Comprehensive Cyber Security Report for JL Company in Perth, Australia
VerifiedAdded on 2023/06/03
|17
|2944
|223
Report
AI Summary
This report provides recommendations to JL Company to meet current and future customer security requests, addressing employee reluctance to adopt security measures. It covers five critical security issues: malicious attacks (hacking, viruses), data loss, security breaches, unsecure wireless networks, and IOT threats. For each issue, the report offers specific solutions, such as updating software, regular data backups, employee training, access limitations, and strong password policies. The report also estimates the costs of implementing these security measures and compares the proposed solutions with alternatives, such as different Windows Server versions and antivirus software. The aim is to equip JL Company with a strategic security framework to minimize risks associated with adopting new technologies and online activities.

Running head: Computer security 1
Unit Code
Unit Title
Assignment Title
Student Name
Instructor’s Title
Unit Code
Unit Title
Assignment Title
Student Name
Instructor’s Title
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer security 2
Executive summary
The purpose of this report is to prepare a variety of recommendations that would ensure that
the JL Company meet the contemporary and future customer request. The report would
convince the employees who are very reluctant to adopt the current security issues, in this
paper five critical security issues would be addressed, The report would also provide
recommendations to the JL company on how to solve the current security issues.
Executive summary
The purpose of this report is to prepare a variety of recommendations that would ensure that
the JL Company meet the contemporary and future customer request. The report would
convince the employees who are very reluctant to adopt the current security issues, in this
paper five critical security issues would be addressed, The report would also provide
recommendations to the JL company on how to solve the current security issues.

Computer security 3
Table of Contents
1.0 Introduction.....................................................................................................................................4
2.0 Cyber security issues within the JL Company...................................................................................4
1. Malicious attacks, such as hacking and viruses..........................................................................4
Proposal for the JL Company prevent malicious attack.................................................................5
2.Data loss.........................................................................................................................................5
3 Security breaches...........................................................................................................................6
Recommendations to the JL Company to solve the security beach...............................................6
4 Unsecure wireless network............................................................................................................8
5 IOT threats......................................................................................................................................8
Ways in which the JL Company may apply to prevent IOT threats................................................8
2.6 The cost required for the implementing security measures......................................................9
3.0The comparison of security solution proposed to the JL Company with other solutions........11
4.0 Conclusions...................................................................................................................................14
1.0 References..............................................................................................................................15
Table of Contents
1.0 Introduction.....................................................................................................................................4
2.0 Cyber security issues within the JL Company...................................................................................4
1. Malicious attacks, such as hacking and viruses..........................................................................4
Proposal for the JL Company prevent malicious attack.................................................................5
2.Data loss.........................................................................................................................................5
3 Security breaches...........................................................................................................................6
Recommendations to the JL Company to solve the security beach...............................................6
4 Unsecure wireless network............................................................................................................8
5 IOT threats......................................................................................................................................8
Ways in which the JL Company may apply to prevent IOT threats................................................8
2.6 The cost required for the implementing security measures......................................................9
3.0The comparison of security solution proposed to the JL Company with other solutions........11
4.0 Conclusions...................................................................................................................................14
1.0 References..............................................................................................................................15
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer security 4
1.0 Introduction
Due to the current security issues concerning cyber security, it is important for the company
to lay day security measures that would assist the company to avoid risk that comes with
cyber security attacks. There are advantages that comes with employing modern security
measures for instance, the company would enhance a general security posture, increase the
efficiency of operation and enhance accountability among the staff and the employees among
other advantages. Handling of data such as for accounting in the organization may be
vulnerable to cyber-attacks, leaking of organization information or even data loss. The JL
Company should adopt to the modern technology in their business operation, it staff should
possess adequate knowledge and skills in handling the modern technology because in case of
any risk it would be a fatal to the organization. It is important for the company to lay down a
strategic security measures that would help in minimizing risk that are associated with
adopting to the new technology (Buczak & Guven, 2016).
