Local Area Networking Technologies, Security and Performance Report
VerifiedAdded on 2020/10/22
|27
|6446
|460
Report
AI Summary
This report provides a comprehensive overview of Local Area Networking (LAN) technologies, focusing on their evaluation, design, implementation, and management. It begins by critically evaluating various LAN technologies like Ethernet, FDDI, and DHCP, considering their suitability for a company like FootFall Field Marketing Ltd. The report then delves into traffic-intensive services, analyzing their impact on network performance and suggesting methods for optimization. Key concerns related to LAN security, reliability, and performance are addressed, along with recommendations to sustain these aspects. The report also includes the design of a LAN infrastructure for FootFall Field Marketing Ltd, a critical evaluation of LAN components, and the implementation of network security measures. Furthermore, it covers the building, configuration, and testing of the LAN, along with monitoring and management strategies to resolve issues and improve overall performance. The conclusion summarizes the key findings and recommendations for effective LAN management.

Local Area Networking
Technologies
Technologies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................1
A.C 1.1 critical evaluation of different LAN technologies ...................................................1
A.C 1.2 Traffic intensive services and their performance......................................................2
A.C 1.3 LAN concerns and recommendations to sustain network security, reliability and
performance............................................................................................................................3
TASK 2 ...........................................................................................................................................4
AC2.1 Designing LAN infrastructure for FootFall field marketing Ltd................................4
A.C 2.2 Critical evaluation of the suitability of LAN components .......................................6
TASK 3............................................................................................................................................8
AC3.1 Building and configuration of LAN............................................................................8
A.C 3.2 Implementation of network security on a LAN ....................................................12
A.C 3.3 critically review and test a LAN.............................................................................15
TASK 4 .........................................................................................................................................16
A.C 4.1 Monitoring and management of LAN infrastructure ............................................16
A.C 4.2 Resolving LAN issues to improve security, reliability and performance ..............18
A.C 4.3 Evaluating LAN performance ................................................................................20
CONCLUSION..............................................................................................................................21
REFERENCES..............................................................................................................................23
INTRODUCTION...........................................................................................................................1
A.C 1.1 critical evaluation of different LAN technologies ...................................................1
A.C 1.2 Traffic intensive services and their performance......................................................2
A.C 1.3 LAN concerns and recommendations to sustain network security, reliability and
performance............................................................................................................................3
TASK 2 ...........................................................................................................................................4
AC2.1 Designing LAN infrastructure for FootFall field marketing Ltd................................4
A.C 2.2 Critical evaluation of the suitability of LAN components .......................................6
TASK 3............................................................................................................................................8
AC3.1 Building and configuration of LAN............................................................................8
A.C 3.2 Implementation of network security on a LAN ....................................................12
A.C 3.3 critically review and test a LAN.............................................................................15
TASK 4 .........................................................................................................................................16
A.C 4.1 Monitoring and management of LAN infrastructure ............................................16
A.C 4.2 Resolving LAN issues to improve security, reliability and performance ..............18
A.C 4.3 Evaluating LAN performance ................................................................................20
CONCLUSION..............................................................................................................................21
REFERENCES..............................................................................................................................23

INTRODUCTION
Local area networking is considered as a network in which a combination of systems are
connected together and are sharing a common communication link (Narayanasamy and Pulla,
2017). It covers small area and range of network, so it can be classified as compatible enough for
schools, small buildings, offices etc. The local area connection can be wireless, wired or both as
well. The report discusses about various types of LAN's and factors associated with it. Also, it
involves the designing and implementation of the local area network for FootFall field marketing
Ltd. It also involves the designing and implementation of the security concerns of LAN.
Reviewing and testing of LAN will also be discussed in the report.
A.C 1.1 critical evaluation of different LAN technologies
The FootFall Field Marketing Ltd can use local area networking (LAN) to establish
interconnections between its computer systems and other devices. A wide number of LAN
technologies are available for the FootFall Field Marketing Ltd such as Ethernet, token ring,
FDDI, virtual LAN, voice over internet protocol internet technology, virtual LAN trucking
protocol and the DHCP serivces.
Voice over protocol
With the use of Voice over internet protocol the FootFall Field Marketing Ltd can use
internet by sending packets of voice data with the help of IP (Qiu andVasilakosJing, 2014). This
technology is able to manage calls and to translate the telephonic data into internet protocol
addresses. This technology reduces cost but during the interruptions or weak internet signals
service is lost. This technology will enable organisation to enhance its accessibility and quality
of voice. But it requires internet connection with high bandwidth. Thus, when FootFall Ltd
implements this technique then during high traffic it will become costly for the company to
manage its efficiency and cost.
Fibre distributed data interface (FDDI)
This LAN technology can provide better speed as compare to Ethernet and token ring
technologies. The organisation can also use this LAN technology as tool to interconnect Ethernet
and token ring. However, their cost is higher and are more fragile (Movassaghi and et.al., 2014).
FDDI is more suitable for the companies which have excessive network traffic so that its
excessive cost is in alignment with high quality. FootFall Ltd may find other options instead of
this technique which can provide solutions in low cost.
1
Local area networking is considered as a network in which a combination of systems are
connected together and are sharing a common communication link (Narayanasamy and Pulla,
2017). It covers small area and range of network, so it can be classified as compatible enough for
schools, small buildings, offices etc. The local area connection can be wireless, wired or both as
well. The report discusses about various types of LAN's and factors associated with it. Also, it
involves the designing and implementation of the local area network for FootFall field marketing
Ltd. It also involves the designing and implementation of the security concerns of LAN.
Reviewing and testing of LAN will also be discussed in the report.
