ITEC 4242: Module 4 Assignment Solutions Spring 2019 - Database Tasks
VerifiedAdded on 2023/01/19
|13
|802
|83
Homework Assignment
AI Summary
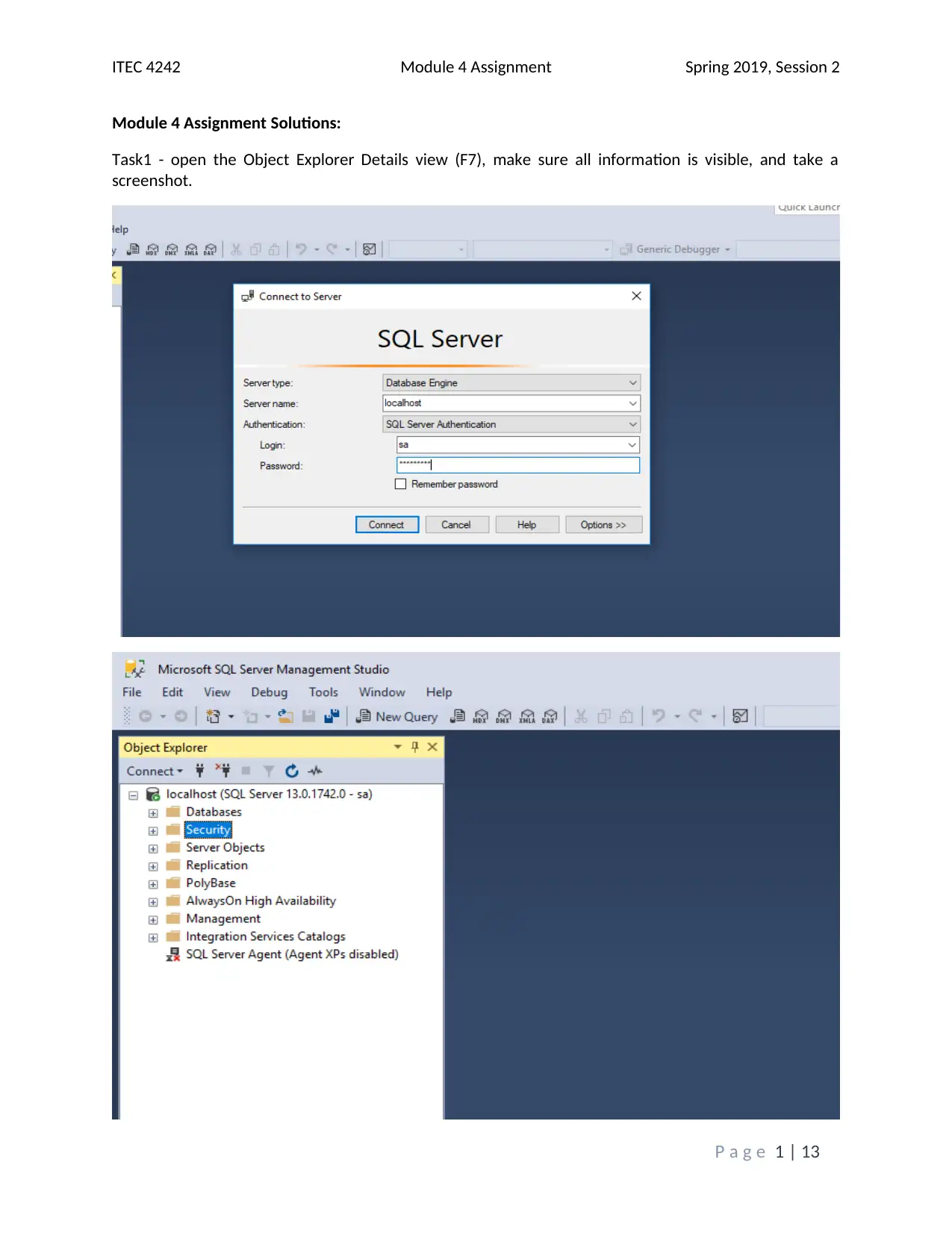
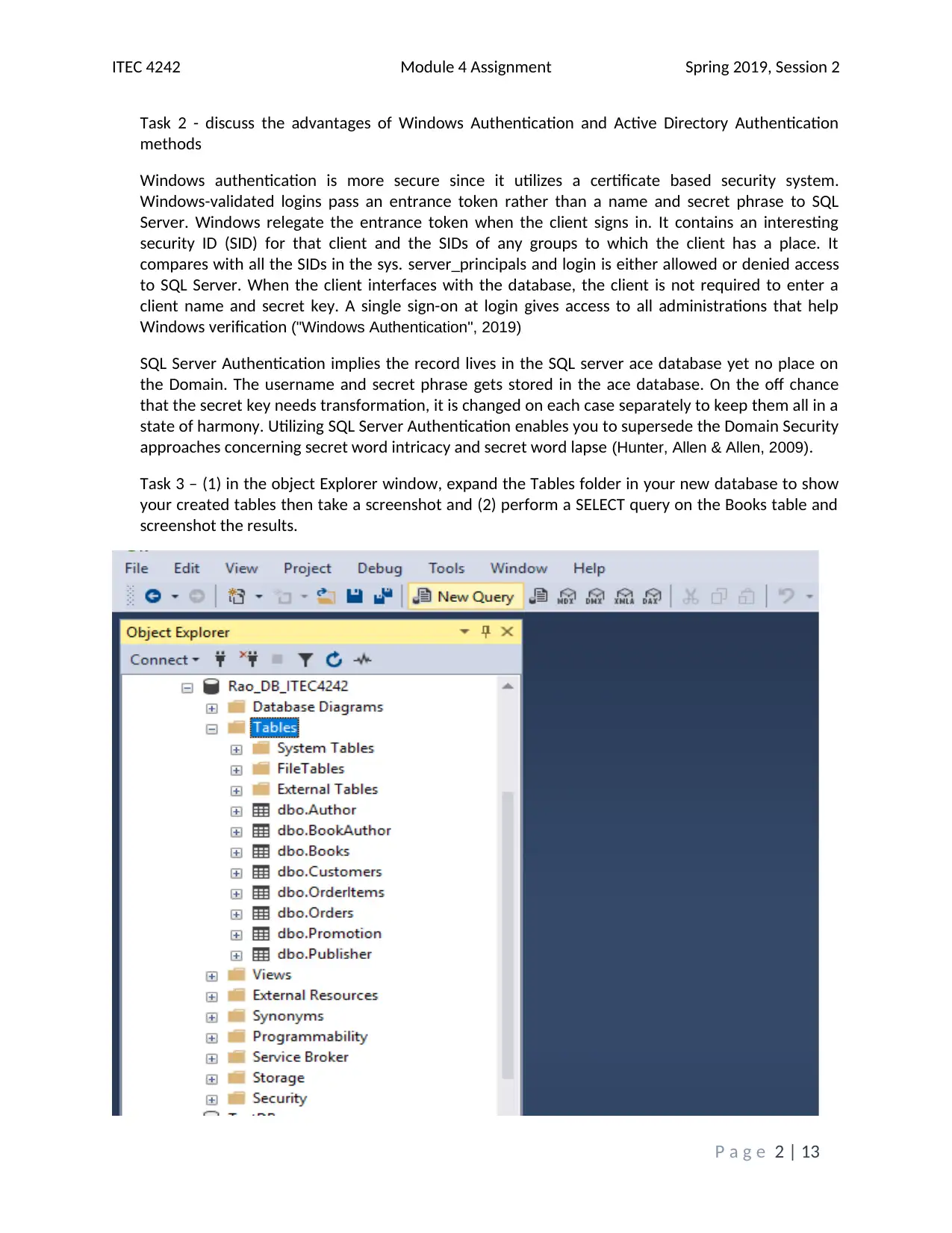
