Designing a Kerberos-Based Authentication Framework with Security
VerifiedAdded on 2022/08/27
|10
|1596
|33
Homework Assignment
AI Summary
This assignment explores the Kerberos authentication protocol, a robust network authentication method utilizing secret key cryptography. It begins with an overview of Kerberos, its integration in major operating systems, and its role in various applications, including broadband services. The assignment details the advantages of Kerberos, such as faster authentication, mutual authentication, and its open standard nature, while also addressing its disadvantages like password database migration and compatibility issues. The core of the assignment involves designing an authentication framework based on Kerberos, incorporating a real-life scenario and addressing potential security attacks. The design includes a diagram supporting the claims and is supported by authoritative sources with proper APA 6th referencing. The framework outlines client authentication steps and vulnerabilities, providing a comprehensive analysis of the protocol's functionality and security implications.

Running head: Kerberos
Kerberos
Name of the Student
Name of the University
Author Note
Kerberos
Name of the Student
Name of the University
Author Note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Kerberos 1
Table of Contents
Kerberos:....................................................................................................................................2
Advantages:............................................................................................................................2
Disadvantages:.......................................................................................................................3
User authentication with Kerberos:........................................................................................3
Kerberos framework:.............................................................................................................4
Vulnerabilities:.......................................................................................................................4
Client authentication:.............................................................................................................4
References:.................................................................................................................................6
Table of Contents
Kerberos:....................................................................................................................................2
Advantages:............................................................................................................................2
Disadvantages:.......................................................................................................................3
User authentication with Kerberos:........................................................................................3
Kerberos framework:.............................................................................................................4
Vulnerabilities:.......................................................................................................................4
Client authentication:.............................................................................................................4
References:.................................................................................................................................6

2Kerberos
Kerberos:
Kerberos is basically a network authentication protocol, it is designed for providing
authentication that is strong for the server or client by utilizing the secret key cryptography
method. Kerberos is built into all of the major operating systems that includes Apple OS X,
Windows, Linux and FreeBSD (Li et al, 2018). The Kerberos protocol has been incorporated
as an authentication method that is default in windows. This is one of the integral components
of the active type of directory services of windows. The providers of broadband service also
utilize the Kerberos for authenticating set top boxes and DOCSIS cable modems to access the
networks.
The main procedure is very much complicated as well as that can vary from one
implementation to other. For starting the Kerberos authentication procedure, the initiation
users send a request to another server for the authentication for getting access to a service
(Tbatou et al. 2017). The primary request is to be deliverd as plain text as there are no
sensitive information that are included in the request. The primary key of client can be
retrieved by the authentication server, by assuming that the user name of the initiating client
that is existed in the database of KDC. If the username of the initiating client can not be
found in the database of KDC, then the client will not be authenticated, in addition the
authentication procedure will be stop (Nath & Karforma, 2018). However, if the username of
the client might be found in the database of KDC then the authentication server may generate
a ticket granting ticket and a session key.
Advantages:
The advantages of Kerberos are as follows:
Faster authentication: A unique ticketing system is used by the Kerberos protocol which is
able to provide the authentication procedure faster.
Kerberos:
Kerberos is basically a network authentication protocol, it is designed for providing
authentication that is strong for the server or client by utilizing the secret key cryptography
method. Kerberos is built into all of the major operating systems that includes Apple OS X,
Windows, Linux and FreeBSD (Li et al, 2018). The Kerberos protocol has been incorporated
as an authentication method that is default in windows. This is one of the integral components
of the active type of directory services of windows. The providers of broadband service also
utilize the Kerberos for authenticating set top boxes and DOCSIS cable modems to access the
networks.