Since the company have started to engage in online activities, the strategic security measures
would play a crucial role in safeguarding the company resources, increasing the number of
staff as suggested by the company would be helpful. This report would major on solution that
that would address the current security concerns of the company. My research on current
cyber security attacks enable to come up with measures that would help in addressing the
current situation (Yunfei, Yuanbao, Xuan & Qi, 2015).
2.0 Cyber security issues within the JL Company
1. Malicious attacks, such as hacking and viruses
Because the computers have the JL company does not have antivirus, the company
have recently been attacked by a ransomware, a ransomware is a malevolent software
1.0 Introduction
Due to the current security issues concerning cyber security, it is important for the company
to lay day security measures that would assist the company to avoid risk that comes with
cyber security attacks. There are advantages that comes with employing modern security
measures for instance, the company would enhance a general security posture, increase the
efficiency of operation and enhance accountability among the staff and the employees among
other advantages. Handling of data such as for accounting in the organization may be
vulnerable to cyber-attacks, leaking of organization information or even data loss. The JL
Company should adopt to the modern technology in their business operation, it staff should
possess adequate knowledge and skills in handling the modern technology because in case of
any risk it would be a fatal to the organization. It is important for the company to lay down a
strategic security measures that would help in minimizing risk that are associated with
adopting to the new technology (Buczak & Guven, 2016).
Since the company have started to engage in online activities, the strategic security measures
would play a crucial role in safeguarding the company resources, increasing the number of
staff as suggested by the company would be helpful. This report would major on solution that
that would address the current security concerns of the company. My research on current
cyber security attacks enable to come up with measures that would help in addressing the
current situation (Yunfei, Yuanbao, Xuan & Qi, 2015).
2.0 Cyber security issues within the JL Company
1. Malicious attacks, such as hacking and viruses
Because the computers have the JL company does not have antivirus, the company
have recently been attacked by a ransomware, a ransomware is a malevolent software
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer security 5
which is created to block accessibility of computer till a specified amount of money is
paid.
Proposal for the JL Company prevent malicious attack
I. The JL Company should update from windows server 2000 to windows 2012
which have more security features. This would assist the company to limit the
vulnerability. In fact the company should do regular updates to the software.
Generally it is important for the company to download latest version of
windows once it is available.
II. The JL Company should do regular backups to files remotely daily on an
external hard drive which is not connected to the internet. As long as the data
would be backup on the external hard drive, the company won’t lose any data
if is attacked by the ransomware attack
III. Employees Apply should always be warned on opening any distrustful email
attachments and to never download any app that is not coming from the real
store. The employees should always read reviews if they must download the
app otherwise it is not recommended.
IV. The company should make use of the antiviruses which has an ability to scan
files and identify if it has the ransomware. The company should utilise this
antivirus before downloading.
2. Data loss
The data loss in the JL Company courses the computer to misbehave, this is because
of the errors in the systems in which the data is destroyed by neglect or failures in
storage processing or data transmission. Data loss is also closely related to data beach,
which is created to block accessibility of computer till a specified amount of money is
paid.
Proposal for the JL Company prevent malicious attack
I. The JL Company should update from windows server 2000 to windows 2012
which have more security features. This would assist the company to limit the
vulnerability. In fact the company should do regular updates to the software.
Generally it is important for the company to download latest version of
windows once it is available.
II. The JL Company should do regular backups to files remotely daily on an
external hard drive which is not connected to the internet. As long as the data
would be backup on the external hard drive, the company won’t lose any data
if is attacked by the ransomware attack
III. Employees Apply should always be warned on opening any distrustful email
attachments and to never download any app that is not coming from the real
store. The employees should always read reviews if they must download the
app otherwise it is not recommended.
IV. The company should make use of the antiviruses which has an ability to scan
files and identify if it has the ransomware. The company should utilise this
antivirus before downloading.
