Comprehensive Report on LAN Technologies, Hardware and QoS Management
VerifiedAdded on 2020/01/28
|50
|6692
|117
Report
AI Summary
This report provides a comprehensive analysis of LAN technologies, focusing on their role in enhancing organizational performance. It details various LAN technologies such as Ethernet, Fast Ethernet, and Gigabit Ethernet, along with their functionalities and applications. The report explores LAN hardware, including file servers, hubs, bridges, switches, routers, and firewalls, categorizing these devices based on the OSI model. It delves into the significance of Quality of Service (QoS) and bandwidth management, explaining their importance with examples. Furthermore, it covers topics such as IP address management, VLANs, and network topologies like bus, star, ring, mesh, tree, and hybrid, offering insights into their configurations and characteristics. The report also examines the role of switches, including their modes of operation and broadcast domains. Overall, the report provides a detailed overview of LAN technologies, network devices, and their impact on network performance and security.

Contents
Introduction.................................................................................................................................................2
TASK 1..........................................................................................................................................................2
LAN Hardware.....................................................................................................................................7
TASK 2........................................................................................................................................................18
TASK 3........................................................................................................................................................21
IP Address and VLSM.............................................................................................................................24
TASK 4........................................................................................................................................................25
TASK 5........................................................................................................................................................27
REFERENCES..............................................................................................................................................42
Introduction.................................................................................................................................................2
TASK 1..........................................................................................................................................................2
LAN Hardware.....................................................................................................................................7
TASK 2........................................................................................................................................................18
TASK 3........................................................................................................................................................21
IP Address and VLSM.............................................................................................................................24
TASK 4........................................................................................................................................................25
TASK 5........................................................................................................................................................27
REFERENCES..............................................................................................................................................42
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction
The report is prepared to analyze the use of LAN technologies and their role to increase the
performance of the organization. The project provides detailsof LAN and related techniques
and models to overcome security related issues. It will also explain LAN hardware such as file
servers, hubs, bridges, switches, routers, multilayer switches, voice gateways, firewalls, and
other devices. Computers in LAN are getting connected with a cable through Ethernet, Fast
Ethernet and Gig Ethernet or other media.
Security is one of the main aspects of any network because of data importance to an
organization. This course will help to learn router configuration, packet filter, troubleshooting
network, test network performance etc. This course will also help to get the understanding of
an IP address/pool management, VLAN, STP , VTP or monitoring tool for a network.
TASK 1
1.1 Evaluate various LAN technologies available in the market. Describe the technologies in
relation with scenario above.
LAN:In an enterprise network computers are getting connected in the same geographic area or
location known as LAN. An organization typically owns the entire campus network and the
The report is prepared to analyze the use of LAN technologies and their role to increase the
performance of the organization. The project provides detailsof LAN and related techniques
and models to overcome security related issues. It will also explain LAN hardware such as file
servers, hubs, bridges, switches, routers, multilayer switches, voice gateways, firewalls, and
other devices. Computers in LAN are getting connected with a cable through Ethernet, Fast
Ethernet and Gig Ethernet or other media.
Security is one of the main aspects of any network because of data importance to an
organization. This course will help to learn router configuration, packet filter, troubleshooting
network, test network performance etc. This course will also help to get the understanding of
an IP address/pool management, VLAN, STP , VTP or monitoring tool for a network.
TASK 1
1.1 Evaluate various LAN technologies available in the market. Describe the technologies in
relation with scenario above.
LAN:In an enterprise network computers are getting connected in the same geographic area or
location known as LAN. An organization typically owns the entire campus network and the
physical wiring. Campus networks commonly consist of Ethernet, 802.11 wireless LANs, higher-
speed Fast Ethernet, Fast Ether Channel, and Gigabit Ethernet LANs.
Institute of Electrical and Electronics Engineers (IEEE) Ethernet (802.3):-
Ethernet is a LAN technology based on the 802.3 standard of IEEE(Institute of Electrical and
Electronics Engineers) and offers a bandwidth of 10 Mbps between end users or PC, in other
words, LAN Technology is used to provide connectivity between PCsusing Ethernet technology
and committed speed is 10 Mbps between every end user. Switched Ethernet can eliminate the
possibility of collisions. In full-duplex modedata can be transmitted or received simultaneously,
hence Full-duplex mode increases network performance with throughput of 10 Mbps in each
direction.
speed Fast Ethernet, Fast Ether Channel, and Gigabit Ethernet LANs.