The main procedure is very much complicated as well as that can vary from one
implementation to other. For starting the Kerberos authentication procedure, the initiation
users send a request to another server for the authentication for getting access to a service
(Tbatou et al. 2017). The primary request is to be deliverd as plain text as there are no
sensitive information that are included in the request. The primary key of client can be
retrieved by the authentication server, by assuming that the user name of the initiating client
that is existed in the database of KDC. If the username of the initiating client can not be
found in the database of KDC, then the client will not be authenticated, in addition the
authentication procedure will be stop (Nath & Karforma, 2018). However, if the username of
the client might be found in the database of KDC then the authentication server may generate
a ticket granting ticket and a session key.
Advantages:
The advantages of Kerberos are as follows:
Faster authentication: A unique ticketing system is used by the Kerberos protocol which is
able to provide the authentication procedure faster.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3Kerberos
Each of the authentication domain entity is having the ability to request tickets from
the local Kerberos KDC for accessing resources of other domain.
The tickets can be considered as the access permits from the resource server.
The tickets can be utilized more than one time as well as they will be cached on the
side of the client.
Mutual authentication: Mutual authentication is supported by Kerberos. The meaning of this
is, the client can authenticate to the services that are having responsibilities for the source
(Nguyen & Dang, 2017). In addition, the service can also authenticate to the client.
Kerberos is an open standard: Kerberos is able to provide single sign on that is between the
windows server 2003 and some of the other Oss that supports Kerberos implementation that
based on RFC 1510.
Disadvantages:
The disadvantages of Kerberos authentication are as follows:
Password database: Kerberos can migrate the user password from the standard password
database of UNIX like / etc / passwd or / etc / shadow to one of the password database of
Kerberos can be tedious as no automatic mechanism is existed there for performing the task.
Compatibility: Kerberos is having a partial compatibility only with the PAM (Pluggable
Authentication Modules) system that is used by most of the servers that are running on Red
hat Linux.
Trusted hosts: It is assumed by the Kerberos that the user is using untrusted network or
trusted network (Shen, Ding & Ren, 2018, March). The main goal of Kerberos is preventing
the clear text passwords from sending across the network.
Each of the authentication domain entity is having the ability to request tickets from
the local Kerberos KDC for accessing resources of other domain.
The tickets can be considered as the access permits from the resource server.
The tickets can be utilized more than one time as well as they will be cached on the
side of the client.
Mutual authentication: Mutual authentication is supported by Kerberos. The meaning of this
is, the client can authenticate to the services that are having responsibilities for the source
(Nguyen & Dang, 2017). In addition, the service can also authenticate to the client.
Kerberos is an open standard: Kerberos is able to provide single sign on that is between the
windows server 2003 and some of the other Oss that supports Kerberos implementation that
based on RFC 1510.
Disadvantages:
The disadvantages of Kerberos authentication are as follows:
Password database: Kerberos can migrate the user password from the standard password
database of UNIX like / etc / passwd or / etc / shadow to one of the password database of
Kerberos can be tedious as no automatic mechanism is existed there for performing the task.
Compatibility: Kerberos is having a partial compatibility only with the PAM (Pluggable
Authentication Modules) system that is used by most of the servers that are running on Red
hat Linux.
