CIS114-6: Linux LDAP Infrastructure Deployment - Portfolio Report
VerifiedAdded on 2022/11/03
|21
|3030
|456
Portfolio
AI Summary
This portfolio documents the implementation and configuration of an LDAP infrastructure on a Linux server, focusing on using OpenLDAP on Ubuntu 18.04. It covers the installation of OpenLDAP and phpLDAPadmin, a web interface for managing LDAP data, including configuring the base DN and setting up authentication. The report details the creation of organizational units, groups (Admin, ICT, Management), and users, assigning users to specific groups. It further explains the process of configuring phpLDAPadmin to utilize the domain and setting up an administrator account, and the importance of securing the LDAP server. The document references the Lightweight Directory Access Protocol's background, its role in directory services, and its application in managing users and groups within a network environment. This portfolio provides a practical guide to deploying LDAP for centralized authentication and directory management.

Name of the Student
Name of the University
Author Note
LDAP ImPLEMENTATION
Name of the University
Author Note
LDAP ImPLEMENTATION
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3
Table of Contents
Introduction......................................................................................................................................2
OpenLDAP:.....................................................................................................................................2
Background......................................................................................................................................3
Installation.......................................................................................................................................4
Administration: root.....................................................................................................................4
Get: OpenLDAP...........................................................................................................................4
Gedit : LDAP...............................................................................................................................6
Server: Configure.........................................................................................................................7
LDAP: search...............................................................................................................................7
Get: Phpldapadmin.......................................................................................................................9
Edit: Text Editor.........................................................................................................................11
Logging: phpLDAPadmin Web Interface.....................................................................................12
Authentication: LDAP...............................................................................................................13
Create: Organizational Unit.......................................................................................................14
Validate: Server.............................................................................................................................17
Conclusion.....................................................................................................................................17
References......................................................................................................................................19
Table of Contents
Introduction......................................................................................................................................2
OpenLDAP:.....................................................................................................................................2
Background......................................................................................................................................3
Installation.......................................................................................................................................4
Administration: root.....................................................................................................................4
Get: OpenLDAP...........................................................................................................................4
Gedit : LDAP...............................................................................................................................6
Server: Configure.........................................................................................................................7
LDAP: search...............................................................................................................................7
Get: Phpldapadmin.......................................................................................................................9
Edit: Text Editor.........................................................................................................................11
Logging: phpLDAPadmin Web Interface.....................................................................................12
Authentication: LDAP...............................................................................................................13
Create: Organizational Unit.......................................................................................................14
Validate: Server.............................................................................................................................17
Conclusion.....................................................................................................................................17
References......................................................................................................................................19

3
Introduction
Lightweight Directory Access Protocol (LDAP) is a standard protocol intended to oversee and
access progressive directory data over a system. It very well may be utilized to store any sort of
data, however it is frequently utilized as a concentrated confirmation framework or for corporate
email and telephone catalogs.
In this report, it is also examine how to introduce and arrange the OpenLDAP server on Ubuntu
18.04. We will at that point introduce phpLDAPadmin, a web interface for review and
controlling LDAP data. We will verify the web interface and the LDAP administration with SSL
certificates from Let's Encrypt, a supplier of free and computerized certificates.
OpenLDAP:
libraries implementing the LDAP protocol, and utilities, tools, and sample clients.
slapd – stand-alone LDAP daemon (server)
This report looks at how to install OpenLDAP and how to configure it in Ubuntu / Debian server.
The server is tested in Ubuntu latest version, Here is the testing system’s details:
Hostname : ldap.com
IP Address : 192.168.109.132/24
Operating System : Ubuntu 18.10 64 bit server
The LDAP or Lightweight Directory Access Protocol is a protocol for questioning and changing
a “X.500”-based directory administration over TCP/IP. The current LDAP rendition is LDAPv3,
as characterized in RFC4510, and the usage in Ubuntu is OpenLDAP."
So the LDAP protocol accesses LDAP catalogs. Here are some key ideas and terms:
A LDAP directory is a tree of information passages that is various leveled in nature and is
known as the Directory Information Tree (DIT).
Introduction
Lightweight Directory Access Protocol (LDAP) is a standard protocol intended to oversee and
access progressive directory data over a system. It very well may be utilized to store any sort of
data, however it is frequently utilized as a concentrated confirmation framework or for corporate
email and telephone catalogs.
In this report, it is also examine how to introduce and arrange the OpenLDAP server on Ubuntu
18.04. We will at that point introduce phpLDAPadmin, a web interface for review and
controlling LDAP data. We will verify the web interface and the LDAP administration with SSL
certificates from Let's Encrypt, a supplier of free and computerized certificates.
OpenLDAP:
libraries implementing the LDAP protocol, and utilities, tools, and sample clients.
slapd – stand-alone LDAP daemon (server)
This report looks at how to install OpenLDAP and how to configure it in Ubuntu / Debian server.
The server is tested in Ubuntu latest version, Here is the testing system’s details:
Hostname : ldap.com
IP Address : 192.168.109.132/24
Operating System : Ubuntu 18.10 64 bit server
The LDAP or Lightweight Directory Access Protocol is a protocol for questioning and changing
a “X.500”-based directory administration over TCP/IP. The current LDAP rendition is LDAPv3,
as characterized in RFC4510, and the usage in Ubuntu is OpenLDAP."
So the LDAP protocol accesses LDAP catalogs. Here are some key ideas and terms:
A LDAP directory is a tree of information passages that is various leveled in nature and is
known as the Directory Information Tree (DIT).
