ITEC647: Data Communication Assignment 1 Solution, 2019
VerifiedAdded on 2022/11/25
|11
|1133
|390
Homework Assignment
AI Summary
This document presents a comprehensive solution to a data communication assignment, addressing both subnetting and network layer concepts, as well as application layer protocols. Part 1 delves into subnetting exercises, including converting slash notations to dotted-decimal notation, calculating the maximum number of hosts for various subnets, and identifying legal and illegal netmasks. It also covers FLSM (Fixed Length Subnet Mask) and VLSM (Variable Length Subnet Mask) schemes, subnetting a given IP address range, and creating tables to show IP address allocations. Part 2 explores application layer protocols like Electronic file transfer (using FTP) and Electronic mail (using SMTP), comparing their functionalities, protocols, and transport layer protocols (TCP and TFTP). The solution explains the architectural differences (client-server vs. peer-to-peer) and provides a detailed bibliography. This assignment provides a clear and concise explanation of the concepts and is suitable for students studying data communication at the university level.

DATA COMMUNICATION
pg. 0
pg. 0
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Part 1: Subnetting and network layer
Questions 1
a. The equivalent of the following subnets are as follows.
I. /23 : 255.255.254.0
II. /11 : 255.254.0.0
III. /29 : 255.255.255.248
IV. /31 : 255.255.255.254
b. The maximum number of hosts in given subnets.
I. /19
H= 2^x
x=32-the subnet mask of the network.
32-19=13
2^13
=8192 hosts.
II. /30
32-30=2
2^2
=4 hosts
III. /23
32-23=9
2^9
=512 hosts.
pg. 1
Questions 1
a. The equivalent of the following subnets are as follows.
I. /23 : 255.255.254.0
II. /11 : 255.254.0.0
III. /29 : 255.255.255.248
IV. /31 : 255.255.255.254
b. The maximum number of hosts in given subnets.
I. /19
H= 2^x
x=32-the subnet mask of the network.
32-19=13
2^13
=8192 hosts.
II. /30
32-30=2
2^2
=4 hosts
III. /23
32-23=9
2^9
=512 hosts.
pg. 1
c. Legal and non-legal netmasks.
i. 255.255.240.0 the slash notation is /20
It is a legal IP address
ii. 255.252.255.0
Not a legal subnet mask. When written in binary it is not continuously filled.
iii. 255.192.0.0
it is a legal IP address
Notation /10
iv. 255.255.255.254
It is legal IP address the slash notation is
/31
Question 2 subnetting
a. FLSM 137.111.0.0 will be divided as below using subnet mast /19
255.255.224.0
The table shows all the IP addresses that were subnetted in order using FLSM
Facilities /entities IP address Usable host range Broadcast
Faculty of Arts 137.111.0.0 137.111.0.1 - 137.111.31.254 137.111.31.255
Macquarie
Business School
137.111.32.0 137.111.32.1 - 137.111.63.254 137.111.63.255
Faculty of human
resource
137.111.96.0 137.111.96.1 - 137.111.95.254 137.111.95.255
Faculty of
Medicine and
Health Sciences
137.111.96.0 137.111.96.1 -
137.111.127.254
137.111.127.255
Faculty of 137.111.128.0 137.111.128.1 - 137.111.159.255
pg. 2
i. 255.255.240.0 the slash notation is /20
It is a legal IP address
ii. 255.252.255.0
Not a legal subnet mask. When written in binary it is not continuously filled.