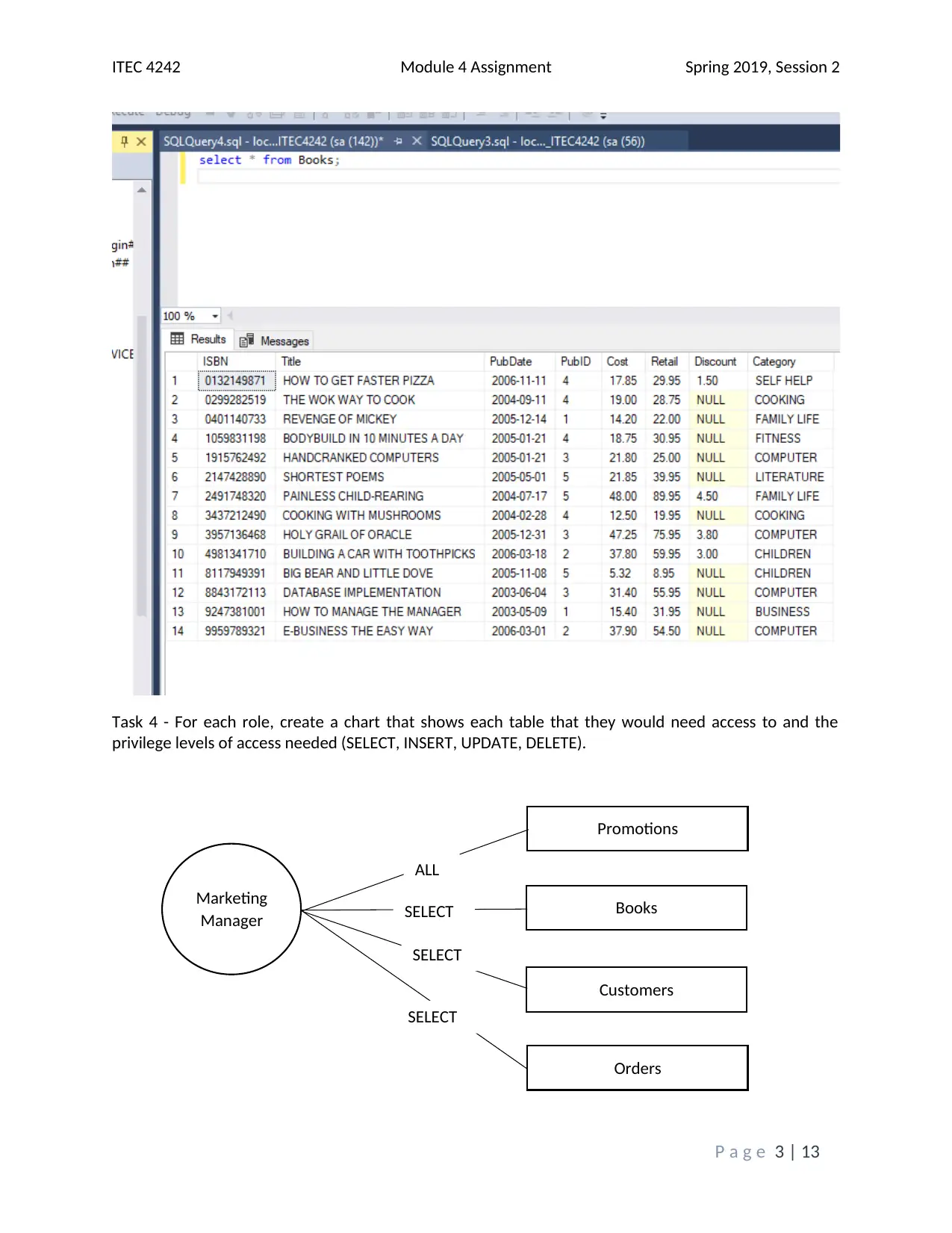
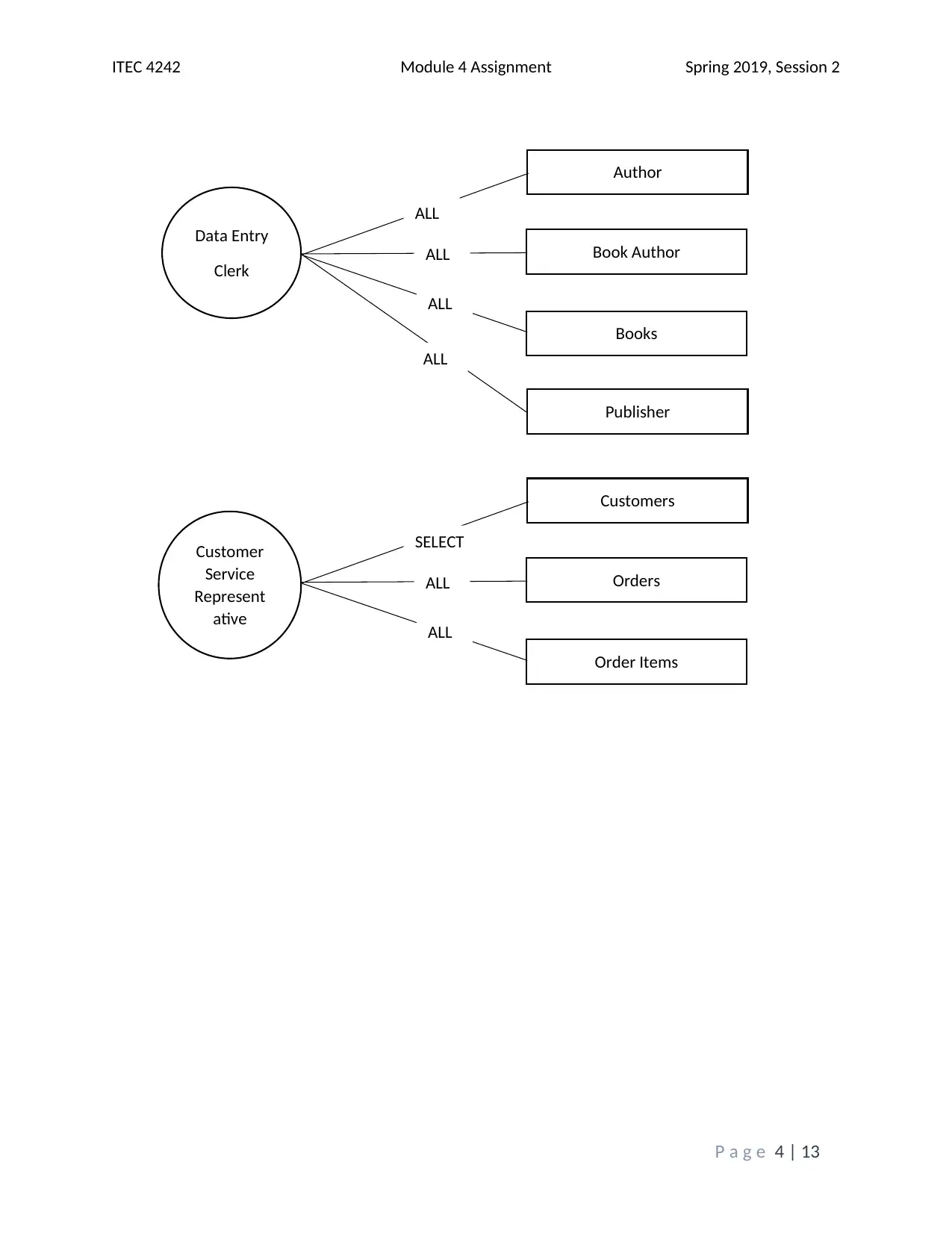
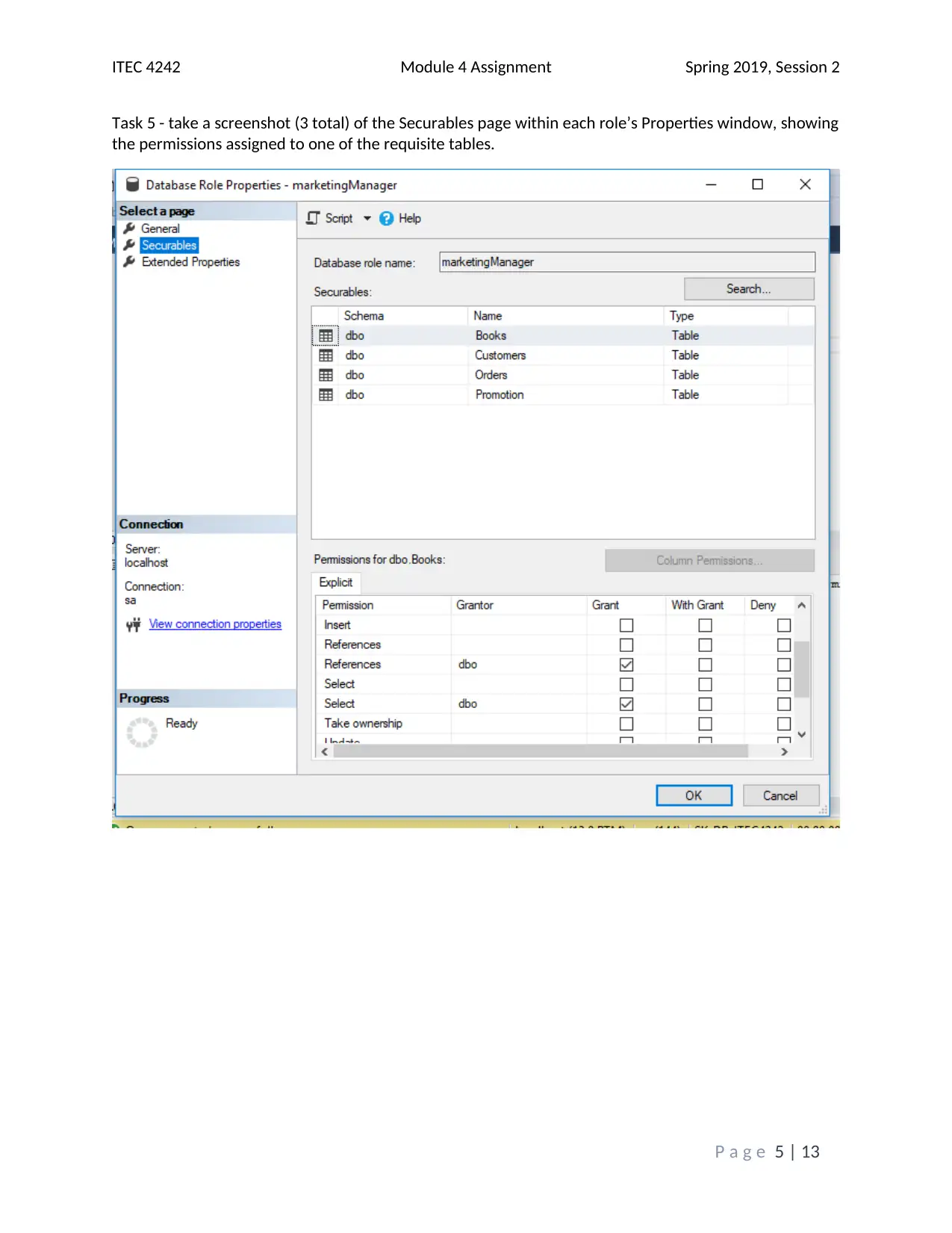
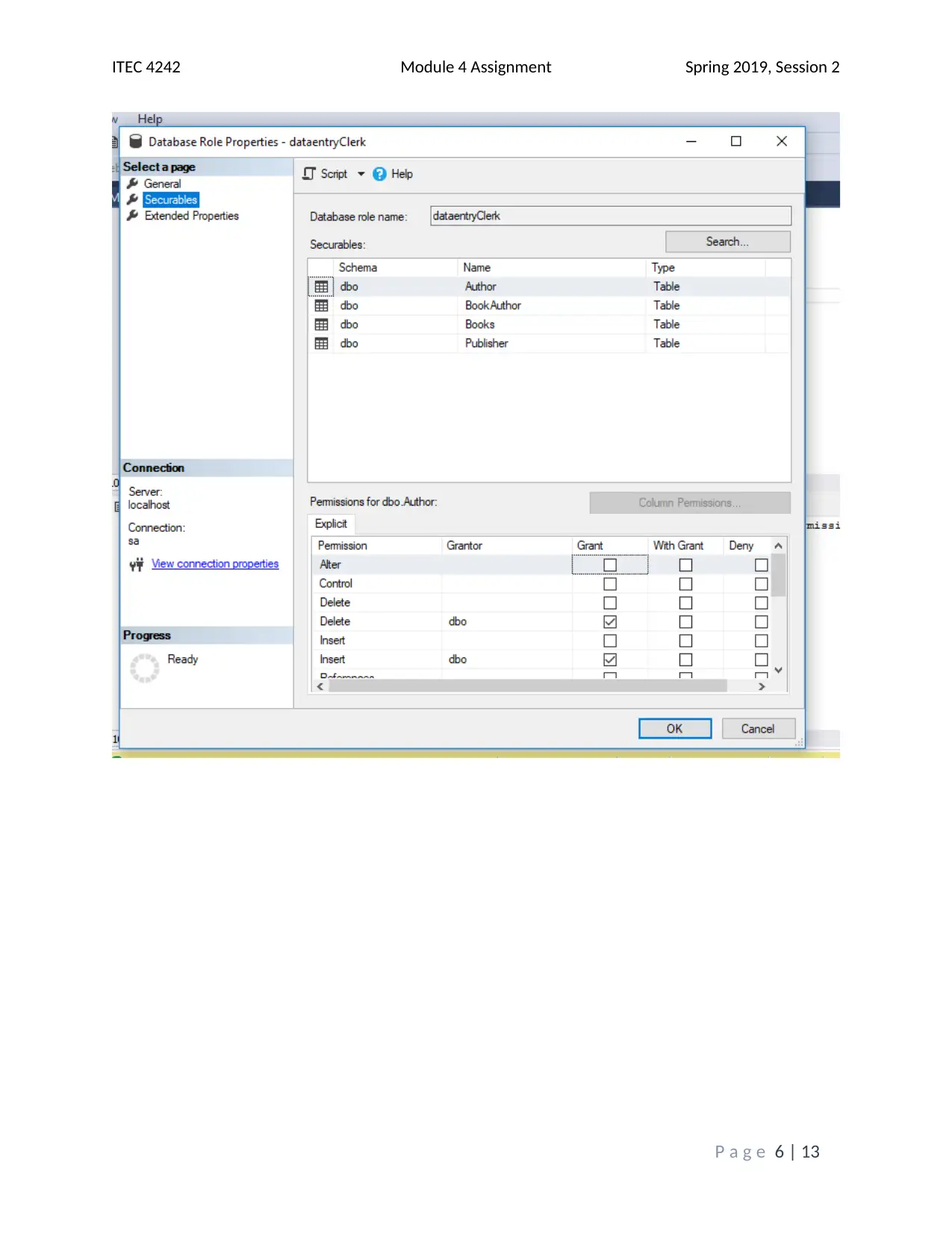
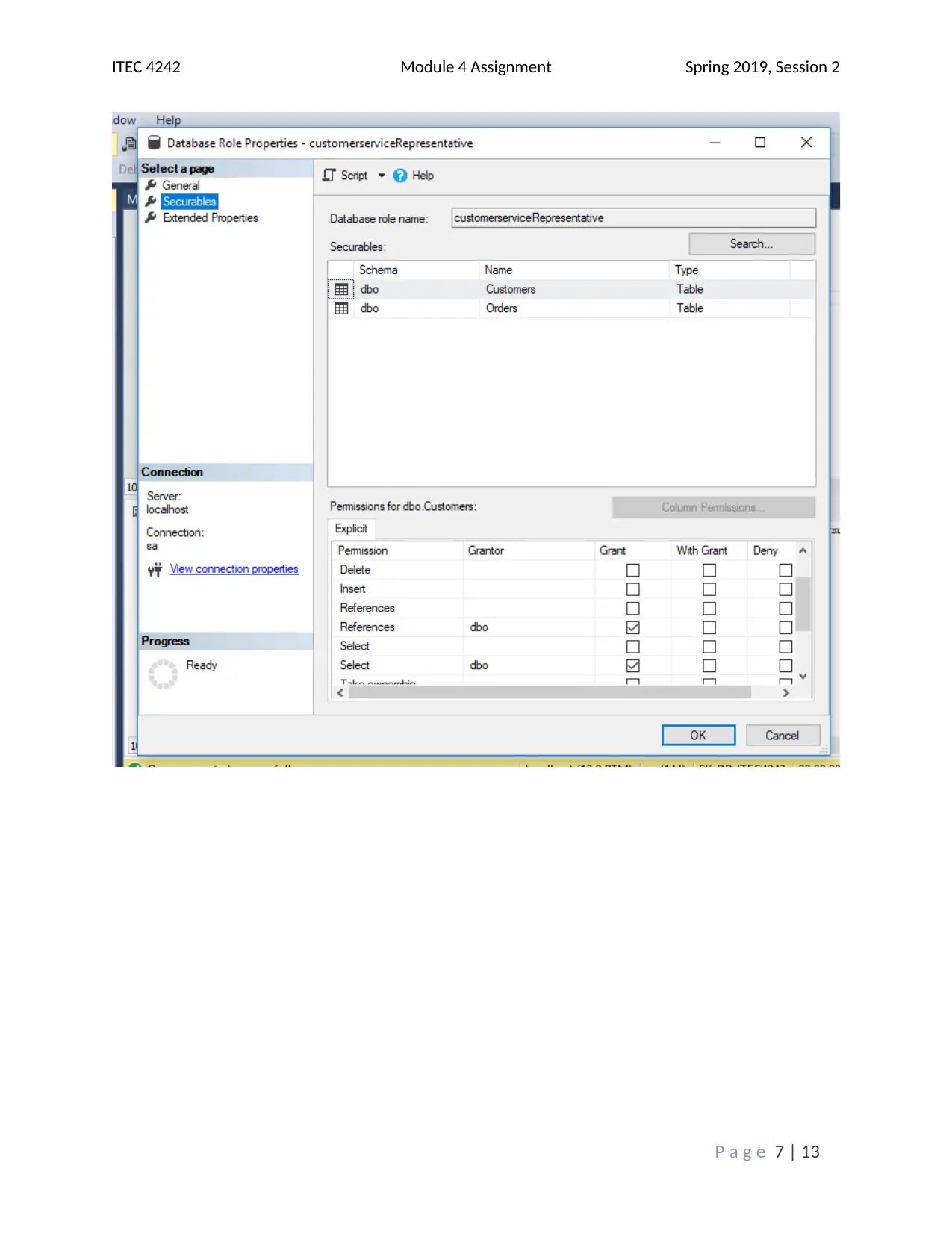
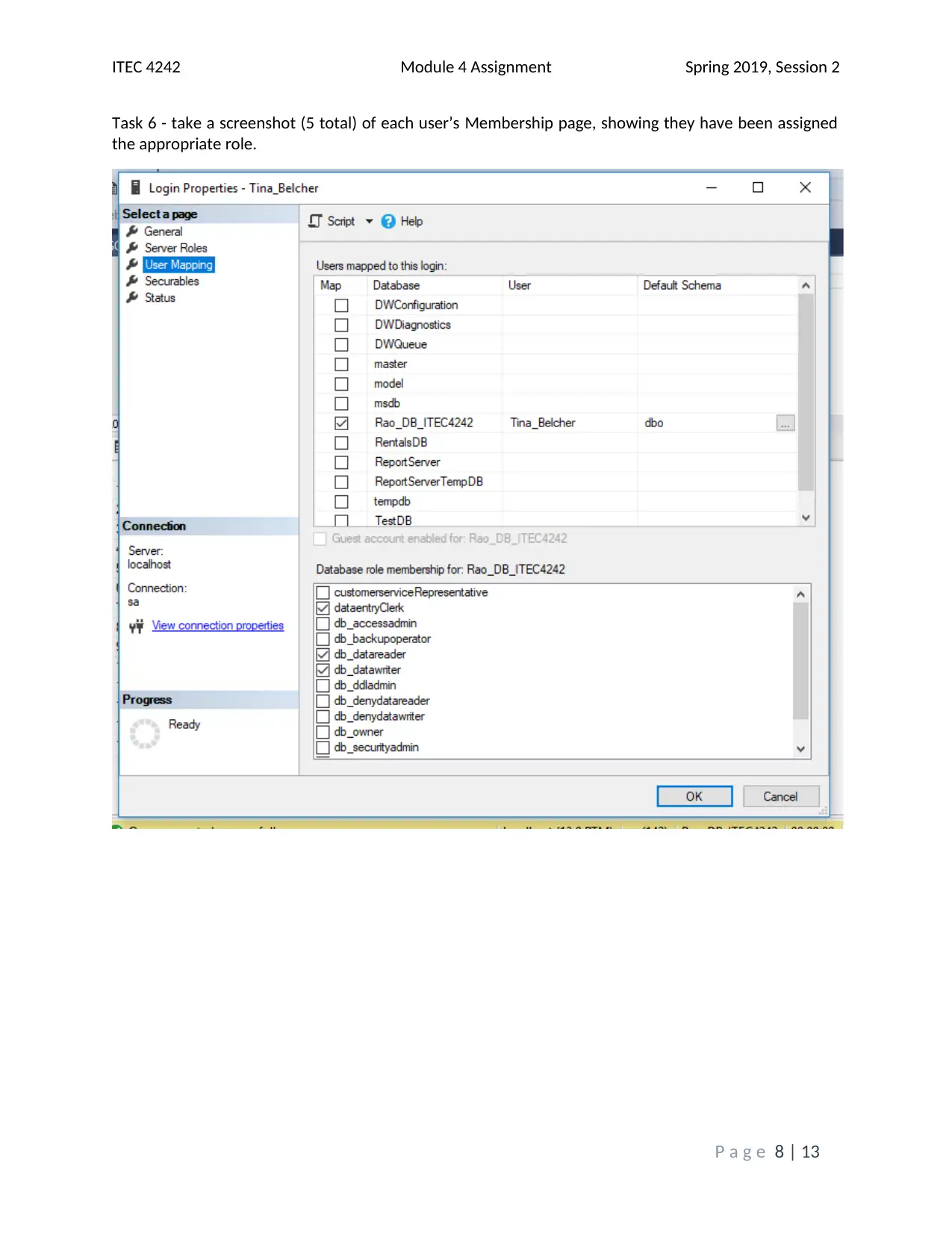
