Computer Science Assignment: Java, OOP, and Social Networks
VerifiedAdded on 2020/07/22
|15
|4930
|206
Homework Assignment
AI Summary
This assignment encompasses several key areas of computer science. Task 1 involves writing Java methods to calculate the average of five numbers and count words in a string. Task 2 requires creating a class diagram representing relationships between Employee, Department, and Company tables, and Project tables. Task 3 delves into object-oriented programming (OOP) principles, critically evaluating the concepts of objects, classes, and methods. Finally, Task 4 examines a social networking site, analyzing its architecture for protecting user privacy and addressing related threats such as information disclosure. This assignment provides a comprehensive overview of programming fundamentals, OOP, and the challenges of maintaining privacy in social networking environments.

Programming
Task 1
a) Write a Java method to compute the average of five numbers
import java.util.Scanner;
public class Avg5 {
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
System.out.print("Input first number: ");
int num1 = in.nextInt();
System.out.print("Input second number: ");
int num2 = in.nextInt();
System.out.print("Input third number: ");
int num3 = in.nextInt();
System.out.print("Input fourth number: ");
int num4 = in.nextInt();
System.out.print("Enter fifth number: ");
int num5 = in.nextInt();
System.out.println("Average of five numbers is: " +
(num1 + num2 + num3 + num4 + num5) / 5);
}
}
Task 1
a) Write a Java method to compute the average of five numbers
import java.util.Scanner;
public class Avg5 {
public static void main(String[] args) {
Scanner in = new Scanner(System.in);
System.out.print("Input first number: ");
int num1 = in.nextInt();
System.out.print("Input second number: ");
int num2 = in.nextInt();
System.out.print("Input third number: ");
int num3 = in.nextInt();
System.out.print("Input fourth number: ");
int num4 = in.nextInt();
System.out.print("Enter fifth number: ");
int num5 = in.nextInt();
System.out.println("Average of five numbers is: " +
(num1 + num2 + num3 + num4 + num5) / 5);
}
}
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) Write a Java method to count all words in a string.
import java.util.Scanner;
public class wordcount {
public static void main(String[] args)
{
Scanner in = new Scanner(System.in);
System.out.print("Input the string: ");
String str = in.nextLine();
System.out.print("Number of words in the string: " +
count_Words(str)+"\n");
}
public static int count_Words(String str)
{
int count = 0;
if (!(" ".equals(str.substring(0, 1))) || !("
".equals(str.substring(str.length() - 1))))
{
for (int i = 0; i < str.length(); i++)
{
if (str.charAt(i) == ' ')
{
count++;
}
}
count = count + 1;
}
return count; // returns 0 if string starts or ends
with space " ".
}
}
import java.util.Scanner;
public class wordcount {
public static void main(String[] args)
{
Scanner in = new Scanner(System.in);
System.out.print("Input the string: ");
String str = in.nextLine();
System.out.print("Number of words in the string: " +
count_Words(str)+"\n");
}
public static int count_Words(String str)
{
int count = 0;
if (!(" ".equals(str.substring(0, 1))) || !("
".equals(str.substring(str.length() - 1))))
{
for (int i = 0; i < str.length(); i++)
{
if (str.charAt(i) == ' ')
{
count++;
}
}
count = count + 1;
}
return count; // returns 0 if string starts or ends
with space " ".
}
}
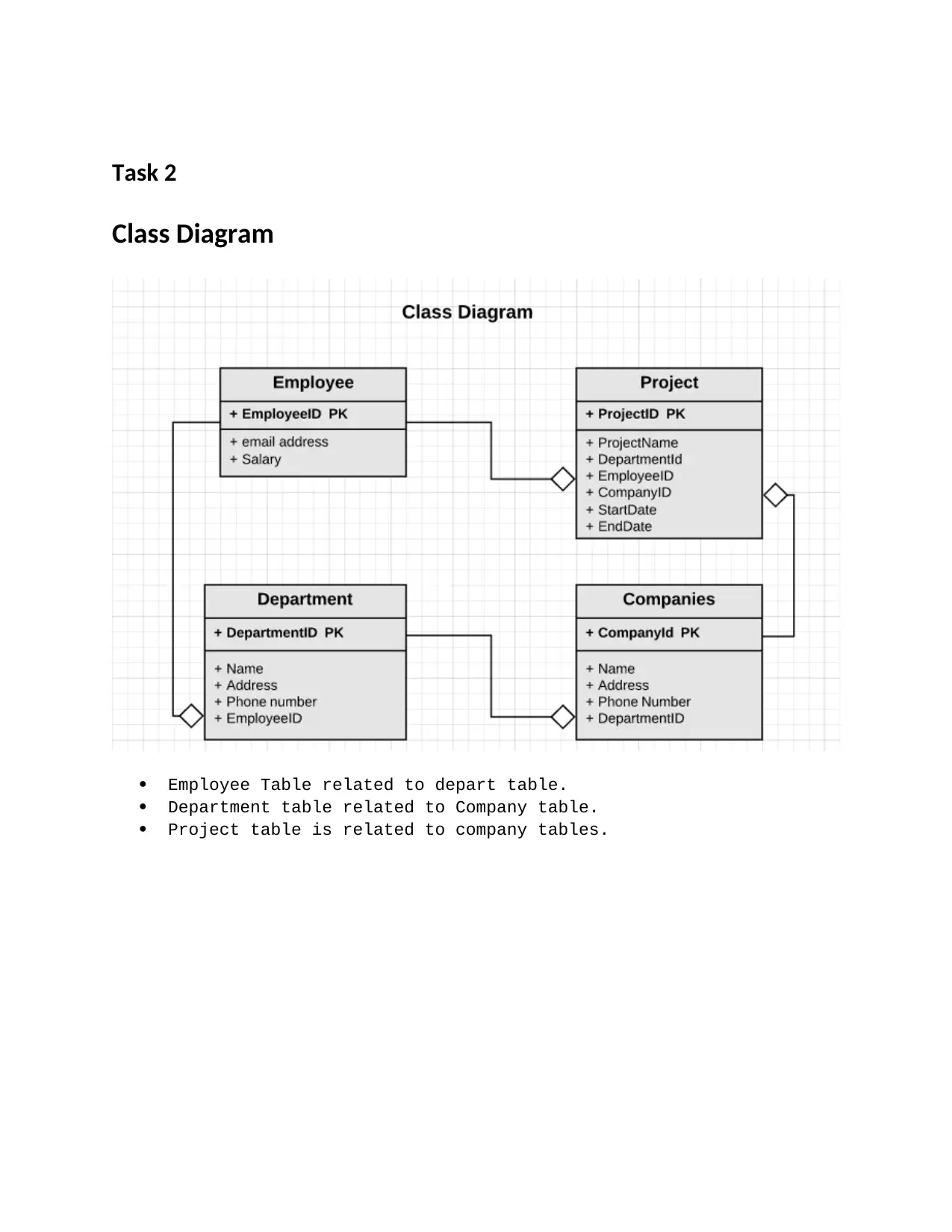
Task 2
Class Diagram
Employee Table related to depart table.
Department table related to Company table.
Project table is related to company tables.
Class Diagram
Employee Table related to depart table.
Department table related to Company table.
