Computer Systems and Networks: Linux Change Logger Script - IMAT5122
VerifiedAdded on 2022/10/11
|10
|1850
|8
Practical Assignment
AI Summary
This document presents a comprehensive solution to a Linux System Change Logger Script assignment, focusing on system monitoring techniques within the Linux operating system. The assignment details the creation of a script to monitor various system resources, including CPU usage, memory allocation, and network interfaces. It explores essential Linux commands such as `ps`, `du`, `ip link`, `awk`, and `cut` for process listing, directory analysis, network interface identification, data manipulation, and text extraction. The solution covers the script's functionality in tracking processes, identifying top resource-consuming processes, and generating system health reports. It also includes screenshots demonstrating the execution of the script and the process of changing script permissions. The document emphasizes the significance of resource management and performance monitoring, highlighting the script's role in identifying and resolving performance bottlenecks. The assignment concludes with a bibliography of relevant research papers and resources used in the development of the solution.

Running head: COMPUTER SYSTEM AND NETWORK
COMPUTER SYSTEM & NETWORK
Name of the Student
Name of the University
Authors note
COMPUTER SYSTEM & NETWORK
Name of the Student
Name of the University
Authors note
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1COMPUTER SYSTEM AND NETWORK
User instruction for executing the change logger script in Linux
Linux operating system is accounted profitable to bigger organizations as well as
individual users. Different kinds of computer frameworks can be done using Linux operating
system using its features that are really noteworthy. Linux operating system may be
favourable to many, however Linux like other operating systems has few vulnerabilities like
imperative breaches, deadlock issues and few more.
Certain commands are available in Linux operating system that requires user privilege
atop basic clients such as root privilege’s requirement for executing a command. Default root
level privileges in Linux distributions like Ubuntu and Fedora, are not present to the users in
most cases. Hence using ‘sudo’ is preferred for executing shell scripts which accompanies
and the health report is generated and the process’s surveillance in certain Linux server
whenever required.
Whenever a file or any directory is developed in Linux, it automatically gets allocated
default permissions based on umask value. The umask command sets the umask value.
Certain digits are present in the umask command which mention several details about the
permissions granted such as the command’s first digit provides permission to the user who
creates the file, the second digit for the command is the permission for the group from where
the user is from. The value for third digit for the command represents permission to other
users.
The script can be executed by the ‘chmod’ command. This command can be used by
some files that require particular access restrictions. This command can be used to alter the
flags for special mode.
A particular shell script’s permission can be changed by the following method:
User instruction for executing the change logger script in Linux
Linux operating system is accounted profitable to bigger organizations as well as
individual users. Different kinds of computer frameworks can be done using Linux operating
system using its features that are really noteworthy. Linux operating system may be
favourable to many, however Linux like other operating systems has few vulnerabilities like
imperative breaches, deadlock issues and few more.
Certain commands are available in Linux operating system that requires user privilege
atop basic clients such as root privilege’s requirement for executing a command. Default root
level privileges in Linux distributions like Ubuntu and Fedora, are not present to the users in
most cases. Hence using ‘sudo’ is preferred for executing shell scripts which accompanies
and the health report is generated and the process’s surveillance in certain Linux server
whenever required.
Whenever a file or any directory is developed in Linux, it automatically gets allocated
default permissions based on umask value. The umask command sets the umask value.
Certain digits are present in the umask command which mention several details about the
permissions granted such as the command’s first digit provides permission to the user who
creates the file, the second digit for the command is the permission for the group from where
the user is from. The value for third digit for the command represents permission to other
users.
The script can be executed by the ‘chmod’ command. This command can be used by
some files that require particular access restrictions. This command can be used to alter the
flags for special mode.
A particular shell script’s permission can be changed by the following method:

2COMPUTER SYSTEM AND NETWORK
chmod + x mySysMonitor.sh
After the permission is changed, the script can be executed using the following command:
Sudo_/ mySysMonitor.sh
Analysis of designing health monitoring script:
For creating health monitoring script according to requirements of the project, the
script which is generated creates a log after collecting data which describes Linux related
system’s different allocations such as processor usage, memories and the resource’s
utilization. A script that keeps track of use of files, home directories uses and other processes.
