CP5603 Research Report: Comparing Hardware and Software Keyloggers
VerifiedAdded on 2022/09/06
|23
|4387
|19
Report
AI Summary
This research report provides a detailed comparison between hardware and software keyloggers, crucial tools for monitoring keystrokes and potentially compromising data security. The report begins with an introduction to keyloggers, explaining their functionality and the threats they pose, including the ability to capture sensitive information like passwords and financial data. It then delves into the two main types: hardware keyloggers, which are physical devices, and software keyloggers, which are applications. The report explores the features of keyloggers, such as keystroke logging, clipboard recording, and website tracking. It elaborates on various types of hardware keyloggers (regular, wireless sniffers, firmware, and keyboard overlays) and software keyloggers (hypervisor-based, kernel-based, API-based, form-grabbing, memory injection, and packet analyzer). The report also discusses the characteristics of hardware keyloggers, reported incidents, and the threats associated with both types. A significant portion of the report is dedicated to comparing hardware and software keyloggers across various aspects, including detectability, portability, security, and complexity. Finally, it concludes with a recommendation for data-oriented companies, advocating for the use of hardware keyloggers due to their advantages. The report is a valuable resource for understanding the nuances of keyloggers and making informed decisions about data security.

Research Report On
“Hardware Keylogger or Software
Keylogger?”
Submitted To:
Submitted By:
Abstract
1
“Hardware Keylogger or Software
Keylogger?”
Submitted To:
Submitted By:
Abstract
1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Essentially, key loggers are the ability to record computer keystrokes. Key loggers are a
serious threat to users because they can track all sensitive data entered from the keyboard,
such as passwords, PINs, and account numbers. When a hacker accesses your personal or
sensitive information, the extracted data can be used to conduct online cash transactions with
your account. Key loggers may be used as spy tools that infringe on data in businesses and
state enterprises.
There are two types of key loggers: hardware and software key loggers. A hardware key
logger is a physical device that can be directly connected to a computer to record the keys
pressed on the computer's keyboard. Software key loggers, on the other hand, are applications
that are installed on computers or mobile devices.
After comparing both types of Keyloggers, Hardware keylogger is best suited for the data-
oriented company to use for the recording and monitoring purposes. I strongly recommend
using the hardware keylogger because of its pros over the software Keyloggers.
2
serious threat to users because they can track all sensitive data entered from the keyboard,
such as passwords, PINs, and account numbers. When a hacker accesses your personal or
sensitive information, the extracted data can be used to conduct online cash transactions with
your account. Key loggers may be used as spy tools that infringe on data in businesses and
state enterprises.
There are two types of key loggers: hardware and software key loggers. A hardware key
logger is a physical device that can be directly connected to a computer to record the keys
pressed on the computer's keyboard. Software key loggers, on the other hand, are applications
that are installed on computers or mobile devices.
After comparing both types of Keyloggers, Hardware keylogger is best suited for the data-
oriented company to use for the recording and monitoring purposes. I strongly recommend
using the hardware keylogger because of its pros over the software Keyloggers.