iii. 255.192.0.0
it is a legal IP address
Notation /10
iv. 255.255.255.254
It is legal IP address the slash notation is
/31
Question 2 subnetting
a. FLSM 137.111.0.0 will be divided as below using subnet mast /19
255.255.224.0
The table shows all the IP addresses that were subnetted in order using FLSM
Facilities /entities IP address Usable host range Broadcast
Faculty of Arts 137.111.0.0 137.111.0.1 - 137.111.31.254 137.111.31.255
Macquarie
Business School
137.111.32.0 137.111.32.1 - 137.111.63.254 137.111.63.255
Faculty of human
resource
137.111.96.0 137.111.96.1 - 137.111.95.254 137.111.95.255
Faculty of
Medicine and
Health Sciences
137.111.96.0 137.111.96.1 -
137.111.127.254
137.111.127.255
Faculty of 137.111.128.0 137.111.128.1 - 137.111.159.255
pg. 2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Engineering and
Science
137.111.159.254
Macuery
international
college
137.111.160.0 137.111.160.1 -
137.111.191.254
137.111.191.255
Macquarie City
Campus
137.111.192.0 137.111.192.1 -
137.111.223.254
137.111.223.255
b. Extended FLSM scheme to VLSM
Faculty of Arts
137.111.0.0/19
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.0.0 137.111.0.1 -
137.111.1.254
255.255.254.0
/23
510 137.111.1.255
2 137.111.2.0 137.111.0.2 -
137.111.3.254
255.255.254.0
/23
510 137.111.3.255
3 137.111.4.0 137.111.4.1-
137.111.4.254
255.255.255.0
/24
256 137.111.4.255
4 137.111.5.0 137.111.5.1-
137.111.5.254
255.255.255.0
/24
256 137.111.5.255
5 137.111.6.0 137.111.6.1-
137.111.7.254
255.255.254.0
/23
510 137.111.7.255
6 137.111.8.0 137.111.8.1-
137.111.9.254
255.255.254.0
/23
510 137.111.5.255
7 137.111.10.0 137.111.10.1-
137.111.11.254
255.255.254.0
/23
510 137.111.11.255
8 137.111.12.0 137.111.12.1- 255.255.255.0 256 137.111.12.255
pg. 3
Science
137.111.159.254
Macuery
international
college
137.111.160.0 137.111.160.1 -
137.111.191.254
137.111.191.255
Macquarie City
Campus
137.111.192.0 137.111.192.1 -
137.111.223.254
137.111.223.255