Project table is related to company tables.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Task 3
a) In a maximum of 500 words, critically evaluate the principles of object oriented programming.
Today, object oriented programming will probably be the predominant programming paradigm as well
as Java is completely subject targeted. In addition, Java has become the various used language amongst
THAT service providers. Therefore, scholars often learn Java and subject oriented programming (OOP)
actually introductory courses. This permits a perfect basis for a “later introduction to other paradigms
which includes logical or useful coding. Moreover, OOP helps introducing students to ideas very much
like specification construction, resistant and also.
These techniques start by showing items, interfaces, classes and also features from the beginning, e. l.
the Outside-In teaching way of OOP based on the programming vocab Eiffel. Problem Statement:
Irrespective of several lecturers having simply by present used the Outside-In teaching approach in their
lessons, little research evidence upon its outcomes dominates. A lot of authors looked simply by the
scheduled program action connected with involved students, nevertheless influence on learning effects
as well as enthusiasm and fascination has not been recently researched to date. Research Objective:
Educating OO rules to apprentices is usually a great important task of program engineering education.
Consequently , with this paper the feasibility as well as effects of employing Outside-In educating for
coaching OOP in a matter of university-level initial courses making use of Java will be empirically looked
at. In particular, the aim was to realize its influence on learning positive components in addition, on
interest and ideas in the participants. Context: We all considered Outside-In teaching in suite an suite in
two opening classes for computer scientific exploration and OOP (Bachelor level, 1st year) at a set of
German universities in the winter period 2012/13. The courses have already been Programming and
Software Development (PSD) at the University associated with Stuttgart (Stuttgart) and Development
Technique from the study course “Information Management Automotive” (IMA) at the Institution of
Modern developments Neu-Ulm (Ulm).
The major challenge was the replacement of Eiffel just by Java. Eiffel is more patristic in its object-
oriented constructs compared to Java. For example, for Caffeine an early introduction of long term
methods is necessary because the strategy is executed with the everlasting key method. The basic
principle of carrying out a program in Eiffel will probably be considerably easier. Compared to Eiffel, Java
lacks an area support for contracts, added tools have to be applied as a result. Regarding the scope, the
two classes at Ulm and Stuttgart distinctly are different. Programming as well as Computer programs
Development (PSD) with Stuttgart consists of four several hours lecture and two occasions tutorials with
teaching colleagues per week. Programming Strategy inside Ulm consists of two a large number of hours
lecture and two period lecturer-guided tutorials. Furthermore, only two additional several hours of
encouraged tutorial each week are offered. Several topics just like the setup as well as the functional
rule of a personal computer system or perhaps data structures are generally products of separate
address classes at Ulm. That is why, these types of units are not included right here. Thus, compared to
Ulm, for Stuttgart much more issues will be examined during a session. PSD at Stuttgart resembles a
great introduction to computer engineering.
a) In a maximum of 500 words, critically evaluate the principles of object oriented programming.