2

Contents
Introduction.........................................................................................................................................4
How Keylogger works?.......................................................................................................................6
Features of Keyloggers........................................................................................................................7
Types of Keyloggers............................................................................................................................9
Hardware Keyloggers..................................................................................................................9
Types of Hardware Keyloggers..................................................................................................9
1. Regular Hardware Keylogger.............................................................................................9
2. Wireless Keylogger Sniffers................................................................................................9
3. Firmware............................................................................................................................10
4. Keyboard overlays.............................................................................................................10
Software Keyloggers..................................................................................................................10
Types of Software Keyloggers...................................................................................................10
1. Hypervisor-based...............................................................................................................10
2. Kernel-based......................................................................................................................10
3. API-based...........................................................................................................................11
4. Form-grabbing based........................................................................................................11
5. Memory Injection based....................................................................................................11
6. Packet analyser..................................................................................................................11
Characteristics of Hardware Keyloggers.........................................................................................12
Reported Incidents of Keylogger......................................................................................................14
Threat of a Keylogger........................................................................................................................16
Difference between Hardware and Software Keyloggers...............................................................17
1. Detect ability......................................................................................................................17
2. Time Consumable..............................................................................................................17
3. Non-volatile memory.........................................................................................................17
4. Portability...........................................................................................................................18
5. Security...............................................................................................................................18
6. Complexity.........................................................................................................................18
Recommendations..............................................................................................................................19
References..........................................................................................................................................21
3
Introduction.........................................................................................................................................4
How Keylogger works?.......................................................................................................................6
Features of Keyloggers........................................................................................................................7
Types of Keyloggers............................................................................................................................9
Hardware Keyloggers..................................................................................................................9
Types of Hardware Keyloggers..................................................................................................9
1. Regular Hardware Keylogger.............................................................................................9
2. Wireless Keylogger Sniffers................................................................................................9
3. Firmware............................................................................................................................10
4. Keyboard overlays.............................................................................................................10
Software Keyloggers..................................................................................................................10
