University Project: LDAP Installation and Configuration (CIS114-6)
VerifiedAdded on 2022/09/21
|31
|3444
|26
Project
AI Summary
This document presents a comprehensive project on installing and configuring LDAP (Lightweight Directory Access Protocol) on a Linux server. The project encompasses a detailed walkthrough of the installation process, including the necessary package installations like OpenLDAP, and the configuration of both the server and client components. It further elaborates on the creation of a specific LDAP infrastructure, including the setup of organizational units and user groups such as Admin, ICT, and Management, along with the addition of individual users (User01, User02, User03) and their respective group memberships. The document also covers the installation of PHPMyAdmin for web-based administration, and the use of services like slapd, slurpd, and smartd. The provided document is a practical guide for anyone looking to implement and manage an LDAP directory service within a network environment.

Network Systems and Administration 1
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Systems and Administration 2
Table of Contents
Introduction................................................................................................................................................3
Installation and configuration of LDAP..................................................................................................4
Working of LDAP..................................................................................................................................5
Uses of LDAP........................................................................................................................................5
Installing LDAP.....................................................................................................................................6
Infrastructure............................................................................................................................................13
Adding Groups.....................................................................................................................................13
Adding organizational Units................................................................................................................16
Adding users........................................................................................................................................16
Service control.....................................................................................................................................19
Wireshark installation..............................................................................................................................24
Conclusion...............................................................................................................................................29
References................................................................................................................................................30
Table of Contents
Introduction................................................................................................................................................3
Installation and configuration of LDAP..................................................................................................4
Working of LDAP..................................................................................................................................5
Uses of LDAP........................................................................................................................................5
Installing LDAP.....................................................................................................................................6
Infrastructure............................................................................................................................................13
Adding Groups.....................................................................................................................................13
Adding organizational Units................................................................................................................16
Adding users........................................................................................................................................16
Service control.....................................................................................................................................19
Wireshark installation..............................................................................................................................24
Conclusion...............................................................................................................................................29
References................................................................................................................................................30

Network Systems and Administration 3
Introduction
Network management is the process of installing and configuring a network system. The process of
administering and monitoring the use of a certain type of network architecture can be also be termed as
the process of network administration. For instance, the users of a certain type of network ecosystem
can be monitored and managed by the network management team. Some of the services which are
provided by this concept include provisioning and maintaining the quality of the service.
A network management software is a type of an application system which is used to administer and
deliver the services to the users. Network administrators are able to maintain the operation of the
network and the types of services used by the networks by using the software tools.
The principles and the strategies used in the evaluation and implementation of a network system can be
used to determine the effectiveness in the delivery of the services to the users.
The implementation of a network system requires a set of rules which are used to manage and prevent
unauthorized access. Network security is an important aspect which is used to control and maintain
authorized access to the resources and the integrity of the system. For instance, access to data and
information within a network requires a set of privileges which are administered by the network
administrator (Cordray, Chart, and Ginter, SCIENCELOGIC, 2015).
A network infrastructure consists of the users of the system, administrators and the managers who have
the sole responsibility of monitoring and limiting access of the network to unauthorized users. Network
solutions are the methodologies which are utilized and installed into the existing architecture to ensure
that the network performance is at optimal and the principles underlying the usage of the network are
not tempered with.
Emerging trends in the use of the network are used to bring about new solutions which are used to
protect the network architecture. New installations into the network should be implemented to ensure
that security mechanisms and procedures are not provoked in an attempt to manipulate the network
architecture. If for instance, a user is able to gain unauthorized access to data and the information in the
Introduction
Network management is the process of installing and configuring a network system. The process of
administering and monitoring the use of a certain type of network architecture can be also be termed as
the process of network administration. For instance, the users of a certain type of network ecosystem
can be monitored and managed by the network management team. Some of the services which are
provided by this concept include provisioning and maintaining the quality of the service.
A network management software is a type of an application system which is used to administer and
deliver the services to the users. Network administrators are able to maintain the operation of the
network and the types of services used by the networks by using the software tools.
The principles and the strategies used in the evaluation and implementation of a network system can be
used to determine the effectiveness in the delivery of the services to the users.
The implementation of a network system requires a set of rules which are used to manage and prevent
unauthorized access. Network security is an important aspect which is used to control and maintain
authorized access to the resources and the integrity of the system. For instance, access to data and
information within a network requires a set of privileges which are administered by the network
administrator (Cordray, Chart, and Ginter, SCIENCELOGIC, 2015).
A network infrastructure consists of the users of the system, administrators and the managers who have
the sole responsibility of monitoring and limiting access of the network to unauthorized users. Network
solutions are the methodologies which are utilized and installed into the existing architecture to ensure
that the network performance is at optimal and the principles underlying the usage of the network are
not tempered with.
