Local Area Network: Networking Principles, Design, Implementation
VerifiedAdded on 2024/05/29
|18
|3979
|462
Report
AI Summary
This report provides a detailed examination of local area networks (LANs), covering networking principles, protocols, and devices. It begins by differentiating between various network types such as WAN, LAN, MAN, PAN, and WLAN, and explores different network topologies like bus, ring, star, tree, mesh, and hybrid. The report also delves into communication and bandwidth requirements, emphasizing the use of TCP/IP and OSPF protocols. Furthermore, it explains the functions of network servers including mail, web, FTP, DNS, and DHCP servers. The report also discusses network devices such as routers, switches, and servers, highlighting the interdependence of workstation hardware and networking software. The report includes a sample network topology diagram and details hardware requirements for the network scenario. Finally, the report provides configuration steps for routers and switches, including setting IP addresses, VLSM, user authentication, and port security.

Local Area Network
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Contents
Introduction......................................................................................................................................3
LO1: Examine networking principles and their protocols, including [P1 and P2]..........................3
LO2: Explain networking devices and operations [P3 and P4].......................................................6
LO3 Designing an efficient network system [P5 and P6]...............................................................8
LO4 Implement and diagnosing network system [P7 and P8]......................................................14
Conclusion.....................................................................................................................................16
References......................................................................................................................................17
Appendix........................................................................................................................................18
Introduction......................................................................................................................................3
LO1: Examine networking principles and their protocols, including [P1 and P2]..........................3
LO2: Explain networking devices and operations [P3 and P4].......................................................6
LO3 Designing an efficient network system [P5 and P6]...............................................................8
LO4 Implement and diagnosing network system [P7 and P8]......................................................14
Conclusion.....................................................................................................................................16
References......................................................................................................................................17
Appendix........................................................................................................................................18

Introduction
With the increase in the use of computers every day, it is necessary that we understand about
how data and other pieces of information are shared between one computer to another. A
Computer Network is formed by connecting different devices like routers, switches, and
computers in a special arrangement so that they can share data with each other.
LO1: Examine networking principles and their protocols, including [P1 and P2].
A Computer network is physically built in an office or home. We also create some small servers
into our office network and also connect it to the internet. We have different types of networks
depending on the size and arrangement of devices.
Wide Area Network (WAN): A wide area network is a connection of different LAN (local area
networks). It extends over a large geographical area and also more complex in nature than LAN.
Sometimes its range can go beyond 100 km. It uses links like Satellite communications,
Telephone lines, and microwave links.
WAN communication occurs at layer 1 and layer 2 of OSI model. The basic three methods to
connect non-local networks are
Dedicated line connection which uses synchronous serial communications. It is
considered to be most expensive option hence it is mostly used by big organizations. Switched line and Internet
Local Area Network (LAN): LAN is considered to be the simplest form of a network. This type
of networks is used to connect computers together over a small distance. The data transmission
rate in a LAN can range from 100 Mbps to 1 Gbps. Twisted pair, Coaxial cables, Fiber optics
and WiFI are some of the technologies used in configuring a LAN. We can connect Personal
computers, workstations, Printers and some small servers in a LAN (Techterms.com, 2018).
Metropolitan Area Network(MAN): MAN is same as LAN but it can expand to a town or city. It
also uses high-speed connections like Coaxial cables and microwave links. MAN networks are
formed by connecting several LANs. We can say that MAN is smaller than WAN(Wide area
network) but larger than LAN (Local Area Network). MAN usually works on Layer 2 (Datalink
layer) of OSI model. One of the best examples of MAN is Cable television network in cities (.
With the increase in the use of computers every day, it is necessary that we understand about
how data and other pieces of information are shared between one computer to another. A
Computer Network is formed by connecting different devices like routers, switches, and
computers in a special arrangement so that they can share data with each other.
LO1: Examine networking principles and their protocols, including [P1 and P2].
A Computer network is physically built in an office or home. We also create some small servers
into our office network and also connect it to the internet. We have different types of networks
depending on the size and arrangement of devices.
Wide Area Network (WAN): A wide area network is a connection of different LAN (local area
networks). It extends over a large geographical area and also more complex in nature than LAN.
Sometimes its range can go beyond 100 km. It uses links like Satellite communications,
Telephone lines, and microwave links.