2. Data loss
The data loss in the JL Company courses the computer to misbehave, this is because
of the errors in the systems in which the data is destroyed by neglect or failures in
storage processing or data transmission. Data loss is also closely related to data beach,

Computer security 6
this is where the data are accessed by unauthorised persons. The JL Company can
prevent data loss by doing the following
I. The can should do regular backup
II. A good working conducts
III. Installing antivirus to the office computers- I recommend the JL Company to
use VIPRE antivirus, it perform better than other antivirus.
IV. Protection against power surge thru a UPS
The JL may also use the following tools for data loss prevention
I. Symantec data loss prevention- which is responsible for data management and
tracking of data
II. Trustwave data loss preventions- manage and track data
III. MacAfee data loss prevention- data tracking and management
IV. Checkpoint data loss prevention- educate on data loss and remediation
3 Security breaches
The data of the JL Company does not have access limit, the employees can access
emails freely. The company should address this issue immediately because it would
bring big security beaches. The consumers of the company would feel worried if this
is going to happen. Data beaches will bring a lot of problems to the JL Company, the
criminal attacks would affect company negatively and it will costs the company
millions of many and it is going to tarnish the reputation of the company
(Peltier,2016).
Recommendations to the JL Company to solve the security beach
this is where the data are accessed by unauthorised persons. The JL Company can
prevent data loss by doing the following
I. The can should do regular backup
II. A good working conducts
III. Installing antivirus to the office computers- I recommend the JL Company to
use VIPRE antivirus, it perform better than other antivirus.
IV. Protection against power surge thru a UPS
The JL may also use the following tools for data loss prevention
I. Symantec data loss prevention- which is responsible for data management and
tracking of data
II. Trustwave data loss preventions- manage and track data
III. MacAfee data loss prevention- data tracking and management
IV. Checkpoint data loss prevention- educate on data loss and remediation
3 Security breaches
The data of the JL Company does not have access limit, the employees can access
emails freely. The company should address this issue immediately because it would
bring big security beaches. The consumers of the company would feel worried if this
is going to happen. Data beaches will bring a lot of problems to the JL Company, the
criminal attacks would affect company negatively and it will costs the company
millions of many and it is going to tarnish the reputation of the company
(Peltier,2016).
Recommendations to the JL Company to solve the security beach
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer security 7
There are several ways in which the JL Company may solve this issue of the security
beach which would help the company to safeguard their data.
I. The company should limit access to the primary data of the
organization.
In the current situation of the company, every employee can access all the
data in the office computer. The employees should stop this immediately
otherwise the company would learn the add way, after all, it is of no reason
for the mailroom workers to access the financial information of the
customers. Limiting access would help in avoiding this scenarios and also
would limit the employees from clicking on links that may harm the data of
the organizations (Perlman, Kaufman & Speciner, 2016).
II. The JL Company should conduct security awareness and training for
the employees.
Analysing the current situations of the JL Company, the employees are
causing the computers of the company to be more susceptible to attacks,
accessing emails daily will have the potentiality to downloading of viruses. I
recommend the company to create posters that would help to warn
employees against cybercrimes and provide ways of avoiding those (Da &
Martins, 2015).
III. Regular software updates
I recommend the JL Company to keep the operating and all the application
software updated. Installation of patches when it is available will be a good
practice. The network of the JL Company is vulnerable because the programs
are not updated and are not patched up. This is an easy way to make the
There are several ways in which the JL Company may solve this issue of the security
beach which would help the company to safeguard their data.
I. The company should limit access to the primary data of the
organization.
In the current situation of the company, every employee can access all the
data in the office computer. The employees should stop this immediately
otherwise the company would learn the add way, after all, it is of no reason
for the mailroom workers to access the financial information of the
customers. Limiting access would help in avoiding this scenarios and also
would limit the employees from clicking on links that may harm the data of
the organizations (Perlman, Kaufman & Speciner, 2016).
II. The JL Company should conduct security awareness and training for
the employees.
Analysing the current situations of the JL Company, the employees are
causing the computers of the company to be more susceptible to attacks,
accessing emails daily will have the potentiality to downloading of viruses. I
recommend the company to create posters that would help to warn
employees against cybercrimes and provide ways of avoiding those (Da &
Martins, 2015).