Emerging trends in the use of the network are used to bring about new solutions which are used to
protect the network architecture. New installations into the network should be implemented to ensure
that security mechanisms and procedures are not provoked in an attempt to manipulate the network
architecture. If for instance, a user is able to gain unauthorized access to data and the information in the
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

Network Systems and Administration 4
system, then the administrators and the managers of the network system should identify the attack and
prevent it from happening.
The main purpose of this document is to set up and configure the installation of LDAP which is used by
the clients for utility performance.
Installation and configuration of LDAP
LDAP (lightweight directory access protocol ) is an implementation of a protocol which is used in the
management and control of information through a hierarchical model using files and directories. LDAP
is able to function in the same way, a relational database works, through storage of information from a
central location and access of the information at another endpoint.
A database performs its functions just in the same way a relational database does. For instance, storage
of files and information which can be accessed from a different location. Directories can be used to
store different types of information, access can be restricted using the strict requirements of the creator.
Some of the directories are created in the instance of a local user and are therefore limited to be
accessed. Information in a directory can be synchronized and normalized to increase the response time
of providing the information to the user and prevent redundancy in the available data.
Several directories which contain the same information can be synchronized together to form an
integral part of information storage which can then be easily accessed.
system, then the administrators and the managers of the network system should identify the attack and
prevent it from happening.
The main purpose of this document is to set up and configure the installation of LDAP which is used by
the clients for utility performance.
Installation and configuration of LDAP
LDAP (lightweight directory access protocol ) is an implementation of a protocol which is used in the
management and control of information through a hierarchical model using files and directories. LDAP
is able to function in the same way, a relational database works, through storage of information from a
central location and access of the information at another endpoint.
A database performs its functions just in the same way a relational database does. For instance, storage
of files and information which can be accessed from a different location. Directories can be used to
store different types of information, access can be restricted using the strict requirements of the creator.
Some of the directories are created in the instance of a local user and are therefore limited to be
accessed. Information in a directory can be synchronized and normalized to increase the response time
of providing the information to the user and prevent redundancy in the available data.
Several directories which contain the same information can be synchronized together to form an
integral part of information storage which can then be easily accessed.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Network Systems and Administration 5
Working of LDAP
The operation of LDAP and it’s services is based on a client-server model. An LDAP directory consists
of the LDAP servers which are configured together and contain the data. The servers can then form a
block unit which can be called the LDAP backend database which acts as a source of information. The
client is also able to connect to the server. This means that the client must be configured to operate in
such a way that it can contact and get connected to the server. Once the client is connected to the server,
then information and data access are possible (Vazquez, 2019).
Once the client has contacted the server with a question, the server is then able to respond with a
pointer to a location where the information can be obtained. The client then is able to follow to the
location where the information is stored, and once the client has access, information retrieval is carried
out.
An important feature with the LDAP is that one server can be able to reference the same directory entry
just like another server would. The servers are able to traverse and access the directories in the same
way. This provides ease with access to the directories.The LDAP server contains a daemon called slapd
which is used to support different kinds of database backends which are meant to be used by clients.
Uses of LDAP
Storage of files – LDAP is an important service which is used for storage of information and the
data. The data stored in an LDAP server can then be accessed by a client. LDAP performs its
operations just like any known database service which is used to store information for later
access. The clients must be authenticated before they can access the data from the LDAP
directories. Some of the data is only limited to certain users only.
Storage of DNS records.
Authenticating the user to certain services.
Working of LDAP
The operation of LDAP and it’s services is based on a client-server model. An LDAP directory consists
of the LDAP servers which are configured together and contain the data. The servers can then form a
block unit which can be called the LDAP backend database which acts as a source of information. The
client is also able to connect to the server. This means that the client must be configured to operate in
such a way that it can contact and get connected to the server. Once the client is connected to the server,
then information and data access are possible (Vazquez, 2019).
Once the client has contacted the server with a question, the server is then able to respond with a
pointer to a location where the information can be obtained. The client then is able to follow to the
location where the information is stored, and once the client has access, information retrieval is carried
out.
An important feature with the LDAP is that one server can be able to reference the same directory entry
just like another server would. The servers are able to traverse and access the directories in the same
way. This provides ease with access to the directories.The LDAP server contains a daemon called slapd
which is used to support different kinds of database backends which are meant to be used by clients.
Uses of LDAP
Storage of files – LDAP is an important service which is used for storage of information and the
data. The data stored in an LDAP server can then be accessed by a client. LDAP performs its
operations just like any known database service which is used to store information for later
access. The clients must be authenticated before they can access the data from the LDAP
directories. Some of the data is only limited to certain users only.
Storage of DNS records.
Authenticating the user to certain services.
Network Systems and Administration 6
Installing LDAP
The installation of LDAP requires prior installation of the following packages.
Openldap – a package used to configure both the clients and the server. For instance, the
communication between the clients and the server can be achieved by using the module. The
client and the server can not be able to communicate before they establish a connection.
openldap-servers – this packages contain the necessary modules which are required to configure
the servers. For instance, for a certain server to be able to communicate effectively with the
clients, the modules must be present.
