System Documentation Report: Configuration of LAN in TridentS
VerifiedAdded on 2020/03/28
|16
|2878
|55
Report
AI Summary
This system documentation report outlines the implementation of technologies within the Local Area Network (LAN) of TridentS, a software development company. It details the selection and configuration of a wireless router, choosing appropriate networking patterns, and the use of switches and hubs. The report covers managing HomeGroups in the OS, server management, and implementing a backup plan to protect sensitive information. Furthermore, it delves into the technologies implemented, including centralized user authentication, the deployment of print servers, and the acquisition of IP addresses from an IIS server. The report also discusses the organization of a default website and the steps involved in creating a new website, including granting web server permissions for web content. The report provides a comprehensive overview of the LAN configuration, aiming for efficient network implementation within the organization.

Configuration of Local Area Network (LAN) in TridentS
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
1. Introduction 3
2. Selecting a Wireless Router 3
2. 1. Selecting a Wireless Router 3
2. 2. Choosing a networking pattern 3
2. 3. Select Network Wiring 4
2. 4. Employing Suitable Client Connectors 4
2. 5. Switch and Hubs 4
3. Managing Home Groups in OS 4
4. Server Management 4
5. Procurement of Power Stream Protection 5
6. Implementation of Backup Plan 5
7. Technologies implemented in TridentS’s LAN 5
7. 1. Centralized User Authentication 5
7. 2. Deploying Print Servers 8
7. 3. Acquirement of IP Addresses from IIS server 10
8.TridentS Website
Hosting.........................................................................................................................................12
8. 1. Organization of a default website 12
8. 2. Steps for creating a new website 13
9. Granting Web server permissions for web content 14
10. Reference................................................................................................................................15
1. Introduction 3
2. Selecting a Wireless Router 3
2. 1. Selecting a Wireless Router 3
2. 2. Choosing a networking pattern 3
2. 3. Select Network Wiring 4
2. 4. Employing Suitable Client Connectors 4
2. 5. Switch and Hubs 4
3. Managing Home Groups in OS 4
4. Server Management 4
5. Procurement of Power Stream Protection 5
6. Implementation of Backup Plan 5
7. Technologies implemented in TridentS’s LAN 5
7. 1. Centralized User Authentication 5
7. 2. Deploying Print Servers 8
7. 3. Acquirement of IP Addresses from IIS server 10
8.TridentS Website
Hosting.........................................................................................................................................12
8. 1. Organization of a default website 12
8. 2. Steps for creating a new website 13
9. Granting Web server permissions for web content 14
10. Reference................................................................................................................................15

1. Introduction
The main constituent of any business is the employment of computer network. The user’s computer
can be connected to the web for the purpose of checking email, creating website, conducting
meetins, etc. The network also allows the users to connect with local computers located in the
consistent local network. Moreover, the employees in the company need to stream multimedia,
share their files and printers, to administer the access to their information.
This system documentation report intends to explain the implementation of the technologies
incorporated in LAN of a software development company, TridentS. For the purpose of achieving
efficient implementation, the objects like users and computers are created within their own
organizational departments.
2. Configuration of LAN in TridentS
2. 1. Selecting a Wireless Router
Router is an essential constituent for provisioning the office network. Mostly each and every
network is an amalgamation of wireless and wired links. And, the wireless router can be able to offer
both wireless and wired connection.
The organizational LAN and the Internet are bridged by means of router that distributes the
connection to all the connected devices. The router is exploited as the network DHCP server. The
role of DHCP server is to provide a private and unique IP address to every connected device and to
enable communication between those devices.
Firewalls are incorporated inside the router in order to prevent the perils and to safeguard the
computer network from other malevolent activities [8]. The Wi-Fi network employed in TridentS is
secured by using WPA or WPA2. Moreover, in order to ensure safety, the administration key of
router is changed and not kept defaulted [1].
The router capable of supporting 5 GHz band is selected for the TridentS for the purpose of adding
print server, including new storage device, and for creating the own web server for company. Since
faster throughput for sharing files and other tasks can be achieved by the utilization of D-Link DIR-
825 Xtreme N Dual Band Gigabit, it is implanted in TridentS. Gigabit Ethernet ports are employed in
the organization for providing speed connections.
The main constituent of any business is the employment of computer network. The user’s computer
can be connected to the web for the purpose of checking email, creating website, conducting
meetins, etc. The network also allows the users to connect with local computers located in the
consistent local network. Moreover, the employees in the company need to stream multimedia,
share their files and printers, to administer the access to their information.
This system documentation report intends to explain the implementation of the technologies
incorporated in LAN of a software development company, TridentS. For the purpose of achieving
efficient implementation, the objects like users and computers are created within their own
organizational departments.
2. Configuration of LAN in TridentS
2. 1. Selecting a Wireless Router
Router is an essential constituent for provisioning the office network. Mostly each and every
network is an amalgamation of wireless and wired links. And, the wireless router can be able to offer
both wireless and wired connection.
The organizational LAN and the Internet are bridged by means of router that distributes the
connection to all the connected devices. The router is exploited as the network DHCP server. The
role of DHCP server is to provide a private and unique IP address to every connected device and to
enable communication between those devices.
Firewalls are incorporated inside the router in order to prevent the perils and to safeguard the
computer network from other malevolent activities [8]. The Wi-Fi network employed in TridentS is
secured by using WPA or WPA2. Moreover, in order to ensure safety, the administration key of
router is changed and not kept defaulted [1].