A.C 1.1 critical evaluation of different LAN technologies
The FootFall Field Marketing Ltd can use local area networking (LAN) to establish
interconnections between its computer systems and other devices. A wide number of LAN
technologies are available for the FootFall Field Marketing Ltd such as Ethernet, token ring,
FDDI, virtual LAN, voice over internet protocol internet technology, virtual LAN trucking
protocol and the DHCP serivces.
Voice over protocol
With the use of Voice over internet protocol the FootFall Field Marketing Ltd can use
internet by sending packets of voice data with the help of IP (Qiu andVasilakosJing, 2014). This
technology is able to manage calls and to translate the telephonic data into internet protocol
addresses. This technology reduces cost but during the interruptions or weak internet signals
service is lost. This technology will enable organisation to enhance its accessibility and quality
of voice. But it requires internet connection with high bandwidth. Thus, when FootFall Ltd
implements this technique then during high traffic it will become costly for the company to
manage its efficiency and cost.
Fibre distributed data interface (FDDI)
This LAN technology can provide better speed as compare to Ethernet and token ring
technologies. The organisation can also use this LAN technology as tool to interconnect Ethernet
and token ring. However, their cost is higher and are more fragile (Movassaghi and et.al., 2014).
FDDI is more suitable for the companies which have excessive network traffic so that its
excessive cost is in alignment with high quality. FootFall Ltd may find other options instead of
this technique which can provide solutions in low cost.
1
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Ethernet:
This technology can give the best solution to FootFall Field Marketing Ltd in terms of
expenses, speed and installation procedures. But their mobility is limited and more vulnerable to
crosstalk issues. As this is suitable for short distance only organisation may bear additional
charges in future for its expansion. This is one of the most suitable LAN technology which can
be implemented easily. The given organisation can also implement this. It will be the best
solution in terms of speed, cost and network traffic (Jing, Vasilakos and Qiu, 2014.). However,
the most advanced organisations does not use it because they prefer some more advanced and
secure techniques such as DHCP.
Dynamic Host Configuration protocol(DHCP):
This technology provides IP address to systems from a predefined range which is
configured for the network. It can easily manage the IP addresses and large network support. It
has higher dependency on server availability which serves as its biggest disadvantage. It is
considered as a network protocol that helps in assigning the IP to any system.
Also, this is considered as an effective way to assign the internet protocol to the systems.
Whether it is about some node, system or branch, dynamic host configuration protocol can help
in assigning IP to any of them. DHCP is mainly preferable for the companies which have large
operational area. FootFall Ltd is operating in one building only. Thus, this solution may not be
feasible and economic for the company (Coronel and Morris, 2016). However, in future when
company plans to expand its business through vast range then it may be suitable but as per
present case study this technology is not recommended for the given organisation.
A.C 1.2 Traffic intensive services and their performance
Network traffic is defined as the amount of data flow which is transmitted through a
network at any particular instant of time. There are certain services which occupies the majority
of network bandwidth and makes traffic occupied. As a result, time delay in transmission of
upcoming data increases. These traffic occupying services are known as the traffic intensive
services (Egbunike and Rajendran, 2017). Activities such as video streaming, voice over internet
protocols are intensive to network traffic because these activities have higher demand. Other
activities such as mailing conversations, browsing does not consume much network traffic
(Grandhi, 2017). For instance FootFall Field Marketing Ltd may have to deal with lots of calls
2
This technology can give the best solution to FootFall Field Marketing Ltd in terms of
expenses, speed and installation procedures. But their mobility is limited and more vulnerable to
crosstalk issues. As this is suitable for short distance only organisation may bear additional
charges in future for its expansion. This is one of the most suitable LAN technology which can
be implemented easily. The given organisation can also implement this. It will be the best
solution in terms of speed, cost and network traffic (Jing, Vasilakos and Qiu, 2014.). However,
the most advanced organisations does not use it because they prefer some more advanced and
secure techniques such as DHCP.
Dynamic Host Configuration protocol(DHCP):
This technology provides IP address to systems from a predefined range which is
configured for the network. It can easily manage the IP addresses and large network support. It
has higher dependency on server availability which serves as its biggest disadvantage. It is
considered as a network protocol that helps in assigning the IP to any system.
Also, this is considered as an effective way to assign the internet protocol to the systems.
Whether it is about some node, system or branch, dynamic host configuration protocol can help
in assigning IP to any of them. DHCP is mainly preferable for the companies which have large
operational area. FootFall Ltd is operating in one building only. Thus, this solution may not be
feasible and economic for the company (Coronel and Morris, 2016). However, in future when
company plans to expand its business through vast range then it may be suitable but as per
present case study this technology is not recommended for the given organisation.
A.C 1.2 Traffic intensive services and their performance
Network traffic is defined as the amount of data flow which is transmitted through a
network at any particular instant of time. There are certain services which occupies the majority
of network bandwidth and makes traffic occupied. As a result, time delay in transmission of
upcoming data increases. These traffic occupying services are known as the traffic intensive
services (Egbunike and Rajendran, 2017). Activities such as video streaming, voice over internet
protocols are intensive to network traffic because these activities have higher demand. Other
activities such as mailing conversations, browsing does not consume much network traffic
(Grandhi, 2017). For instance FootFall Field Marketing Ltd may have to deal with lots of calls
2
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

then these calls need to be at priority. If network usage priorities are set by traffic intensive
services then bandwidth of the network is effectively distributes and hence cost and speed factor
improves. The FootFall Field Marketing Ltd can use differentiated service code-point for
management and classification of network traffic related issues. It also provides quality of
service (QOS).
