Comprehensive TCP/IP Networking Design and Analysis for M2M Solutions
VerifiedAdded on 2020/02/24
|21
|4464
|99
Report
AI Summary
This report presents a comprehensive network design and analysis for M2M Solutions, a company expanding its operations across six different locations in Sydney, Australia. The report begins with an executive summary outlining the need for a robust network to connect approximately 1200 workstations across the company's various departments. Task 1 focuses on network architecture design, including network diagrams, required devices (switches, workstations), and subnet calculation methods to efficiently utilize IP addresses based on the ring topology. The report details the subnetting process for each department, considering the number of workstations and the need for future scalability. Configuration methods for accessing and configuring the network devices are also discussed. Task 2 delves into network analysis, including the use of network analyzers and relevant networking protocols. The report analyzes the advantages of network analysis for M2M Solutions, and potential challenges if the number of hosts increases significantly. The report reasons that static organizing is the better coordinating custom in this situation where divisions are restricted, and it will assist the system controller with impacting the system more to secure adjacent the structure separating contraptions that were prior not permitted to use the authoritative premises.

Running head: TCP/IP NETWORKING
Assignment Number
Assignment Title: TCP/IP Networking
Student Name:
Student ID:
Student Email:
Assignment Number
Assignment Title: TCP/IP Networking
Student Name:
Student ID:
Student Email:
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TCP/IP NETWORKING
Executive Summary
M2M Solutions, a medium evaluated company, based in Sydney, Australia is predicting extending its
operations. Likewise, the affiliation has practical expanded six distinct regions of the city to suit its six
working environments. Those are its Finance Office, Head Office, Information Technology, Transport
Office, Research Office and Sales Office. Prior each one of the units was masterminded in a similar
building, yet now in the wake of moving the divisions to new places, it will be required to assemble a
cover arrange all its business exchanges over the working environments. Starting at now, the aggregate
number of workstations being used is around 1200. This report watches out for all the essential strides
to take after to manufacture a structure over those locales where each site will have their sub interface
with surrendering a few spaces for development in some workstations. Also, it is additionally essential
to use the vast majority of the IP territories and squandering the base number of IPs in this philosophy
of the diagram. This report reasons that static organising is the better coordinating custom in this
situation where divisions are restricted, and it will assist the system controller with impacting the system
more to secure adjacent the structure isolating contraptions that were prior not permitted to use the
authoritative premises. In this manner, the report reveals every single one of the approaches to take
after for the use of noteworthy system openness in the association.
Student Name Student Number
Executive Summary
M2M Solutions, a medium evaluated company, based in Sydney, Australia is predicting extending its
operations. Likewise, the affiliation has practical expanded six distinct regions of the city to suit its six
working environments. Those are its Finance Office, Head Office, Information Technology, Transport
Office, Research Office and Sales Office. Prior each one of the units was masterminded in a similar
building, yet now in the wake of moving the divisions to new places, it will be required to assemble a
cover arrange all its business exchanges over the working environments. Starting at now, the aggregate
number of workstations being used is around 1200. This report watches out for all the essential strides
to take after to manufacture a structure over those locales where each site will have their sub interface
with surrendering a few spaces for development in some workstations. Also, it is additionally essential
to use the vast majority of the IP territories and squandering the base number of IPs in this philosophy
of the diagram. This report reasons that static organising is the better coordinating custom in this
situation where divisions are restricted, and it will assist the system controller with impacting the system
more to secure adjacent the structure isolating contraptions that were prior not permitted to use the
authoritative premises. In this manner, the report reveals every single one of the approaches to take
after for the use of noteworthy system openness in the association.