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3
The section's DN isn't a quality. It isn't viewed as a component of the passage itself.
Every section has a special identifier: its Distinguished Name (DN or dn). This, thus,
comprises of a Relative Distinguished Name (RDN) trailed by the parent section's DN.
Qualities and objectclasses are characterized in outlines (an objectclass is really
considered as a unique sort of property).
A passage comprises of a lot of properties.
A property has a sort (a name/depiction) and at least one qualities.
Each quality must be characterized in at any rate one objectClass.
Background
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL was at first made by Steve Kille of Isode
Limited Tim Howes of the University of Michigan, and Wengyik Yeong of Performance
Systems International, in the aerly 1990s. It depends on the X.500 standard, yet is
straightforward and effectively adjusts to address custom issues whose particulars are
characterized in the Requests for Comments (RFCs).
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL is likewise cross-stage and principles
based. In this way, the network components are not worried about the server kind facilitating the
directory. The LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL servers are anything but
difficult to introduce, keep up and upgrade (Shrivastavaand Rizvi 2014). The LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL server procedure questions and updates the
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL data directory. LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL servers are fit for reproducing information either through
push or draw techniques. The innovation identified with replication is effectively designed and
implicit. LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL grants verified agent read and
change expert dependent on necessities utilizing Microsoft Access control records. The client
application layer does not undergo any security checks. All this is carried out together through
the LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL directory (Wu, Huanand Yu 2014).
The section's DN isn't a quality. It isn't viewed as a component of the passage itself.
Every section has a special identifier: its Distinguished Name (DN or dn). This, thus,
comprises of a Relative Distinguished Name (RDN) trailed by the parent section's DN.
Qualities and objectclasses are characterized in outlines (an objectclass is really
considered as a unique sort of property).
A passage comprises of a lot of properties.
A property has a sort (a name/depiction) and at least one qualities.
Each quality must be characterized in at any rate one objectClass.
Background
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL was at first made by Steve Kille of Isode
Limited Tim Howes of the University of Michigan, and Wengyik Yeong of Performance
Systems International, in the aerly 1990s. It depends on the X.500 standard, yet is
straightforward and effectively adjusts to address custom issues whose particulars are
characterized in the Requests for Comments (RFCs).
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL is likewise cross-stage and principles
based. In this way, the network components are not worried about the server kind facilitating the
directory. The LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL servers are anything but
difficult to introduce, keep up and upgrade (Shrivastavaand Rizvi 2014). The LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL server procedure questions and updates the
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL data directory. LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL servers are fit for reproducing information either through
push or draw techniques. The innovation identified with replication is effectively designed and
implicit. LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL grants verified agent read and
change expert dependent on necessities utilizing Microsoft Access control records. The client
application layer does not undergo any security checks. All this is carried out together through
the LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL directory (Wu, Huanand Yu 2014).
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

3
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL,fails to describe how projects are
cleared on the customer server end, however it defines the language utilized by clients’ projects
to communicate with servers. LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL servers
go from little servers for workgroups to huge hierarchical and open servers.
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL directory servers holds information
progressively. Among its strategies is to segment the directory utilizing LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL referrals, which empower clients to allude
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL solicitations to an alternate server. The
focal idea of LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL is the data model, which
manages the sort of data put away in registries and the organizing of data. The data model spins
around a passage, which is a gathering of properties with sort and worth. Passages are sorted out
in a tree-like arrangement identified as the directory data tree. The sections are created around
genuine ideas, association, individuals and items (Hsuet al. 2014). Characteristic sorts are related
with language structure characterizing permitted data. A solitary property can encase numerous
qualities inside it. The recognized names in LIGHTWEIGHT DIRECTORY ACCESS
PROTOCOL are perused from base to top. The left section is known as the relative separated
name and the correct fragment is the base recognized name.
Numerous sellers of server items and directory customers support LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL . Organizations with LIGHTWEIGHT DIRECTORY
ACCESS PROTOCOL aims incorporate IBM, AT&T, Sun and Novell. Eudora and Netscape
communicator additionally support LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL .
Government organizations and huge colleges additionally use LIGHTWEIGHT DIRECTORY
ACCESS PROTOCOL servers for putting away and sorting out data.
|For any system,a catalog is applied to show users where each component is located. For TCP/IP
protocols (counting the Internet), the Domain Name Service (DNS) is the index context applied
to distinguish the identity of an area to a specific system address (a one of a kind zone on the
system). In certain instances,users may not recognize the area name. LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL enables users to look for an individual without realizing
where they're found.
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL,fails to describe how projects are
cleared on the customer server end, however it defines the language utilized by clients’ projects
to communicate with servers. LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL servers
go from little servers for workgroups to huge hierarchical and open servers.
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL directory servers holds information
progressively. Among its strategies is to segment the directory utilizing LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL referrals, which empower clients to allude
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL solicitations to an alternate server. The
focal idea of LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL is the data model, which
manages the sort of data put away in registries and the organizing of data. The data model spins
around a passage, which is a gathering of properties with sort and worth. Passages are sorted out
in a tree-like arrangement identified as the directory data tree. The sections are created around
genuine ideas, association, individuals and items (Hsuet al. 2014). Characteristic sorts are related
with language structure characterizing permitted data. A solitary property can encase numerous
qualities inside it. The recognized names in LIGHTWEIGHT DIRECTORY ACCESS
PROTOCOL are perused from base to top. The left section is known as the relative separated
name and the correct fragment is the base recognized name.
