Network Analysis: TCP/IP Networking Report for M2M Organization
VerifiedAdded on 2020/02/24
|10
|1538
|72
Report
AI Summary
This report provides a detailed analysis of TCP/IP networking within the context of an M2M organization. It begins with an introduction to computer networks and network protocols, including ATM, Token Ring, Ethernet, and FDDI. The report outlines the proposed network infrastructure for the M2M organization, detailing its six buildings, departments, and workstation distribution. A network diagram illustrates the connections between buildings, routers, and workstations. The report then covers IP addressing schemes for each building. Task 2 delves into the role of network analyzers, emphasizing their importance in network troubleshooting and security. It highlights the capabilities of Wireshark, a prominent network analyzer, including its features and purpose. The report recommends the implementation of Wireshark to improve network efficiency and security, addressing the organization's current policy against network analyzer tools. The report concludes with a list of references used in the analysis. This report is aimed at helping the M2M organization to improve their network infrastructure.

TCP/IP NETWORKING
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Table of Contents
Task – 1................................................................................................................................................2
Introduction.....................................................................................................................................2
Network diagram.............................................................................................................................3
IP addressing....................................................................................................................................5
Task – 2................................................................................................................................................6
Role of Network analyser................................................................................................................6
Purpose of Wireshark.....................................................................................................................7
Features of wireshark......................................................................................................................8
Recommendations............................................................................................................................8
1
Task – 1................................................................................................................................................2
Introduction.....................................................................................................................................2
Network diagram.............................................................................................................................3
IP addressing....................................................................................................................................5
Task – 2................................................................................................................................................6
Role of Network analyser................................................................................................................6
Purpose of Wireshark.....................................................................................................................7
Features of wireshark......................................................................................................................8
Recommendations............................................................................................................................8
1

Task – 1
Introduction
A computer network is the infrastructure and it used to allow more than one computer to
communication with each other. This process is achieving by providing the collection of
communication rule is called as protocols. The Protocols are observed by participating hosts.
The collection of network protocol rules are includes the following characteristics of the
network such as data transfer speed, access method, cable types and physical topologies. The
Network protocols are listed below ("A brief explanation of computer network protocols",
2017).
ATM
Token ring
Local talk
Ethernet
FDDI
The M2M solutions contains the six building. Each building has the various departments.
The Building are connected with the network by using router. The M2M solutions proposed
network infrastructure provide the high efficiency and scalability of the network. It using the
network analysers to reduce the troubleshooting problems. The company contains the 1200
work stations. These are divided into six building. Six building are Head office, Information
technology, Sales office, transport office, finance office and research office. The Proposed
network infrastructure is will be discussed. It use the network analyser tool that is wireshark
to reduce the trouble shooting issues in the network. The Current company policies does not
allow the network analyser tools for the network. But the network Analysers tool provides the
effective network. So the Company management team interested to using the network
analyser tool. So gives the network analysers proposal for company board. So the staff are
analyse the best network analyser tool and their features, benefits, recommendations and how
it support the proposed network infrastructure. These informations are once gathered and then
it provided to company board. The network analyser tools are will be discuss (Callahan, n.d.).
2
Introduction
A computer network is the infrastructure and it used to allow more than one computer to
communication with each other. This process is achieving by providing the collection of
communication rule is called as protocols. The Protocols are observed by participating hosts.
The collection of network protocol rules are includes the following characteristics of the
network such as data transfer speed, access method, cable types and physical topologies. The
Network protocols are listed below ("A brief explanation of computer network protocols",
2017).
ATM
Token ring
Local talk
Ethernet
FDDI
The M2M solutions contains the six building. Each building has the various departments.