WAN communication occurs at layer 1 and layer 2 of OSI model. The basic three methods to
connect non-local networks are
Dedicated line connection which uses synchronous serial communications. It is
considered to be most expensive option hence it is mostly used by big organizations. Switched line and Internet
Local Area Network (LAN): LAN is considered to be the simplest form of a network. This type
of networks is used to connect computers together over a small distance. The data transmission
rate in a LAN can range from 100 Mbps to 1 Gbps. Twisted pair, Coaxial cables, Fiber optics
and WiFI are some of the technologies used in configuring a LAN. We can connect Personal
computers, workstations, Printers and some small servers in a LAN (Techterms.com, 2018).
Metropolitan Area Network(MAN): MAN is same as LAN but it can expand to a town or city. It
also uses high-speed connections like Coaxial cables and microwave links. MAN networks are
formed by connecting several LANs. We can say that MAN is smaller than WAN(Wide area
network) but larger than LAN (Local Area Network). MAN usually works on Layer 2 (Datalink
layer) of OSI model. One of the best examples of MAN is Cable television network in cities (.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Personal area network(PAN): Pan is a computer network organized around an individual
person.IT can be created by wired or wireless methods. Wireless methods include Bluetooth and
Infrared connections and Wired connection includes USB and Firewire technologies. Usually,
the range of a PAN is less than 10 meters (SearchNetworking. 2018).
Wireless LAN (WLAN): It provides wireless network communication over short distances using
radio or infrared signals instead of traditional LAN cabling. WLAN is a type of LAN. WLAN is
used independently then compared to Wired networks. WLAN provides flexibility, portability,
mobility and ease of installation.
Network Topologies:
Bus: In a Bus topology, All the computers are connected with a central bus or the main cable and
the data flow in a single direction. It is cost effective, used in small networks and it is easy to
expand. But the disadvantage of using this arrangement is that it is dependent on the main cable
or bus. if it fails all the devices becomes non-functional.
Ring: In a ring topology, all the computer are connected in a continuous way or one after another
forming a ring-like structure. The data flow is unidirectional. But if any one of the nodes
undergoes any failure then all whole network is disturbed.
Star: In a star topology, there is a central hub or switch and all the computers are connected to it.
There is dedicated connection for each computer. You can upgrade the hub or switch easily but
the speed of the network is dependent on the hub or switch and if it fails then the whole network
will fail.
Tree Topology
it is considered to be a combination of bus and star topology. Used in wide area networks which
makes it costly and tough while making wired connections.
Mesh: In a mesh topology, all the computers are connected with each other and there are n(n-2)/2
channels to connect to n devices. It is secure, robust and it's logical! The best example of this
topology is the point to point connections.
person.IT can be created by wired or wireless methods. Wireless methods include Bluetooth and
Infrared connections and Wired connection includes USB and Firewire technologies. Usually,
the range of a PAN is less than 10 meters (SearchNetworking. 2018).
Wireless LAN (WLAN): It provides wireless network communication over short distances using
radio or infrared signals instead of traditional LAN cabling. WLAN is a type of LAN. WLAN is
used independently then compared to Wired networks. WLAN provides flexibility, portability,
mobility and ease of installation.
Network Topologies:
Bus: In a Bus topology, All the computers are connected with a central bus or the main cable and
the data flow in a single direction. It is cost effective, used in small networks and it is easy to
expand. But the disadvantage of using this arrangement is that it is dependent on the main cable
or bus. if it fails all the devices becomes non-functional.
Ring: In a ring topology, all the computer are connected in a continuous way or one after another
forming a ring-like structure. The data flow is unidirectional. But if any one of the nodes
undergoes any failure then all whole network is disturbed.
Star: In a star topology, there is a central hub or switch and all the computers are connected to it.
There is dedicated connection for each computer. You can upgrade the hub or switch easily but
the speed of the network is dependent on the hub or switch and if it fails then the whole network
will fail.
Tree Topology
it is considered to be a combination of bus and star topology. Used in wide area networks which
makes it costly and tough while making wired connections.
Mesh: In a mesh topology, all the computers are connected with each other and there are n(n-2)/2
channels to connect to n devices. It is secure, robust and it's logical! The best example of this
topology is the point to point connections.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Hybrid: A Hybrid topology is made by using one or more topology used to connect computers in
a network. The main combination is star bus and ring topology. One of the main advantages of
using this topology in our network is that it becomes easy to detect and remove the faulty part in
a network (GeeksforGeeks. 2017).