Numerous sellers of server items and directory customers support LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL . Organizations with LIGHTWEIGHT DIRECTORY
ACCESS PROTOCOL aims incorporate IBM, AT&T, Sun and Novell. Eudora and Netscape
communicator additionally support LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL .
Government organizations and huge colleges additionally use LIGHTWEIGHT DIRECTORY
ACCESS PROTOCOL servers for putting away and sorting out data.
|For any system,a catalog is applied to show users where each component is located. For TCP/IP
protocols (counting the Internet), the Domain Name Service (DNS) is the index context applied
to distinguish the identity of an area to a specific system address (a one of a kind zone on the
system). In certain instances,users may not recognize the area name. LIGHTWEIGHT
DIRECTORY ACCESS PROTOCOL enables users to look for an individual without realizing
where they're found.
3
A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL catalog is sorted out in a
direct "tree" chain of command made up of the associated levels:
People (which includes users, documents, and shared components, such as, printers,)
The root catalog (the beginning spot or the wellspring of the tree), which branches out to
Nations, every one of which branches out to
Associations, which branch out to Hierarchical units (divisions, offices, etc), which
branches out to (incorporates a passage for)
A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL index can be spread among several
servers. All servers can contain an imitated different of the all out index that is matched often. A
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL server is known as a Directory System
Agent (DSA). A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL server that obtains a
solicitation from a client adopts responsibility for the solicitation, transferring it to other DSAs as
important, yet ensuring a unique composed reaction for the user.
Installation
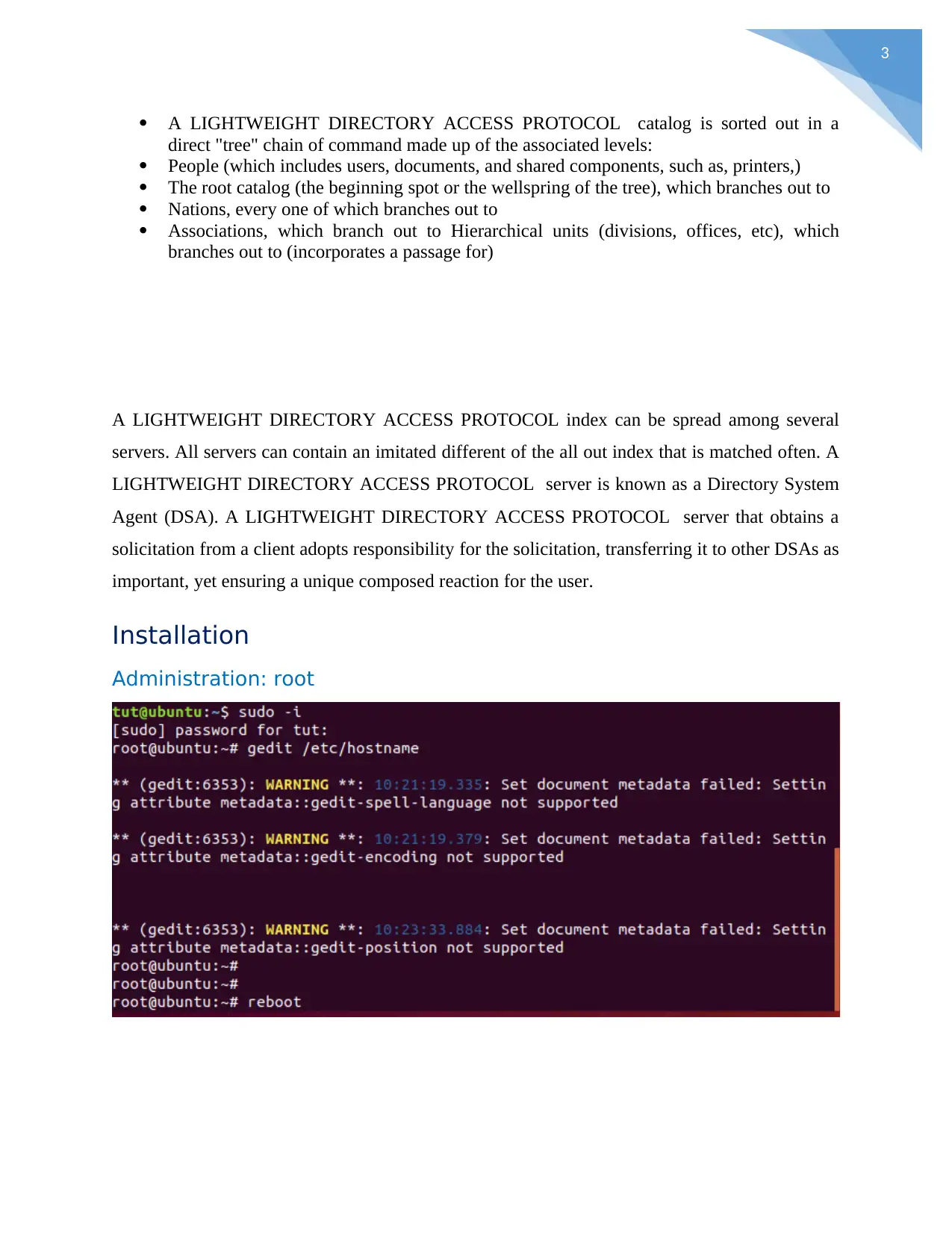
Administration: root
A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL catalog is sorted out in a
direct "tree" chain of command made up of the associated levels:
People (which includes users, documents, and shared components, such as, printers,)
The root catalog (the beginning spot or the wellspring of the tree), which branches out to
Nations, every one of which branches out to
Associations, which branch out to Hierarchical units (divisions, offices, etc), which
branches out to (incorporates a passage for)
A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL index can be spread among several
servers. All servers can contain an imitated different of the all out index that is matched often. A
LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL server is known as a Directory System
Agent (DSA). A LIGHTWEIGHT DIRECTORY ACCESS PROTOCOL server that obtains a
solicitation from a client adopts responsibility for the solicitation, transferring it to other DSAs as
important, yet ensuring a unique composed reaction for the user.
