related to the operations.
Insiders/employees disclosing the
details to outsiders.
Man-in-the middle attacks
Fire damages
From the above analysis, the strengths and weaknesses can be ascertained and the steps that can
be taken by Gigantic Corporation for mitigating the threats that have been identified. The
weaknesses and threats can be mitigated by using the opportunities that have been identified in
the above analysis. Hence, SWOT analysis has been conducted for analysing the risks involved
while developing the system based on Internet of Things in Gigantic Corporation. This analysis
will help in making important decisions related to the use of preventive measures that can be
used for developing a comprehensive and effective IT infrastructure.
Tools and Techniques: Various tools and techniques were used for ascertaining the probability
of risks associated with the project such as probability and impact matrix, risk data quality
assessment along with performing quantitative risk analysis.
These tools and techniques enable to understand the extent of the actual risks involved while
performing various activities and the extent to which the available data is reliable. Also, these
tools enable to identify those risks which require immediate attention.
Risk Assessment and Analysis:
The first step in the process involves understanding the risk appetite of Gigantic Corporation that
is, the risk that can be tolerated by the firm for conducting the business operations. As the
company is a large firm, the resources are available to absorb a few risks. The level of risks
involved depends on the goals and objectives of the organisation and the priorities of the
business towards performing various operations. The assets of the companies are also defined for
developing the counter-measures such as funds, operational data, previous records, and technical
know-how.
The company has to categorise the Internet of Things (IoT) as;
IoT which can be controlled, and
8
IoT which cannot be controlled
IoT which can be controlled are the computers and other devices which are used by the
employees within and outside of the company. These devices can be tracked and hence, the risks
associated with these devices and applications are limited. The users of these devices can be
identified easily, therefore, the instance of data breach and any other threats can be easily
identified.
IoT which cannot be controlled is those where the systems of the firm are connected through
an external networks such as communication between the customers and the company. Here, the
interacting phase cannot be controlled as the customers use a different type of devices and