Trusted hosts: It is assumed by the Kerberos that the user is using untrusted network or
trusted network (Shen, Ding & Ren, 2018, March). The main goal of Kerberos is preventing
the clear text passwords from sending across the network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4Kerberos
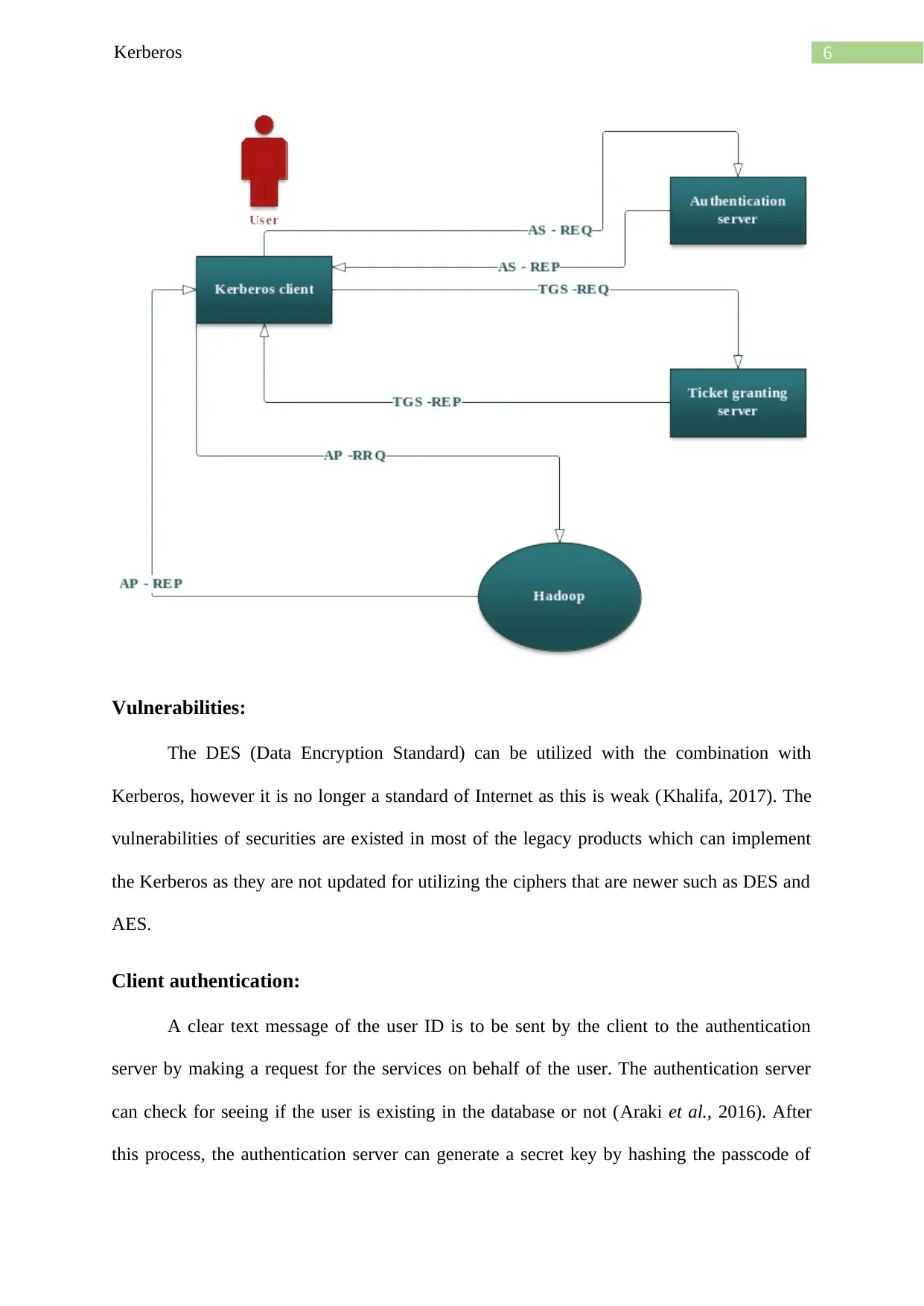
User authentication with Kerberos:
Below are some basic steps that can be taken for authenticating in the kerberized
environment.
An authentication ticket is requested by the client from the key distribution centre.
The credentials are verified by KDC and sends them back a session key and encrypted
TGT.
The TGT can be encrypted by utilizing the secret key of Ticket Granting Service.
The client can store the TGT as well as after expiring the local session manager will
request other TGT.