The Building are connected with the network by using router. The M2M solutions proposed
network infrastructure provide the high efficiency and scalability of the network. It using the
network analysers to reduce the troubleshooting problems. The company contains the 1200
work stations. These are divided into six building. Six building are Head office, Information
technology, Sales office, transport office, finance office and research office. The Proposed
network infrastructure is will be discussed. It use the network analyser tool that is wireshark
to reduce the trouble shooting issues in the network. The Current company policies does not
allow the network analyser tools for the network. But the network Analysers tool provides the
effective network. So the Company management team interested to using the network
analyser tool. So gives the network analysers proposal for company board. So the staff are
analyse the best network analyser tool and their features, benefits, recommendations and how
it support the proposed network infrastructure. These informations are once gathered and then
it provided to company board. The network analyser tools are will be discuss (Callahan, n.d.).
2
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
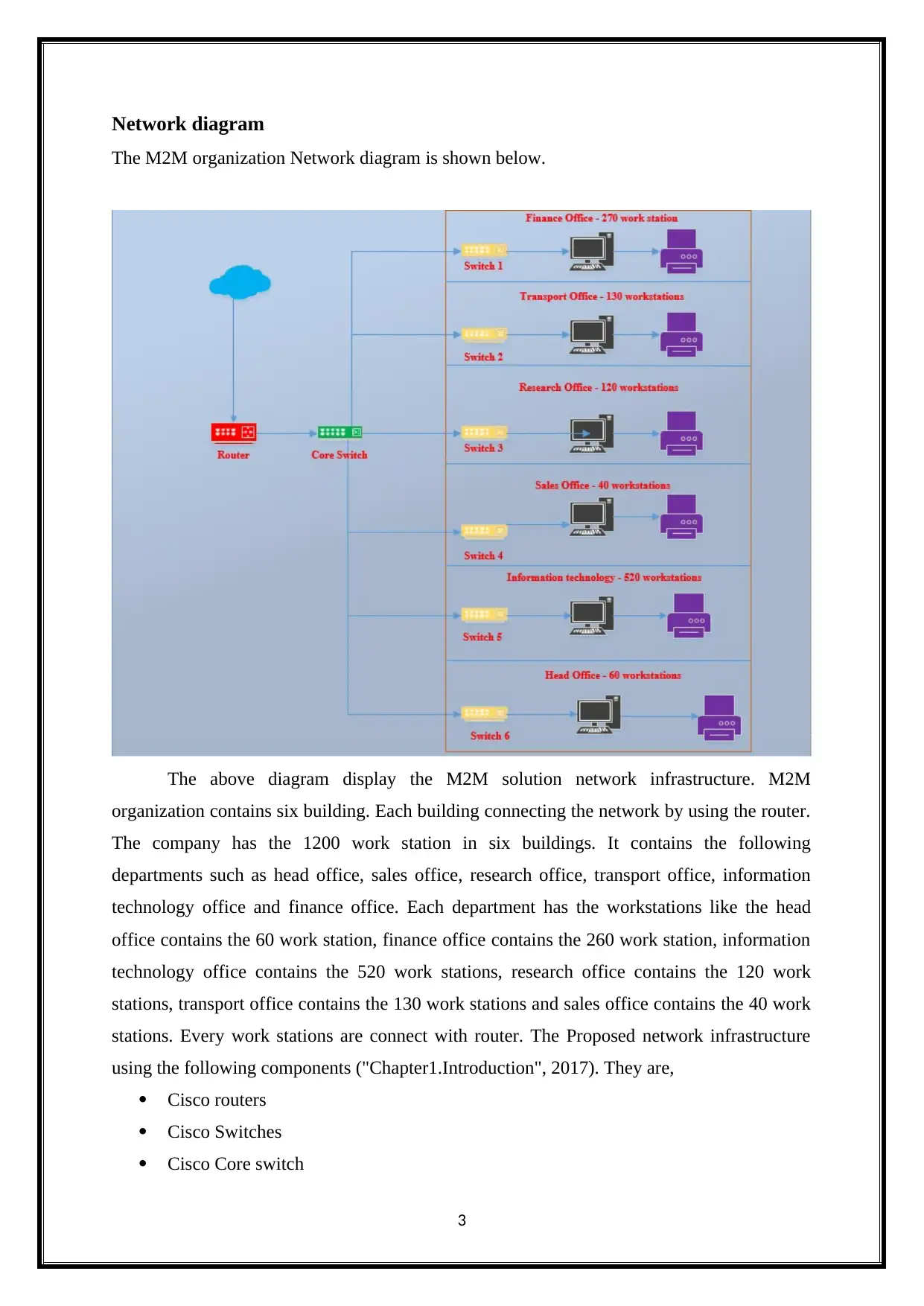
Network diagram
The M2M organization Network diagram is shown below.