connections. These external agents are a serious threat as the malicious content can enter the
server thereby involves a high amount of risk.
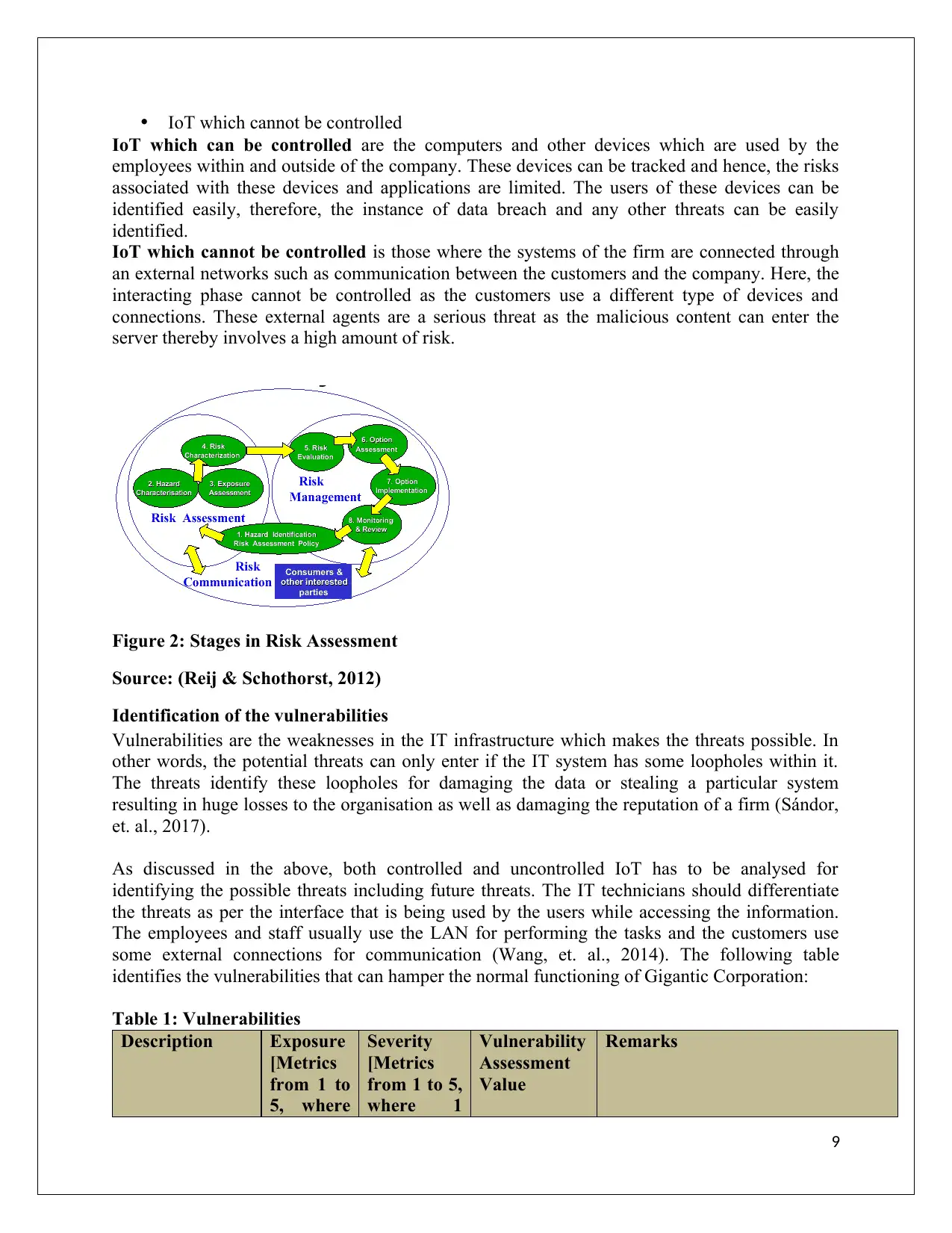
Figure 2: Stages in Risk Assessment
Source: (Reij & Schothorst, 2012)
Identification of the vulnerabilities
Vulnerabilities are the weaknesses in the IT infrastructure which makes the threats possible. In
other words, the potential threats can only enter if the IT system has some loopholes within it.
The threats identify these loopholes for damaging the data or stealing a particular system
resulting in huge losses to the organisation as well as damaging the reputation of a firm (Sándor,
et. al., 2017).
As discussed in the above, both controlled and uncontrolled IoT has to be analysed for
identifying the possible threats including future threats. The IT technicians should differentiate
the threats as per the interface that is being used by the users while accessing the information.
The employees and staff usually use the LAN for performing the tasks and the customers use
some external connections for communication (Wang, et. al., 2014). The following table
identifies the vulnerabilities that can hamper the normal functioning of Gigantic Corporation:
Table 1: Vulnerabilities
Description Exposure
[Metrics
from 1 to
5, where
Severity
[Metrics
from 1 to 5,
where 1
Vulnerability
Assessment
Value
Remarks
9
IoT which can be controlled are the computers and other devices which are used by the
employees within and outside of the company. These devices can be tracked and hence, the risks
associated with these devices and applications are limited. The users of these devices can be
identified easily, therefore, the instance of data breach and any other threats can be easily
identified.
IoT which cannot be controlled is those where the systems of the firm are connected through
an external networks such as communication between the customers and the company. Here, the
interacting phase cannot be controlled as the customers use a different type of devices and
connections. These external agents are a serious threat as the malicious content can enter the
server thereby involves a high amount of risk.
Figure 2: Stages in Risk Assessment
Source: (Reij & Schothorst, 2012)
Identification of the vulnerabilities
Vulnerabilities are the weaknesses in the IT infrastructure which makes the threats possible. In
other words, the potential threats can only enter if the IT system has some loopholes within it.
The threats identify these loopholes for damaging the data or stealing a particular system
resulting in huge losses to the organisation as well as damaging the reputation of a firm (Sándor,
et. al., 2017).
