Detailed Report: LAN Technologies, Infrastructure, and Implementation
VerifiedAdded on 2024/05/29
|44
|4999
|454
Report
AI Summary
This report provides a detailed analysis of local area network (LAN) technologies, covering various topologies such as star, ring, bus, hybrid, and mesh, with a focus on hybrid topology due to its flexibility and scalability. It critically evaluates traffic-intensive services, network performance, and Quality of Service (QoS), emphasizing load sharing, deadlock prevention, and security constraints. The report discusses LAN concerns like security, performance, reliability, and efficiency, recommending a hierarchical network model to enhance security and performance. It includes a network infrastructure design fulfilling specific requirements, evaluates network components, and details the implementation of a LAN, including services and network security measures. Furthermore, it reviews and tests the LAN, discusses tools for monitoring and troubleshooting, addresses potential attacks and threats, and evaluates network performance, proposing solutions to improve server traffic. The document is available on Desklib, a platform offering study tools and resources for students.

Local Area Networking Technologies
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Introduction:....................................................................................................................................5
LO1: Understand the impact of LAN technologies.........................................................................6
1.1 With the aid of diagram (if applicable), critically evaluate different technologies/topologies
available in the market, establishing the most appropriate and suitable technology that can be
used in the above scenario?..........................................................................................................6
1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?.....................................................10
1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?..............12
LO2: Be able to design LAN infrastructures.................................................................................13
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]..........................................................................................13
2.2 Critically evaluate your network components and design, including [P2.2, M2]................15
LO3: Be able to implement LAN infrastructures..........................................................................17
3.1 Build and configure a LAN (including services) to meet a given requirement...................17
3.2 implement network security on a LAN................................................................................29
3.3 critically review and test a LAN (M3).................................................................................31
LO4: Be able to manage LAN infrastructures...............................................................................38
4.1 There are many tools available in the market to monitor the network, describe and choose
one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]...............38
4.2 Local Area Network is not immune from many attacks and threats produce a report to
improve security, reliability and performance. [P4.2]...............................................................39
4.3 Critically evaluate the performance of your network proposing a solution to improve
network performance in relation to server’s traffic. [P4.3, M3]................................................40
Introduction:....................................................................................................................................5
LO1: Understand the impact of LAN technologies.........................................................................6
1.1 With the aid of diagram (if applicable), critically evaluate different technologies/topologies
available in the market, establishing the most appropriate and suitable technology that can be
used in the above scenario?..........................................................................................................6
1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?.....................................................10
1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?..............12
LO2: Be able to design LAN infrastructures.................................................................................13
2.1 Design network infrastructure to fulfil the requirement of above scenario, your network
design guidance include: [P2.1, D2]..........................................................................................13
2.2 Critically evaluate your network components and design, including [P2.2, M2]................15
LO3: Be able to implement LAN infrastructures..........................................................................17
3.1 Build and configure a LAN (including services) to meet a given requirement...................17
3.2 implement network security on a LAN................................................................................29
3.3 critically review and test a LAN (M3).................................................................................31
LO4: Be able to manage LAN infrastructures...............................................................................38
4.1 There are many tools available in the market to monitor the network, describe and choose
one showing the usefulness of this tool to monitor and troubleshoot a LAN? [P4.1]...............38
4.2 Local Area Network is not immune from many attacks and threats produce a report to
improve security, reliability and performance. [P4.2]...............................................................39
4.3 Critically evaluate the performance of your network proposing a solution to improve
network performance in relation to server’s traffic. [P4.3, M3]................................................40

Conclusion.....................................................................................................................................41
Reference:......................................................................................................................................42
Appendix........................................................................................................................................44
List of figure:
Figure 1: Star...................................................................................................................................5
Figure 2: Ring..................................................................................................................................6
Figure 3: Bus....................................................................................................................................6
Figure 4: Hybrid or tree...................................................................................................................7
Figure 5: Mesh.................................................................................................................................7
Figure 6: Proposed Network..........................................................................................................13
Figure 7: Design View of network................................................................................................16
Figure 8: Metadata 1......................................................................................................................17
Figure 9 Metadata 2.......................................................................................................................18
Figure 10: Metadata 3....................................................................................................................19
Figure 11: Metadata 4...................................................................................................................20
Figure 12: Web server implementation.........................................................................................21
Figure 13: Implemented LAN network design..............................................................................21
Figure 14: DNS Configuration......................................................................................................22
Figure 15: DHCP Configuration....................................................................................................22
Figure 16: Switch Configuration 1................................................................................................23
