LAN Technologies: Infrastructure Design, Implementation, and Security
VerifiedAdded on 2024/05/20
|44
|8567
|496
Report
AI Summary
This report provides an in-depth analysis of Local Area Network (LAN) technologies, covering IEEE 802 standards, VLANs, VTP, DHCP, and LAN hardware. It critically evaluates different LAN technologies, analyzes traffic-intensive services, and addresses LAN concerns related to security, reliability, and performance. The report includes a LAN infrastructure design for a company, an implementation of a secure network using Cisco Packet Tracer, and a review of network security measures. Furthermore, it discusses LAN monitoring, troubleshooting, and performance evaluation, along with recommendations for sustaining network security and reliability. The document concludes with a reflection on the work and a justification of the conclusions.

Local Area Networking
Technology
Technology
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
INTRODUCTION..........................................................................................................................3
LO1 Understand the impact of LAN technologies......................................................................4
A.C 1.1 critically evaluates different LAN technologies.........................................................4
A.C 1.2 critically analyze traffic intensive services and their performance.........................12
A.C 1.3 Discuss LAN concerns and makes recommendations to sustain network..............14
M1. Identify and apply strategies to find appropriate solutions.........................................15
LO2 Be able to design LAN infrastructures..............................................................................16
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of their
requirements........................................................................................................................16
A.C 2.2 critically evaluates the suitability of LAN component.............................................19
LO3 Be able to implement LAN infrastructures.......................................................................20
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement........20
A.C 3.2 Implement network securities on a LAN.................................................................25
A.C 3.3 critically reviews and tests a LAN............................................................................29
M2. Select/ design and apply appropriate methods/ techniques.......................................32
M3. Present and communicate appropriate findings..........................................................32
D2. Take responsibility for managing and organizing activities...........................................33
D3. Demonstrate convergent, lateral and creative thinking...............................................33
LO4. Be able to manage LAN infrastructures...........................................................................34
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and managed
(via troubleshooting)............................................................................................................34
A.C 4.2 Resolve LAN issues to improve security, reliability, and performance.......................35
A.C 4.3 critically evaluates the performance of a LAN.........................................................37
D1. Use critical reflection to evaluate own work and justify the valid conclusion..............38
1
INTRODUCTION..........................................................................................................................3
LO1 Understand the impact of LAN technologies......................................................................4
A.C 1.1 critically evaluates different LAN technologies.........................................................4
A.C 1.2 critically analyze traffic intensive services and their performance.........................12
A.C 1.3 Discuss LAN concerns and makes recommendations to sustain network..............14
M1. Identify and apply strategies to find appropriate solutions.........................................15
LO2 Be able to design LAN infrastructures..............................................................................16
A.C 2.1 Designs a LAN infrastructure for the company which will facilitate all of their
requirements........................................................................................................................16
A.C 2.2 critically evaluates the suitability of LAN component.............................................19
LO3 Be able to implement LAN infrastructures.......................................................................20
A.C 3.1 Build and configure a LAN (including services) to meet a given requirement........20
A.C 3.2 Implement network securities on a LAN.................................................................25
A.C 3.3 critically reviews and tests a LAN............................................................................29
M2. Select/ design and apply appropriate methods/ techniques.......................................32
M3. Present and communicate appropriate findings..........................................................32
D2. Take responsibility for managing and organizing activities...........................................33
D3. Demonstrate convergent, lateral and creative thinking...............................................33
LO4. Be able to manage LAN infrastructures...........................................................................34
A.C 4.1 critically discusses how this LAN infrastructure will be monitored and managed
(via troubleshooting)............................................................................................................34
A.C 4.2 Resolve LAN issues to improve security, reliability, and performance.......................35
A.C 4.3 critically evaluates the performance of a LAN.........................................................37
D1. Use critical reflection to evaluate own work and justify the valid conclusion..............38
1

Conclusion................................................................................................................................40
References................................................................................................................................41
List of Figures
Figure 1 IEEE 802........................................................................................................................4
Figure 2 IEEE 802.11...................................................................................................................5
Figure 3 STP................................................................................................................................5
Figure 4 VLAN.............................................................................................................................6
Figure 5 VTP...............................................................................................................................6
Figure 6 Standby routing............................................................................................................7
Figure 7 Ether channel...............................................................................................................7
Figure 8 ISL.................................................................................................................................8
Figure 9 DHCP.............................................................................................................................8
Figure 10 Layer 2 switches.........................................................................................................9
Figure 11 Layer 3 switches.........................................................................................................9
Figure 12 Layer 4 switches.......................................................................................................10
Figure 13 Wireless devices.......................................................................................................10
