MN603 Wireless Networks: LTE/LTE-A Network Security Evaluation T2 2018
VerifiedAdded on 2023/06/07
|9
|2427
|132
Report
AI Summary
This report provides an evaluation of LTE and LTE-A network security, beginning with a comparison of various cellular network generations (1G, 2G, 3G, 4G, and 5G) and their characteristics. It delves into the architecture of LTE networks, differentiating between the radio access system (E-UTRAN) and the core system (EPC), and outlines the functions of key components such as MME, HSS, SGW, P-SGW, and PCRF. The report identifies and analyzes various attacks on both access and core networks, including IMSI disclosure, radio frequency jamming, DoS/DDoS attacks, and insider attacks, further discussing countermeasures like encryption, cryptography, and firewalls. The conclusion emphasizes the importance of security frameworks, software updates, and cloud-based services to mitigate these risks in LTE networks. Desklib provides access to similar solved assignments and past papers for students.

networksLTE 0
valuation of A etwork SecurityE LTE/LTE- N
valuation of A etwork SecurityE LTE/LTE- N
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

R SLTE NETWO K
1
Introduction
LTE refer as long-term evaluation which
provides modern communication
services to many people and it increased
the performance and efficiency of
cellular networks [1]. There are many
advantages of this network, for example,
higher bandwidth, more effective,
reduced distortion losses [2]. It also
suffers from many attacks and threats
which are explaining in this report and
to achieve LTE security measurements
many security plans developed in the
last few years [2]. The main aim of this
report is to evaluate various cellular
generation and architecture of LTE
network. This report categorises into
four parts, for example, the comparison
between cellular network generations,
LTE architecture, LTE attacks on access
network and core networks, and
identification of biggest LTE attack [3].
Comparison of the existing cellular
networks generations
The wireless network is a system which
is used to produce a communication
step between two or more person [4].
The main concept of this network is that
it can be used to transmit the signal over
long distance and improved
performance of cellular networks [4].
There are various kinds of cellular
networks generation, for example, 1G,
2G, 3G, 4G, and 5G and all this
generation is explaining in this part.
First generation
This technology is completely based on
analogy technology in which an input
signal transmits in the form of analog
signals [5]. This is one of the first
processes which use frequency
modulation and FDD methods for
communication purpose. The frequency
modulation method work on 150 MHz
frequency and a channel bandwidth of
1G is around 30 KHz.
Second generation
This is an advanced generation of
mobile network which uses digital
communication system because analog
technology reduces data speed and
strength of signals [5]. In which digital
modulation technology is used rather
than frequency modulation that
increases the efficiency of mobile
networks. The uplink frequency of 2G is
890 MHz and downlink frequency is 935
MHz and bandwidth of this network is
around 25 MHz [6].
1
Introduction
LTE refer as long-term evaluation which
provides modern communication
services to many people and it increased
the performance and efficiency of
cellular networks [1]. There are many
advantages of this network, for example,
higher bandwidth, more effective,
reduced distortion losses [2]. It also
suffers from many attacks and threats
which are explaining in this report and
to achieve LTE security measurements
many security plans developed in the
last few years [2]. The main aim of this
report is to evaluate various cellular
generation and architecture of LTE
network. This report categorises into
four parts, for example, the comparison
between cellular network generations,
LTE architecture, LTE attacks on access
network and core networks, and
identification of biggest LTE attack [3].
Comparison of the existing cellular
networks generations
The wireless network is a system which
is used to produce a communication
step between two or more person [4].
The main concept of this network is that
it can be used to transmit the signal over
long distance and improved
performance of cellular networks [4].
There are various kinds of cellular
networks generation, for example, 1G,
2G, 3G, 4G, and 5G and all this
generation is explaining in this part.
First generation
This technology is completely based on
analogy technology in which an input
signal transmits in the form of analog
signals [5]. This is one of the first
processes which use frequency
modulation and FDD methods for
communication purpose. The frequency
modulation method work on 150 MHz
frequency and a channel bandwidth of
1G is around 30 KHz.
