LAN Infrastructure: Design, Implementation, and Performance Report
VerifiedAdded on 2024/05/27
|31
|5787
|289
Report
AI Summary
This report provides a detailed analysis of Local Area Network (LAN) technologies and their implementation within an organizational context, specifically focusing on Footfall Field Marketing Ltd. It evaluates various LAN technologies such as IEEE 802 standards, VTP, DHCP, FDDI, and Token Ring, examining their suitability for modern network infrastructures. The report also critically analyzes traffic-intensive services like DSCP, QOS, and IP precedence, discussing their impact on network performance. Furthermore, it addresses LAN concerns related to network security, performance, and reliability, offering recommendations for sustainable improvements. The design and configuration of a LAN infrastructure to meet specific organizational requirements, including the selection and suitability of LAN components such as routers, switches, and firewalls, are thoroughly covered. The practical aspects of building and configuring a LAN, implementing security measures, and evaluating network performance through testing are also discussed, along with strategies for monitoring the LAN and resolving issues to enhance security, reliability, and overall performance. This document is available on Desklib, a platform offering a wide array of study tools and resources for students.

LOCAL AREA NETWORK
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
1.1 Critically evaluate different LAN technologies.....................................................................2
1.2 Critically analysis traffic intensive services and their performance......................................5
1.3 Discuss LAN concerns and make recommendations to sustain network security,
performance and reliability..........................................................................................................6
Task 2...............................................................................................................................................7
2.1 Design a LAN infrastructure to meet the organization requirements....................................7
2.2 Suitability of LAN components.............................................................................................9
Task 3.............................................................................................................................................13
3.1 build and configure a LAN..................................................................................................13
3.2 security implementation.......................................................................................................15
3.3 Evaluation and testing of network.......................................................................................17
Task 4.............................................................................................................................................20
4.1 Monitoring of LAN..............................................................................................................20
4.2 Resolve LAN issues to improve security, reliability and performance...............................22
4.3 Performance of a LAN.........................................................................................................23
Conclusion.....................................................................................................................................24
References......................................................................................................................................25
Introduction......................................................................................................................................1
Task 1...............................................................................................................................................2
1.1 Critically evaluate different LAN technologies.....................................................................2
1.2 Critically analysis traffic intensive services and their performance......................................5
1.3 Discuss LAN concerns and make recommendations to sustain network security,
performance and reliability..........................................................................................................6
Task 2...............................................................................................................................................7
2.1 Design a LAN infrastructure to meet the organization requirements....................................7
2.2 Suitability of LAN components.............................................................................................9
Task 3.............................................................................................................................................13
3.1 build and configure a LAN..................................................................................................13
3.2 security implementation.......................................................................................................15
3.3 Evaluation and testing of network.......................................................................................17
Task 4.............................................................................................................................................20
4.1 Monitoring of LAN..............................................................................................................20
4.2 Resolve LAN issues to improve security, reliability and performance...............................22
4.3 Performance of a LAN.........................................................................................................23
Conclusion.....................................................................................................................................24
References......................................................................................................................................25

LIST OF TABLES
Table 1: Devices in the networking system.....................................................................................7
Table 1: Devices in the networking system.....................................................................................7
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

LIST OF FIGURES
Figure 1: VTP..................................................................................................................................2
Figure 2: DHCP...............................................................................................................................3
Figure 3: FDDI................................................................................................................................4
Figure 4: Token ring........................................................................................................................4
Figure 5: Network design................................................................................................................8
Figure 6: Switch configuration........................................................................................................9
Figure 7: Router configuration......................................................................................................10
Figure 8: Firewall configuration....................................................................................................11
Figure 9: DHCP configuration.......................................................................................................12
Figure 10: Design of the LAN for the organization......................................................................14
Figure 11: Working of the Firewall in the network.......................................................................14
Figure 1: VTP..................................................................................................................................2
Figure 2: DHCP...............................................................................................................................3
Figure 3: FDDI................................................................................................................................4
Figure 4: Token ring........................................................................................................................4
Figure 5: Network design................................................................................................................8
Figure 6: Switch configuration........................................................................................................9
Figure 7: Router configuration......................................................................................................10
Figure 8: Firewall configuration....................................................................................................11
Figure 9: DHCP configuration.......................................................................................................12
Figure 10: Design of the LAN for the organization......................................................................14
Figure 11: Working of the Firewall in the network.......................................................................14
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The local area network (LAN) can be used in the business for connecting the different
departments and floors of the organization as this will cover the small geographical area of the
organization. This report will cover the scenario of Footfall Field Marketing Ltd organization as
they want to connect their three separate floors in one building. This report will include the
discussion about the local area network in which LAN technologies will also be included. This
report will design the local area network for the organization along with the configuration of the
network devices. The report will also cover the testing of the designed network and after that its
maintenance will also be covered in this report. The report will also focus on the performance
and effectiveness of the network in the organization for their users.
