FootFall Ltd: LAN Technologies, Performance, and Security Analysis
VerifiedAdded on 2020/10/22
|22
|5996
|215
Report
AI Summary
This report provides a comprehensive analysis of Local Area Network (LAN) technologies, evaluating various options such as Wireless LAN, Ethernet, and VLANs, along with their suitability for FootFall Ltd. It explores the performance of traffic-intensive services, emphasizing Quality of Service (QoS) measures and factors like bandwidth, data packet loss, and delays. The report also addresses critical aspects of network security and reliability, recommending measures like updated antivirus databases, passive monitoring for wireless LANs, and the use of Media Access Control (MAC) methods. Furthermore, it examines the implementation of access control lists (ACLs) and strategies to mitigate risks associated with rogue access points and DHCP configurations. The report concludes with recommendations for sustaining optimal LAN performance, security, and reliability, making it a valuable resource for understanding and implementing effective LAN solutions.

Local Area Networking Technologies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TABLE OF CONTENTS
INTRODUCTION...........................................................................................................................2
TASK 1............................................................................................................................................2
A.C 1.1 LAN Technologies....................................................................................................2
A.C 1.2 Performance evaluation of traffic intensive services................................................4
A.C 1.3 Recommendations for sustaining the performance, security and reliability of LAN5
TASK 2............................................................................................................................................7
A.C 2.1 LAN infrastructure for FootFall Ltd.........................................................................7
2.2 Suitability of LAN components........................................................................................9
TASK 3............................................................................................................................................9
A.C 3.1 build and configure a LAN to meet a given requirement.........................................9
A.C 3.2 implement network security on a LAN...................................................................11
A.C 3.3 Test LAN using tools and platforms.......................................................................12
TASK 4..........................................................................................................................................14
A.C 4.1 critically describe how LAN infrastructure will be monitored and managed.........14
A.C 4.2 Solve LAN issues to improve reliability and security, performance,.....................15
A.C 4.3 Evaluate the performance of a LAN.......................................................................16
CONCLUSION..............................................................................................................................18
REFERENCES..............................................................................................................................19
1
INTRODUCTION...........................................................................................................................2
TASK 1............................................................................................................................................2
A.C 1.1 LAN Technologies....................................................................................................2
A.C 1.2 Performance evaluation of traffic intensive services................................................4
A.C 1.3 Recommendations for sustaining the performance, security and reliability of LAN5
TASK 2............................................................................................................................................7
A.C 2.1 LAN infrastructure for FootFall Ltd.........................................................................7
2.2 Suitability of LAN components........................................................................................9
TASK 3............................................................................................................................................9
A.C 3.1 build and configure a LAN to meet a given requirement.........................................9
A.C 3.2 implement network security on a LAN...................................................................11
A.C 3.3 Test LAN using tools and platforms.......................................................................12
TASK 4..........................................................................................................................................14
A.C 4.1 critically describe how LAN infrastructure will be monitored and managed.........14
A.C 4.2 Solve LAN issues to improve reliability and security, performance,.....................15
A.C 4.3 Evaluate the performance of a LAN.......................................................................16
CONCLUSION..............................................................................................................................18
REFERENCES..............................................................................................................................19
1

INTRODUCTION
Local area network (LAN) technology is defined as networking approach which
interconnect computers and related devices to each other within a local or limited area. The LAN
techniques allow each of the participating device to share and exchange data (Bello and
Zeadally, 2016). The report will evaluate the various LAN technologies and the performance of
traffic intensive services in relation to FootFall Field Marketing Ltd. This organisation requires
expanding its network by implementing the LAN.
The report will also analyse the security and reliability concerns associated with LAN
implementation. It will evaluate the LAN infrastructure and suitability of its various components
in relation with business operations of FootFall Ltd. The report will explain the monitoring and
security concern which arise with implementation of LAN network. Moreover, it will describe
the troubleshooting issues and will provide solutions to improve the LAN performance and
reliability.
TASK 1
A.C 1.1 LAN Technologies
FootFall Ltd can use various LAN technologies for meeting the requirements of their
expanding business functions.
Wireless LAN technology:
The key principle in this technology is the wireless communication. This can be one of
the most efficient LAN technique. It follows the IEEE 802.11 standards and provides facility to
remain connected even by even when the user is out of range. The IEEE 802.11 standard has its
major emphasis on bottom layers of ISO which are physical layer. Wireless LAN eliminates the
complex cluster of wires and cables and ensure free movement of users without restricting them.
However, wireless LAN is considered as less secure and have slower speed. So organization
cannot use this technology to transmit sensitive information's. For example: Ethernet is the most
used LAN technology under IEEE 802.11 standard. It is easy to understand, implement and
maintain with very low cost. Ethernet operates in two layers of OSI model which physical and
data link layer. Other examples are Token Ring, FDDI and ARCNET.