As discussed in the above, both controlled and uncontrolled IoT has to be analysed for
identifying the possible threats including future threats. The IT technicians should differentiate
the threats as per the interface that is being used by the users while accessing the information.
The employees and staff usually use the LAN for performing the tasks and the customers use
some external connections for communication (Wang, et. al., 2014). The following table
identifies the vulnerabilities that can hamper the normal functioning of Gigantic Corporation:
Table 1: Vulnerabilities
Description Exposure
[Metrics
from 1 to
5, where
Severity
[Metrics
from 1 to 5,
where 1
Vulnerability
Assessment
Value
Remarks
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
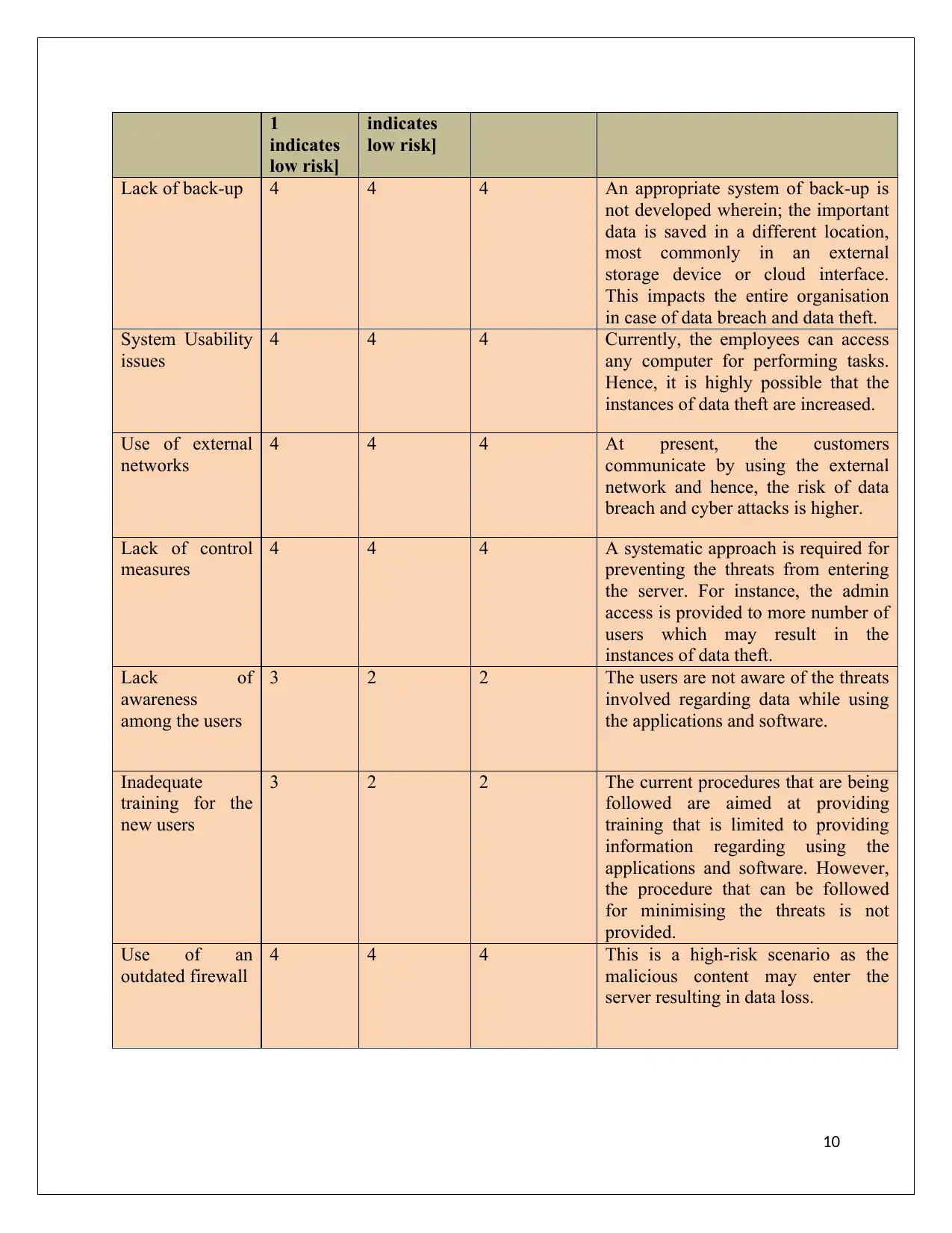
1
indicates
low risk]
indicates
low risk]
Lack of back-up 4 4 4 An appropriate system of back-up is
not developed wherein; the important
data is saved in a different location,
most commonly in an external
storage device or cloud interface.