Network topology, communication, and bandwidth requirements.
Depending upon the type of topology used we will further decide the bandwidth which will be
required in our network. If the network is large then we must ensure that every node has a route
to reach the specific destination.
Some of the common technologies and protocols used for this purpose are:
TCP/IP (Transmission control protocol /internet protocol): It is one of the most used and
preferred models for creating a network. It defines a set of protocols or rules for network
implementation.
OSPF (Open shortest path first): OSPF is a dynamic routing protocol which is responsible for
providing the routes between routers of a network. It works on the Network layer. It works on
Link state routing algorithm.
Bandwidth Requirements: The minimum bandwidth requirement in our network will be around
100 Mbps. For gaining that much speed we must use Ethernet or Fast Ethernet LAN. It is one of
the most commonly used LAN connections which is so easy to configure and maintain. It uses
further technologies like VLAN (Virtual local area network), STP(Spanning tree protocol),
Switches port security and many more (WhatIs.com. 2018).
a network. The main combination is star bus and ring topology. One of the main advantages of
using this topology in our network is that it becomes easy to detect and remove the faulty part in
a network (GeeksforGeeks. 2017).
Network topology, communication, and bandwidth requirements.
Depending upon the type of topology used we will further decide the bandwidth which will be
required in our network. If the network is large then we must ensure that every node has a route
to reach the specific destination.
Some of the common technologies and protocols used for this purpose are:
TCP/IP (Transmission control protocol /internet protocol): It is one of the most used and
preferred models for creating a network. It defines a set of protocols or rules for network
implementation.
OSPF (Open shortest path first): OSPF is a dynamic routing protocol which is responsible for
providing the routes between routers of a network. It works on the Network layer. It works on
Link state routing algorithm.
Bandwidth Requirements: The minimum bandwidth requirement in our network will be around
100 Mbps. For gaining that much speed we must use Ethernet or Fast Ethernet LAN. It is one of
the most commonly used LAN connections which is so easy to configure and maintain. It uses
further technologies like VLAN (Virtual local area network), STP(Spanning tree protocol),
Switches port security and many more (WhatIs.com. 2018).

LO2: Explain networking devices and operations [P3 and P4].
Network servers: In our Network or LAN, we create or establish some local servers. The task of
these servers is to give a response to the client whenever it tries to access it or passes any request.
Some of those local servers are explained below:
1. Mail Server: One of the main tasks which happen in a company is exchanging Emails. So for
sharing Emails from client to server or vice-versa we use Mail Servers. It is commonly done
by using SMTP (Simple Mail Transfer Protocol) which uses port no 23 as a standard port.
2. WEB Server: All the HTTP (Hypertext transfer protocol) or Https (HTTP Secure) requests
are processed by web servers. It is mostly used to host websites and web pages HTTP and
HTTPS uses TCP port no 80 and 443 respectively as standard ports.
3. FTP Server: A server which has an FTP address and which is installed to receive the FTP
connections. It works on TCP/IP network and uses TCP port no 20 and 21 as Standard ports.
4. Domain Nameserver (DNS): A server which stores a list of IP addresses and their respective
domain names. Whenever a user passes a request to the DNS server, it resolves the IP
address to the respective hostname or vice-versa. The standard port for DNS is 53
5. Dynamic Host Configuration Protocol (DHCP): Configuring IP addresses on every
individual Host is a tough and time-taking task. A DHCP server is configured to assign the IP
addresses to the connecting hosts dynamically. We can make a router of our network as a
DHCP server. It will assign the IP addresses from a range of IP address or say a pool of
network (Definitions, S. and Hope, C. 2018).
Network Devices:
1. Router: A router is a device which works at Network layer i.e., third layer of OSI (Open
system interconnection) Model. Routers break the broadcast domain or networks. That means
a router is used to connect two different networks. Dynamic or static routing protocols are
configured on routers in order to reach to other routers.
2. Switch: Switch works at Layer 2 or Datalink layer of OSI model. Switch task is to receive the
packet from a source and then forward it to its destined host. The switch is updated device for
HUB. The switch uses a combination of addresses for packet forwarding. Its forward the
Network servers: In our Network or LAN, we create or establish some local servers. The task of
these servers is to give a response to the client whenever it tries to access it or passes any request.