Today, object oriented programming will probably be the predominant programming paradigm as well
as Java is completely subject targeted. In addition, Java has become the various used language amongst
THAT service providers. Therefore, scholars often learn Java and subject oriented programming (OOP)
actually introductory courses. This permits a perfect basis for a “later introduction to other paradigms
which includes logical or useful coding. Moreover, OOP helps introducing students to ideas very much
like specification construction, resistant and also.
These techniques start by showing items, interfaces, classes and also features from the beginning, e. l.
the Outside-In teaching way of OOP based on the programming vocab Eiffel. Problem Statement:
Irrespective of several lecturers having simply by present used the Outside-In teaching approach in their
lessons, little research evidence upon its outcomes dominates. A lot of authors looked simply by the
scheduled program action connected with involved students, nevertheless influence on learning effects
as well as enthusiasm and fascination has not been recently researched to date. Research Objective:
Educating OO rules to apprentices is usually a great important task of program engineering education.
Consequently , with this paper the feasibility as well as effects of employing Outside-In educating for
coaching OOP in a matter of university-level initial courses making use of Java will be empirically looked
at. In particular, the aim was to realize its influence on learning positive components in addition, on
interest and ideas in the participants. Context: We all considered Outside-In teaching in suite an suite in
two opening classes for computer scientific exploration and OOP (Bachelor level, 1st year) at a set of
German universities in the winter period 2012/13. The courses have already been Programming and
Software Development (PSD) at the University associated with Stuttgart (Stuttgart) and Development
Technique from the study course “Information Management Automotive” (IMA) at the Institution of
Modern developments Neu-Ulm (Ulm).
The major challenge was the replacement of Eiffel just by Java. Eiffel is more patristic in its object-
oriented constructs compared to Java. For example, for Caffeine an early introduction of long term
methods is necessary because the strategy is executed with the everlasting key method. The basic
principle of carrying out a program in Eiffel will probably be considerably easier. Compared to Eiffel, Java
lacks an area support for contracts, added tools have to be applied as a result. Regarding the scope, the
two classes at Ulm and Stuttgart distinctly are different. Programming as well as Computer programs
Development (PSD) with Stuttgart consists of four several hours lecture and two occasions tutorials with
teaching colleagues per week. Programming Strategy inside Ulm consists of two a large number of hours
lecture and two period lecturer-guided tutorials. Furthermore, only two additional several hours of
encouraged tutorial each week are offered. Several topics just like the setup as well as the functional
rule of a personal computer system or perhaps data structures are generally products of separate
address classes at Ulm. That is why, these types of units are not included right here. Thus, compared to
Ulm, for Stuttgart much more issues will be examined during a session. PSD at Stuttgart resembles a
great introduction to computer engineering.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

b) In clear terms, explain your understanding of each of the following object-orientated programming
concepts:
i) Objects
An object is a component of software that knows how to perform particular actions and how to
work together to elements of the program. Objects will be the basic units of object-oriented
programming. A simple example of a subject would be a person. Logically, you will anticipate a
person to get a true name. This would be deemed a property of the person. You might count on
a person to do something, such as walking as well as driving. This would be considered a
procedure for the person.
ii) Classes
A class is known as a blueprint of an object. You can imagine} a class as a thought, as well as the
object is the embodiment of the concept. You need to have a class just before an object can be
created simply by you. So, let's say you wish to use a person in your software. You want to be
ready to describe anybody and have the person do something. A category called 'person' would
offer a blueprint for what a person looks like and how person can do. To genuinely use a person
within your program, you need to create a subject. The person is used by you class to create an
object from the type 'person. ‘Anyone can demonstrate this person and have that do something.
iii) Methods
A method in object-oriented programming is a strategy associated with a class. A method
becomes the behavior of the objects which can be created from the class. Another way to
declare this is that a method is a task that an excellent object has the ability to perform. The
association amongst method and class is known as binding. Consider the sort of an object of the
type 'person, ' created using the person course. Methods associated with this course could
consist of things like taking walks and driving. Strategies are occasionally confused with
functions, but they are specific.
concepts:
i) Objects
An object is a component of software that knows how to perform particular actions and how to
work together to elements of the program. Objects will be the basic units of object-oriented
programming. A simple example of a subject would be a person. Logically, you will anticipate a
person to get a true name. This would be deemed a property of the person. You might count on
a person to do something, such as walking as well as driving. This would be considered a
procedure for the person.
ii) Classes
A class is known as a blueprint of an object. You can imagine} a class as a thought, as well as the
object is the embodiment of the concept. You need to have a class just before an object can be
created simply by you. So, let's say you wish to use a person in your software. You want to be
ready to describe anybody and have the person do something. A category called 'person' would
offer a blueprint for what a person looks like and how person can do. To genuinely use a person
within your program, you need to create a subject. The person is used by you class to create an
object from the type 'person. ‘Anyone can demonstrate this person and have that do something.
iii) Methods
A method in object-oriented programming is a strategy associated with a class. A method
becomes the behavior of the objects which can be created from the class. Another way to
declare this is that a method is a task that an excellent object has the ability to perform. The
association amongst method and class is known as binding. Consider the sort of an object of the
type 'person, ' created using the person course. Methods associated with this course could
consist of things like taking walks and driving. Strategies are occasionally confused with
functions, but they are specific.