Openldap-clients – used to configure how the clients are able to establish a connection with the
server. Once the clients are connected to the server, then the client can be able to request for a
certain resource and the server is then able to respond with a pointer to the location of the
resource.
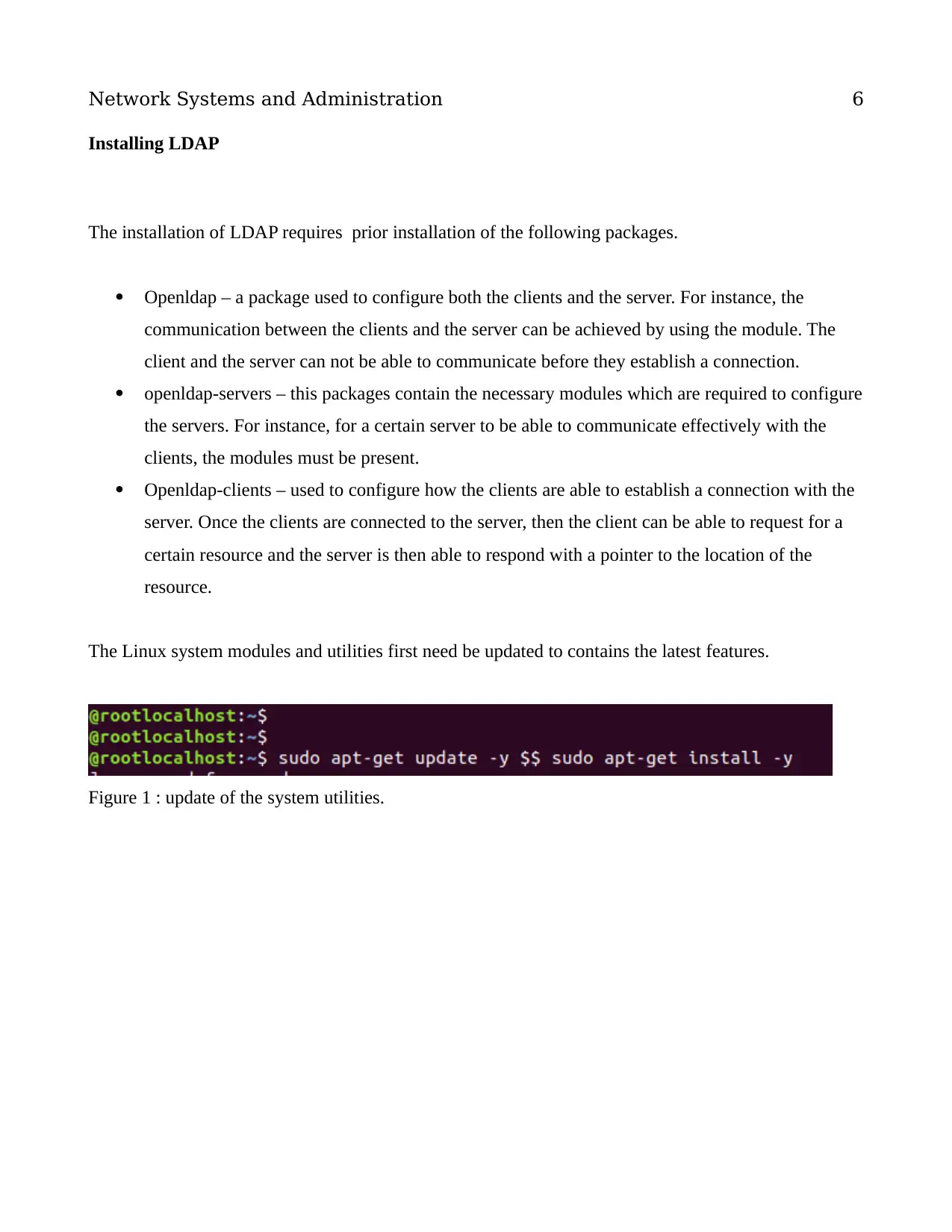
The Linux system modules and utilities first need be updated to contains the latest features.
Figure 1 : update of the system utilities.
Installing LDAP
The installation of LDAP requires prior installation of the following packages.
Openldap – a package used to configure both the clients and the server. For instance, the
communication between the clients and the server can be achieved by using the module. The
client and the server can not be able to communicate before they establish a connection.
openldap-servers – this packages contain the necessary modules which are required to configure
the servers. For instance, for a certain server to be able to communicate effectively with the
clients, the modules must be present.
Openldap-clients – used to configure how the clients are able to establish a connection with the
server. Once the clients are connected to the server, then the client can be able to request for a
certain resource and the server is then able to respond with a pointer to the location of the
resource.
The Linux system modules and utilities first need be updated to contains the latest features.
