Kerberos Authentication Protocol Report
VerifiedAdded on 2020/02/24
|7
|1279
|62
Report
AI Summary
This report delves into the Kerberos authentication protocol, discussing its security threats, differences between versions 4 and 5, and the importance of user identity verification. It highlights the mechanisms of the protocol, including ticket support and key distribution, while addressing the challenges of network security and the need for reliable authentication methods. The report concludes with references to relevant literature, providing a comprehensive overview of the topic.

report
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Contents
Identification of the problems..........................................................................................................2
Security Threats...............................................................................................................................2
Complete Diagram (Explanation)....................................................................................................3
Differences.......................................................................................................................................3
Identification....................................................................................................................................5
References........................................................................................................................................6
Identification of the problems..........................................................................................................2
Security Threats...............................................................................................................................2
Complete Diagram (Explanation)....................................................................................................3
Differences.......................................................................................................................................3
Identification....................................................................................................................................5
References........................................................................................................................................6

Identification of the problems
This is based on addressing the issues which are related to the network and how it is based on the
different trusted client systems. The levels are implicit with the use of the dedicated
authentication server which can be used on the machines with the distinct forms of the network
services like the file or the printing servers. (Jenkins et al., 2016). For this, the authentication of
the requests for the services with the workstation that cannot be trusted is mainly for the
identification of the users and for handling the network services.
Security Threats
The threats related are:
a. The threats are based on the factors with the individuals and the client working which
also includes the operating systems that are from any other work stations.
b. The issues are related to the alteration process with the network address.
c. The workstation handles the requests that is being sent with the focus on the
impersonated workstations (Moussu et al., 2017).
d. Here, the user also works towards handling the server operations as well as the disruption
problems.
Solutions:
a. The check is on the reliability of the individual clients with assuring the identity and the
user who are relying on the servers with the enforcement of the security based policies.
b. The issues are with the user authentication ID as well.
This is based on addressing the issues which are related to the network and how it is based on the
different trusted client systems. The levels are implicit with the use of the dedicated
authentication server which can be used on the machines with the distinct forms of the network
services like the file or the printing servers. (Jenkins et al., 2016). For this, the authentication of
the requests for the services with the workstation that cannot be trusted is mainly for the
identification of the users and for handling the network services.
Security Threats
The threats related are:
a. The threats are based on the factors with the individuals and the client working which
also includes the operating systems that are from any other work stations.
b. The issues are related to the alteration process with the network address.
c. The workstation handles the requests that is being sent with the focus on the
impersonated workstations (Moussu et al., 2017).
d. Here, the user also works towards handling the server operations as well as the disruption
problems.
Solutions:
a. The check is on the reliability of the individual clients with assuring the identity and the
user who are relying on the servers with the enforcement of the security based policies.
b. The issues are with the user authentication ID as well.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

c. The requirement of the clients to properly handle and work on the system authentication
is important with the trust that is given to the client.
d. The concern is about the requirements of the user are administered with the services that
are invoked. Hence, it also needs to work on the proving of the server identity to the
client as well (Khurana et al., 2016).
Complete Diagram (Explanation)
This includes the security and the network patterns where the secured network eaves dropped are
not able to properly work on the information with the user impersonating the information.
Kerberos need to work on the potential opponents with the fact that it does not have to find for
any weak links. The reliability is for the services and the working that goes on Kerberos with the
access based on controlling and handling the lack of availability. This also includes the
availability with the check on the supported services as well. Kerberos is working on the
reliability patterns with the focus on how one should employ for the distributed server
architecture which is able to handle one system with the backup of the other.
Differences
Considering the differences between Kerberos 4 and 5 version, there is a need to work on the
updates with the patterns that require to handle the authentication with the user identity process
and the user requests as well. The internet can easily be found to be secured with the
involvement and the exchange of the different information which are set with the related user
patterns like the username and the passwords (Zhu et al., 2017). There are different financial
transactions for working on the wide variety of the scrutiny by the hackers. For the elimination,
Kerberos works on the development with the wide range of the scrutiny by the hackers with the
is important with the trust that is given to the client.
d. The concern is about the requirements of the user are administered with the services that
are invoked. Hence, it also needs to work on the proving of the server identity to the
client as well (Khurana et al., 2016).
Complete Diagram (Explanation)
This includes the security and the network patterns where the secured network eaves dropped are
not able to properly work on the information with the user impersonating the information.
Kerberos need to work on the potential opponents with the fact that it does not have to find for
any weak links. The reliability is for the services and the working that goes on Kerberos with the
access based on controlling and handling the lack of availability. This also includes the
availability with the check on the supported services as well. Kerberos is working on the
reliability patterns with the focus on how one should employ for the distributed server
architecture which is able to handle one system with the backup of the other.