The router capable of supporting 5 GHz band is selected for the TridentS for the purpose of adding
print server, including new storage device, and for creating the own web server for company. Since
faster throughput for sharing files and other tasks can be achieved by the utilization of D-Link DIR-
825 Xtreme N Dual Band Gigabit, it is implanted in TridentS. Gigabit Ethernet ports are employed in
the organization for providing speed connections.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.2. Choosing a networking pattern
Choosing a suitable networking pattern is an additional factor in configuring LAN. Since most of the
routing devices, wireless gadgets such as iPad and desktops like Apple mac Mini, are conforming to
the 802.11n networking pattern, it is exploited in TridentS containing more number of N devices [3].
The connectivity is not a major if the older devices do not support N pattern.
2.3. Select Network Wiring
The devices like desktop, laptop, etc. can send the information very quickly through wired Ethernet
connectivity rather than wireless notably when the employee is transferring any type of files. Game
consoles, routers, and NAS drivers are associated with Ethernet cables [5]. When the network of the
organization is to be extended, then extra cables are to be procured.
2.4. Employing Suitable Client Connectors
The wireless adapter is required to every device in the network for receiving the Wi-Fi signal when
the users do not want to make a connection with the router. Most of the web-ready computers in
TridentS have wireless adapters in it. Ethernet ports are used by many connected devices and
servers.
2.5. Installation of Switches and Hubs
In order to provide wiring to storage devices, computers, and servers, the embedded router contains
three Ethernet Ports. Switch can be purchased if the network configuration needs additional ports.
3. Managing HomeGroups in OS
After finishing the network configuration, it should be administered by means of adding folders,
users, files, and printer sharing options. The Windows 7 operating system has been installed in the
computers used in TridentS. There are some built-in features embedded in Windows 7 for small
network management. By joining the HomeGroups, the users can disclose the printers and files [2].
4. Server Management
For controlling the network and to configure file sharing, server plays a major role. Server is not
necessarily required in case of small networks. The NAS devices implanted in TridentS perform as
network server.
Choosing a suitable networking pattern is an additional factor in configuring LAN. Since most of the
routing devices, wireless gadgets such as iPad and desktops like Apple mac Mini, are conforming to
the 802.11n networking pattern, it is exploited in TridentS containing more number of N devices [3].
The connectivity is not a major if the older devices do not support N pattern.
2.3. Select Network Wiring
The devices like desktop, laptop, etc. can send the information very quickly through wired Ethernet
connectivity rather than wireless notably when the employee is transferring any type of files. Game
consoles, routers, and NAS drivers are associated with Ethernet cables [5]. When the network of the
organization is to be extended, then extra cables are to be procured.
2.4. Employing Suitable Client Connectors
The wireless adapter is required to every device in the network for receiving the Wi-Fi signal when
the users do not want to make a connection with the router. Most of the web-ready computers in
TridentS have wireless adapters in it. Ethernet ports are used by many connected devices and
servers.
2.5. Installation of Switches and Hubs
In order to provide wiring to storage devices, computers, and servers, the embedded router contains
three Ethernet Ports. Switch can be purchased if the network configuration needs additional ports.
3. Managing HomeGroups in OS
After finishing the network configuration, it should be administered by means of adding folders,
users, files, and printer sharing options. The Windows 7 operating system has been installed in the
computers used in TridentS. There are some built-in features embedded in Windows 7 for small
network management. By joining the HomeGroups, the users can disclose the printers and files [2].
4. Server Management
For controlling the network and to configure file sharing, server plays a major role. Server is not
necessarily required in case of small networks. The NAS devices implanted in TridentS perform as
network server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Since TridentS employs a personalized web server, higher flexibility is attained by their own server.
This can be achieved by the incorporation of NAS devices.
5. Procurement of Power stream protection
A recovery plan is arranged in TridentS during the occurrence of any disaster like crashed hard drive,
power spear, and data distortions. The investments are made for the power protection
requirements in the organization [6]. If the company’s server goes down, funds and time will be
wasted. Hence a protector is installed in TridentS if there are any power surge issues.
6. Backup Plan Implementation
The sensitive information in the organization should be protected by implementing certain backup
plans. The backup systems are verified regularly to make sure that the data backups do not contain
any information distortions [5].
The organization network data is recovered by various strategies. An external storage space is
allocated for local backup system. Windows server also possesses built-in backup aspects [7].
7. Technologies implemented in TridentS’s LAN
7.1. Centralized User Authentication
Many of the modern threats took place at the application layer. So, the data should be protected by
employing defensive mechanism. By configuring the file permissions and data encryption, the
confidentiality of the information can be maintained [10]. To ensure the data security, the physical
and network access to servers are restricted in TridentS. The data safety can be ensured by the
following steps depicted below:
The service dependencies are determined before a service is disabled as shown in the figure
below.
This can be achieved by the incorporation of NAS devices.
5. Procurement of Power stream protection
A recovery plan is arranged in TridentS during the occurrence of any disaster like crashed hard drive,
power spear, and data distortions. The investments are made for the power protection
requirements in the organization [6]. If the company’s server goes down, funds and time will be
wasted. Hence a protector is installed in TridentS if there are any power surge issues.
6. Backup Plan Implementation
The sensitive information in the organization should be protected by implementing certain backup
plans. The backup systems are verified regularly to make sure that the data backups do not contain
any information distortions [5].
The organization network data is recovered by various strategies. An external storage space is
allocated for local backup system. Windows server also possesses built-in backup aspects [7].