Figure 17: Switch Configuration 2................................................................................................24
Figure 18: Switch Configuration 3................................................................................................25
Figure 19: Email service Implemented..........................................................................................25
Figure 20: FTP server....................................................................................................................26
Figure 21: SSH access on router from remote user.......................................................................26
Figure 22: VLAN configuration over switch.................................................................................27
Figure 23: ACL configuration over router.....................................................................................28
Figure 24: Router configuration....................................................................................................28
Reference:......................................................................................................................................42
Appendix........................................................................................................................................44
List of figure:
Figure 1: Star...................................................................................................................................5
Figure 2: Ring..................................................................................................................................6
Figure 3: Bus....................................................................................................................................6
Figure 4: Hybrid or tree...................................................................................................................7
Figure 5: Mesh.................................................................................................................................7
Figure 6: Proposed Network..........................................................................................................13
Figure 7: Design View of network................................................................................................16
Figure 8: Metadata 1......................................................................................................................17
Figure 9 Metadata 2.......................................................................................................................18
Figure 10: Metadata 3....................................................................................................................19
Figure 11: Metadata 4...................................................................................................................20
Figure 12: Web server implementation.........................................................................................21
Figure 13: Implemented LAN network design..............................................................................21
Figure 14: DNS Configuration......................................................................................................22
Figure 15: DHCP Configuration....................................................................................................22
Figure 16: Switch Configuration 1................................................................................................23
Figure 17: Switch Configuration 2................................................................................................24
Figure 18: Switch Configuration 3................................................................................................25
Figure 19: Email service Implemented..........................................................................................25
Figure 20: FTP server....................................................................................................................26
Figure 21: SSH access on router from remote user.......................................................................26
Figure 22: VLAN configuration over switch.................................................................................27
Figure 23: ACL configuration over router.....................................................................................28
Figure 24: Router configuration....................................................................................................28
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Figure 25: Test Plan 1....................................................................................................................30
Figure 26: Test Plan 2....................................................................................................................31
Figure 27: Test Plan 3...................................................................................................................31
Figure 28: Test Plan 4....................................................................................................................32
Figure 29: Test Plan 5....................................................................................................................32
Figure 30: Test Plan 6....................................................................................................................33
Figure 31: Test Plan 7....................................................................................................................33
Figure 32: Test Plan 8....................................................................................................................34
Figure 33: Test Plan 9....................................................................................................................34
Figure 34: Test Plan 10..................................................................................................................35
Figure 26: Test Plan 2....................................................................................................................31
Figure 27: Test Plan 3...................................................................................................................31
Figure 28: Test Plan 4....................................................................................................................32
Figure 29: Test Plan 5....................................................................................................................32
Figure 30: Test Plan 6....................................................................................................................33
Figure 31: Test Plan 7....................................................................................................................33
Figure 32: Test Plan 8....................................................................................................................34
Figure 33: Test Plan 9....................................................................................................................34
Figure 34: Test Plan 10..................................................................................................................35
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Introduction:
LAN mentioned to as Local Area Network. It covered small geographical area for the Network
that gives their facility in the university, college, small agency, workplace, or company.
Documents and assets are mutual at the LAN for the communication. The organization has
wanted a community so that it will deliver connectivity to their staff and place of business. Here,
I should scheme the LAN for the organization. There are 4 elements in the assignments.
The first part of the file will supply a reason for LAN network with the wi-fi and stressed out the
community. Then, the VLAN, device of LAN community, intensive services of traffic, and cable
will be described that beneficial for the Given LAN Network. design Network could be planned
in line with enterprise agency requirements and might be anticipated of the device inside the
second component. LAN Network may be carried out and configured inside the third elements.
There may be a communication approximately the network safety after which trying out of the
connection of community is executed. Troubleshooting and Monitoring procedure might be well-
defined and can be solved protection, reliability, and performance concerns inside the fourth
elements.
LAN mentioned to as Local Area Network. It covered small geographical area for the Network
that gives their facility in the university, college, small agency, workplace, or company.