Some of those local servers are explained below:
1. Mail Server: One of the main tasks which happen in a company is exchanging Emails. So for
sharing Emails from client to server or vice-versa we use Mail Servers. It is commonly done
by using SMTP (Simple Mail Transfer Protocol) which uses port no 23 as a standard port.
2. WEB Server: All the HTTP (Hypertext transfer protocol) or Https (HTTP Secure) requests
are processed by web servers. It is mostly used to host websites and web pages HTTP and
HTTPS uses TCP port no 80 and 443 respectively as standard ports.
3. FTP Server: A server which has an FTP address and which is installed to receive the FTP
connections. It works on TCP/IP network and uses TCP port no 20 and 21 as Standard ports.
4. Domain Nameserver (DNS): A server which stores a list of IP addresses and their respective
domain names. Whenever a user passes a request to the DNS server, it resolves the IP
address to the respective hostname or vice-versa. The standard port for DNS is 53
5. Dynamic Host Configuration Protocol (DHCP): Configuring IP addresses on every
individual Host is a tough and time-taking task. A DHCP server is configured to assign the IP
addresses to the connecting hosts dynamically. We can make a router of our network as a
DHCP server. It will assign the IP addresses from a range of IP address or say a pool of
network (Definitions, S. and Hope, C. 2018).
Network Devices:
1. Router: A router is a device which works at Network layer i.e., third layer of OSI (Open
system interconnection) Model. Routers break the broadcast domain or networks. That means
a router is used to connect two different networks. Dynamic or static routing protocols are
configured on routers in order to reach to other routers.
2. Switch: Switch works at Layer 2 or Datalink layer of OSI model. Switch task is to receive the
packet from a source and then forward it to its destined host. The switch is updated device for
HUB. The switch uses a combination of addresses for packet forwarding. Its forward the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

packets on the basis of destination MAC address. ARP(Address resolution protocol),
STP(Spanning tree protocol), VLAN(Virtual -LAN) are some of the features run at a switch.
3. Servers: Servers are installed into our local network when either there is a need of hosting
large files or hosting for key applications. We configure some local servers like WEB,
EMAIL, DNS etc. servers in order to be less relied on the internet or other sources
(GeeksforGeeks. 2015).
Inter-dependence of workstation hardware and Networking software
Workstation hardware is a device which is intended to do a specific high-end technical work like
graphics design, video editing etc.
We install a diskless workstation in our network and configure it in such a manner that its
booting takes place through a server in our local area network. It helps in creating a less cost and
more secure network for a company.
While booting up, the Operating system is loaded into the workstation from a server. Now
Whenever a client or workstation wants a data then it makes a request to the server. Then server
response it by sharing the required data and then after processing both the raw and processed
data are stored back into the server.
It is advised to use workstation one person at a time. However, it supports multi-tasking but in
order to make our network smooth and reliable, it is advised so. Servers and Workstations are put
under maintenance in a regular period of time (Networksguy 2010).
STP(Spanning tree protocol), VLAN(Virtual -LAN) are some of the features run at a switch.
3. Servers: Servers are installed into our local network when either there is a need of hosting
large files or hosting for key applications. We configure some local servers like WEB,
EMAIL, DNS etc. servers in order to be less relied on the internet or other sources
(GeeksforGeeks. 2015).
Inter-dependence of workstation hardware and Networking software
Workstation hardware is a device which is intended to do a specific high-end technical work like
graphics design, video editing etc.
We install a diskless workstation in our network and configure it in such a manner that its
booting takes place through a server in our local area network. It helps in creating a less cost and
more secure network for a company.
While booting up, the Operating system is loaded into the workstation from a server. Now
Whenever a client or workstation wants a data then it makes a request to the server. Then server
response it by sharing the required data and then after processing both the raw and processed
data are stored back into the server.
