University Report: Firewall Testing on Kali Linux Using Nmap
VerifiedAdded on 2023/01/23
|18
|1810
|98
Report
AI Summary
This report provides a detailed analysis of firewall testing using Nmap within the Kali Linux environment. It begins with an introduction to Kali Linux and Nmap, explaining their functionalities and applications in cybersecurity. The report then delves into the core functions of Nmap, including OS detection, network scanning, stealth scanning, and Maimon scanning, along with their performance metrics. The central part of the report demonstrates practical firewall testing techniques using Nmap, such as identifying open ports with stealth scanners and testing individual ports with Maimon scanners. It also covers finding the operating system versions of devices attached to open ports. The report concludes with a mitigation plan to address the vulnerabilities identified during the network scan and a practical section on firewall configuration in Kali Linux, including checking firewall status, enabling/disabling the firewall, allowing services, verifying firewall rules, securing a web server, allowing and denying port ranges, allowing HTTP from a specific subnet, blocking connections to a network interface, and finalizing the firewall status. The report references several sources to support its findings and recommendations.

Running head: FIREWALL TESTING ON KALI LINUX USING NMAP
FIREWALL TESTING ON KALI LINUX USING NMAP
Name of the Student:
Name of the University:
Author Note:
FIREWALL TESTING ON KALI LINUX USING NMAP
Name of the Student:
Name of the University:
Author Note:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1FIREWALL TESTING ON KALI LINUX USING NMAP
Table of Contents
PART A......................................................................................................................................2
Introduction............................................................................................................................2
NMAP....................................................................................................................................2
Performance of the above mentioned tools:...........................................................................6
The firewall testing using Nmap:...........................................................................................7
Mitigation plan.....................................................................................................................10
PART B....................................................................................................................................11