Virtual LAN:
It is defined as the logical sub network which has ability to group various devices from
number of physical local area networks. If FootFall Ltd uses this technology then it will become
2
Local area network (LAN) technology is defined as networking approach which
interconnect computers and related devices to each other within a local or limited area. The LAN
techniques allow each of the participating device to share and exchange data (Bello and
Zeadally, 2016). The report will evaluate the various LAN technologies and the performance of
traffic intensive services in relation to FootFall Field Marketing Ltd. This organisation requires
expanding its network by implementing the LAN.
The report will also analyse the security and reliability concerns associated with LAN
implementation. It will evaluate the LAN infrastructure and suitability of its various components
in relation with business operations of FootFall Ltd. The report will explain the monitoring and
security concern which arise with implementation of LAN network. Moreover, it will describe
the troubleshooting issues and will provide solutions to improve the LAN performance and
reliability.
TASK 1
A.C 1.1 LAN Technologies
FootFall Ltd can use various LAN technologies for meeting the requirements of their
expanding business functions.
Wireless LAN technology:
The key principle in this technology is the wireless communication. This can be one of
the most efficient LAN technique. It follows the IEEE 802.11 standards and provides facility to
remain connected even by even when the user is out of range. The IEEE 802.11 standard has its
major emphasis on bottom layers of ISO which are physical layer. Wireless LAN eliminates the
complex cluster of wires and cables and ensure free movement of users without restricting them.
However, wireless LAN is considered as less secure and have slower speed. So organization
cannot use this technology to transmit sensitive information's. For example: Ethernet is the most
used LAN technology under IEEE 802.11 standard. It is easy to understand, implement and
maintain with very low cost. Ethernet operates in two layers of OSI model which physical and
data link layer. Other examples are Token Ring, FDDI and ARCNET.
Virtual LAN:
It is defined as the logical sub network which has ability to group various devices from
number of physical local area networks. If FootFall Ltd uses this technology then it will become
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

very convenient for the organization to share sensitive information with high level of security but
it is very complex and difficult to maintain the effectiveness of Virtual LAN (Gupta and Jha,
2015). It reduces broadcast traffic and has strong policies for ensuring the data security. VLAN
technology also eliminates the physical boundaries and has high performance characteristics in
terms of resource and data sharing as well as in lowering latency. However, it does not allow
communication with other VLANs without routers. Another important advantage of VLAN
implementation is that it minimizes the router requirement by flooding data packets to limited
switch ports only. In order to ensure only authorized access to information it confines the
broadcasting domain. For example: A company has three department offices i.e. development,
production and administration. Every department has 3 computers. For some default
configuration all system has same broadcast domain to access the resources of other department.
For this VLAN create a logical boundary over physcial network. VLAN router is used to
connected network.
LAN using switching:
In this LAN technology switching methods are used for networking. FootFall Ltd can
use layer 2 switch which uses MAC address and networking interface cards for ensuring low
latency. It is highly efficient as data encapsulation does not allow changes to data and is effective
for group connectivity. Layer 3 and 4 switches will be expensive as organization has smaller
network. Layer 2 switch based LAN has low cost and latency and does not require routing gears
but is suffers from certain disadvantages. The major one is that data transmitted from one device
is received by all other available devices which in turn reduces network efficiency. For example-
LAN switching is a modern technology and Football organization uses this technique to enables
for controlling the switch port and every switch port associates with the fast Ethernet. It helps for
manage the display speed and duplex.
Ethernet:
This technology is very effective in terms of cost and flexibility in topologies. It uses
CSMA/CD mechanism for controlling access. It executes in TCP/IP architecture of link layer
and provides connectionless communication. This technology has low cost and higher immunity
to noise but it does not support traffic intensive applications and acknowledgement facility
(Liang and Yu, 2015). It provides easy troubleshooting methods and transfer speed can be
increased up to Gbps as well. However, it does not support video and voice traffic. This
3
it is very complex and difficult to maintain the effectiveness of Virtual LAN (Gupta and Jha,
2015). It reduces broadcast traffic and has strong policies for ensuring the data security. VLAN
technology also eliminates the physical boundaries and has high performance characteristics in
terms of resource and data sharing as well as in lowering latency. However, it does not allow
communication with other VLANs without routers. Another important advantage of VLAN
implementation is that it minimizes the router requirement by flooding data packets to limited
switch ports only. In order to ensure only authorized access to information it confines the
broadcasting domain. For example: A company has three department offices i.e. development,
production and administration. Every department has 3 computers. For some default
configuration all system has same broadcast domain to access the resources of other department.
For this VLAN create a logical boundary over physcial network. VLAN router is used to
connected network.
LAN using switching:
In this LAN technology switching methods are used for networking. FootFall Ltd can
use layer 2 switch which uses MAC address and networking interface cards for ensuring low
latency. It is highly efficient as data encapsulation does not allow changes to data and is effective
for group connectivity. Layer 3 and 4 switches will be expensive as organization has smaller
network. Layer 2 switch based LAN has low cost and latency and does not require routing gears
but is suffers from certain disadvantages. The major one is that data transmitted from one device
is received by all other available devices which in turn reduces network efficiency. For example-
LAN switching is a modern technology and Football organization uses this technique to enables
for controlling the switch port and every switch port associates with the fast Ethernet. It helps for
manage the display speed and duplex.