b. Extended FLSM scheme to VLSM
Faculty of Arts
137.111.0.0/19
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.0.0 137.111.0.1 -
137.111.1.254
255.255.254.0
/23
510 137.111.1.255
2 137.111.2.0 137.111.0.2 -
137.111.3.254
255.255.254.0
/23
510 137.111.3.255
3 137.111.4.0 137.111.4.1-
137.111.4.254
255.255.255.0
/24
256 137.111.4.255
4 137.111.5.0 137.111.5.1-
137.111.5.254
255.255.255.0
/24
256 137.111.5.255
5 137.111.6.0 137.111.6.1-
137.111.7.254
255.255.254.0
/23
510 137.111.7.255
6 137.111.8.0 137.111.8.1-
137.111.9.254
255.255.254.0
/23
510 137.111.5.255
7 137.111.10.0 137.111.10.1-
137.111.11.254
255.255.254.0
/23
510 137.111.11.255
8 137.111.12.0 137.111.12.1- 255.255.255.0 256 137.111.12.255
pg. 3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
137.111.12.254 /24
9 137.111.13.0 137.111.13.1-
137.111.13.254
255.255.255.0
/24
256 137.111.13.255
10 137.111.14.0 137.111.14.1 -
137.111.14.126
255.255.255.128
/25
128 137.111.14.126
11 137.111.14.128 137.111.14.129
-
137.111.14.254
255.255.255.128
/25
128 137.111.14.255
12 137.111.15.0 137.111.15.1 -
137.111.15.255
255.255.255.0
/24
256 137.111.15.255
13 137.111.16.0 137.111.16.1 -
137.111.16.255
c 256
Business school
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.32.0 137.111.32.1 -
137.111.32.30
255.255.255.224
/27
32 137.111.32.31
2 137.111.32.0 137.111.32.33 -
137.111.32.62
255.255.255.224
/27
32 137.111.32.63
3 137.111.33.0 137.111.33.1 -
137.111.33.255
255.255.255.0
/24
256 137.111.33.255
4 137.111.34.0 137.111.34.1 -
137.111.34.255
255.255.255.0
/24
256 137.111.34.255
5 137.111.35.0 137.111.35.1 -
137.111.35.255
255.255.255.0
/24
256 137.111.35.255
6 137.111.36.0 137.111.36.1 -
137.111.36.255
255.255.255.0
/24
256 137.111.36.255
Human Resource
pg. 4
9 137.111.13.0 137.111.13.1-
137.111.13.254
255.255.255.0
/24
256 137.111.13.255
10 137.111.14.0 137.111.14.1 -
137.111.14.126
255.255.255.128
/25
128 137.111.14.126
11 137.111.14.128 137.111.14.129
-