Figure 1 : update of the system utilities.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Systems and Administration 7
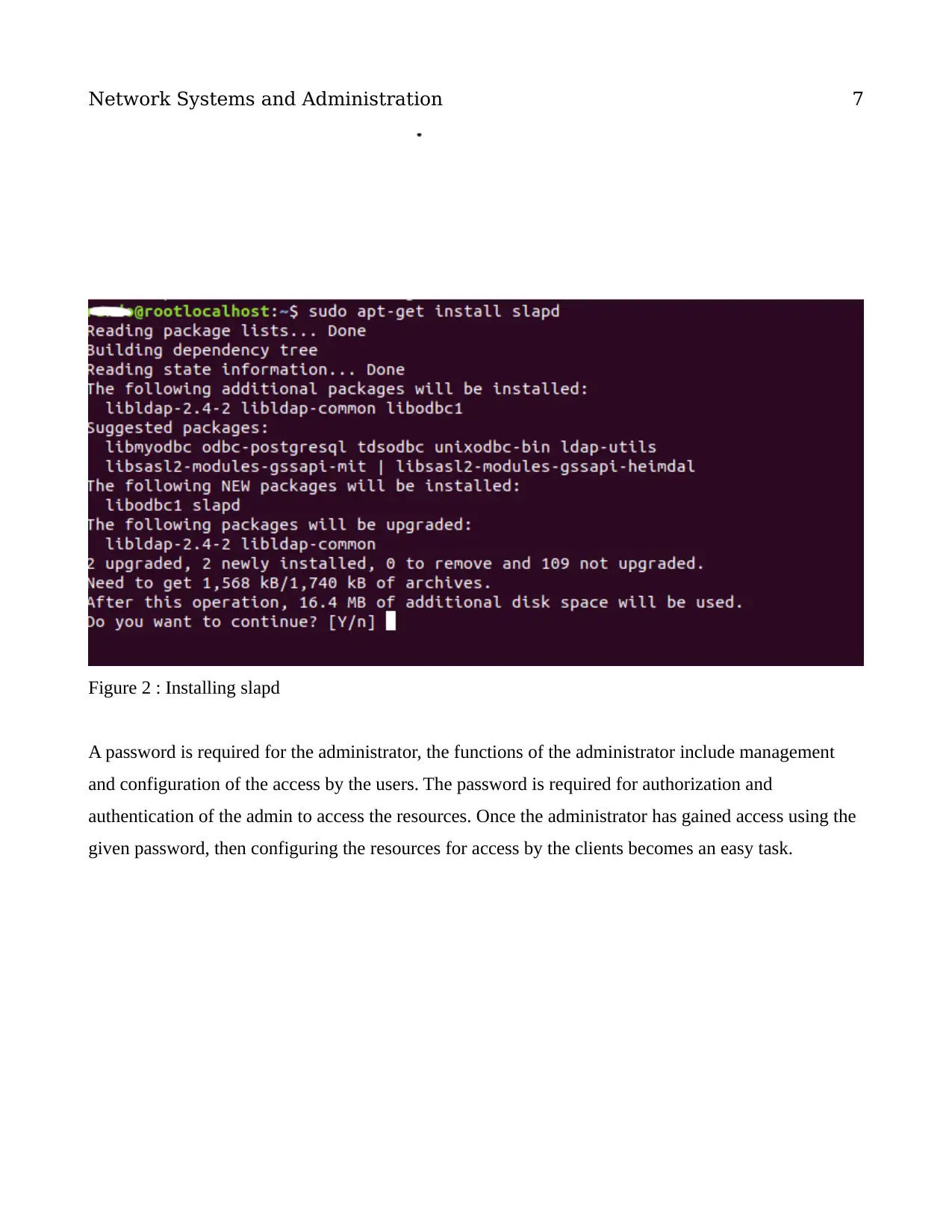
Figure 2 : Installing slapd
A password is required for the administrator, the functions of the administrator include management
and configuration of the access by the users. The password is required for authorization and
authentication of the admin to access the resources. Once the administrator has gained access using the
given password, then configuring the resources for access by the clients becomes an easy task.