Institute of Electrical and Electronics Engineers (IEEE) Ethernet (802.3):-
Ethernet is a LAN technology based on the 802.3 standard of IEEE(Institute of Electrical and
Electronics Engineers) and offers a bandwidth of 10 Mbps between end users or PC, in other
words, LAN Technology is used to provide connectivity between PCsusing Ethernet technology
and committed speed is 10 Mbps between every end user. Switched Ethernet can eliminate the
possibility of collisions. In full-duplex modedata can be transmitted or received simultaneously,
hence Full-duplex mode increases network performance with throughput of 10 Mbps in each
direction.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
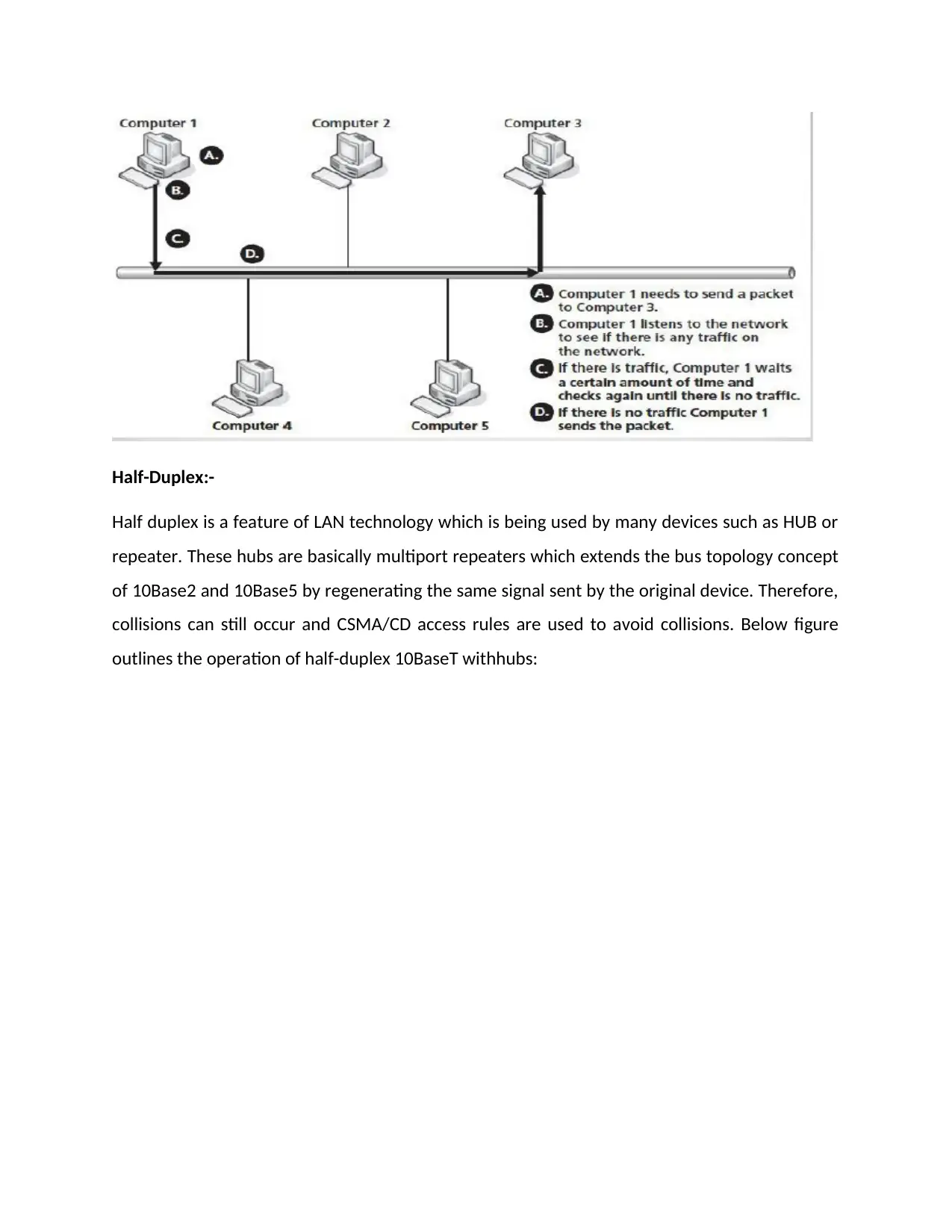
Half-Duplex:-
Half duplex is a feature of LAN technology which is being used by many devices such as HUB or
repeater. These hubs are basically multiport repeaters which extends the bus topology concept
of 10Base2 and 10Base5 by regenerating the same signal sent by the original device. Therefore,
collisions can still occur and CSMA/CD access rules are used to avoid collisions. Below figure
outlines the operation of half-duplex 10BaseT withhubs:
Half duplex is a feature of LAN technology which is being used by many devices such as HUB or
repeater. These hubs are basically multiport repeaters which extends the bus topology concept
of 10Base2 and 10Base5 by regenerating the same signal sent by the original device. Therefore,
collisions can still occur and CSMA/CD access rules are used to avoid collisions. Below figure
outlines the operation of half-duplex 10BaseT withhubs:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
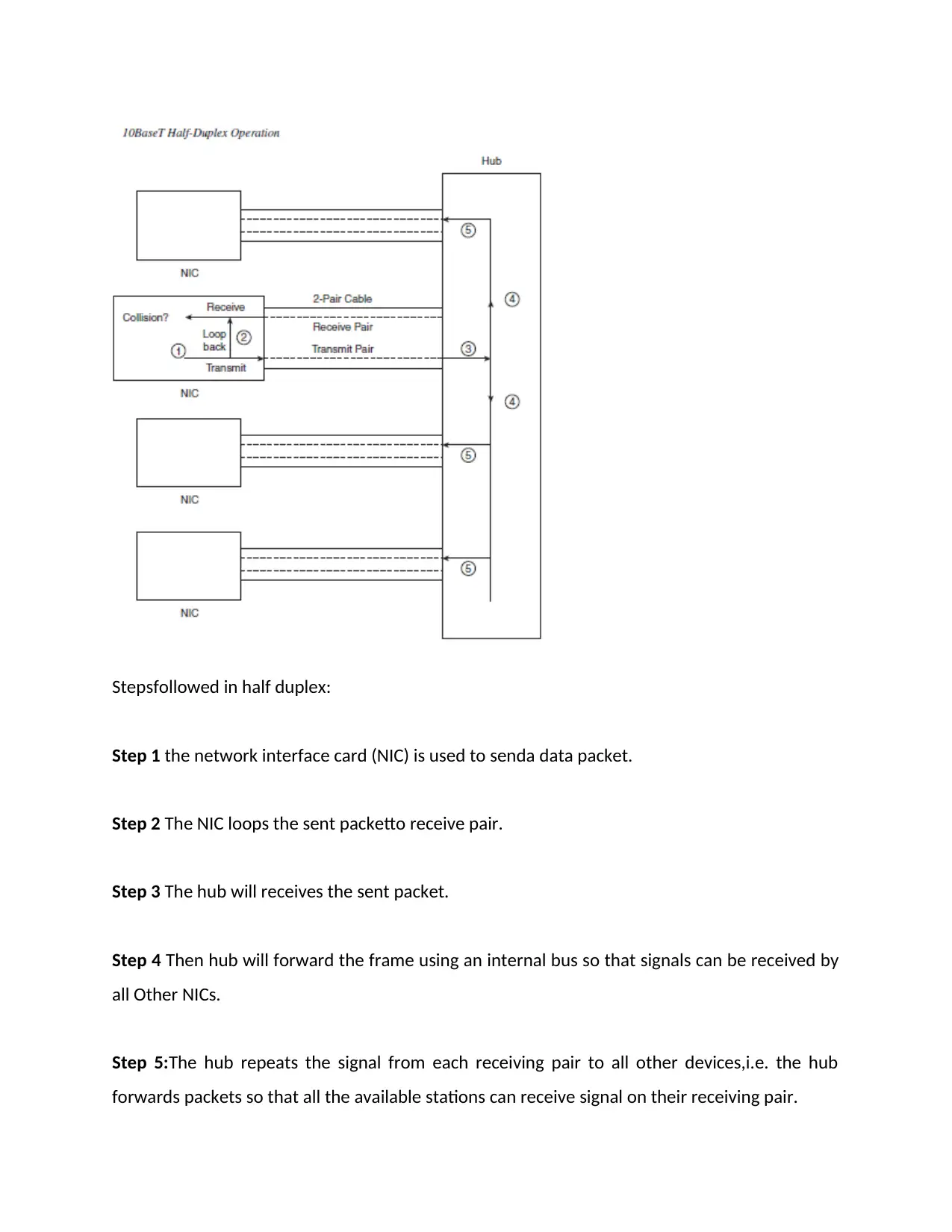
Stepsfollowed in half duplex:
Step 1 the network interface card (NIC) is used to senda data packet.