Ethernet:
This technology is very effective in terms of cost and flexibility in topologies. It uses
CSMA/CD mechanism for controlling access. It executes in TCP/IP architecture of link layer
and provides connectionless communication. This technology has low cost and higher immunity
to noise but it does not support traffic intensive applications and acknowledgement facility
(Liang and Yu, 2015). It provides easy troubleshooting methods and transfer speed can be
increased up to Gbps as well. However, it does not support video and voice traffic. This
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

technology will be the best option for FootFall Ltd in terms of speed and security measures. For
Example: If connect computer with 10 BASE-T NIC to a 100 BASE-T network, the computer
will only be able to send and receive data at 10 Mbps. But if Gigabit Ethernet router connect
devices it using 100BASE-T cables with maximum data transfer rate will be 100 Mbps.
Voice over protocol:
This technology integrates the local area network with phone calls. Thus, users can make
calls over LAN. It converts voice signal (analog) into digital signals. As compare to traditional
methods of calling system VoIP is less costly and its quality is not affected by the distance
between sender and receiver. However, for high quality it requires private box exchange with
high speed internet connection. It suffers from major disadvantage, that it requires power supply
and internet connection. In the absence of these factors the organization will not be able to make
calls. The bandwidth requirement of voice over protocol are higher and due to this data packets
are delayed during transmission. It can also be a challenging and difficult task to trace the
address of the sender. Thus, from security concerns it may not be considered suitable for the
organization. The speed of processor is variable with multitasking approaches. The quality of
calls made by voice over protocol LAN technology can degrade if speed of the processor is
reduced. For examples of applications that use VOIP technology are whats app, google phone,
Facebook video, voice chat and Skype.
A.C 1.2 Performance evaluation of traffic intensive services
Certain activities which are in high demand and keeps the traffic engaged at greater
extent are known as traffic intensive activities. For instance, downloading, video and audio
streaming are highly intensive towards traffic whereas activities like chatting, browsing does not
contribute to network traffic. For ensuring the effectiveness of the LAN system, it is essential for
Footfall Ltd to analyse performance of these traffic intensive services. The organisation must
consider the performance of traffic intensive services in order to achieve its objectives of LAN
Implementation.
Quality of service (QoS) measures the overall effectiveness of LAN network by giving
priority to various applications and ensuring desired standards in performance. These services
aim at minimizing the network traffic by monitoring the extent of traffic and delay in data
transmission. Their performance can be measured by factors like bandwidth, loss of data packets
and delays. For instance, for Footfall Ltd voice over IP can be the first priority and video
4
Example: If connect computer with 10 BASE-T NIC to a 100 BASE-T network, the computer
will only be able to send and receive data at 10 Mbps. But if Gigabit Ethernet router connect
devices it using 100BASE-T cables with maximum data transfer rate will be 100 Mbps.
Voice over protocol:
This technology integrates the local area network with phone calls. Thus, users can make
calls over LAN. It converts voice signal (analog) into digital signals. As compare to traditional
methods of calling system VoIP is less costly and its quality is not affected by the distance
between sender and receiver. However, for high quality it requires private box exchange with
high speed internet connection. It suffers from major disadvantage, that it requires power supply
and internet connection. In the absence of these factors the organization will not be able to make
calls. The bandwidth requirement of voice over protocol are higher and due to this data packets
are delayed during transmission. It can also be a challenging and difficult task to trace the
address of the sender. Thus, from security concerns it may not be considered suitable for the
organization. The speed of processor is variable with multitasking approaches. The quality of
calls made by voice over protocol LAN technology can degrade if speed of the processor is
reduced. For examples of applications that use VOIP technology are whats app, google phone,
Facebook video, voice chat and Skype.
A.C 1.2 Performance evaluation of traffic intensive services
Certain activities which are in high demand and keeps the traffic engaged at greater
extent are known as traffic intensive activities. For instance, downloading, video and audio
streaming are highly intensive towards traffic whereas activities like chatting, browsing does not
contribute to network traffic. For ensuring the effectiveness of the LAN system, it is essential for
Footfall Ltd to analyse performance of these traffic intensive services. The organisation must
consider the performance of traffic intensive services in order to achieve its objectives of LAN
Implementation.
Quality of service (QoS) measures the overall effectiveness of LAN network by giving
priority to various applications and ensuring desired standards in performance. These services
aim at minimizing the network traffic by monitoring the extent of traffic and delay in data
transmission. Their performance can be measured by factors like bandwidth, loss of data packets
and delays. For instance, for Footfall Ltd voice over IP can be the first priority and video
4

streaming can be second priority so when both requests are appeared simultaneously then QoS
gives priority to VOIP and will hold secondary activities until network traffic is not cleared. This
approach not only improve effectiveness but also reduces operating costs. For giving priorities to
activities quality of service standards mark the data packets by means of either IP precedence or
IP DSCP (differentiated service code point).