This impacts the entire organisation
in case of data breach and data theft.
System Usability
issues
4 4 4 Currently, the employees can access
any computer for performing tasks.
Hence, it is highly possible that the
instances of data theft are increased.
Use of external
networks
4 4 4 At present, the customers
communicate by using the external
network and hence, the risk of data
breach and cyber attacks is higher.
Lack of control
measures
4 4 4 A systematic approach is required for
preventing the threats from entering
the server. For instance, the admin
access is provided to more number of
users which may result in the
instances of data theft.
Lack of
awareness
among the users
3 2 2 The users are not aware of the threats
involved regarding data while using
the applications and software.
Inadequate
training for the
new users
3 2 2 The current procedures that are being
followed are aimed at providing
training that is limited to providing
information regarding using the
applications and software. However,
the procedure that can be followed
for minimising the threats is not
provided.
Use of an
outdated firewall
4 4 4 This is a high-risk scenario as the
malicious content may enter the
server resulting in data loss.
10
indicates
low risk]
indicates
low risk]
Lack of back-up 4 4 4 An appropriate system of back-up is
not developed wherein; the important
data is saved in a different location,
most commonly in an external
storage device or cloud interface.
This impacts the entire organisation
in case of data breach and data theft.
System Usability
issues
4 4 4 Currently, the employees can access
any computer for performing tasks.
Hence, it is highly possible that the
instances of data theft are increased.
Use of external
networks
4 4 4 At present, the customers
communicate by using the external
network and hence, the risk of data
breach and cyber attacks is higher.
Lack of control
measures
4 4 4 A systematic approach is required for
preventing the threats from entering
the server. For instance, the admin
access is provided to more number of
users which may result in the
instances of data theft.
Lack of
awareness
among the users
3 2 2 The users are not aware of the threats
involved regarding data while using
the applications and software.
Inadequate
training for the
new users
3 2 2 The current procedures that are being
followed are aimed at providing
training that is limited to providing
information regarding using the
applications and software. However,
the procedure that can be followed
for minimising the threats is not
provided.
Use of an
outdated firewall
4 4 4 This is a high-risk scenario as the
malicious content may enter the
server resulting in data loss.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The above-mentioned vulnerabilities have been identified for developing a comprehensive
system which can be used for developing a system for mitigating the issues. A detailed
explanation regarding the vulnerabilities has also been explained which is helpful for
ascertaining the solutions that can be used while implementing control mechanisms.