1
The local area network (LAN) can be used in the business for connecting the different
departments and floors of the organization as this will cover the small geographical area of the
organization. This report will cover the scenario of Footfall Field Marketing Ltd organization as
they want to connect their three separate floors in one building. This report will include the
discussion about the local area network in which LAN technologies will also be included. This
report will design the local area network for the organization along with the configuration of the
network devices. The report will also cover the testing of the designed network and after that its
maintenance will also be covered in this report. The report will also focus on the performance
and effectiveness of the network in the organization for their users.
1
Task 1
1.1 Critically evaluate different LAN technologies
LAN (Local area network) is mainly used for connecting the small geographical area which is
related to the organization with the help of cable connection. This LAN connection can be done
by implementing wireless connection by using the server link as this will make the data sharing
easy for the organization. There are various types of LAN technologies that are used by
organization while connecting their network. Following are the various types of LAN
technologies:
IEEE 802 standard: This LAN technology mainly deals in the MAN network metropolitan area
network and LAN (Local area network). This technology is effective for the organization as it
provides access method, high speed, media and topologies. Variable size packets in the network
have some sort of restrictions (Gong et al, 2015).
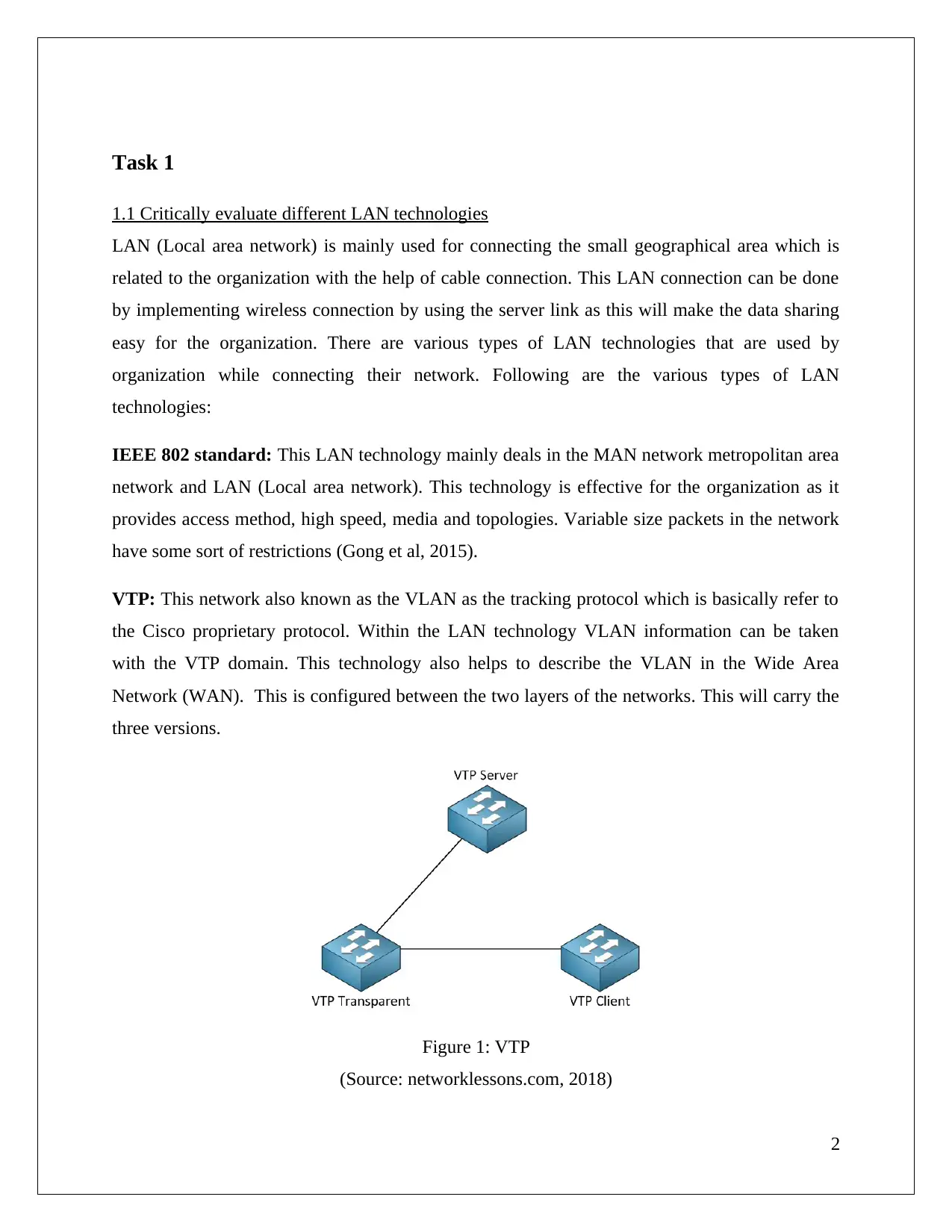
VTP: This network also known as the VLAN as the tracking protocol which is basically refer to
the Cisco proprietary protocol. Within the LAN technology VLAN information can be taken
with the VTP domain. This technology also helps to describe the VLAN in the Wide Area
Network (WAN). This is configured between the two layers of the networks. This will carry the
three versions.