For giving priority to data packets with IP precedence method the data packet which has
higher value of IP precedence field will be given first priority. IP precedence uses only first three
bits for allocating the priority while on the other hand DSCP uses the first 6 bits for prioritizing
the packets (Liang, Yu, and Zhang, 2015). The delay experienced by traffic intensive services
due to priority allocation by QoS also depends upon the position of the data or IP packets in the
queue. The traffic intensive activities can also use frame tagging methods.
These methods identify the data packets which passes through trunk lines. The
identification is accomplished by giving them specific tags before transmissions. The tagging of
packets ensure that data packets are not lost and network traffic is not disturbed by intervention
from these misplaced packets. Hence, it is essential for the organisation that these traffic
intensive services are monitored regularly. Their performance evaluation parameters such as
delay, traffic intensity, and effectiveness in giving priority to desired operations.
A.C 1.3 Recommendations for sustaining the performance, security and reliability of LAN
The major concerns in relation with the local area networking are security and control
related concerns. The desired LAN implementation of Footfall Ltd must ensure that traffic
intensive services are effectively used so that network traffic does not degrade the performance
of the network. The networking system must use appropriate security measurements to ensure
the data transmission via safe and secure networking path. The most basic approach which can
be used by the organisation to avoid security threat is to keep their antivirus database updated. It
will greatly reduce the risks of security threats (threats to wireless security, 2010).
If Footfall Ltd employs wireless LAN, then it becomes essential for the organisation to
include passive monitoring. There are possibilities that the data is unintentionally propagated
outside the wireless range of organisation and thus it can be easily vulnerable to unauthorised
accessing. During transmissions via LAN network it may happen that more than one system
transmits the signal or data at the same time. In such cases in order to avoid signal interference or
collision media access control methods (MAC) can be used. MAC methods are implemented at
5
gives priority to VOIP and will hold secondary activities until network traffic is not cleared. This
approach not only improve effectiveness but also reduces operating costs. For giving priorities to
activities quality of service standards mark the data packets by means of either IP precedence or
IP DSCP (differentiated service code point).
For giving priority to data packets with IP precedence method the data packet which has
higher value of IP precedence field will be given first priority. IP precedence uses only first three
bits for allocating the priority while on the other hand DSCP uses the first 6 bits for prioritizing
the packets (Liang, Yu, and Zhang, 2015). The delay experienced by traffic intensive services
due to priority allocation by QoS also depends upon the position of the data or IP packets in the
queue. The traffic intensive activities can also use frame tagging methods.
These methods identify the data packets which passes through trunk lines. The
identification is accomplished by giving them specific tags before transmissions. The tagging of
packets ensure that data packets are not lost and network traffic is not disturbed by intervention
from these misplaced packets. Hence, it is essential for the organisation that these traffic
intensive services are monitored regularly. Their performance evaluation parameters such as
delay, traffic intensity, and effectiveness in giving priority to desired operations.
A.C 1.3 Recommendations for sustaining the performance, security and reliability of LAN
The major concerns in relation with the local area networking are security and control
related concerns. The desired LAN implementation of Footfall Ltd must ensure that traffic
intensive services are effectively used so that network traffic does not degrade the performance
of the network. The networking system must use appropriate security measurements to ensure
the data transmission via safe and secure networking path. The most basic approach which can
be used by the organisation to avoid security threat is to keep their antivirus database updated. It
will greatly reduce the risks of security threats (threats to wireless security, 2010).
If Footfall Ltd employs wireless LAN, then it becomes essential for the organisation to
include passive monitoring. There are possibilities that the data is unintentionally propagated
outside the wireless range of organisation and thus it can be easily vulnerable to unauthorised
accessing. During transmissions via LAN network it may happen that more than one system
transmits the signal or data at the same time. In such cases in order to avoid signal interference or
collision media access control methods (MAC) can be used. MAC methods are implemented at
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the data link stage. For instance, in Ethernet CSMA/CD media access method is used. For
enhancing the security in wireless local area network organisation can use access control list in
networking. This list will allow only authorised access to the objects.
The systems which do not have permission are not allowed to modify or transmit the
data. Access control list also provide specification about which operations can be performed on
the objects as well as the scope of data objects. Access control list can serve as rule set to filter
the network traffic of Footfall Ltd. The extended version of access list allows as to evaluate the
complete details of IP address along with the Layer 3 type protocol whereas the standard access
list can evaluate only IP address (Securing Networks: Access Control List (ACL) concepts,
2012). Thus, for security perspective it will be more suitable for FootFall Ltd to implement
extended version. ACL can be implemented on firewall or routers but due to less complexity
mainly they are preferred over routers.