References................................................................................................................................16
Table of Contents
PART A......................................................................................................................................2
Introduction............................................................................................................................2
NMAP....................................................................................................................................2
Performance of the above mentioned tools:...........................................................................6
The firewall testing using Nmap:...........................................................................................7
Mitigation plan.....................................................................................................................10
PART B....................................................................................................................................11
References................................................................................................................................16

2FIREWALL TESTING ON KALI LINUX USING NMAP
PART A
Introduction
The Kali Linux is an operating system that is based on the Debian architecture and is mainly
used for vulnerability and security testing by ethical hackers and cyber security specialists.
The system helps the users identify the main loopholes in a connected networks. It is a free to
use software and is widely used for penetration testing and vulnerability detection purposes.
In this report, the use of nmap will be shown. It is a tool which can be used through Kali
Linux to scan large networks and single hosts alike. The tool helps in detecting vulnerabilities
of a given network and helps the user in identifying the security risks associated with his
system.
NMAP
Nmap tool has a wide number of functions. It is mainly designed as a free and open source
network scanner. It can be effectively used to find out services and hosts in a given computer
network. It can also be used for effective firewall testing and find out vulnerabilities in the
systems connected to a given network. It can be effectively used in a variety of other
operating systems like Windows, MacOS and BSD. However, it can be best used in Kali
linux to detect vulnerabilities.
The four main functions of the Nmap are:
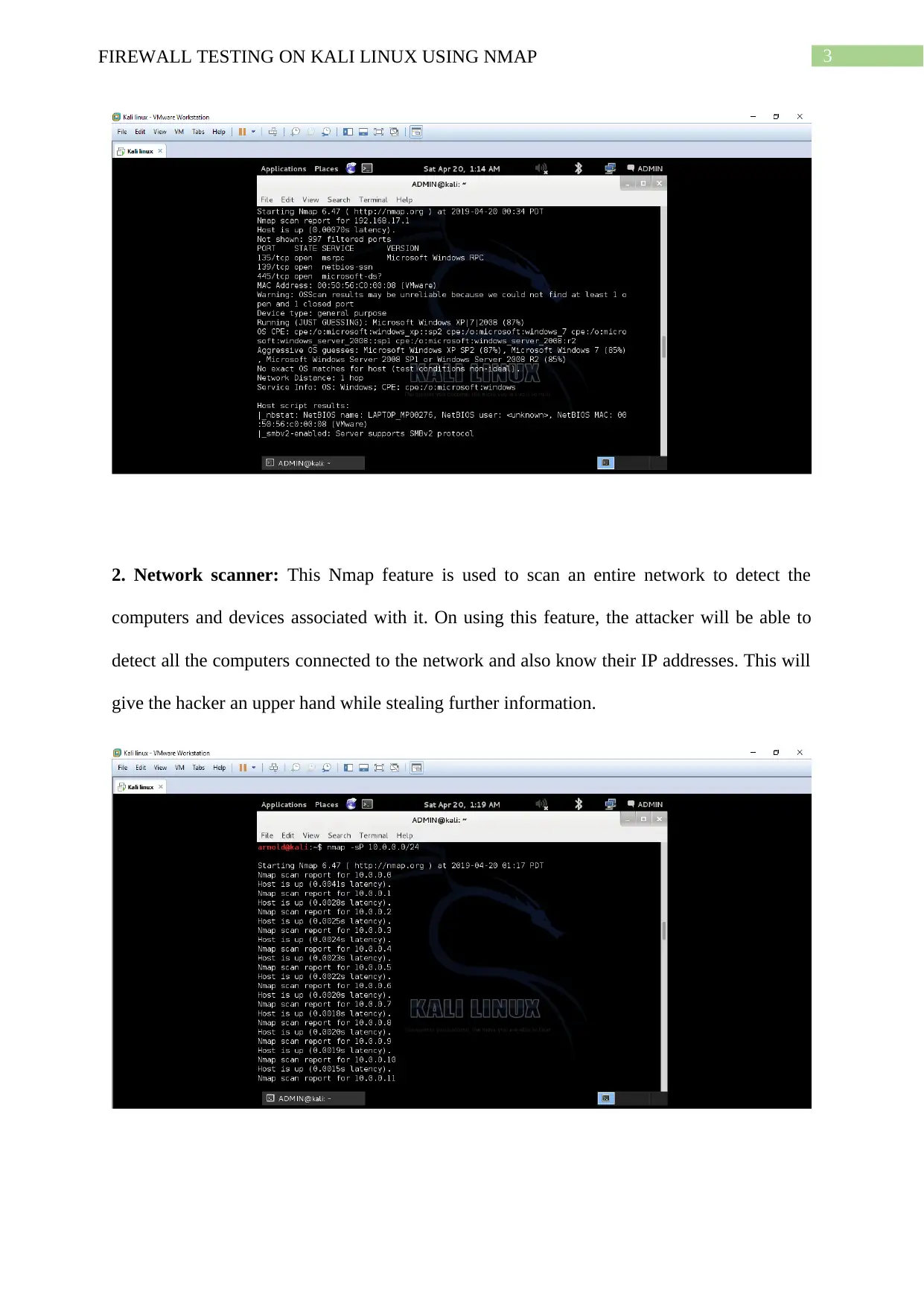
1. OS detection: The Nmap feature can be used to detect the operating systems of computers