III. Regular software updates
I recommend the JL Company to keep the operating and all the application
software updated. Installation of patches when it is available will be a good
practice. The network of the JL Company is vulnerable because the programs
are not updated and are not patched up. This is an easy way to make the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computer security 8
network to be strong and eliminate attacks before it happens (Ghai, Sharma
& Jain. 2015).
IV. Application of strong passwords which are hard to decipher
The current passwords used by the JL company admin is very easy to predict.
Employees should be encourage to change passwords regularly in order to
avoid cyber beaches. The employees should learn to use combination of
special characters, uppercase, lowercase, letters and numbers while setting
passwords. The password should be made difficult to make it impossible for
the thieves to break it and still the data (Flowerday & Tuyikeze, 2016).
4 Unsecure wireless network
The internet access in the company is through ADSL utilizing D-Link wireless router.
This type of network have certain vulnerabilities. The company can resolve in the
following ways:
Securing the client settings
The wireless network contain some vulnerabilities such as man-in-the-middle attacks,
this happens in a this scenario: the attack set up a wireless network that have the same
SSID with the network they are going to copy, when someone tries to connect to the
network a ‘’ bogus RADIOUS server’’ capture the logins credentials. The attacker
would then connect to the real network using the captured logins (Soomro, Shah &
Ahmed, 2016).
Apply enterprise WPA2 with 802.1x secure validation
Most of the useful mechanism to use is deploying enterprise mode of wireless
securities because it would assist to authenticate every user independently. So in an
network to be strong and eliminate attacks before it happens (Ghai, Sharma
& Jain. 2015).
IV. Application of strong passwords which are hard to decipher
The current passwords used by the JL company admin is very easy to predict.
Employees should be encourage to change passwords regularly in order to
avoid cyber beaches. The employees should learn to use combination of
special characters, uppercase, lowercase, letters and numbers while setting
passwords. The password should be made difficult to make it impossible for
the thieves to break it and still the data (Flowerday & Tuyikeze, 2016).
4 Unsecure wireless network
The internet access in the company is through ADSL utilizing D-Link wireless router.
This type of network have certain vulnerabilities. The company can resolve in the
following ways:
Securing the client settings
The wireless network contain some vulnerabilities such as man-in-the-middle attacks,
this happens in a this scenario: the attack set up a wireless network that have the same
SSID with the network they are going to copy, when someone tries to connect to the
network a ‘’ bogus RADIOUS server’’ capture the logins credentials. The attacker
would then connect to the real network using the captured logins (Soomro, Shah &
Ahmed, 2016).
Apply enterprise WPA2 with 802.1x secure validation
Most of the useful mechanism to use is deploying enterprise mode of wireless
securities because it would assist to authenticate every user independently. So in an

Computer security 9
event of computer being stolen or as staff leaves the organization, the user logins
would be revoked (Biscop, 2016)
Use wired network instead of wireless network- is more secure against threats
5 IOT threats
The JL Company use an incorporated computing devices, digital and mechanical
machines that has unique identifiers. This IOT are vulnerable to bring security
issues to the company (Wang, Jajodia, Singhal, Cheng & Noel, 2014).
Ways in which the JL Company may apply to prevent IOT threats
1) The password for each and every device must be change from default.
The devices that does not allow the password update from the default
should not be utilized.
2) It would be a good idea for the company to contain a different network
that is behind a firewall that is under monitoring. For the all the IOT
devices. This will help in securing devices that are allocated from the
resources and network (Layton, 2016).
3) Check for regular updates to make sure that the office computers are
getting latest patches. Never use software that does not have updates.
4) Ensure that the computers and office devices does not connect
automatically to any open WI-FI networks, this not good, it is important to
make sure that the devices does not do that (Knapp & Langill, 2014).