It is advised to use workstation one person at a time. However, it supports multi-tasking but in
order to make our network smooth and reliable, it is advised so. Servers and Workstations are put
under maintenance in a regular period of time (Networksguy 2010).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
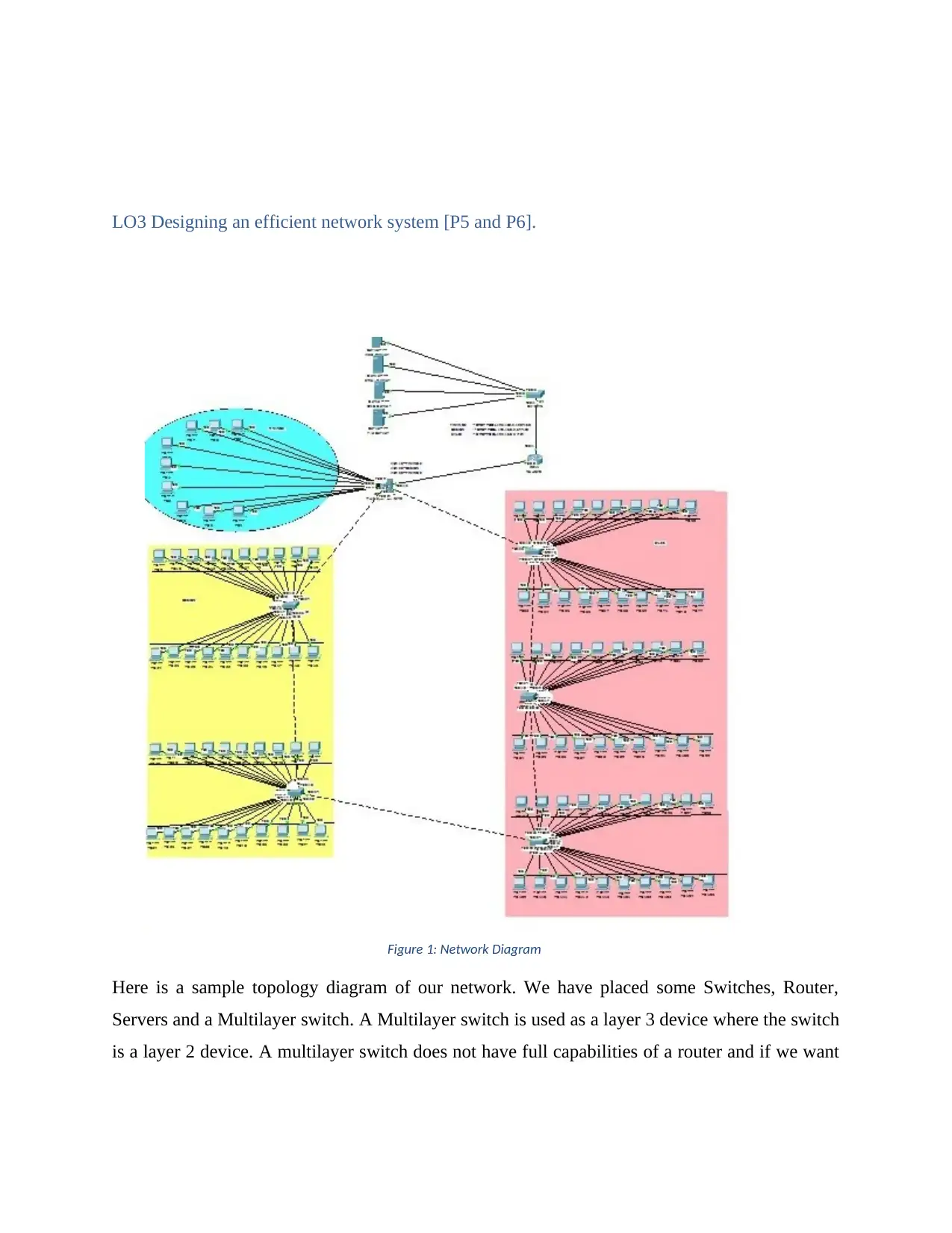
LO3 Designing an efficient network system [P5 and P6].
Here is a sample topology diagram of our network. We have placed some Switches, Router,
Servers and a Multilayer switch. A Multilayer switch is used as a layer 3 device where the switch
is a layer 2 device. A multilayer switch does not have full capabilities of a router and if we want
Figure 1: Network Diagram
Here is a sample topology diagram of our network. We have placed some Switches, Router,
Servers and a Multilayer switch. A Multilayer switch is used as a layer 3 device where the switch
is a layer 2 device. A multilayer switch does not have full capabilities of a router and if we want
Figure 1: Network Diagram

to make it work as a layer 3 device then we have to enable the Internet protocols on it otherwise
it will work as a layer 2 device.