Step 2 The NIC loops the sent packetto receive pair.
Step 3 The hub will receives the sent packet.
Step 4 Then hub will forward the frame using an internal bus so that signals can be received by
all Other NICs.
Step 5:The hub repeats the signal from each receiving pair to all other devices,i.e. the hub
forwards packets so that all the available stations can receive signal on their receiving pair.
Step 1 the network interface card (NIC) is used to senda data packet.
Step 2 The NIC loops the sent packetto receive pair.
Step 3 The hub will receives the sent packet.
Step 4 Then hub will forward the frame using an internal bus so that signals can be received by
all Other NICs.
Step 5:The hub repeats the signal from each receiving pair to all other devices,i.e. the hub
forwards packets so that all the available stations can receive signal on their receiving pair.
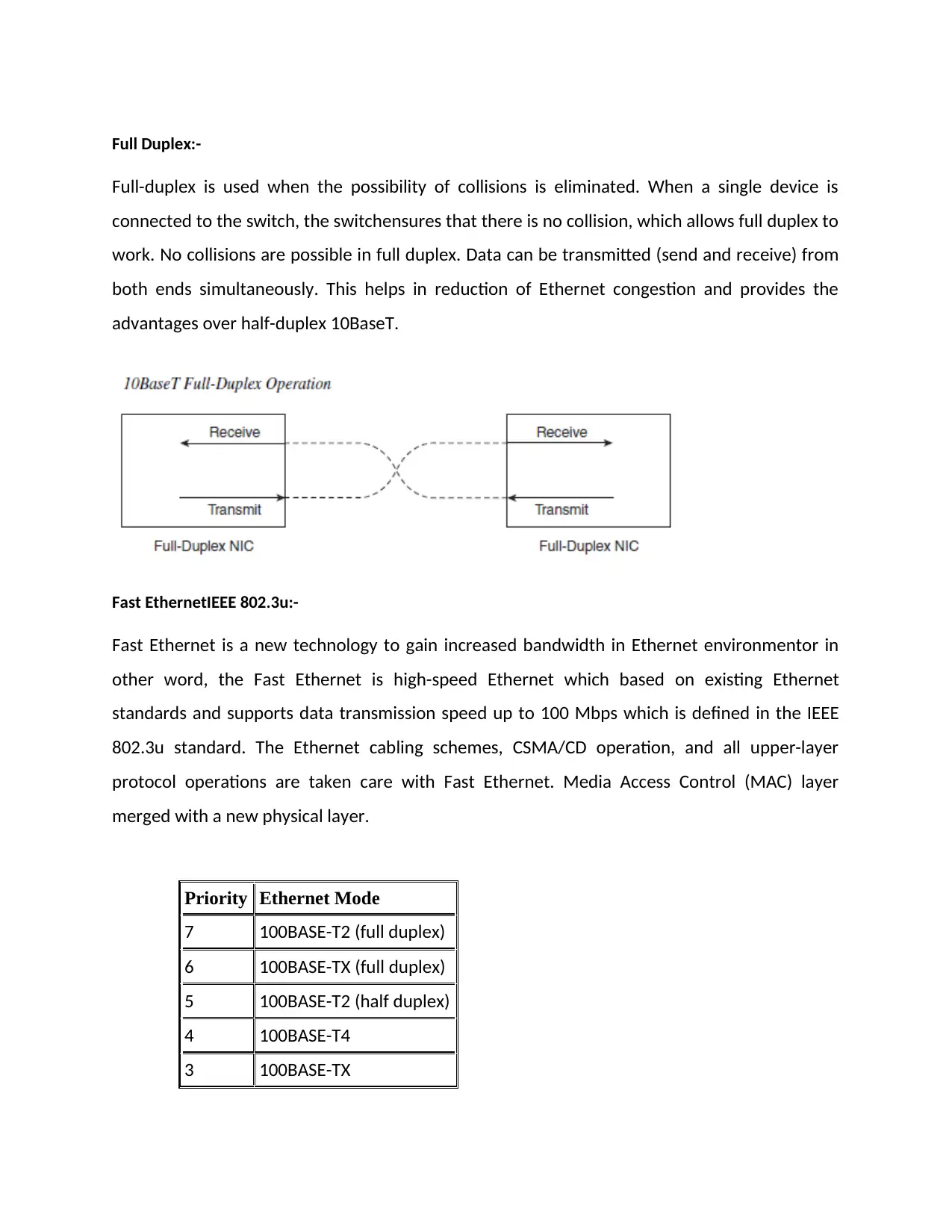
Full Duplex:-
Full-duplex is used when the possibility of collisions is eliminated. When a single device is
connected to the switch, the switchensures that there is no collision, which allows full duplex to
work. No collisions are possible in full duplex. Data can be transmitted (send and receive) from
both ends simultaneously. This helps in reduction of Ethernet congestion and provides the
advantages over half-duplex 10BaseT.
Fast EthernetIEEE 802.3u:-
Fast Ethernet is a new technology to gain increased bandwidth in Ethernet environmentor in
other word, the Fast Ethernet is high-speed Ethernet which based on existing Ethernet
standards and supports data transmission speed up to 100 Mbps which is defined in the IEEE
802.3u standard. The Ethernet cabling schemes, CSMA/CD operation, and all upper-layer
protocol operations are taken care with Fast Ethernet. Media Access Control (MAC) layer
merged with a new physical layer.