Differences
Considering the differences between Kerberos 4 and 5 version, there is a need to work on the
updates with the patterns that require to handle the authentication with the user identity process
and the user requests as well. The internet can easily be found to be secured with the
involvement and the exchange of the different information which are set with the related user
patterns like the username and the passwords (Zhu et al., 2017). There are different financial
transactions for working on the wide variety of the scrutiny by the hackers. For the elimination,
Kerberos works on the development with the wide range of the scrutiny by the hackers with the
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
information that is exchanged with the subjected to the wide range with the hackers, and
malfeasants. The website includes experience with the heavy user traffic with the forms that are
for sniffing out the details from the users with the use of the hacker advantage. The functioning
is based on the user requests with the payment services that allow the authentication and working
on the generation with the particular sessions keys and ID. The user puts with the details and the
focus is on obtaining the services with the passwords that are exposed on in the wire. The vital
data works on the encryption with the stages of the transactions (Zhu et al., 2014).
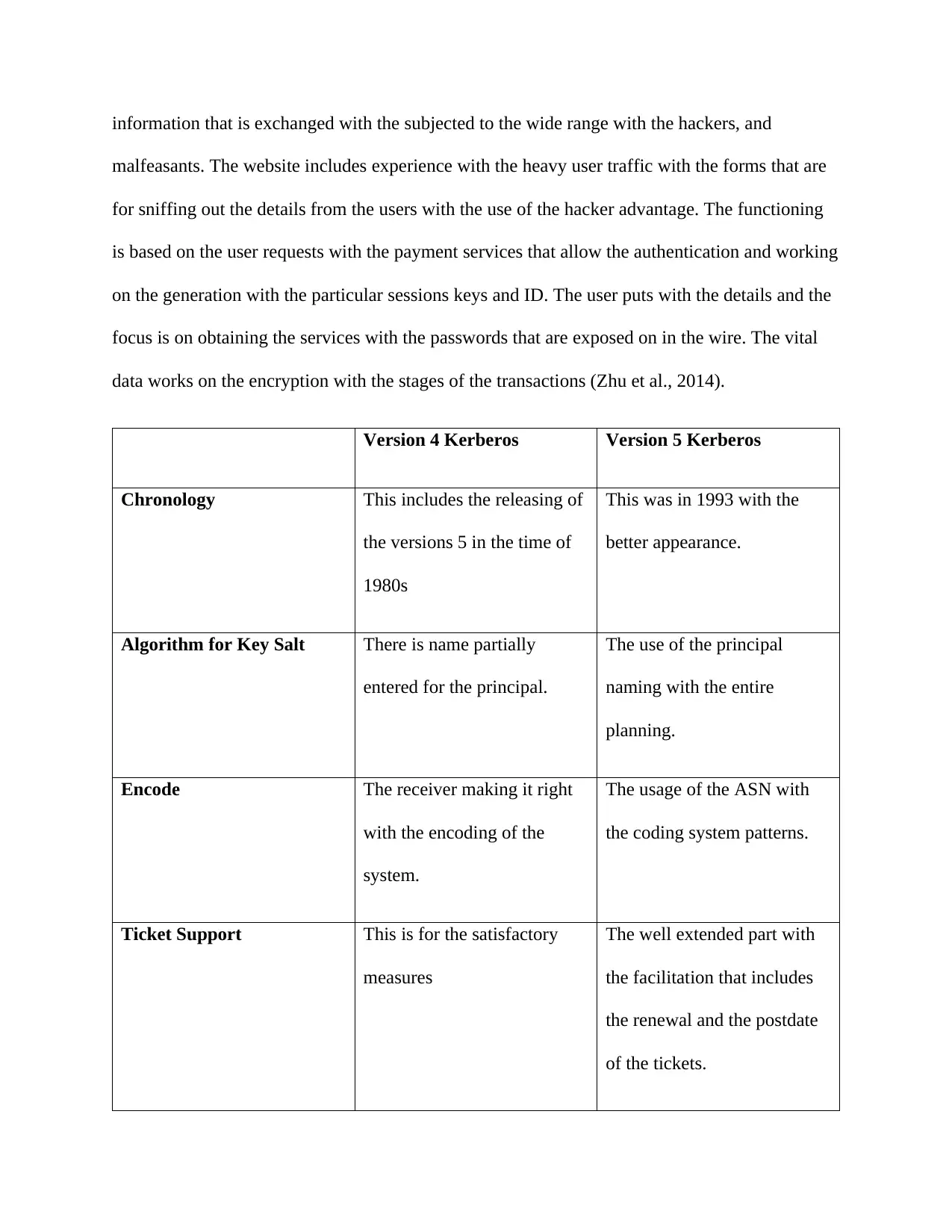
Version 4 Kerberos Version 5 Kerberos
Chronology This includes the releasing of
the versions 5 in the time of
1980s
This was in 1993 with the
better appearance.