3.0 The cost required for the implementing security
measures
For the JL Company to set up a security measure, it would have to use substantial capital to
establish a security measure that would help the company to reduce the risk that are exposed
to. The infrastructure required would be the servers and servers. The latest security software
event of computer being stolen or as staff leaves the organization, the user logins
would be revoked (Biscop, 2016)
Use wired network instead of wireless network- is more secure against threats
5 IOT threats
The JL Company use an incorporated computing devices, digital and mechanical
machines that has unique identifiers. This IOT are vulnerable to bring security
issues to the company (Wang, Jajodia, Singhal, Cheng & Noel, 2014).
Ways in which the JL Company may apply to prevent IOT threats
1) The password for each and every device must be change from default.
The devices that does not allow the password update from the default
should not be utilized.
2) It would be a good idea for the company to contain a different network
that is behind a firewall that is under monitoring. For the all the IOT
devices. This will help in securing devices that are allocated from the
resources and network (Layton, 2016).
3) Check for regular updates to make sure that the office computers are
getting latest patches. Never use software that does not have updates.
4) Ensure that the computers and office devices does not connect
automatically to any open WI-FI networks, this not good, it is important to
make sure that the devices does not do that (Knapp & Langill, 2014).
3.0 The cost required for the implementing security
measures
For the JL Company to set up a security measure, it would have to use substantial capital to
establish a security measure that would help the company to reduce the risk that are exposed