Priority Ethernet Mode
7 100BASE-T2 (full duplex)
6 100BASE-TX (full duplex)
5 100BASE-T2 (half duplex)
4 100BASE-T4
3 100BASE-TX
Full-duplex is used when the possibility of collisions is eliminated. When a single device is
connected to the switch, the switchensures that there is no collision, which allows full duplex to
work. No collisions are possible in full duplex. Data can be transmitted (send and receive) from
both ends simultaneously. This helps in reduction of Ethernet congestion and provides the
advantages over half-duplex 10BaseT.
Fast EthernetIEEE 802.3u:-
Fast Ethernet is a new technology to gain increased bandwidth in Ethernet environmentor in
other word, the Fast Ethernet is high-speed Ethernet which based on existing Ethernet
standards and supports data transmission speed up to 100 Mbps which is defined in the IEEE
802.3u standard. The Ethernet cabling schemes, CSMA/CD operation, and all upper-layer
protocol operations are taken care with Fast Ethernet. Media Access Control (MAC) layer
merged with a new physical layer.
Priority Ethernet Mode
7 100BASE-T2 (full duplex)
6 100BASE-TX (full duplex)
5 100BASE-T2 (half duplex)
4 100BASE-T4
3 100BASE-TX
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Priority Ethernet Mode
2 10BASE-T (full duplex)
1 10BASE-T
Gigabit Ethernet IEEE 802.3z or IEEE 802.3ab:-
Gigabit Ethernet is based on the IEEE 802.3ab and IEEE 802.3z standard and Gigabit Ethernet
issupports 1000 Mbps or 1 Gbps per port of network switch. The physical layer has been
modified to increase data-transmission speeds. Gigabit Ethernet can connect access-layer
switches to distribution-layer switches.
10-Gigabit EthernetIEEE 802.3ae:-
Gigabit Ethernet uses 1000BASE-X to indicate the media type, 10-Gigabit Ethernet uses
10GBASE-X. PMDs along with type of fiber and distance limitations are defined in the standard
which may vary in nature. All fiber-optic PMDs can be used as either a LAN or a WAN PHY,
except for the 10GBASE-LX4, which is only a PHY.
LAN Hardware
This segment covers the hardware or network devices of LAN and their categories based on OSI
model:
Repeaters
Repeaters are the elementary unit in the networks that connect singledivisions and accept
incomingframes or packet and then forwards frame to all other interfaces except receiving
port.Repeaters work at the OSI model’s physical layer. Repeaters are unaware of
datagram/packets or frame formats. They do not control broadcasts or collision domains.
2 10BASE-T (full duplex)
1 10BASE-T
Gigabit Ethernet IEEE 802.3z or IEEE 802.3ab:-
Gigabit Ethernet is based on the IEEE 802.3ab and IEEE 802.3z standard and Gigabit Ethernet
issupports 1000 Mbps or 1 Gbps per port of network switch. The physical layer has been
modified to increase data-transmission speeds. Gigabit Ethernet can connect access-layer
switches to distribution-layer switches.
10-Gigabit EthernetIEEE 802.3ae:-
Gigabit Ethernet uses 1000BASE-X to indicate the media type, 10-Gigabit Ethernet uses
10GBASE-X. PMDs along with type of fiber and distance limitations are defined in the standard
which may vary in nature. All fiber-optic PMDs can be used as either a LAN or a WAN PHY,
except for the 10GBASE-LX4, which is only a PHY.
LAN Hardware
This segment covers the hardware or network devices of LAN and their categories based on OSI
model:
Repeaters
Repeaters are the elementary unit in the networks that connect singledivisions and accept
incomingframes or packet and then forwards frame to all other interfaces except receiving
port.Repeaters work at the OSI model’s physical layer. Repeaters are unaware of
datagram/packets or frame formats. They do not control broadcasts or collision domains.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
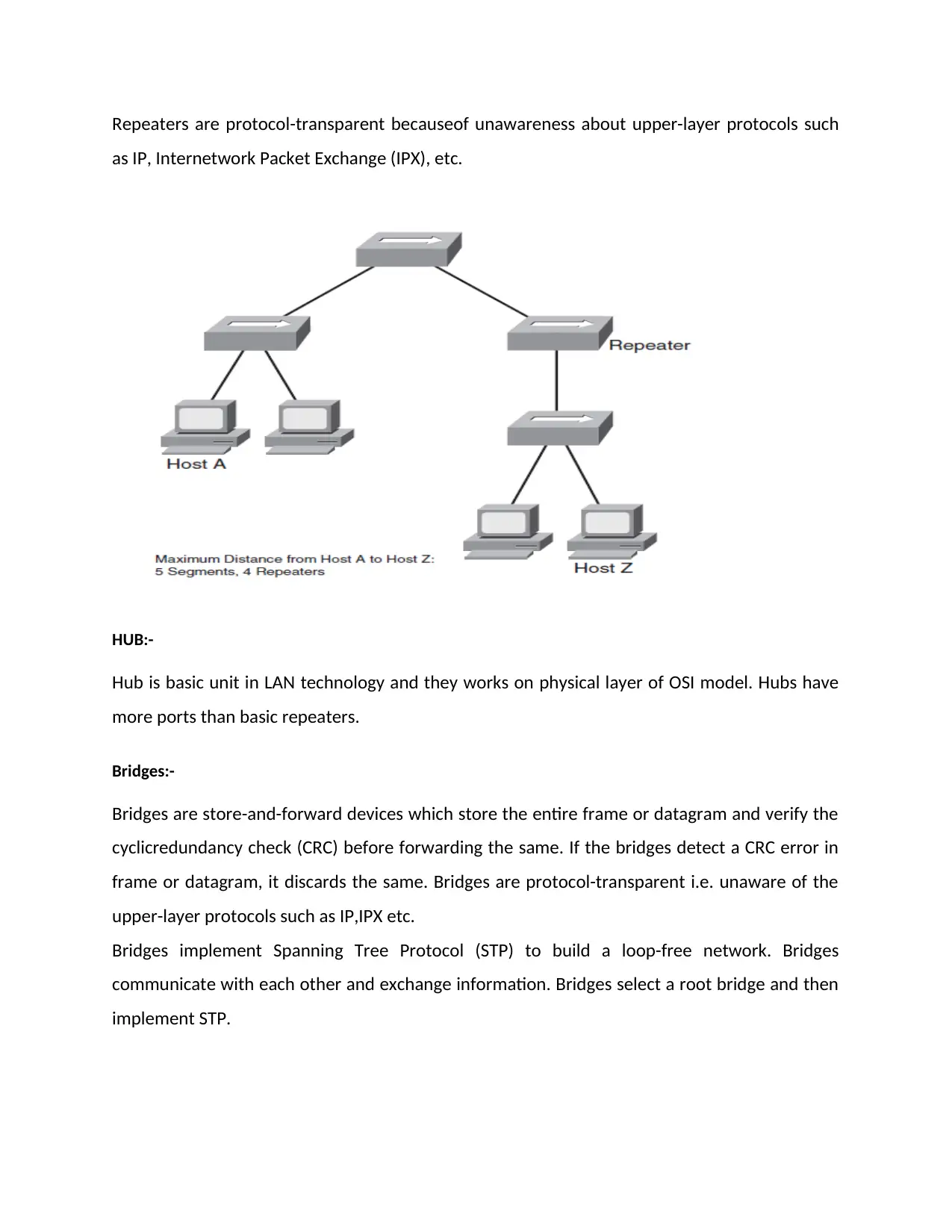
Repeaters are protocol-transparent becauseof unawareness about upper-layer protocols such
as IP, Internetwork Packet Exchange (IPX), etc.