connected to a certain network. This feature can be used by hackers to detect the operating
system type and version of a given computer connected to the network. This will help them
plan an attack considering the vulnerabilities of the given operating system.
PART A
Introduction
The Kali Linux is an operating system that is based on the Debian architecture and is mainly
used for vulnerability and security testing by ethical hackers and cyber security specialists.
The system helps the users identify the main loopholes in a connected networks. It is a free to
use software and is widely used for penetration testing and vulnerability detection purposes.
In this report, the use of nmap will be shown. It is a tool which can be used through Kali
Linux to scan large networks and single hosts alike. The tool helps in detecting vulnerabilities
of a given network and helps the user in identifying the security risks associated with his
system.
NMAP
Nmap tool has a wide number of functions. It is mainly designed as a free and open source
network scanner. It can be effectively used to find out services and hosts in a given computer
network. It can also be used for effective firewall testing and find out vulnerabilities in the
systems connected to a given network. It can be effectively used in a variety of other
operating systems like Windows, MacOS and BSD. However, it can be best used in Kali
linux to detect vulnerabilities.
The four main functions of the Nmap are:
1. OS detection: The Nmap feature can be used to detect the operating systems of computers
connected to a certain network. This feature can be used by hackers to detect the operating
system type and version of a given computer connected to the network. This will help them
plan an attack considering the vulnerabilities of the given operating system.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3FIREWALL TESTING ON KALI LINUX USING NMAP
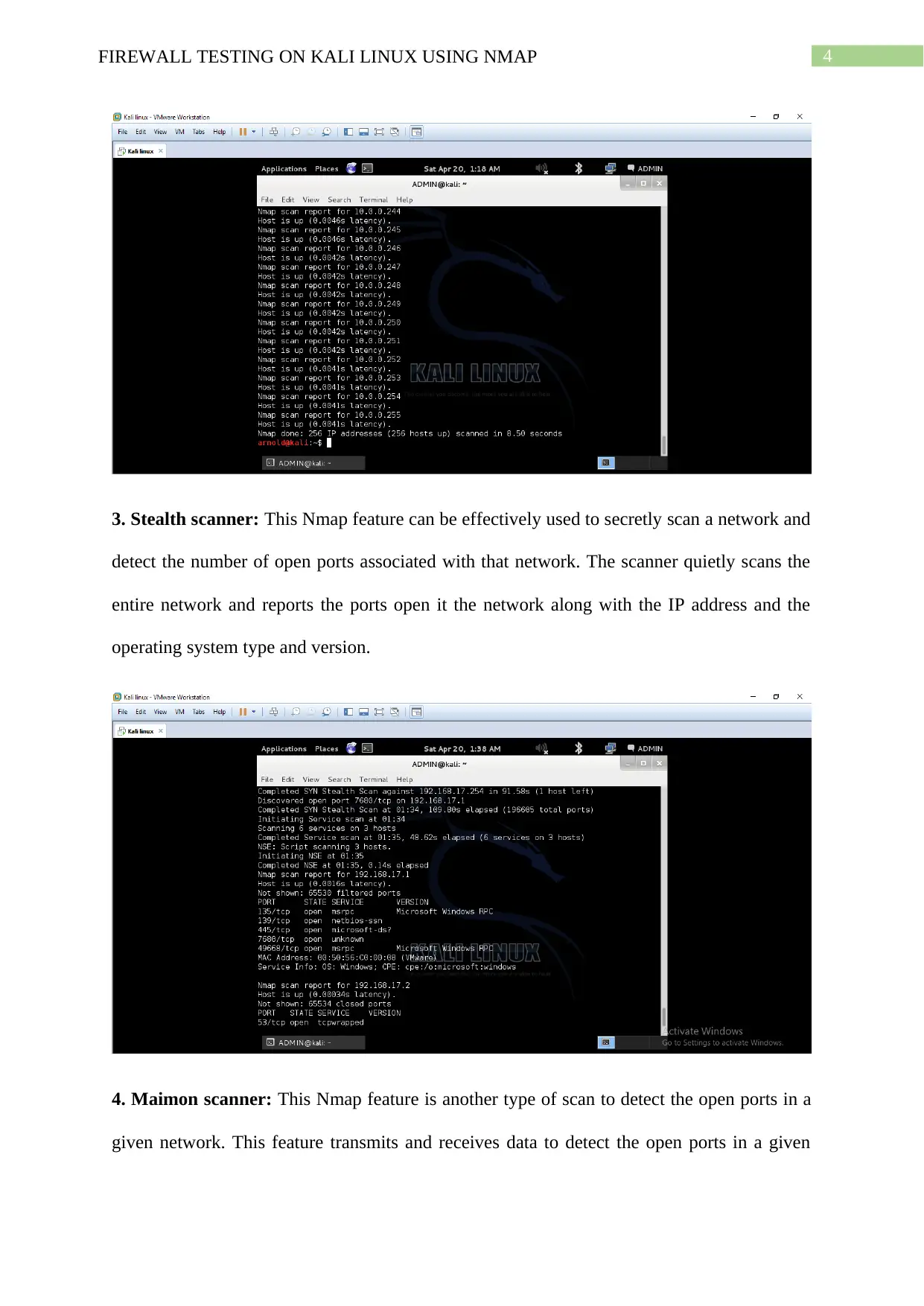
2. Network scanner: This Nmap feature is used to scan an entire network to detect the
computers and devices associated with it. On using this feature, the attacker will be able to
detect all the computers connected to the network and also know their IP addresses. This will
give the hacker an upper hand while stealing further information.
2. Network scanner: This Nmap feature is used to scan an entire network to detect the
computers and devices associated with it. On using this feature, the attacker will be able to
detect all the computers connected to the network and also know their IP addresses. This will
give the hacker an upper hand while stealing further information.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4FIREWALL TESTING ON KALI LINUX USING NMAP