The interfaces available for different networks, their status of availability and USB devices
list would be developed. The on-going process will also be checked by the script.
Listing for current processes:
The command which is used to list all processes in the Linux operating system is
psCommand. The ps or process status command is used to retrieve the process’s information
that is currently running in the system. This command includes few unique numbers specified
that are termed as PIDs. The program’s running instance that is a method present in the
system is termed as task.
List of top 5 RAM and CPU utilizing processes:
There are several commands available in Linux that can be used to list top 5 RAM
and CPU utilization processes such as:
ps -eo pid, ppid, cmd, %cpu, %mem --sort=-%mem | head
Any sort of data can be extracted about processes and arranging them by their memory
consumption’s status is obtained by using the above command.
chmod + x mySysMonitor.sh
After the permission is changed, the script can be executed using the following command:
Sudo_/ mySysMonitor.sh
Analysis of designing health monitoring script:
For creating health monitoring script according to requirements of the project, the
script which is generated creates a log after collecting data which describes Linux related
system’s different allocations such as processor usage, memories and the resource’s
utilization. A script that keeps track of use of files, home directories uses and other processes.
The interfaces available for different networks, their status of availability and USB devices
list would be developed. The on-going process will also be checked by the script.
Listing for current processes:
The command which is used to list all processes in the Linux operating system is
psCommand. The ps or process status command is used to retrieve the process’s information
that is currently running in the system. This command includes few unique numbers specified
that are termed as PIDs. The program’s running instance that is a method present in the
system is termed as task.
List of top 5 RAM and CPU utilizing processes:
There are several commands available in Linux that can be used to list top 5 RAM
and CPU utilization processes such as:
ps -eo pid, ppid, cmd, %cpu, %mem --sort=-%mem | head
Any sort of data can be extracted about processes and arranging them by their memory
consumption’s status is obtained by using the above command.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

3COMPUTER SYSTEM AND NETWORK
Main directories:
The main directories is found out by usage of following command:
du -a /home | sort -n -r | head -n 5
The directory which consists of highest user data in operating system’s several different parts
are listed with the help of this command.
Network Interfaces:
All the interfaces can be listed which are available in a system with usage of ip link
show command in Linux distribution’s latest versions. The ip link show command is more
used than the ‘inconfig’ command and the researches have proved it. The ip link command is
more suited than the ‘ifconfig’ command in Linux’s latest versions as the output is better.
This command can be used for utilizing dynamic routing, app containerized and other several
network issues.
Awk command:
Awk command is used for data manipulation and report generation. The awk
command is a scripting language that can be used for processing of text. It is used for
searching words, find and match specific patterns.
String and arithmetic operators, defining variables, defining and usage of controlled
flow and loops, generating user defined and customized reports can be used by the
administrators. The data collected can be manipulated by using the utility tool. This can be
done with regards to the fields used from system and are put in general reports. Compilation
is not required in Linux system for scripting language. Thus logical operations and string
numerical can be easily manipulated.
Main directories:
The main directories is found out by usage of following command:
du -a /home | sort -n -r | head -n 5
The directory which consists of highest user data in operating system’s several different parts
are listed with the help of this command.
Network Interfaces:
All the interfaces can be listed which are available in a system with usage of ip link
show command in Linux distribution’s latest versions. The ip link show command is more
used than the ‘inconfig’ command and the researches have proved it. The ip link command is
more suited than the ‘ifconfig’ command in Linux’s latest versions as the output is better.
This command can be used for utilizing dynamic routing, app containerized and other several
network issues.
Awk command:
Awk command is used for data manipulation and report generation. The awk
command is a scripting language that can be used for processing of text. It is used for
searching words, find and match specific patterns.
String and arithmetic operators, defining variables, defining and usage of controlled
flow and loops, generating user defined and customized reports can be used by the
administrators. The data collected can be manipulated by using the utility tool. This can be
done with regards to the fields used from system and are put in general reports. Compilation
is not required in Linux system for scripting language. Thus logical operations and string
numerical can be easily manipulated.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4COMPUTER SYSTEM AND NETWORK
System administrators and script programmers develop small useful scripts using this
tool. Developing smaller scripts that are useful can be done by the simple commands in
Linux. The scripts helps to extract text patterns and it is essential to health monitoring
structure. This patterns of text are essential for configuration file. The data extracted from
systems are used in a certain report format. The results retrieved when some match is found
during retrieval time can be used too.