Figure 1: VTP
(Source: networklessons.com, 2018)
2
1.1 Critically evaluate different LAN technologies
LAN (Local area network) is mainly used for connecting the small geographical area which is
related to the organization with the help of cable connection. This LAN connection can be done
by implementing wireless connection by using the server link as this will make the data sharing
easy for the organization. There are various types of LAN technologies that are used by
organization while connecting their network. Following are the various types of LAN
technologies:
IEEE 802 standard: This LAN technology mainly deals in the MAN network metropolitan area
network and LAN (Local area network). This technology is effective for the organization as it
provides access method, high speed, media and topologies. Variable size packets in the network
have some sort of restrictions (Gong et al, 2015).
VTP: This network also known as the VLAN as the tracking protocol which is basically refer to
the Cisco proprietary protocol. Within the LAN technology VLAN information can be taken
with the VTP domain. This technology also helps to describe the VLAN in the Wide Area
Network (WAN). This is configured between the two layers of the networks. This will carry the
three versions.
Figure 1: VTP
(Source: networklessons.com, 2018)
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
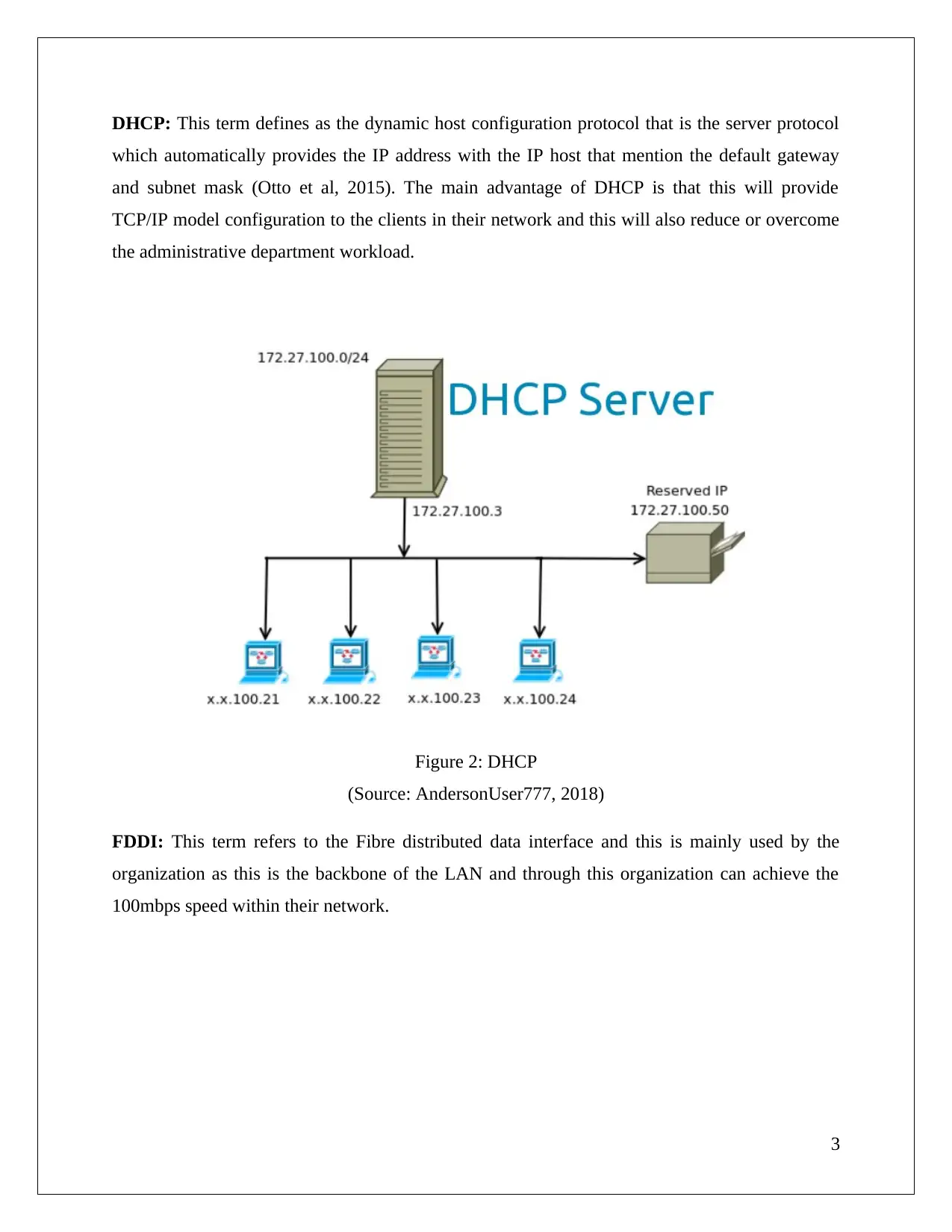
DHCP: This term defines as the dynamic host configuration protocol that is the server protocol
which automatically provides the IP address with the IP host that mention the default gateway
and subnet mask (Otto et al, 2015). The main advantage of DHCP is that this will provide
TCP/IP model configuration to the clients in their network and this will also reduce or overcome
the administrative department workload.