Types of Software Keyloggers...................................................................................................10
1. Hypervisor-based...............................................................................................................10
2. Kernel-based......................................................................................................................10
3. API-based...........................................................................................................................11
4. Form-grabbing based........................................................................................................11
5. Memory Injection based....................................................................................................11
6. Packet analyser..................................................................................................................11
Characteristics of Hardware Keyloggers.........................................................................................12
Reported Incidents of Keylogger......................................................................................................14
Threat of a Keylogger........................................................................................................................16
Difference between Hardware and Software Keyloggers...............................................................17
1. Detect ability......................................................................................................................17
2. Time Consumable..............................................................................................................17
3. Non-volatile memory.........................................................................................................17
4. Portability...........................................................................................................................18
5. Security...............................................................................................................................18
6. Complexity.........................................................................................................................18
Recommendations..............................................................................................................................19
References..........................................................................................................................................21
3
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
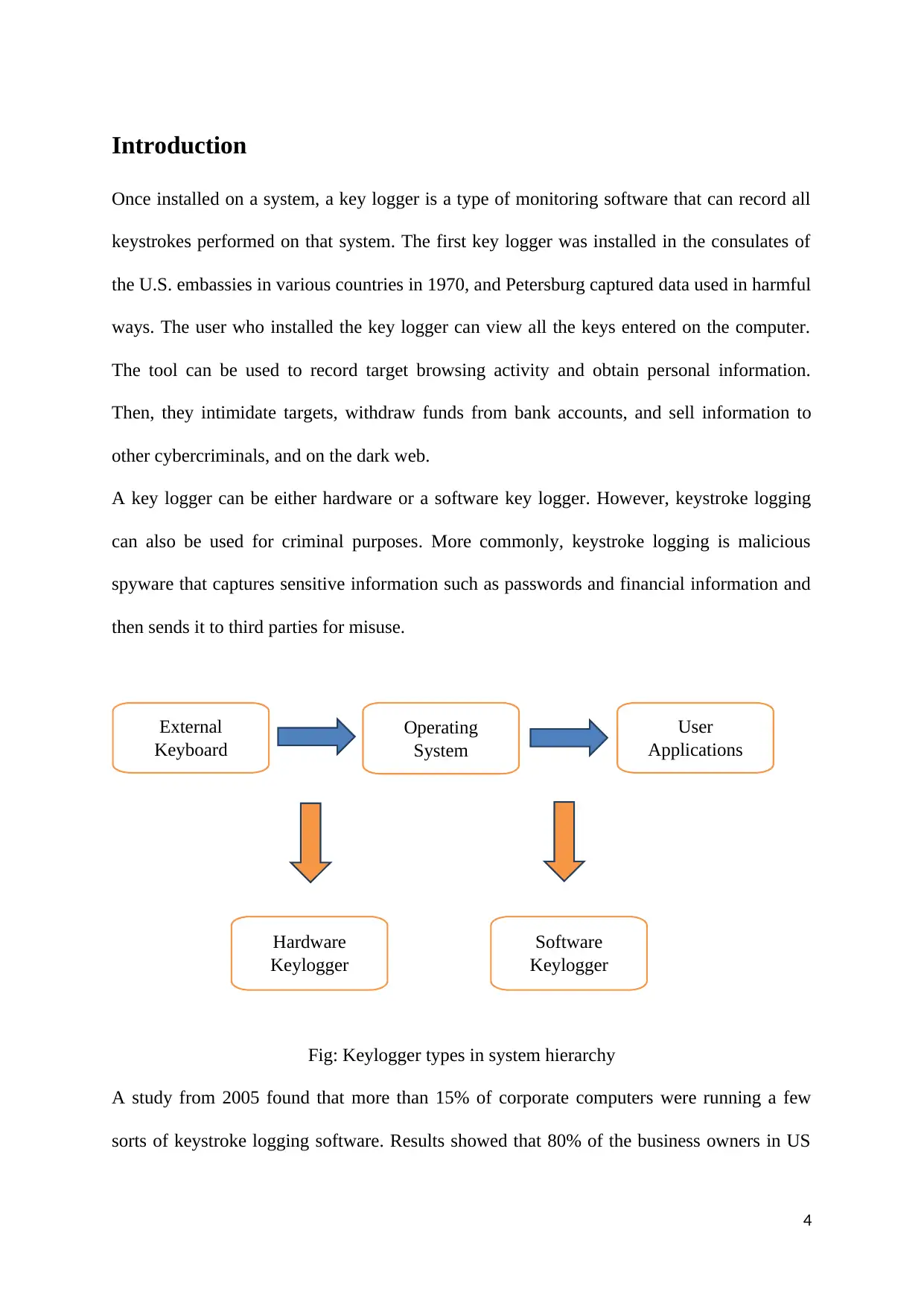
Introduction
Once installed on a system, a key logger is a type of monitoring software that can record all
keystrokes performed on that system. The first key logger was installed in the consulates of
the U.S. embassies in various countries in 1970, and Petersburg captured data used in harmful
ways. The user who installed the key logger can view all the keys entered on the computer.
The tool can be used to record target browsing activity and obtain personal information.
Then, they intimidate targets, withdraw funds from bank accounts, and sell information to
other cybercriminals, and on the dark web.
A key logger can be either hardware or a software key logger. However, keystroke logging
can also be used for criminal purposes. More commonly, keystroke logging is malicious
spyware that captures sensitive information such as passwords and financial information and
then sends it to third parties for misuse.
Fig: Keylogger types in system hierarchy
A study from 2005 found that more than 15% of corporate computers were running a few
sorts of keystroke logging software. Results showed that 80% of the business owners in US
4
External
Keyboard
Hardware
Keylogger
Software
Keylogger
Operating
System
User
Applications
Once installed on a system, a key logger is a type of monitoring software that can record all
keystrokes performed on that system. The first key logger was installed in the consulates of
the U.S. embassies in various countries in 1970, and Petersburg captured data used in harmful
ways. The user who installed the key logger can view all the keys entered on the computer.
The tool can be used to record target browsing activity and obtain personal information.
Then, they intimidate targets, withdraw funds from bank accounts, and sell information to
other cybercriminals, and on the dark web.
A key logger can be either hardware or a software key logger. However, keystroke logging
can also be used for criminal purposes. More commonly, keystroke logging is malicious
spyware that captures sensitive information such as passwords and financial information and
then sends it to third parties for misuse.
Fig: Keylogger types in system hierarchy
A study from 2005 found that more than 15% of corporate computers were running a few
sorts of keystroke logging software. Results showed that 80% of the business owners in US
4
External
Keyboard
Hardware
Keylogger
Software
Keylogger
Operating
System
User
Applications
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

have been found using Keyloggers to check their employees’ movement but nowadays use of
Keyloggers have been sky rocketed by much more than before (Adhikary et al., 2012).
5
Keyloggers have been sky rocketed by much more than before (Adhikary et al., 2012).
5

How Keylogger works?
Software Keylogger
Once the keylogger is installed, it starts operating in the background (in a stealth mode) and
captures every keystroke of the target device.