Task 4
A social networking site
Abstract-Social networking sites, such as Zynga or Facebook or myspace, Flickr and Facebook, will be
elevating more and more status between Internet users often. As users are doing your best with this
new design of multi-level marketing usually, personal privacy concerns are also developing raising public
attention because of reviews about personal privacy minimizes about social multilevel marketing sites.
All of us advise a fantastic architecture that defends buyer privacy by using an on the internet
community site by simply shielding some sort of user’s personal information from the web-site and from
several other users that have been certainly not explicitly authorized throughout the user. At the same
time, Face The distribution preserves usability from your site’s services seamlessly. Face Keep achieves
these goals by just enabling fake information towards the Myspace and Facebook blog and by
possessing sensitized info in encrypted form on the separate server. Most of us integrated our solution
as a standard Firefox internet browser extension to your Facebook platform. Our trial offers show that
our remedy with success conceals a user’s info that is personal together, while allowing the consumer in
addition to her friends to learn Facebook pages and services a lot of.
A social networking site
Abstract-Social networking sites, such as Zynga or Facebook or myspace, Flickr and Facebook, will be
elevating more and more status between Internet users often. As users are doing your best with this
new design of multi-level marketing usually, personal privacy concerns are also developing raising public
attention because of reviews about personal privacy minimizes about social multilevel marketing sites.
All of us advise a fantastic architecture that defends buyer privacy by using an on the internet
community site by simply shielding some sort of user’s personal information from the web-site and from
several other users that have been certainly not explicitly authorized throughout the user. At the same
time, Face The distribution preserves usability from your site’s services seamlessly. Face Keep achieves
these goals by just enabling fake information towards the Myspace and Facebook blog and by
possessing sensitized info in encrypted form on the separate server. Most of us integrated our solution
as a standard Firefox internet browser extension to your Facebook platform. Our trial offers show that
our remedy with success conceals a user’s info that is personal together, while allowing the consumer in
addition to her friends to learn Facebook pages and services a lot of.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

INTRODUCTION
The advent along with fast adoption of Web 2. 0 technologies provides drastically changed the Internet
and has energized people to build social networks on the internet in spite of their geographical areas.
Recognized social networking sites, such as Myspace, let users to explore extra users with similar
passions, show personal information with good friends, display photos, etc. The ease of making friends
online moreover raises level of privacy concerns however, resulting in serious consequences
occasionally. The same to 13 crew users identified themselves dismissed simply by Virgin mobile
Underwater due to their inappropriate posts Facebook or Myspace. (Crew sacked over Facebook posts)
Wisconsin was could be following she posted a fantastic picture of herself with a weapon to Facebook.
Social networking sites permit visitors to post sensitive personal information generally, just like
relationship status, sex-related placement, political affiliation, and various personal interests. Even
though the neighborhood is regularly given notice about the risks associated with sociable social
network sites, a massive part
Of the population stays unacquainted with the potential privacy excitation or perhaps chooses to expose
prone facts despite these risks. In front of you survey conducted by Carnegie Mellon University, often
the university’s users of Facebook or possibly Myspace or Myspace present an astonishing amount of
facts: 90. 8% of the owners include an image, 87. 8% of the users show their particular birth date, 39. 9%
variety a phone number (including 28. 8% of profiles that contain usually the cellphone telephone
number), and fifty-five. 8% list their present home. As well as the wishful convinced that the Internet is a
relatives of well-behaved users seriously, one more factor that contributes to people’s disregard of
privacy hazards is the trust in the coverage measures and good reasons for a social networking site.
Sad to say, these sites are no more secure when compared with any other website in terms of protecting
themselves against malicious competitors. The two biggest players within just online social networking
just, Web sites and Facebook, ended up both equally found to be at risk of cross-site scripting attacks
helping assailants to steal user.
GOALS and presumptions
Degree of privacy protection upon social network marketing sites can be described as complicated
research problem. To the absolute best knowledge, there are not any normally accepted protection
strategies. Our goal is to make our personal solution instantly usable and get that cover more
individualized personal privacy risks than earlier research. In this section, we all examine the threat unit
plus the design thoughts that underlie our therapy. (Teacher Suspended for Gun Photos on Facebook)
The advent along with fast adoption of Web 2. 0 technologies provides drastically changed the Internet
and has energized people to build social networks on the internet in spite of their geographical areas.
Recognized social networking sites, such as Myspace, let users to explore extra users with similar
passions, show personal information with good friends, display photos, etc. The ease of making friends
online moreover raises level of privacy concerns however, resulting in serious consequences
occasionally. The same to 13 crew users identified themselves dismissed simply by Virgin mobile
Underwater due to their inappropriate posts Facebook or Myspace. (Crew sacked over Facebook posts)
Wisconsin was could be following she posted a fantastic picture of herself with a weapon to Facebook.