Virtual malicious traffic due to inefficient management of wireless network is also one of
the important consideration for the organisation. To mitigate these concerns IT department of
organisation must disable DHCP (Dynamic host configuration). Instead of it static IP address can
be used. Rogue access points can encourage the network traffic so in order to eliminate them
organisation must conduct site survey for determining all available access points. WEP
encryption method can give wireless security which is equivalently effective as wired local area
network. In order to manage the network traffic intensity and to monitor the traffic, LAN must
can include switch port analyser (SPAN). It is also known as the port mirroring. For analysing
the network packets port spanning is enabled so that switch can transmit copy of network packets
on selected port for analysing (The do’s and do not's of SPAN ports, 2013).
It is essential that during its setup source and destination must not be mixed otherwise it
will affect the quality of LAN networking. Thus SPAN ports are very useful and beneficial for
the LAN as they enhance the visibility of all activities executing on LAN and provide effective
quality data for troubleshooting and application decoding. However, SPAN ports may suffer
from certain limitations. They can add time delay to the data packets and some packets can be
dropped or missed due to over subscription or their poor quality. For deeply analysing the
packets traffic related to firewall must be SPAN.
6
enhancing the security in wireless local area network organisation can use access control list in
networking. This list will allow only authorised access to the objects.
The systems which do not have permission are not allowed to modify or transmit the
data. Access control list also provide specification about which operations can be performed on
the objects as well as the scope of data objects. Access control list can serve as rule set to filter
the network traffic of Footfall Ltd. The extended version of access list allows as to evaluate the
complete details of IP address along with the Layer 3 type protocol whereas the standard access
list can evaluate only IP address (Securing Networks: Access Control List (ACL) concepts,
2012). Thus, for security perspective it will be more suitable for FootFall Ltd to implement
extended version. ACL can be implemented on firewall or routers but due to less complexity
mainly they are preferred over routers.
Virtual malicious traffic due to inefficient management of wireless network is also one of
the important consideration for the organisation. To mitigate these concerns IT department of
organisation must disable DHCP (Dynamic host configuration). Instead of it static IP address can
be used. Rogue access points can encourage the network traffic so in order to eliminate them
organisation must conduct site survey for determining all available access points. WEP
encryption method can give wireless security which is equivalently effective as wired local area
network. In order to manage the network traffic intensity and to monitor the traffic, LAN must
can include switch port analyser (SPAN). It is also known as the port mirroring. For analysing
the network packets port spanning is enabled so that switch can transmit copy of network packets
on selected port for analysing (The do’s and do not's of SPAN ports, 2013).
It is essential that during its setup source and destination must not be mixed otherwise it
will affect the quality of LAN networking. Thus SPAN ports are very useful and beneficial for
the LAN as they enhance the visibility of all activities executing on LAN and provide effective
quality data for troubleshooting and application decoding. However, SPAN ports may suffer
from certain limitations. They can add time delay to the data packets and some packets can be
dropped or missed due to over subscription or their poor quality. For deeply analysing the
packets traffic related to firewall must be SPAN.
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

TASK 2
A.C 2.1 LAN infrastructure for FootFall Ltd
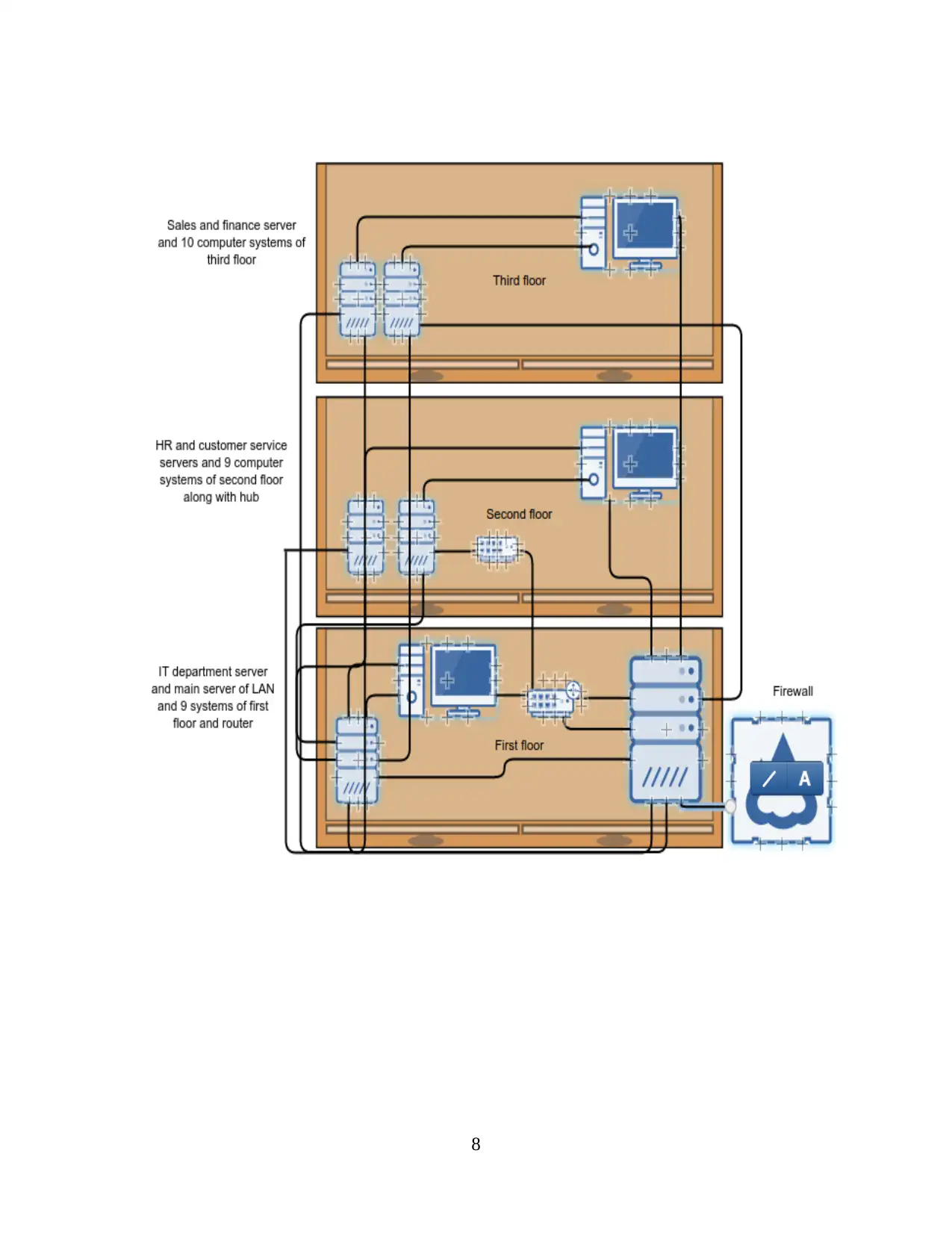