Documents and assets are mutual at the LAN for the communication. The organization has
wanted a community so that it will deliver connectivity to their staff and place of business. Here,
I should scheme the LAN for the organization. There are 4 elements in the assignments.
The first part of the file will supply a reason for LAN network with the wi-fi and stressed out the
community. Then, the VLAN, device of LAN community, intensive services of traffic, and cable
will be described that beneficial for the Given LAN Network. design Network could be planned
in line with enterprise agency requirements and might be anticipated of the device inside the
second component. LAN Network may be carried out and configured inside the third elements.
There may be a communication approximately the network safety after which trying out of the
connection of community is executed. Troubleshooting and Monitoring procedure might be well-
defined and can be solved protection, reliability, and performance concerns inside the fourth
elements.
LO1: Understand the impact of LAN technologies
1.1 With the aid of diagram (if applicable), critically evaluate different
technologies/topologies available in the market, establishing the most appropriate and
suitable technology that can be used in the above scenario?
Ans. Different type of topologies are:
Star (Stub)
Ring
Bus
Hybrid
Mesh
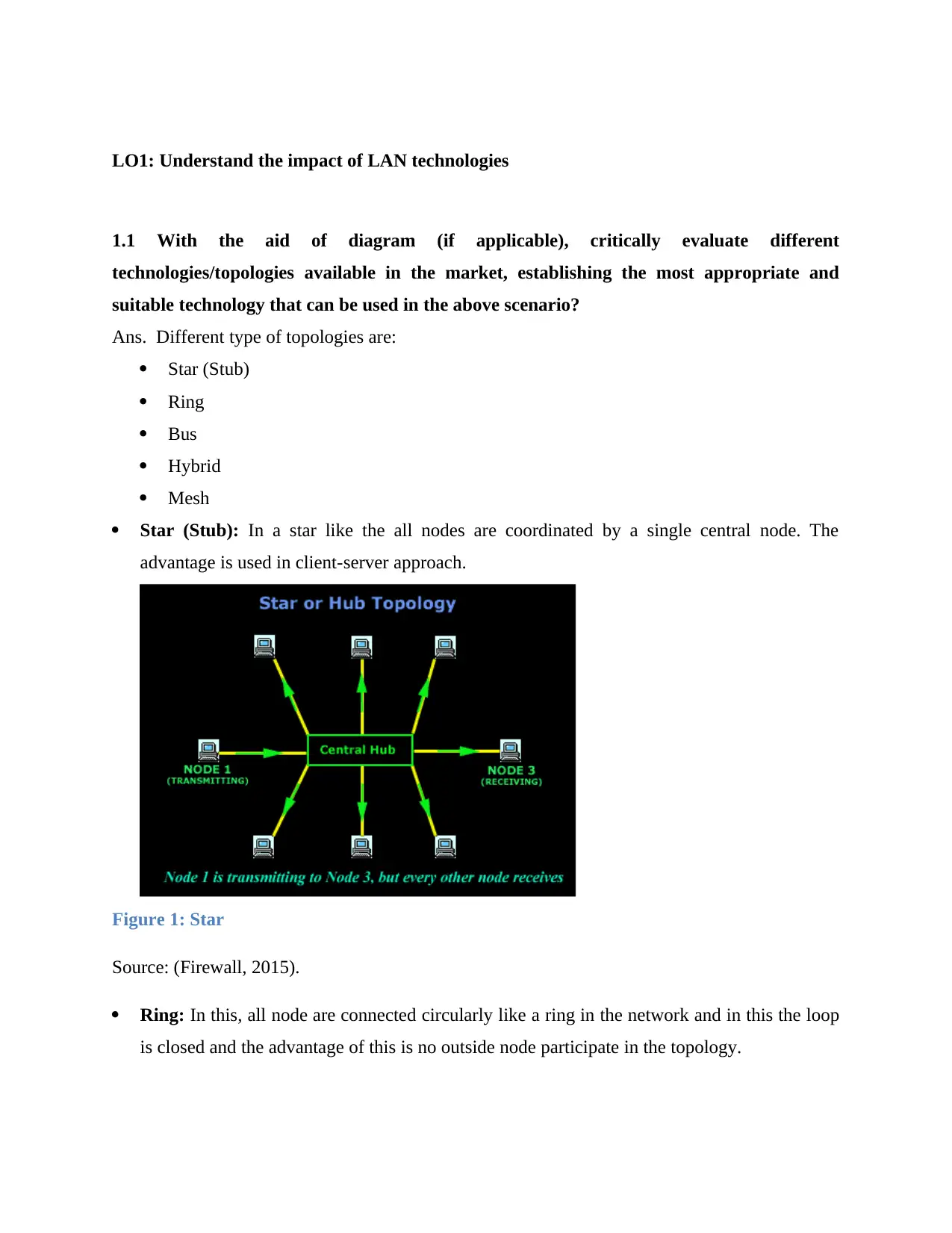
Star (Stub): In a star like the all nodes are coordinated by a single central node. The
advantage is used in client-server approach.