7. Technologies implemented in TridentS’s LAN
7.1. Centralized User Authentication
Many of the modern threats took place at the application layer. So, the data should be protected by
employing defensive mechanism. By configuring the file permissions and data encryption, the
confidentiality of the information can be maintained [10]. To ensure the data security, the physical
and network access to servers are restricted in TridentS. The data safety can be ensured by the
following steps depicted below:
The service dependencies are determined before a service is disabled as shown in the figure
below.
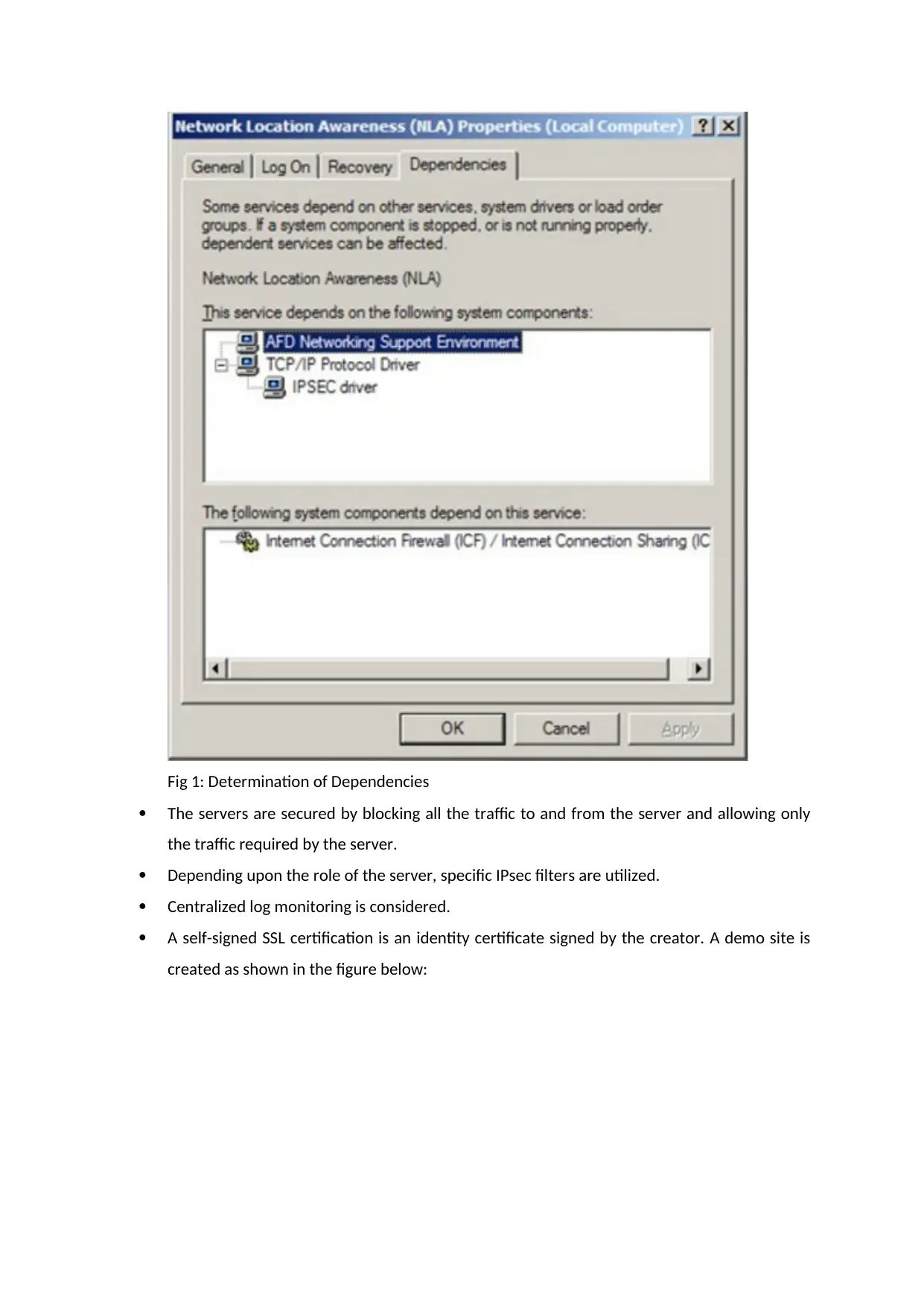
Fig 1: Determination of Dependencies
The servers are secured by blocking all the traffic to and from the server and allowing only
the traffic required by the server.
Depending upon the role of the server, specific IPsec filters are utilized.
Centralized log monitoring is considered.
A self-signed SSL certification is an identity certificate signed by the creator. A demo site is
created as shown in the figure below:
The servers are secured by blocking all the traffic to and from the server and allowing only
the traffic required by the server.
Depending upon the role of the server, specific IPsec filters are utilized.
Centralized log monitoring is considered.