The most important parameters for measurement of quality of video and voice over
internet protocol are latency, jitters and path delay and the perception of the network quality by
organisation. Another tool for resolving the traffic intensive issues is to use TOS byte (Smith,
and et.al., 2017). When the performance of traffic intensive services are not evaluated then it
may be difficult for the company to maintain the networking quality. These methods make it
easy for the organisation to analyse the activities which increases the network traffic and hence
they help in improving speed parameters. For the companies which do not have specific methods
for its measurement traffic can cause delay in executing priority tasks. TYPE OF SERVICE
(TOS) byte is one of the attributes of IP packets. To achieve QOS we can only give a priority
request so that a low delay and reliable high throughput routing path can be provided. In TOS
byte 3 bits of beginning are precedence bits, following 4 bits are defined as TOS bits and last bit
is defined as the MBZ (must be zero) bit (Movassaghi and et.al., 2014). To deliver video and
audio stream FootFall Field Marketing Ltd can use streaming server for assuring regular flow of
audio-video across congested and slow network. During interference also it will try to sustain the
stream flow, by degrading the quality.
A.C 1.3 LAN concerns and recommendations to sustain network security, reliability and
performance
Concerns related to LAN implementation:
Apart from major security issues LAN network also suffers from installation issues, path
loss, battery longevity and interferences issues. The multipath propagation and interference
issues can corrupt the received signals. FootFall Field Marketing Ltd has indoor application
multiple path propagation can be a severe issue. This interference problems can be reduced by
implementing equalizers and antenna.
Networking threats:
3
services then bandwidth of the network is effectively distributes and hence cost and speed factor
improves. The FootFall Field Marketing Ltd can use differentiated service code-point for
management and classification of network traffic related issues. It also provides quality of
service (QOS).
The most important parameters for measurement of quality of video and voice over
internet protocol are latency, jitters and path delay and the perception of the network quality by
organisation. Another tool for resolving the traffic intensive issues is to use TOS byte (Smith,
and et.al., 2017). When the performance of traffic intensive services are not evaluated then it
may be difficult for the company to maintain the networking quality. These methods make it
easy for the organisation to analyse the activities which increases the network traffic and hence
they help in improving speed parameters. For the companies which do not have specific methods
for its measurement traffic can cause delay in executing priority tasks. TYPE OF SERVICE
(TOS) byte is one of the attributes of IP packets. To achieve QOS we can only give a priority
request so that a low delay and reliable high throughput routing path can be provided. In TOS
byte 3 bits of beginning are precedence bits, following 4 bits are defined as TOS bits and last bit
is defined as the MBZ (must be zero) bit (Movassaghi and et.al., 2014). To deliver video and
audio stream FootFall Field Marketing Ltd can use streaming server for assuring regular flow of
audio-video across congested and slow network. During interference also it will try to sustain the
stream flow, by degrading the quality.
A.C 1.3 LAN concerns and recommendations to sustain network security, reliability and
performance
Concerns related to LAN implementation:
Apart from major security issues LAN network also suffers from installation issues, path
loss, battery longevity and interferences issues. The multipath propagation and interference
issues can corrupt the received signals. FootFall Field Marketing Ltd has indoor application
multiple path propagation can be a severe issue. This interference problems can be reduced by
implementing equalizers and antenna.
Networking threats:
3

FootFall Ltd requires dealing with networking threats which are major concerns for the
authorities. Ineffective strategies to deal with these issues can lead to system crash and data
leakage. A firewall resource can be implemented as an initial router. For providing password
encryption security protocols. Secured LAN network must consider attributes such as switching
and layer 2 security, IP permission list, port authentication and related security (Waliullah,
Moniruzzaman and Rahman, 2015).
Unauthorised access:
The network security can be enhanced by preventing unauthenticated usage of network
traffic. For this purpose access control list (ACL) can be implemented by FootFall Ltd to prevent
the unauthorised access (Narayanasamy and Pulla, 2017). Thus, ACL's main task is to effectively
manage authentication issues in a fine grained manner. Another secure tool is to use media
access control (MAC) filtering. This security control tool allows blacklisting of certain networks
from accessing in order to prevent the unauthorised access. Since MAC can identify devices only
an authorised member will also need to be in white list for every system that will be used to
access the network. MAC filtering gives more effective results ins wired networking because in
wired networking it becomes more difficult to identify the authorised one. Hence, security of
LAN is increased.
TASK 2
AC2.1 Designing LAN infrastructure for FootFall field marketing Ltd.
This is the infra structure of FootFall field marketing Ltd. It makes involvement of all the five
departments and IT department is connected to all the other departments of the organisation. The
basic requirement of the FootFall field marketing Ltd is that the manager of IT department
should be able to access the other systems that are connected over the network. So, it has been
centralised in a way so that it remains connected with all the other systems.
4
authorities. Ineffective strategies to deal with these issues can lead to system crash and data
leakage. A firewall resource can be implemented as an initial router. For providing password
encryption security protocols. Secured LAN network must consider attributes such as switching
and layer 2 security, IP permission list, port authentication and related security (Waliullah,
Moniruzzaman and Rahman, 2015).
Unauthorised access:
The network security can be enhanced by preventing unauthenticated usage of network
traffic. For this purpose access control list (ACL) can be implemented by FootFall Ltd to prevent
the unauthorised access (Narayanasamy and Pulla, 2017). Thus, ACL's main task is to effectively
manage authentication issues in a fine grained manner. Another secure tool is to use media
access control (MAC) filtering. This security control tool allows blacklisting of certain networks
from accessing in order to prevent the unauthorised access. Since MAC can identify devices only
an authorised member will also need to be in white list for every system that will be used to
access the network. MAC filtering gives more effective results ins wired networking because in
wired networking it becomes more difficult to identify the authorised one. Hence, security of
LAN is increased.