Figure 1: Star
Source: (Firewall, 2015).
Ring: In this, all node are connected circularly like a ring in the network and in this the loop
is closed and the advantage of this is no outside node participate in the topology.
1.1 With the aid of diagram (if applicable), critically evaluate different
technologies/topologies available in the market, establishing the most appropriate and
suitable technology that can be used in the above scenario?
Ans. Different type of topologies are:
Star (Stub)
Ring
Bus
Hybrid
Mesh
Star (Stub): In a star like the all nodes are coordinated by a single central node. The
advantage is used in client-server approach.
Figure 1: Star
Source: (Firewall, 2015).
Ring: In this, all node are connected circularly like a ring in the network and in this the loop
is closed and the advantage of this is no outside node participate in the topology.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
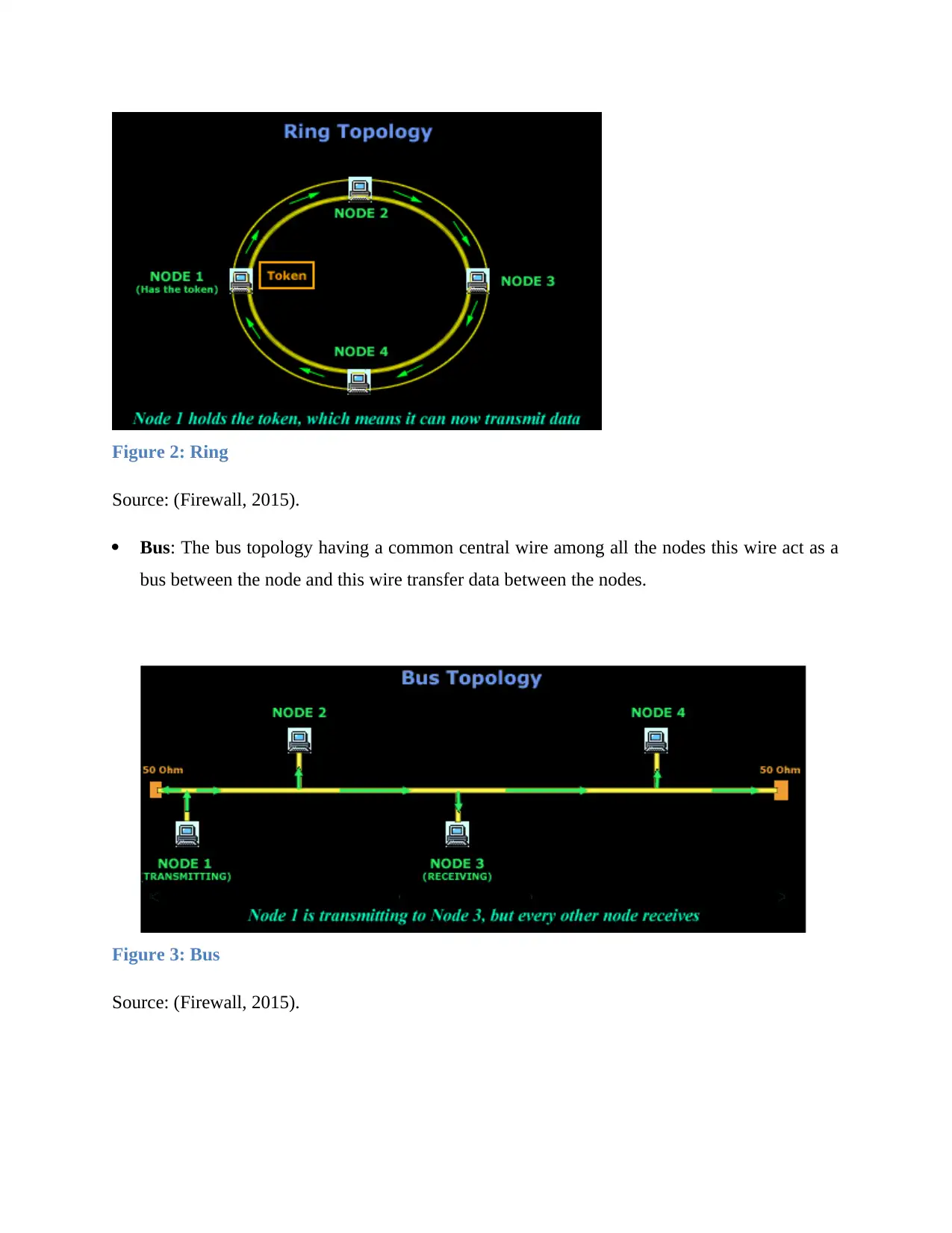
Figure 2: Ring
Source: (Firewall, 2015).