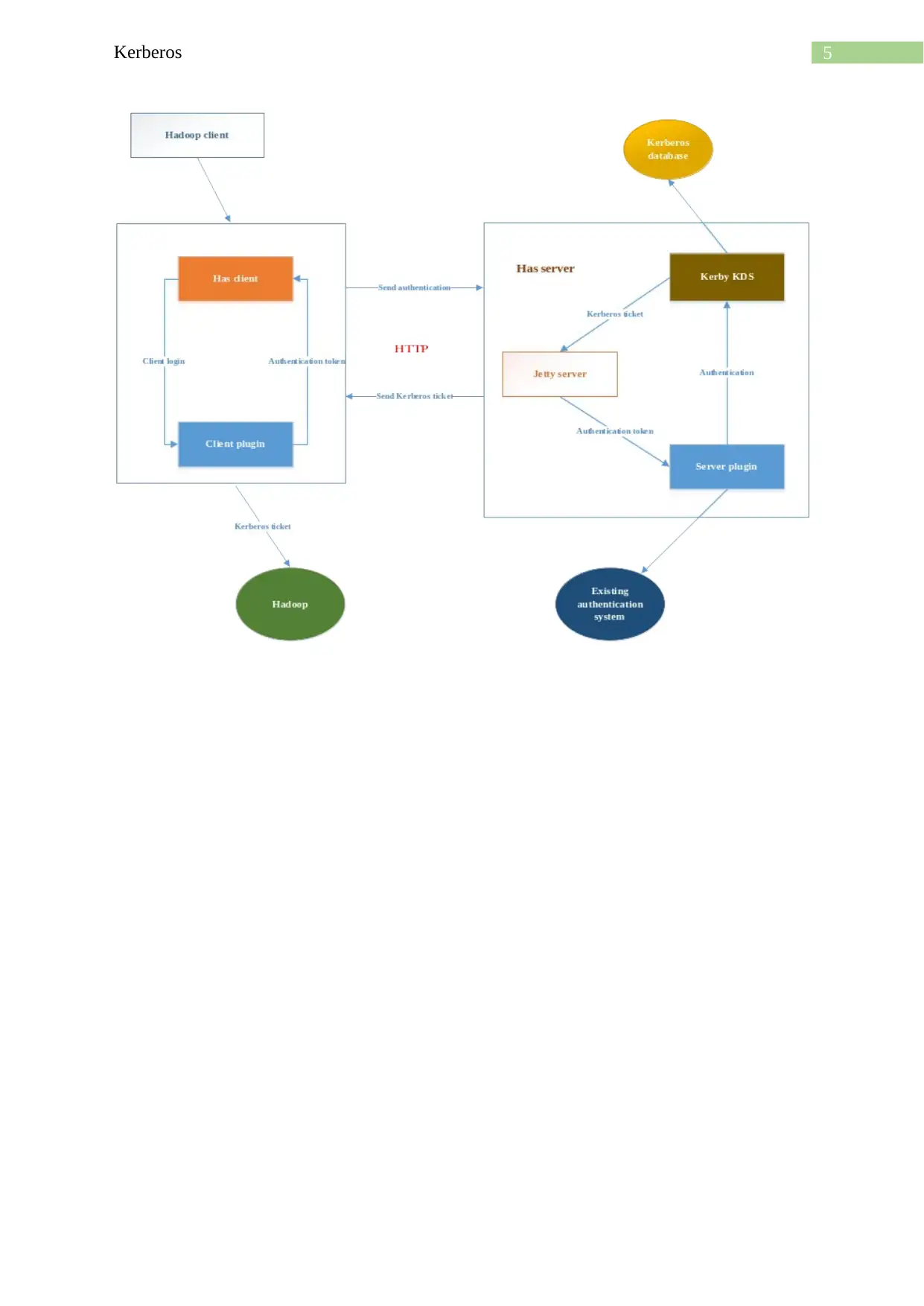
Kerberos framework:
The Kerberos framework is basically a match O framework that is included with the
Mac OS X 10.2 or later. The v4 and v5 protocols, KClient, GSSAPI as well as some of the
relatable libraries that are for the Kerberos ticket management, are provided by it. For using
the Kerberos framework, the user need to add Kerberos. Framework to the project as well as
the user need to include Kerberos.h as the header file (Sun & Gao, 2019). The client can
authenticate the authentication server that can forward the user name to the key distribution
centre. After this procedure, the KDC can issue a secret key of the ticket granting service as
well as then return the encrypted result to the workstation of the user. This process can be
done infrequently, the TGT will be expired at some of the point. Below is a Big Data Security
Solution Based on Kerberos.