Second generation
This is an advanced generation of
mobile network which uses digital
communication system because analog
technology reduces data speed and
strength of signals [5]. In which digital
modulation technology is used rather
than frequency modulation that
increases the efficiency of mobile
networks. The uplink frequency of 2G is
890 MHz and downlink frequency is 935
MHz and bandwidth of this network is
around 25 MHz [6].
R SLTE NETWO K
2
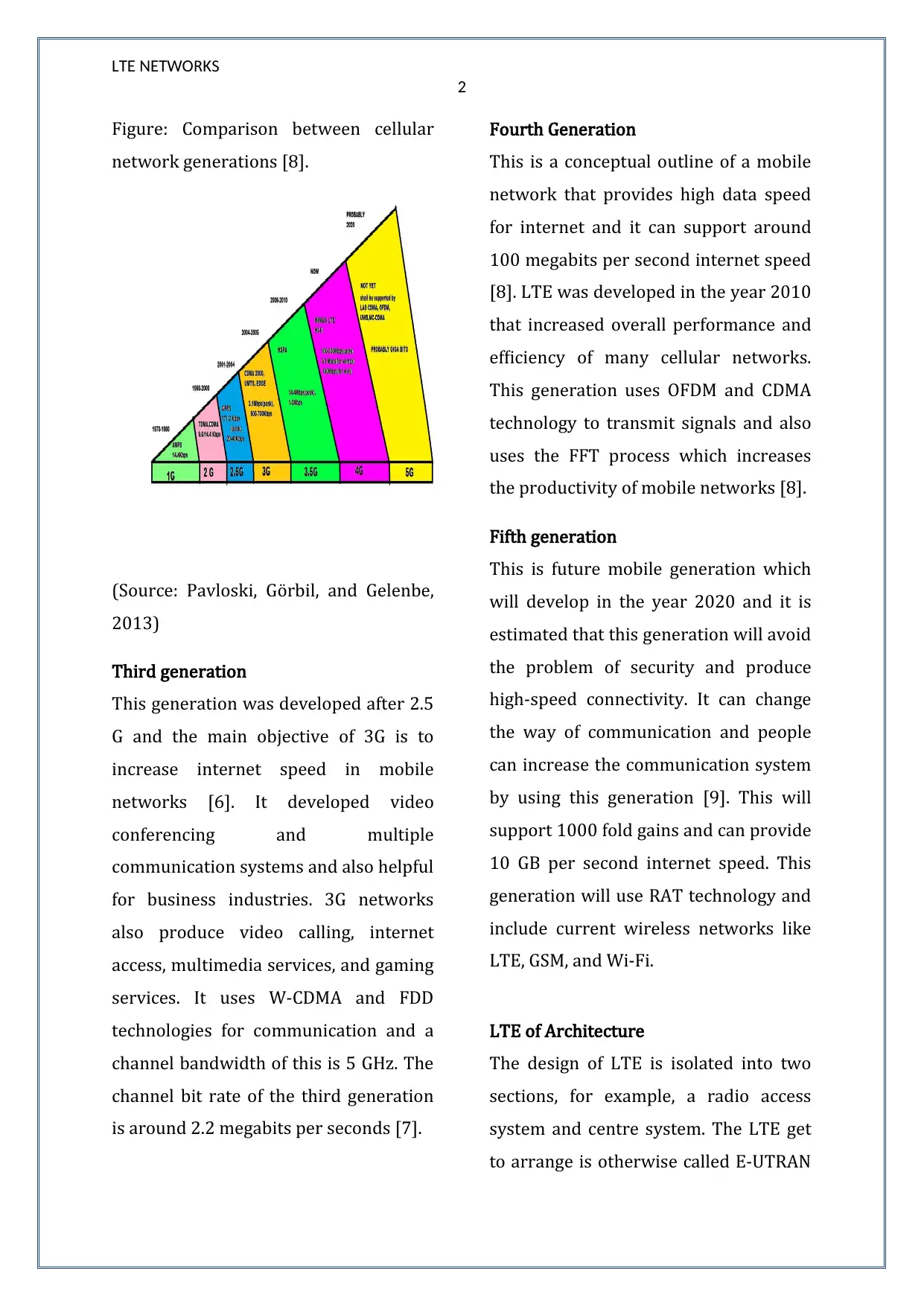
Figure: Comparison between cellular
network generations [8].