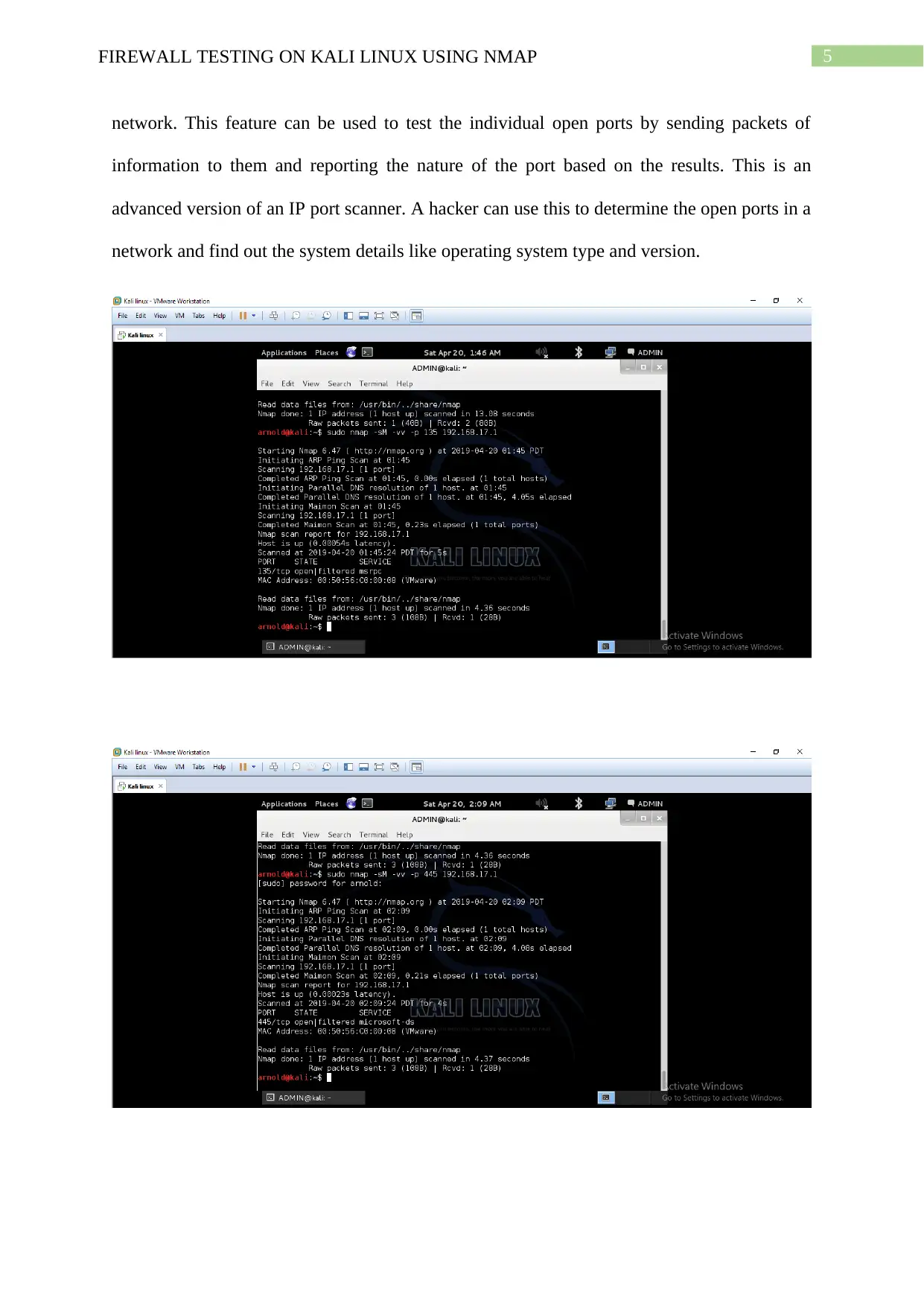
3. Stealth scanner: This Nmap feature can be effectively used to secretly scan a network and
detect the number of open ports associated with that network. The scanner quietly scans the
entire network and reports the ports open it the network along with the IP address and the
operating system type and version.
4. Maimon scanner: This Nmap feature is another type of scan to detect the open ports in a
given network. This feature transmits and receives data to detect the open ports in a given
3. Stealth scanner: This Nmap feature can be effectively used to secretly scan a network and
detect the number of open ports associated with that network. The scanner quietly scans the
entire network and reports the ports open it the network along with the IP address and the
operating system type and version.
4. Maimon scanner: This Nmap feature is another type of scan to detect the open ports in a
given network. This feature transmits and receives data to detect the open ports in a given
5FIREWALL TESTING ON KALI LINUX USING NMAP
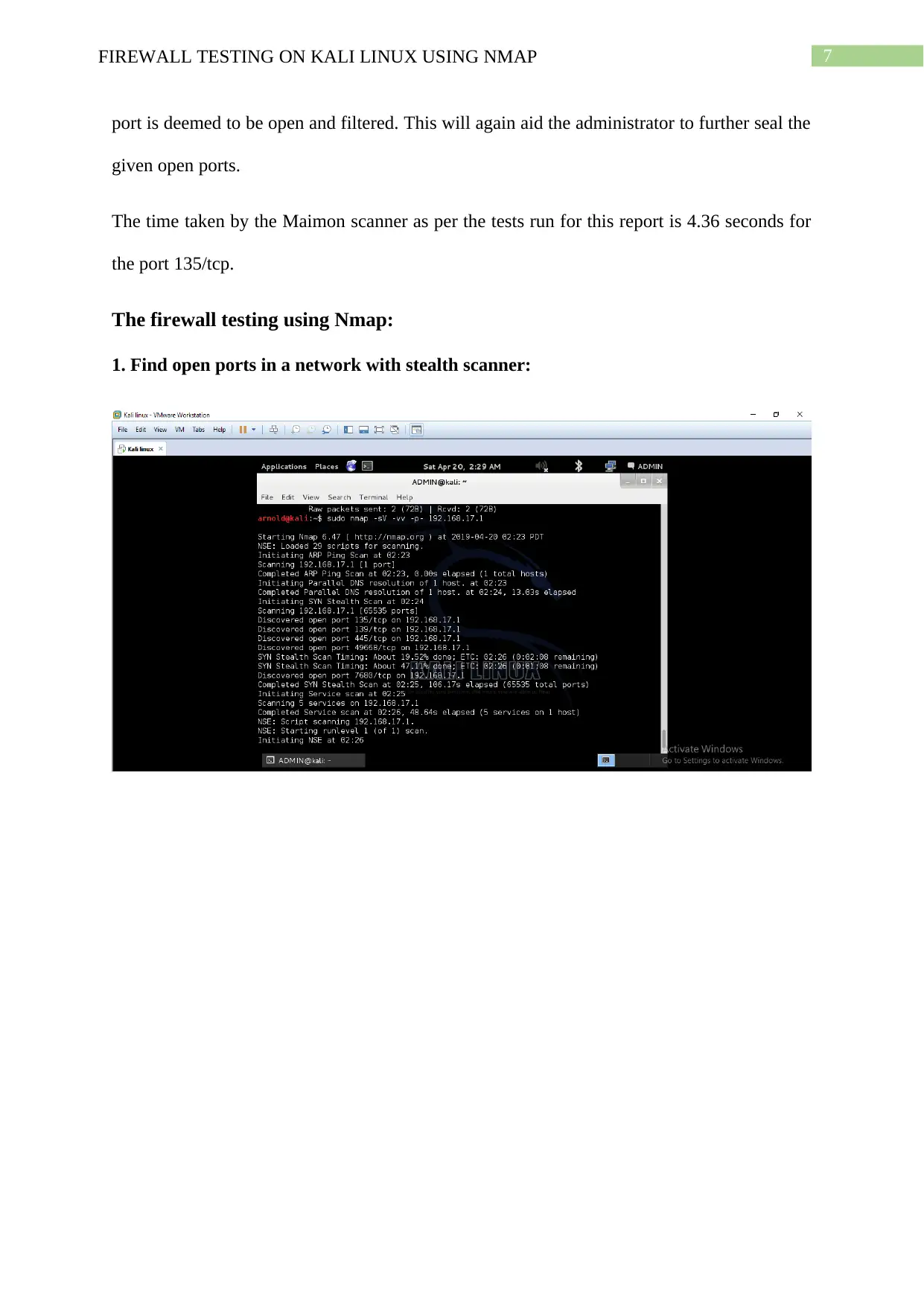
network. This feature can be used to test the individual open ports by sending packets of
information to them and reporting the nature of the port based on the results. This is an
advanced version of an IP port scanner. A hacker can use this to determine the open ports in a
network and find out the system details like operating system type and version.
network. This feature can be used to test the individual open ports by sending packets of
information to them and reporting the nature of the port based on the results. This is an
advanced version of an IP port scanner. A hacker can use this to determine the open ports in a
network and find out the system details like operating system type and version.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

6FIREWALL TESTING ON KALI LINUX USING NMAP
Performance of the above mentioned tools:
1. OS scanner: The Operating system scanner is more or less efficient in detecting the
operating system of a computer connected to a given network. It can be used to check the rate
of successful detection of a given operating system and then patch up the detected operating
system with latest updates to avoid further detection. Once patched it becomes harder for the
hacker to detect the system using the OS scanner.
The time taken to detect the OS by this scanner is 87.82 seconds as per the test run for this
report.
2. Network scanner: This tool can be used for a security purpose to detect the open and