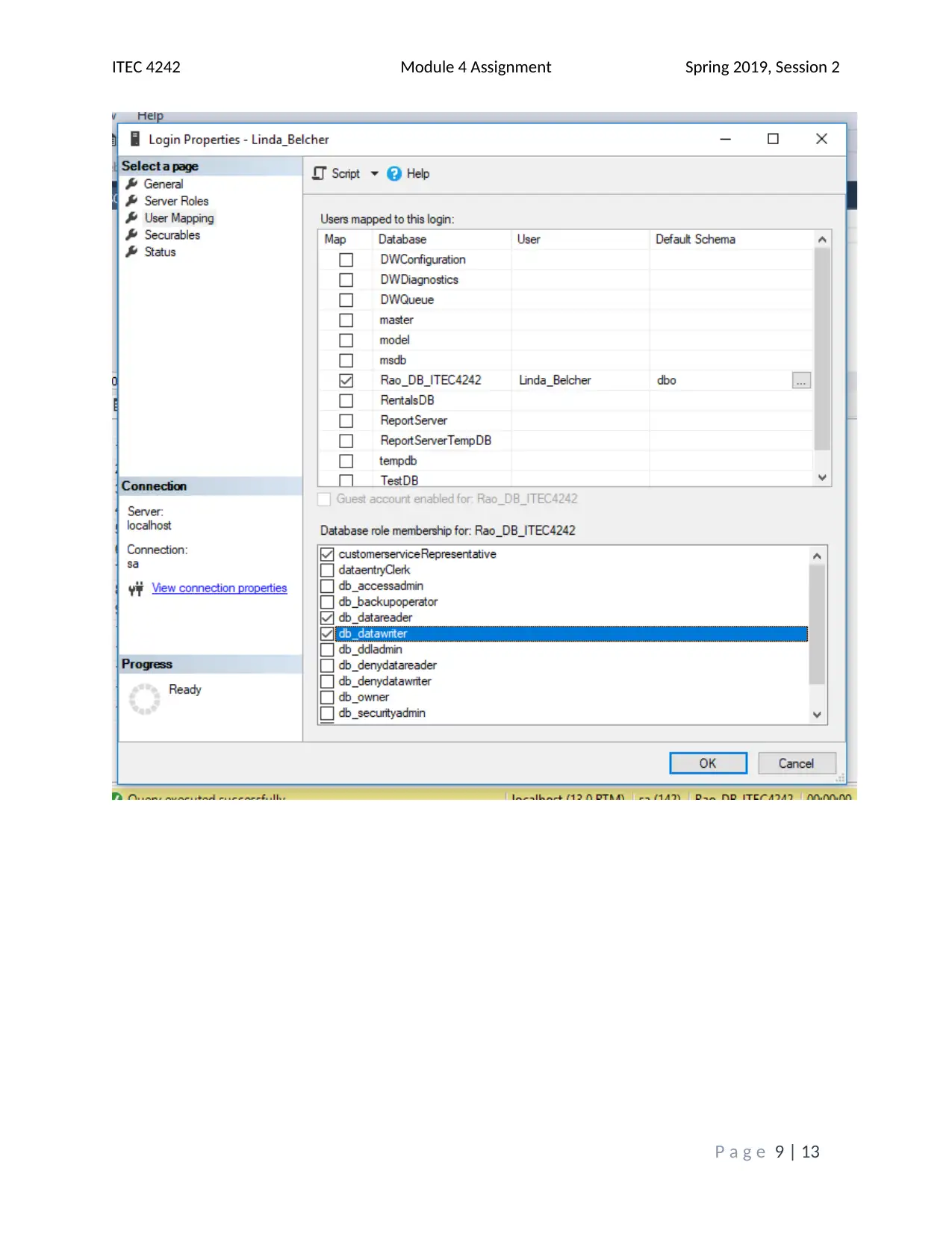
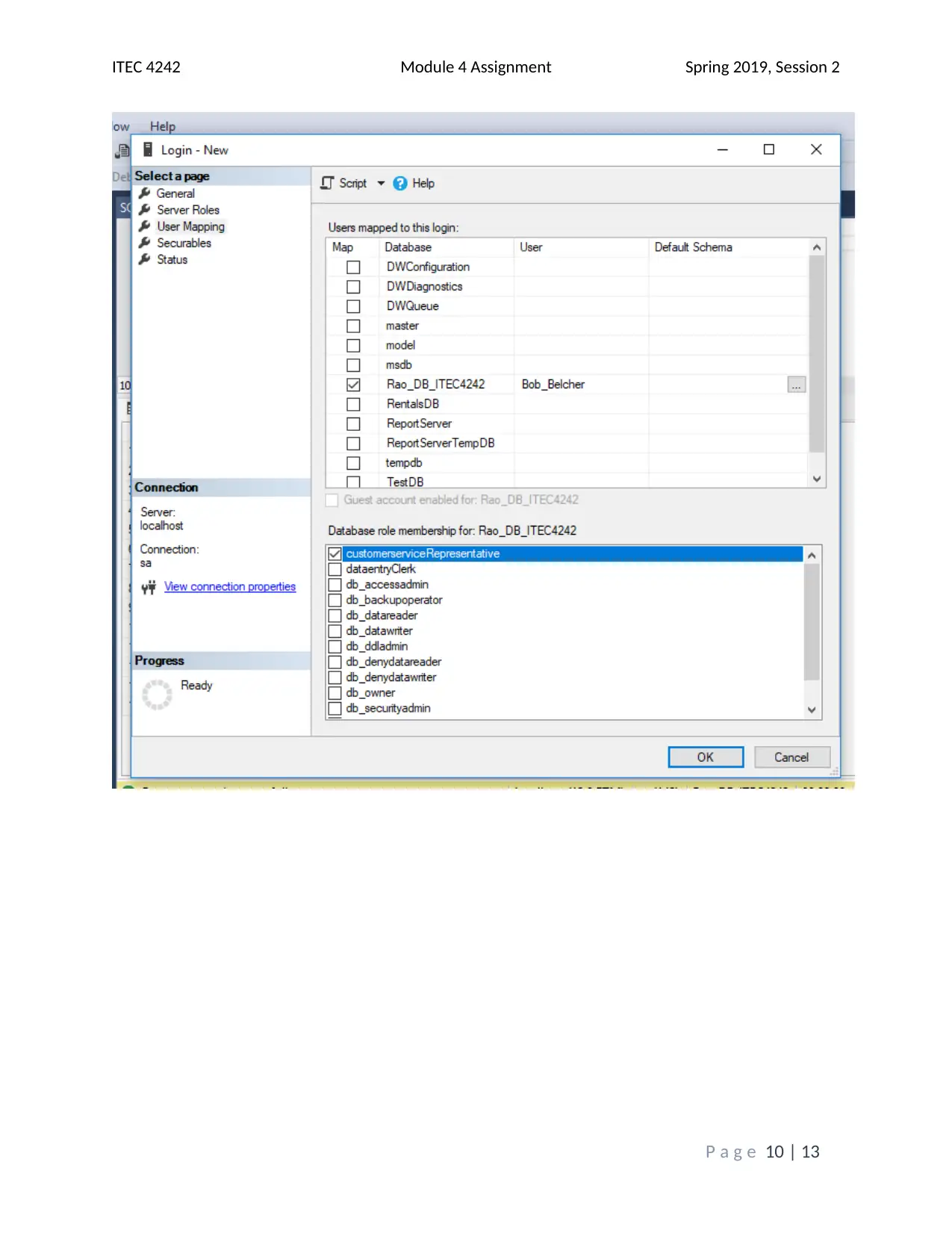
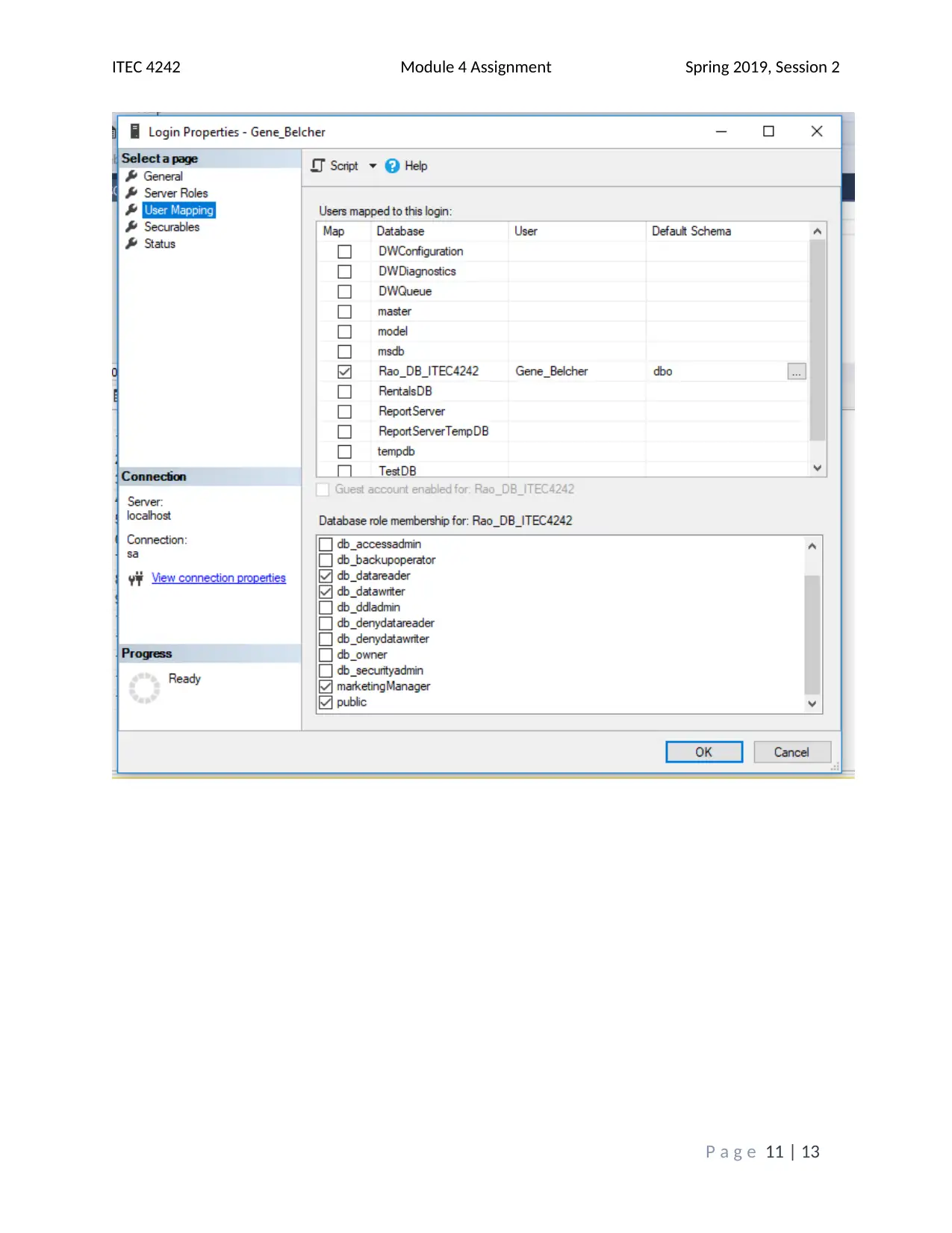
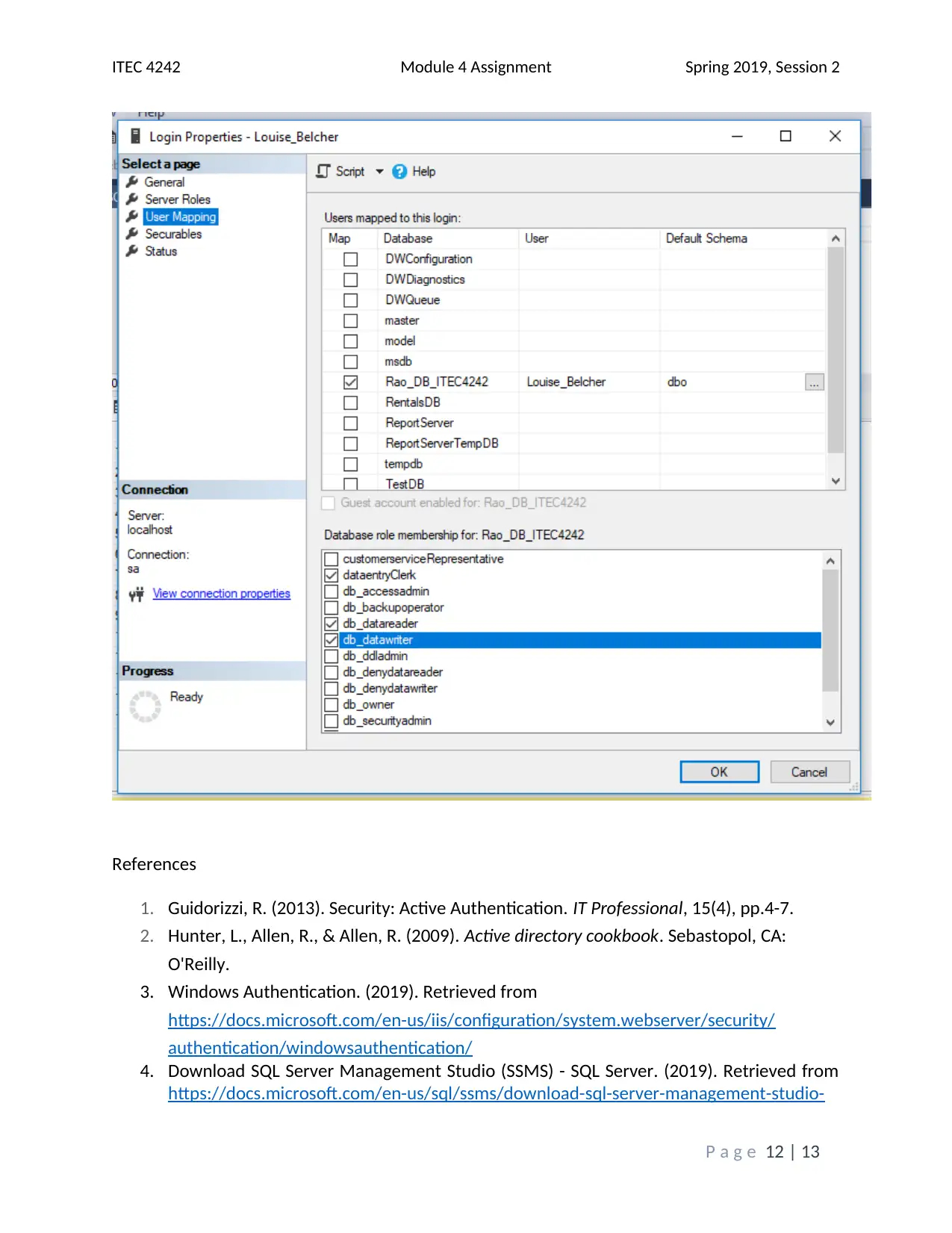
This assignment solution addresses the ITEC 4242 Module 4 requirements, focusing on database security and authentication within SQL Server 2017. The solution begins with screenshots of the Object Explorer Details view and discusses the advantages of Windows Authentication and Active Directory Authentication methods. It then covers creating a new database and tables, including screenshots of the tables folder and results of a SELECT query on the Books table. Furthermore, the solution creates charts illustrating table access and privilege levels for different roles, such as Promotions, Author, and Customer Service Representative. Screenshots of the Securables page within each role's Properties window are provided, demonstrating the assigned permissions. Finally, screenshots of each user's Membership page confirm the appropriate role assignments. The assignment incorporates screenshots to illustrate the steps taken and the outcomes achieved, and it cites relevant sources to support the analysis and findings. The assignment covers database security, authentication, and SQL Server tasks.
1 out of 13





![[object Object]](/_next/static/media/star-bottom.7253800d.svg)