Figure 2: DHCP
(Source: AndersonUser777, 2018)
FDDI: This term refers to the Fibre distributed data interface and this is mainly used by the
organization as this is the backbone of the LAN and through this organization can achieve the
100mbps speed within their network.
3
which automatically provides the IP address with the IP host that mention the default gateway
and subnet mask (Otto et al, 2015). The main advantage of DHCP is that this will provide
TCP/IP model configuration to the clients in their network and this will also reduce or overcome
the administrative department workload.
Figure 2: DHCP
(Source: AndersonUser777, 2018)
FDDI: This term refers to the Fibre distributed data interface and this is mainly used by the
organization as this is the backbone of the LAN and through this organization can achieve the
100mbps speed within their network.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
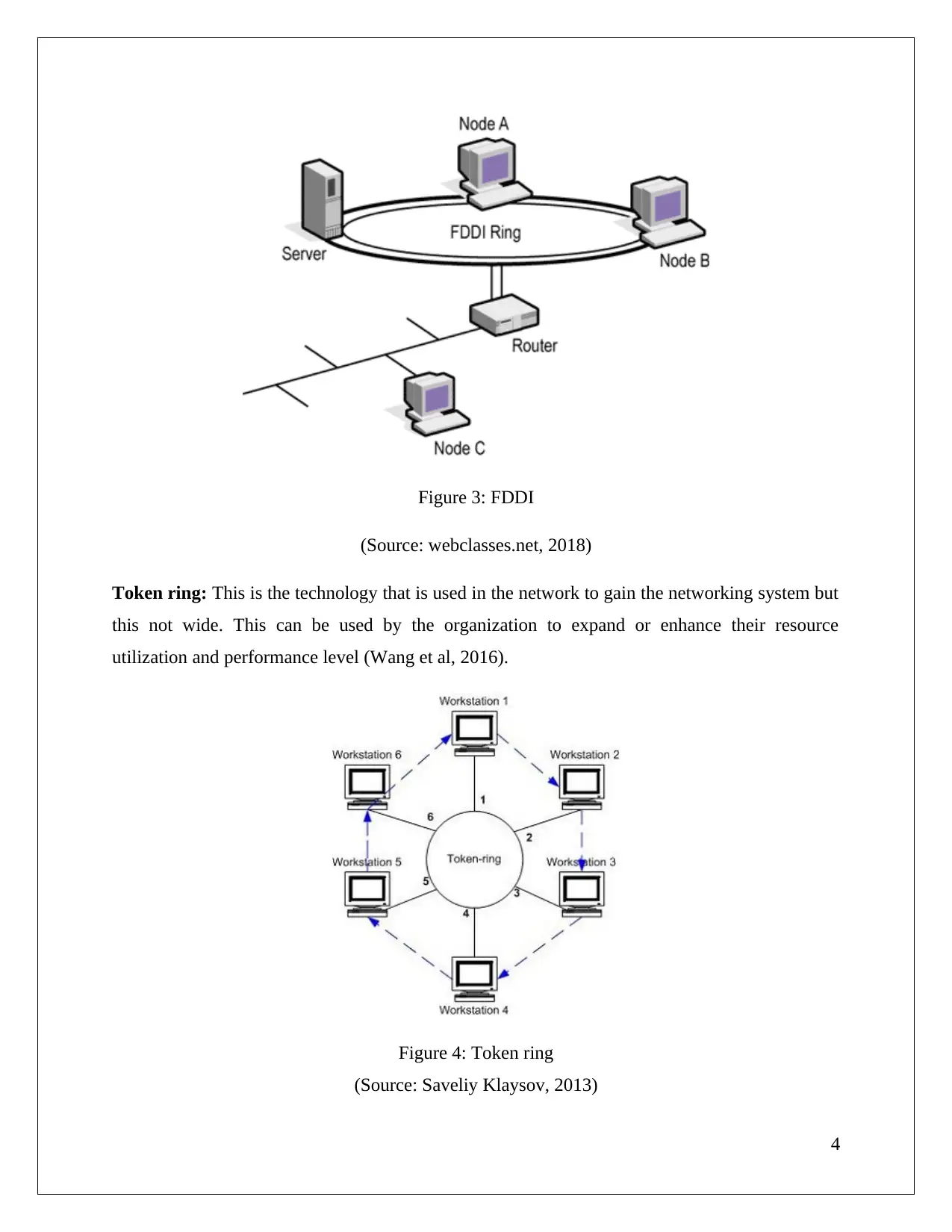
Figure 3: FDDI
(Source: webclasses.net, 2018)
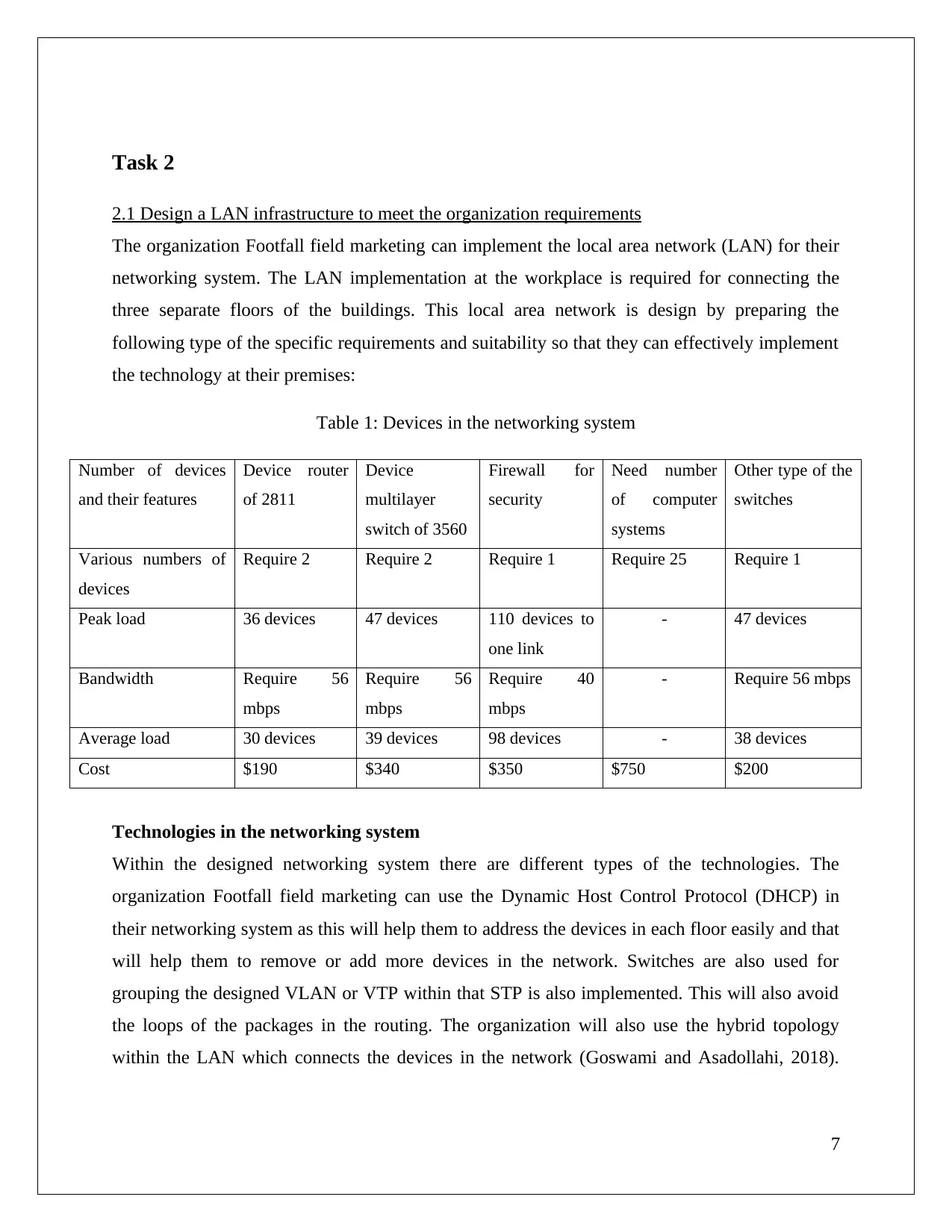
Token ring: This is the technology that is used in the network to gain the networking system but
this not wide. This can be used by the organization to expand or enhance their resource
utilization and performance level (Wang et al, 2016).