Student Name Student Number

2TCP/IP NETWORKING
Table of Contents
TASK 1: Network Architecture Designing.....................................................................................................3
1.1 Network Designing...................................................................................................................3
1.1.1 Network Diagram Design..........................................................................................3
1.1.2 Required Devices for the Network............................................................................4
1.1.3 Subnet Calculation Method......................................................................................4
1.1.4 Configuration Method............................................................................................10
1.2 What if host number increases over 1024 per department ?.................................................11
1.2.1 Difficulties...............................................................................................................11
TASK 2: Network Analysis..........................................................................................................................12
2.1 Network Analyser...................................................................................................................12
2.1.1 Network Analysing Processes.................................................................................12
2.1.2 Networking Protocols.............................................................................................13
2.1.3 Situations when Network Analyser helps................................................................17
2.2 Network Analysis of M2M Solution........................................................................................18
2.2.1 Advantages of Network Analysis.............................................................................18
Recommendation.........................................................................................................................19
References.................................................................................................................................................20
Student Name Student Number
Table of Contents
TASK 1: Network Architecture Designing.....................................................................................................3
1.1 Network Designing...................................................................................................................3
1.1.1 Network Diagram Design..........................................................................................3
1.1.2 Required Devices for the Network............................................................................4
1.1.3 Subnet Calculation Method......................................................................................4
1.1.4 Configuration Method............................................................................................10
1.2 What if host number increases over 1024 per department ?.................................................11
1.2.1 Difficulties...............................................................................................................11
TASK 2: Network Analysis..........................................................................................................................12
2.1 Network Analyser...................................................................................................................12
2.1.1 Network Analysing Processes.................................................................................12
2.1.2 Networking Protocols.............................................................................................13
2.1.3 Situations when Network Analyser helps................................................................17