User authentication with Kerberos:
Below are some basic steps that can be taken for authenticating in the kerberized
environment.
An authentication ticket is requested by the client from the key distribution centre.
The credentials are verified by KDC and sends them back a session key and encrypted
TGT.
The TGT can be encrypted by utilizing the secret key of Ticket Granting Service.
The client can store the TGT as well as after expiring the local session manager will
request other TGT.
Kerberos framework:
The Kerberos framework is basically a match O framework that is included with the
Mac OS X 10.2 or later. The v4 and v5 protocols, KClient, GSSAPI as well as some of the
relatable libraries that are for the Kerberos ticket management, are provided by it. For using
the Kerberos framework, the user need to add Kerberos. Framework to the project as well as
the user need to include Kerberos.h as the header file (Sun & Gao, 2019). The client can
authenticate the authentication server that can forward the user name to the key distribution
centre. After this procedure, the KDC can issue a secret key of the ticket granting service as
well as then return the encrypted result to the workstation of the user. This process can be
done infrequently, the TGT will be expired at some of the point. Below is a Big Data Security
Solution Based on Kerberos.
5Kerberos
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6Kerberos
Vulnerabilities:
The DES (Data Encryption Standard) can be utilized with the combination with
Kerberos, however it is no longer a standard of Internet as this is weak (Khalifa, 2017). The
vulnerabilities of securities are existed in most of the legacy products which can implement
the Kerberos as they are not updated for utilizing the ciphers that are newer such as DES and
AES.
Client authentication:
A clear text message of the user ID is to be sent by the client to the authentication
server by making a request for the services on behalf of the user. The authentication server
can check for seeing if the user is existing in the database or not (Araki et al., 2016). After
this process, the authentication server can generate a secret key by hashing the passcode of
Vulnerabilities:
The DES (Data Encryption Standard) can be utilized with the combination with
Kerberos, however it is no longer a standard of Internet as this is weak (Khalifa, 2017). The
vulnerabilities of securities are existed in most of the legacy products which can implement
the Kerberos as they are not updated for utilizing the ciphers that are newer such as DES and
AES.
Client authentication:
A clear text message of the user ID is to be sent by the client to the authentication
server by making a request for the services on behalf of the user. The authentication server
can check for seeing if the user is existing in the database or not (Araki et al., 2016). After
this process, the authentication server can generate a secret key by hashing the passcode of
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7Kerberos
the users that will be found in the database as well as then it will be sent back the messages to
the user, are given below:
Message A: TGS/Client Session key that is encrypted by using the secret key of the user or
client.
Message B: Ticket Granting Ticket that includes the ID of the client, network address of the
client, TGS or client session key, validity period of the ticket.
The time when a client will receive a message, the client will make an attempt for decrypting
the message A with the help of the secret key that is generated by the password which is
entered by the client (Kim & Lee, 2017). If a password will not match with the password that
is existed in the AS database. The secret key of the client will be different as well as they will
not be having the ability to decrypt the message.
the users that will be found in the database as well as then it will be sent back the messages to
the user, are given below:
Message A: TGS/Client Session key that is encrypted by using the secret key of the user or
client.
Message B: Ticket Granting Ticket that includes the ID of the client, network address of the
client, TGS or client session key, validity period of the ticket.
The time when a client will receive a message, the client will make an attempt for decrypting
the message A with the help of the secret key that is generated by the password which is
entered by the client (Kim & Lee, 2017). If a password will not match with the password that
is existed in the AS database. The secret key of the client will be different as well as they will
not be having the ability to decrypt the message.