Figure 4: Token ring
(Source: Saveliy Klaysov, 2013)
4
(Source: webclasses.net, 2018)
Token ring: This is the technology that is used in the network to gain the networking system but
this not wide. This can be used by the organization to expand or enhance their resource
utilization and performance level (Wang et al, 2016).
Figure 4: Token ring
(Source: Saveliy Klaysov, 2013)
4

1.2 Critically analysis traffic intensive services and their performance
Within the intensive service, there are mainly two types of things that include the bandwidth and
internet. These types of services will help organization for reducing their problems within the
network. There are some of the traffic intensive services and their performance which are
discussed as below:
DSCP: DSCP refers to the differentiated service code point that is basically a type of the internet
work protocol. This will mainly provide the type of service layer that helps various devices for
getting the connection in the network. This service used by the organization for defining the IP
header field. There are mainly 8 type of the field within with upper 6 bit which contain the value
and that is known as the DSCP.
QOS (Quality of services): Quality of services is mainly used for measuring the performance of
the telephone signals and internet signals (Gupta et al, 2015). Users in the network use these
qualities of services for evaluating the performance in the network for buying some of the
specific purpose. In the network when user check the QOS (Quality of services) then there are
some of the factors which consider the some errors, transmission delay, network availability and
jitters. Within these services the video streaming services that are demanded with some of the
online services which important for the good quality of the services. On the other side, audio
streaming services are also used for listen the information.
IP precedence: This service is available in the IP header that is mainly defines the RFC 791.
This type of services performed by the network services control and shows that if the precedence
values are high then IP packets have the high priority (Belhaouane et al, 2015).
With the help of the above discussion it will become clear that the organization will use these
types of services for achieving traffic intensive services with the resources proper use, quality of
bandwidth and the proper management of the services. These traffic intensive services are also
required in the network for achieving the communication flexibility.
5
Within the intensive service, there are mainly two types of things that include the bandwidth and
internet. These types of services will help organization for reducing their problems within the
network. There are some of the traffic intensive services and their performance which are
discussed as below:
DSCP: DSCP refers to the differentiated service code point that is basically a type of the internet
work protocol. This will mainly provide the type of service layer that helps various devices for
getting the connection in the network. This service used by the organization for defining the IP
header field. There are mainly 8 type of the field within with upper 6 bit which contain the value
and that is known as the DSCP.
QOS (Quality of services): Quality of services is mainly used for measuring the performance of
the telephone signals and internet signals (Gupta et al, 2015). Users in the network use these
qualities of services for evaluating the performance in the network for buying some of the
specific purpose. In the network when user check the QOS (Quality of services) then there are
some of the factors which consider the some errors, transmission delay, network availability and
jitters. Within these services the video streaming services that are demanded with some of the
online services which important for the good quality of the services. On the other side, audio
streaming services are also used for listen the information.
IP precedence: This service is available in the IP header that is mainly defines the RFC 791.
This type of services performed by the network services control and shows that if the precedence
values are high then IP packets have the high priority (Belhaouane et al, 2015).
With the help of the above discussion it will become clear that the organization will use these
types of services for achieving traffic intensive services with the resources proper use, quality of
bandwidth and the proper management of the services. These traffic intensive services are also
required in the network for achieving the communication flexibility.
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.3 Discuss LAN concerns and make recommendations to sustain network security, performance
and reliability
The LAN (Local area network) is mainly used by the organization like Footfall Field Marketing
Ltd for connecting their main servers with the same segments for effective communication but
this will despite to the access control on firewall. On the other side, firewall is mainly used for
connecting the number of devices on the DMZ because through this they can get the security
within the network will be achieved. Data is also protected with the help of the firewall in the
network. There are some of the securities in the local area network that are required by the
organization to protect the network:
ACL (Access control list): This is the security system that will be used in the organization to
access the control over the entries of the accessibility within the network because through this
network can be secured and protected. Within this type of security system the users will be
restricted to access the information without having permission of the authorized user. This will
protect the network and its information from the unauthorized users. SACL and DACL are the
two types of access control lists (Sama et al, 2015).