Social networking sites permit visitors to post sensitive personal information generally, just like
relationship status, sex-related placement, political affiliation, and various personal interests. Even
though the neighborhood is regularly given notice about the risks associated with sociable social
network sites, a massive part
Of the population stays unacquainted with the potential privacy excitation or perhaps chooses to expose
prone facts despite these risks. In front of you survey conducted by Carnegie Mellon University, often
the university’s users of Facebook or possibly Myspace or Myspace present an astonishing amount of
facts: 90. 8% of the owners include an image, 87. 8% of the users show their particular birth date, 39. 9%
variety a phone number (including 28. 8% of profiles that contain usually the cellphone telephone
number), and fifty-five. 8% list their present home. As well as the wishful convinced that the Internet is a
relatives of well-behaved users seriously, one more factor that contributes to people’s disregard of
privacy hazards is the trust in the coverage measures and good reasons for a social networking site.
Sad to say, these sites are no more secure when compared with any other website in terms of protecting
themselves against malicious competitors. The two biggest players within just online social networking
just, Web sites and Facebook, ended up both equally found to be at risk of cross-site scripting attacks
helping assailants to steal user.
GOALS and presumptions
Degree of privacy protection upon social network marketing sites can be described as complicated
research problem. To the absolute best knowledge, there are not any normally accepted protection
strategies. Our goal is to make our personal solution instantly usable and get that cover more
individualized personal privacy risks than earlier research. In this section, we all examine the threat unit
plus the design thoughts that underlie our therapy. (Teacher Suspended for Gun Photos on Facebook)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
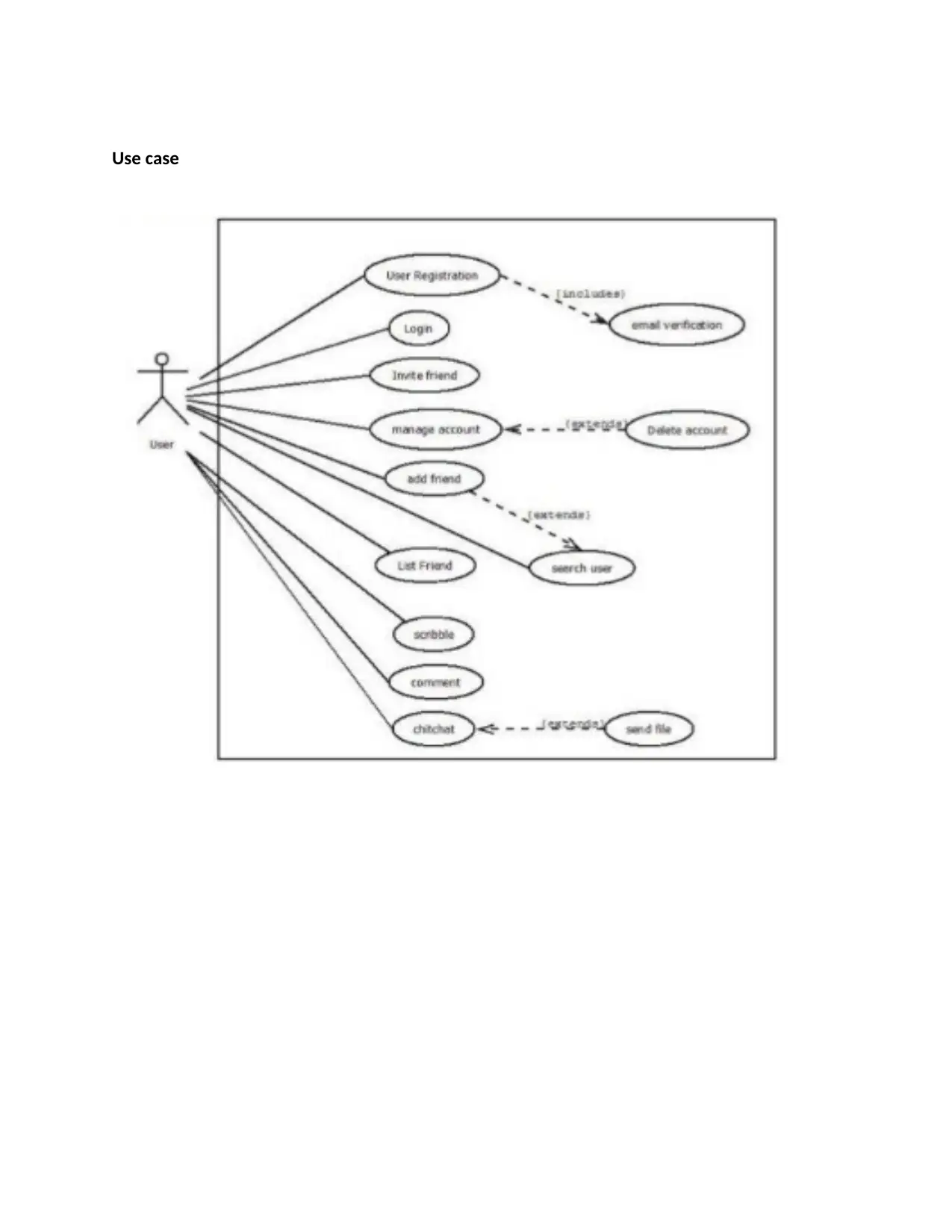
Use case

A. Threat Model
All of us consider a couple of different types of menace: The internet site itself and prone facts seekers.