Figure 14 Network interfaces...................................................................................................11
Figure 15 Client devices...........................................................................................................11
Figure 16 IP precedence...........................................................................................................12
Figure 17 Design view of an arganization................................................................................16
Figure 18 Router 0 configuration.............................................................................................23
Figure 19 DNS server of the company.....................................................................................24
Figure 20 Network diagram on Cisco Packet tracer.................................................................24
Figure 21 Router 1 configuartion.............................................................................................28
Figure 22 Test case 1................................................................................................................30
Figure 23 Test case 2................................................................................................................30
Figure 24 Test case 3................................................................................................................31
Figure 25 Test case 4................................................................................................................31
Figure 26 Test case 5................................................................................................................32
List of Tables
2
References................................................................................................................................41
List of Figures
Figure 1 IEEE 802........................................................................................................................4
Figure 2 IEEE 802.11...................................................................................................................5
Figure 3 STP................................................................................................................................5
Figure 4 VLAN.............................................................................................................................6
Figure 5 VTP...............................................................................................................................6
Figure 6 Standby routing............................................................................................................7
Figure 7 Ether channel...............................................................................................................7
Figure 8 ISL.................................................................................................................................8
Figure 9 DHCP.............................................................................................................................8
Figure 10 Layer 2 switches.........................................................................................................9
Figure 11 Layer 3 switches.........................................................................................................9
Figure 12 Layer 4 switches.......................................................................................................10
Figure 13 Wireless devices.......................................................................................................10
Figure 14 Network interfaces...................................................................................................11
Figure 15 Client devices...........................................................................................................11
Figure 16 IP precedence...........................................................................................................12
Figure 17 Design view of an arganization................................................................................16
Figure 18 Router 0 configuration.............................................................................................23
Figure 19 DNS server of the company.....................................................................................24
Figure 20 Network diagram on Cisco Packet tracer.................................................................24
Figure 21 Router 1 configuartion.............................................................................................28
Figure 22 Test case 1................................................................................................................30
Figure 23 Test case 2................................................................................................................30
Figure 24 Test case 3................................................................................................................31
Figure 25 Test case 4................................................................................................................31
Figure 26 Test case 5................................................................................................................32
List of Tables
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Table 1 Test cases.....................................................................................................................33
INTRODUCTION
The purpose of this project is to understand the concept of LAN technologies. This project
will help to learn the LAN technology in depth and the designing of network infrastructure
will take place. The requirements of LAN network will be understood and identified in this
project. In the project, I will learn how to implement a secure network according to the
requirement. Also, the network designed should be scalable for the company. By the help of
this project, various network technologies will be understood that are IEEE 802 standards of
LAN, VLAN, ether channel, VTP, DHCP, LAN hardware and various security
recommendations. In this project, I will also analyze traffic intensive interfaces, various LAN
concerns, and LAN performance.
In this report, I will learn the methodologies to secure the data from unauthorized access.
Data or information of an organization is important and needs to be secured. I will also test
the infrastructure of LAN implemented and review it.
3
INTRODUCTION
The purpose of this project is to understand the concept of LAN technologies. This project
will help to learn the LAN technology in depth and the designing of network infrastructure
will take place. The requirements of LAN network will be understood and identified in this
project. In the project, I will learn how to implement a secure network according to the
requirement. Also, the network designed should be scalable for the company. By the help of
this project, various network technologies will be understood that are IEEE 802 standards of
LAN, VLAN, ether channel, VTP, DHCP, LAN hardware and various security
recommendations. In this project, I will also analyze traffic intensive interfaces, various LAN
concerns, and LAN performance.
In this report, I will learn the methodologies to secure the data from unauthorized access.
Data or information of an organization is important and needs to be secured. I will also test
the infrastructure of LAN implemented and review it.
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
LO1 Understand the impact of LAN technologies
A.C 1.1 critically evaluates different LAN technologies
Local area network
The Local network is the sort of the system, which incorporates gathering of a PC
framework, diverse gadgets, and so forth. The LAN network is utilized to exchange the
information and data starting with one end then onto the next end with no issue. This
system is utilized by various organization, office, universities or business. The setup of this
system is simple and the man preferred standpoint of this system is that it diminishes the
cost of the system and it incorporates least segment look at then different systems. Be that
as it may, the negative purpose of LAN organizes that is utilized for the just little region.
