Security Options Analysis for JKL Company: A Comprehensive Report
VerifiedAdded on 2023/02/01
|12
|841
|51
Report
AI Summary
This report analyzes the security threats faced by JKL Company, focusing on computer viruses and Trojan horse attacks, which are significant risks given the company's data transfer activities. The report identifies JKL's business requirements for network security, including secure internet gateways and email security strategies. It then explores two key tools for mitigating these threats: Nessus, a vulnerability assessment solution that identifies and fixes weaknesses, and Hydra, a penetration testing tool used to crack login credentials. The report highlights the installation and operational aspects of both tools, concluding that Nessus is the most suitable security tool for JKL Company due to its ease of use and comprehensive features. The report also provides relevant references for further research.

Analyzing Security
Options for JKL company
Student name
Professor’s name
Unit title
Options for JKL company
Student name
Professor’s name
Unit title
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Security threats facing JKL Company
computer viruses-Computer viruses are programmed to spread across computers. In
most cases, they are sent as email attachments or downloaded from unique webpages
with the aim to infect network devices by using systems on the network [1]. If a virus
manages to penetrate JKL’s computer network, they can be able to disable the security
settings, steal personal data such as passwords or even delete data stored on users’
drives.
. Computer viruses are likely to gain entry into the company’s system since the
company’s operations involve multiple data transfers between the two sites over the
network. This creates a vulnerable loophole on JKL’s network as chances of sending or
downloading data containing a virus are high.
computer viruses-Computer viruses are programmed to spread across computers. In
most cases, they are sent as email attachments or downloaded from unique webpages
with the aim to infect network devices by using systems on the network [1]. If a virus
manages to penetrate JKL’s computer network, they can be able to disable the security
settings, steal personal data such as passwords or even delete data stored on users’
drives.
. Computer viruses are likely to gain entry into the company’s system since the
company’s operations involve multiple data transfers between the two sites over the
network. This creates a vulnerable loophole on JKL’s network as chances of sending or
downloading data containing a virus are high.

JKL’s business requirements
JKL’s business requirements in terms of network security include secure
internet gateways which will provide powerful cloud security
The cloud security strategy will mitigate threats at the IP and DNS
layers. This way the company will be able to defend against ransomware
and phishing a step earlier.
. JKL also needs an email security strategy. An effective email security
strategy should contain innovative threat monitoring capabilities with
end-to-end encryption.
JKL’s business requirements in terms of network security include secure
internet gateways which will provide powerful cloud security
The cloud security strategy will mitigate threats at the IP and DNS
layers. This way the company will be able to defend against ransomware
and phishing a step earlier.
. JKL also needs an email security strategy. An effective email security
strategy should contain innovative threat monitoring capabilities with
end-to-end encryption.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Trojan horse attack
This attack occurs when the users of a system run a malicious code
which is hiding behind a legitimate program. They are often spread via
email and are presented as emails from familiar individuals.
They are often spread via email and are presented as emails from
familiar individuals. After gaining access to the system, the Trojan horse
can then record passwords and steal sensitive data. Collaboration and
communication of staff between the two sites promotes Trojan horse
attacks to spread on JKL’s network.
This attack occurs when the users of a system run a malicious code
which is hiding behind a legitimate program. They are often spread via
email and are presented as emails from familiar individuals.
They are often spread via email and are presented as emails from
familiar individuals. After gaining access to the system, the Trojan horse
can then record passwords and steal sensitive data. Collaboration and
communication of staff between the two sites promotes Trojan horse
attacks to spread on JKL’s network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Tools that JKL Company can apply to
mitigate the security threats: Nessus
Nessus is a vulnerability assessment solution. The tool allows network administrators on
the front end to easily and quickly identify and fix vulnerabilities such as missing
patches and software flaws that result in virus and Trojan horse attacks.
Nessus’s tenable web app scanning product offers automated web application scanning.
