Secure Remote Access: VPN Benefits for JKS Accounting in Sydney
VerifiedAdded on 2023/06/16
|13
|864
|310
Presentation
AI Summary
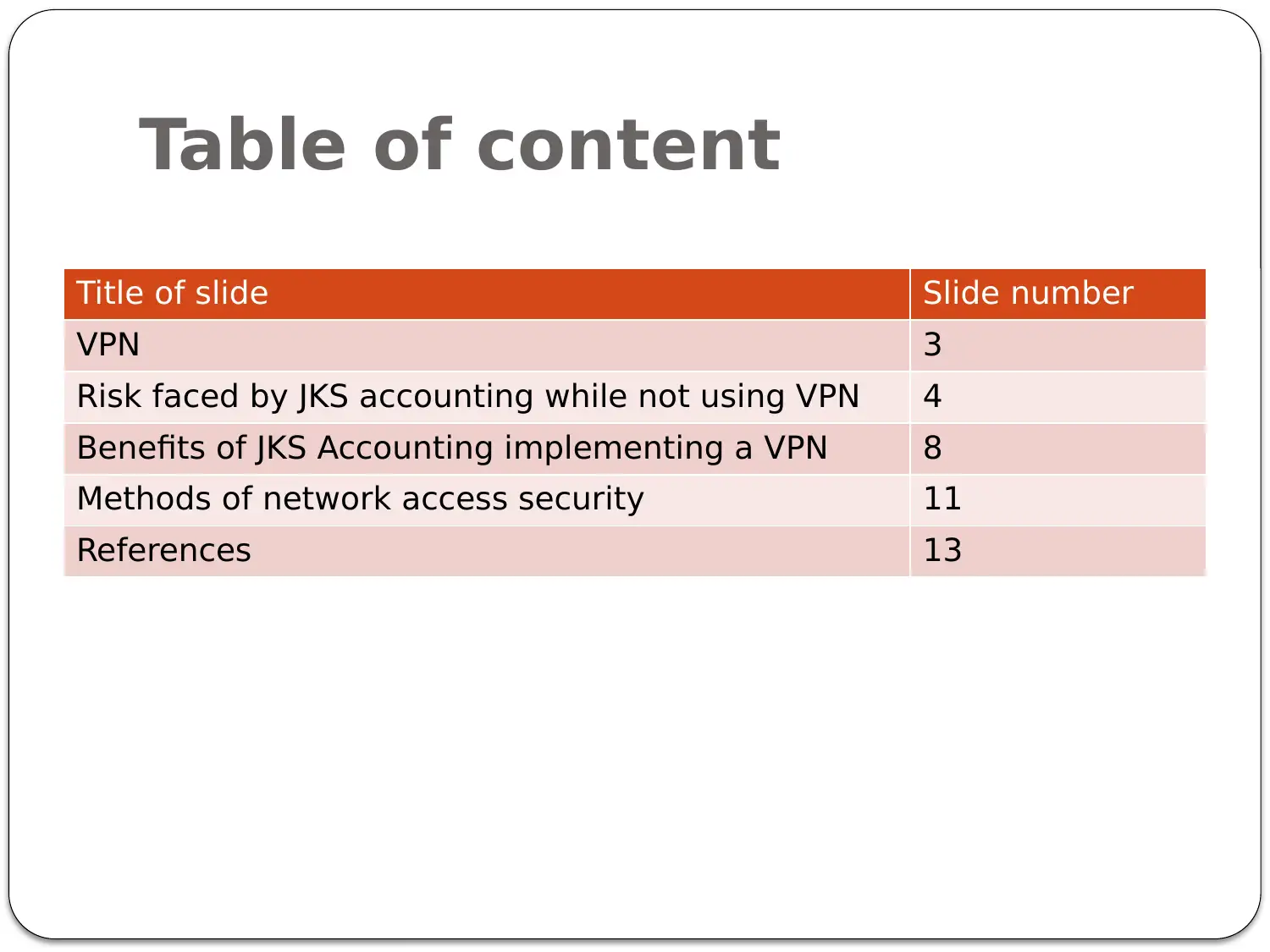
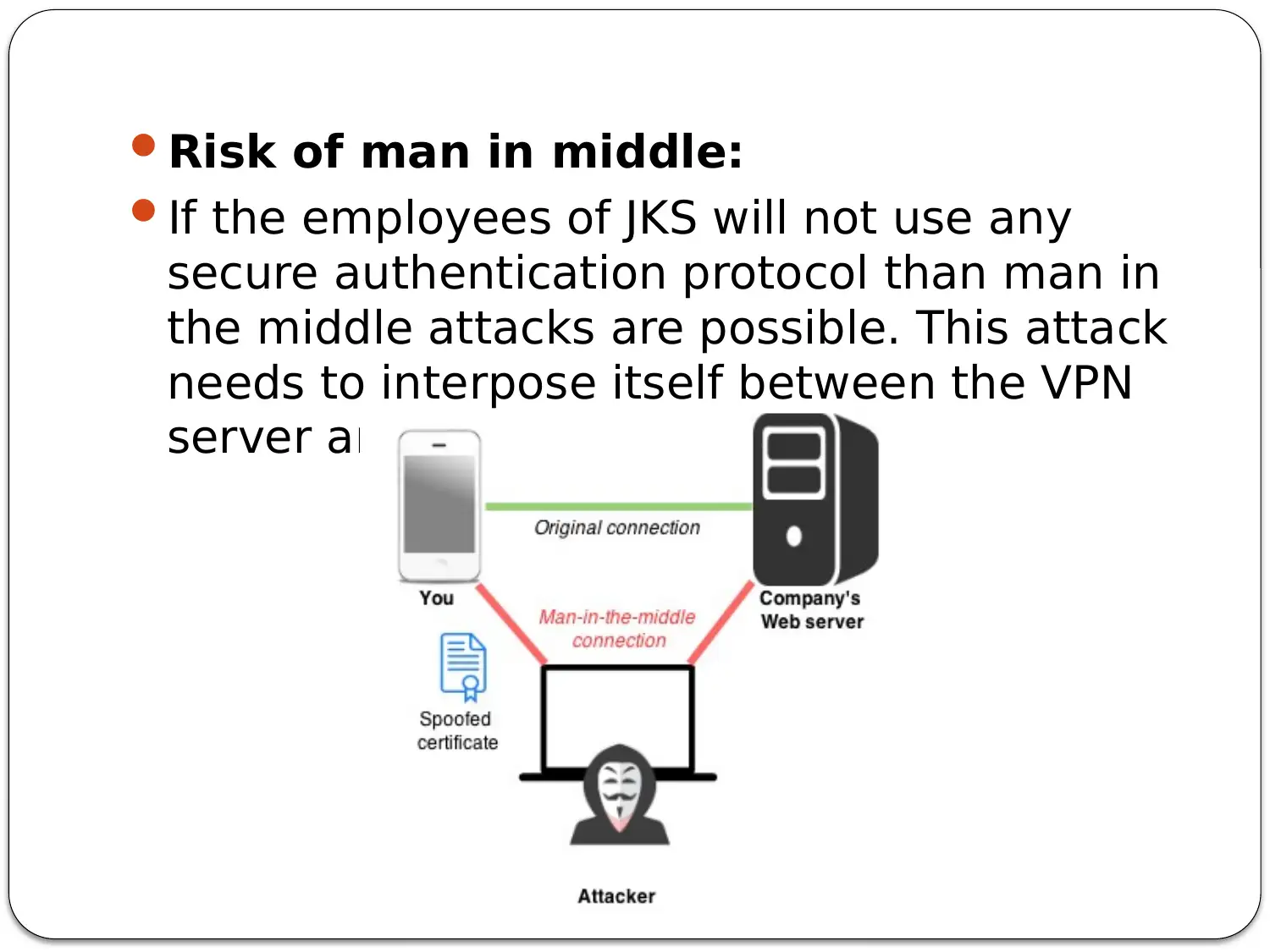
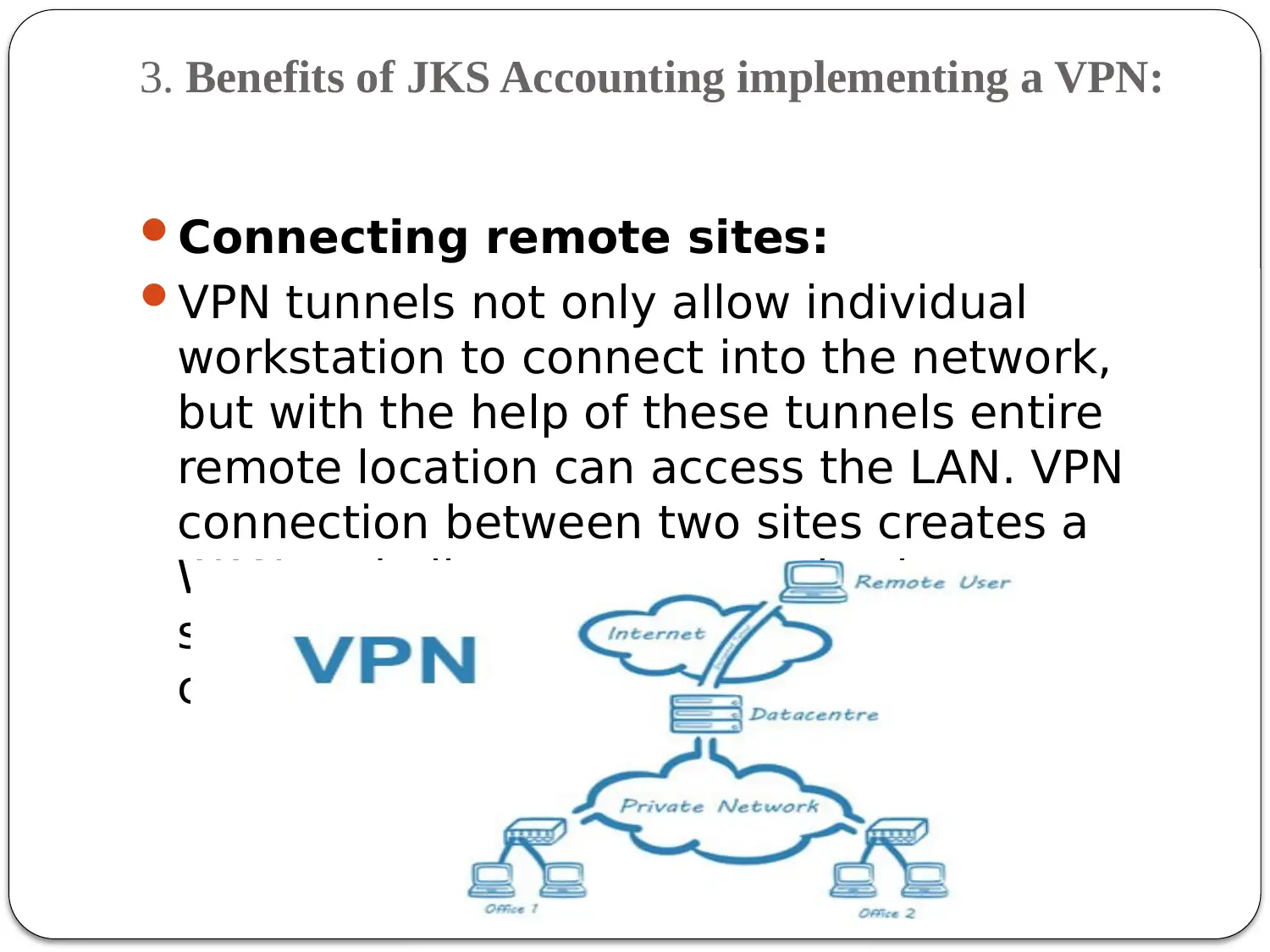
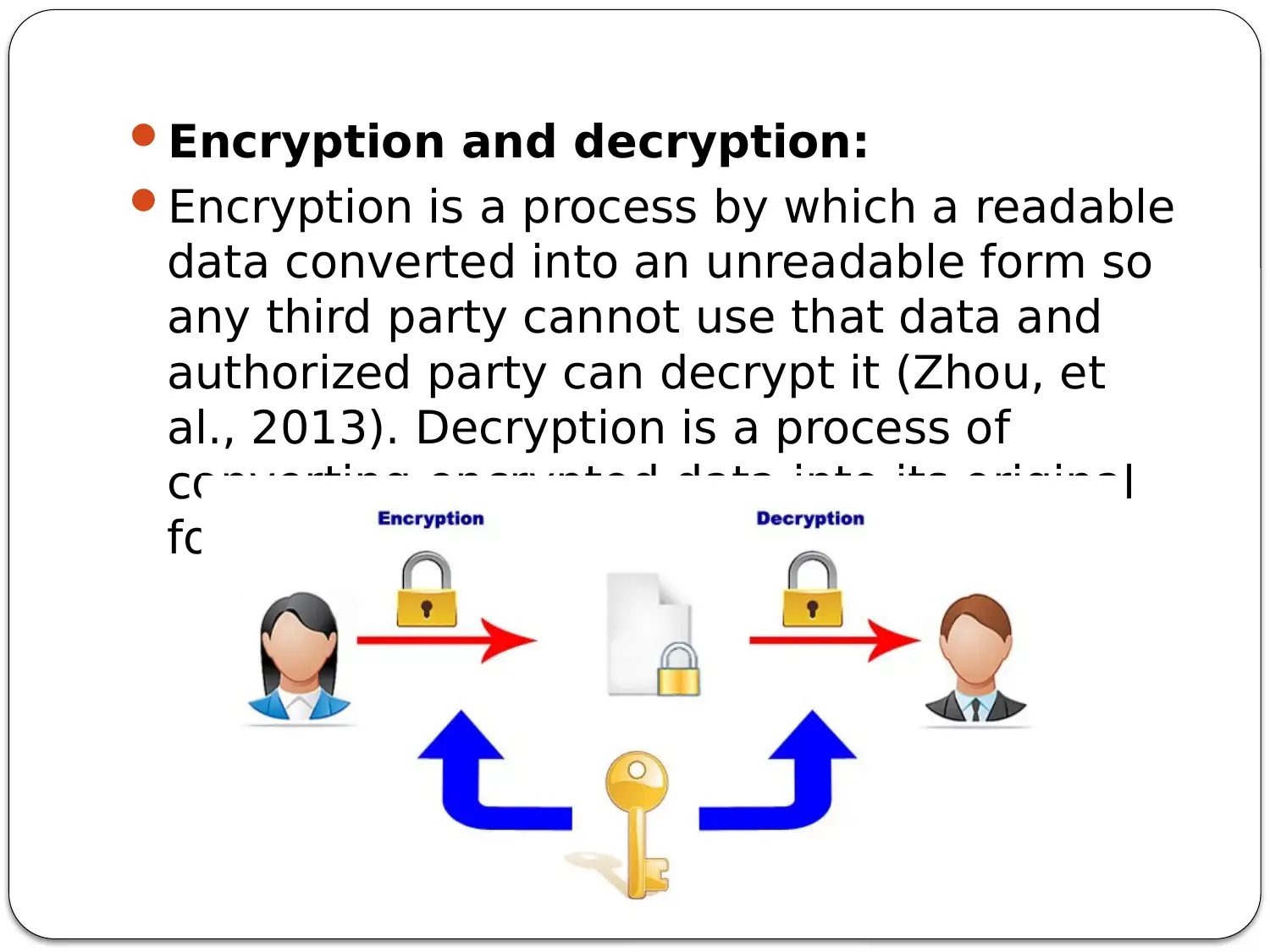
This presentation addresses the need for secure remote access at JKS Accounting, outlining the benefits of implementing a Virtual Private Network (VPN). It begins by defining VPNs and their role in securing private and public networks, particularly for corporations handling sensitive data. The presentation then highlights the risks JKS Accounting faces without a VPN, including man-in-the-middle attacks, DDoS vulnerabilities due to unsecured end-user devices, and the risk of data breaches when employees work remotely. Subsequently, it details the advantages of VPN implementation, such as connecting remote sites, reducing overhead costs by enabling remote work, providing emergency data recovery, and enhancing overall security for the company and its employees. Finally, the presentation touches upon other network access security methods like Access Control Lists (ACL), IP filtering, and encryption/decryption to provide a comprehensive security strategy for JKS Accounting.
1 out of 13














![[object Object]](/_next/static/media/star-bottom.7253800d.svg)