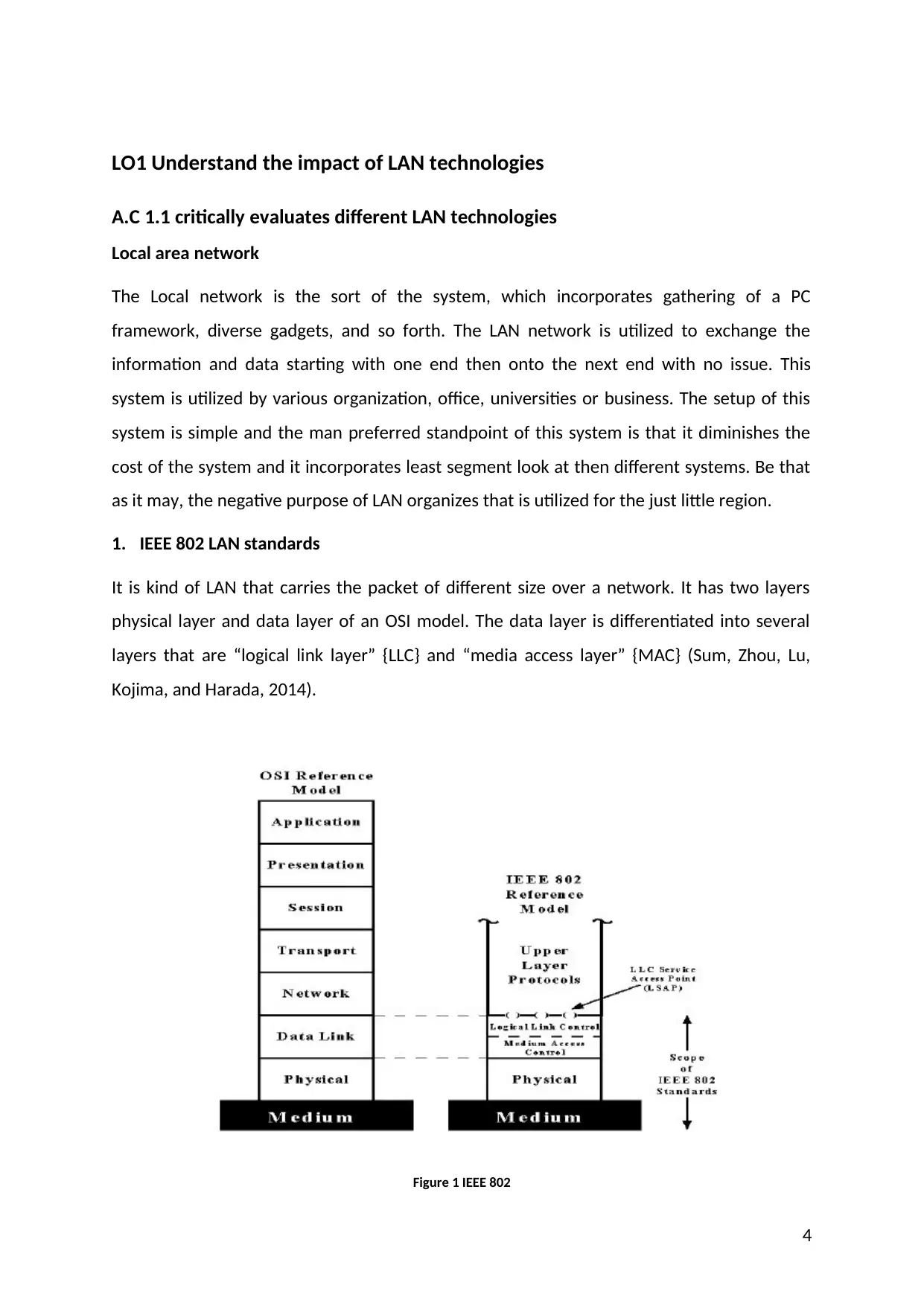
1. IEEE 802 LAN standards
It is kind of LAN that carries the packet of different size over a network. It has two layers
physical layer and data layer of an OSI model. The data layer is differentiated into several
layers that are “logical link layer” {LLC} and “media access layer” {MAC} (Sum, Zhou, Lu,
Kojima, and Harada, 2014).
Figure 1 IEEE 802
4
A.C 1.1 critically evaluates different LAN technologies
Local area network
The Local network is the sort of the system, which incorporates gathering of a PC
framework, diverse gadgets, and so forth. The LAN network is utilized to exchange the
information and data starting with one end then onto the next end with no issue. This
system is utilized by various organization, office, universities or business. The setup of this
system is simple and the man preferred standpoint of this system is that it diminishes the
cost of the system and it incorporates least segment look at then different systems. Be that
as it may, the negative purpose of LAN organizes that is utilized for the just little region.
1. IEEE 802 LAN standards
It is kind of LAN that carries the packet of different size over a network. It has two layers
physical layer and data layer of an OSI model. The data layer is differentiated into several
layers that are “logical link layer” {LLC} and “media access layer” {MAC} (Sum, Zhou, Lu,
Kojima, and Harada, 2014).
Figure 1 IEEE 802
4
2. IEEE 802.11 wireless standards
It is the collection of the physical layer and media access (MAC) for completing LAN
connection. It is used for providing wireless services like Bluetooth and Wi-Fi (Au, 2016).
Figure 2 IEEE 802.11
3. STP (Spanning Tree Protocol)
For connecting two networks of the different computer a protocol is needed that will allow
information exchange among the computer present in the network. The protocol needed
for the purpose is spanning tree (Cohen, 2015).
Figure 3 STP
4. VLANs (Virtual LAN)
5
It is the collection of the physical layer and media access (MAC) for completing LAN
connection. It is used for providing wireless services like Bluetooth and Wi-Fi (Au, 2016).
Figure 2 IEEE 802.11
3. STP (Spanning Tree Protocol)
For connecting two networks of the different computer a protocol is needed that will allow
information exchange among the computer present in the network. The protocol needed
for the purpose is spanning tree (Cohen, 2015).