2.2 Network Analysis of M2M Solution........................................................................................18
2.2.1 Advantages of Network Analysis.............................................................................18
Recommendation.........................................................................................................................19
References.................................................................................................................................................20
Student Name Student Number
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
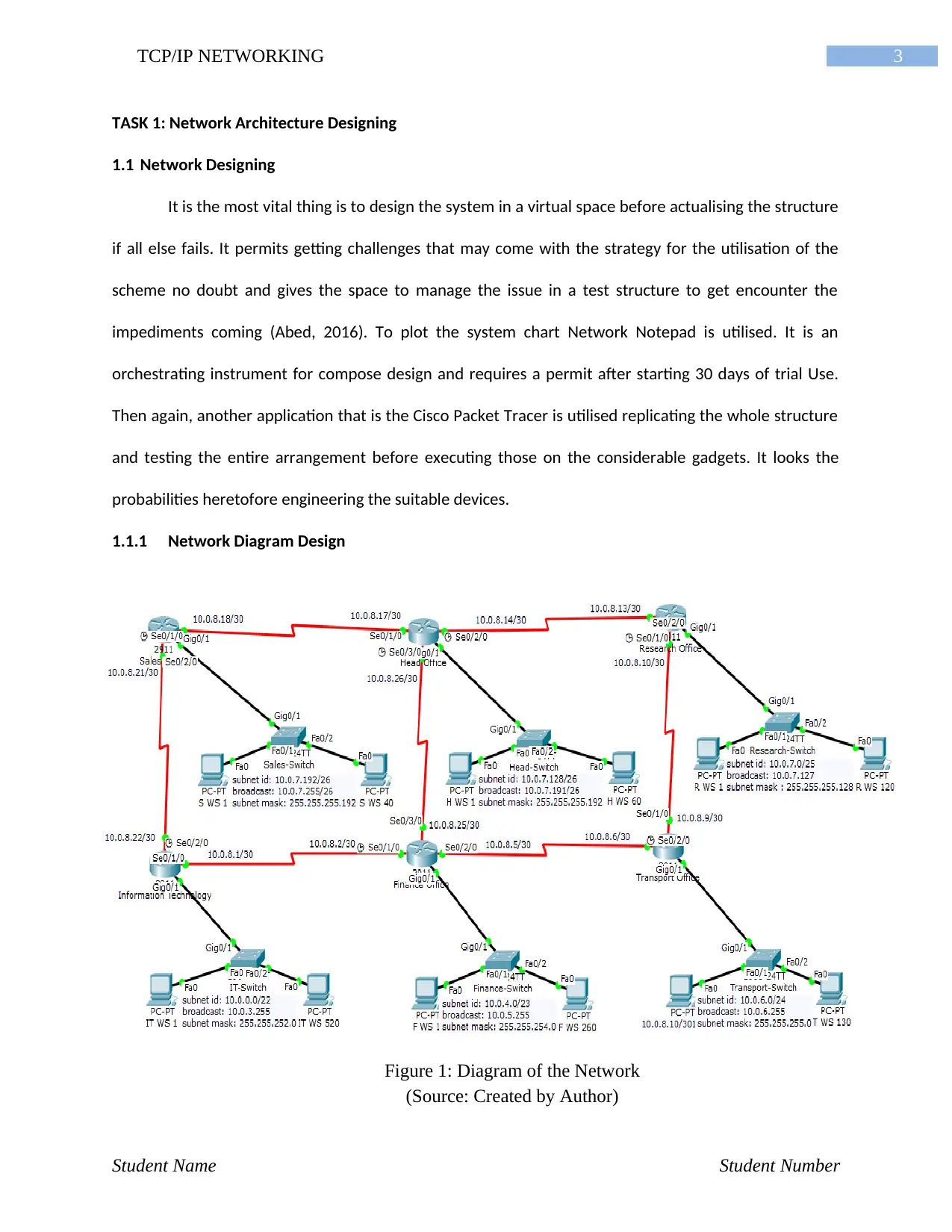
3TCP/IP NETWORKING
TASK 1: Network Architecture Designing
1.1 Network Designing
It is the most vital thing is to design the system in a virtual space before actualising the structure
if all else fails. It permits getting challenges that may come with the strategy for the utilisation of the
scheme no doubt and gives the space to manage the issue in a test structure to get encounter the
impediments coming (Abed, 2016). To plot the system chart Network Notepad is utilised. It is an
orchestrating instrument for compose design and requires a permit after starting 30 days of trial Use.
Then again, another application that is the Cisco Packet Tracer is utilised replicating the whole structure
and testing the entire arrangement before executing those on the considerable gadgets. It looks the
probabilities heretofore engineering the suitable devices.
1.1.1 Network Diagram Design
Student Name Student Number
Figure 1: Diagram of the Network
(Source: Created by Author)
TASK 1: Network Architecture Designing
1.1 Network Designing
It is the most vital thing is to design the system in a virtual space before actualising the structure
if all else fails. It permits getting challenges that may come with the strategy for the utilisation of the
scheme no doubt and gives the space to manage the issue in a test structure to get encounter the
impediments coming (Abed, 2016). To plot the system chart Network Notepad is utilised. It is an
orchestrating instrument for compose design and requires a permit after starting 30 days of trial Use.
Then again, another application that is the Cisco Packet Tracer is utilised replicating the whole structure
and testing the entire arrangement before executing those on the considerable gadgets. It looks the
probabilities heretofore engineering the suitable devices.
1.1.1 Network Diagram Design
Student Name Student Number
Figure 1: Diagram of the Network
(Source: Created by Author)
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

4TCP/IP NETWORKING
1.1.2 Required Devices for the Network
• Core Networking Devices: Six switches are set in each of the crates where the divisions are
suited (Cui et al., 2015). Switches are masterminding gadget that transmits information bundles
between PC structures utilising activity arranging limits.
•Workstations: The quantity of workstations utilized is talked about underneath.
• 520 workstations in the Information Technology office
• 260 workstations in the Finance Department
• 130 workstations in the Transport Department
• 120 workstations in the Research Department
• 60 workstations in the Head Office
• 40 workstations in the Sales office
1.1.3 Subnet Calculation Method
The IP address is a unique number doled out to every gadget on the structure. Then again, IP-
tending to construe appropriating IP passes on to every device on the structure. Prior IP addresses were
classful. Those are the class a, b, c, d and e. This method winds up abused piles of IP addresses since IP
addresses were settled in numbers for each class (Duke et al., 2015). Similarly, the need for subnetting
came into the photo. Subnetting segregates single structure IP into different grouped systems. This extra
to use the majority of the IP keeps an eye out for that were prior left surrendered.