to. The infrastructure required would be the servers and servers. The latest security software
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Computer security 10
should also be bought and installed to the computers systems of the organization. These
infrastructure may be costly to the JL Company because it would also require experts to that
would assist the company in the installation, configuration and maintenance of the system.
The following table summarises the cost per unit and the total cost that would be required in
US dollars (Siponen, Mahmood & Pahnila, 2014).
should also be bought and installed to the computers systems of the organization. These
infrastructure may be costly to the JL Company because it would also require experts to that
would assist the company in the installation, configuration and maintenance of the system.
The following table summarises the cost per unit and the total cost that would be required in
US dollars (Siponen, Mahmood & Pahnila, 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
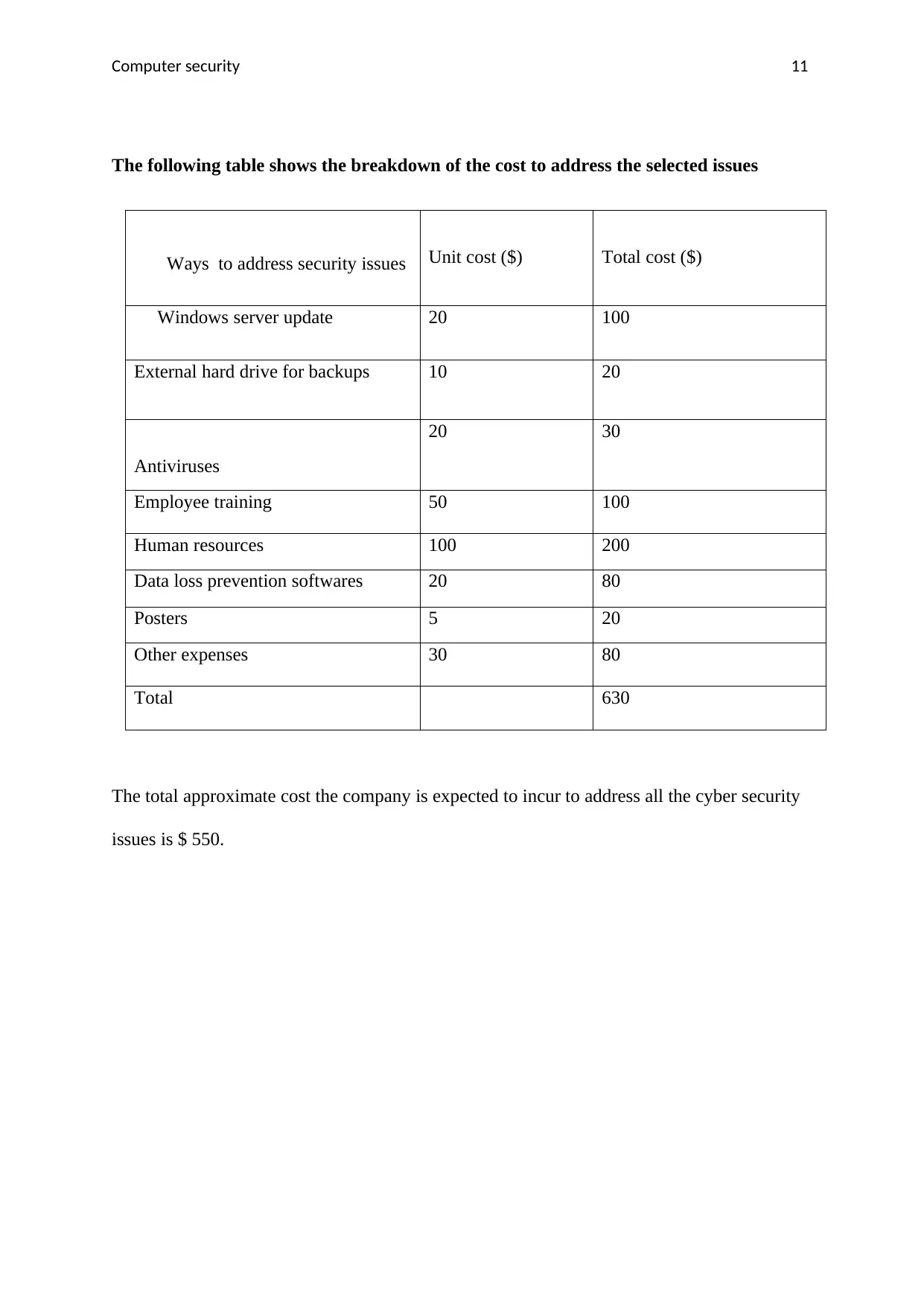
Computer security 11
The following table shows the breakdown of the cost to address the selected issues
Ways to address security issues Unit cost ($) Total cost ($)
Windows server update 20 100
External hard drive for backups 10 20
Antiviruses
20 30
Employee training 50 100
Human resources 100 200
Data loss prevention softwares 20 80
Posters 5 20
Other expenses 30 80
Total 630
The total approximate cost the company is expected to incur to address all the cyber security
issues is $ 550.
The following table shows the breakdown of the cost to address the selected issues
Ways to address security issues Unit cost ($) Total cost ($)
Windows server update 20 100
External hard drive for backups 10 20