HUB:-
Hub is basic unit in LAN technology and they works on physical layer of OSI model. Hubs have
more ports than basic repeaters.
Bridges:-
Bridges are store-and-forward devices which store the entire frame or datagram and verify the
cyclicredundancy check (CRC) before forwarding the same. If the bridges detect a CRC error in
frame or datagram, it discards the same. Bridges are protocol-transparent i.e. unaware of the
upper-layer protocols such as IP,IPX etc.
Bridges implement Spanning Tree Protocol (STP) to build a loop-free network. Bridges
communicate with each other and exchange information. Bridges select a root bridge and then
implement STP.
as IP, Internetwork Packet Exchange (IPX), etc.
HUB:-
Hub is basic unit in LAN technology and they works on physical layer of OSI model. Hubs have
more ports than basic repeaters.
Bridges:-
Bridges are store-and-forward devices which store the entire frame or datagram and verify the
cyclicredundancy check (CRC) before forwarding the same. If the bridges detect a CRC error in
frame or datagram, it discards the same. Bridges are protocol-transparent i.e. unaware of the
upper-layer protocols such as IP,IPX etc.
Bridges implement Spanning Tree Protocol (STP) to build a loop-free network. Bridges
communicate with each other and exchange information. Bridges select a root bridge and then
implement STP.
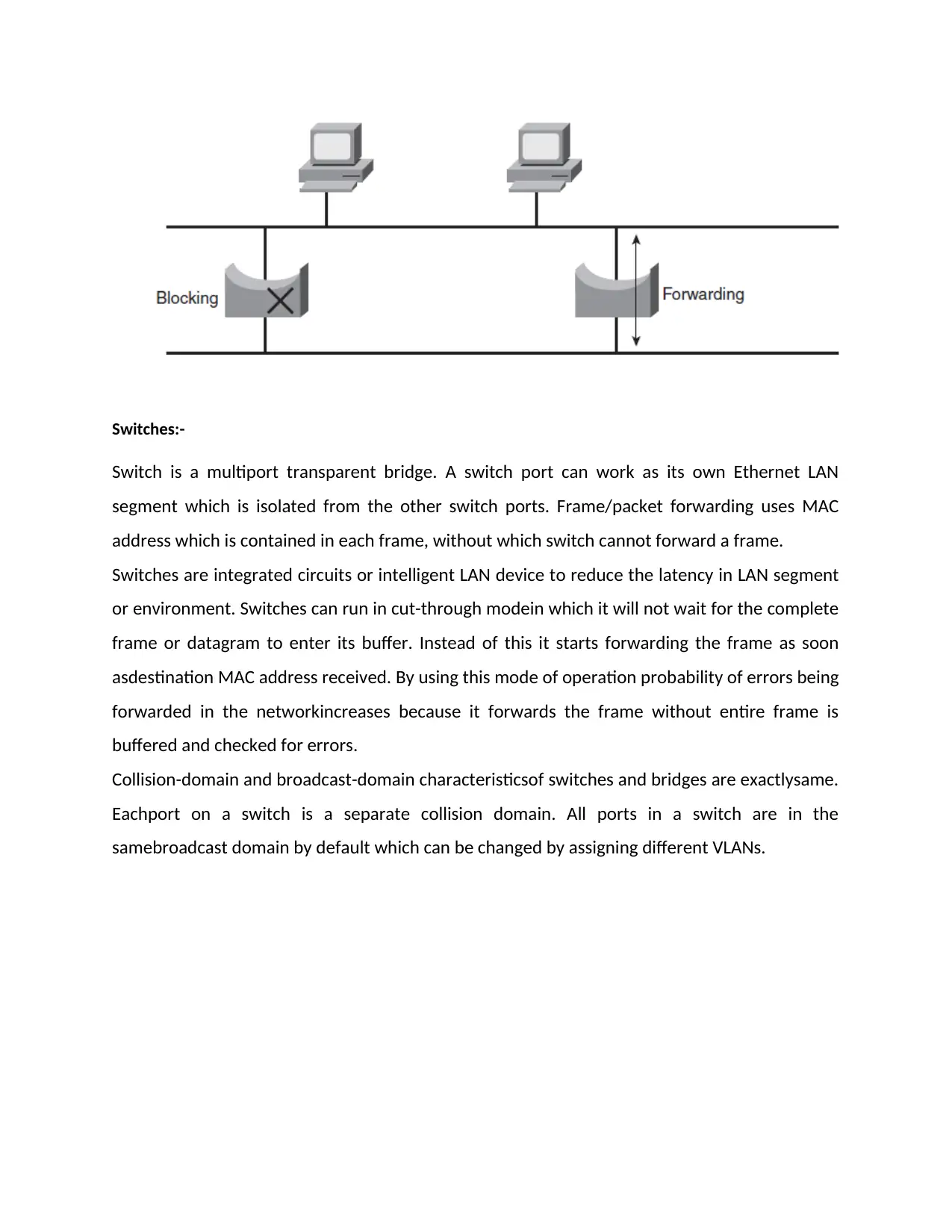
Switches:-
Switch is a multiport transparent bridge. A switch port can work as its own Ethernet LAN
segment which is isolated from the other switch ports. Frame/packet forwarding uses MAC
address which is contained in each frame, without which switch cannot forward a frame.