Cut command:
The cut command provides more accuracy to the user. A certain character or column
number is extracted from any results or files with this command. It reacts like a filter
command as the field’s delimiter need to be mentioned for cutting out certain column or row.
The delimiter divides the columns in a text so the field sections can be identified.
Operating System Version:
Certain commands are used for finding the operating system’s version installed in
system. The commands cat/etc/os-release are used in the script to find the OS version. The
cat command is elision of “concatenate”. Cat is one of the few commands used mostly in
UNIX and Linux operating system. The users can create a single or multiple files as per
requirements of the user by using the cat command. The data available in a file can be viewed
and the file’s output can be redirected with this command and the file’s data is concatenated
to another file with this command.
Following are some of the screenshots
Changing the permission of the shell script for execution
System administrators and script programmers develop small useful scripts using this
tool. Developing smaller scripts that are useful can be done by the simple commands in
Linux. The scripts helps to extract text patterns and it is essential to health monitoring
structure. This patterns of text are essential for configuration file. The data extracted from
systems are used in a certain report format. The results retrieved when some match is found
during retrieval time can be used too.
Cut command:
The cut command provides more accuracy to the user. A certain character or column
number is extracted from any results or files with this command. It reacts like a filter
command as the field’s delimiter need to be mentioned for cutting out certain column or row.
The delimiter divides the columns in a text so the field sections can be identified.
Operating System Version:
Certain commands are used for finding the operating system’s version installed in