The above diagram display the M2M solution network infrastructure. M2M
organization contains six building. Each building connecting the network by using the router.
The company has the 1200 work station in six buildings. It contains the following
departments such as head office, sales office, research office, transport office, information
technology office and finance office. Each department has the workstations like the head
office contains the 60 work station, finance office contains the 260 work station, information
technology office contains the 520 work stations, research office contains the 120 work
stations, transport office contains the 130 work stations and sales office contains the 40 work
stations. Every work stations are connect with router. The Proposed network infrastructure
using the following components ("Chapter1.Introduction", 2017). They are,
Cisco routers
Cisco Switches
Cisco Core switch
3
The M2M organization Network diagram is shown below.
The above diagram display the M2M solution network infrastructure. M2M
organization contains six building. Each building connecting the network by using the router.
The company has the 1200 work station in six buildings. It contains the following
departments such as head office, sales office, research office, transport office, information
technology office and finance office. Each department has the workstations like the head
office contains the 60 work station, finance office contains the 260 work station, information
technology office contains the 520 work stations, research office contains the 120 work
stations, transport office contains the 130 work stations and sales office contains the 40 work
stations. Every work stations are connect with router. The Proposed network infrastructure
using the following components ("Chapter1.Introduction", 2017). They are,
Cisco routers
Cisco Switches
Cisco Core switch
3
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

Cisco application server
Cisco authentication server
Cisco main Server
PC
Printer
The cisco products are used to provide the effective network. It reduce the business costs.
The Cisco products are also support the medium size organization. It provides the high