(Source: Pavloski, Go9rbil, and Gelenbe,
2013)
Third generation
This generation was developed after 2.5
G and the main objective of 3G is to
increase internet speed in mobile
networks [6]. It developed video
conferencing and multiple
communication systems and also helpful
for business industries. 3G networks
also produce video calling, internet
access, multimedia services, and gaming
services. It uses W-CDMA and FDD
technologies for communication and a
channel bandwidth of this is 5 GHz. The
channel bit rate of the third generation
is around 2.2 megabits per seconds [7].
Fourth Generation
This is a conceptual outline of a mobile
network that provides high data speed
for internet and it can support around
100 megabits per second internet speed
[8]. LTE was developed in the year 2010
that increased overall performance and
efficiency of many cellular networks.
This generation uses OFDM and CDMA
technology to transmit signals and also
uses the FFT process which increases
the productivity of mobile networks [8].
Fifth generation
This is future mobile generation which
will develop in the year 2020 and it is
estimated that this generation will avoid
the problem of security and produce
high-speed connectivity. It can change
the way of communication and people
can increase the communication system
by using this generation [9]. This will
support 1000 fold gains and can provide
10 GB per second internet speed. This
generation will use RAT technology and
include current wireless networks like
LTE, GSM, and Wi-Fi.
LTE of Architecture
The design of LTE is isolated into two
sections, for example, a radio access
system and centre system. The LTE get
to arrange is otherwise called E-UTRAN
2
Figure: Comparison between cellular
network generations [8].
(Source: Pavloski, Go9rbil, and Gelenbe,
2013)
Third generation
This generation was developed after 2.5
G and the main objective of 3G is to
increase internet speed in mobile
networks [6]. It developed video
conferencing and multiple
communication systems and also helpful
for business industries. 3G networks
also produce video calling, internet
access, multimedia services, and gaming
services. It uses W-CDMA and FDD
technologies for communication and a
channel bandwidth of this is 5 GHz. The
channel bit rate of the third generation
is around 2.2 megabits per seconds [7].
Fourth Generation
This is a conceptual outline of a mobile
network that provides high data speed
for internet and it can support around
100 megabits per second internet speed
[8]. LTE was developed in the year 2010