Figure 3 STP
4. VLANs (Virtual LAN)
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
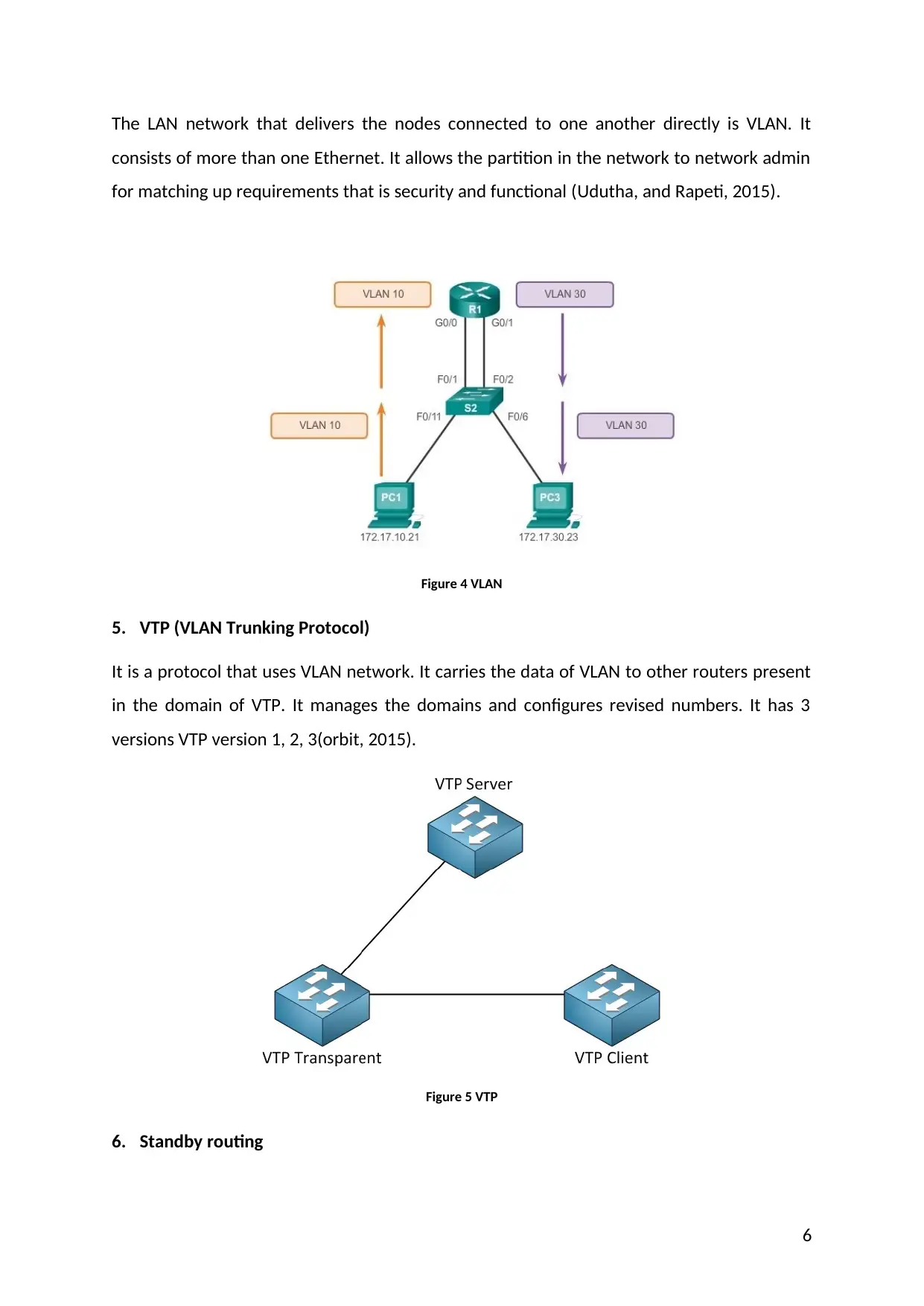
The LAN network that delivers the nodes connected to one another directly is VLAN. It
consists of more than one Ethernet. It allows the partition in the network to network admin
for matching up requirements that is security and functional (Udutha, and Rapeti, 2015).
Figure 4 VLAN
5. VTP (VLAN Trunking Protocol)
It is a protocol that uses VLAN network. It carries the data of VLAN to other routers present
in the domain of VTP. It manages the domains and configures revised numbers. It has 3
versions VTP version 1, 2, 3(orbit, 2015).
Figure 5 VTP
6. Standby routing
6
consists of more than one Ethernet. It allows the partition in the network to network admin
for matching up requirements that is security and functional (Udutha, and Rapeti, 2015).
Figure 4 VLAN
5. VTP (VLAN Trunking Protocol)
It is a protocol that uses VLAN network. It carries the data of VLAN to other routers present
in the domain of VTP. It manages the domains and configures revised numbers. It has 3
versions VTP version 1, 2, 3(orbit, 2015).