security and scalability of the network.
IP addressing
M2M organization network infrastructure IP addressing for each building is shown below
("Five free network analyzers worth any IT admin's time", 2017).
10.0.0.0/22 (Building 1)
10.1.0.0/22 (Building 2)
10.2.0.0/22 (Building 3)
4
Cisco authentication server
Cisco main Server
PC
Printer
The cisco products are used to provide the effective network. It reduce the business costs.
The Cisco products are also support the medium size organization. It provides the high
security and scalability of the network.
IP addressing
M2M organization network infrastructure IP addressing for each building is shown below
("Five free network analyzers worth any IT admin's time", 2017).
10.0.0.0/22 (Building 1)
10.1.0.0/22 (Building 2)
10.2.0.0/22 (Building 3)
4
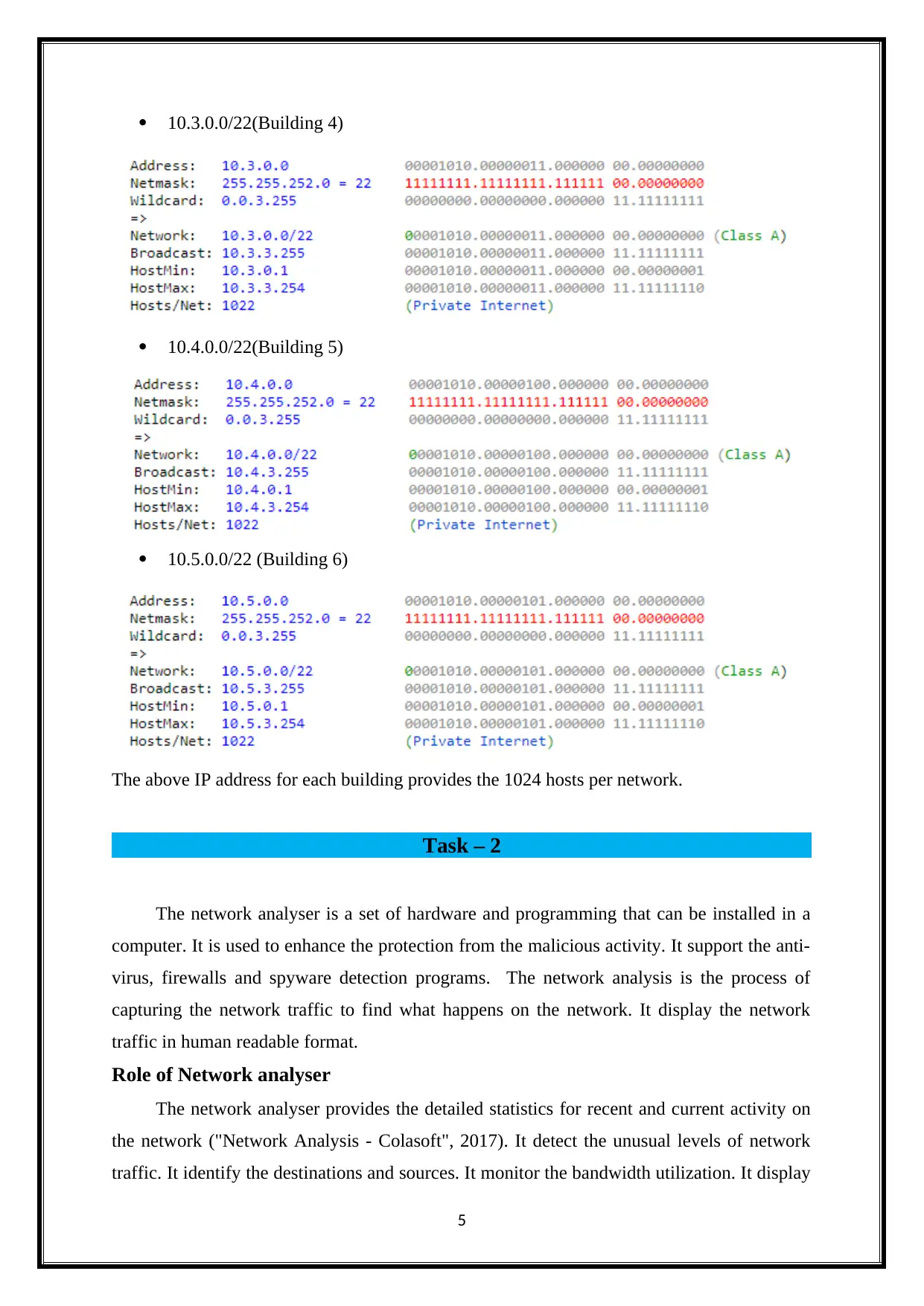
10.3.0.0/22(Building 4)
10.4.0.0/22(Building 5)
10.5.0.0/22 (Building 6)
The above IP address for each building provides the 1024 hosts per network.
Task – 2
The network analyser is a set of hardware and programming that can be installed in a
computer. It is used to enhance the protection from the malicious activity. It support the anti-
virus, firewalls and spyware detection programs. The network analysis is the process of
capturing the network traffic to find what happens on the network. It display the network
traffic in human readable format.
Role of Network analyser
The network analyser provides the detailed statistics for recent and current activity on
the network ("Network Analysis - Colasoft", 2017). It detect the unusual levels of network
traffic. It identify the destinations and sources. It monitor the bandwidth utilization. It display
5
10.4.0.0/22(Building 5)
10.5.0.0/22 (Building 6)
The above IP address for each building provides the 1024 hosts per network.
Task – 2
The network analyser is a set of hardware and programming that can be installed in a
computer. It is used to enhance the protection from the malicious activity. It support the anti-
virus, firewalls and spyware detection programs. The network analysis is the process of
capturing the network traffic to find what happens on the network. It display the network
traffic in human readable format.