Through its automated scanning feature, tenable enables highly automated scans for
constant protection. It also allows the administrator to easily stipulate the frequency and
timing limits for automated testing.
mitigate the security threats: Nessus
Nessus is a vulnerability assessment solution. The tool allows network administrators on
the front end to easily and quickly identify and fix vulnerabilities such as missing
patches and software flaws that result in virus and Trojan horse attacks.
Nessus’s tenable web app scanning product offers automated web application scanning.
Through its automated scanning feature, tenable enables highly automated scans for
constant protection. It also allows the administrator to easily stipulate the frequency and
timing limits for automated testing.

Nessus
To use Nessus products, users need to download and install the software
on their machines from the Nessus webpage. The process takes less
than five minutes and the products have a free trial period for testing
before purchasing the entire package.
Once the Nessus software has been installed, it automatically detects
the threats and vulnerabilities that arise instantly.
To use Nessus products, users need to download and install the software
on their machines from the Nessus webpage. The process takes less
than five minutes and the products have a free trial period for testing
before purchasing the entire package.
Once the Nessus software has been installed, it automatically detects
the threats and vulnerabilities that arise instantly.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
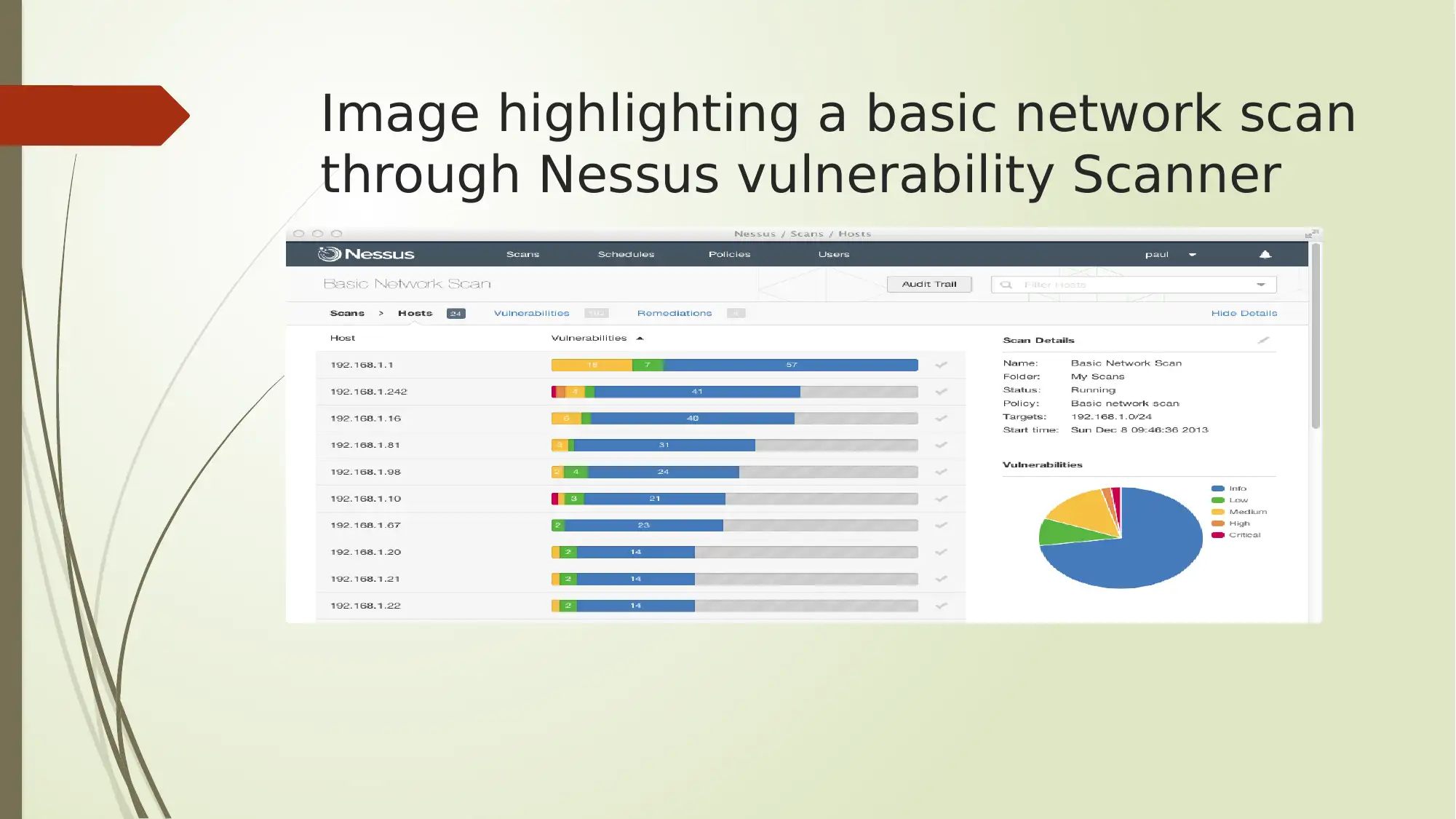
Image highlighting a basic network scan
through Nessus vulnerability Scanner
through Nessus vulnerability Scanner
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

The Hydra solution
. Hydra is a penetration testing tool that cracks login credentials [2]. It
supports several protocols to attack and is quite flexible and fast.