• Social media marketing internet site. In Section I really, we certainly have already outlined several
strategies in which a social networking web page, typically not deliberately, may reveal a user’s
information that is certainly personal to parties not really authorized by the user. In addition, an
outstanding attacker may break into usually the cultural network site and reach any user’s personal
information, or perhaps even the provider of the blog could potentially be forced by government or
maybe a courtroom to disclose personal information. Within our peril model, we visualize a great
attacker can commence any kind of
Attack against the online networks blog and gain access to just about any private information that and
user gives placed on the site. Therefore, the real social networking site must be looked at a potential
threat for buyer a higher level privacy and should not have access to almost any user’s personal
information.
Really secret information seeker. A fragile information seeker tries to injury the privacy of the users on
your social networking blog by researching the site’s pages to gather subtle individual information. In
particular, meant for users who fail to reduce use of only their buddy’s, facts seekers can search their
very own profiles, their internet sites. (Information Revelation and Privacy found in Net Social Networks)
Design and style Guidelines
All of us consider a couple of different types of menace: The internet site itself and prone facts seekers.
• Social media marketing internet site. In Section I really, we certainly have already outlined several
strategies in which a social networking web page, typically not deliberately, may reveal a user’s
information that is certainly personal to parties not really authorized by the user. In addition, an
outstanding attacker may break into usually the cultural network site and reach any user’s personal
information, or perhaps even the provider of the blog could potentially be forced by government or
maybe a courtroom to disclose personal information. Within our peril model, we visualize a great
attacker can commence any kind of
Attack against the online networks blog and gain access to just about any private information that and
user gives placed on the site. Therefore, the real social networking site must be looked at a potential
threat for buyer a higher level privacy and should not have access to almost any user’s personal
information.
Really secret information seeker. A fragile information seeker tries to injury the privacy of the users on
your social networking blog by researching the site’s pages to gather subtle individual information. In
particular, meant for users who fail to reduce use of only their buddy’s, facts seekers can search their
very own profiles, their internet sites. (Information Revelation and Privacy found in Net Social Networks)
Design and style Guidelines
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

The design of Encounter Booklet is based on four crucial guidelines:
1) Preservation of common surfing around experience. An important residence for your usable
privacy protected answer is to refrain from altering users’ normal browsing workouts. Even more
specifically, the solution should do quickly most of the time and require small user interaction.
Constantly interrupting users for perception or possibly actions will discompose these people. Our
solution right away can be applied data encryption/decryption, site treatment, etc. and needs not much
user engagement.
2) A small amount of server-side changes. Providers related to social networking sites value economical
earnings as their primary goal, as any other organization, and individual privacy defense is more than
not put on the back burner typically. There generally is just not a great inspiration for these providers so
as to generate changes to their methodology architecture for the purpose of privacy simple safeness,
unless those shifts incorporate monetary gains and/or required properly. Therefore, a generally
deployable privacy safeguard unit should not count about server side help or adjustments. Our decision
requires very little such synergy and developments. (Another 0-day Myspace XSS Exploit)
3) Self-containment and minimal person configurations. Users of social networking sites include
specialized skill
Levels beginning coming from almost zero to experience extremely. To make a privacy security answer
functional to all customers irrespective of their skills, the ideal option is should be self-contained, not
really trust users to install extra program, and require little method. We implemented Deal with E-book
as a Firefox web browser growth, which can be installed just as each different Firefox internet browser
off of shoot, and this needs no building.
4) Incremental deployment. Deal with Publication users should not be halted coming from getting in
touch with old mates. To get incremental request, Come across Publication must ensure compatibility
relating to those people using that and the ones which are not relying on it.
Encryption Time frame
Assuming a content composer has attached Face E-book in her browser, the girl climbs into texts in PHP
PAGE forms on a social media web site just as she normally will probably, except that she prepends the
particular arrived to text using a particular marker pre-defined simply by Handle Book (“@@” in the
present implementation). For unique type elements, such as dropdown selections and even radio
buttons, the face area Information automatically adds one other couple of the same inputs prefixed
utilizing the special sign. Since getting some sort of design principle is secure release ability, users should
1) Preservation of common surfing around experience. An important residence for your usable
privacy protected answer is to refrain from altering users’ normal browsing workouts. Even more
specifically, the solution should do quickly most of the time and require small user interaction.