FootFall Ltd requires expanding their network in same building across 3 different floors.
IT department requires one system at each floor. At first floor each department requires 2
computers thus total 9 systems at first floor. Whereas at second and third floor organisation want
to implement 9 and 10 computers respectively. Since Footfall Ltd is small organisation, it will be
suitable to use class C IP address in which first byte contain range from 192-223. With class C IP
address there is less number of host IP address hence it becomes very easy to manage DHCP.
Users: Foot fall organization always provide the best quality of product and services to their
customer. Many users attract towards LAN technology because it is easier for people to
understand their process. In this way, user communicate with other people to share information
form one place to another.
Applications: LAN provide variety of applications to helps for user and customer. There are
some important common LAN useful such as:
Personal computer LAN- It is a common configuration of LAN which support the computers. In
this way, managers communicate with different departments of organization to share important
data and information.
Scalable- Local area network is scalable wireless network that is support the mobility in Internet
protocol and local area network.
Security: Local area network provide privacy for secure personal information and data of
organizations and customers. This network uses TCP protocol for transmission of signals form
one part to another.
Traffic intensive services: Local area network transmitted large amount of data form one place
to another. This data will encapsulate in the form of packets and also provide loads in network.
In this way, it can be measure the network traffic.
Technology: LAN is Modern technology and many biggest organization used for sharing
information from one place to another.
7
A.C 2.1 LAN infrastructure for FootFall Ltd
FootFall Ltd requires expanding their network in same building across 3 different floors.
IT department requires one system at each floor. At first floor each department requires 2
computers thus total 9 systems at first floor. Whereas at second and third floor organisation want
to implement 9 and 10 computers respectively. Since Footfall Ltd is small organisation, it will be
suitable to use class C IP address in which first byte contain range from 192-223. With class C IP
address there is less number of host IP address hence it becomes very easy to manage DHCP.
Users: Foot fall organization always provide the best quality of product and services to their
customer. Many users attract towards LAN technology because it is easier for people to
understand their process. In this way, user communicate with other people to share information
form one place to another.
Applications: LAN provide variety of applications to helps for user and customer. There are
some important common LAN useful such as:
Personal computer LAN- It is a common configuration of LAN which support the computers. In
this way, managers communicate with different departments of organization to share important
data and information.
Scalable- Local area network is scalable wireless network that is support the mobility in Internet
protocol and local area network.
Security: Local area network provide privacy for secure personal information and data of
organizations and customers. This network uses TCP protocol for transmission of signals form
one part to another.
Traffic intensive services: Local area network transmitted large amount of data form one place
to another. This data will encapsulate in the form of packets and also provide loads in network.
In this way, it can be measure the network traffic.
Technology: LAN is Modern technology and many biggest organization used for sharing
information from one place to another.
7
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

2.2 Suitability of LAN components
For achieving the benefits of networking it is necessary that suitable LAN components
are used in the infrastructure. Local area network has following components.