Let’s take up a small example:
If you are the target and you opens the http://facebook.com and types “username” and
“password” for the log in. The keylogger records your username and password silently. The
person who installed the keylogger in your computer can misuse the data and can make
trouble for you in the future.
Hardware Keyloggers
The hardware Keyloggers must be plugged in the computer system either in the
keyboard or in the operating system. They record every stroke of the user and send
it to the person who plugged the keylogger.
6
Software Keylogger
Once the keylogger is installed, it starts operating in the background (in a stealth mode) and
captures every keystroke of the target device.
Let’s take up a small example:
If you are the target and you opens the http://facebook.com and types “username” and
“password” for the log in. The keylogger records your username and password silently. The
person who installed the keylogger in your computer can misuse the data and can make
trouble for you in the future.
Hardware Keyloggers
The hardware Keyloggers must be plugged in the computer system either in the
keyboard or in the operating system. They record every stroke of the user and send
it to the person who plugged the keylogger.
6
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Features of Keyloggers
Here is a list of features of Keyloggers.
1. Keystrokes Logging
After the installation of keylogger, it records all the key strokes in the log and sent to
the person who has installed the keylogger.
2. Clipboard Record
Another feature is that keylogger records all the words or texts that are copied and
pasted on the clipboard. This helps to know about who selected and copied which text
and information.
3. Application Tracking
Keylogger tracks all the applications which are visited and run by the user. The
purpose is to easily understand what time which user is running what applications in
the computer.
4. Websites Visited
All the activities done in the websites like site titles, clicking links, URLs can be
monitored by the Keyloggers. Its main purpose is to record at what time user is using
which websites and number of times s/he visited the websites.
5. Screen Capture
Beside the keystrokes, it can capture the screen to understand what’s going on with
the computer.
6. Web-Camera Recording
Unlike the Screen Capture, web-camera clicks and records the pictures of the
activities of the user.
7
Here is a list of features of Keyloggers.
1. Keystrokes Logging
After the installation of keylogger, it records all the key strokes in the log and sent to
the person who has installed the keylogger.
2. Clipboard Record
Another feature is that keylogger records all the words or texts that are copied and
pasted on the clipboard. This helps to know about who selected and copied which text
and information.
3. Application Tracking
Keylogger tracks all the applications which are visited and run by the user. The
purpose is to easily understand what time which user is running what applications in
the computer.
4. Websites Visited
All the activities done in the websites like site titles, clicking links, URLs can be
monitored by the Keyloggers. Its main purpose is to record at what time user is using
which websites and number of times s/he visited the websites.
5. Screen Capture
Beside the keystrokes, it can capture the screen to understand what’s going on with
the computer.
6. Web-Camera Recording
Unlike the Screen Capture, web-camera clicks and records the pictures of the
activities of the user.
7
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7. Email log delivery
Keylogger also records the email delivery times in the logs (Creutzburg, 2017).
8
Keylogger also records the email delivery times in the logs (Creutzburg, 2017).
8

Types of Keyloggers
Basically, there are 2 types of Keyloggers i.e. Hardware Keyloggers and Software
Keyloggers.
Hardware Keyloggers
Hardware Keyloggers are any physical device that can plug directly into a computer in order
to record the keys that are pressed on that computer's keyboard. A common hardware key
logger takes the form of a flash drive that plugs directly into the USB port of a computer.
This flash drive contains special software that records the keystrokes of the user in a text file.
Types of Hardware Keyloggers
1. Regular Hardware Keylogger
Ordinary equipment key lumberjacks are utilized to log keystrokes by equipment
circuits that are associated between the PC's console and the PC. Record all console
movement in inward memory that can be gotten to by entering a lot of predefined
characters.
2. Wireless Keylogger Sniffers
The remote key lumberjack sniffer gathers bundles of information moved from the
remote console and its beneficiary and endeavours to unscramble the encryption key
used to secure remote correspondence between the two gadgets.
3. Firmware
Profiles on PCs that typically handle console occasions can be reconstructed to record
when preparing keystrokes.
9
Basically, there are 2 types of Keyloggers i.e. Hardware Keyloggers and Software
Keyloggers.