TASK 2
AC2.1 Designing LAN infrastructure for FootFall field marketing Ltd.
This is the infra structure of FootFall field marketing Ltd. It makes involvement of all the five
departments and IT department is connected to all the other departments of the organisation. The
basic requirement of the FootFall field marketing Ltd is that the manager of IT department
should be able to access the other systems that are connected over the network. So, it has been
centralised in a way so that it remains connected with all the other systems.
4
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
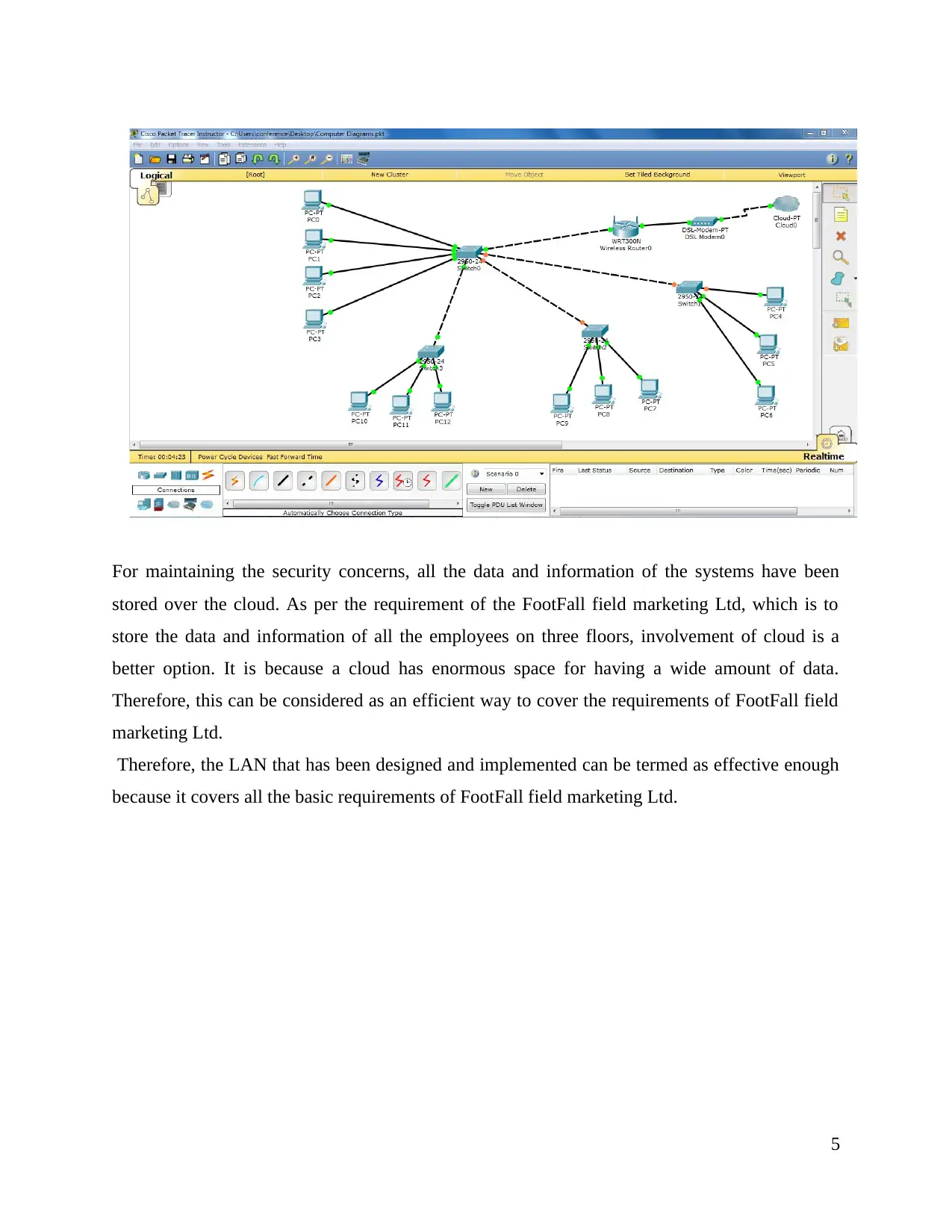
For maintaining the security concerns, all the data and information of the systems have been
stored over the cloud. As per the requirement of the FootFall field marketing Ltd, which is to
store the data and information of all the employees on three floors, involvement of cloud is a
better option. It is because a cloud has enormous space for having a wide amount of data.
Therefore, this can be considered as an efficient way to cover the requirements of FootFall field
marketing Ltd.
Therefore, the LAN that has been designed and implemented can be termed as effective enough
because it covers all the basic requirements of FootFall field marketing Ltd.
5
stored over the cloud. As per the requirement of the FootFall field marketing Ltd, which is to
store the data and information of all the employees on three floors, involvement of cloud is a
better option. It is because a cloud has enormous space for having a wide amount of data.
Therefore, this can be considered as an efficient way to cover the requirements of FootFall field
marketing Ltd.
Therefore, the LAN that has been designed and implemented can be termed as effective enough
because it covers all the basic requirements of FootFall field marketing Ltd.