Hubs and switches: These are one of the basic components for networking. Hubs are also known
as routers and they connect multiple computer systems with each other. These are used in both
wireless and in wired LAN. They provide the routing path for effective information exchange.
Power supply: All LAN technologies essentially consist of power supply. The wired local area
network shares data with the use of cables. Thus, in wired LAN data is interpreted as electronic
pulse. On the other hand, in wireless network data is transmitted via radio waves. These waves
are produced by using current.
Network adapter and medium: To establish the connection network adapter is required. It first
converts data into suitable electronic signals and then if network traffic is not present then it
transmits the data to network. The element of network adapter which serves this purpose is called
media access control (MAC). The MAC address is defined as the serial number of network
adapter. In most of the computer systems it is integrated into motherboard of system.
The networking medium in wired local area networks is called as networking cables.
Organisation can use twisted pair cable or fibre optic cables (Ojha, Misra and Raghuwanshi,
2015). Unshielded twisted cable is also called Ethernet cable. To connect cables connectors are
used. The most commonly used connector is RJ45. Every computer system in the network has
RJ45 port for providing connections to twisted pair cables. For wireless local area networks
cables are not used as networking medium rather they use radio waves as transmitting medium.
Network software: For analysing and monitoring the data as well as for transmitting the data
over local area network, a specific software is also required which can fragment the data into
meaningful packets. All packets have the address of their source as well as destination.
Receiving computers deliver these packets at desired destination after interpreting them.
TASK 3
A.C 3.1 build and configure a LAN to meet a given requirement
VLAN- VLAN trunk protocol is reduced the administration in switched networking and the
configuration has been occurred with the help of VTP server, it also distributed in all the
switches.
9
For achieving the benefits of networking it is necessary that suitable LAN components
are used in the infrastructure. Local area network has following components.
Hubs and switches: These are one of the basic components for networking. Hubs are also known
as routers and they connect multiple computer systems with each other. These are used in both
wireless and in wired LAN. They provide the routing path for effective information exchange.
Power supply: All LAN technologies essentially consist of power supply. The wired local area
network shares data with the use of cables. Thus, in wired LAN data is interpreted as electronic
pulse. On the other hand, in wireless network data is transmitted via radio waves. These waves
are produced by using current.
Network adapter and medium: To establish the connection network adapter is required. It first
converts data into suitable electronic signals and then if network traffic is not present then it
transmits the data to network. The element of network adapter which serves this purpose is called
media access control (MAC). The MAC address is defined as the serial number of network
adapter. In most of the computer systems it is integrated into motherboard of system.
The networking medium in wired local area networks is called as networking cables.
Organisation can use twisted pair cable or fibre optic cables (Ojha, Misra and Raghuwanshi,
2015). Unshielded twisted cable is also called Ethernet cable. To connect cables connectors are
used. The most commonly used connector is RJ45. Every computer system in the network has
RJ45 port for providing connections to twisted pair cables. For wireless local area networks
cables are not used as networking medium rather they use radio waves as transmitting medium.
Network software: For analysing and monitoring the data as well as for transmitting the data
over local area network, a specific software is also required which can fragment the data into
meaningful packets. All packets have the address of their source as well as destination.
Receiving computers deliver these packets at desired destination after interpreting them.
TASK 3
A.C 3.1 build and configure a LAN to meet a given requirement
VLAN- VLAN trunk protocol is reduced the administration in switched networking and the
configuration has been occurred with the help of VTP server, it also distributed in all the
switches.
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Routing is directly configured and proving many routing functions with the help of devices on
switch A and Switch B.
Configuration of VTP and STP-
VLAN 21, Name: Marketing is helpful for supporting two servers attached such as fa0/9 and
fa0/10
VLAN 22, Name: Sale is helpful for supporting two servers such as fa0/13 and fa0/14 Vlan 23,
VLAN 23,Name: Engineering, will support two servers attached to fa0/15 and fa0/16
Access ports that connect to server should transition immediately to forwarding state upon
detecting the connection of a device.
SwitchB VTP mode needs to be the same as SwitchA.
SwitchB must operate in the same spanning tree mode as SwitchA.
No routing is to be configured on SwitchB.
–Only the SVI vlan 1 is to be configured and it is to use address 192.168.1.11/24.
Building a LAN
To Build a LAN, first of all it is important for network typologies to support the
information across the network. There is various type of typologies used such as tree, bus, Mesh,
star topology etc. Mesh technology is local area network that connect one node to another. It is
the most interactive process useful for communication from one place to another. But nowadays,
eternal is playing important role in communication network because it is standard based medium
protocol. It sends the signal with the help of media and connect computer system to local area
network. The Football Field Marketing Ltd also uses the different communication network for
transmitting the signal from one place to another. Recently, the organization use Ethernet
networks to build a valid channel for communication.
A switch is medium that connects two or more devices in communication network
system. This is basically made by Local area network. This medium is very helpful for
exchanging information and data. It easily connects another device effectively and efficiently.