Bus: The bus topology having a common central wire among all the nodes this wire act as a
bus between the node and this wire transfer data between the nodes.
Figure 3: Bus
Source: (Firewall, 2015).
Source: (Firewall, 2015).
Bus: The bus topology having a common central wire among all the nodes this wire act as a
bus between the node and this wire transfer data between the nodes.
Figure 3: Bus
Source: (Firewall, 2015).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
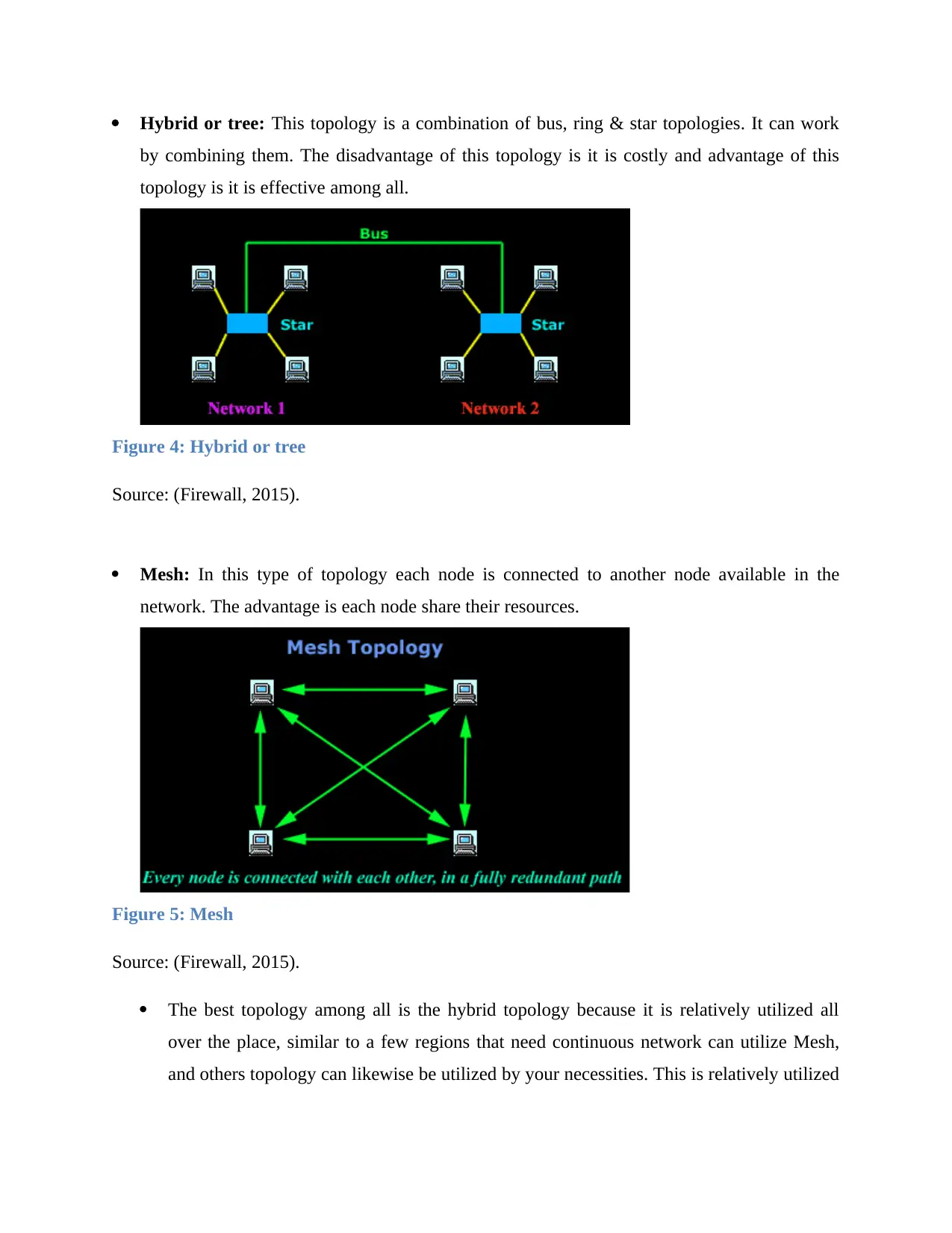
Hybrid or tree: This topology is a combination of bus, ring & star topologies. It can work
by combining them. The disadvantage of this topology is it is costly and advantage of this
topology is it is effective among all.
Figure 4: Hybrid or tree
Source: (Firewall, 2015).
Mesh: In this type of topology each node is connected to another node available in the
network. The advantage is each node share their resources.
Figure 5: Mesh
Source: (Firewall, 2015).
The best topology among all is the hybrid topology because it is relatively utilized all
over the place, similar to a few regions that need continuous network can utilize Mesh,
and others topology can likewise be utilized by your necessities. This is relatively utilized
by combining them. The disadvantage of this topology is it is costly and advantage of this
topology is it is effective among all.
Figure 4: Hybrid or tree
Source: (Firewall, 2015).
Mesh: In this type of topology each node is connected to another node available in the
network. The advantage is each node share their resources.
Figure 5: Mesh
Source: (Firewall, 2015).
The best topology among all is the hybrid topology because it is relatively utilized all
over the place, similar to a few regions that need continuous network can utilize Mesh,
and others topology can likewise be utilized by your necessities. This is relatively utilized

all around, similar to a few zones that need continuous network can utilize Mesh, and
others topology can likewise be utilized by your necessities (Differencebetween, 2018).
others topology can likewise be utilized by your necessities (Differencebetween, 2018).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

1.2 Local Area Networks need to be robust both at the level of availability and quality of
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?
Ans. The LAN should provide robustness among the network components because at any time