Switches are integrated circuits or intelligent LAN device to reduce the latency in LAN segment
or environment. Switches can run in cut-through modein which it will not wait for the complete
frame or datagram to enter its buffer. Instead of this it starts forwarding the frame as soon
asdestination MAC address received. By using this mode of operation probability of errors being
forwarded in the networkincreases because it forwards the frame without entire frame is
buffered and checked for errors.
Collision-domain and broadcast-domain characteristicsof switches and bridges are exactlysame.
Eachport on a switch is a separate collision domain. All ports in a switch are in the
samebroadcast domain by default which can be changed by assigning different VLANs.
Switch is a multiport transparent bridge. A switch port can work as its own Ethernet LAN
segment which is isolated from the other switch ports. Frame/packet forwarding uses MAC
address which is contained in each frame, without which switch cannot forward a frame.
Switches are integrated circuits or intelligent LAN device to reduce the latency in LAN segment
or environment. Switches can run in cut-through modein which it will not wait for the complete
frame or datagram to enter its buffer. Instead of this it starts forwarding the frame as soon
asdestination MAC address received. By using this mode of operation probability of errors being
forwarded in the networkincreases because it forwards the frame without entire frame is
buffered and checked for errors.
Collision-domain and broadcast-domain characteristicsof switches and bridges are exactlysame.
Eachport on a switch is a separate collision domain. All ports in a switch are in the
samebroadcast domain by default which can be changed by assigning different VLANs.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
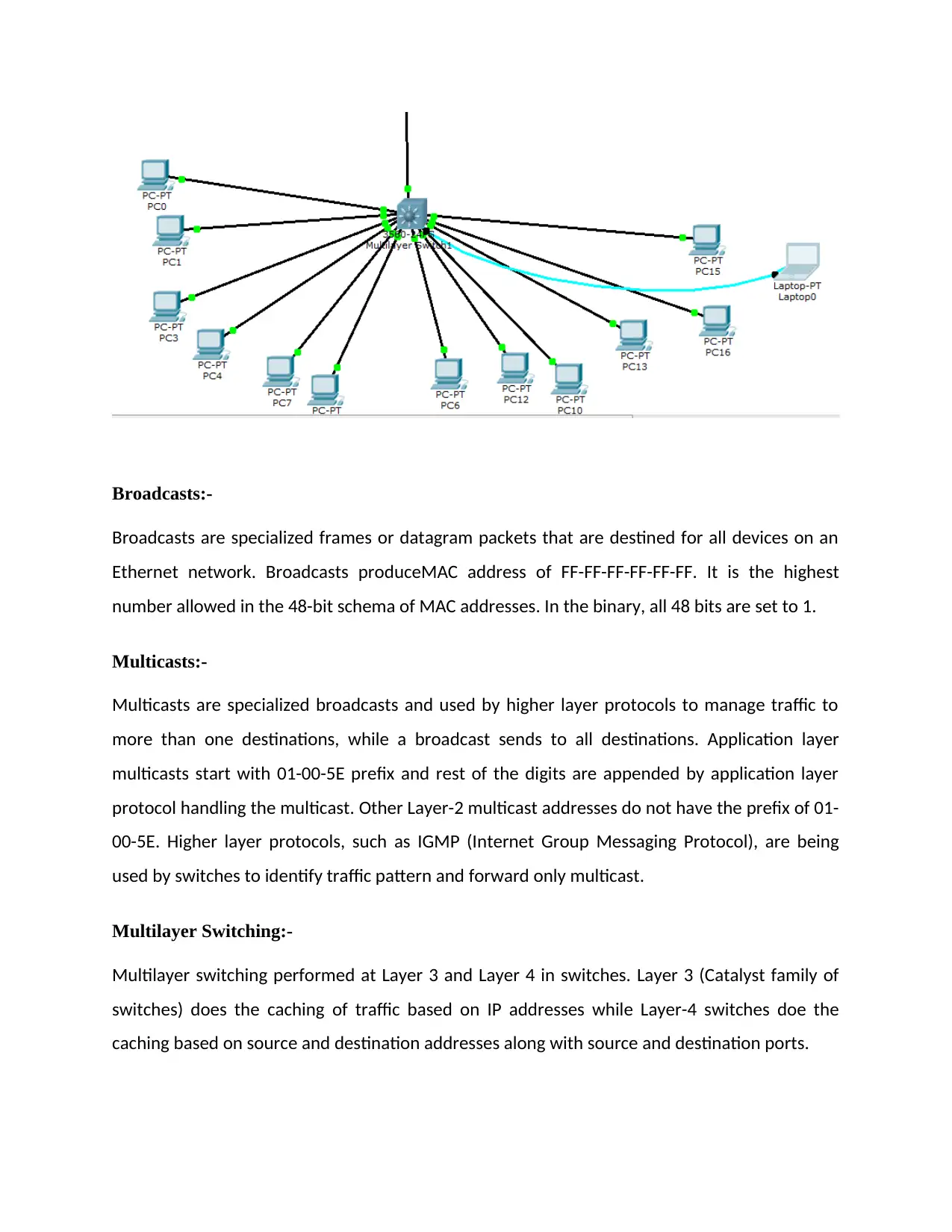
Broadcasts:-
Broadcasts are specialized frames or datagram packets that are destined for all devices on an
Ethernet network. Broadcasts produceMAC address of FF-FF-FF-FF-FF-FF. It is the highest
number allowed in the 48-bit schema of MAC addresses. In the binary, all 48 bits are set to 1.