137.111.14.254
255.255.255.128
/25
128 137.111.14.255
12 137.111.15.0 137.111.15.1 -
137.111.15.255
255.255.255.0
/24
256 137.111.15.255
13 137.111.16.0 137.111.16.1 -
137.111.16.255
c 256
Business school
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.32.0 137.111.32.1 -
137.111.32.30
255.255.255.224
/27
32 137.111.32.31
2 137.111.32.0 137.111.32.33 -
137.111.32.62
255.255.255.224
/27
32 137.111.32.63
3 137.111.33.0 137.111.33.1 -
137.111.33.255
255.255.255.0
/24
256 137.111.33.255
4 137.111.34.0 137.111.34.1 -
137.111.34.255
255.255.255.0
/24
256 137.111.34.255
5 137.111.35.0 137.111.35.1 -
137.111.35.255
255.255.255.0
/24
256 137.111.35.255
6 137.111.36.0 137.111.36.1 -
137.111.36.255
255.255.255.0
/24
256 137.111.36.255
Human Resource
pg. 4
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.96.0 137.111.96.1 -
137.111.96.30
255.255.255.224
/27
32 137.111.96.31
2 137.111.96.33 137.111.96.33 -
137.111.96.96
255.255.255.224
/27
32 137.111.96.65
3 137.111.65.0 137.111.65.1 -
137.111.65.255
255.255.255.0
/24
256 137.111.65.255
4 137.111.65.0 137.111.65.1 -
137.111.65.126
255.255.255.128
/25
128 137.111.65.126
pg. 5
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.96.0 137.111.96.1 -
137.111.96.30
255.255.255.224
/27
32 137.111.96.31
2 137.111.96.33 137.111.96.33 -
137.111.96.96
255.255.255.224
/27
32 137.111.96.65
3 137.111.65.0 137.111.65.1 -
137.111.65.255
255.255.255.0
/24
256 137.111.65.255
4 137.111.65.0 137.111.65.1 -
137.111.65.126
255.255.255.128
/25
128 137.111.65.126
pg. 5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
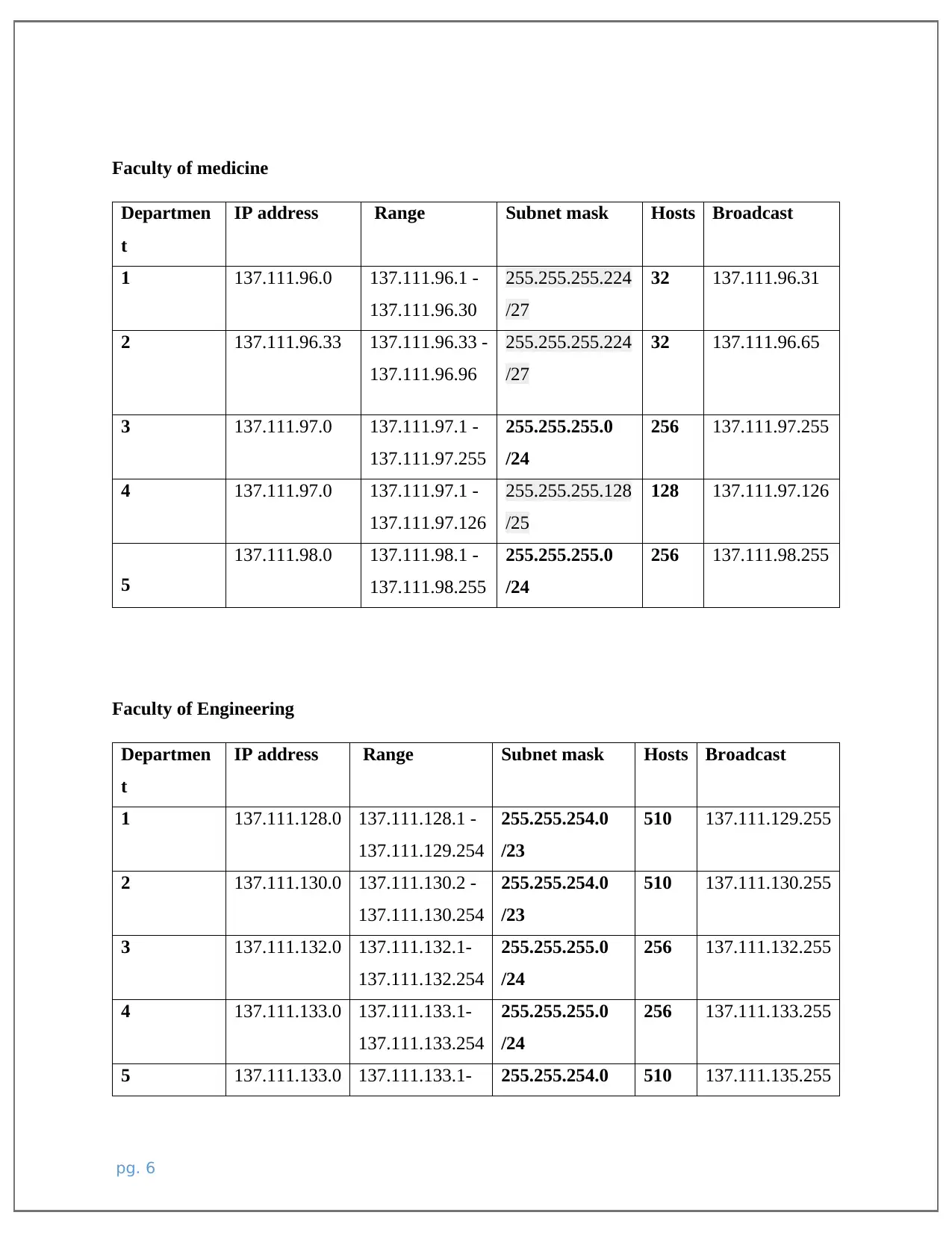
Faculty of medicine
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.96.0 137.111.96.1 -
137.111.96.30
255.255.255.224
/27
32 137.111.96.31
2 137.111.96.33 137.111.96.33 -
137.111.96.96
255.255.255.224
/27
32 137.111.96.65
3 137.111.97.0 137.111.97.1 -
137.111.97.255
255.255.255.0
/24
256 137.111.97.255
4 137.111.97.0 137.111.97.1 -
137.111.97.126