Hardware Keyloggers
Hardware Keyloggers are any physical device that can plug directly into a computer in order
to record the keys that are pressed on that computer's keyboard. A common hardware key
logger takes the form of a flash drive that plugs directly into the USB port of a computer.
This flash drive contains special software that records the keystrokes of the user in a text file.
Types of Hardware Keyloggers
1. Regular Hardware Keylogger
Ordinary equipment key lumberjacks are utilized to log keystrokes by equipment
circuits that are associated between the PC's console and the PC. Record all console
movement in inward memory that can be gotten to by entering a lot of predefined
characters.
2. Wireless Keylogger Sniffers
The remote key lumberjack sniffer gathers bundles of information moved from the
remote console and its beneficiary and endeavours to unscramble the encryption key
used to secure remote correspondence between the two gadgets.
3. Firmware
Profiles on PCs that typically handle console occasions can be reconstructed to record
when preparing keystrokes.
9
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

4. Keyboard overlays
Since a bogus keypad is set over the genuine keypad, every one of the keys that are
squeezed is enlisted by both the listening in gadget and the real gadget that the client
is utilizing.
Software Keyloggers
Software Keyloggers, on the other hand, are applications that are installed on a computer or
mobile device. In a similar fashion to hardware Keyloggers, software Keyloggers records the
keys that are pressed on the device's keyboard and stores that information so that the hacker
can access it later. Software Keyloggers are the most common Keyloggers used for recording
the keystrokes on virtual keyboards (Damopoulos, Kambourakis & Gritzalis, 2013).
Types of Software Keyloggers
1. Hypervisor-based
Key loggers can reside on malware hypervisors that run theoretically under the
operating system, so they remain intact. It's virtual. Blue pill is a conceptual example.
2. Kernel-based
Kernel-based key loggers prohibit the core of the computer's operating system,
making it very difficult to identify and remove them. Since both of these methods are
difficult to write, these key loggers are less common than other software key loggers.
These key loggers exist at the kernel level, making them difficult to detect, especially
for user-mode applications that do not have root access.
10
Since a bogus keypad is set over the genuine keypad, every one of the keys that are
squeezed is enlisted by both the listening in gadget and the real gadget that the client
is utilizing.
Software Keyloggers
Software Keyloggers, on the other hand, are applications that are installed on a computer or
mobile device. In a similar fashion to hardware Keyloggers, software Keyloggers records the
keys that are pressed on the device's keyboard and stores that information so that the hacker
can access it later. Software Keyloggers are the most common Keyloggers used for recording
the keystrokes on virtual keyboards (Damopoulos, Kambourakis & Gritzalis, 2013).
Types of Software Keyloggers
1. Hypervisor-based
Key loggers can reside on malware hypervisors that run theoretically under the
operating system, so they remain intact. It's virtual. Blue pill is a conceptual example.
2. Kernel-based
Kernel-based key loggers prohibit the core of the computer's operating system,
making it very difficult to identify and remove them. Since both of these methods are
difficult to write, these key loggers are less common than other software key loggers.
These key loggers exist at the kernel level, making them difficult to detect, especially
for user-mode applications that do not have root access.
10
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3. API-based
API-based Keyloggers are by distant the foremost common type of keylogger. These
pieces of key logging software utilize the keyboard API (brief for Application
Programming Interface) to record the keystrokes typed by the user. Every time, you
press a key, a notification is sent to the application that you are typing that’s the typed
character would show up on the screen.
4. Form-grabbing based
Rather than logging each keystroke separately, form grabbing-based Keyloggers
log web form submissions by recording the web browsing on submit events. This can
include your full name, address, email phone number, login credentials or credit card
info. This happens when the user completes a form and submits it; usually by clicking
a button or hitting enter.
5. Memory Injection based
Memory Injection (MitB)-based Keyloggers perform their logging function by
altering the memory tables associated with the browser and other system functions.
By patching the memory tables or injecting directly into memory, this technique can
be used by malware authors to bypass Windows UAC (User Account Control).