5
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
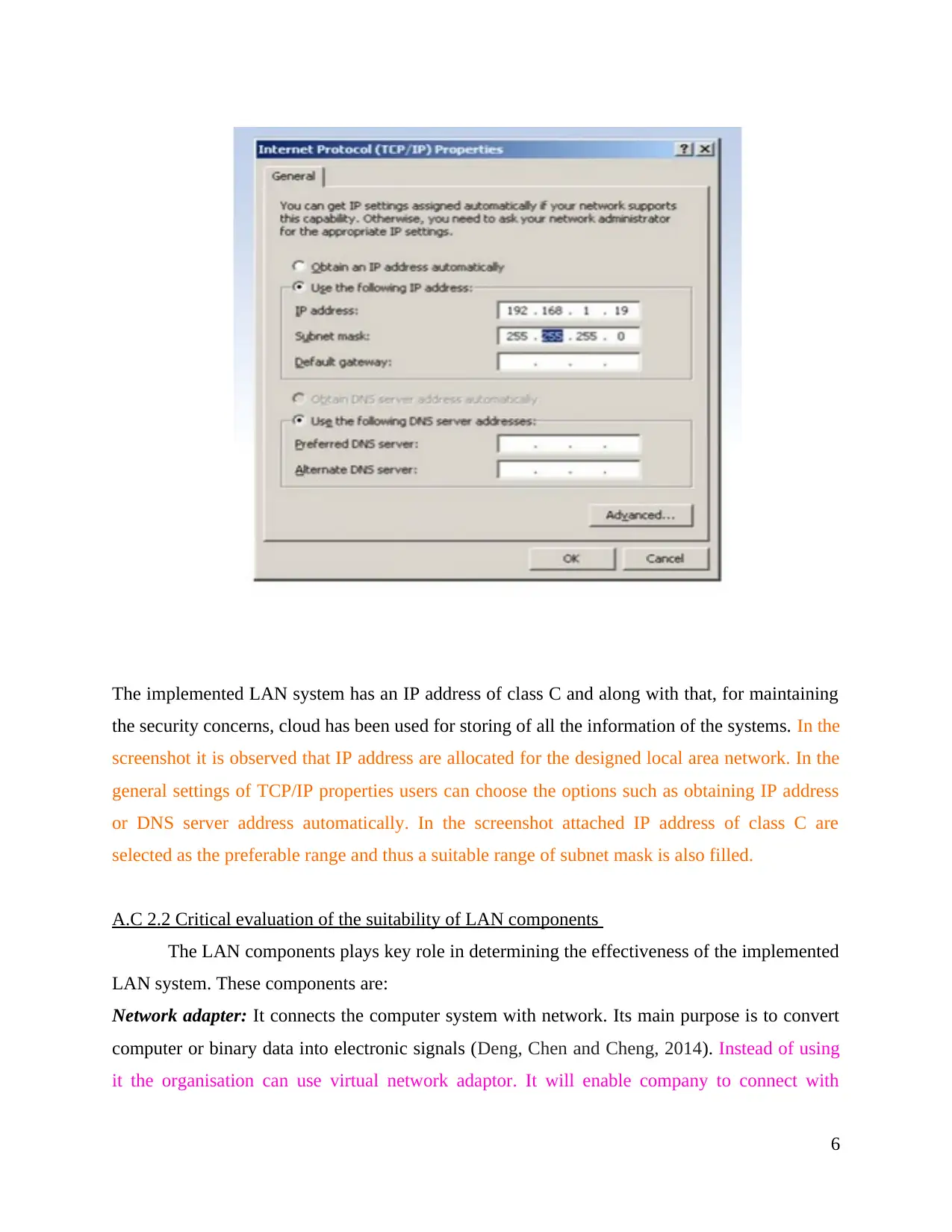
The implemented LAN system has an IP address of class C and along with that, for maintaining
the security concerns, cloud has been used for storing of all the information of the systems. In the
screenshot it is observed that IP address are allocated for the designed local area network. In the
general settings of TCP/IP properties users can choose the options such as obtaining IP address
or DNS server address automatically. In the screenshot attached IP address of class C are
selected as the preferable range and thus a suitable range of subnet mask is also filled.
A.C 2.2 Critical evaluation of the suitability of LAN components
The LAN components plays key role in determining the effectiveness of the implemented
LAN system. These components are:
Network adapter: It connects the computer system with network. Its main purpose is to convert
computer or binary data into electronic signals (Deng, Chen and Cheng, 2014). Instead of using
it the organisation can use virtual network adaptor. It will enable company to connect with
6
the security concerns, cloud has been used for storing of all the information of the systems. In the
screenshot it is observed that IP address are allocated for the designed local area network. In the
general settings of TCP/IP properties users can choose the options such as obtaining IP address
or DNS server address automatically. In the screenshot attached IP address of class C are
selected as the preferable range and thus a suitable range of subnet mask is also filled.
A.C 2.2 Critical evaluation of the suitability of LAN components
The LAN components plays key role in determining the effectiveness of the implemented
LAN system. These components are:
Network adapter: It connects the computer system with network. Its main purpose is to convert
computer or binary data into electronic signals (Deng, Chen and Cheng, 2014). Instead of using
it the organisation can use virtual network adaptor. It will enable company to connect with
6

internet and to make its functions more accurate and smooth. With the help of this the company
will be able to transmit its data and information from one system to other over network. Thus, it
will make data sharing easy and quick for the organisation and help to achieve its operational
task with ease.
Network Medium: The wired LAN network requires cables for interconnections. There are
various options available such as twisted pair cable, optical fibre cable, UTP cable or coaxial
cable. Twisted cable is also known as Ethernet or network cable. UTP cable has higher
bandwidth range and lower cost as compare to twisted pair or optical fibre. For wireless LAN
network data transmission is achieved by radio waves instead of cables. The data transfer rate is
very higher for network medium comprising optical fibres. They are transparent and expensive
hence their usage can increase the cost of implementation (Simmons, 2014).