system. The commands cat/etc/os-release are used in the script to find the OS version. The
cat command is elision of “concatenate”. Cat is one of the few commands used mostly in
UNIX and Linux operating system. The users can create a single or multiple files as per
requirements of the user by using the cat command. The data available in a file can be viewed
and the file’s output can be redirected with this command and the file’s data is concatenated
to another file with this command.
Following are some of the screenshots
Changing the permission of the shell script for execution
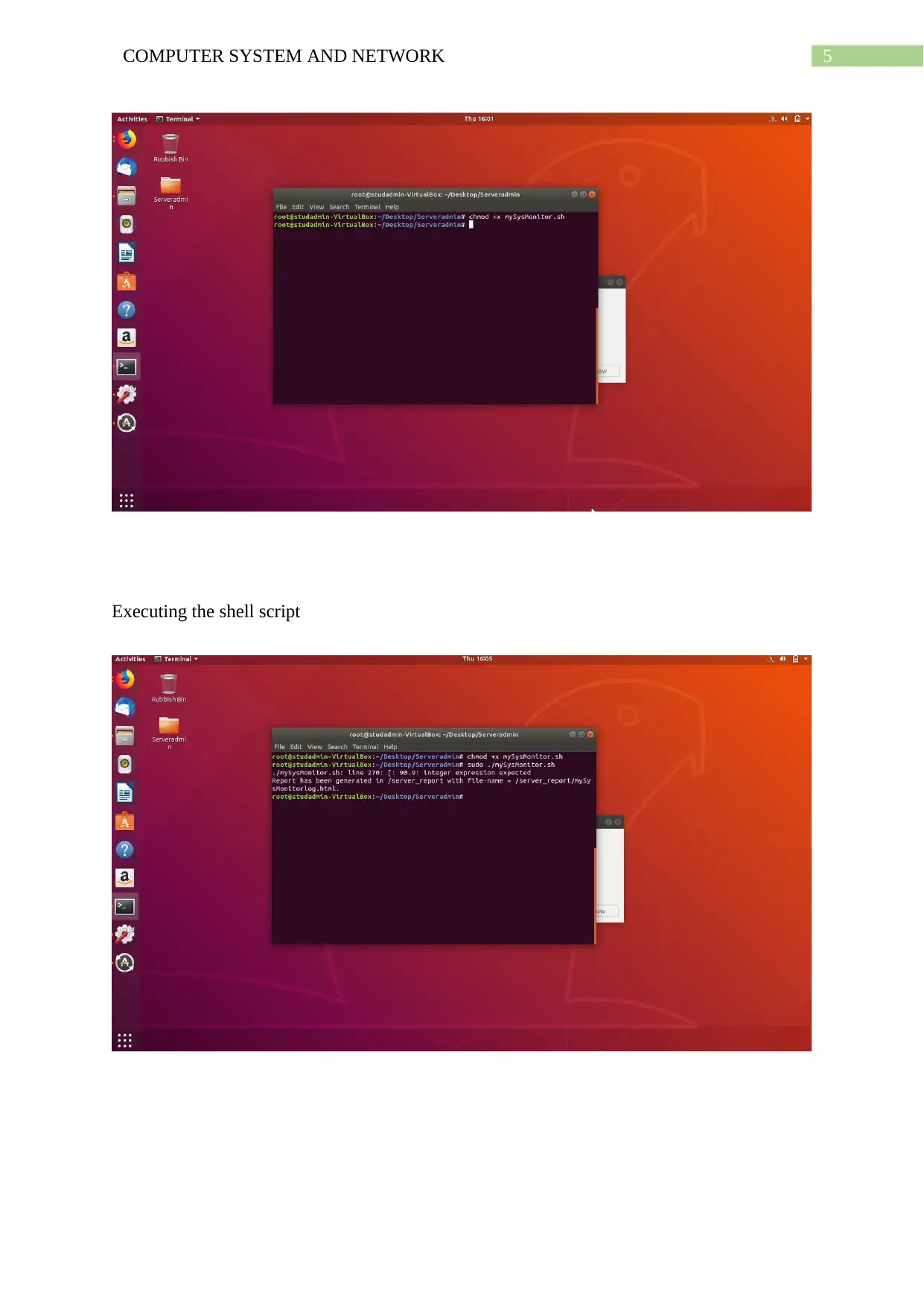
5COMPUTER SYSTEM AND NETWORK
Executing the shell script
Executing the shell script
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
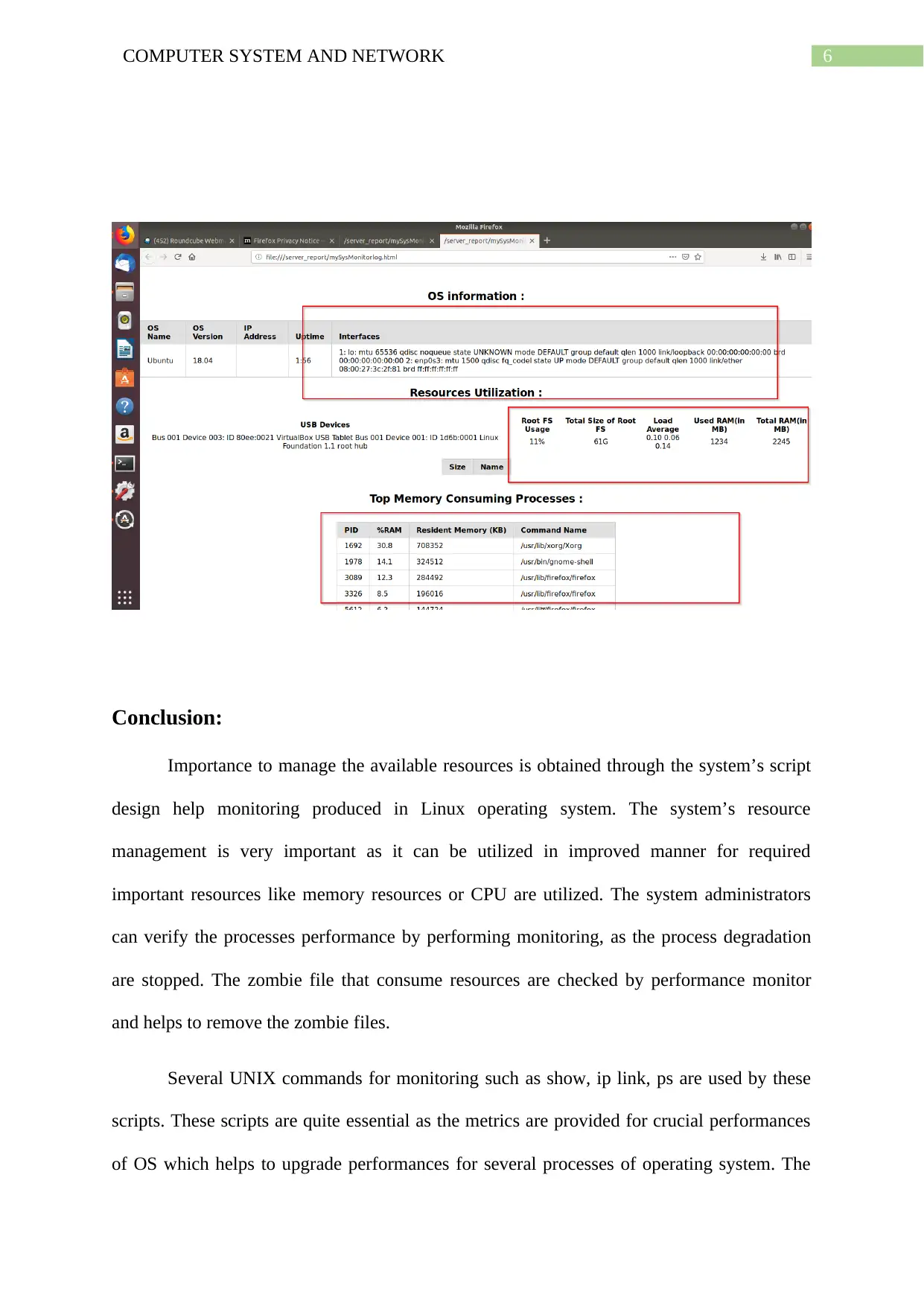
6COMPUTER SYSTEM AND NETWORK
Conclusion:
Importance to manage the available resources is obtained through the system’s script
design help monitoring produced in Linux operating system. The system’s resource
management is very important as it can be utilized in improved manner for required
important resources like memory resources or CPU are utilized. The system administrators
can verify the processes performance by performing monitoring, as the process degradation
are stopped. The zombie file that consume resources are checked by performance monitor
and helps to remove the zombie files.
Several UNIX commands for monitoring such as show, ip link, ps are used by these
scripts. These scripts are quite essential as the metrics are provided for crucial performances
of OS which helps to upgrade performances for several processes of operating system. The
Conclusion:
Importance to manage the available resources is obtained through the system’s script
design help monitoring produced in Linux operating system. The system’s resource
management is very important as it can be utilized in improved manner for required
important resources like memory resources or CPU are utilized. The system administrators