255.255.255.128
/25
128 137.111.97.126
5
137.111.98.0 137.111.98.1 -
137.111.98.255
255.255.255.0
/24
256 137.111.98.255
Faculty of Engineering
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.128.0 137.111.128.1 -
137.111.129.254
255.255.254.0
/23
510 137.111.129.255
2 137.111.130.0 137.111.130.2 -
137.111.130.254
255.255.254.0
/23
510 137.111.130.255
3 137.111.132.0 137.111.132.1-
137.111.132.254
255.255.255.0
/24
256 137.111.132.255
4 137.111.133.0 137.111.133.1-
137.111.133.254
255.255.255.0
/24
256 137.111.133.255
5 137.111.133.0 137.111.133.1- 255.255.254.0 510 137.111.135.255
pg. 6
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.96.0 137.111.96.1 -
137.111.96.30
255.255.255.224
/27
32 137.111.96.31
2 137.111.96.33 137.111.96.33 -
137.111.96.96
255.255.255.224
/27
32 137.111.96.65
3 137.111.97.0 137.111.97.1 -
137.111.97.255
255.255.255.0
/24
256 137.111.97.255
4 137.111.97.0 137.111.97.1 -
137.111.97.126
255.255.255.128
/25
128 137.111.97.126
5
137.111.98.0 137.111.98.1 -
137.111.98.255
255.255.255.0
/24
256 137.111.98.255
Faculty of Engineering
Departmen
t
IP address Range Subnet mask Hosts Broadcast
1 137.111.128.0 137.111.128.1 -
137.111.129.254
255.255.254.0
/23
510 137.111.129.255
2 137.111.130.0 137.111.130.2 -
137.111.130.254
255.255.254.0
/23
510 137.111.130.255
3 137.111.132.0 137.111.132.1-
137.111.132.254
255.255.255.0
/24
256 137.111.132.255
4 137.111.133.0 137.111.133.1-
137.111.133.254
255.255.255.0
/24
256 137.111.133.255
5 137.111.133.0 137.111.133.1- 255.255.254.0 510 137.111.135.255
pg. 6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
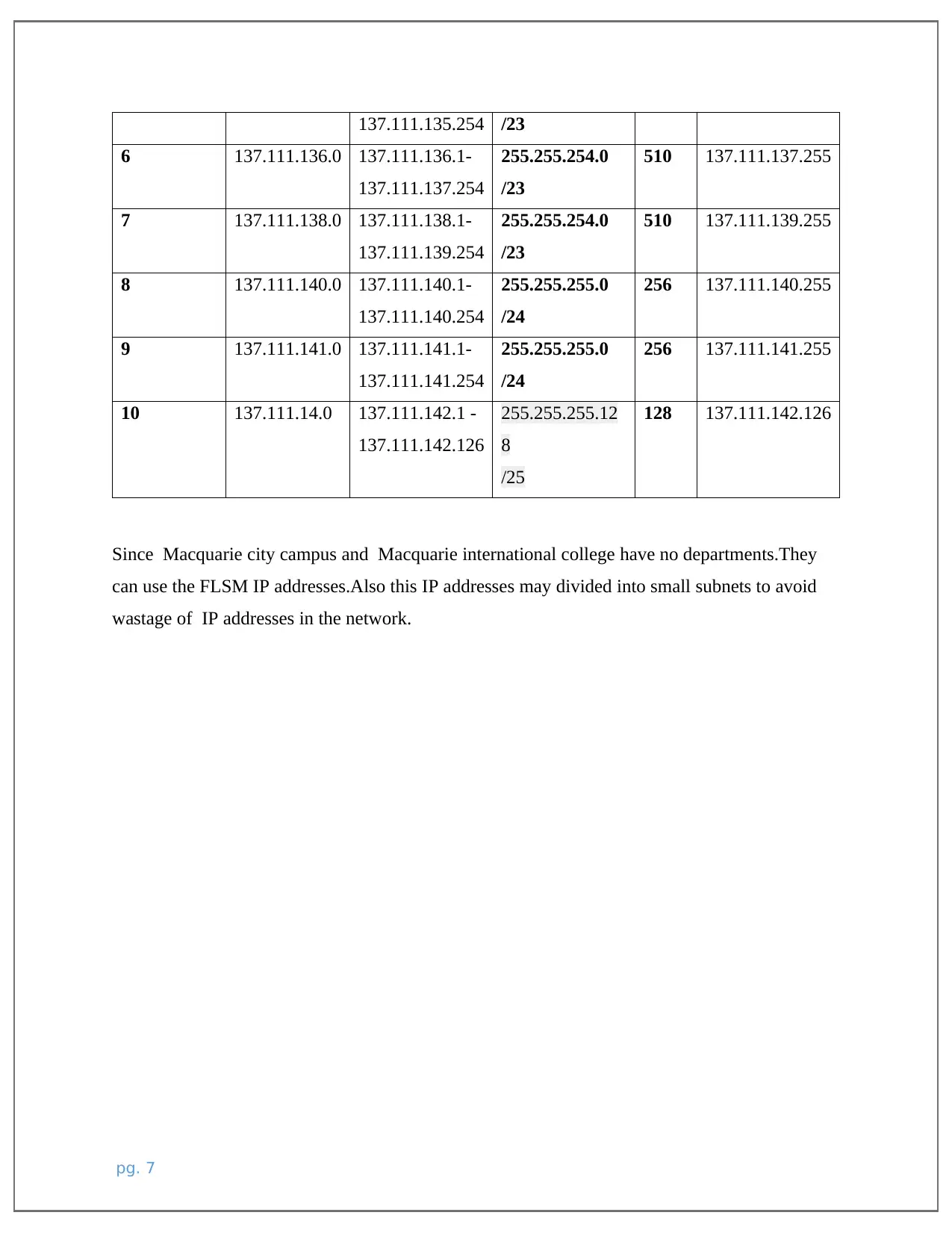
137.111.135.254 /23
6 137.111.136.0 137.111.136.1-
137.111.137.254
255.255.254.0
/23
510 137.111.137.255
7 137.111.138.0 137.111.138.1-
137.111.139.254
255.255.254.0
/23
510 137.111.139.255
8 137.111.140.0 137.111.140.1-
137.111.140.254
255.255.255.0
/24
256 137.111.140.255
9 137.111.141.0 137.111.141.1-