Cable connector: These are also known as network or Ethernet port. RJ45 is the most widely
used connector. It mainly connects the twisted pair cable. Thus, for wired network this is an
important component. The use of cable connector for wired network increases the complexity of
design and implementation. If organisation will use these connectors then, there will be complex
network of cables. In cases when there is problem in specific cable then it becomes difficult to
select the one from the bunch of cables or from the cables which are transplanted in walls. The
Ethernet provided with cable connection can provide high speed as compare to the wireless
connection. It is because the wireless connection will involve more interference. Hence, for
better productivity the LAN design of the company must use wired connection.
Power supply: This one is the component which is implemented by both wired and wireless
networks. Organisation implementing wired network uses cables to transmit data in the form of
electronic pulse (Deng, Chen and Cheng, 2014). On the other hand in case of wireless network
the power supply is re requited to generate the radio waves which serves as the networking
medium.
Switch: Switch is also called hub or router. It provides routing path. Signals received on one port
of the switch is transmitted to all of its other ports. They provide a switching table in RAM. If
company will use hubs instead of these switches then, there will be great impact on latency and
speed of the LAN network. In comparison to hubs switches are more capable and provide high
speed. The company can prefer routers over switches. But in regards with the small size of the
LAN network of organisation switches will be more suitable from cost perspective. It will also
7
will be able to transmit its data and information from one system to other over network. Thus, it
will make data sharing easy and quick for the organisation and help to achieve its operational
task with ease.
Network Medium: The wired LAN network requires cables for interconnections. There are
various options available such as twisted pair cable, optical fibre cable, UTP cable or coaxial
cable. Twisted cable is also known as Ethernet or network cable. UTP cable has higher
bandwidth range and lower cost as compare to twisted pair or optical fibre. For wireless LAN
network data transmission is achieved by radio waves instead of cables. The data transfer rate is
very higher for network medium comprising optical fibres. They are transparent and expensive