Threats
Threats are the negative event that results in undesired outcome such as data loss or incurring
financial losses. These threats are initiated by Threat Actors who breach the security apparatus
because of drawbacks in the IT management system (Chatzimichailidou, et. al., 2015). The
threats that can potentially damage the company’s data are competitors trying to steal vital
information from Gigantic Corporation. The threats that can cause damage to the company have
been provided in the following table:
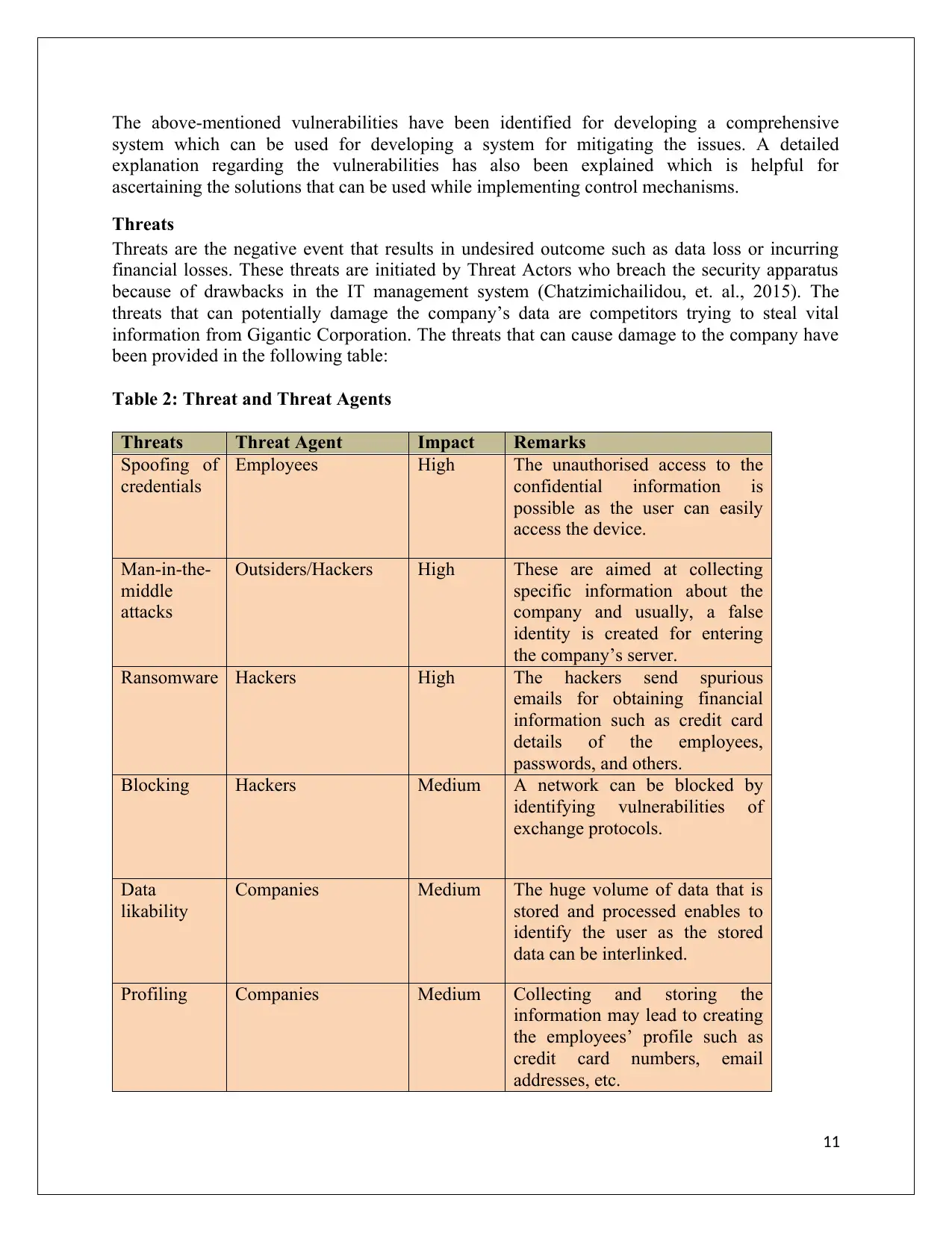
Table 2: Threat and Threat Agents
Threats Threat Agent Impact Remarks
Spoofing of
credentials
Employees High The unauthorised access to the
confidential information is
possible as the user can easily
access the device.
Man-in-the-
middle
attacks
Outsiders/Hackers High These are aimed at collecting
specific information about the
company and usually, a false
identity is created for entering
the company’s server.