Hardware requirements according to the scenario
Four Servers including Web, Email, DNS and File server
One printer for each department
A Router
Six switches and a multilayer switch in order to connect 104 Computers of different
departments.
Configuring devices of Network
Routers
I. We have configured the router interfaces with the given IP address range of
192.168.2.0/24.
II. VLSM(Variable length subnet mask) feature is used to divide this following range of IP
into multiple subnets. IP addresses and networks are divided into such a way that there is
a different network running between every department of the company.
III. For providing IP address to a router interface we use following method:
Router(config)# int fa0/0
Router(config-if)# ip add 192.168.2.1 255.255.255.192
Router(config-if)# no shut
Router(config-if)# exit
IV. Authenticating users: We must set a username and password for authorized access.
Router(config)# username admin password company1
Switch
I. Switches are connected with the hosts or user computers.
it will work as a layer 2 device.
Hardware requirements according to the scenario
Four Servers including Web, Email, DNS and File server
One printer for each department
A Router
Six switches and a multilayer switch in order to connect 104 Computers of different
departments.
Configuring devices of Network
Routers
I. We have configured the router interfaces with the given IP address range of
192.168.2.0/24.
II. VLSM(Variable length subnet mask) feature is used to divide this following range of IP
into multiple subnets. IP addresses and networks are divided into such a way that there is
a different network running between every department of the company.
III. For providing IP address to a router interface we use following method:
Router(config)# int fa0/0
Router(config-if)# ip add 192.168.2.1 255.255.255.192
Router(config-if)# no shut
Router(config-if)# exit
IV. Authenticating users: We must set a username and password for authorized access.
Router(config)# username admin password company1
Switch
I. Switches are connected with the hosts or user computers.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
II. Switches are configured in such a way that every user can communicate or share data
between other users of the network.
III. Port security feature is enabled on every switch port in order to protect the network from
unauthorized access. If an attacker will try to attack our network then it will be blocked to
do so.
V. Authenticating users: We must set a username and password for authorized access.