hence their usage can increase the cost of implementation (Simmons, 2014).
Cable connector: These are also known as network or Ethernet port. RJ45 is the most widely
used connector. It mainly connects the twisted pair cable. Thus, for wired network this is an
important component. The use of cable connector for wired network increases the complexity of
design and implementation. If organisation will use these connectors then, there will be complex
network of cables. In cases when there is problem in specific cable then it becomes difficult to
select the one from the bunch of cables or from the cables which are transplanted in walls. The
Ethernet provided with cable connection can provide high speed as compare to the wireless
connection. It is because the wireless connection will involve more interference. Hence, for
better productivity the LAN design of the company must use wired connection.
Power supply: This one is the component which is implemented by both wired and wireless
networks. Organisation implementing wired network uses cables to transmit data in the form of
electronic pulse (Deng, Chen and Cheng, 2014). On the other hand in case of wireless network
the power supply is re requited to generate the radio waves which serves as the networking
medium.
Switch: Switch is also called hub or router. It provides routing path. Signals received on one port
of the switch is transmitted to all of its other ports. They provide a switching table in RAM. If
company will use hubs instead of these switches then, there will be great impact on latency and
speed of the LAN network. In comparison to hubs switches are more capable and provide high
speed. The company can prefer routers over switches. But in regards with the small size of the
LAN network of organisation switches will be more suitable from cost perspective. It will also
7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
provide additional advantage of providing sufficient bandwidth to each device connected with
the switch.
Network Software: This software application converts the data packets into segments and each
segment is converted into packets. These network software enhances the security of the system
and are of low cost. Each packet has its source and destination mentioned on it. These data
packets are interpreted by the receiver to convert into meaningful information and to transmit it
to the desired destination (Jing, Vasilakos and Qiu, 2014).
TASK 3
AC3.1 Building and configuration of LAN
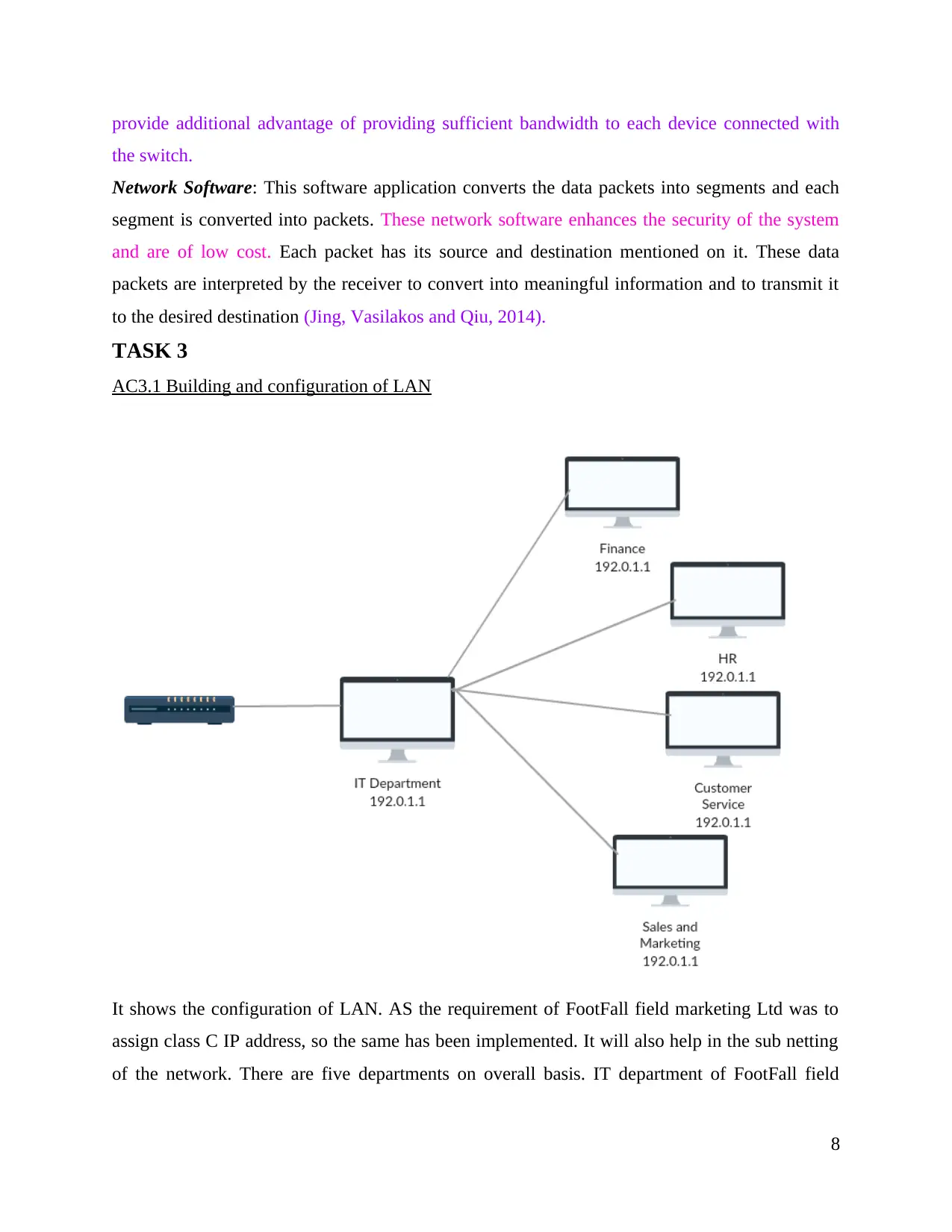
It shows the configuration of LAN. AS the requirement of FootFall field marketing Ltd was to