Figure 5 VTP
6. Standby routing
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
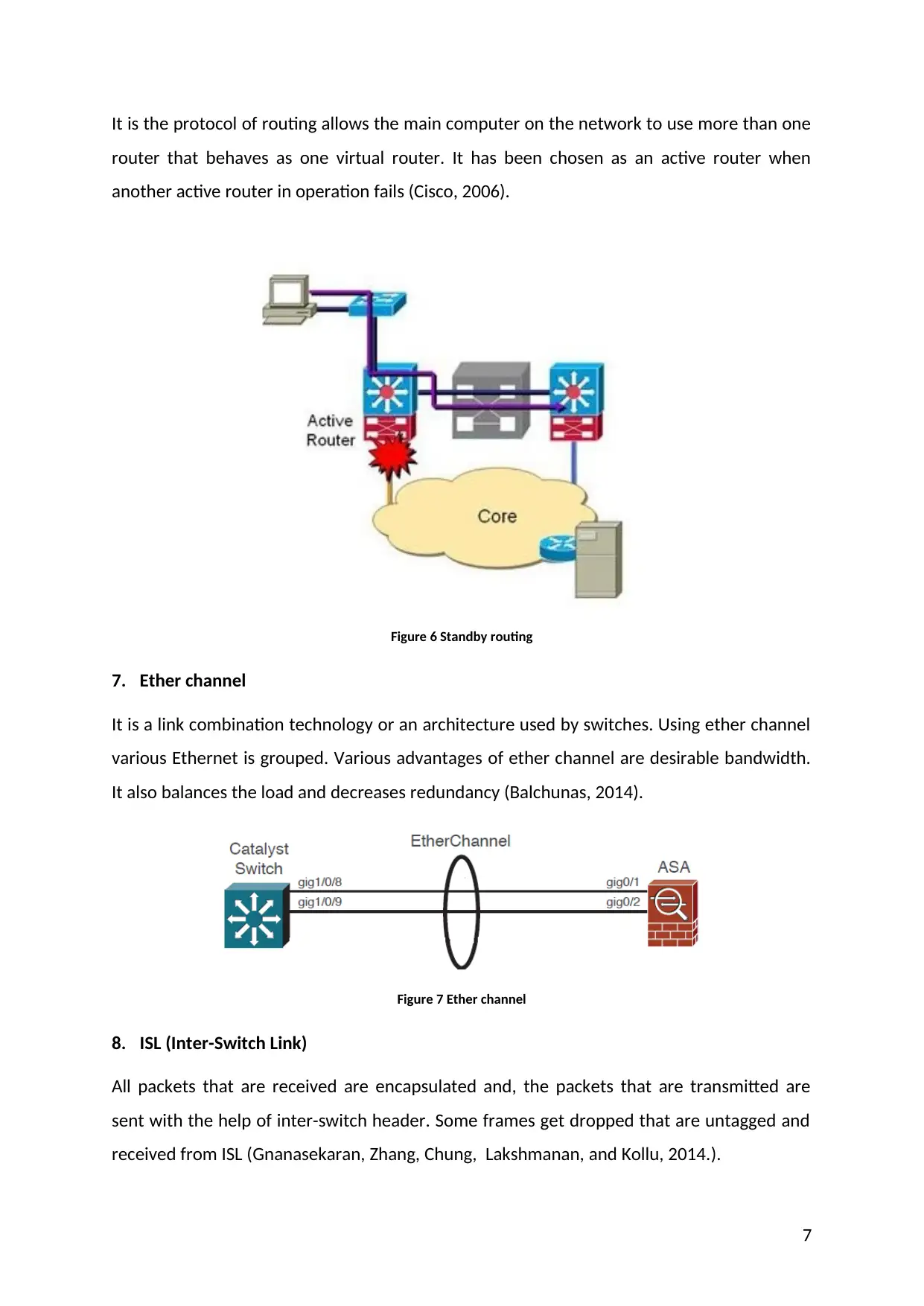
It is the protocol of routing allows the main computer on the network to use more than one
router that behaves as one virtual router. It has been chosen as an active router when
another active router in operation fails (Cisco, 2006).
Figure 6 Standby routing
7. Ether channel
It is a link combination technology or an architecture used by switches. Using ether channel
various Ethernet is grouped. Various advantages of ether channel are desirable bandwidth.
It also balances the load and decreases redundancy (Balchunas, 2014).
Figure 7 Ether channel
8. ISL (Inter-Switch Link)
All packets that are received are encapsulated and, the packets that are transmitted are
sent with the help of inter-switch header. Some frames get dropped that are untagged and
received from ISL (Gnanasekaran, Zhang, Chung, Lakshmanan, and Kollu, 2014.).
7
router that behaves as one virtual router. It has been chosen as an active router when
another active router in operation fails (Cisco, 2006).
Figure 6 Standby routing
7. Ether channel
It is a link combination technology or an architecture used by switches. Using ether channel
various Ethernet is grouped. Various advantages of ether channel are desirable bandwidth.
It also balances the load and decreases redundancy (Balchunas, 2014).
Figure 7 Ether channel
8. ISL (Inter-Switch Link)
All packets that are received are encapsulated and, the packets that are transmitted are
sent with the help of inter-switch header. Some frames get dropped that are untagged and
received from ISL (Gnanasekaran, Zhang, Chung, Lakshmanan, and Kollu, 2014.).