that increased overall performance and
efficiency of many cellular networks.
This generation uses OFDM and CDMA
technology to transmit signals and also
uses the FFT process which increases
the productivity of mobile networks [8].
Fifth generation
This is future mobile generation which
will develop in the year 2020 and it is
estimated that this generation will avoid
the problem of security and produce
high-speed connectivity. It can change
the way of communication and people
can increase the communication system
by using this generation [9]. This will
support 1000 fold gains and can provide
10 GB per second internet speed. This
generation will use RAT technology and
include current wireless networks like
LTE, GSM, and Wi-Fi.
LTE of Architecture
The design of LTE is isolated into two
sections, for example, a radio access
system and centre system. The LTE get
to arrange is otherwise called E-UTRAN
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
R SLTE NETWO K
3
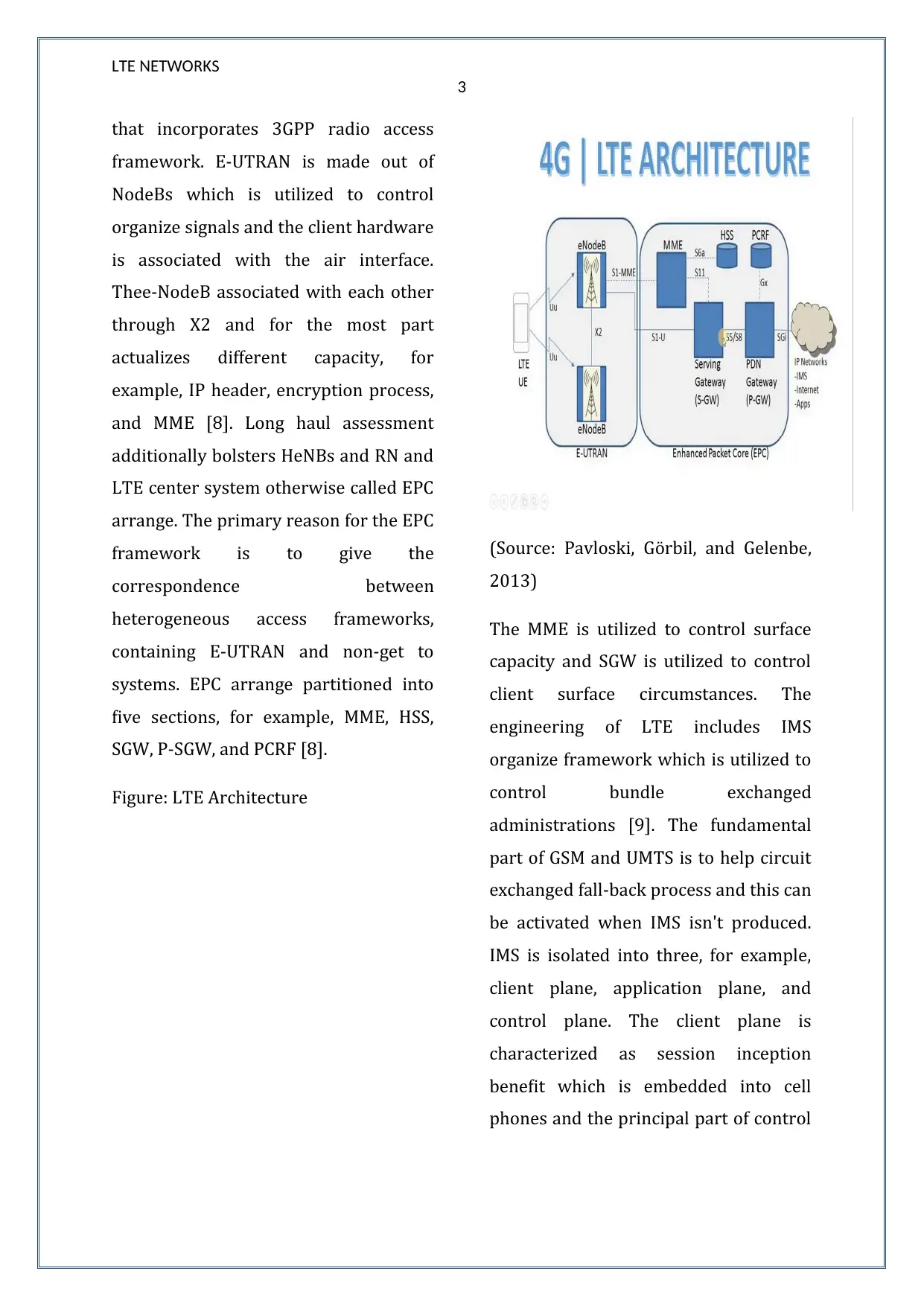
that incorporates 3GPP radio access
framework. E-UTRAN is made out of
NodeBs which is utilized to control
organize signals and the client hardware
is associated with the air interface.
Thee-NodeB associated with each other
through X2 and for the most part
actualizes different capacity, for
example, IP header, encryption process,
and MME [8]. Long haul assessment
additionally bolsters HeNBs and RN and
LTE center system otherwise called EPC
arrange. The primary reason for the EPC
framework is to give the
correspondence between
heterogeneous access frameworks,
containing E-UTRAN and non-get to
systems. EPC arrange partitioned into
five sections, for example, MME, HSS,
SGW, P-SGW, and PCRF [8].
Figure: LTE Architecture
(Source: Pavloski, Go9rbil, and Gelenbe,
2013)
The MME is utilized to control surface
capacity and SGW is utilized to control
client surface circumstances. The
engineering of LTE includes IMS
organize framework which is utilized to
control bundle exchanged
administrations [9]. The fundamental
part of GSM and UMTS is to help circuit
exchanged fall-back process and this can
be activated when IMS isn't produced.
IMS is isolated into three, for example,
client plane, application plane, and
control plane. The client plane is
characterized as session inception
benefit which is embedded into cell
phones and the principal part of control
3
that incorporates 3GPP radio access
framework. E-UTRAN is made out of
NodeBs which is utilized to control
organize signals and the client hardware
is associated with the air interface.