Constantly interrupting users for perception or possibly actions will discompose these people. Our
solution right away can be applied data encryption/decryption, site treatment, etc. and needs not much
user engagement.
2) A small amount of server-side changes. Providers related to social networking sites value economical
earnings as their primary goal, as any other organization, and individual privacy defense is more than
not put on the back burner typically. There generally is just not a great inspiration for these providers so
as to generate changes to their methodology architecture for the purpose of privacy simple safeness,
unless those shifts incorporate monetary gains and/or required properly. Therefore, a generally
deployable privacy safeguard unit should not count about server side help or adjustments. Our decision
requires very little such synergy and developments. (Another 0-day Myspace XSS Exploit)
3) Self-containment and minimal person configurations. Users of social networking sites include
specialized skill
Levels beginning coming from almost zero to experience extremely. To make a privacy security answer
functional to all customers irrespective of their skills, the ideal option is should be self-contained, not
really trust users to install extra program, and require little method. We implemented Deal with E-book
as a Firefox web browser growth, which can be installed just as each different Firefox internet browser
off of shoot, and this needs no building.
4) Incremental deployment. Deal with Publication users should not be halted coming from getting in
touch with old mates. To get incremental request, Come across Publication must ensure compatibility
relating to those people using that and the ones which are not relying on it.
Encryption Time frame
Assuming a content composer has attached Face E-book in her browser, the girl climbs into texts in PHP
PAGE forms on a social media web site just as she normally will probably, except that she prepends the
particular arrived to text using a particular marker pre-defined simply by Handle Book (“@@” in the
present implementation). For unique type elements, such as dropdown selections and even radio
buttons, the face area Information automatically adds one other couple of the same inputs prefixed
utilizing the special sign. Since getting some sort of design principle is secure release ability, users should
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

go any field unencrypted (by not prefixing it along with the special marker) for features such. As
disclosing actual names to get in touch with older friends.
Decryption Phase
Deal with Book, as installed in an exceedingly content viewer’s browser, comprehends which of the
viewer’s buddy’s use Face Book likewise, because it has the friends’ grasp and personal index keys. Yet,
next downloading a friend’s web page, Face Book will not recognize which of the downloaded records is
fake or perhaps real. Certainly, we could not noticing fake information and retailer tags with the
interpersonal social networking site, since this will allow the site to find Face Reserve users. Buying Face
Publication store label words in the area on users’ personal computers would not scale. Instead, for any
single again piece of information that could be artificial (I. e., a profile or perhaps a great article), Face
Publication computes an index, as examined in Section IV-A, as well as tries to download the matching
value from the third party pieces. If there is a value, Face Set up checks the integrity inside the received
cipher text message, decrypts that, and changes the preserved page by simply substituting the actual
info to get the fake documents. In any other case, the data is maintained unaffected. We use the exact
same technique when downloading this post viewer’s own pages. When an articles viewer without the
understanding important and the personal listing crucial of an account uncover browses the account’s
websites, the lady shall receive fake particulars and will not necessarily be able. (New Cross-Site
Scripting Vulnerability Observed On)
SECURITY ANALYSIS
It determines the security of Experience E-book by considering a variety of approaches against our
design. Our alternative guards against all the risks arising from the social networking site itself, while
described on the inside Section III-A. A user’s sensitive details that the purchaser chooses to guard using
Knowledge Publication is stored more than another server previously mentioned this reach of the social
networking web-site. The info stored on the site’s hardware is fake, that can contains no significant this
means by any means. However , we execute count on the user to judge precisely what specifics is
sensitive and can even be protected according to the female very own standard, and Encounter Guide
never forces you shield her information. One more threat that our solution refers to is definitely the
social networking site planning to acknowledge users of Encounter Manual and then taking punitive
measures against them, just like suspending their accounts. Specifically, usually the fake facts generated
by simply just Encounter Book looks real (see Section VI-A).
In addition, by simply which include an user’s owned or operated index key, which is certainly not seen
to the social networking web page, interior index of information kept when using third party web server,
we all makes it impossible for the internet site to help query publicly regarded trip servers about the
existence with regards to encrypted info posted for that user’s accounts. (How Facebook employees
enter your profile)
disclosing actual names to get in touch with older friends.