A self-signed SSL certification is an identity certificate signed by the creator. A demo site is
created as shown in the figure below:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
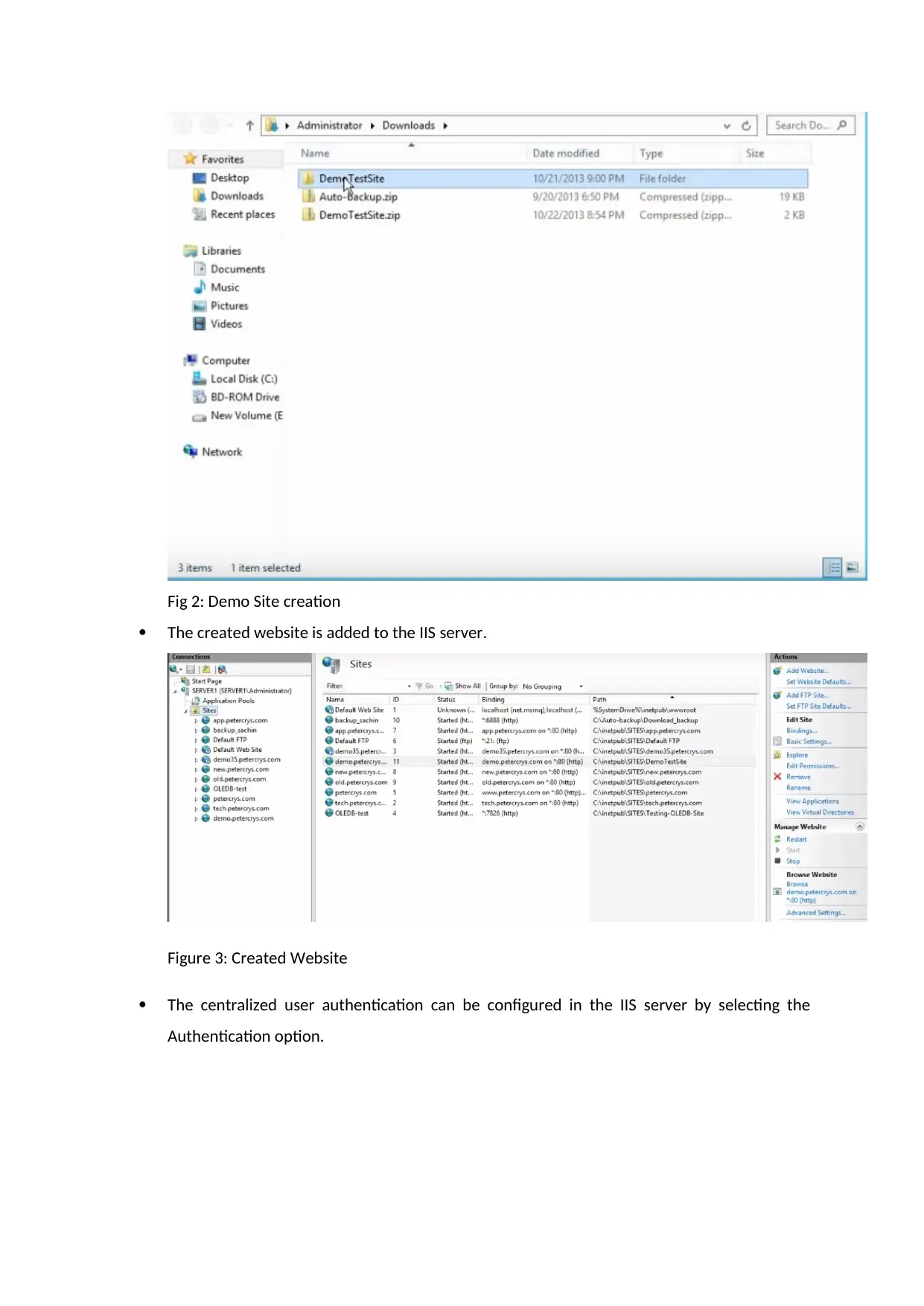
Fig 2: Demo Site creation
The created website is added to the IIS server.
Figure 3: Created Website
The centralized user authentication can be configured in the IIS server by selecting the
Authentication option.
The created website is added to the IIS server.
Figure 3: Created Website
The centralized user authentication can be configured in the IIS server by selecting the
Authentication option.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
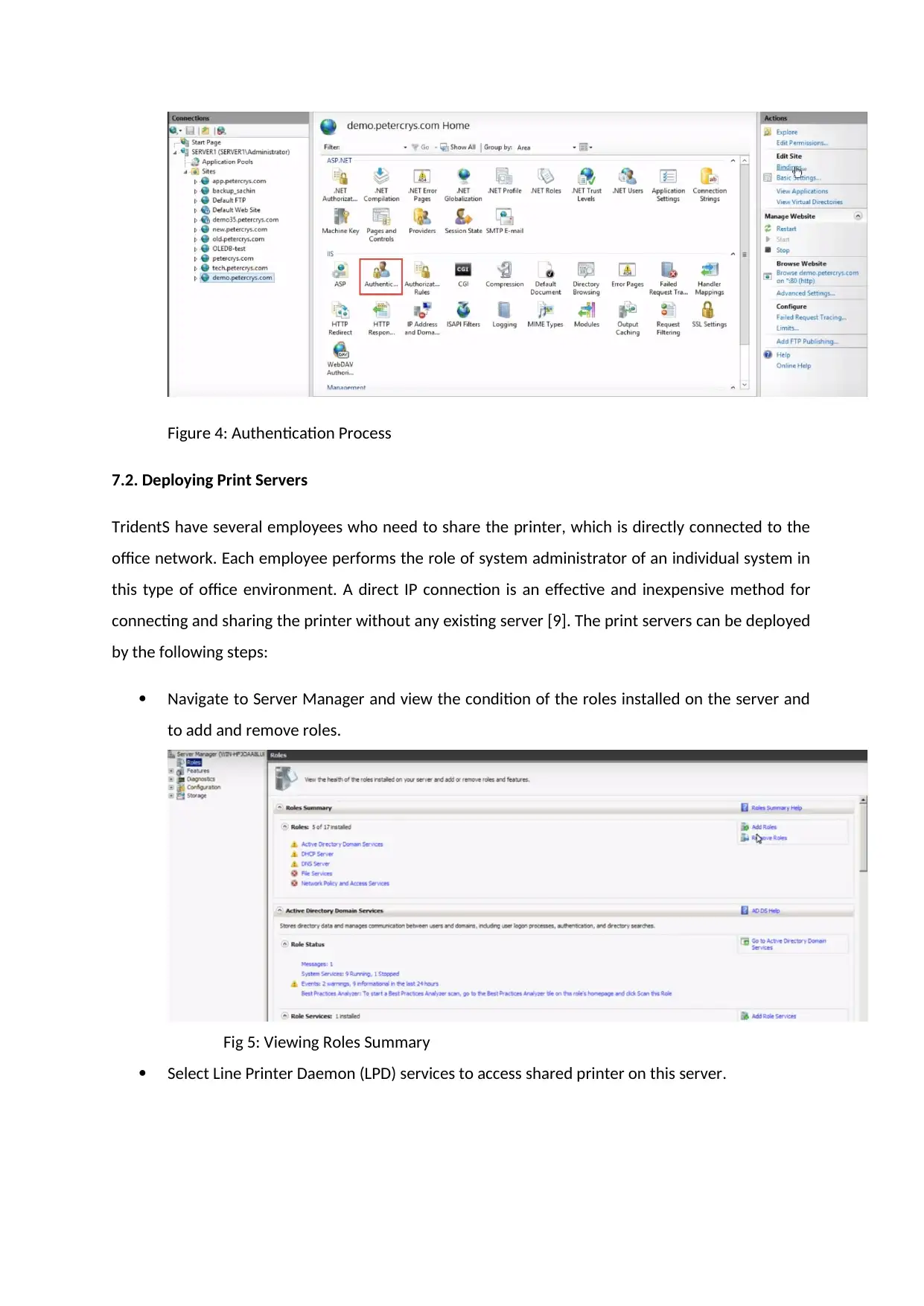
Figure 4: Authentication Process
7.2. Deploying Print Servers
TridentS have several employees who need to share the printer, which is directly connected to the
office network. Each employee performs the role of system administrator of an individual system in
this type of office environment. A direct IP connection is an effective and inexpensive method for
connecting and sharing the printer without any existing server [9]. The print servers can be deployed