Thee-NodeB associated with each other
through X2 and for the most part
actualizes different capacity, for
example, IP header, encryption process,
and MME [8]. Long haul assessment
additionally bolsters HeNBs and RN and
LTE center system otherwise called EPC
arrange. The primary reason for the EPC
framework is to give the
correspondence between
heterogeneous access frameworks,
containing E-UTRAN and non-get to
systems. EPC arrange partitioned into
five sections, for example, MME, HSS,
SGW, P-SGW, and PCRF [8].
Figure: LTE Architecture
(Source: Pavloski, Go9rbil, and Gelenbe,
2013)
The MME is utilized to control surface
capacity and SGW is utilized to control
client surface circumstances. The
engineering of LTE includes IMS
organize framework which is utilized to
control bundle exchanged
administrations [9]. The fundamental
part of GSM and UMTS is to help circuit
exchanged fall-back process and this can
be activated when IMS isn't produced.
IMS is isolated into three, for example,
client plane, application plane, and
control plane. The client plane is
characterized as session inception
benefit which is embedded into cell
phones and the principal part of control
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

R SLTE NETWO K
4
plane or framework is to control session
of gadgets [10].
The LTE attacks on the access and core
networks
Attacks on Access Network
Disclosure of the International Mobile
Subscriber Identity (IMSI)
It is characterized as a personality
membership framework which is a
distinguishing proof process. It is
watched that numerous individuals
utilize IMSI to distinguish data of any
individual which is the huge issue in
correspondence division. In this cutting-
edge age, numerous associations are
utilizing the wireless system to speak
with other individual yet principle issue
happen in LTE and any remote
framework is that absence of security.
IMSI is where individuals utilize
worldwide supporter character through
which they go into human individual
servers and hack every individual
record [4]. LTE diminish the recurrence
of IMSI over the space interface and in
LTE flag transmitted into the air which
can be effortlessly scrambled or hacked.
In this way, it is researched that IMSI
procedure can diminish human
information or data and furthermore
diminish change information [5].
Radio Frequency jamming
This is an extremely regular issue in
remote correspondence and they
assault on individuals PC framework
and other fringe gadgets [5]. Radio
recurrence sticking targets transmitter
and collector of correspondence
framework and diminish the flag to
clamour proportion of transmitted
signs. For this sort of circumstance,
3GPP proclaim the required recurrence
and time through which individuals can
dodge area assault and DOS assault.
DOS/DDOS ATTACKS
DoS and Distributed Denial of Service
(DDoS) strikes are both genuine attacks
on LTE/LTE-A framework. A
commonplace method for DoS
ambushes is that aggressors send floods
of messages to a target server and
exhaust its CPU resources, influencing
the goal to unfit to offer organizations to
true blue customers [11]. Despite this
sort of DoS attacks, diverse DoS
ambushes constantly manhandle the
loophole in the LTE/LTE-A framework
tradition. In the DDoS attacks,
aggressors can deliver generous
development volume using botnet
directed by Command and Control
Focuses (C&C) or hacked versatile UE
[12].
4
plane or framework is to control session
of gadgets [10].
The LTE attacks on the access and core
networks
Attacks on Access Network
Disclosure of the International Mobile
Subscriber Identity (IMSI)
It is characterized as a personality
membership framework which is a
distinguishing proof process. It is
watched that numerous individuals
utilize IMSI to distinguish data of any
individual which is the huge issue in
correspondence division. In this cutting-
edge age, numerous associations are
utilizing the wireless system to speak
with other individual yet principle issue
happen in LTE and any remote
framework is that absence of security.
IMSI is where individuals utilize
worldwide supporter character through
which they go into human individual
servers and hack every individual
record [4]. LTE diminish the recurrence
of IMSI over the space interface and in
LTE flag transmitted into the air which
can be effortlessly scrambled or hacked.
In this way, it is researched that IMSI
procedure can diminish human
information or data and furthermore
diminish change information [5].
Radio Frequency jamming
This is an extremely regular issue in
remote correspondence and they
assault on individuals PC framework
and other fringe gadgets [5]. Radio
recurrence sticking targets transmitter
and collector of correspondence
framework and diminish the flag to
clamour proportion of transmitted
signs. For this sort of circumstance,
3GPP proclaim the required recurrence
and time through which individuals can
dodge area assault and DOS assault.