8Kerberos
References:
Araki, T., Barak, A., Furukawa, J., Lindell, Y., Nof, A., & Ohara, K. (2016, October). High-
Throughput Secure Three-Party Computation of Kerberos Ticket Generation. In Proceedings
of the 2016 ACM SIGSAC Conference on Computer and Communications Security (pp. 1841-
1843). ACM.
Khalifa, M. (2017). ENHANCED KERBEROS AUTHENTICATION FOR DISTRIBUTED
ENVIRONMENT USING TWO PHASES SECURITY. Compusoft, 6(4), 2323.
Kim, H., & Lee, E. A. (2017). Authentication and Authorization for the Internet of Things. IT
Professional, 19(5), 27-33.
Li, H., Niu, Y., Yi, J., & Li, H. (2018). Securing offline delivery services by using Kerberos
authentication. IEEE Access, 6, 40735-40746.
Nath, M. D., & Karforma, S. (2018). Object-Oriented Modelling Of Kerberos Based
Authentication Process In E-Banking Transaction.
Nguyen, T. A. T., & Dang, T. K. (2017). Protecting biometrics using fuzzy extractor and non-
invertible transformation methods in Kerberos authentication protocol. In Transactions on
Large-Scale Data-and Knowledge-Centered Systems XXXI (pp. 47-66). Springer, Berlin,
Heidelberg.
Shen, P., Ding, X., & Ren, W. (2018, March). Research on Kerberos Technology Based on
Hadoop Cluster Security. In 2018 2nd International Conference on Advances in Energy,
Environment and Chemical Science (AEECS 2018). Atlantis Press.
Sun, J., & Gao, Z. (2019). Improved Mobile Application Security Mechanism based on
Kerberos.
References:
Araki, T., Barak, A., Furukawa, J., Lindell, Y., Nof, A., & Ohara, K. (2016, October). High-
Throughput Secure Three-Party Computation of Kerberos Ticket Generation. In Proceedings
of the 2016 ACM SIGSAC Conference on Computer and Communications Security (pp. 1841-
1843). ACM.
Khalifa, M. (2017). ENHANCED KERBEROS AUTHENTICATION FOR DISTRIBUTED
ENVIRONMENT USING TWO PHASES SECURITY. Compusoft, 6(4), 2323.
Kim, H., & Lee, E. A. (2017). Authentication and Authorization for the Internet of Things. IT
Professional, 19(5), 27-33.
Li, H., Niu, Y., Yi, J., & Li, H. (2018). Securing offline delivery services by using Kerberos
authentication. IEEE Access, 6, 40735-40746.
Nath, M. D., & Karforma, S. (2018). Object-Oriented Modelling Of Kerberos Based
Authentication Process In E-Banking Transaction.
Nguyen, T. A. T., & Dang, T. K. (2017). Protecting biometrics using fuzzy extractor and non-
invertible transformation methods in Kerberos authentication protocol. In Transactions on
Large-Scale Data-and Knowledge-Centered Systems XXXI (pp. 47-66). Springer, Berlin,
Heidelberg.
Shen, P., Ding, X., & Ren, W. (2018, March). Research on Kerberos Technology Based on
Hadoop Cluster Security. In 2018 2nd International Conference on Advances in Energy,
Environment and Chemical Science (AEECS 2018). Atlantis Press.
Sun, J., & Gao, Z. (2019). Improved Mobile Application Security Mechanism based on
Kerberos.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9Kerberos
Tbatou, Z., Asimi, A., Asimi, Y., Sadqi, Y., & Guezzaz, A. (2017). A New Mutuel Kerberos
Authentication Protocol for Distributed Systems. IJ Network Security, 19(6), 889-898.
Tbatou, Z., Asimi, A., Asimi, Y., Sadqi, Y., & Guezzaz, A. (2017). A New Mutuel Kerberos
Authentication Protocol for Distributed Systems. IJ Network Security, 19(6), 889-898.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