Hydra makes it possible for security consultants and researchers to
highlight how easy one can gain unauthorized access to the network
remotely.
The solution developed by Kali Linux has several tools included in its
package such as the pw-inspector which reads passwords and prints the
ones which meet the requirements [3].
. Hydra is a penetration testing tool that cracks login credentials [2]. It
supports several protocols to attack and is quite flexible and fast.
Hydra makes it possible for security consultants and researchers to
highlight how easy one can gain unauthorized access to the network
remotely.
The solution developed by Kali Linux has several tools included in its
package such as the pw-inspector which reads passwords and prints the
ones which meet the requirements [3].

The Hydra solution
By running the pw-inspector code, it returns the number of valid
passwords found.
The time taken to detect the threat through hydra penetration depends
on how long the code takes to be developed and run.
It may take several hours for complex systems or even days. It could
also be a few minutes for a small scale LAN network.
By running the pw-inspector code, it returns the number of valid
passwords found.
The time taken to detect the threat through hydra penetration depends
on how long the code takes to be developed and run.
It may take several hours for complex systems or even days. It could
also be a few minutes for a small scale LAN network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
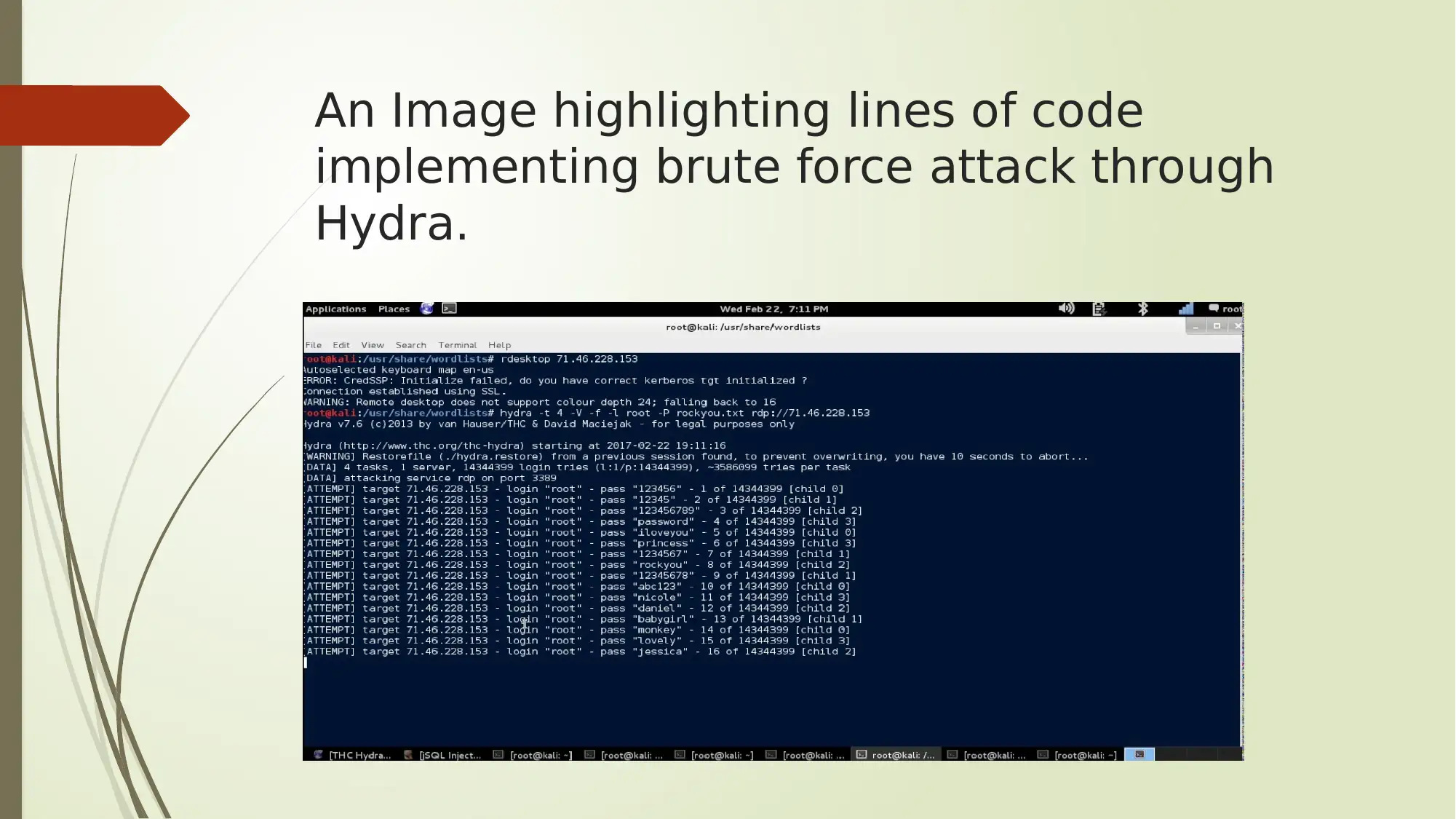
An Image highlighting lines of code
implementing brute force attack through
Hydra.
implementing brute force attack through
Hydra.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