when any system fails then it should not stop working. Other components in the network may
work. Like in a road at a time from a road only 150 vehicle are use the road if the limit exceeds
then it should break the network due to this the availability for the vehicle may not achieve so
when this problem strike in the network the other path may be started which serves them.
Another example of robust is at a time one server accepts request up to certain limit when it
reaches the other server start receiving a request from client side so at one server no load is
provided. By this, the system QoS is achieved by available the resources to each and every
component which require them without the deadlock in the network. The exchange press and
merchant publicizing have a tendency to underline transmission speed instead of what truly
checks and that is the strength of the remote associations, all things considered, conditions. In the
lab, the transmission speed is estimated under perfect conditions e.g. a coordinated association
and no obstruction.
Several features which improve the QoS in the LAN are:
It should have the feature of load sharing and load balancing.
It does not provide any deadlock with high priority component cannot wait long for a
resource which should be utilized by another component in the network.
It should be transferable in case of failure.
Security constraints may be used to provide flexibility among the components in the local
area network.
In the LAN only authenticated a user can access a resource by successful authorization.
It should always flexible in terms of topology requirement in the network because at any
time any requirement may adopt new features so it should use best to reduce cost and
always available serves in the network.
Power should be effectively utilized by each and every component in the local area
network.
service, critically analyses traffic intensive services of network performance and Quality of
Services (QoS) providing some example of applicable use?
Ans. The LAN should provide robustness among the network components because at any time
when any system fails then it should not stop working. Other components in the network may
work. Like in a road at a time from a road only 150 vehicle are use the road if the limit exceeds
then it should break the network due to this the availability for the vehicle may not achieve so
when this problem strike in the network the other path may be started which serves them.