Antiviruses
20 30
Employee training 50 100
Human resources 100 200
Data loss prevention softwares 20 80
Posters 5 20
Other expenses 30 80
Total 630
The total approximate cost the company is expected to incur to address all the cyber security
issues is $ 550.
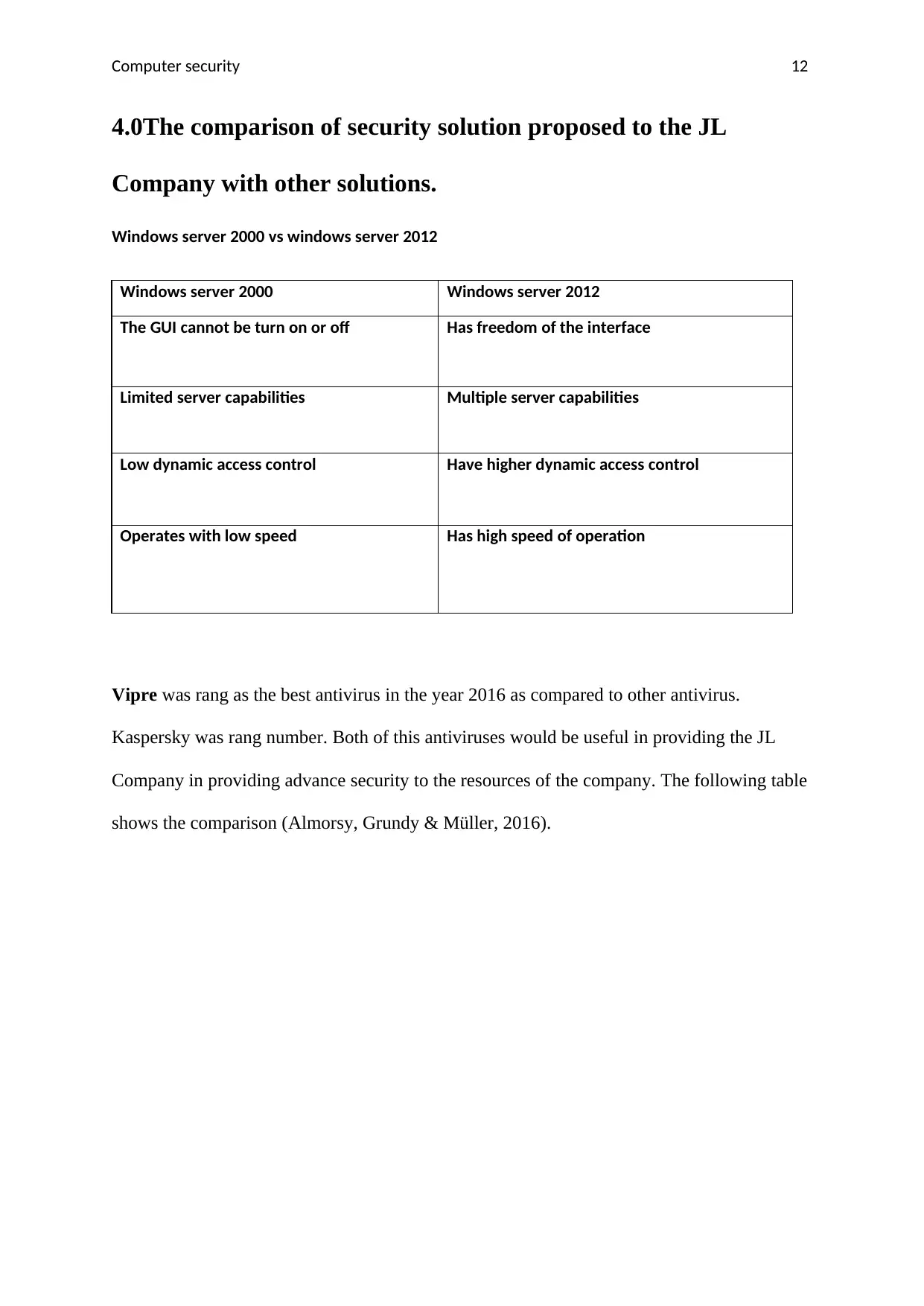
Computer security 12
4.0The comparison of security solution proposed to the JL
Company with other solutions.
Windows server 2000 vs windows server 2012
Windows server 2000 Windows server 2012
The GUI cannot be turn on or off Has freedom of the interface
Limited server capabilities Multiple server capabilities
Low dynamic access control Have higher dynamic access control
Operates with low speed Has high speed of operation
Vipre was rang as the best antivirus in the year 2016 as compared to other antivirus.
Kaspersky was rang number. Both of this antiviruses would be useful in providing the JL
Company in providing advance security to the resources of the company. The following table
shows the comparison (Almorsy, Grundy & Müller, 2016).
4.0The comparison of security solution proposed to the JL
Company with other solutions.
Windows server 2000 vs windows server 2012
Windows server 2000 Windows server 2012
The GUI cannot be turn on or off Has freedom of the interface
Limited server capabilities Multiple server capabilities
Low dynamic access control Have higher dynamic access control
Operates with low speed Has high speed of operation
Vipre was rang as the best antivirus in the year 2016 as compared to other antivirus.
Kaspersky was rang number. Both of this antiviruses would be useful in providing the JL
Company in providing advance security to the resources of the company. The following table
shows the comparison (Almorsy, Grundy & Müller, 2016).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