by the following steps:
Navigate to Server Manager and view the condition of the roles installed on the server and
to add and remove roles.
Fig 5: Viewing Roles Summary
Select Line Printer Daemon (LPD) services to access shared printer on this server.
7.2. Deploying Print Servers
TridentS have several employees who need to share the printer, which is directly connected to the
office network. Each employee performs the role of system administrator of an individual system in
this type of office environment. A direct IP connection is an effective and inexpensive method for
connecting and sharing the printer without any existing server [9]. The print servers can be deployed
by the following steps:
Navigate to Server Manager and view the condition of the roles installed on the server and
to add and remove roles.
Fig 5: Viewing Roles Summary
Select Line Printer Daemon (LPD) services to access shared printer on this server.
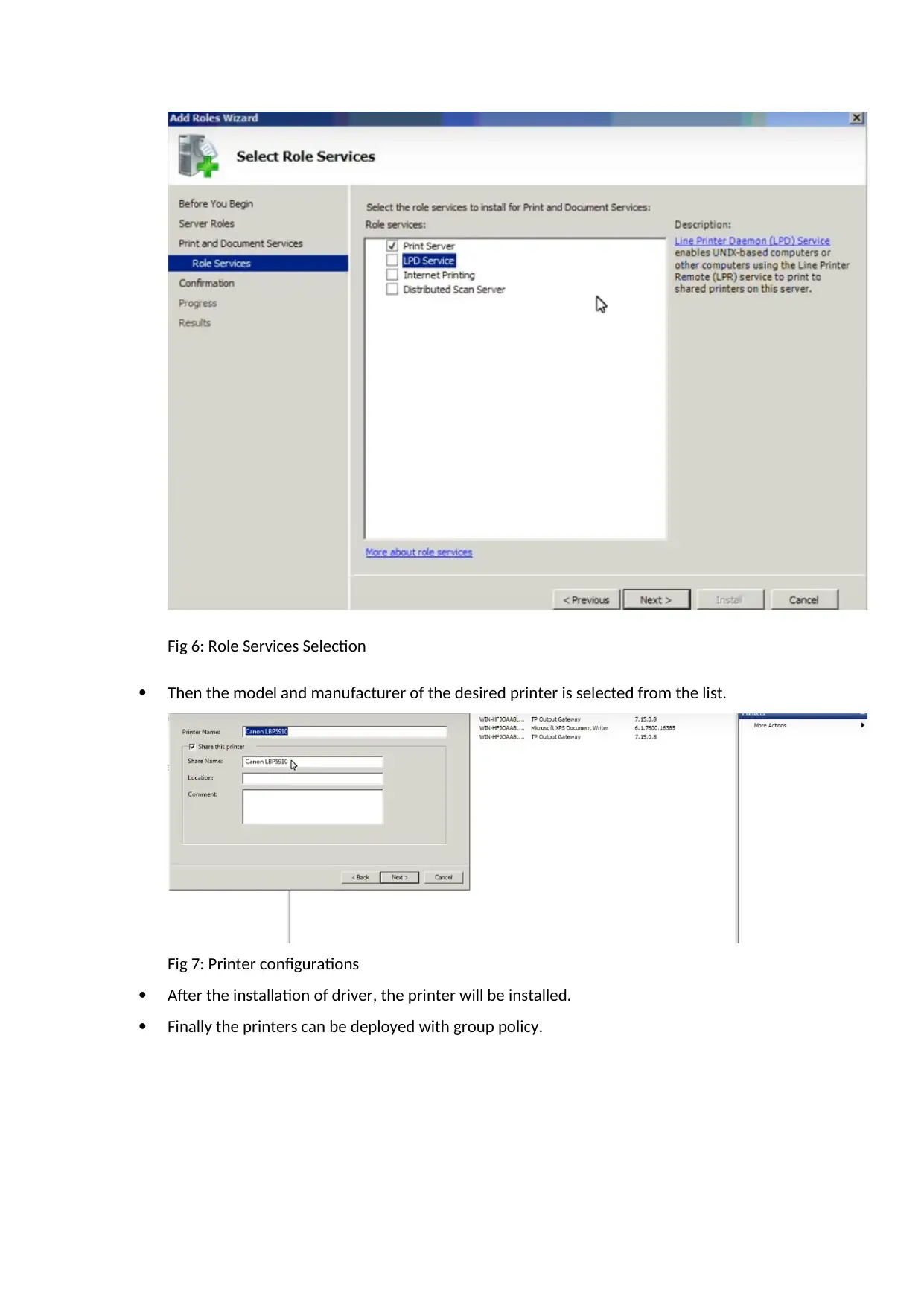
Fig 6: Role Services Selection
Then the model and manufacturer of the desired printer is selected from the list.