uptime IP addresses connected to the network. This will help us determine which devices are
visible in the network and take necessary steps to hide them from the hacker.
The time taken by the scanner to detect the systems in a given IP subnet as per the test run for
this report is 8.50 seconds.
3. Stealth scanner: This feature is a very useful tool of Nmap that can help detect the IP
addresses with open ports in a given network. The IP addresses detected with open ports are
shown individually and all the open ports are mentioned clearly. This will help the
administrator to close the open ports to prevent any inbound attacks and secure the network.
The time taken by the tool to detect the open ports in a network as per the tests run for this
report is 48.62 seconds.
4. Maimon scanner: This feature is also quite useful as it does the same job as the stealth
scanner but uses data packets to individual ports in a given network to detect the port’s status.
This method is more reliable than normal scanner as if a reply to a packet is not received, the
Performance of the above mentioned tools:
1. OS scanner: The Operating system scanner is more or less efficient in detecting the
operating system of a computer connected to a given network. It can be used to check the rate
of successful detection of a given operating system and then patch up the detected operating
system with latest updates to avoid further detection. Once patched it becomes harder for the
hacker to detect the system using the OS scanner.
The time taken to detect the OS by this scanner is 87.82 seconds as per the test run for this
report.
2. Network scanner: This tool can be used for a security purpose to detect the open and
uptime IP addresses connected to the network. This will help us determine which devices are
visible in the network and take necessary steps to hide them from the hacker.
The time taken by the scanner to detect the systems in a given IP subnet as per the test run for
this report is 8.50 seconds.
3. Stealth scanner: This feature is a very useful tool of Nmap that can help detect the IP
addresses with open ports in a given network. The IP addresses detected with open ports are
shown individually and all the open ports are mentioned clearly. This will help the
administrator to close the open ports to prevent any inbound attacks and secure the network.
The time taken by the tool to detect the open ports in a network as per the tests run for this
report is 48.62 seconds.
4. Maimon scanner: This feature is also quite useful as it does the same job as the stealth
scanner but uses data packets to individual ports in a given network to detect the port’s status.