assign class C IP address, so the same has been implemented. It will also help in the sub netting
of the network. There are five departments on overall basis. IT department of FootFall field
8
the switch.
Network Software: This software application converts the data packets into segments and each
segment is converted into packets. These network software enhances the security of the system
and are of low cost. Each packet has its source and destination mentioned on it. These data
packets are interpreted by the receiver to convert into meaningful information and to transmit it
to the desired destination (Jing, Vasilakos and Qiu, 2014).
TASK 3
AC3.1 Building and configuration of LAN
It shows the configuration of LAN. AS the requirement of FootFall field marketing Ltd was to
assign class C IP address, so the same has been implemented. It will also help in the sub netting
of the network. There are five departments on overall basis. IT department of FootFall field
8
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
marketing Ltd have been centralised in a way that the manager of department can access all the
other department systems that are connected over the network.
9
other department systems that are connected over the network.
9
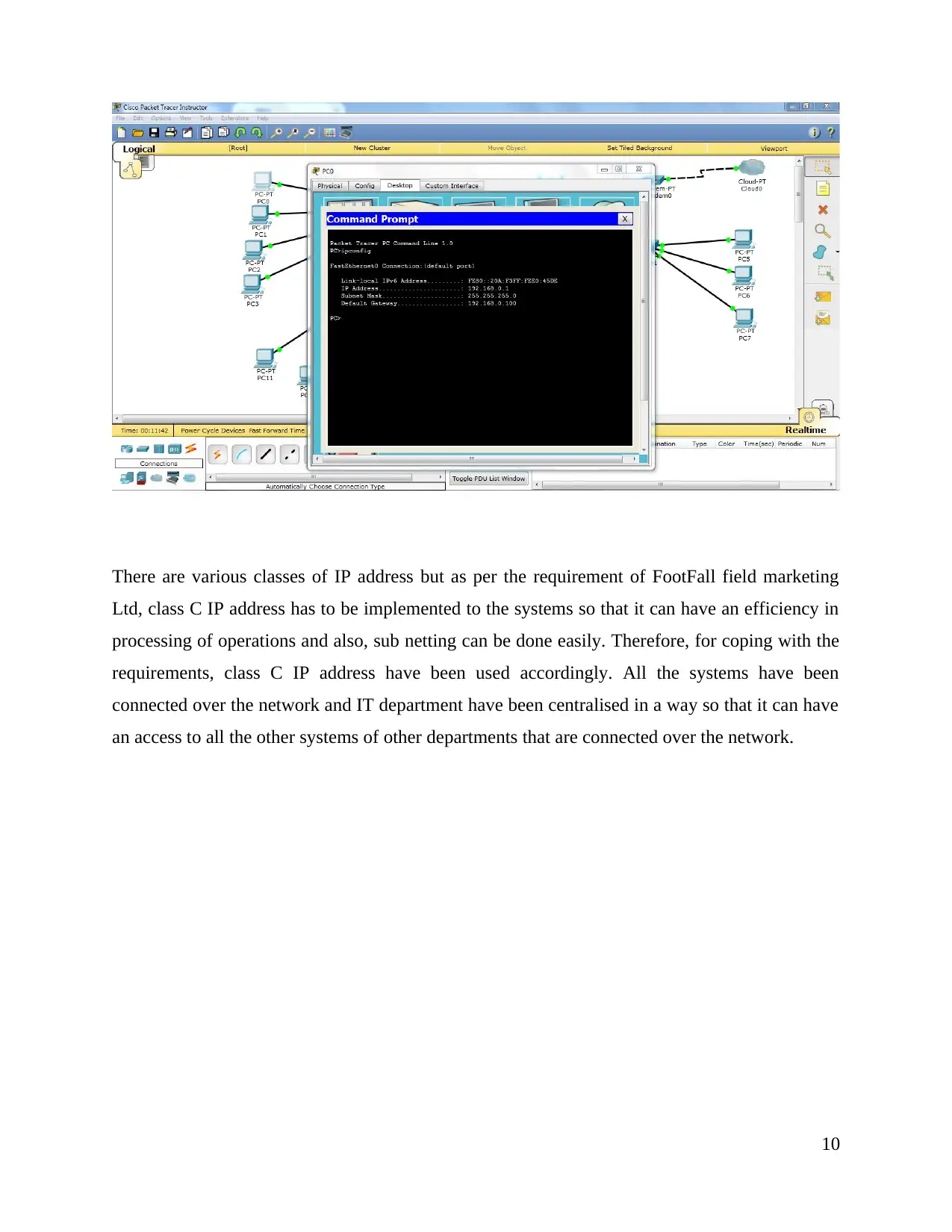
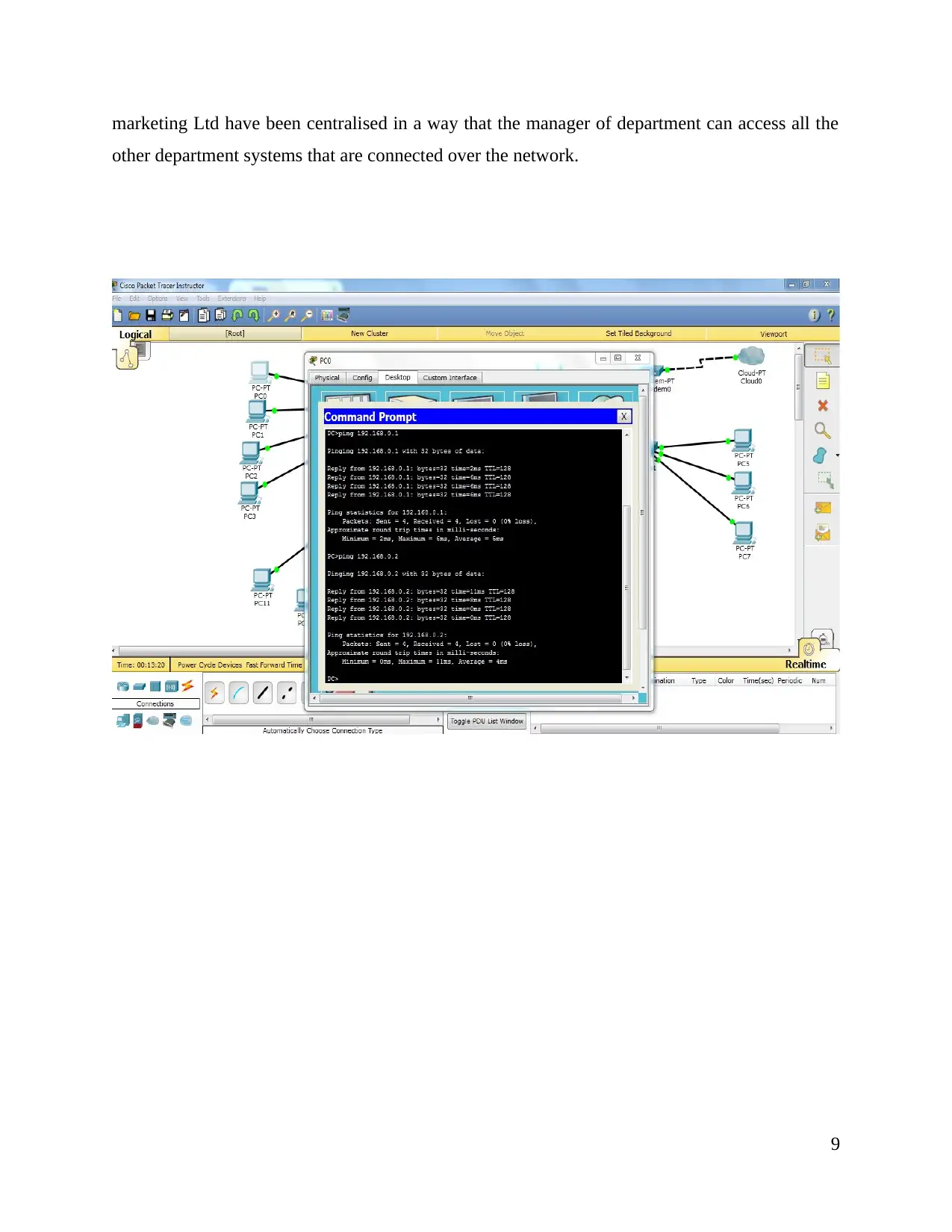
There are various classes of IP address but as per the requirement of FootFall field marketing
Ltd, class C IP address has to be implemented to the systems so that it can have an efficiency in
processing of operations and also, sub netting can be done easily. Therefore, for coping with the
requirements, class C IP address have been used accordingly. All the systems have been
connected over the network and IT department have been centralised in a way so that it can have
an access to all the other systems of other departments that are connected over the network.
10
Ltd, class C IP address has to be implemented to the systems so that it can have an efficiency in
processing of operations and also, sub netting can be done easily. Therefore, for coping with the
requirements, class C IP address have been used accordingly. All the systems have been
connected over the network and IT department have been centralised in a way so that it can have
an access to all the other systems of other departments that are connected over the network.
10
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 27
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2025 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