Ransomware Hackers High The hackers send spurious
emails for obtaining financial
information such as credit card
details of the employees,
passwords, and others.
Blocking Hackers Medium A network can be blocked by
identifying vulnerabilities of
exchange protocols.
Data
likability
Companies Medium The huge volume of data that is
stored and processed enables to
identify the user as the stored
data can be interlinked.
Profiling Companies Medium Collecting and storing the
information may lead to creating
the employees’ profile such as
credit card numbers, email
addresses, etc.
11
system which can be used for developing a system for mitigating the issues. A detailed
explanation regarding the vulnerabilities has also been explained which is helpful for
ascertaining the solutions that can be used while implementing control mechanisms.
Threats
Threats are the negative event that results in undesired outcome such as data loss or incurring
financial losses. These threats are initiated by Threat Actors who breach the security apparatus
because of drawbacks in the IT management system (Chatzimichailidou, et. al., 2015). The
threats that can potentially damage the company’s data are competitors trying to steal vital
information from Gigantic Corporation. The threats that can cause damage to the company have
been provided in the following table:
Table 2: Threat and Threat Agents
Threats Threat Agent Impact Remarks
Spoofing of
credentials
Employees High The unauthorised access to the
confidential information is
possible as the user can easily
access the device.
Man-in-the-
middle
attacks
Outsiders/Hackers High These are aimed at collecting
specific information about the
company and usually, a false
identity is created for entering
the company’s server.
Ransomware Hackers High The hackers send spurious
emails for obtaining financial
information such as credit card
details of the employees,
passwords, and others.
Blocking Hackers Medium A network can be blocked by
identifying vulnerabilities of
exchange protocols.
Data
likability
Companies Medium The huge volume of data that is
stored and processed enables to
identify the user as the stored
data can be interlinked.
Profiling Companies Medium Collecting and storing the
information may lead to creating
the employees’ profile such as
credit card numbers, email
addresses, etc.
11
Fire
Accidents
Outsiders/Staff High Fire accidents result in damaging
the cables affecting the
communication channel.
The above threats have the potential of damaging the reputation of the firm resulting in facing