DOS/DDOS ATTACKS
DoS and Distributed Denial of Service
(DDoS) strikes are both genuine attacks
on LTE/LTE-A framework. A
commonplace method for DoS
ambushes is that aggressors send floods
of messages to a target server and
exhaust its CPU resources, influencing
the goal to unfit to offer organizations to
true blue customers [11]. Despite this
sort of DoS attacks, diverse DoS
ambushes constantly manhandle the
loophole in the LTE/LTE-A framework
tradition. In the DDoS attacks,
aggressors can deliver generous
development volume using botnet
directed by Command and Control
Focuses (C&C) or hacked versatile UE
[12].

R SLTE NETWO K
5
Attacks on Core Networks
DOS is an extremely basic issue for LTE
or any media transmission association
and DOS assault on centre system by
which they can go into servers. A
versatile botnet is a procedure which is
utilized to set up DOS assaults and
individuals can utilize this to deliver the
surge of dangers. There are primarily
two issues happen into DOS assaults, for
example, over-burden of SGW, and over-
burden of HSS [13].
An insider attack is characterized by
security risk that happens within a
server or PC framework. This sort of
dangers can close down framework
hubs in the centre system and create a
calculation procedure to square
individual documents [13]. It is assessed
that this assault can likewise square
base station through which individuals
can't speak with another individual.
Identify and analyse the attack
DOS/DDOS
DOS attack embeds into individuals
personal servers and programmers
scramble every individual datum or data
records. It happens when any
programmer creates a calculation into
PC frameworks and squares all
individual servers [12]. It creates a
flooding framework which can't re-
establish without the consent of the
assailant and numerous associations'
faces this sort of issue [12].
Programmers target web
administrations of numerous online
networks, servers of managing account
divisions, and other internet-based life
after that they scramble all information
documents and request cash to re-
establish back [11].
Countermeasures
The issue of DOS and DDOS assaults can
be lessened by receiving numerous
security framework and numerous
associations created credible servers
and security designs [10]. There are
different sorts of a process through
which individuals can maintain a
strategic distance from these kinds of
assaults, for instance, the encryption
technique, the cryptography process,
firewall, and example acknowledgment.
Every one of these strategies ought to
lessen numerous dangers and assaults
in remote systems [11].
Conclusion
LTE is a kind of remote system which is
the fourth era cell organizes that stay
away from the issue of long separation
correspondence. This report evaluated
5
Attacks on Core Networks
DOS is an extremely basic issue for LTE
or any media transmission association
and DOS assault on centre system by
which they can go into servers. A
versatile botnet is a procedure which is
utilized to set up DOS assaults and
individuals can utilize this to deliver the
surge of dangers. There are primarily
two issues happen into DOS assaults, for
example, over-burden of SGW, and over-
burden of HSS [13].
An insider attack is characterized by
security risk that happens within a
server or PC framework. This sort of
dangers can close down framework
hubs in the centre system and create a
calculation procedure to square
individual documents [13]. It is assessed
that this assault can likewise square
base station through which individuals
can't speak with another individual.
Identify and analyse the attack
DOS/DDOS
DOS attack embeds into individuals
personal servers and programmers
scramble every individual datum or data
records. It happens when any
programmer creates a calculation into
PC frameworks and squares all
individual servers [12]. It creates a
flooding framework which can't re-
establish without the consent of the
assailant and numerous associations'
faces this sort of issue [12].
Programmers target web
administrations of numerous online
networks, servers of managing account
divisions, and other internet-based life
after that they scramble all information
documents and request cash to re-
establish back [11].
Countermeasures
The issue of DOS and DDOS assaults can
be lessened by receiving numerous
security framework and numerous
associations created credible servers
and security designs [10]. There are
different sorts of a process through
which individuals can maintain a
strategic distance from these kinds of
assaults, for instance, the encryption
technique, the cryptography process,
firewall, and example acknowledgment.
Every one of these strategies ought to
lessen numerous dangers and assaults
in remote systems [11].