Installation
Administration: root
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3
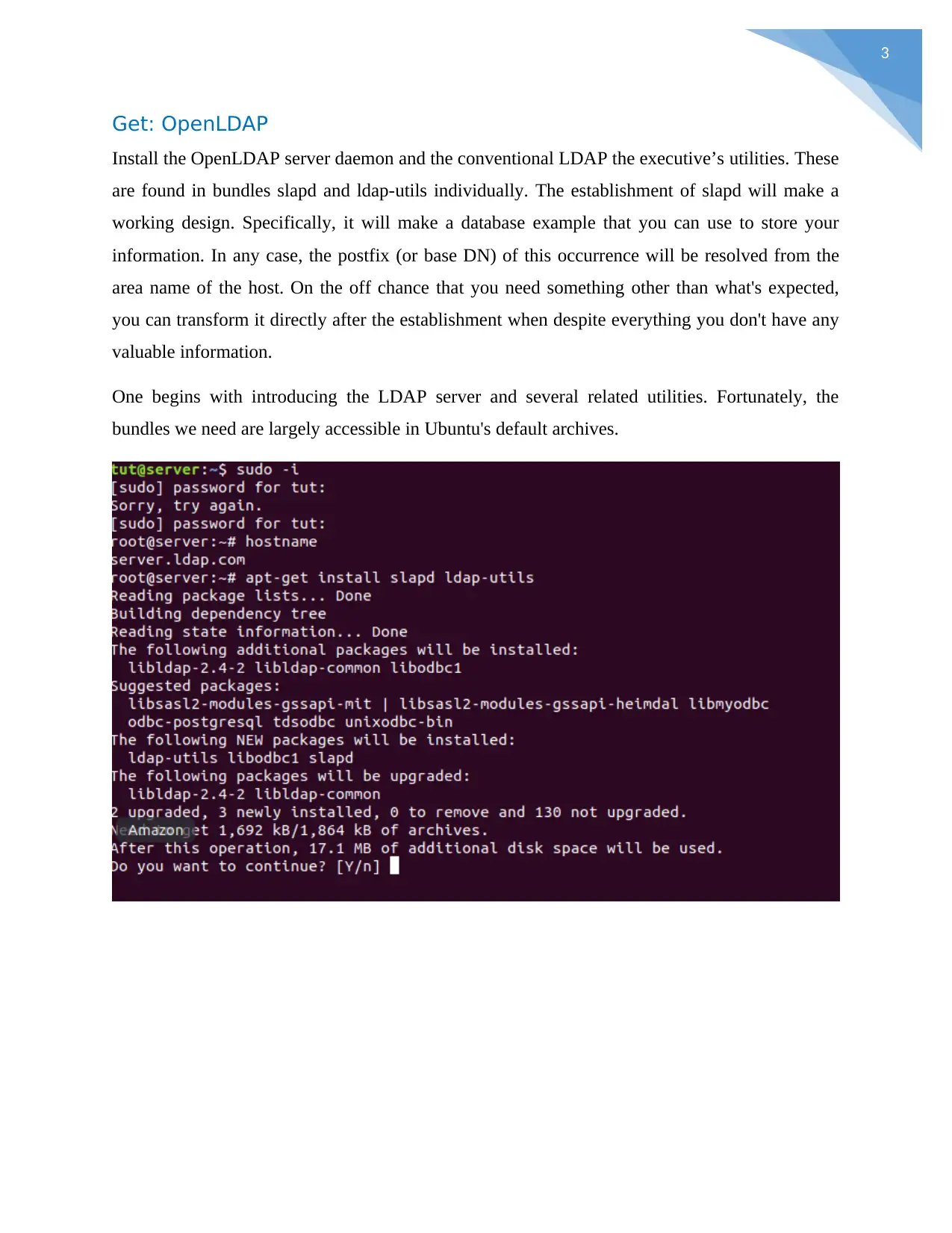
Get: OpenLDAP
Install the OpenLDAP server daemon and the conventional LDAP the executive’s utilities. These
are found in bundles slapd and ldap-utils individually. The establishment of slapd will make a
working design. Specifically, it will make a database example that you can use to store your
information. In any case, the postfix (or base DN) of this occurrence will be resolved from the
area name of the host. On the off chance that you need something other than what's expected,
you can transform it directly after the establishment when despite everything you don't have any
valuable information.
One begins with introducing the LDAP server and several related utilities. Fortunately, the
bundles we need are largely accessible in Ubuntu's default archives.
Get: OpenLDAP
Install the OpenLDAP server daemon and the conventional LDAP the executive’s utilities. These
are found in bundles slapd and ldap-utils individually. The establishment of slapd will make a
working design. Specifically, it will make a database example that you can use to store your
information. In any case, the postfix (or base DN) of this occurrence will be resolved from the
area name of the host. On the off chance that you need something other than what's expected,
you can transform it directly after the establishment when despite everything you don't have any
valuable information.