6. Packet analyser
This involves capturing network traffic associated with HTTP POST events to
retrieve unencrypted passwords. This is made more difficult when connecting via
HTTPS, which is one of the reasons HTTPS was invented (Esbel & Christian, 2016).
11
API-based Keyloggers are by distant the foremost common type of keylogger. These
pieces of key logging software utilize the keyboard API (brief for Application
Programming Interface) to record the keystrokes typed by the user. Every time, you
press a key, a notification is sent to the application that you are typing that’s the typed
character would show up on the screen.
4. Form-grabbing based
Rather than logging each keystroke separately, form grabbing-based Keyloggers
log web form submissions by recording the web browsing on submit events. This can
include your full name, address, email phone number, login credentials or credit card
info. This happens when the user completes a form and submits it; usually by clicking
a button or hitting enter.
5. Memory Injection based
Memory Injection (MitB)-based Keyloggers perform their logging function by
altering the memory tables associated with the browser and other system functions.
By patching the memory tables or injecting directly into memory, this technique can
be used by malware authors to bypass Windows UAC (User Account Control).
6. Packet analyser
This involves capturing network traffic associated with HTTP POST events to
retrieve unencrypted passwords. This is made more difficult when connecting via
HTTPS, which is one of the reasons HTTPS was invented (Esbel & Christian, 2016).
11

Characteristics of Hardware Keyloggers
Equipment key lumberjacks can be introduced by anybody with access to space and the nerve
to do it.
A key lumberjack records everything entered on a console or other info gadget. Programming
key lumberjacks are progressively normal and surely understood. They are malware that will
be introduced on the injured individual's PC.
Equipment key lumberjacks are physical gadgets, for example, USB sticks, PS2 links, or
divider chargers that record keystrokes and other information. These were generally wired
however there were likewise remote sniffing types.
You can introduce the keylogger programming through phishing mail. Equipment key
lumberjacks expect somebody to have physical access to the area. This is on the grounds that
the majority of the equipment key lumberjack cases are out in the open places, for example,
libraries, or in generally less secure places, for example, schools, or in at any rate one case in
the newsroom.
Equipment key lumberjacks sidestep numerous encryption and other standard security
hindrances to recognize and store real keystrokes entered from the console.
Equipment key lumberjacks can't be identified by an antivirus or other programming
research.
They are physically perceptible, yet by and large nobody needs to check them. Key
lumberjacks can speak to individuals who need to discover something explicit, for example, a
secret key, yet don't have the information to get malware on the objective PC. Equipment key
lumberjacks can be introduced by anybody with access to space and the nerve to do it.
While equipment key lumberjacks have since quite a while ago cantered around standard PS2
consoles, gadgets, for example, Key Sweeper might be in danger for remote consoles. The
12
Equipment key lumberjacks can be introduced by anybody with access to space and the nerve
to do it.
A key lumberjack records everything entered on a console or other info gadget. Programming
key lumberjacks are progressively normal and surely understood. They are malware that will
be introduced on the injured individual's PC.
Equipment key lumberjacks are physical gadgets, for example, USB sticks, PS2 links, or
divider chargers that record keystrokes and other information. These were generally wired
however there were likewise remote sniffing types.
You can introduce the keylogger programming through phishing mail. Equipment key
lumberjacks expect somebody to have physical access to the area. This is on the grounds that
the majority of the equipment key lumberjack cases are out in the open places, for example,
libraries, or in generally less secure places, for example, schools, or in at any rate one case in
the newsroom.
Equipment key lumberjacks sidestep numerous encryption and other standard security
hindrances to recognize and store real keystrokes entered from the console.
Equipment key lumberjacks can't be identified by an antivirus or other programming
research.
They are physically perceptible, yet by and large nobody needs to check them. Key
lumberjacks can speak to individuals who need to discover something explicit, for example, a
secret key, yet don't have the information to get malware on the objective PC. Equipment key
lumberjacks can be introduced by anybody with access to space and the nerve to do it.
While equipment key lumberjacks have since quite a while ago cantered around standard PS2
consoles, gadgets, for example, Key Sweeper might be in danger for remote consoles. The
12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 23
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