Security issues: Security issues are required by the organization for protecting the switches and
routers local configuration from the mainly unwanted access and manipulations. On the other
side, all the network devices within the network need equal type of the security for accessing the
data prevention from the loss and theft. For providing the network security it is suggested to
configure defaults and security in the network. For the organization it is also recommended that
for managing the data they need to use centralized devices as this will improve the security of the
data in the organization.
Switch port control: This security system is important for the organization as this will protect
and secure the local area network because this can be used for controlling and also to limit the
addresses to find (Porras et al, 2015). This will be allowed for sending the traffic in switches
ports in the network. The organization Footfall Field marketing if use this security system then it
is essential for them to provide the configuration of the switches for the security purpose.
6
and reliability
The LAN (Local area network) is mainly used by the organization like Footfall Field Marketing
Ltd for connecting their main servers with the same segments for effective communication but
this will despite to the access control on firewall. On the other side, firewall is mainly used for
connecting the number of devices on the DMZ because through this they can get the security
within the network will be achieved. Data is also protected with the help of the firewall in the
network. There are some of the securities in the local area network that are required by the
organization to protect the network:
ACL (Access control list): This is the security system that will be used in the organization to
access the control over the entries of the accessibility within the network because through this
network can be secured and protected. Within this type of security system the users will be
restricted to access the information without having permission of the authorized user. This will
protect the network and its information from the unauthorized users. SACL and DACL are the
two types of access control lists (Sama et al, 2015).
Security issues: Security issues are required by the organization for protecting the switches and
routers local configuration from the mainly unwanted access and manipulations. On the other
side, all the network devices within the network need equal type of the security for accessing the
data prevention from the loss and theft. For providing the network security it is suggested to
configure defaults and security in the network. For the organization it is also recommended that
for managing the data they need to use centralized devices as this will improve the security of the
data in the organization.
Switch port control: This security system is important for the organization as this will protect
and secure the local area network because this can be used for controlling and also to limit the
addresses to find (Porras et al, 2015). This will be allowed for sending the traffic in switches
ports in the network. The organization Footfall Field marketing if use this security system then it
is essential for them to provide the configuration of the switches for the security purpose.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Task 2
2.1 Design a LAN infrastructure to meet the organization requirements
The organization Footfall field marketing can implement the local area network (LAN) for their
networking system. The LAN implementation at the workplace is required for connecting the
three separate floors of the buildings. This local area network is design by preparing the
following type of the specific requirements and suitability so that they can effectively implement
the technology at their premises:
Table 1: Devices in the networking system
Number of devices
and their features
Device router
of 2811
Device
multilayer
switch of 3560
Firewall for
security
Need number
of computer
systems
Other type of the
switches
Various numbers of
devices
Require 2 Require 2 Require 1 Require 25 Require 1
Peak load 36 devices 47 devices 110 devices to
one link
- 47 devices
Bandwidth Require 56
mbps
Require 56
mbps
Require 40
mbps
- Require 56 mbps
Average load 30 devices 39 devices 98 devices - 38 devices
Cost $190 $340 $350 $750 $200
Technologies in the networking system
Within the designed networking system there are different types of the technologies. The
organization Footfall field marketing can use the Dynamic Host Control Protocol (DHCP) in
their networking system as this will help them to address the devices in each floor easily and that
will help them to remove or add more devices in the network. Switches are also used for
grouping the designed VLAN or VTP within that STP is also implemented. This will also avoid
the loops of the packages in the routing. The organization will also use the hybrid topology
within the LAN which connects the devices in the network (Goswami and Asadollahi, 2018).
7
2.1 Design a LAN infrastructure to meet the organization requirements
The organization Footfall field marketing can implement the local area network (LAN) for their
networking system. The LAN implementation at the workplace is required for connecting the
three separate floors of the buildings. This local area network is design by preparing the
following type of the specific requirements and suitability so that they can effectively implement
the technology at their premises:
Table 1: Devices in the networking system
Number of devices
and their features
Device router
of 2811
Device
multilayer
switch of 3560
Firewall for
security
Need number
of computer
systems
Other type of the
switches
Various numbers of
devices
Require 2 Require 2 Require 1 Require 25 Require 1
Peak load 36 devices 47 devices 110 devices to
one link
- 47 devices
Bandwidth Require 56
mbps
Require 56
mbps
Require 40
mbps
- Require 56 mbps
Average load 30 devices 39 devices 98 devices - 38 devices
Cost $190 $340 $350 $750 $200
Technologies in the networking system
Within the designed networking system there are different types of the technologies. The
organization Footfall field marketing can use the Dynamic Host Control Protocol (DHCP) in
their networking system as this will help them to address the devices in each floor easily and that
will help them to remove or add more devices in the network. Switches are also used for
grouping the designed VLAN or VTP within that STP is also implemented. This will also avoid
the loops of the packages in the routing. The organization will also use the hybrid topology
within the LAN which connects the devices in the network (Goswami and Asadollahi, 2018).