Fig 7: Printer configurations
After the installation of driver, the printer will be installed.
Finally the printers can be deployed with group policy.
Then the model and manufacturer of the desired printer is selected from the list.
Fig 7: Printer configurations
After the installation of driver, the printer will be installed.
Finally the printers can be deployed with group policy.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
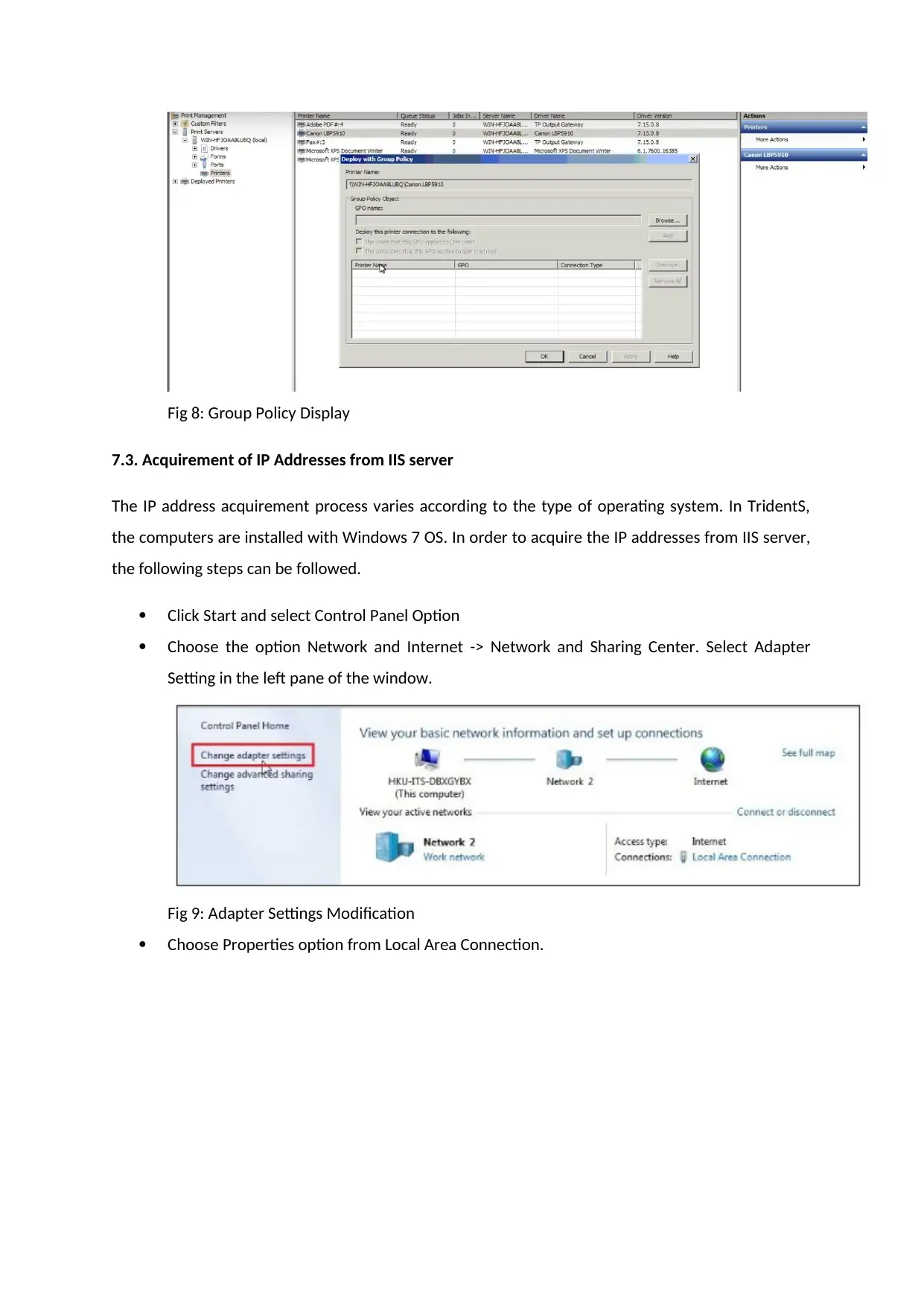
Fig 8: Group Policy Display
7.3. Acquirement of IP Addresses from IIS server
The IP address acquirement process varies according to the type of operating system. In TridentS,
the computers are installed with Windows 7 OS. In order to acquire the IP addresses from IIS server,
the following steps can be followed.