Role of Network analyser
The network analyser provides the detailed statistics for recent and current activity on
the network ("Network Analysis - Colasoft", 2017). It detect the unusual levels of network
traffic. It identify the destinations and sources. It monitor the bandwidth utilization. It display
5
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

the all statistics on a user friendly. The Network analyser is used to define the conventions
and rules for communication between the network devices. It include the device mechanisms
to identify and create the connection with each other. It also specify and formatting the data.
It support the data compression and message acknowledgement for high performance. The
network analyser using the packet switching techniques to send and receive the messages.
The network analyser easily detecting the compromised computer and discovering the faulty
network card. It prevent the cyber-crime from the network intrusion detection. It easily
analysis the applications operations.
The M2M organization current policy does not allow the use of network analysers. But
the network analyser tools provides the efficiency in network troubleshooting processes. The
Most power network analyser is Wireshark. It is used to capture the network packets and it
provide the packet details ("What's a Wireshark Network Protocol Analyzer?", 2017).
Purpose of Wireshark
The network administrators are using the wireshark for network troubleshooting
problems
The network developers are using the wireshark to debug the protocol
implementations
The network security engineers are using the wireshark to examine the security
problems ("Network Protocol - Types of Network Protocols", 2017).
6
and rules for communication between the network devices. It include the device mechanisms
to identify and create the connection with each other. It also specify and formatting the data.
It support the data compression and message acknowledgement for high performance. The
network analyser using the packet switching techniques to send and receive the messages.
The network analyser easily detecting the compromised computer and discovering the faulty
network card. It prevent the cyber-crime from the network intrusion detection. It easily
analysis the applications operations.
The M2M organization current policy does not allow the use of network analysers. But
the network analyser tools provides the efficiency in network troubleshooting processes. The
Most power network analyser is Wireshark. It is used to capture the network packets and it
provide the packet details ("What's a Wireshark Network Protocol Analyzer?", 2017).
Purpose of Wireshark
The network administrators are using the wireshark for network troubleshooting
problems
The network developers are using the wireshark to debug the protocol
implementations
The network security engineers are using the wireshark to examine the security
problems ("Network Protocol - Types of Network Protocols", 2017).
6
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
Features of wireshark
It support the windows and Linux.
It create the various statistics.
It saves the captured packets.
It easily import the packet data to text file includes the hex dumps.
It capture the live packet data from the internet (Sanders, n.d.).
The wireshark is a protocol analyser and it used to solve the network problems. The
hackers are using the wireshark to hack the computer. The wireshark is the ability to capture
the network traffic in the network. When trouble shooting problems are occur most of the
professionals are using the black approach but it does not provides the effective network. So
provides the effective network by using the wireshark. It check everything in the internet site
and computer. It capture the network traffic being exchanged by out computer and network.
The hackers also using the wireshark to hack (Shimonski, 2013). The most network protocols
are designed for security but the HTTP, TELNET and FTP protocols are non-secure
protocols. The wireshark capture your login session that is user name and password. So the
hackers are easily hack another computer user name and password.
7
It support the windows and Linux.
It create the various statistics.
It saves the captured packets.
It easily import the packet data to text file includes the hex dumps.
It capture the live packet data from the internet (Sanders, n.d.).
The wireshark is a protocol analyser and it used to solve the network problems. The
hackers are using the wireshark to hack the computer. The wireshark is the ability to capture
the network traffic in the network. When trouble shooting problems are occur most of the
professionals are using the black approach but it does not provides the effective network. So
provides the effective network by using the wireshark. It check everything in the internet site
and computer. It capture the network traffic being exchanged by out computer and network.
The hackers also using the wireshark to hack (Shimonski, 2013). The most network protocols
are designed for security but the HTTP, TELNET and FTP protocols are non-secure
protocols. The wireshark capture your login session that is user name and password. So the
hackers are easily hack another computer user name and password.