Figure 2 : Installing slapd
A password is required for the administrator, the functions of the administrator include management
and configuration of the access by the users. The password is required for authorization and
authentication of the admin to access the resources. Once the administrator has gained access using the
given password, then configuring the resources for access by the clients becomes an easy task.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Systems and Administration 8
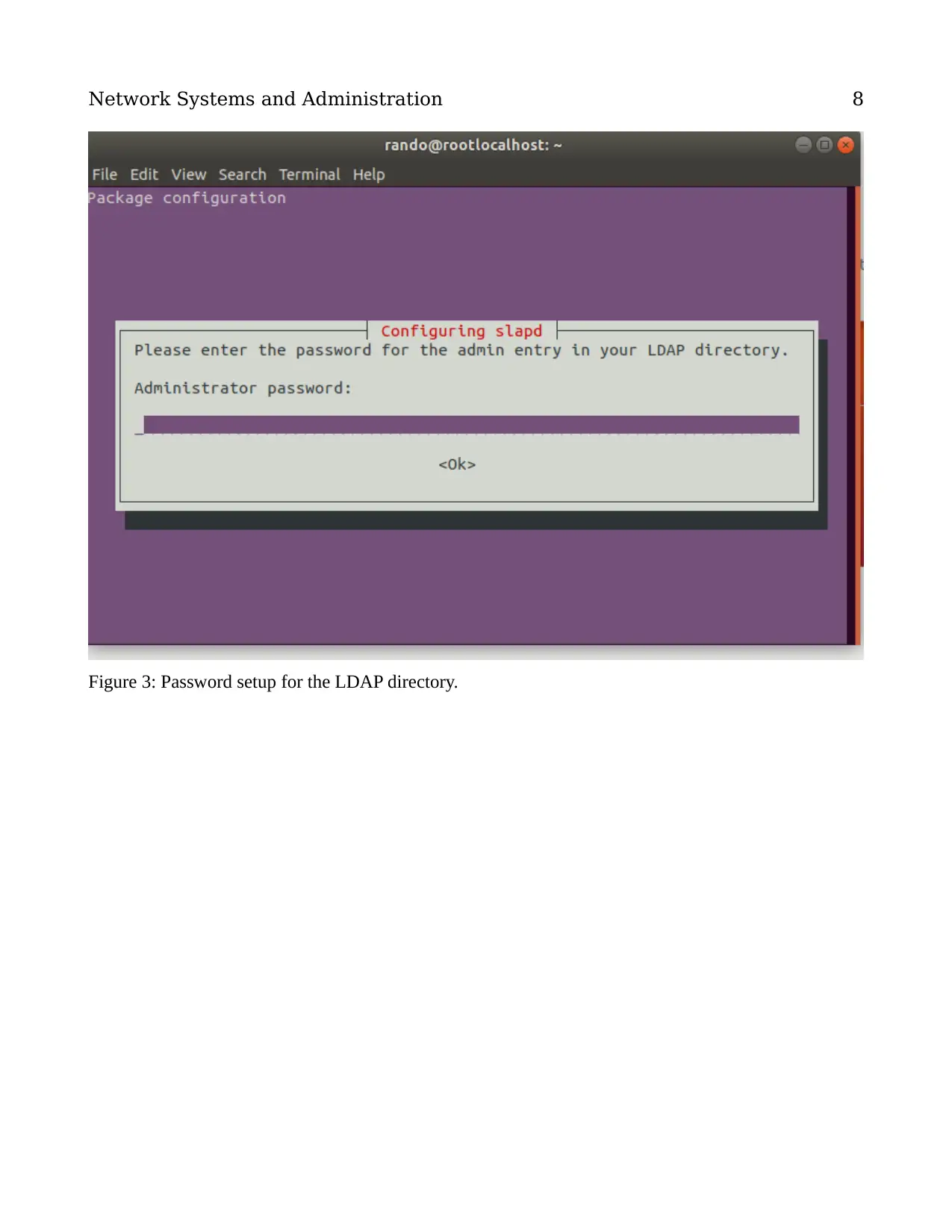