The best security tool that JKL should
implement
Nessus would be the best security tool that JKL should implement
The solution is easier to install and run and also comes in different
products offering alternatives to several security issues.
The Hydra solution is quite complex since it requires one to run codes
while testing hence suited only for the users with knowledge on
programming skills.
implement
Nessus would be the best security tool that JKL should implement
The solution is easier to install and run and also comes in different
products offering alternatives to several security issues.
The Hydra solution is quite complex since it requires one to run codes
while testing hence suited only for the users with knowledge on
programming skills.

References
[
1
]
Department of Public Safety and Emergency Preparedness , "Common threats to be aware of," 20 October 2017.
[Online]. Available: https://www.getcybersafe.gc.ca/cnt/rsks/cmmn-thrts-en.aspx.
[
2
]
Kali Linux, "Hydra Package Description," 2019. [Online]. Available: https://tools.kali.org/password-attacks/hydra.
[
3
]
N. Mitropoulos, "Using Hydra To Crack The Door Open," 2013. [Online]. Available:
https://hakin9.org/usinghydratocrackthedooropen/.
[
1
]
Department of Public Safety and Emergency Preparedness , "Common threats to be aware of," 20 October 2017.
[Online]. Available: https://www.getcybersafe.gc.ca/cnt/rsks/cmmn-thrts-en.aspx.
[
2
]
Kali Linux, "Hydra Package Description," 2019. [Online]. Available: https://tools.kali.org/password-attacks/hydra.
[
3
]
N. Mitropoulos, "Using Hydra To Crack The Door Open," 2013. [Online]. Available:
https://hakin9.org/usinghydratocrackthedooropen/.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