Conclusion
LTE is a kind of remote system which is
the fourth era cell organizes that stay
away from the issue of long separation
correspondence. This report evaluated
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

R SLTE NETWO K
6
different types of cellular networks and
engineering of LTE, and different
assaults in LTE systems. There are
numerous assaults identified in LTE, for
example, area following, discloser of
IMSI, DOS assaults, and insider assaults.
Individuals can maintain a strategic
distance from this kind of risk by
utilizing security frameworks, the
encryption process and by receiving
firewall programming. Many
organizations use cloud-based services
to protect their personal information
and people should update their software
on a daily basis.
6
different types of cellular networks and
engineering of LTE, and different
assaults in LTE systems. There are
numerous assaults identified in LTE, for
example, area following, discloser of
IMSI, DOS assaults, and insider assaults.
Individuals can maintain a strategic
distance from this kind of risk by
utilizing security frameworks, the
encryption process and by receiving
firewall programming. Many
organizations use cloud-based services
to protect their personal information
and people should update their software
on a daily basis.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

R SLTE NETWO K
7
References
1. Gupta, T. Verma, S. Bali, and S. Kaul,
‘‘Detecting MS initiated signaling DDoS
attacks in 3G/4G wireless networks,’’ in
Proc. Int. Conf. Commun. Syst. Netw.,
2013, pp. 1–60.
2. M. Pavloski, G. Go9rbil, and E. Gelenbe,
‘‘Bandwidth usage—Based detection of
signaling attacks,’’ Inf. Sci. Syst., vol. 363,
pp. 105–114, Sep. 2015.
3. S. Wahl, K. Rieck, P. Laskov, P.
Domschitz, and K. R. Mu9ller, ‘‘Securing
IMS against novel threats,’’ Bell Labs
Tech. J., vol. 14, no. 1, pp. 243–257,
2009.
4. M. Nassar, R. State, and O. Festor,
‘‘Monitoring SIP traffic using support
vector machines,’’ in Proc. Int.
Workshop Recent Adv. Intrusion
Detection, 2008, pp. 311–330.
5. D. Seo, H. Lee, and E. Nuwere, ‘‘SIPAD:
SIP-VoIP anomaly detection using a
stateful rule tree,’’ Comput. Commun.,
vol. 36, no. 5, pp. 562–574, Mar. 2013.
6. S. Zhang, L. Zhou, M. Wu, Z. Tang, N.
Ruan, and H. Zhu, ‘‘Automatic detection
of SIP-aware attacks on VoLTE device,’’
in Proc. IEEE Veh. Technol. Conf., Sep.
2016, pp. 1–5
7. R.A., Ruiter, L.T., Kessels, G.J.Y. Peters
and G., Kok, “Sixty years of fear appeal
research: Current state of the
evidence.”
International journal of
psychology, vol. 49, no. 2, pp.63-70,
2014.
8. R., Zhang, M., Wang, L.X., Cai, Z., Zheng,
X. Shen and L.L., Xie. “LTE-unlicensed:
the future of spectrum aggregation for
cellular networks.
IEEE Wireless
Communications, vol. 22, no. 3, pp.150-
159, 2015.
9. A., Laya, L. Alonso and J., Alonso, “Is
the Random Access Channel of LTE and
LTE-A Suitable for M2M
Communications? A Survey of
Alternatives.”
IEEE Communications
Surveys and Tutorials, vol. 16, no. 1,
pp.4-16, 2014.
10. J., Lee, Y., Kim, Y., Kwak, J., Zhang, A.,
Papasakellariou, T., Nolan, C. Sun and Y.,
Li. “LTE-advanced in 3GPP Rel-13/14:
an evolution toward 5G.”
IEEE
Communications Magazine, vol. 54, no.
3, pp.36-42, 2016.
7
References
1. Gupta, T. Verma, S. Bali, and S. Kaul,
‘‘Detecting MS initiated signaling DDoS
attacks in 3G/4G wireless networks,’’ in
Proc. Int. Conf. Commun. Syst. Netw.,
2013, pp. 1–60.