7

Recommendations
The Proposed network infrastructure using the network analyser tool to provide the
secure and effective network ("What is network analyzer (protocol analyzer or packet
analyzer)? - Definition from WhatIs.com", 2017). The Best network analysis tool is
wireshark. The wireshark is used to provide the effective network to solve the network issues.
It capture the network traffic from the network. So M2M organization decided to use the
wireshark network analyser tool to reduce the network problems. The organization team
members are fully analysed the wireshark tools and provide the information the organization
board. The M2M organization using the wireshark tool to provides the scalable and flexible
network for the staff. It helps to optimize the business costs.
References
A brief explanation of computer network protocols. (2017). Lifewire. Retrieved 31 August
2017, from https://www.lifewire.com/definition-of-protocol-network-817949
Callahan, M. Wireshark.
Chapter�1.�Introduction. (2017). Wireshark.org. Retrieved 31 August 2017, from
https://www.wireshark.org/docs/wsug_html_chunked/ChapterIntroduction.html
Five free network analyzers worth any IT admin's time. (2017). TechRepublic. Retrieved 31
August 2017, from http://www.techrepublic.com/blog/five-apps/five-free-network-
analyzers-worth-any-it-admins-time/
Network Analysis - Colasoft. (2017). Colasoft.com. Retrieved 31 August 2017, from
http://www.colasoft.com/resources/network_analysis.php
Network Protocol - Types of Network Protocols. (2017). Edrawsoft.com. Retrieved 31 August
2017, from https://www.edrawsoft.com/Network-Protocol.php
Sanders, C. Practical packet analysis.
Shimonski, R. (2013). The wireshark field guide. Amsterdam: Syngress.
What is network analyzer (protocol analyzer or packet analyzer)? - Definition from
WhatIs.com. (2017). SearchNetworking. Retrieved 31 August 2017, from
http://searchnetworking.techtarget.com/definition/network-analyzer
8
The Proposed network infrastructure using the network analyser tool to provide the
secure and effective network ("What is network analyzer (protocol analyzer or packet
analyzer)? - Definition from WhatIs.com", 2017). The Best network analysis tool is
wireshark. The wireshark is used to provide the effective network to solve the network issues.
It capture the network traffic from the network. So M2M organization decided to use the
wireshark network analyser tool to reduce the network problems. The organization team
members are fully analysed the wireshark tools and provide the information the organization
board. The M2M organization using the wireshark tool to provides the scalable and flexible
network for the staff. It helps to optimize the business costs.
References
A brief explanation of computer network protocols. (2017). Lifewire. Retrieved 31 August
2017, from https://www.lifewire.com/definition-of-protocol-network-817949
Callahan, M. Wireshark.
Chapter�1.�Introduction. (2017). Wireshark.org. Retrieved 31 August 2017, from
https://www.wireshark.org/docs/wsug_html_chunked/ChapterIntroduction.html
Five free network analyzers worth any IT admin's time. (2017). TechRepublic. Retrieved 31
August 2017, from http://www.techrepublic.com/blog/five-apps/five-free-network-
analyzers-worth-any-it-admins-time/
Network Analysis - Colasoft. (2017). Colasoft.com. Retrieved 31 August 2017, from
http://www.colasoft.com/resources/network_analysis.php
Network Protocol - Types of Network Protocols. (2017). Edrawsoft.com. Retrieved 31 August
2017, from https://www.edrawsoft.com/Network-Protocol.php
Sanders, C. Practical packet analysis.
Shimonski, R. (2013). The wireshark field guide. Amsterdam: Syngress.
What is network analyzer (protocol analyzer or packet analyzer)? - Definition from
WhatIs.com. (2017). SearchNetworking. Retrieved 31 August 2017, from
http://searchnetworking.techtarget.com/definition/network-analyzer
8
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
What's a Wireshark Network Protocol Analyzer?. (2017). Lifewire. Retrieved 31 August
2017, from https://www.lifewire.com/wireshark-network-protocol-analyzer-2487928
9
2017, from https://www.lifewire.com/wireshark-network-protocol-analyzer-2487928
9
1 out of 10
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