Router(config)# username admin password company1
Servers
I. Local servers are configured into the network for giving the response or required data and
information to the users of the network. Some of the servers present our the Web server,
Mail server, File server and DNS server.
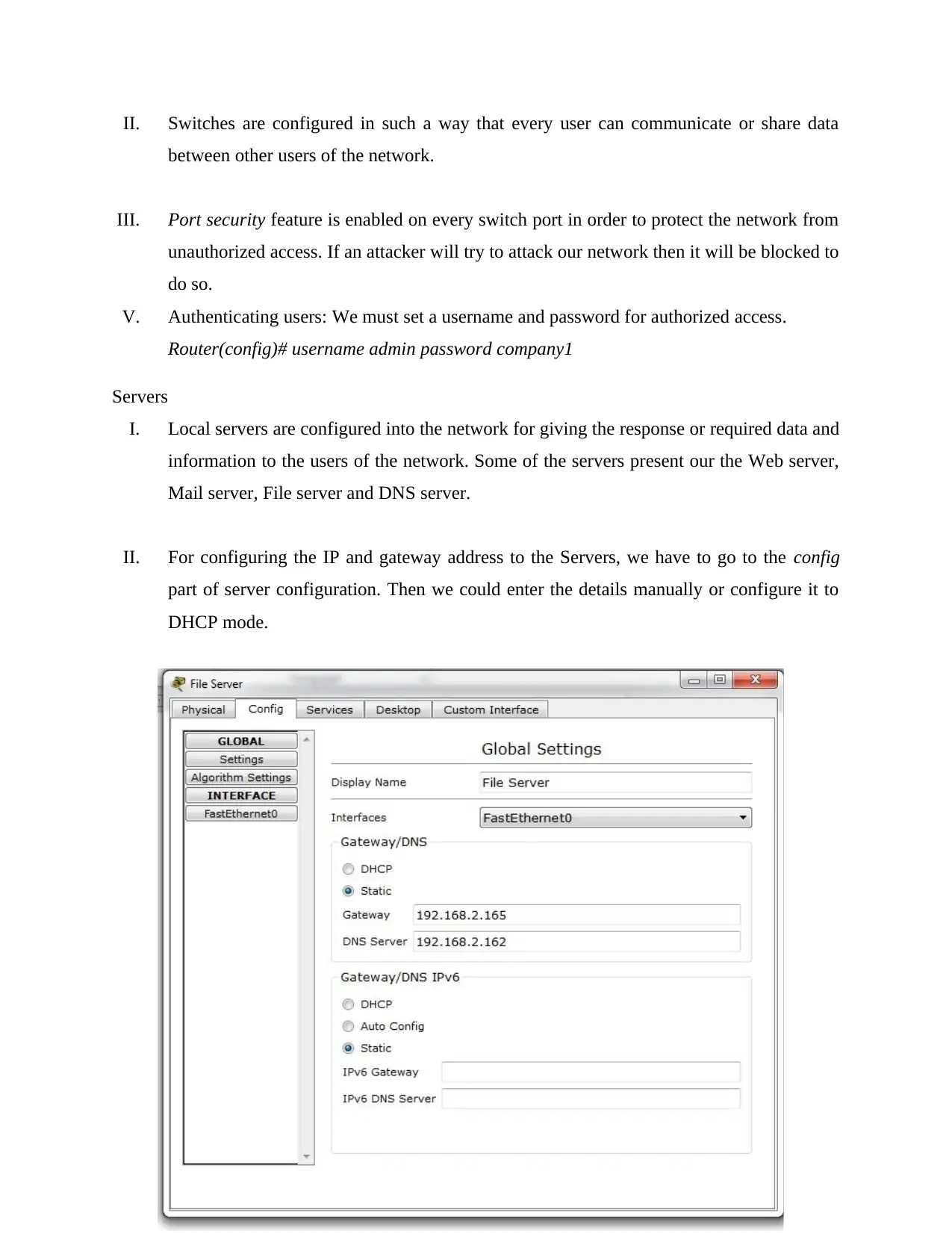
II. For configuring the IP and gateway address to the Servers, we have to go to the config
part of server configuration. Then we could enter the details manually or configure it to
DHCP mode.
between other users of the network.
III. Port security feature is enabled on every switch port in order to protect the network from
unauthorized access. If an attacker will try to attack our network then it will be blocked to
do so.
V. Authenticating users: We must set a username and password for authorized access.
Router(config)# username admin password company1
Servers
I. Local servers are configured into the network for giving the response or required data and
information to the users of the network. Some of the servers present our the Web server,
Mail server, File server and DNS server.
II. For configuring the IP and gateway address to the Servers, we have to go to the config
part of server configuration. Then we could enter the details manually or configure it to
DHCP mode.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Computers
I. Windows or Linux based Operating system
II. Internet connection
III. Latest Antivirus software for threat protection.
IV. Update checks should be done regularly for the fast and smooth functioning of the
computers.
Printers
I. Clean the Printers Head, Insides and Hood regularly in order to maintain them for a long
time.
II. Use the right refills and cartridges for your printer.
III. While not in use, turn them off.
IV. Keep updated drivers and try to use it regularly.
Testing the network
I. Checking the connectivity :
Check the connectivity to other hosts of network using PING command
For eg: ping 192.168.2.195
Pinging 192.168.2.195 with 32 bytes of data:
Reply from 192.168.2.195: bytes=32 time=2ms TTL=128
Reply from 192.168.2.195: bytes=32 time=1ms TTL=128
Reply from 192.168.2.195: bytes=32 time=6ms TTL=128
I. Windows or Linux based Operating system
II. Internet connection
III. Latest Antivirus software for threat protection.
IV. Update checks should be done regularly for the fast and smooth functioning of the
computers.
Printers
I. Clean the Printers Head, Insides and Hood regularly in order to maintain them for a long
time.