This method is more reliable than normal scanner as if a reply to a packet is not received, the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
7FIREWALL TESTING ON KALI LINUX USING NMAP
port is deemed to be open and filtered. This will again aid the administrator to further seal the
given open ports.
The time taken by the Maimon scanner as per the tests run for this report is 4.36 seconds for
the port 135/tcp.
The firewall testing using Nmap:
1. Find open ports in a network with stealth scanner:
port is deemed to be open and filtered. This will again aid the administrator to further seal the
given open ports.
The time taken by the Maimon scanner as per the tests run for this report is 4.36 seconds for
the port 135/tcp.
The firewall testing using Nmap:
1. Find open ports in a network with stealth scanner:
8FIREWALL TESTING ON KALI LINUX USING NMAP
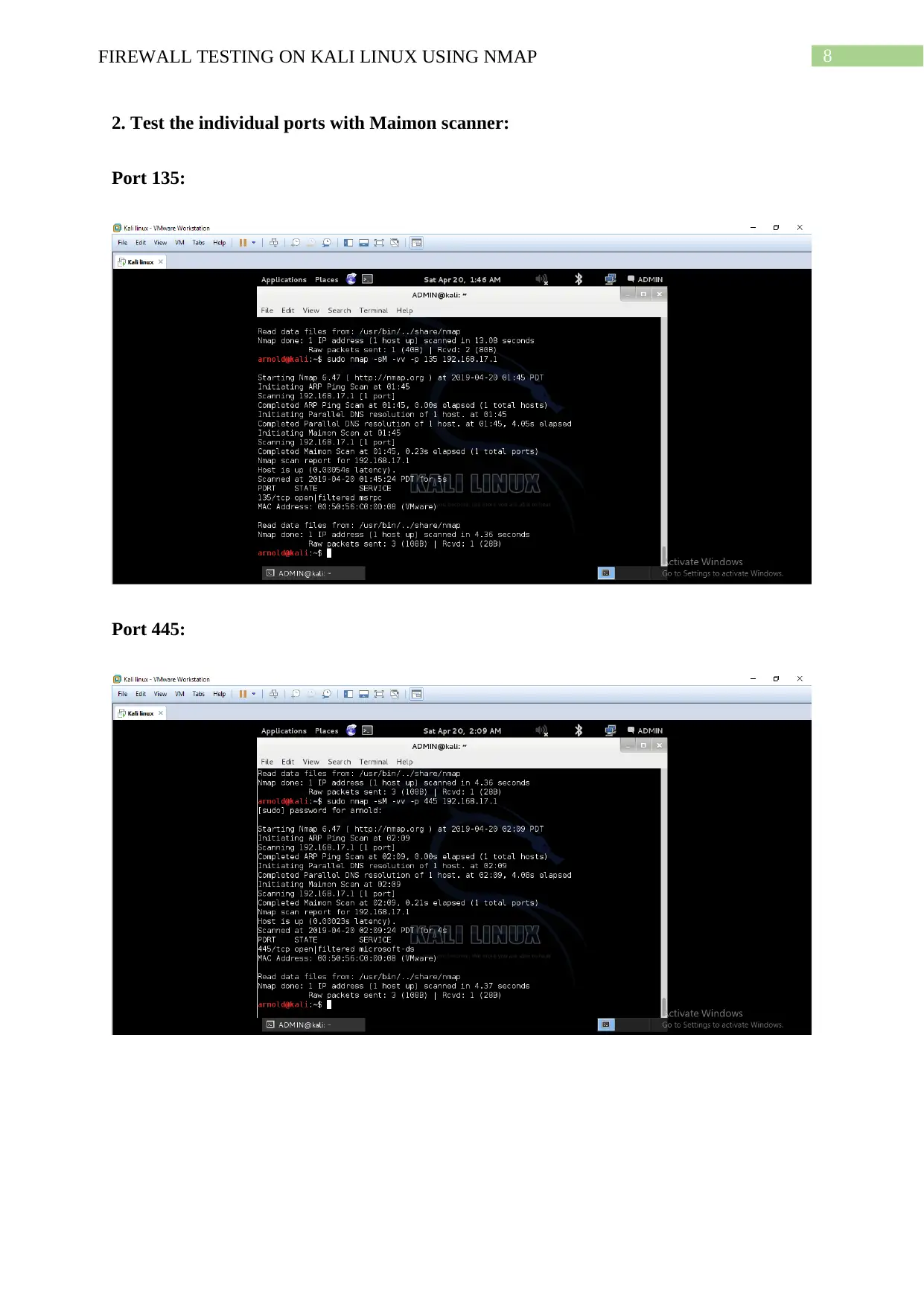
2. Test the individual ports with Maimon scanner:
Port 135:
Port 445:
2. Test the individual ports with Maimon scanner:
Port 135:
Port 445:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9FIREWALL TESTING ON KALI LINUX USING NMAP
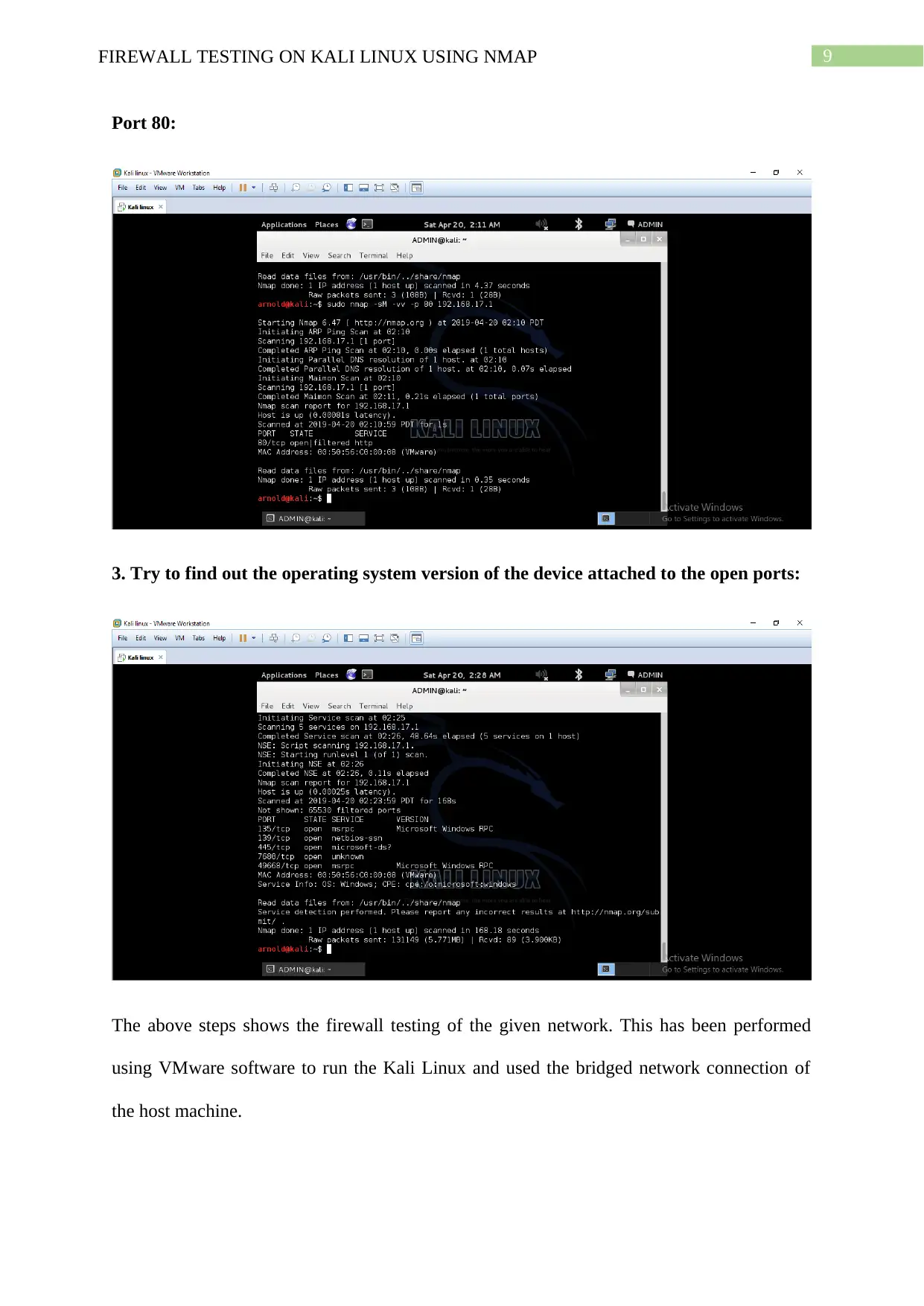
Port 80:
3. Try to find out the operating system version of the device attached to the open ports:
The above steps shows the firewall testing of the given network. This has been performed
using VMware software to run the Kali Linux and used the bridged network connection of
the host machine.
Port 80:
3. Try to find out the operating system version of the device attached to the open ports:
The above steps shows the firewall testing of the given network. This has been performed
using VMware software to run the Kali Linux and used the bridged network connection of
the host machine.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

10FIREWALL TESTING ON KALI LINUX USING NMAP
Performing the above steps will help the user detect the open ports visible in a
network through a given default firewall. The firewall in this operating system is quite weak
as it is designed for testing and security purposes. The user can then use the result to patch
the operating systems of the shown devices and secure the network by closing the above seen
open ports.
Mitigation plan
The threats that arises as seen from the given network scan can be mitigated by following the
mentioned steps:
1. The network should be patched and made more secure to limit the visibility of the other
devices connected to the network.
2. The firewall is the main shield against the internet. Therefore, the firewall should be
updated to make the penetration testing of the firewall useless.
3. The open ports are a big threat to the company as it exposes all the system device
information and network addresses. It even exposes the model number of the device.