can verify the processes performance by performing monitoring, as the process degradation
are stopped. The zombie file that consume resources are checked by performance monitor
and helps to remove the zombie files.
Several UNIX commands for monitoring such as show, ip link, ps are used by these
scripts. These scripts are quite essential as the metrics are provided for crucial performances
of OS which helps to upgrade performances for several processes of operating system. The
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

7COMPUTER SYSTEM AND NETWORK
system administrator manages the performances for diagnosing the degrading performance’s
cause and bottlenecks of available resources. System performance’s diagnosis with the help
of different tools can be quite time consuming through manual way.
Bibliography
AbdelSalam, A., Clad, F., Filsfils, C., Salsano, S., Siracusano, G. and Veltri, L., 2017, July.
Implementation of virtual network function chaining through segment routing in a linux-
based nfv infrastructure. In 2017 IEEE Conference on Network Softwarization (NetSoft) (pp.
1-5). IEEE.
system administrator manages the performances for diagnosing the degrading performance’s
cause and bottlenecks of available resources. System performance’s diagnosis with the help
of different tools can be quite time consuming through manual way.
Bibliography
AbdelSalam, A., Clad, F., Filsfils, C., Salsano, S., Siracusano, G. and Veltri, L., 2017, July.
Implementation of virtual network function chaining through segment routing in a linux-
based nfv infrastructure. In 2017 IEEE Conference on Network Softwarization (NetSoft) (pp.
1-5). IEEE.

8COMPUTER SYSTEM AND NETWORK
Arnautov, S., Trach, B., Gregor, F., Knauth, T., Martin, A., Priebe, C., Lind, J.,
Muthukumaran, D., O'Keeffe, D., Stillwell, M.L. and Goltzsche, D., 2016. {SCONE}: Secure
Linux Containers with Intel {SGX}. In 12th {USENIX} Symposium on Operating Systems
Design and Implementation ({OSDI} 16) (pp. 689-703).