II. Use the right refills and cartridges for your printer.
III. While not in use, turn them off.
IV. Keep updated drivers and try to use it regularly.
Testing the network
I. Checking the connectivity :
Check the connectivity to other hosts of network using PING command
For eg: ping 192.168.2.195
Pinging 192.168.2.195 with 32 bytes of data:
Reply from 192.168.2.195: bytes=32 time=2ms TTL=128
Reply from 192.168.2.195: bytes=32 time=1ms TTL=128
Reply from 192.168.2.195: bytes=32 time=6ms TTL=128
Reply from 192.168.2.195: bytes=32 time=23ms TTL=128
Ping statistics for 192.168.2.195:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 23ms, Average = 8ms
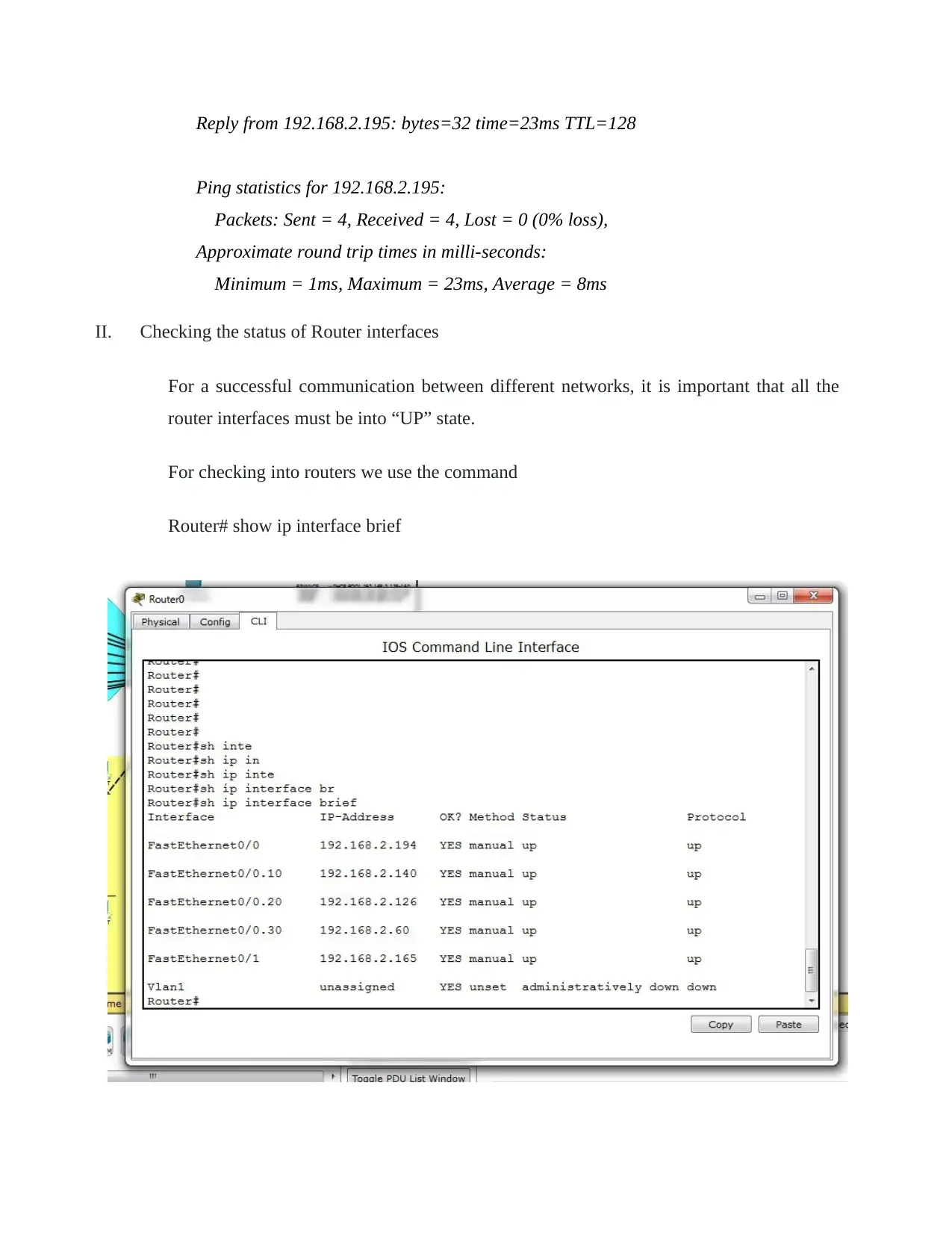
II. Checking the status of Router interfaces
For a successful communication between different networks, it is important that all the
router interfaces must be into “UP” state.
For checking into routers we use the command
Router# show ip interface brief
Ping statistics for 192.168.2.195:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 1ms, Maximum = 23ms, Average = 8ms
II. Checking the status of Router interfaces
For a successful communication between different networks, it is important that all the
router interfaces must be into “UP” state.
For checking into routers we use the command
Router# show ip interface brief
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 18
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