One begins with introducing the LDAP server and several related utilities. Fortunately, the
bundles we need are largely accessible in Ubuntu's default archives.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
3
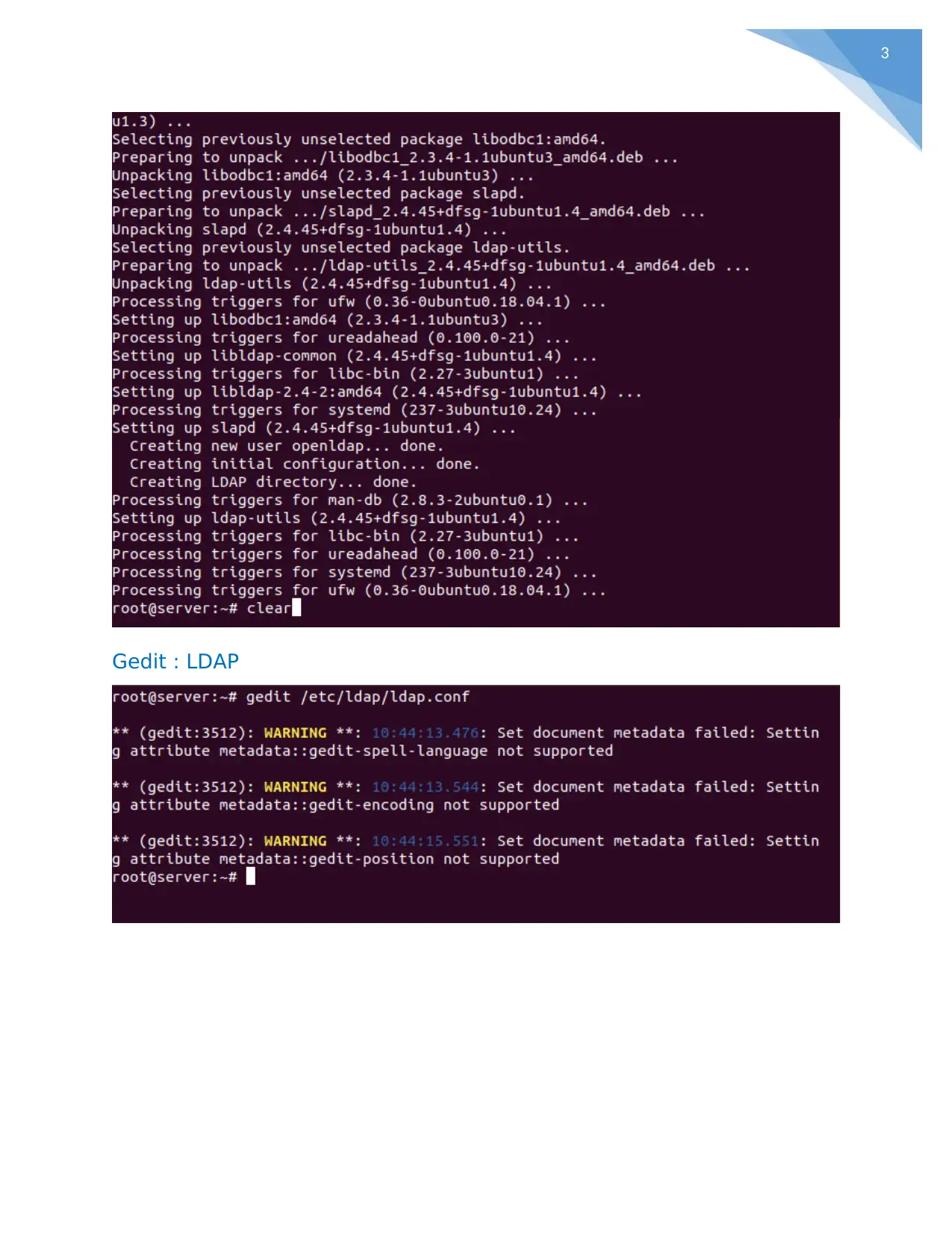
Gedit : LDAP
Gedit : LDAP
3
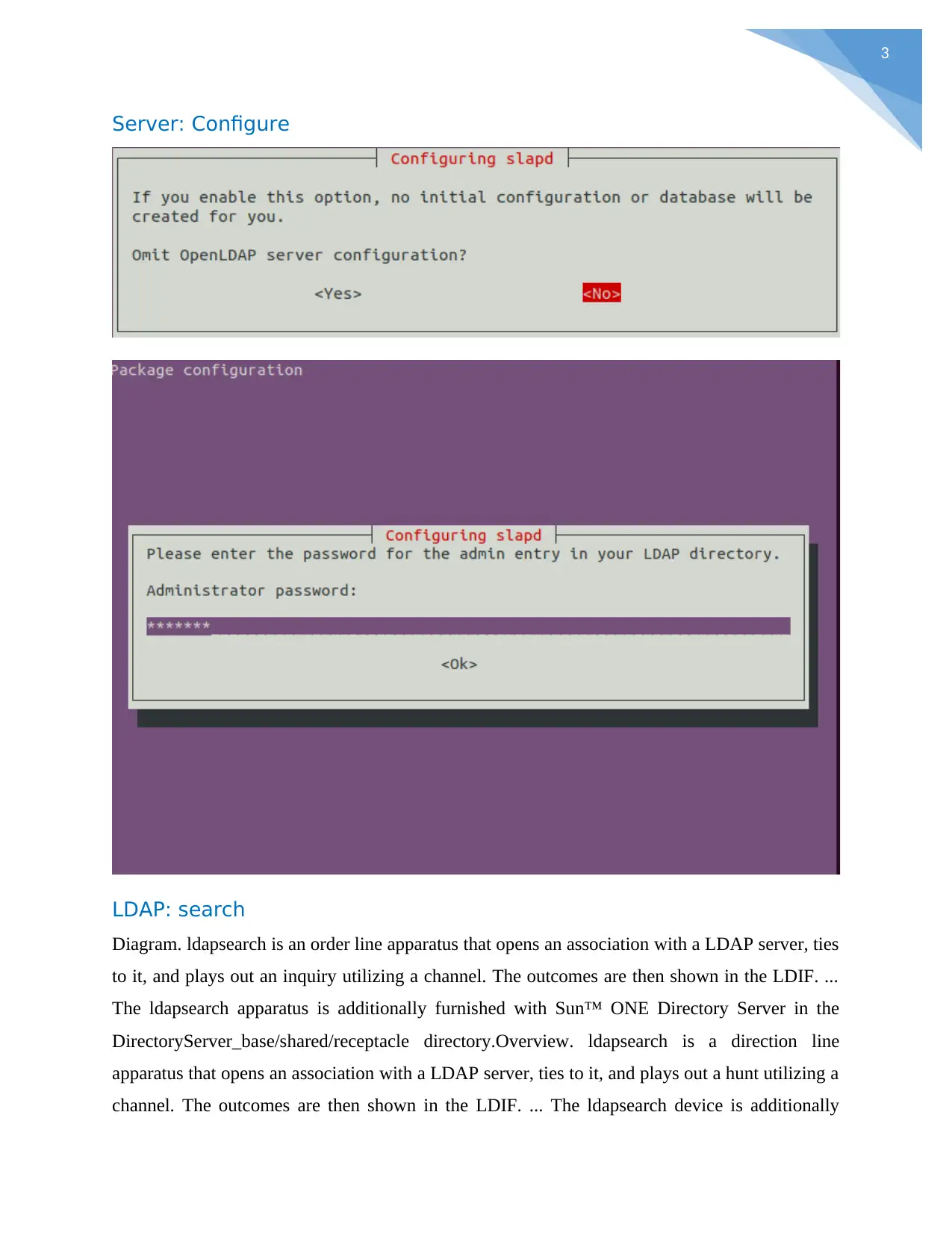
Server: Configure
LDAP: search
Diagram. ldapsearch is an order line apparatus that opens an association with a LDAP server, ties
to it, and plays out an inquiry utilizing a channel. The outcomes are then shown in the LDIF. ...
The ldapsearch apparatus is additionally furnished with Sun™ ONE Directory Server in the
DirectoryServer_base/shared/receptacle directory.Overview. ldapsearch is a direction line