137.111.141.254
255.255.255.0
/24
256 137.111.141.255
10 137.111.14.0 137.111.142.1 -
137.111.142.126
255.255.255.12
8
/25
128 137.111.142.126
Since Macquarie city campus and Macquarie international college have no departments.They
can use the FLSM IP addresses.Also this IP addresses may divided into small subnets to avoid
wastage of IP addresses in the network.
pg. 7
6 137.111.136.0 137.111.136.1-
137.111.137.254
255.255.254.0
/23
510 137.111.137.255
7 137.111.138.0 137.111.138.1-
137.111.139.254
255.255.254.0
/23
510 137.111.139.255
8 137.111.140.0 137.111.140.1-
137.111.140.254
255.255.255.0
/24
256 137.111.140.255
9 137.111.141.0 137.111.141.1-
137.111.141.254
255.255.255.0
/24
256 137.111.141.255
10 137.111.14.0 137.111.142.1 -
137.111.142.126
255.255.255.12
8
/25
128 137.111.142.126
Since Macquarie city campus and Macquarie international college have no departments.They
can use the FLSM IP addresses.Also this IP addresses may divided into small subnets to avoid
wastage of IP addresses in the network.
pg. 7

Part 2: Applications, layering, protocols
From the list, I have chosen Electronic file transfer and Electronic mail application to use them
in
answering the questions.
a) Electronic file transfer application uses a file transfer protocol as which is a client-server
protocol as the application-layer protocol. It is used in the transfer or exchange of files with
the host computer. Electronic mail uses a simple mail transfer protocol as its application-layer
protocol. For proper functionality, the mail message must be properly formatted and simple
mail transfer protocol processes must be run on both the client and the server.
b) The simple mail transfer protocol in Electronic mail protocol transfers mails efficiently and
reliably and its message formats require a message header and body. The message body
may contain any amount of text but the header contains properly formatted recipients’
and senders’ email addresses.