Multicasts:-
Multicasts are specialized broadcasts and used by higher layer protocols to manage traffic to
more than one destinations, while a broadcast sends to all destinations. Application layer
multicasts start with 01-00-5E prefix and rest of the digits are appended by application layer
protocol handling the multicast. Other Layer-2 multicast addresses do not have the prefix of 01-
00-5E. Higher layer protocols, such as IGMP (Internet Group Messaging Protocol), are being
used by switches to identify traffic pattern and forward only multicast.
Multilayer Switching:-
Multilayer switching performed at Layer 3 and Layer 4 in switches. Layer 3 (Catalyst family of
switches) does the caching of traffic based on IP addresses while Layer-4 switches doe the
caching based on source and destination addresses along with source and destination ports.
Broadcasts are specialized frames or datagram packets that are destined for all devices on an
Ethernet network. Broadcasts produceMAC address of FF-FF-FF-FF-FF-FF. It is the highest
number allowed in the 48-bit schema of MAC addresses. In the binary, all 48 bits are set to 1.
Multicasts:-
Multicasts are specialized broadcasts and used by higher layer protocols to manage traffic to
more than one destinations, while a broadcast sends to all destinations. Application layer
multicasts start with 01-00-5E prefix and rest of the digits are appended by application layer
protocol handling the multicast. Other Layer-2 multicast addresses do not have the prefix of 01-
00-5E. Higher layer protocols, such as IGMP (Internet Group Messaging Protocol), are being
used by switches to identify traffic pattern and forward only multicast.
Multilayer Switching:-
Multilayer switching performed at Layer 3 and Layer 4 in switches. Layer 3 (Catalyst family of
switches) does the caching of traffic based on IP addresses while Layer-4 switches doe the
caching based on source and destination addresses along with source and destination ports.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Router:-
Logical addressing in network can be achieved with routers because network layer (Layer 3)
address can be used to uniquely identify a device in the network. Actual data/frame forwarding
happens at Layer 2 byusing address of devices. A method is used to associate a device's MAC
address (data link layer) with its IP address (network layer). A router has addresses from both
layers assigned to each of its interfaces which are connected to network.
LAN Topologies:-
Logical LAN topologies can be configured with equipment’s such as router or switch. There are
mainly 6 types of topologies:
1) Bus
2) Star
3) Ring
4) Mesh
5) Tree
6) Hybrid
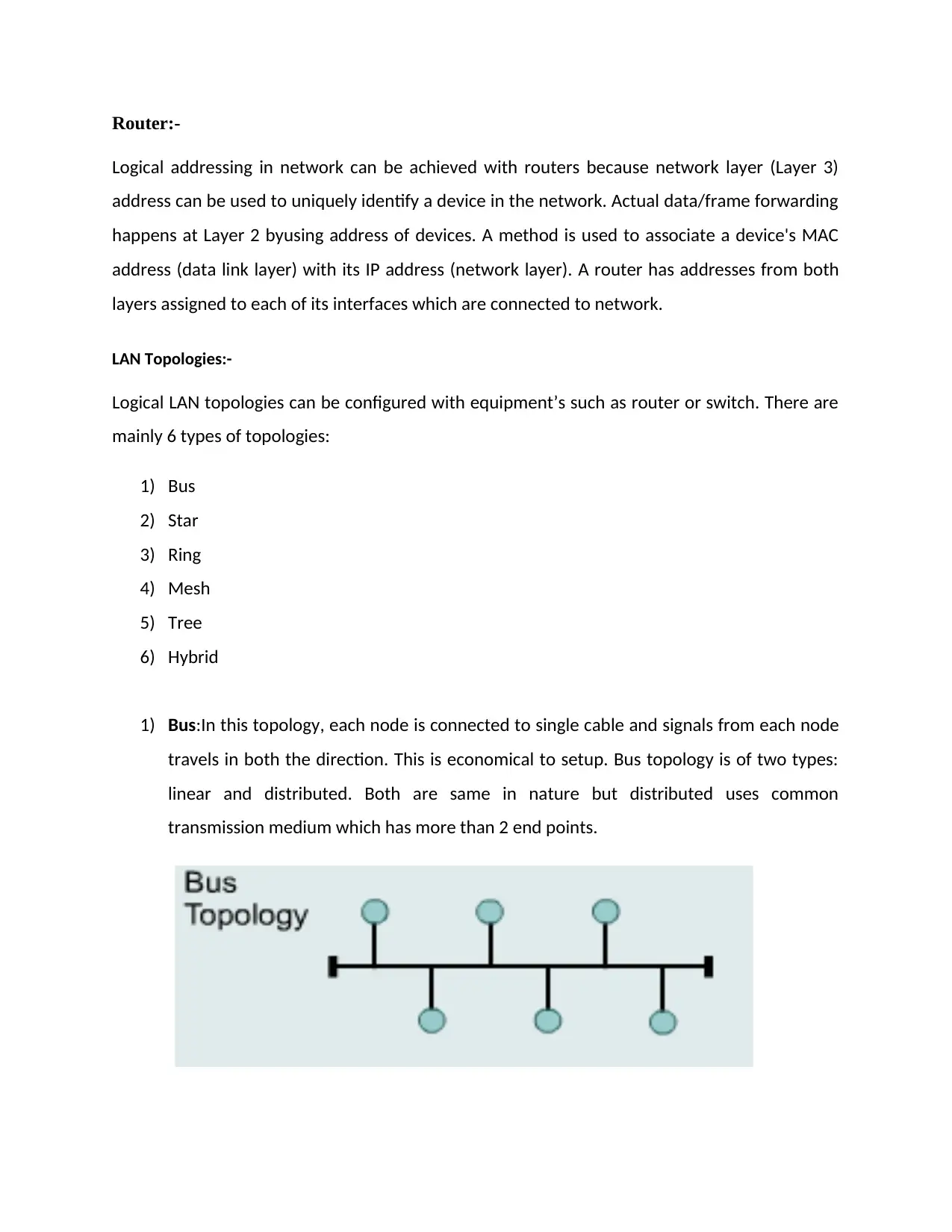
1) Bus:In this topology, each node is connected to single cable and signals from each node
travels in both the direction. This is economical to setup. Bus topology is of two types:
linear and distributed. Both are same in nature but distributed uses common
transmission medium which has more than 2 end points.