7
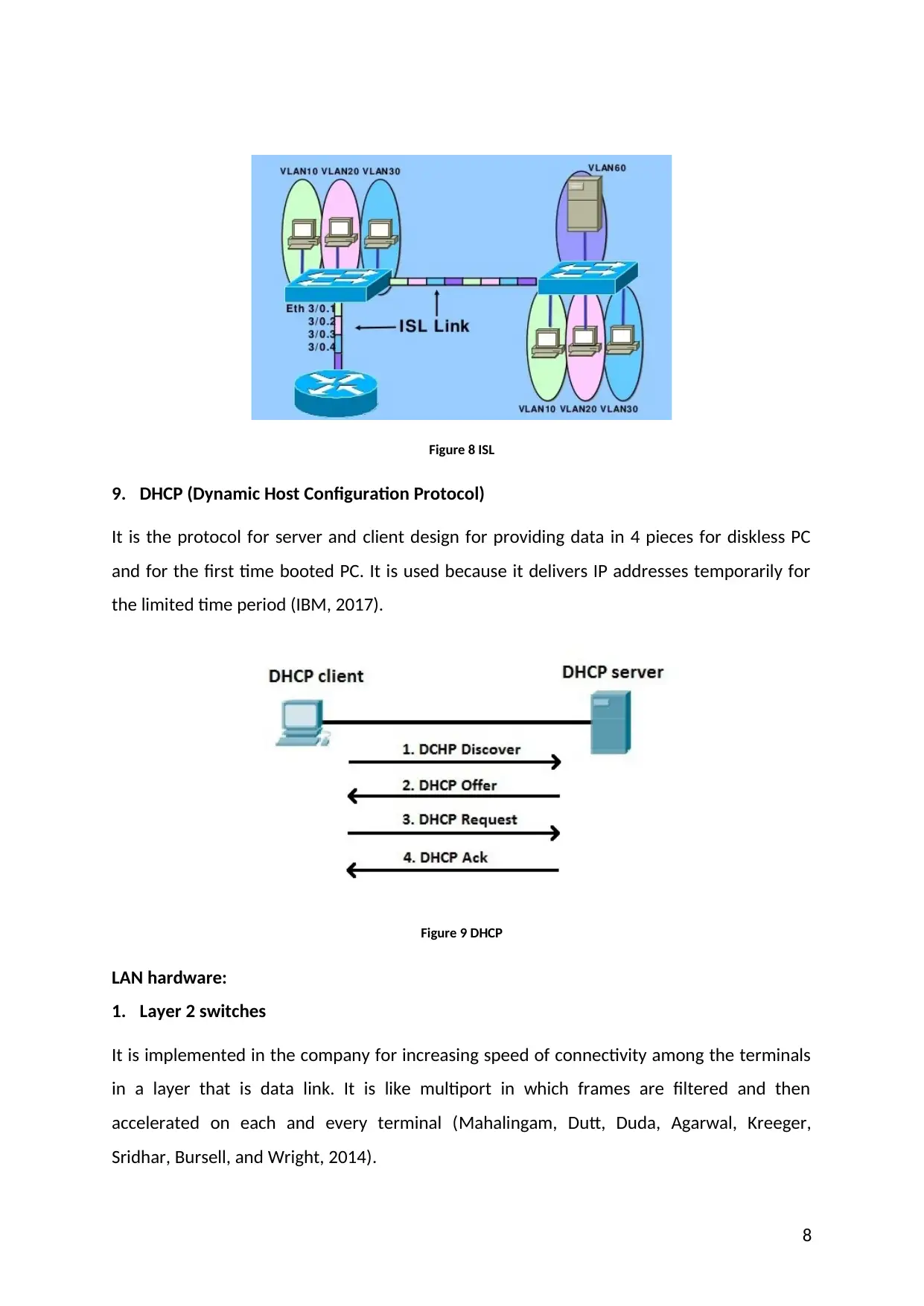
Figure 8 ISL
9. DHCP (Dynamic Host Configuration Protocol)
It is the protocol for server and client design for providing data in 4 pieces for diskless PC
and for the first time booted PC. It is used because it delivers IP addresses temporarily for
the limited time period (IBM, 2017).
Figure 9 DHCP
LAN hardware:
1. Layer 2 switches
It is implemented in the company for increasing speed of connectivity among the terminals
in a layer that is data link. It is like multiport in which frames are filtered and then
accelerated on each and every terminal (Mahalingam, Dutt, Duda, Agarwal, Kreeger,
Sridhar, Bursell, and Wright, 2014).
8
9. DHCP (Dynamic Host Configuration Protocol)
It is the protocol for server and client design for providing data in 4 pieces for diskless PC
and for the first time booted PC. It is used because it delivers IP addresses temporarily for
the limited time period (IBM, 2017).
Figure 9 DHCP
LAN hardware:
1. Layer 2 switches
It is implemented in the company for increasing speed of connectivity among the terminals
in a layer that is data link. It is like multiport in which frames are filtered and then
accelerated on each and every terminal (Mahalingam, Dutt, Duda, Agarwal, Kreeger,
Sridhar, Bursell, and Wright, 2014).