7
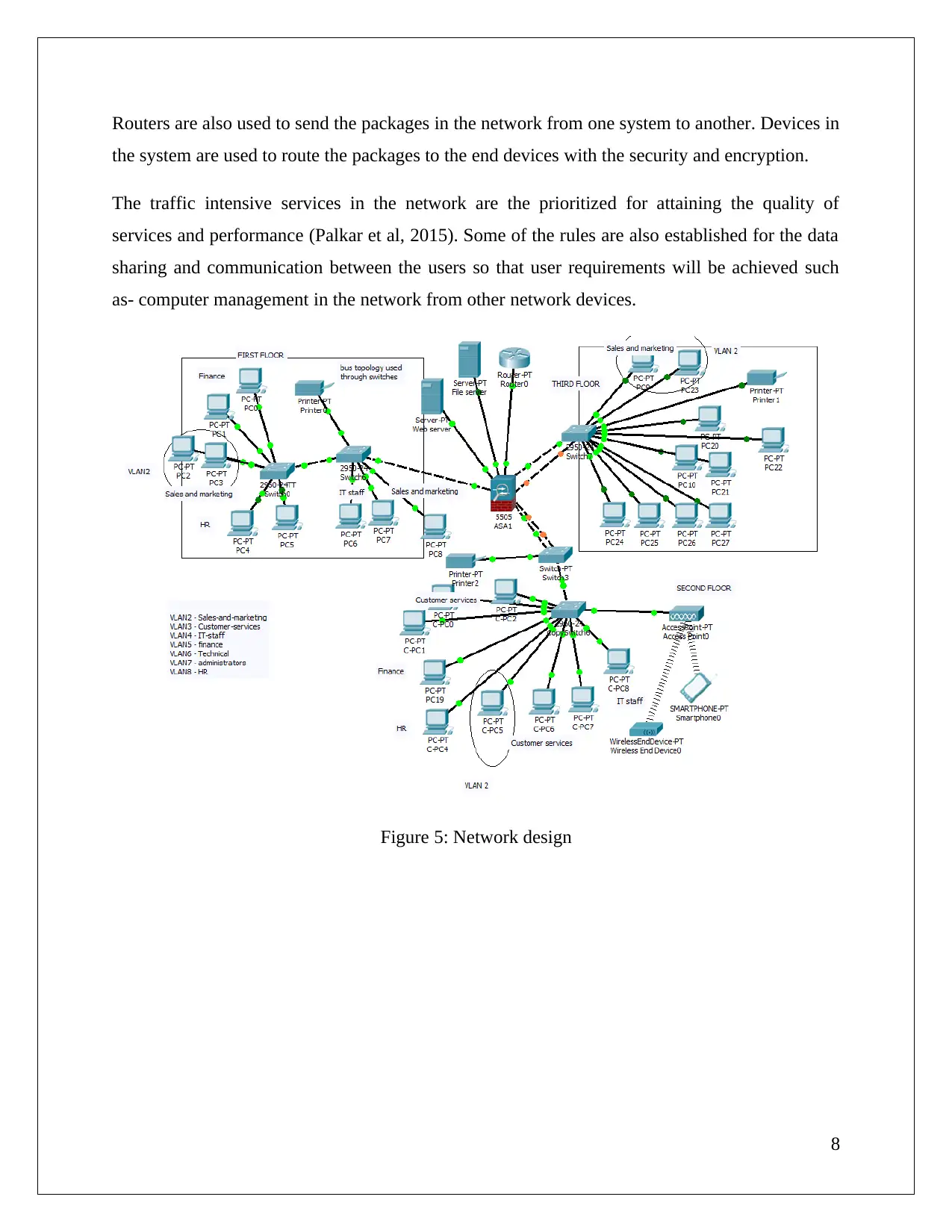
Routers are also used to send the packages in the network from one system to another. Devices in
the system are used to route the packages to the end devices with the security and encryption.
The traffic intensive services in the network are the prioritized for attaining the quality of
services and performance (Palkar et al, 2015). Some of the rules are also established for the data
sharing and communication between the users so that user requirements will be achieved such
as- computer management in the network from other network devices.
Figure 5: Network design
8
the system are used to route the packages to the end devices with the security and encryption.
The traffic intensive services in the network are the prioritized for attaining the quality of
services and performance (Palkar et al, 2015). Some of the rules are also established for the data
sharing and communication between the users so that user requirements will be achieved such
as- computer management in the network from other network devices.
Figure 5: Network design
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