File transfer protocol in Electronic file transfer supports authentication with user names and
passwords but anonymous file transfer protocol allows users to access files from the
internet without user identification. It is also a standard used to move or transfer files from
one computer to another using IP networks
c) Electronic mail uses Transmission control protocol (TCP) as its transport layer protocol which
is used to interconnect network devices on the internet. Electronic file transfer uses Trivial
file transfer protocol.
d) The transmission control protocol is applied in Electronic mail application because it is
designed
pg. 8
From the list, I have chosen Electronic file transfer and Electronic mail application to use them
in
answering the questions.
a) Electronic file transfer application uses a file transfer protocol as which is a client-server
protocol as the application-layer protocol. It is used in the transfer or exchange of files with
the host computer. Electronic mail uses a simple mail transfer protocol as its application-layer
protocol. For proper functionality, the mail message must be properly formatted and simple
mail transfer protocol processes must be run on both the client and the server.
b) The simple mail transfer protocol in Electronic mail protocol transfers mails efficiently and
reliably and its message formats require a message header and body. The message body
may contain any amount of text but the header contains properly formatted recipients’
and senders’ email addresses.
File transfer protocol in Electronic file transfer supports authentication with user names and
passwords but anonymous file transfer protocol allows users to access files from the
internet without user identification. It is also a standard used to move or transfer files from
one computer to another using IP networks
c) Electronic mail uses Transmission control protocol (TCP) as its transport layer protocol which
is used to interconnect network devices on the internet. Electronic file transfer uses Trivial
file transfer protocol.
d) The transmission control protocol is applied in Electronic mail application because it is
designed
pg. 8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

to make networks reliable and supports recovery in case of any device failure on the
network and it also requires little central management.
Trivial file transfer protocol is applied in Electronic file transfer application as it does not
require a lot of memory to load and also uses application layer recovery by embedding small
header between the User Diagram Protocol header and the data.
e) Transmission control protocol uses peer-to-peer architecture while Trivial file transfer
protocol uses client-server architecture.
f) Client-server architecture is applied in Electronic file transfer application because it allows
sharing of resources by devices connected on a network. The server hosts and manages
resources and the clients access the resources through the connection to a central server.
Electronic mail application applies peer-to-peer architecture in its functionality since each
workstation or network device has the same capabilities as the other. Peers are equally
privileged or have equal participation in the application.
pg. 9
network and it also requires little central management.
Trivial file transfer protocol is applied in Electronic file transfer application as it does not
require a lot of memory to load and also uses application layer recovery by embedding small
header between the User Diagram Protocol header and the data.
e) Transmission control protocol uses peer-to-peer architecture while Trivial file transfer
protocol uses client-server architecture.
f) Client-server architecture is applied in Electronic file transfer application because it allows
sharing of resources by devices connected on a network. The server hosts and manages
resources and the clients access the resources through the connection to a central server.
Electronic mail application applies peer-to-peer architecture in its functionality since each
workstation or network device has the same capabilities as the other. Peers are equally
privileged or have equal participation in the application.
pg. 9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Bibliography
Chamberlain, S., Giles, H. and Lientz, A., Experian Marketing Solutions Inc, 2011. Service for
mapping IP addresses to user segments. U.S. Patent 7,996,521.
Raphel, J., Kailash, K. and Devarajan, S., Zscaler Inc, 2012. Handling overlapping IP addresses
in a multi-tenant architecture. U.S. Patent 8,259,571.
pg. 10
Chamberlain, S., Giles, H. and Lientz, A., Experian Marketing Solutions Inc, 2011. Service for
mapping IP addresses to user segments. U.S. Patent 7,996,521.
Raphel, J., Kailash, K. and Devarajan, S., Zscaler Inc, 2012. Handling overlapping IP addresses
in a multi-tenant architecture. U.S. Patent 8,259,571.
pg. 10
1 out of 11
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