Logical addressing in network can be achieved with routers because network layer (Layer 3)
address can be used to uniquely identify a device in the network. Actual data/frame forwarding
happens at Layer 2 byusing address of devices. A method is used to associate a device's MAC
address (data link layer) with its IP address (network layer). A router has addresses from both
layers assigned to each of its interfaces which are connected to network.
LAN Topologies:-
Logical LAN topologies can be configured with equipment’s such as router or switch. There are
mainly 6 types of topologies:
1) Bus
2) Star
3) Ring
4) Mesh
5) Tree
6) Hybrid
1) Bus:In this topology, each node is connected to single cable and signals from each node
travels in both the direction. This is economical to setup. Bus topology is of two types:
linear and distributed. Both are same in nature but distributed uses common
transmission medium which has more than 2 end points.
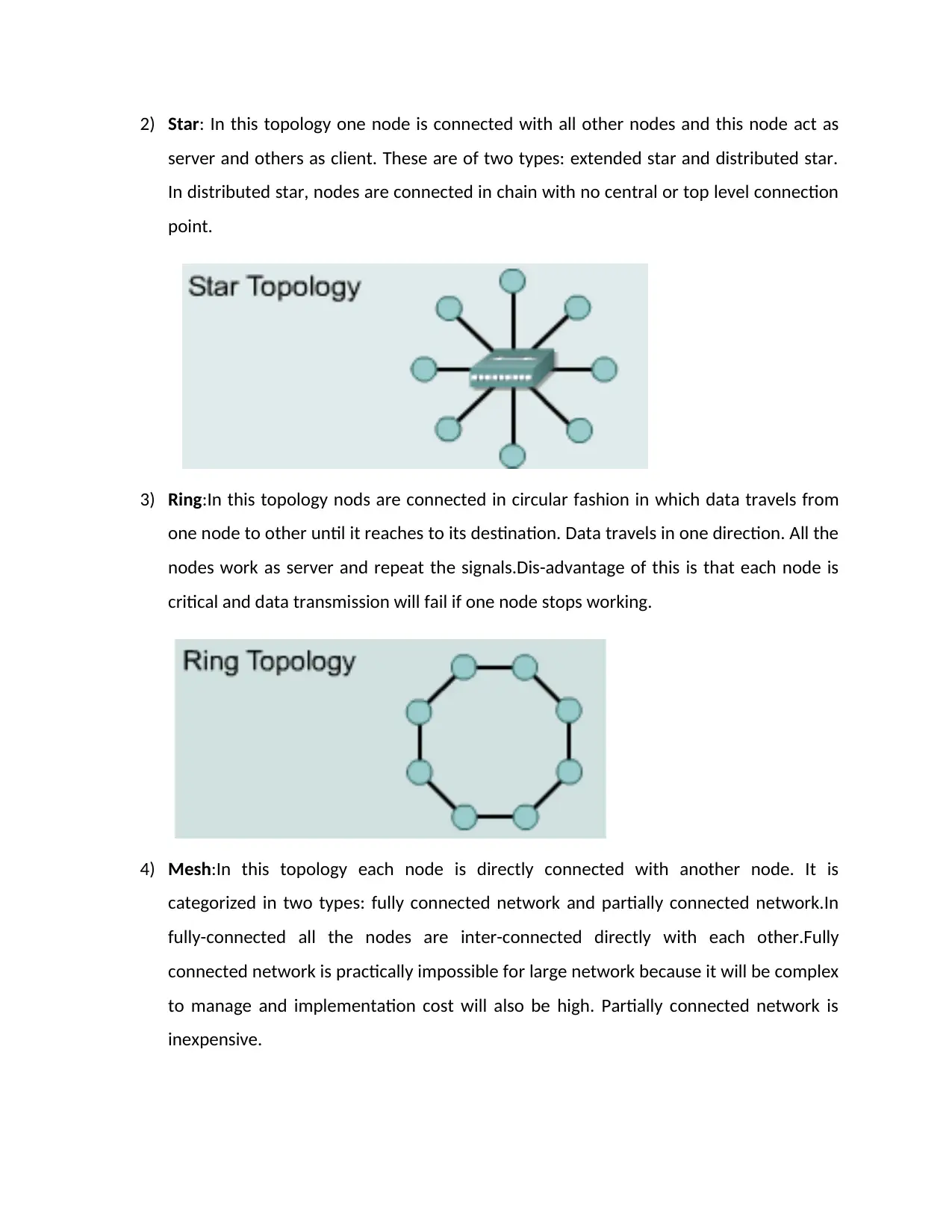
2) Star: In this topology one node is connected with all other nodes and this node act as
server and others as client. These are of two types: extended star and distributed star.
In distributed star, nodes are connected in chain with no central or top level connection
point.
3) Ring:In this topology nods are connected in circular fashion in which data travels from
one node to other until it reaches to its destination. Data travels in one direction. All the
nodes work as server and repeat the signals.Dis-advantage of this is that each node is
critical and data transmission will fail if one node stops working.
4) Mesh:In this topology each node is directly connected with another node. It is
categorized in two types: fully connected network and partially connected network.In
fully-connected all the nodes are inter-connected directly with each other.Fully
connected network is practically impossible for large network because it will be complex
to manage and implementation cost will also be high. Partially connected network is
inexpensive.
server and others as client. These are of two types: extended star and distributed star.
In distributed star, nodes are connected in chain with no central or top level connection
point.
3) Ring:In this topology nods are connected in circular fashion in which data travels from
one node to other until it reaches to its destination. Data travels in one direction. All the
nodes work as server and repeat the signals.Dis-advantage of this is that each node is
critical and data transmission will fail if one node stops working.
4) Mesh:In this topology each node is directly connected with another node. It is
categorized in two types: fully connected network and partially connected network.In
fully-connected all the nodes are inter-connected directly with each other.Fully
connected network is practically impossible for large network because it will be complex
to manage and implementation cost will also be high. Partially connected network is
inexpensive.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 50
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