Barrett, D.J., 2016. Linux Pocket Guide: Essential Commands. " O'Reilly Media, Inc.".
Costache, C., Machidon, O., Mladin, A., Sandu, F. and Bocu, R., 2014, September. Software-
defined networking of linux containers. In 2014 RoEduNet Conference 13th Edition:
Networking in Education and Research Joint Event RENAM 8th Conference (pp. 1-4). IEEE.
Fox, R., 2014. Linux with operating system concepts. Chapman and Hall/CRC.
Gregg, B., 2013. Linux performance analysis and tools. Technical report, Joyent.
Hernantes, J., Gallardo, G. and Serrano, N., 2015. IT infrastructure-monitoring tools. IEEE
Software, 32(4), pp.88-93.
Mittek, M., Carlson, J.D. and Pérez, L.C., 2014, June. Design and implementation of a low-
cost embedded Linux gateway for smart home health monitoring. In IEEE International
Conference on Electro/Information Technology (pp. 485-490). IEEE.
Molloy, D., 2019. Exploring BeagleBone: tools and techniques for building with embedded
Linux. Wiley.
Rosen, R., 2014. Linux containers and the future cloud. Linux J, 240(4), pp.86-95.
Salvador, O. and Angolini, D., 2014. Embedded Linux Development with Yocto Project.
Packt Publishing Ltd.
Salvador, O. and Angolini, D., 2014. Embedded Linux Development with Yocto Project.
Packt Publishing Ltd.
Arnautov, S., Trach, B., Gregor, F., Knauth, T., Martin, A., Priebe, C., Lind, J.,
Muthukumaran, D., O'Keeffe, D., Stillwell, M.L. and Goltzsche, D., 2016. {SCONE}: Secure
Linux Containers with Intel {SGX}. In 12th {USENIX} Symposium on Operating Systems
Design and Implementation ({OSDI} 16) (pp. 689-703).
Barrett, D.J., 2016. Linux Pocket Guide: Essential Commands. " O'Reilly Media, Inc.".
Costache, C., Machidon, O., Mladin, A., Sandu, F. and Bocu, R., 2014, September. Software-
defined networking of linux containers. In 2014 RoEduNet Conference 13th Edition:
Networking in Education and Research Joint Event RENAM 8th Conference (pp. 1-4). IEEE.
Fox, R., 2014. Linux with operating system concepts. Chapman and Hall/CRC.
Gregg, B., 2013. Linux performance analysis and tools. Technical report, Joyent.
Hernantes, J., Gallardo, G. and Serrano, N., 2015. IT infrastructure-monitoring tools. IEEE
Software, 32(4), pp.88-93.
Mittek, M., Carlson, J.D. and Pérez, L.C., 2014, June. Design and implementation of a low-
cost embedded Linux gateway for smart home health monitoring. In IEEE International
Conference on Electro/Information Technology (pp. 485-490). IEEE.
Molloy, D., 2019. Exploring BeagleBone: tools and techniques for building with embedded
Linux. Wiley.
Rosen, R., 2014. Linux containers and the future cloud. Linux J, 240(4), pp.86-95.
Salvador, O. and Angolini, D., 2014. Embedded Linux Development with Yocto Project.
Packt Publishing Ltd.
Salvador, O. and Angolini, D., 2014. Embedded Linux Development with Yocto Project.
Packt Publishing Ltd.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

9COMPUTER SYSTEM AND NETWORK
Tazaki, H., Nakamura, R. and Sekiya, Y., 2015. Library operating system with mainline
Linux network stack. Proceedings of netdev.
Tsai, C. C., Jain, B., Abdul, N. A., & Porter, D. E. (2016, April). A study of modern Linux
API usage and compatibility: what to support when you're supporting. In Proceedings of the
Eleventh European Conference on Computer Systems (p. 16). ACM.
Tazaki, H., Nakamura, R. and Sekiya, Y., 2015. Library operating system with mainline
Linux network stack. Proceedings of netdev.
Tsai, C. C., Jain, B., Abdul, N. A., & Porter, D. E. (2016, April). A study of modern Linux
API usage and compatibility: what to support when you're supporting. In Proceedings of the
Eleventh European Conference on Computer Systems (p. 16). ACM.
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.