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
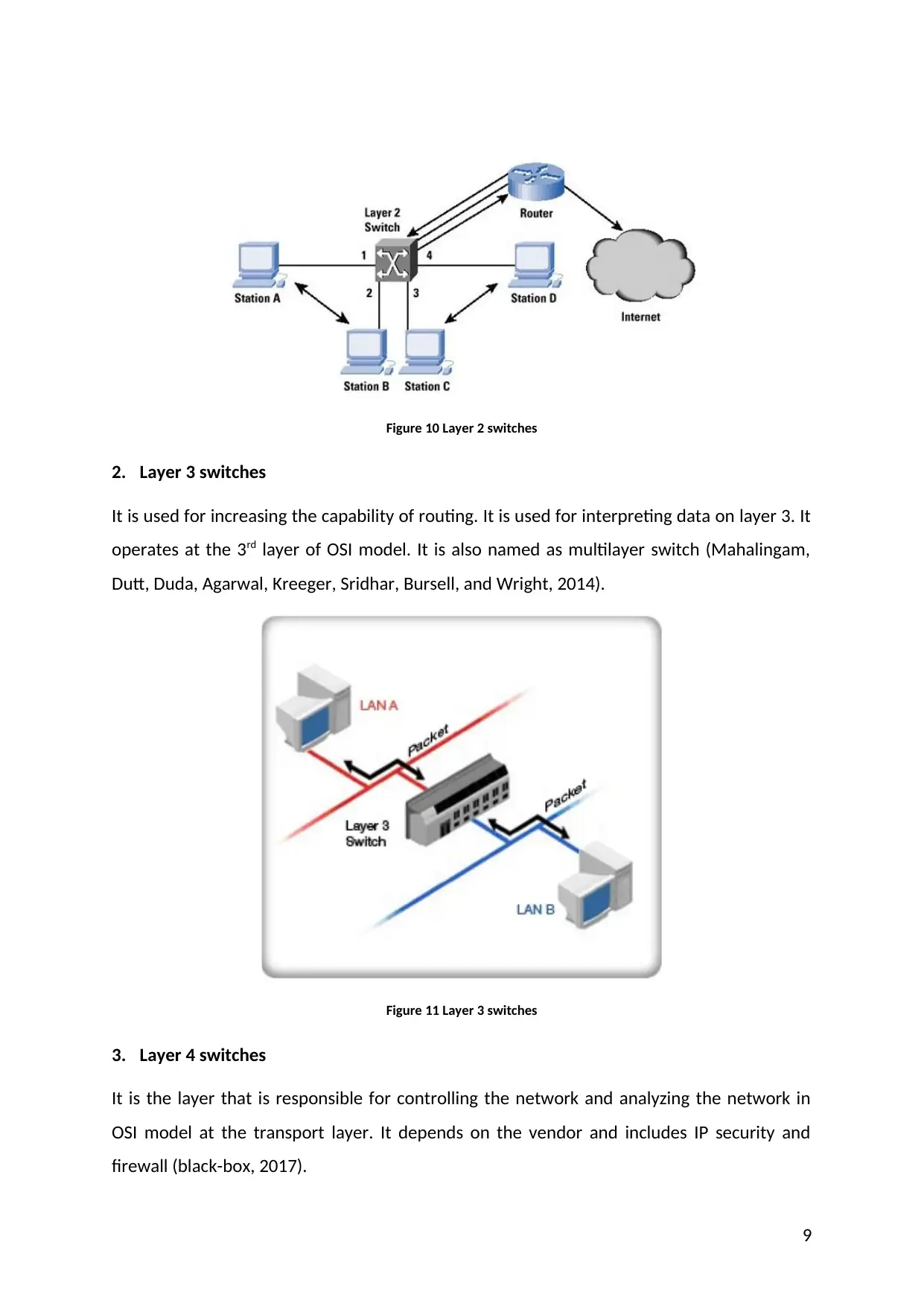
Figure 10 Layer 2 switches
2. Layer 3 switches
It is used for increasing the capability of routing. It is used for interpreting data on layer 3. It
operates at the 3rd layer of OSI model. It is also named as multilayer switch (Mahalingam,
Dutt, Duda, Agarwal, Kreeger, Sridhar, Bursell, and Wright, 2014).
Figure 11 Layer 3 switches
3. Layer 4 switches
It is the layer that is responsible for controlling the network and analyzing the network in
OSI model at the transport layer. It depends on the vendor and includes IP security and
firewall (black-box, 2017).
9
2. Layer 3 switches
It is used for increasing the capability of routing. It is used for interpreting data on layer 3. It
operates at the 3rd layer of OSI model. It is also named as multilayer switch (Mahalingam,
Dutt, Duda, Agarwal, Kreeger, Sridhar, Bursell, and Wright, 2014).
Figure 11 Layer 3 switches
3. Layer 4 switches
It is the layer that is responsible for controlling the network and analyzing the network in
OSI model at the transport layer. It depends on the vendor and includes IP security and
firewall (black-box, 2017).