This is also linked with router which is helpful for providing the positioning and direction of web
traffic. There are wide range of local area network is also known as Wide area network or MAN.
It is simply enhanced the communication network all over the world (Raza, Kulkarni, and
Sooriyabandara, 2017).
Configuration of LAN-
10
switch A and Switch B.
Configuration of VTP and STP-
VLAN 21, Name: Marketing is helpful for supporting two servers attached such as fa0/9 and
fa0/10
VLAN 22, Name: Sale is helpful for supporting two servers such as fa0/13 and fa0/14 Vlan 23,
VLAN 23,Name: Engineering, will support two servers attached to fa0/15 and fa0/16
Access ports that connect to server should transition immediately to forwarding state upon
detecting the connection of a device.
SwitchB VTP mode needs to be the same as SwitchA.
SwitchB must operate in the same spanning tree mode as SwitchA.
No routing is to be configured on SwitchB.
–Only the SVI vlan 1 is to be configured and it is to use address 192.168.1.11/24.
Building a LAN
To Build a LAN, first of all it is important for network typologies to support the
information across the network. There is various type of typologies used such as tree, bus, Mesh,
star topology etc. Mesh technology is local area network that connect one node to another. It is
the most interactive process useful for communication from one place to another. But nowadays,
eternal is playing important role in communication network because it is standard based medium
protocol. It sends the signal with the help of media and connect computer system to local area
network. The Football Field Marketing Ltd also uses the different communication network for
transmitting the signal from one place to another. Recently, the organization use Ethernet
networks to build a valid channel for communication.
A switch is medium that connects two or more devices in communication network
system. This is basically made by Local area network. This medium is very helpful for
exchanging information and data. It easily connects another device effectively and efficiently.
This is also linked with router which is helpful for providing the positioning and direction of web
traffic. There are wide range of local area network is also known as Wide area network or MAN.
It is simply enhanced the communication network all over the world (Raza, Kulkarni, and
Sooriyabandara, 2017).
Configuration of LAN-
10

The firewall comprises a list of different functions which required in configuration of
Local area network. VPN Firewall is device that is designed for protecting unauthorized and
malicious attacks. VPN is basically installed in server and work for dynamic host configuration
protocol server. This configuration is also known as DHCP. They provide the Internet protocol
address and gateway. There are some important steps in order to configure a Local area network:
First step is go to network configuration and choose LAN setup options.
Enter the correct IP address
router calculates the network number
DHCP server is enabled with the help of following steps such as
1. Enter the domain name of router
2. Starting the IP Address and ending
3. Mention lease time for clients
4. Enable and DNS Proxy checked in proper ways
5. After competing process, click on Apply button.
A.C 3.2 implement network security on a LAN
Local area network is collection of computer that connect to device and share
information and data to server. It is necessary for Footfall Field Marketing Ltd organization to
secure their data and personal information. There is different way of implementing network
security in Local area network that is as follows: -
Filtering/ Port Blocking- The important data and information are represented as packet
of data. Firewall plays important role to protect the data against unauthorized stuffs and intruders
because they can access the personal data and information of Footfall Field marketing. Internet
connection medium can harm system or hardware. Firewall filters removes irrelevant data in
system because they will damage the entire computer system.
Encryption- Encryption process to secure data in the communication network and they
provide the security by unauthorized person. This concept is helping the high authentication
through cryptography (Vaquero and Rodero-Merino, 2014). Some personal data send in the form
of code and only receiver understand the information and data. The confidential data and
information to be secured in the communication network.
11
Local area network. VPN Firewall is device that is designed for protecting unauthorized and
malicious attacks. VPN is basically installed in server and work for dynamic host configuration
protocol server. This configuration is also known as DHCP. They provide the Internet protocol
address and gateway. There are some important steps in order to configure a Local area network:
First step is go to network configuration and choose LAN setup options.
Enter the correct IP address
router calculates the network number
DHCP server is enabled with the help of following steps such as
1. Enter the domain name of router
2. Starting the IP Address and ending
3. Mention lease time for clients
4. Enable and DNS Proxy checked in proper ways
5. After competing process, click on Apply button.
A.C 3.2 implement network security on a LAN
Local area network is collection of computer that connect to device and share
information and data to server. It is necessary for Footfall Field Marketing Ltd organization to
secure their data and personal information. There is different way of implementing network
security in Local area network that is as follows: -
Filtering/ Port Blocking- The important data and information are represented as packet
of data. Firewall plays important role to protect the data against unauthorized stuffs and intruders
because they can access the personal data and information of Footfall Field marketing. Internet
connection medium can harm system or hardware. Firewall filters removes irrelevant data in
system because they will damage the entire computer system.
Encryption- Encryption process to secure data in the communication network and they
provide the security by unauthorized person. This concept is helping the high authentication
through cryptography (Vaquero and Rodero-Merino, 2014). Some personal data send in the form
of code and only receiver understand the information and data. The confidential data and
information to be secured in the communication network.
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 22
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