Click Start and select Control Panel Option
Choose the option Network and Internet -> Network and Sharing Center. Select Adapter
Setting in the left pane of the window.
Fig 9: Adapter Settings Modification
Choose Properties option from Local Area Connection.
7.3. Acquirement of IP Addresses from IIS server
The IP address acquirement process varies according to the type of operating system. In TridentS,
the computers are installed with Windows 7 OS. In order to acquire the IP addresses from IIS server,
the following steps can be followed.
Click Start and select Control Panel Option
Choose the option Network and Internet -> Network and Sharing Center. Select Adapter
Setting in the left pane of the window.
Fig 9: Adapter Settings Modification
Choose Properties option from Local Area Connection.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
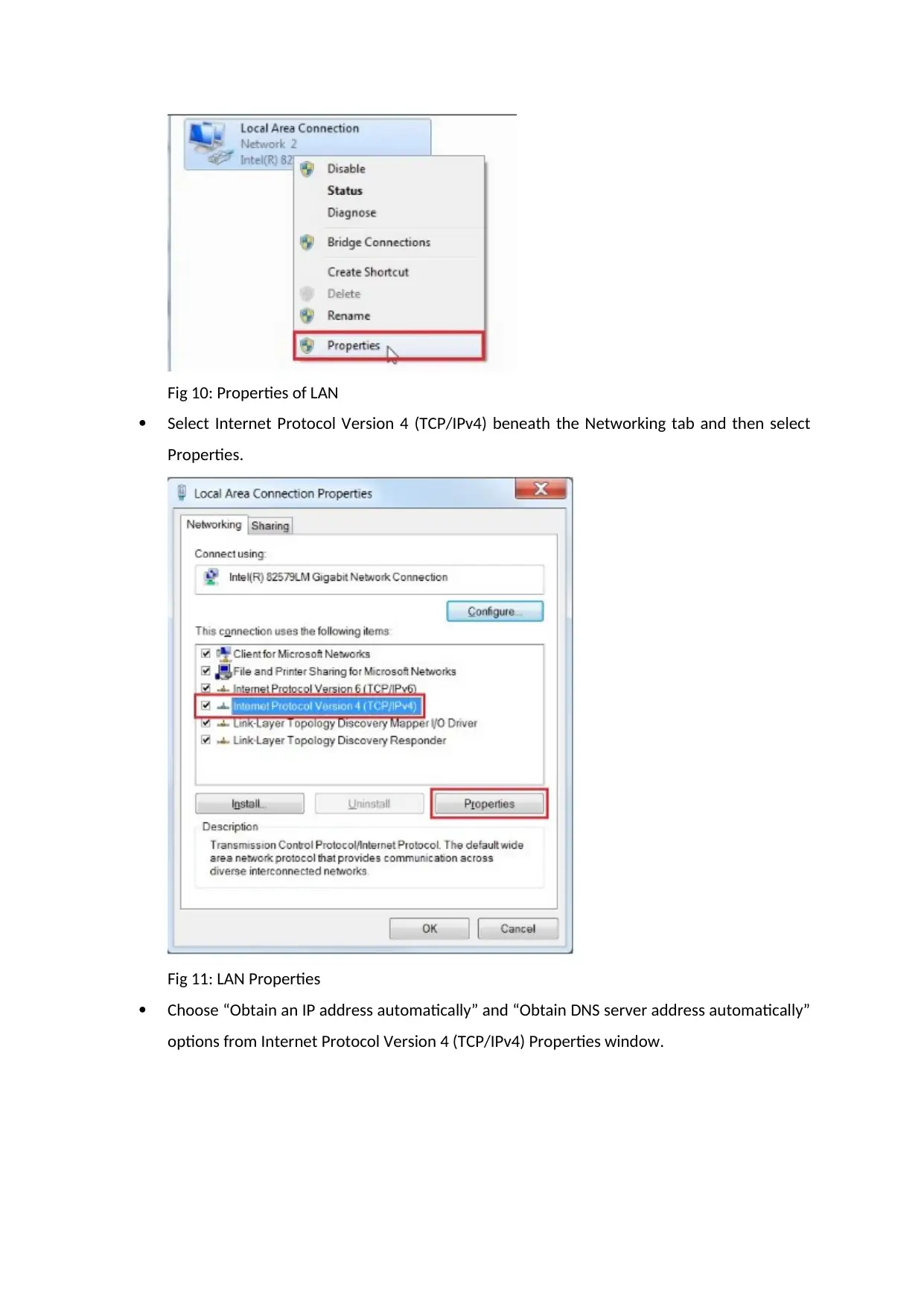
Fig 10: Properties of LAN
Select Internet Protocol Version 4 (TCP/IPv4) beneath the Networking tab and then select
Properties.
Fig 11: LAN Properties
Choose “Obtain an IP address automatically” and “Obtain DNS server address automatically”
options from Internet Protocol Version 4 (TCP/IPv4) Properties window.
Select Internet Protocol Version 4 (TCP/IPv4) beneath the Networking tab and then select
Properties.