9
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
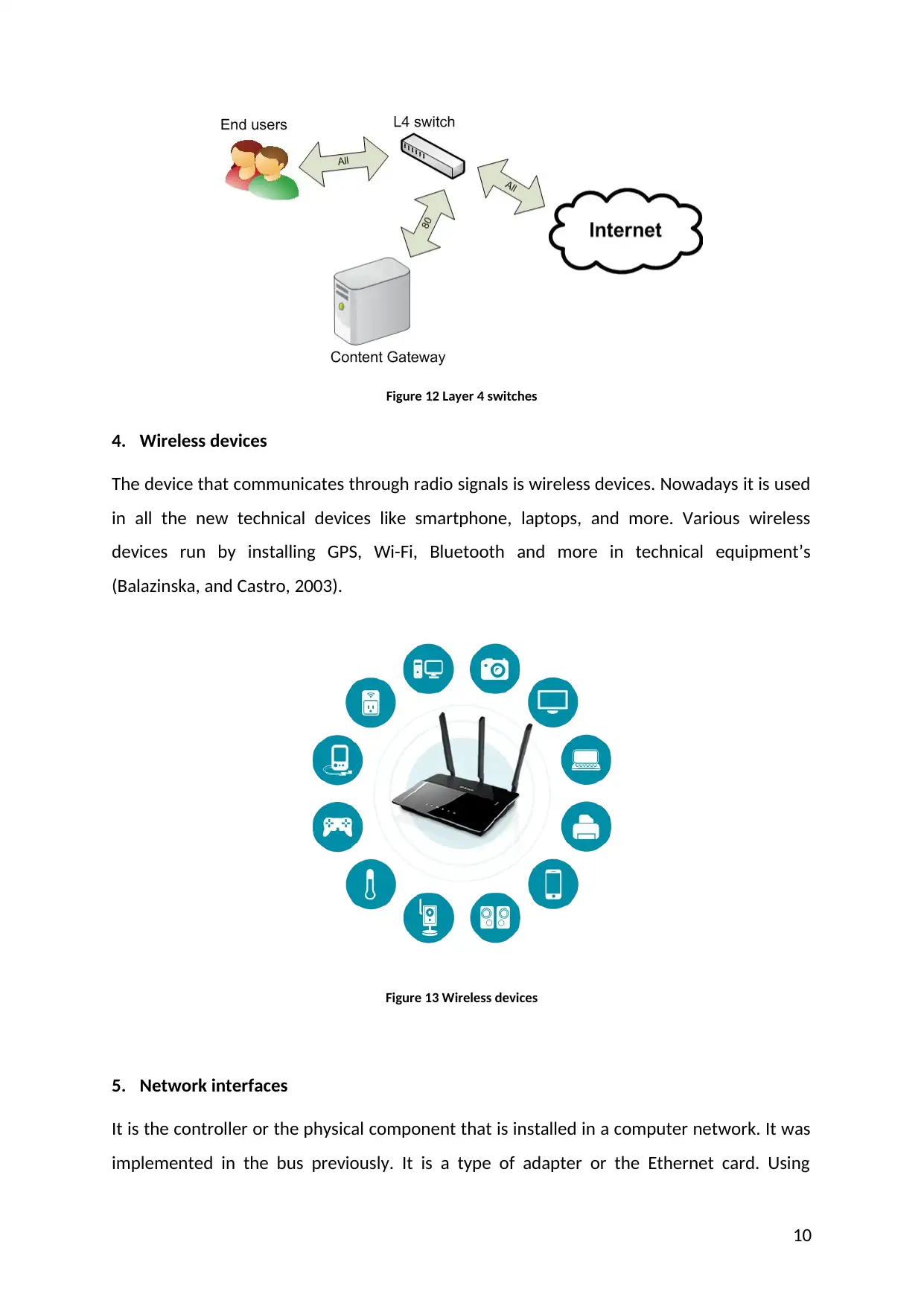
Figure 12 Layer 4 switches
4. Wireless devices
The device that communicates through radio signals is wireless devices. Nowadays it is used
in all the new technical devices like smartphone, laptops, and more. Various wireless
devices run by installing GPS, Wi-Fi, Bluetooth and more in technical equipment’s
(Balazinska, and Castro, 2003).
Figure 13 Wireless devices
5. Network interfaces
It is the controller or the physical component that is installed in a computer network. It was
implemented in the bus previously. It is a type of adapter or the Ethernet card. Using
10
4. Wireless devices
The device that communicates through radio signals is wireless devices. Nowadays it is used
in all the new technical devices like smartphone, laptops, and more. Various wireless
devices run by installing GPS, Wi-Fi, Bluetooth and more in technical equipment’s
(Balazinska, and Castro, 2003).
Figure 13 Wireless devices
5. Network interfaces
It is the controller or the physical component that is installed in a computer network. It was
implemented in the bus previously. It is a type of adapter or the Ethernet card. Using
10
network interface computer system gets connected to the network. An example of the
network interface is RJ-45 (Sqa, 2010).
Figure 14 Network interfaces
6. Client devices
These are the peripherals that are used by the user or client. The devices accessible by the
user are client devices. Various client devices are PC, mobile, laptop and more.
Figure 15 Client devices
11
network interface is RJ-45 (Sqa, 2010).
Figure 14 Network interfaces
6. Client devices
These are the peripherals that are used by the user or client. The devices accessible by the
user are client devices. Various client devices are PC, mobile, laptop and more.
Figure 15 Client devices
11
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 44
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