2. M. Pavloski, G. Go9rbil, and E. Gelenbe,
‘‘Bandwidth usage—Based detection of
signaling attacks,’’ Inf. Sci. Syst., vol. 363,
pp. 105–114, Sep. 2015.
3. S. Wahl, K. Rieck, P. Laskov, P.
Domschitz, and K. R. Mu9ller, ‘‘Securing
IMS against novel threats,’’ Bell Labs
Tech. J., vol. 14, no. 1, pp. 243–257,
2009.
4. M. Nassar, R. State, and O. Festor,
‘‘Monitoring SIP traffic using support
vector machines,’’ in Proc. Int.
Workshop Recent Adv. Intrusion
Detection, 2008, pp. 311–330.
5. D. Seo, H. Lee, and E. Nuwere, ‘‘SIPAD:
SIP-VoIP anomaly detection using a
stateful rule tree,’’ Comput. Commun.,
vol. 36, no. 5, pp. 562–574, Mar. 2013.
6. S. Zhang, L. Zhou, M. Wu, Z. Tang, N.
Ruan, and H. Zhu, ‘‘Automatic detection
of SIP-aware attacks on VoLTE device,’’
in Proc. IEEE Veh. Technol. Conf., Sep.
2016, pp. 1–5
7. R.A., Ruiter, L.T., Kessels, G.J.Y. Peters
and G., Kok, “Sixty years of fear appeal
research: Current state of the
evidence.”
International journal of
psychology, vol. 49, no. 2, pp.63-70,
2014.
8. R., Zhang, M., Wang, L.X., Cai, Z., Zheng,
X. Shen and L.L., Xie. “LTE-unlicensed:
the future of spectrum aggregation for
cellular networks.
IEEE Wireless
Communications, vol. 22, no. 3, pp.150-
159, 2015.
9. A., Laya, L. Alonso and J., Alonso, “Is
the Random Access Channel of LTE and
LTE-A Suitable for M2M
Communications? A Survey of
Alternatives.”
IEEE Communications
Surveys and Tutorials, vol. 16, no. 1,
pp.4-16, 2014.
10. J., Lee, Y., Kim, Y., Kwak, J., Zhang, A.,
Papasakellariou, T., Nolan, C. Sun and Y.,
Li. “LTE-advanced in 3GPP Rel-13/14:
an evolution toward 5G.”
IEEE
Communications Magazine, vol. 54, no.
3, pp.36-42, 2016.

R SLTE NETWO K
8
11. A., Al, S., Ni, Q. Rubaye and E., Sousa,
“5G communications race: Pursuit of
more capacity triggers LTE in an
unlicensed band.”
IEEE vehicular
technology magazine, vol. 10, no. 1,
pp.43-51, 2015.
12. S., Deb, P., Monogioudis, J. Miernik
and J.P., Seymour, “Algorithms for
enhanced inter-cell interference
coordination (eICIC) in LTE
HetNets.”
IEEE/ACM transactions on
networking, vol. 22, no.1, pp.137-150,
2014.
13. P., Bru9ll, L.T., Kessels, L., Repetto, A.
Dirkson and R.A., Ruiter. “ERPs Reveal
Disengagement Processes Related to
Condom Use Embarrassment in
Intention-Behavior Inconsistent Young
Adults.”
Archives of sexual behavior, vol.
12, pp.1-12, 2018.
8
11. A., Al, S., Ni, Q. Rubaye and E., Sousa,
“5G communications race: Pursuit of
more capacity triggers LTE in an
unlicensed band.”
IEEE vehicular
technology magazine, vol. 10, no. 1,
pp.43-51, 2015.
12. S., Deb, P., Monogioudis, J. Miernik
and J.P., Seymour, “Algorithms for
enhanced inter-cell interference
coordination (eICIC) in LTE
HetNets.”
IEEE/ACM transactions on
networking, vol. 22, no.1, pp.137-150,
2014.
13. P., Bru9ll, L.T., Kessels, L., Repetto, A.
Dirkson and R.A., Ruiter. “ERPs Reveal
Disengagement Processes Related to
Condom Use Embarrassment in
Intention-Behavior Inconsistent Young
Adults.”
Archives of sexual behavior, vol.
12, pp.1-12, 2018.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 9
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