Decryption Phase
Deal with Book, as installed in an exceedingly content viewer’s browser, comprehends which of the
viewer’s buddy’s use Face Book likewise, because it has the friends’ grasp and personal index keys. Yet,
next downloading a friend’s web page, Face Book will not recognize which of the downloaded records is
fake or perhaps real. Certainly, we could not noticing fake information and retailer tags with the
interpersonal social networking site, since this will allow the site to find Face Reserve users. Buying Face
Publication store label words in the area on users’ personal computers would not scale. Instead, for any
single again piece of information that could be artificial (I. e., a profile or perhaps a great article), Face
Publication computes an index, as examined in Section IV-A, as well as tries to download the matching
value from the third party pieces. If there is a value, Face Set up checks the integrity inside the received
cipher text message, decrypts that, and changes the preserved page by simply substituting the actual
info to get the fake documents. In any other case, the data is maintained unaffected. We use the exact
same technique when downloading this post viewer’s own pages. When an articles viewer without the
understanding important and the personal listing crucial of an account uncover browses the account’s
websites, the lady shall receive fake particulars and will not necessarily be able. (New Cross-Site
Scripting Vulnerability Observed On)
SECURITY ANALYSIS
It determines the security of Experience E-book by considering a variety of approaches against our
design. Our alternative guards against all the risks arising from the social networking site itself, while
described on the inside Section III-A. A user’s sensitive details that the purchaser chooses to guard using
Knowledge Publication is stored more than another server previously mentioned this reach of the social
networking web-site. The info stored on the site’s hardware is fake, that can contains no significant this
means by any means. However , we execute count on the user to judge precisely what specifics is
sensitive and can even be protected according to the female very own standard, and Encounter Guide
never forces you shield her information. One more threat that our solution refers to is definitely the
social networking site planning to acknowledge users of Encounter Manual and then taking punitive
measures against them, just like suspending their accounts. Specifically, usually the fake facts generated
by simply just Encounter Book looks real (see Section VI-A).
In addition, by simply which include an user’s owned or operated index key, which is certainly not seen
to the social networking web page, interior index of information kept when using third party web server,
we all makes it impossible for the internet site to help query publicly regarded trip servers about the
existence with regards to encrypted info posted for that user’s accounts. (How Facebook employees
enter your profile)

B. Alternate between parties Server
The third get together net server, which is accountable for keeping coded data, can easily develop into
the pay attention to of attackers also, or possibly the hardware itself could switch damaging. In these full
cases, the opponent can help view each of the cipher texts, alternatively is not really their plaintexts.
The opponent cannot figure out the user account owner of the encrypted. You can then advise the
supplier of the different server from the breaking along with the original articles can be refurbished from
a backup. If the distributor on the third party server changed malevolent, the user should opt for a fresh
server. In the worst case, anyone may lose all given facts stored with the old storage space.
SCIENTIFIC and implementation RESEARCH
In this section, we elaborate about the implementation of Are up against Book and present trials that we
carried out by meeting new people having a real social networking site and in addition services. We look
at constraints of the current tips as well.
A. Firefox Browser Down shoot
Our current execution relating Face Book functions for Facebook mainly. We all made the decision
Myspace because it is just about the largest mom site. Nevertheless we do not expect much problems
porting Face Book sites further. We are at the moment owning a public release of the setup.
The user clicks the particular “Email” button then, which will give attention to her default e-mail
customers with the subject of the e-mail, the recipient’s e-mail deal with, and the pre-composed
content (I. get older., the personal index moreover to master keys and some educational information) all
filled in. An additional tool is dynamically produced
On the Facebook page to acquire adding a close friend. Following buying sent a close good friend
request, raising daylight cost savings time replaces the website link text “Add as Friend” with website
page textual content “Email Your Keys”, that this user can please just click to bring up her e-mail
consumers with all parts already determined.
Furthermore, to prevent facts seepage caused by Facebook applications, determined currently similarly
supports level of amount of privacy protection for Facebook Walls Facebook and structure Notes
program. Generating fraudulent text while using two applications is disturbing, since the content
material is not really nominal and may be about
The third get together net server, which is accountable for keeping coded data, can easily develop into
the pay attention to of attackers also, or possibly the hardware itself could switch damaging. In these full
cases, the opponent can help view each of the cipher texts, alternatively is not really their plaintexts.
The opponent cannot figure out the user account owner of the encrypted. You can then advise the
supplier of the different server from the breaking along with the original articles can be refurbished from
a backup. If the distributor on the third party server changed malevolent, the user should opt for a fresh
server. In the worst case, anyone may lose all given facts stored with the old storage space.
SCIENTIFIC and implementation RESEARCH
In this section, we elaborate about the implementation of Are up against Book and present trials that we
carried out by meeting new people having a real social networking site and in addition services. We look
at constraints of the current tips as well.
A. Firefox Browser Down shoot
Our current execution relating Face Book functions for Facebook mainly. We all made the decision
Myspace because it is just about the largest mom site. Nevertheless we do not expect much problems
porting Face Book sites further. We are at the moment owning a public release of the setup.
The user clicks the particular “Email” button then, which will give attention to her default e-mail
customers with the subject of the e-mail, the recipient’s e-mail deal with, and the pre-composed
content (I. get older., the personal index moreover to master keys and some educational information) all
filled in. An additional tool is dynamically produced
On the Facebook page to acquire adding a close friend. Following buying sent a close good friend
request, raising daylight cost savings time replaces the website link text “Add as Friend” with website
page textual content “Email Your Keys”, that this user can please just click to bring up her e-mail
consumers with all parts already determined.
Furthermore, to prevent facts seepage caused by Facebook applications, determined currently similarly
supports level of amount of privacy protection for Facebook Walls Facebook and structure Notes
program. Generating fraudulent text while using two applications is disturbing, since the content
material is not really nominal and may be about
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 15
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