long-term consequences. The increased usage of the Internet of Things applications results in
storing important details of the employees and staff and the threat agents exploit the
vulnerabilities for creating damages. The threats and threat agents both require sufficient time
and space for entering the system and there are various methods in which the vulnerabilities are
exploited such as man-in-the-middle attacks.
Evaluation of the risks
These are the chances of facing a negative event which is to be avoided along with its probability
and impact, which can be denoted as:
Risk = probability X impact\
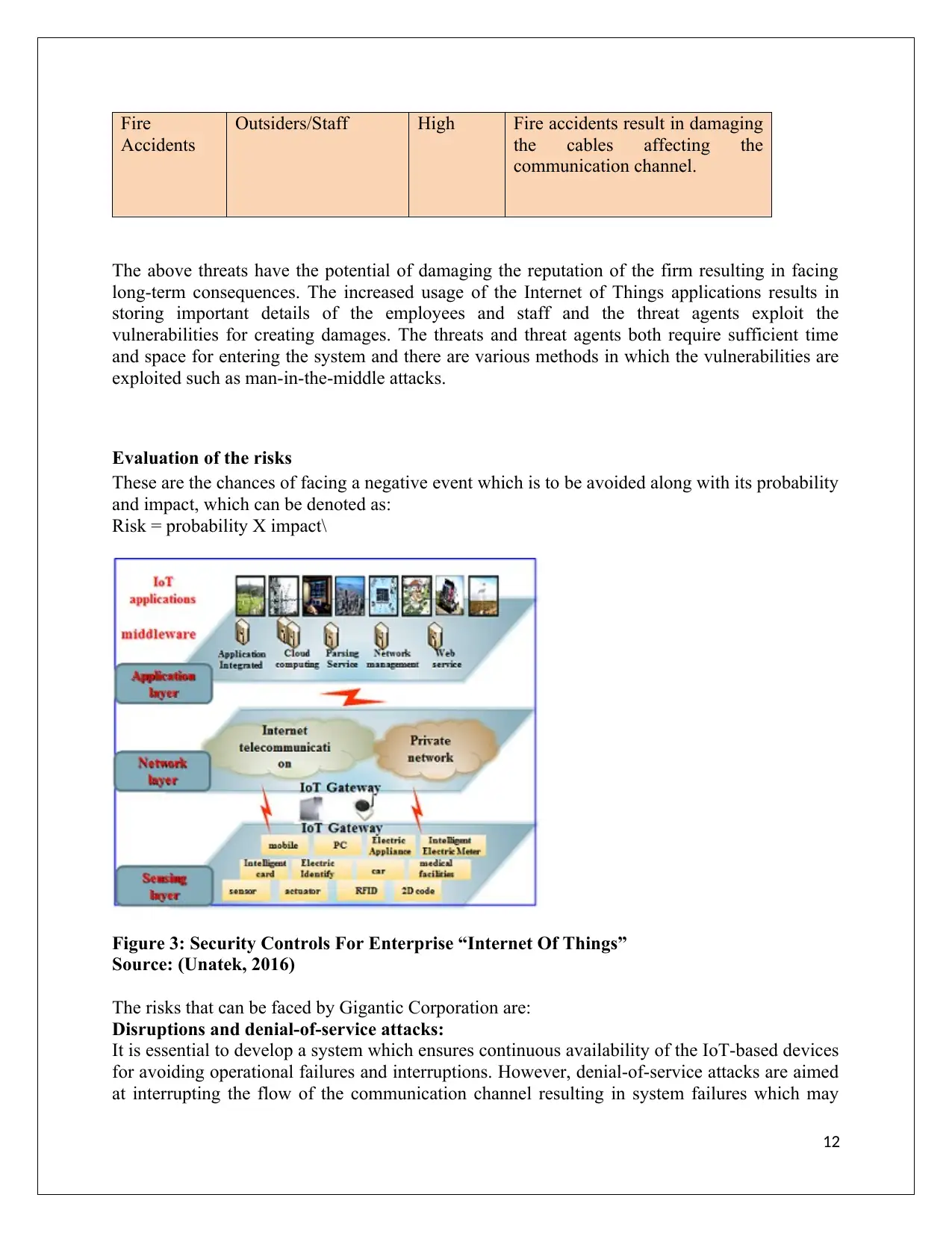
Figure 3: Security Controls For Enterprise “Internet Of Things”
Source: (Unatek, 2016)
The risks that can be faced by Gigantic Corporation are:
Disruptions and denial-of-service attacks:
It is essential to develop a system which ensures continuous availability of the IoT-based devices
for avoiding operational failures and interruptions. However, denial-of-service attacks are aimed
at interrupting the flow of the communication channel resulting in system failures which may
12
Accidents
Outsiders/Staff High Fire accidents result in damaging
the cables affecting the
communication channel.
The above threats have the potential of damaging the reputation of the firm resulting in facing
long-term consequences. The increased usage of the Internet of Things applications results in
storing important details of the employees and staff and the threat agents exploit the
vulnerabilities for creating damages. The threats and threat agents both require sufficient time
and space for entering the system and there are various methods in which the vulnerabilities are
exploited such as man-in-the-middle attacks.
Evaluation of the risks
These are the chances of facing a negative event which is to be avoided along with its probability
and impact, which can be denoted as:
Risk = probability X impact\
Figure 3: Security Controls For Enterprise “Internet Of Things”
Source: (Unatek, 2016)
The risks that can be faced by Gigantic Corporation are:
Disruptions and denial-of-service attacks:
It is essential to develop a system which ensures continuous availability of the IoT-based devices
for avoiding operational failures and interruptions. However, denial-of-service attacks are aimed
at interrupting the flow of the communication channel resulting in system failures which may
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 20
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