Figure 3: Password setup for the LDAP directory.
Figure 3: Password setup for the LDAP directory.
Network Systems and Administration 9
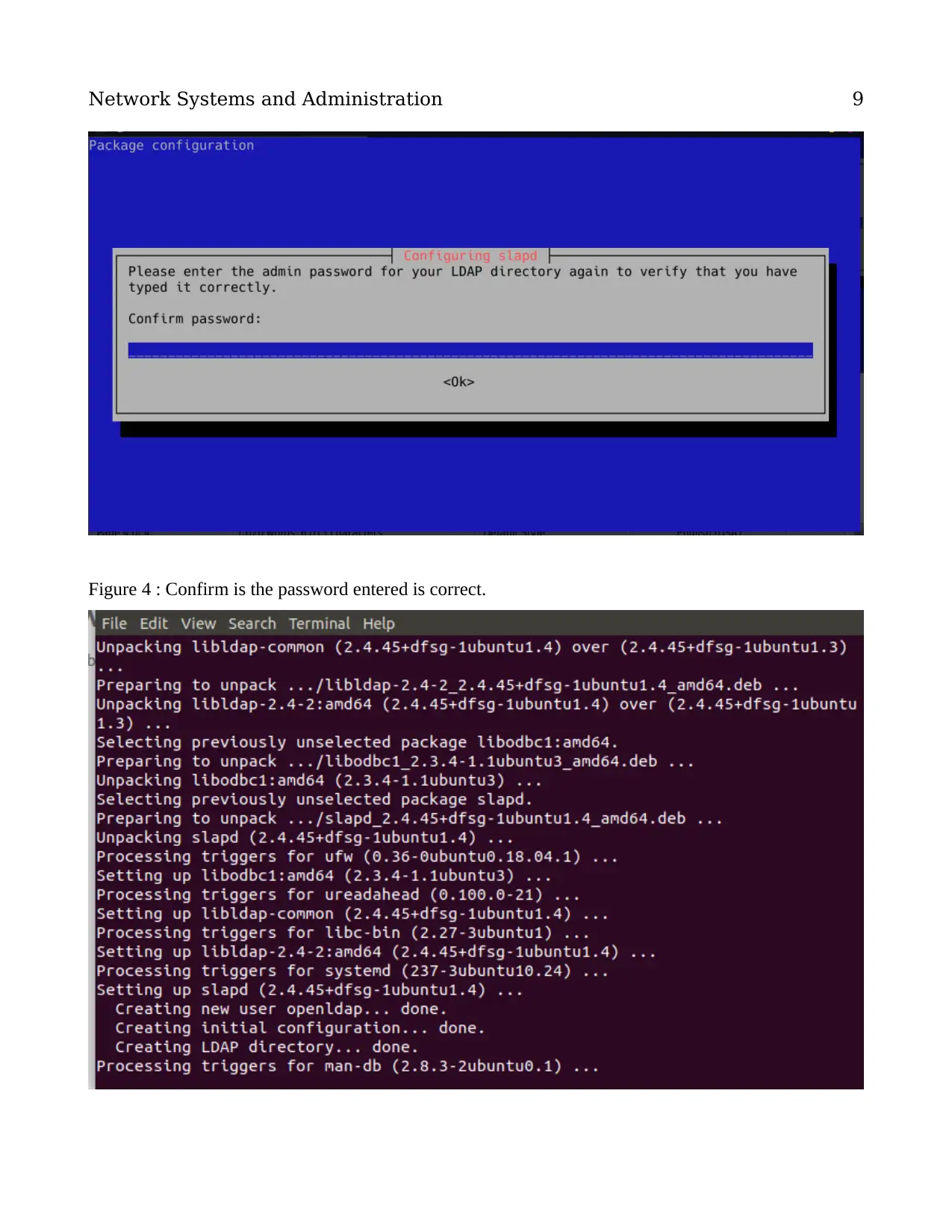
Figure 4 : Confirm is the password entered is correct.
Figure 4 : Confirm is the password entered is correct.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
Network Systems and Administration 10
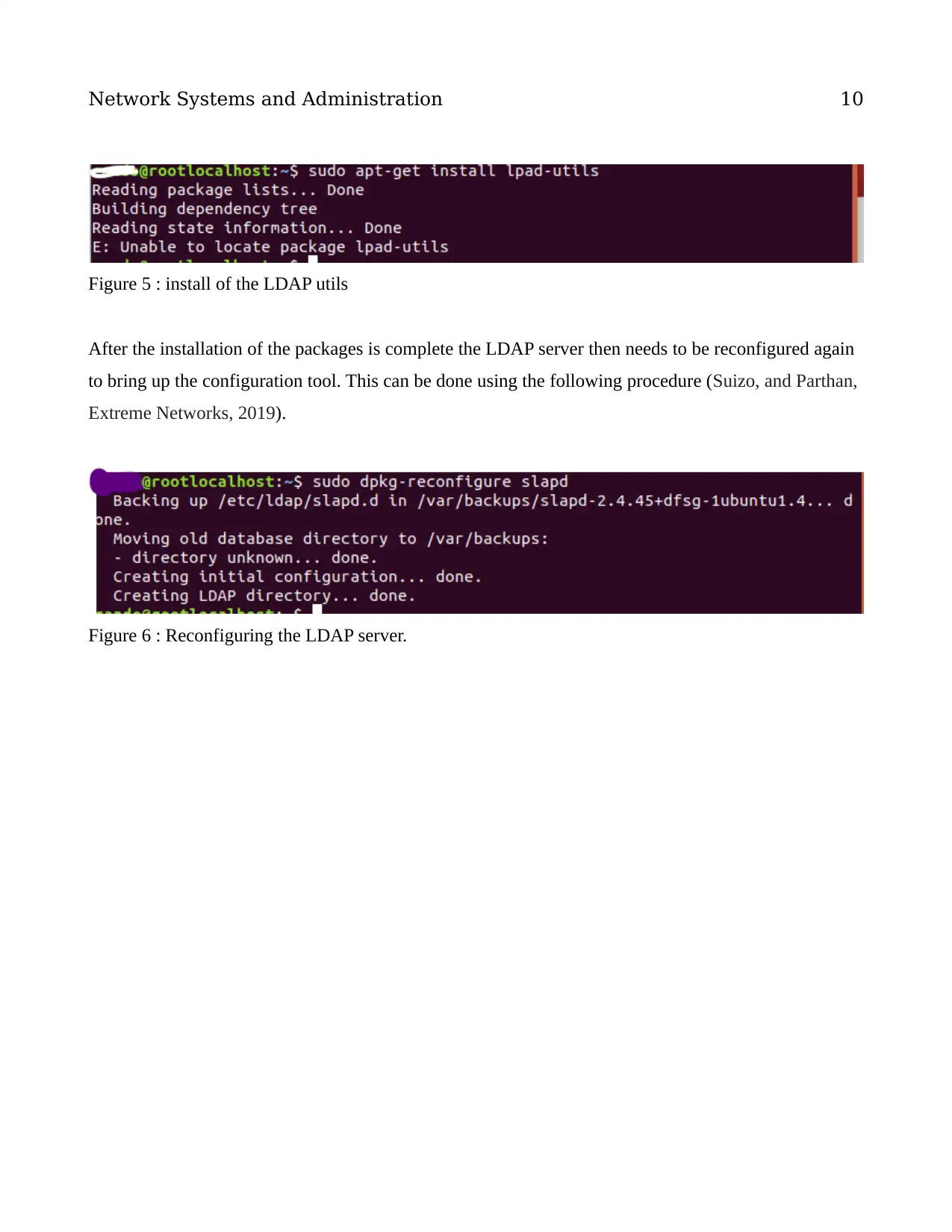
Figure 5 : install of the LDAP utils
After the installation of the packages is complete the LDAP server then needs to be reconfigured again