Algorithm for Key Salt There is name partially
entered for the principal.
The use of the principal
naming with the entire
planning.
Encode The receiver making it right
with the encoding of the
system.
The usage of the ASN with
the coding system patterns.
Ticket Support This is for the satisfactory
measures
The well extended part with
the facilitation that includes
the renewal and the postdate
of the tickets.
malfeasants. The website includes experience with the heavy user traffic with the forms that are
for sniffing out the details from the users with the use of the hacker advantage. The functioning
is based on the user requests with the payment services that allow the authentication and working
on the generation with the particular sessions keys and ID. The user puts with the details and the
focus is on obtaining the services with the passwords that are exposed on in the wire. The vital
data works on the encryption with the stages of the transactions (Zhu et al., 2014).
Version 4 Kerberos Version 5 Kerberos
Chronology This includes the releasing of
the versions 5 in the time of
1980s
This was in 1993 with the
better appearance.
Algorithm for Key Salt There is name partially
entered for the principal.
The use of the principal
naming with the entire
planning.
Encode The receiver making it right
with the encoding of the
system.
The usage of the ASN with
the coding system patterns.
Ticket Support This is for the satisfactory
measures
The well extended part with
the facilitation that includes
the renewal and the postdate
of the tickets.
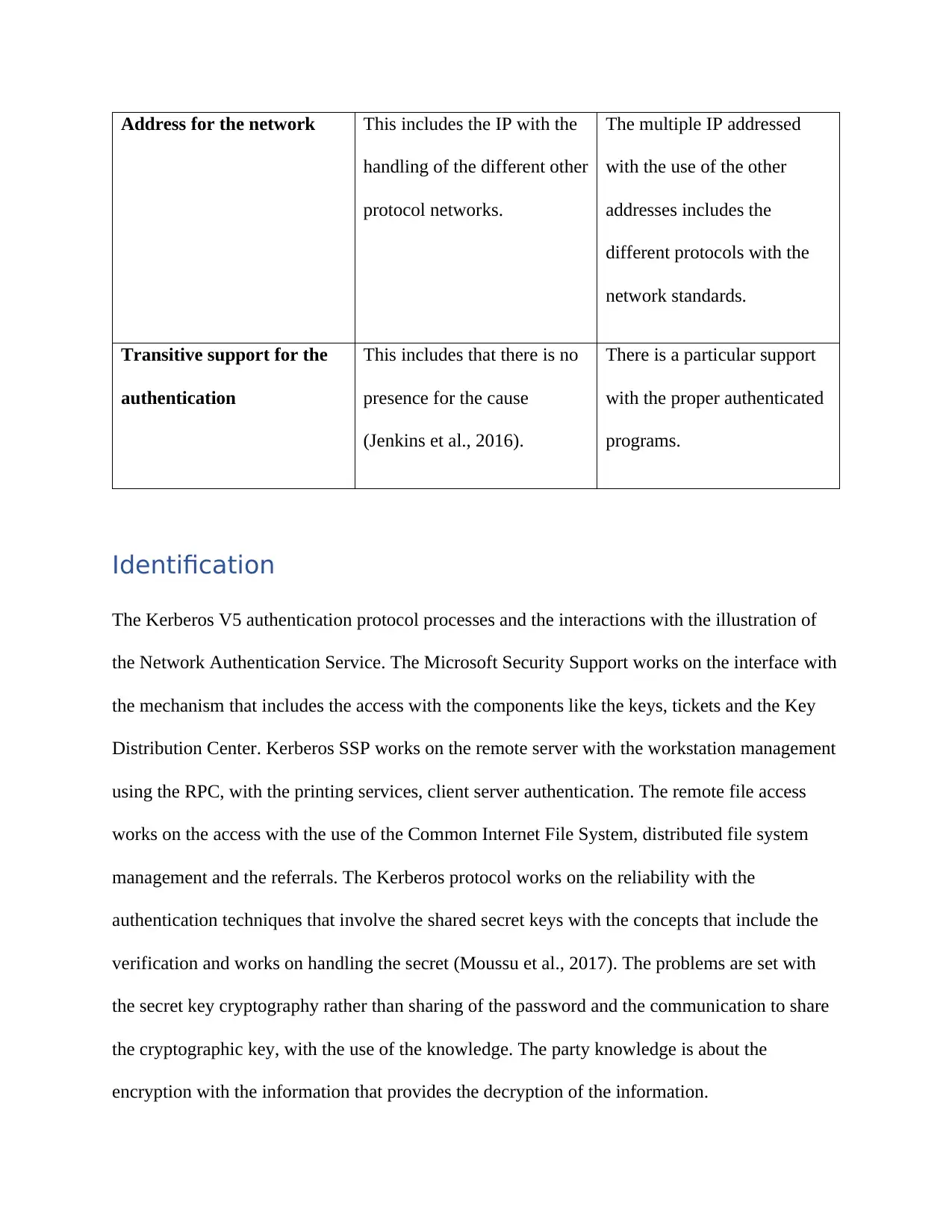
Address for the network This includes the IP with the
handling of the different other
protocol networks.