Another example of robust is at a time one server accepts request up to certain limit when it
reaches the other server start receiving a request from client side so at one server no load is
provided. By this, the system QoS is achieved by available the resources to each and every
component which require them without the deadlock in the network. The exchange press and
merchant publicizing have a tendency to underline transmission speed instead of what truly
checks and that is the strength of the remote associations, all things considered, conditions. In the
lab, the transmission speed is estimated under perfect conditions e.g. a coordinated association
and no obstruction.
Several features which improve the QoS in the LAN are:
It should have the feature of load sharing and load balancing.
It does not provide any deadlock with high priority component cannot wait long for a
resource which should be utilized by another component in the network.
It should be transferable in case of failure.
Security constraints may be used to provide flexibility among the components in the local
area network.
In the LAN only authenticated a user can access a resource by successful authorization.
It should always flexible in terms of topology requirement in the network because at any
time any requirement may adopt new features so it should use best to reduce cost and
always available serves in the network.
Power should be effectively utilized by each and every component in the local area
network.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Each component may serve in specific time domain no component may be waiting for an
infinitely long time because it can degrade the performance of the network.
A node may follow both encryption and decryption process in the network because for
one node act as a client for other served as a server in the network.
LAN should provide smart access to resources in a round robin network and the resources
available on the network should be transferable and various replications are provided of
the resources at various places (Slattery,2013).
infinitely long time because it can degrade the performance of the network.
A node may follow both encryption and decryption process in the network because for
one node act as a client for other served as a server in the network.
LAN should provide smart access to resources in a round robin network and the resources
available on the network should be transferable and various replications are provided of
the resources at various places (Slattery,2013).

1.3 Discuss & evaluate Local Area Network concerns and make recommendations showing
how a hierarchal network model can improve security, reliability and performance?
Ans. Local area network several issues are faced by clients and server. Some of them are:
Security
Performance
Efficiency
Reliability
Authenticity
Failure Handling or fixing
Utilization
Utilization of failed (or no) remote encryption. Trust it or not, numerous ventures still utilize
WEP encryption to "secure" their systems. As I specified in a before the article, WEP
encryption is on a very basic level defective and ought to never be depended upon to secure a
remote system. Utilize WPA encryption.
Efficiency can be achieved by distributing the load or divide the network into several levels.
Only the authenticated user can use the LAN and after successful authorization they provide
access.
LAN should always provide performance among the entire user by load sharing and balance.
Encryption is used so no attacker attacks on the network areas.
The hierarchal network should be very useful at several places where we want security,
performance and reliability because it can separate the network into the various level of
hierarchy so that each hierarchy provide the separate security features needed in the network.
Like an organization, each employee has a different set of power so we provide access according
to that same as we do in a hierarchical network. So by this security is improved in between the
nodes (Ubiquiti, 2017).
The load is shared among different network so when high load on network strike then
performance cannot be degraded or at any time any system in the network fail it does not affect
the other network component. So by this, the reliability of components in the network can be
achieved.
how a hierarchal network model can improve security, reliability and performance?
Ans. Local area network several issues are faced by clients and server. Some of them are:
Security
Performance
Efficiency
Reliability
Authenticity
Failure Handling or fixing
Utilization
Utilization of failed (or no) remote encryption. Trust it or not, numerous ventures still utilize
WEP encryption to "secure" their systems. As I specified in a before the article, WEP
encryption is on a very basic level defective and ought to never be depended upon to secure a
remote system. Utilize WPA encryption.
Efficiency can be achieved by distributing the load or divide the network into several levels.
Only the authenticated user can use the LAN and after successful authorization they provide
access.
LAN should always provide performance among the entire user by load sharing and balance.
Encryption is used so no attacker attacks on the network areas.
The hierarchal network should be very useful at several places where we want security,
performance and reliability because it can separate the network into the various level of
hierarchy so that each hierarchy provide the separate security features needed in the network.
Like an organization, each employee has a different set of power so we provide access according
to that same as we do in a hierarchical network. So by this security is improved in between the
nodes (Ubiquiti, 2017).
The load is shared among different network so when high load on network strike then
performance cannot be degraded or at any time any system in the network fail it does not affect
the other network component. So by this, the reliability of components in the network can be
achieved.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 44
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