apparatus that opens an association with a LDAP server, ties to it, and plays out a hunt utilizing a
channel. The outcomes are then shown in the LDIF. ... The ldapsearch device is additionally
Server: Configure
LDAP: search
Diagram. ldapsearch is an order line apparatus that opens an association with a LDAP server, ties
to it, and plays out an inquiry utilizing a channel. The outcomes are then shown in the LDIF. ...
The ldapsearch apparatus is additionally furnished with Sun™ ONE Directory Server in the
DirectoryServer_base/shared/receptacle directory.Overview. ldapsearch is a direction line
apparatus that opens an association with a LDAP server, ties to it, and plays out a hunt utilizing a
channel. The outcomes are then shown in the LDIF. ... The ldapsearch device is additionally
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
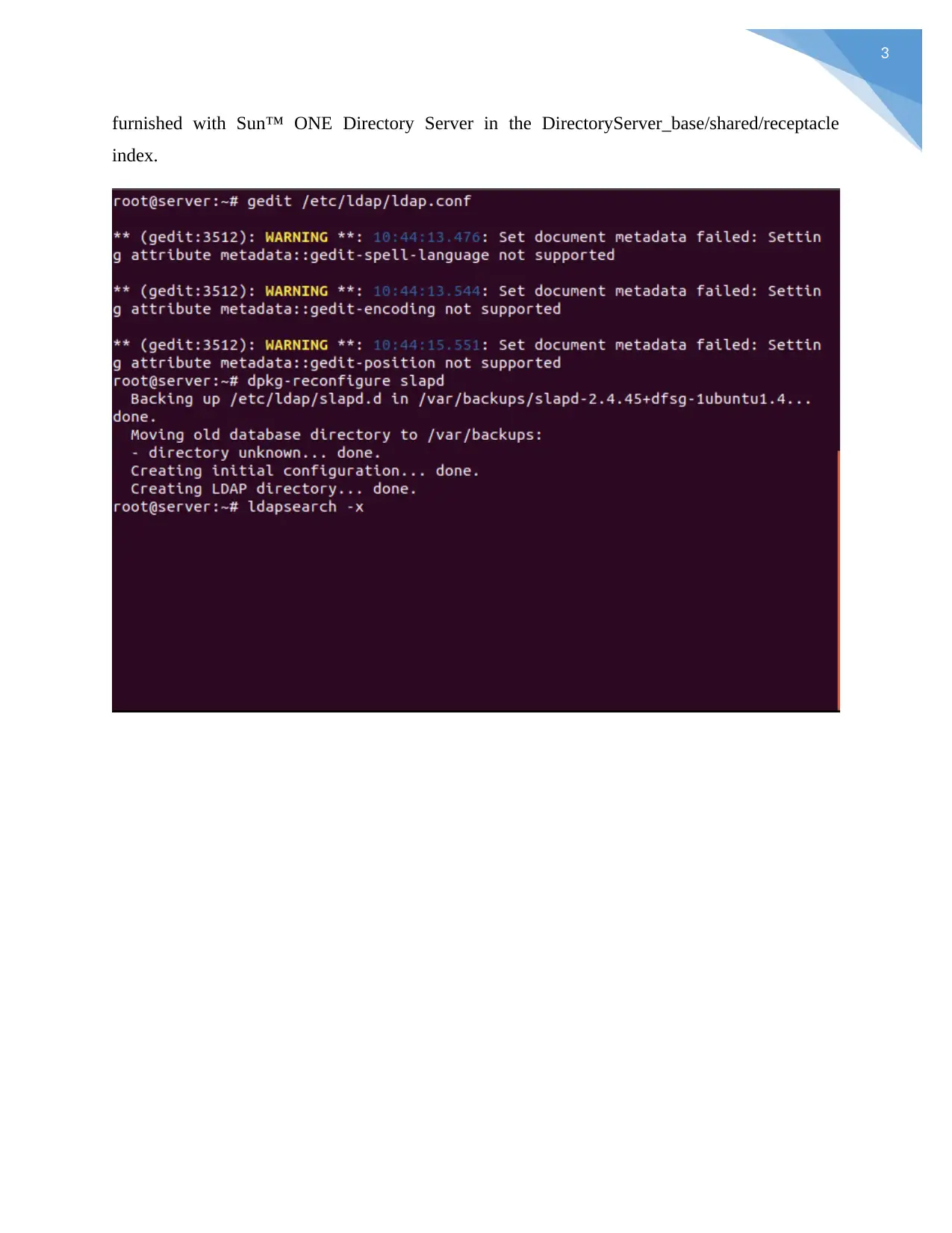
3
furnished with Sun™ ONE Directory Server in the DirectoryServer_base/shared/receptacle
index.
furnished with Sun™ ONE Directory Server in the DirectoryServer_base/shared/receptacle
index.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
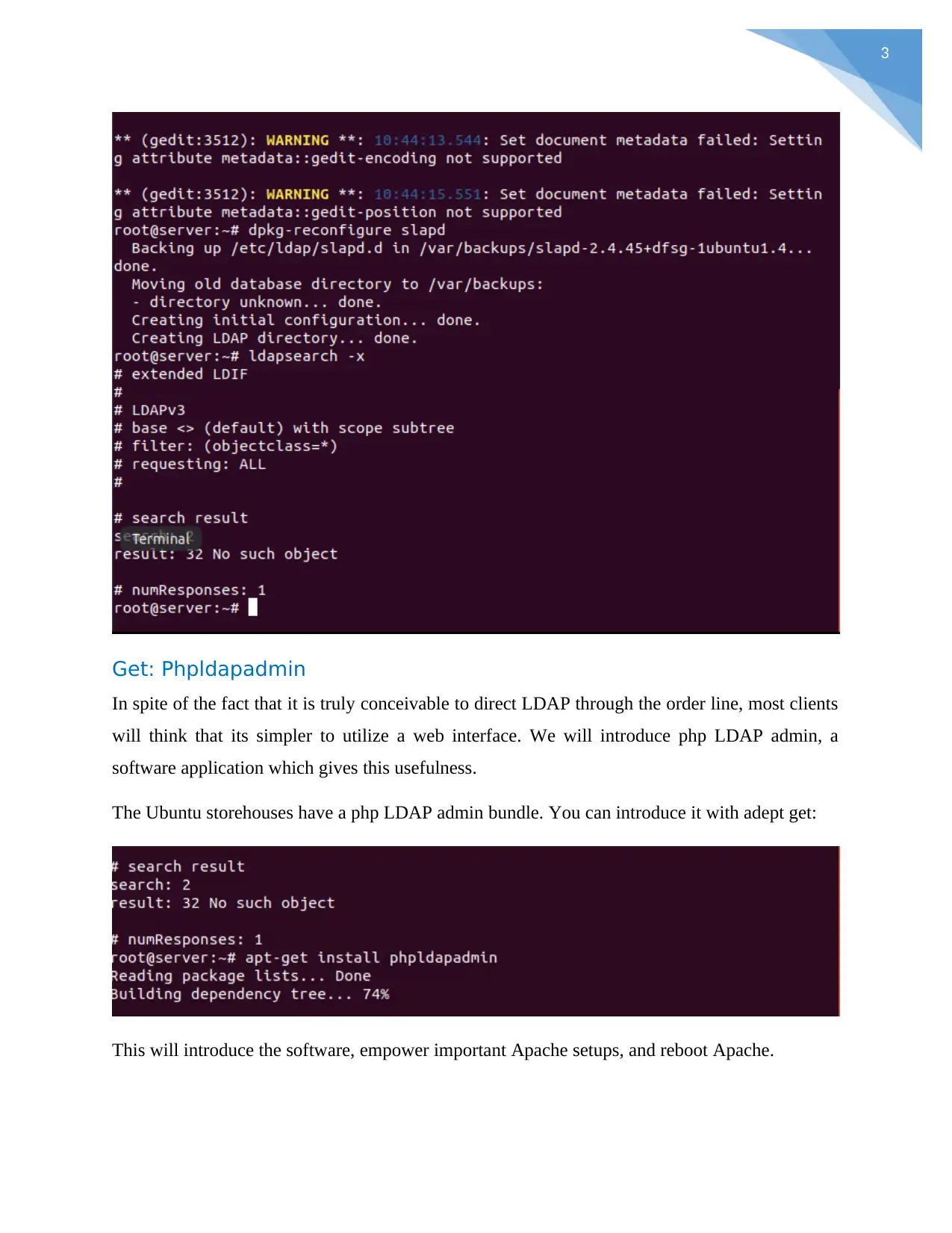
3
Get: Phpldapadmin
In spite of the fact that it is truly conceivable to direct LDAP through the order line, most clients
will think that its simpler to utilize a web interface. We will introduce php LDAP admin, a
software application which gives this usefulness.