Therefore, all the open ports must be closed to increase security.
Performing the above steps will help the user detect the open ports visible in a
network through a given default firewall. The firewall in this operating system is quite weak
as it is designed for testing and security purposes. The user can then use the result to patch
the operating systems of the shown devices and secure the network by closing the above seen
open ports.
Mitigation plan
The threats that arises as seen from the given network scan can be mitigated by following the
mentioned steps:
1. The network should be patched and made more secure to limit the visibility of the other
devices connected to the network.
2. The firewall is the main shield against the internet. Therefore, the firewall should be
updated to make the penetration testing of the firewall useless.
3. The open ports are a big threat to the company as it exposes all the system device
information and network addresses. It even exposes the model number of the device.
Therefore, all the open ports must be closed to increase security.
11FIREWALL TESTING ON KALI LINUX USING NMAP
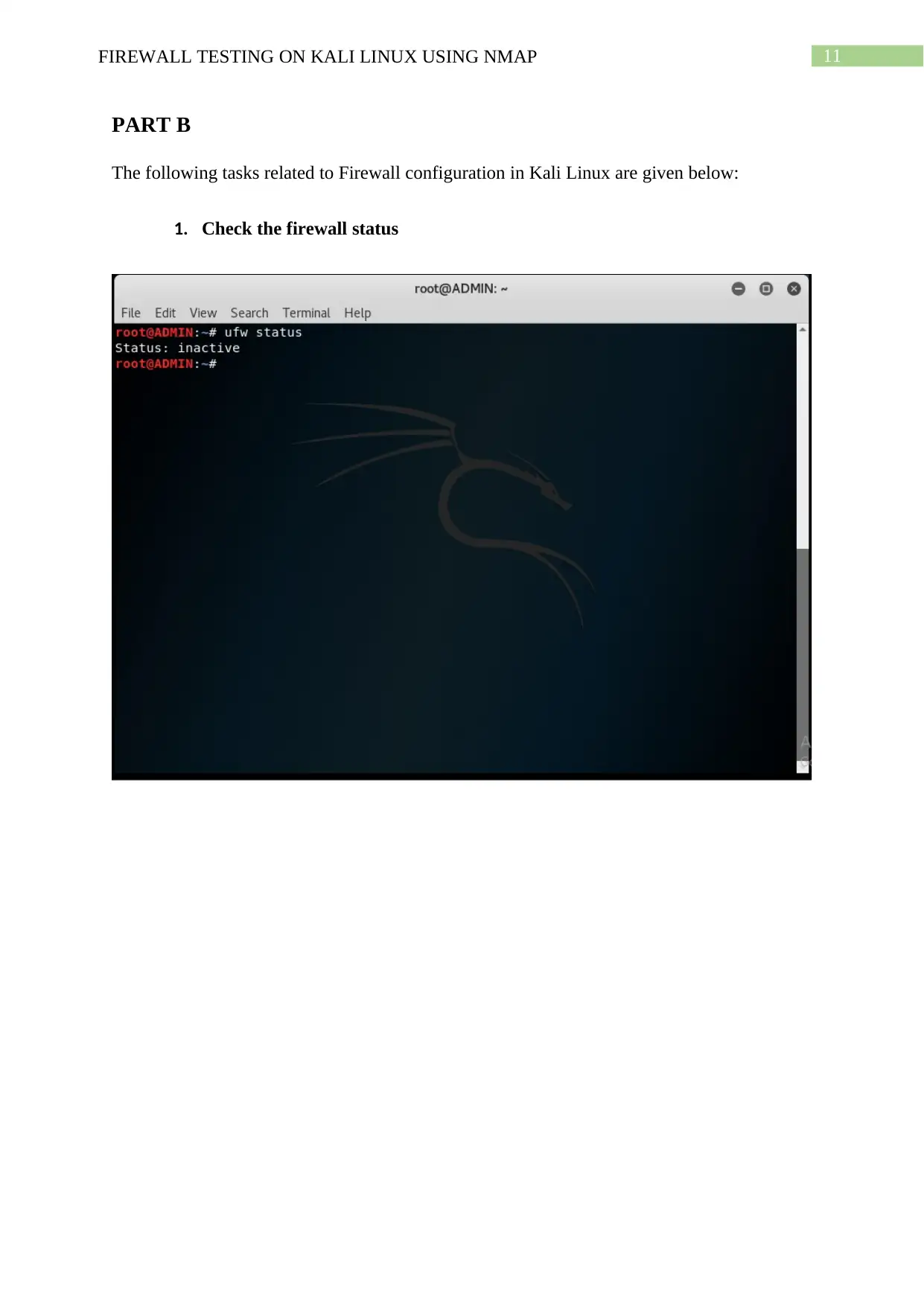
PART B
The following tasks related to Firewall configuration in Kali Linux are given below:
1. Check the firewall status
PART B
The following tasks related to Firewall configuration in Kali Linux are given below:
1. Check the firewall status
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