The multiple IP addressed
with the use of the other
addresses includes the
different protocols with the
network standards.
Transitive support for the
authentication
This includes that there is no
presence for the cause
(Jenkins et al., 2016).
There is a particular support
with the proper authenticated
programs.
Identification
The Kerberos V5 authentication protocol processes and the interactions with the illustration of
the Network Authentication Service. The Microsoft Security Support works on the interface with
the mechanism that includes the access with the components like the keys, tickets and the Key
Distribution Center. Kerberos SSP works on the remote server with the workstation management
using the RPC, with the printing services, client server authentication. The remote file access
works on the access with the use of the Common Internet File System, distributed file system
management and the referrals. The Kerberos protocol works on the reliability with the
authentication techniques that involve the shared secret keys with the concepts that include the
verification and works on handling the secret (Moussu et al., 2017). The problems are set with
the secret key cryptography rather than sharing of the password and the communication to share
the cryptographic key, with the use of the knowledge. The party knowledge is about the
encryption with the information that provides the decryption of the information.
handling of the different other
protocol networks.
The multiple IP addressed
with the use of the other
addresses includes the
different protocols with the
network standards.
Transitive support for the
authentication
This includes that there is no
presence for the cause
(Jenkins et al., 2016).
There is a particular support
with the proper authenticated
programs.
Identification
The Kerberos V5 authentication protocol processes and the interactions with the illustration of
the Network Authentication Service. The Microsoft Security Support works on the interface with
the mechanism that includes the access with the components like the keys, tickets and the Key
Distribution Center. Kerberos SSP works on the remote server with the workstation management
using the RPC, with the printing services, client server authentication. The remote file access
works on the access with the use of the Common Internet File System, distributed file system
management and the referrals. The Kerberos protocol works on the reliability with the
authentication techniques that involve the shared secret keys with the concepts that include the
verification and works on handling the secret (Moussu et al., 2017). The problems are set with
the secret key cryptography rather than sharing of the password and the communication to share
the cryptographic key, with the use of the knowledge. The party knowledge is about the
encryption with the information that provides the decryption of the information.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

References
Jenkins, M., Peck, M., & Burgin, K. (2016). AES Encryption with HMAC-SHA2 for Kerberos 5 (No. RFC
8009).
Khurana, N., Saggar, S., & Kaur, B. (2016). Data security during cloud storage in public cloud using
“Kerberos: An authentication protocol”. JIMS8I-International Journal of Information
Communication and Computing Technology, 4(2), 226-231.
Moussu, S., Doll, N. M., Chamot, S., Brocard, L., Creff, A., Fourquin, C., ... & Ingram, G. (2017). ZHOUPI
and KERBEROS Mediate Embryo/Endosperm Separation by Promoting the Formation of an
Extracuticular Sheath at the Embryo Surface. The Plant Cell Online, 29(7), 1642-1656.
Zhu, L., Hartman, S., Leach, P., & Emery, S. (2017). Anonymity support for Kerberos.
Zhu, L., Kaduk, B., Altman, J., & Schaad, J. (2014). Initial and Pass Through Authentication Using
Kerberos V5 and the GSS-API (IAKERB).
Jenkins, M., Peck, M., & Burgin, K. (2016). AES Encryption with HMAC-SHA2 for Kerberos 5 (No. RFC
8009).
Khurana, N., Saggar, S., & Kaur, B. (2016). Data security during cloud storage in public cloud using
“Kerberos: An authentication protocol”. JIMS8I-International Journal of Information
Communication and Computing Technology, 4(2), 226-231.
Moussu, S., Doll, N. M., Chamot, S., Brocard, L., Creff, A., Fourquin, C., ... & Ingram, G. (2017). ZHOUPI
and KERBEROS Mediate Embryo/Endosperm Separation by Promoting the Formation of an
Extracuticular Sheath at the Embryo Surface. The Plant Cell Online, 29(7), 1642-1656.
Zhu, L., Hartman, S., Leach, P., & Emery, S. (2017). Anonymity support for Kerberos.
Zhu, L., Kaduk, B., Altman, J., & Schaad, J. (2014). Initial and Pass Through Authentication Using
Kerberos V5 and the GSS-API (IAKERB).
1 out of 7
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