to bring up the configuration tool. This can be done using the following procedure (Suizo, and Parthan,
Extreme Networks, 2019).
Figure 6 : Reconfiguring the LDAP server.
Figure 5 : install of the LDAP utils
After the installation of the packages is complete the LDAP server then needs to be reconfigured again
to bring up the configuration tool. This can be done using the following procedure (Suizo, and Parthan,
Extreme Networks, 2019).
Figure 6 : Reconfiguring the LDAP server.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Network Systems and Administration 11
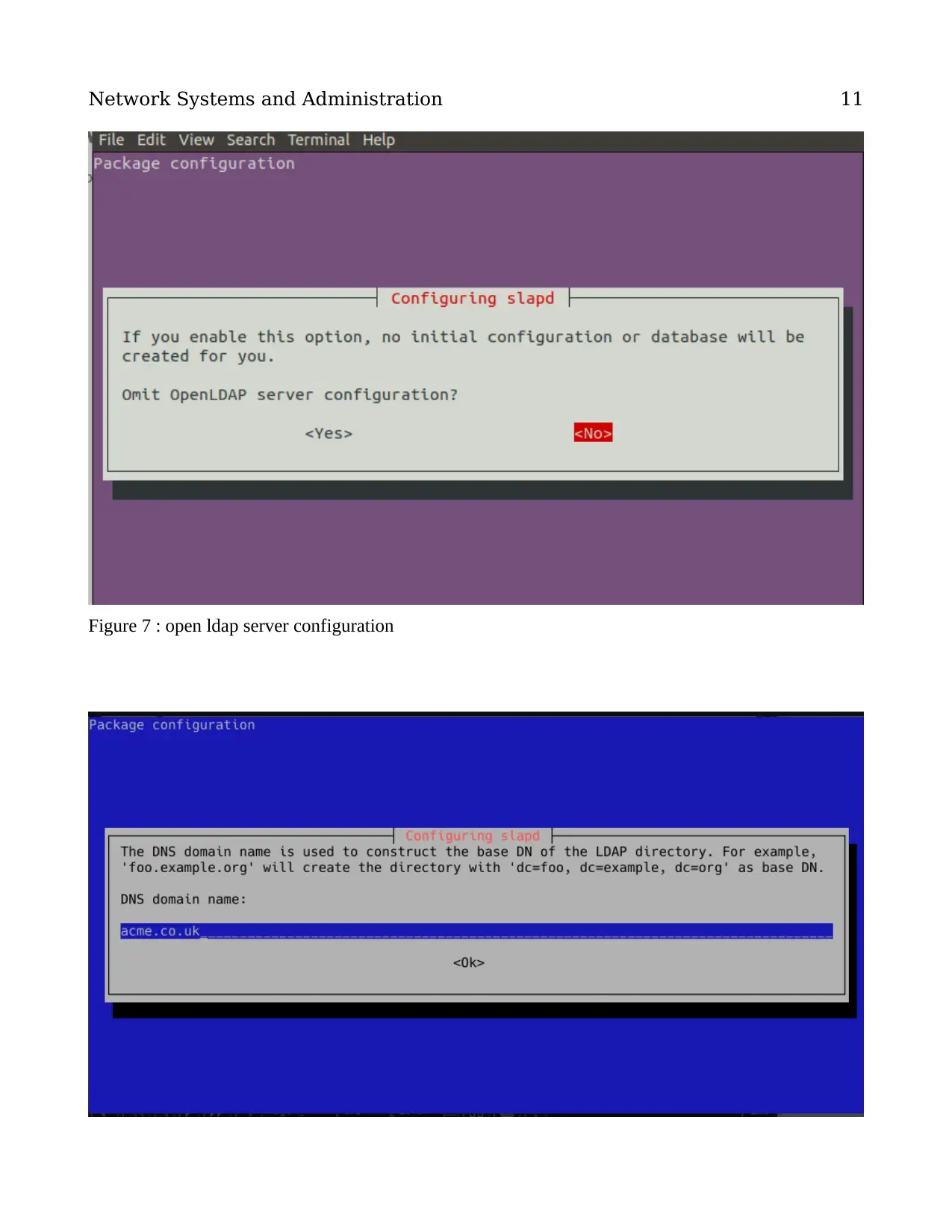
Figure 7 : open ldap server configuration
Figure 7 : open ldap server configuration
Network Systems and Administration 12
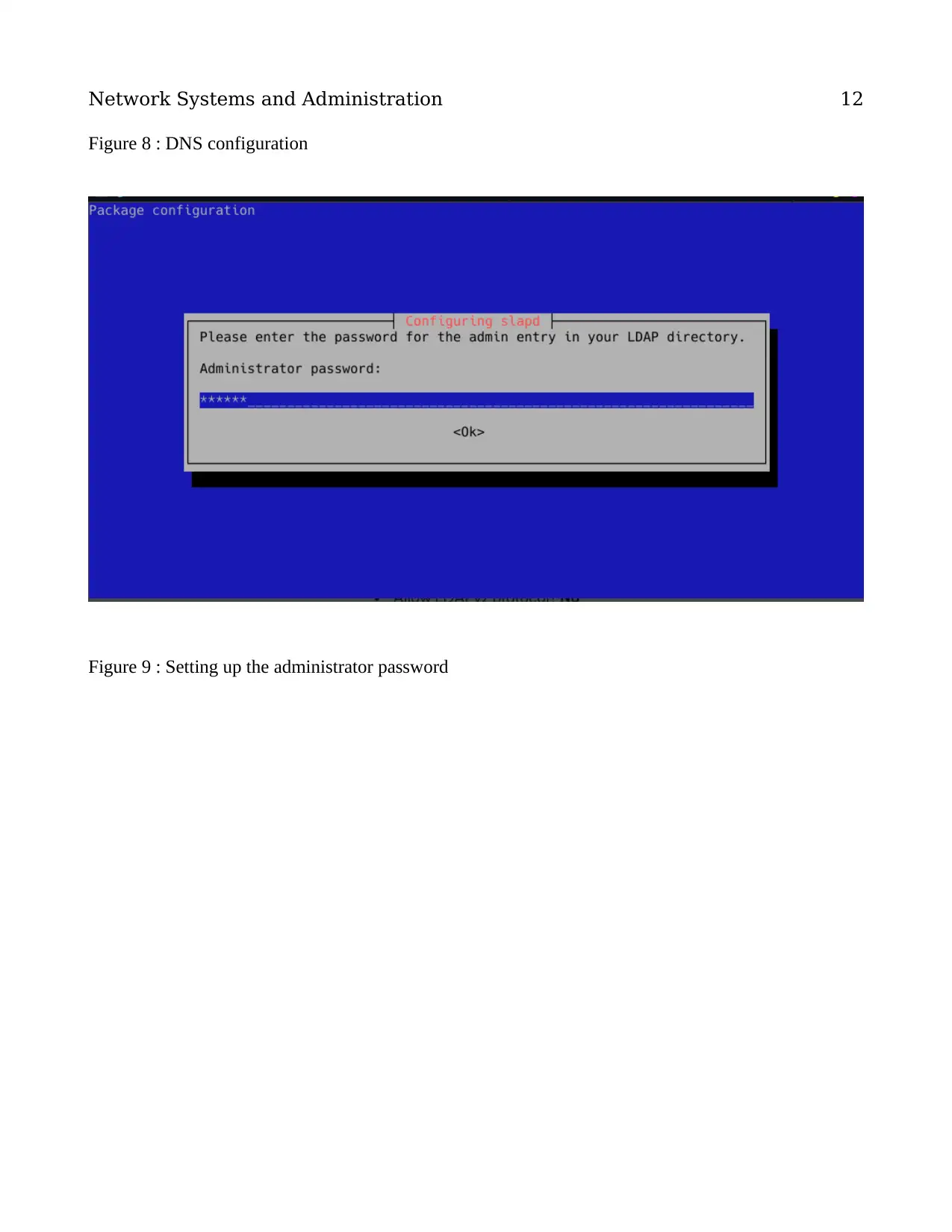
Figure 8 : DNS configuration
Figure 9 : Setting up the administrator password
Figure 8 : DNS configuration
Figure 9 : Setting up the administrator password
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 31
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