Fig 11: LAN Properties
Choose “Obtain an IP address automatically” and “Obtain DNS server address automatically”
options from Internet Protocol Version 4 (TCP/IPv4) Properties window.
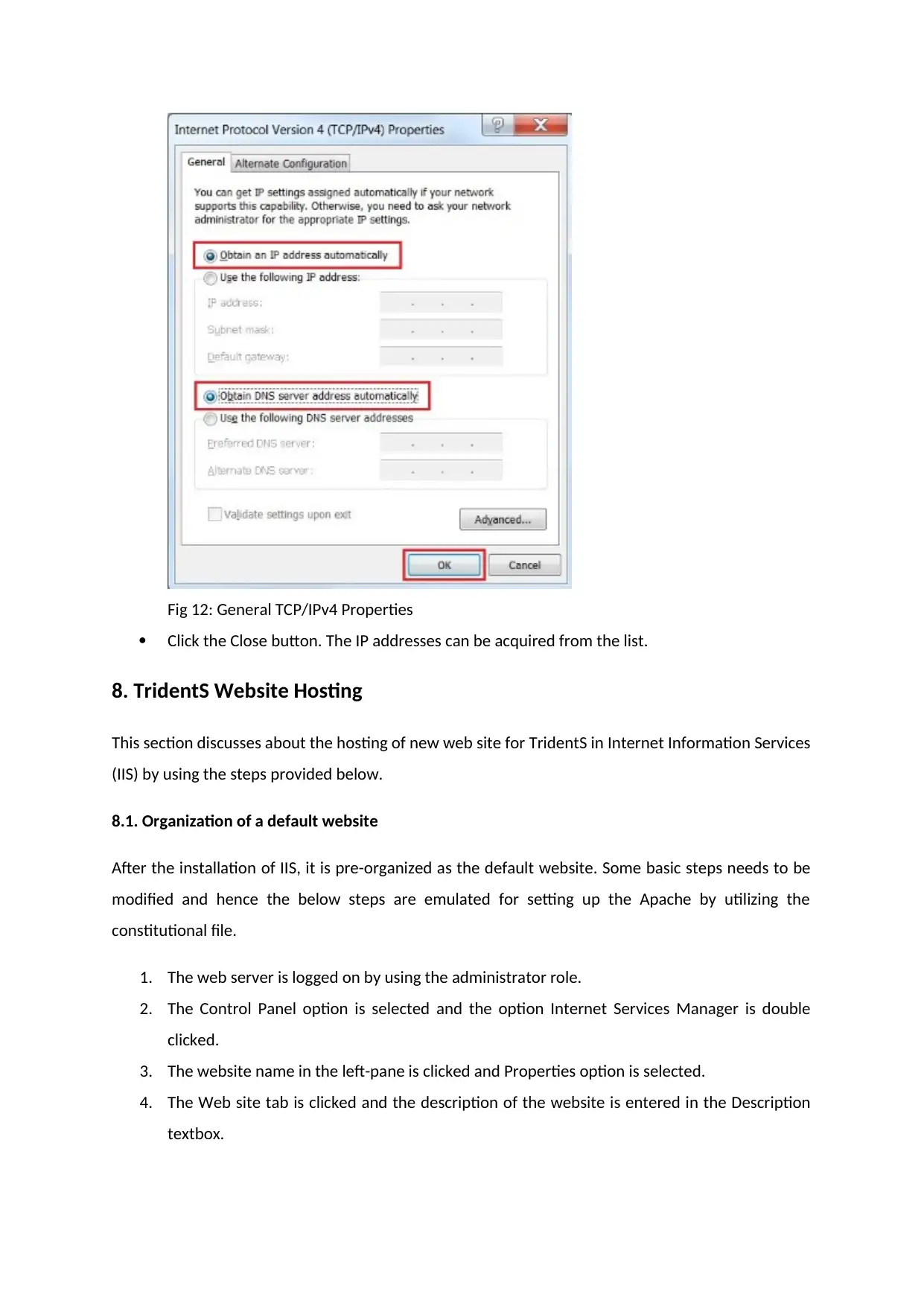
Fig 12: General TCP/IPv4 Properties
Click the Close button. The IP addresses can be acquired from the list.
8. TridentS Website Hosting
This section discusses about the hosting of new web site for TridentS in Internet Information Services
(IIS) by using the steps provided below.
8.1. Organization of a default website
After the installation of IIS, it is pre-organized as the default website. Some basic steps needs to be
modified and hence the below steps are emulated for setting up the Apache by utilizing the
constitutional file.
1. The web server is logged on by using the administrator role.
2. The Control Panel option is selected and the option Internet Services Manager is double
clicked.
3. The website name in the left-pane is clicked and Properties option is selected.
4. The Web site tab is clicked and the description of the website is entered in the Description
textbox.
Click the Close button. The IP addresses can be acquired from the list.
8. TridentS Website Hosting
This section discusses about the hosting of new web site for TridentS in Internet Information Services
(IIS) by using the steps provided below.
8.1. Organization of a default website
After the installation of IIS, it is pre-organized as the default website. Some basic steps needs to be
modified and hence the below steps are emulated for setting up the Apache by utilizing the
constitutional file.
1. The web server is logged on by using the administrator role.
2. The Control Panel option is selected and the option Internet Services Manager is double
clicked.
3. The website name in the left-pane is clicked and Properties option is selected.
4. The Web site tab is clicked and the description of the website is entered in the Description
textbox.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 16
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