The Ubuntu storehouses have a php LDAP admin bundle. You can introduce it with adept get:
This will introduce the software, empower important Apache setups, and reboot Apache.
Get: Phpldapadmin
In spite of the fact that it is truly conceivable to direct LDAP through the order line, most clients
will think that its simpler to utilize a web interface. We will introduce php LDAP admin, a
software application which gives this usefulness.
The Ubuntu storehouses have a php LDAP admin bundle. You can introduce it with adept get:
This will introduce the software, empower important Apache setups, and reboot Apache.
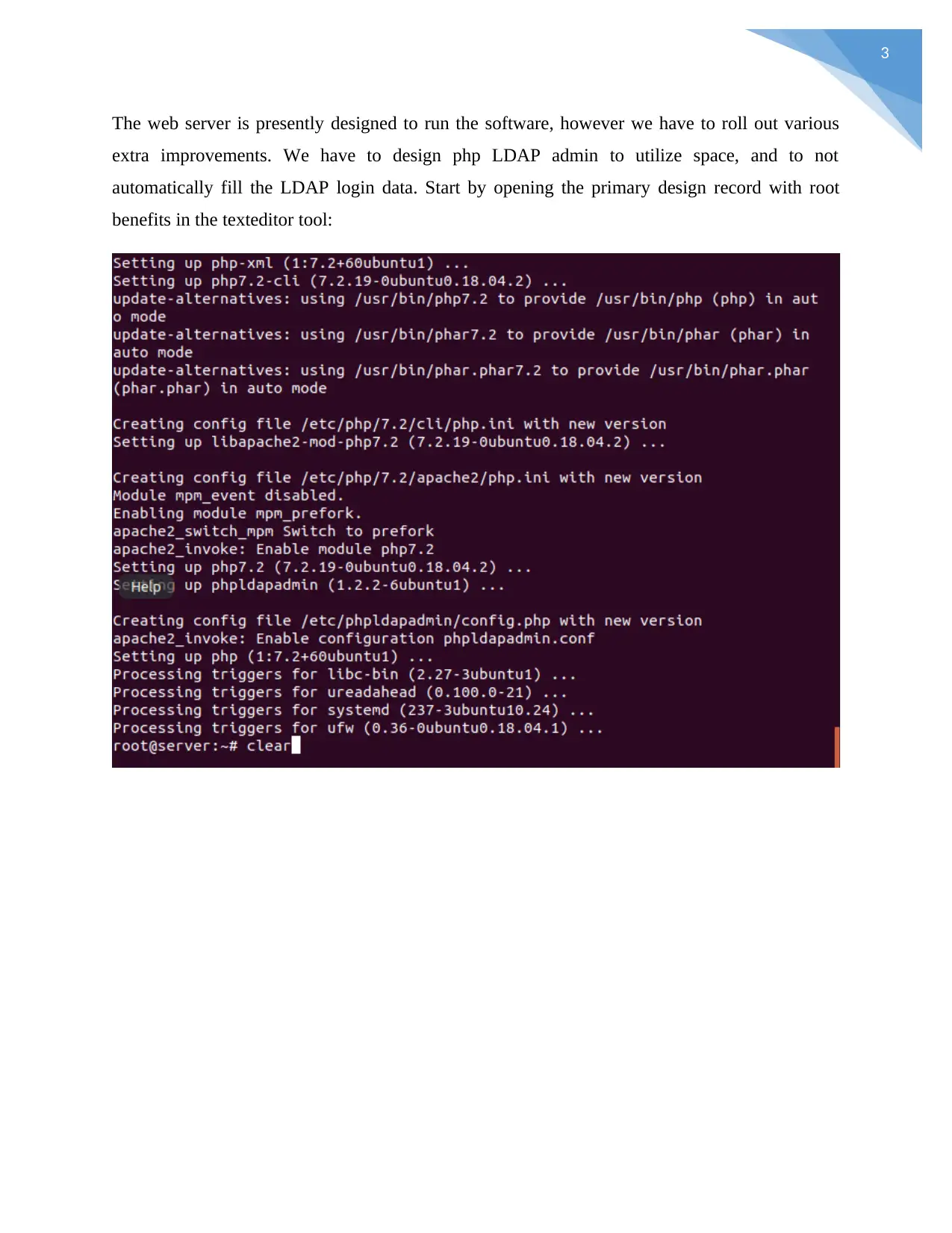
3
The web server is presently designed to run the software, however we have to roll out various
extra improvements. We have to design php LDAP admin to utilize space, and to not
automatically fill the LDAP login data. Start by opening the primary design record with root
benefits in the texteditor tool:
The web server is presently designed to run the software, however we have to roll out various
extra improvements. We have to design php LDAP admin to utilize space, and to not
automatically fill the LDAP login data. Start by opening the primary design record with root
benefits in the texteditor tool:
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.