The association has the IP Network 10.0.0.0, and it is said to utilise that structure IP to affect all
to the sub organise. As indicated by the format, the structure will utilise the ring topology. In work
topology, the greater part of the focuses is associated with the following and past hub centre point or
focal contraption. For this condition, the switch orchestrated in the head office is the crucial contraption
or switch that is associated with five direct channels with different switches arranged in various working
Student Name Student Number
1.1.2 Required Devices for the Network
• Core Networking Devices: Six switches are set in each of the crates where the divisions are
suited (Cui et al., 2015). Switches are masterminding gadget that transmits information bundles
between PC structures utilising activity arranging limits.
•Workstations: The quantity of workstations utilized is talked about underneath.
• 520 workstations in the Information Technology office
• 260 workstations in the Finance Department
• 130 workstations in the Transport Department
• 120 workstations in the Research Department
• 60 workstations in the Head Office
• 40 workstations in the Sales office
1.1.3 Subnet Calculation Method
The IP address is a unique number doled out to every gadget on the structure. Then again, IP-
tending to construe appropriating IP passes on to every device on the structure. Prior IP addresses were
classful. Those are the class a, b, c, d and e. This method winds up abused piles of IP addresses since IP
addresses were settled in numbers for each class (Duke et al., 2015). Similarly, the need for subnetting
came into the photo. Subnetting segregates single structure IP into different grouped systems. This extra
to use the majority of the IP keeps an eye out for that were prior left surrendered.
The association has the IP Network 10.0.0.0, and it is said to utilise that structure IP to affect all
to the sub organise. As indicated by the format, the structure will utilise the ring topology. In work
topology, the greater part of the focuses is associated with the following and past hub centre point or
focal contraption. For this condition, the switch orchestrated in the head office is the crucial contraption
or switch that is associated with five direct channels with different switches arranged in various working
Student Name Student Number

5TCP/IP NETWORKING
environments (Keceli, Inan and Ayanoglu, 2015). In this manner, six rooms and five committed channel
show 11 sub-frameworks are required. The focal methodology in subnetting is to sort the structure as
indicated by the crucial IP addresses in dropping requesting. In this manner in the wake of sorting out IT
office with 520 workstations starts things out, by the back office with 260 workstations come next after
that Transport office with 130 workstations come third, by then Research office with 120 workstations
approach, after that the head office with 60 workstations continue fifth, and the business office comes
last at 6th (Khalifa et al., 2014). Beginning there forward, the five unmistakable correspondence
channels are tallied. The IP address is a 32-bit address, it is confined to parts the hidden segment is the
system part, and the rest is the host part.
The IP address arrangement starts at 00000000.00000000.00000000.00000000 , That is 0.0.0.0
and Moreover, the last IP address is 11111111.11111111.11111111.11111111 That is 255.255.255.255
in Decimal separately. There is an including procedure to choose how much bits to be gotten from the
host part. That is 2n-2. This infers in case you get 2 bits you will get 22-2=2 IP addresses if 3 bits are
obtained you will get 23-2=6 IP addresses.
Student Name Student Number
environments (Keceli, Inan and Ayanoglu, 2015). In this manner, six rooms and five committed channel
show 11 sub-frameworks are required. The focal methodology in subnetting is to sort the structure as
indicated by the crucial IP addresses in dropping requesting. In this manner in the wake of sorting out IT
office with 520 workstations starts things out, by the back office with 260 workstations come next after
that Transport office with 130 workstations come third, by then Research office with 120 workstations
approach, after that the head office with 60 workstations continue fifth, and the business office comes
last at 6th (Khalifa et al., 2014). Beginning there forward, the five unmistakable correspondence
channels are tallied. The IP address is a 32-bit address, it is confined to parts the hidden segment is the
system part, and the rest is the host part.
The IP address arrangement starts at 00000000.00000000.00000000.00000000 , That is 0.0.0.0
and Moreover, the last IP address is 11111111.11111111.11111111.11111111 That is 255.255.255.255
in Decimal separately. There is an including procedure to choose how much bits to be gotten from the
host part. That is 2n-2. This infers in case you get 2 bits you will get 22-2=2 IP addresses if 3 bits are
obtained you will get 23-2=6 IP addresses.
Student Name Student Number
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
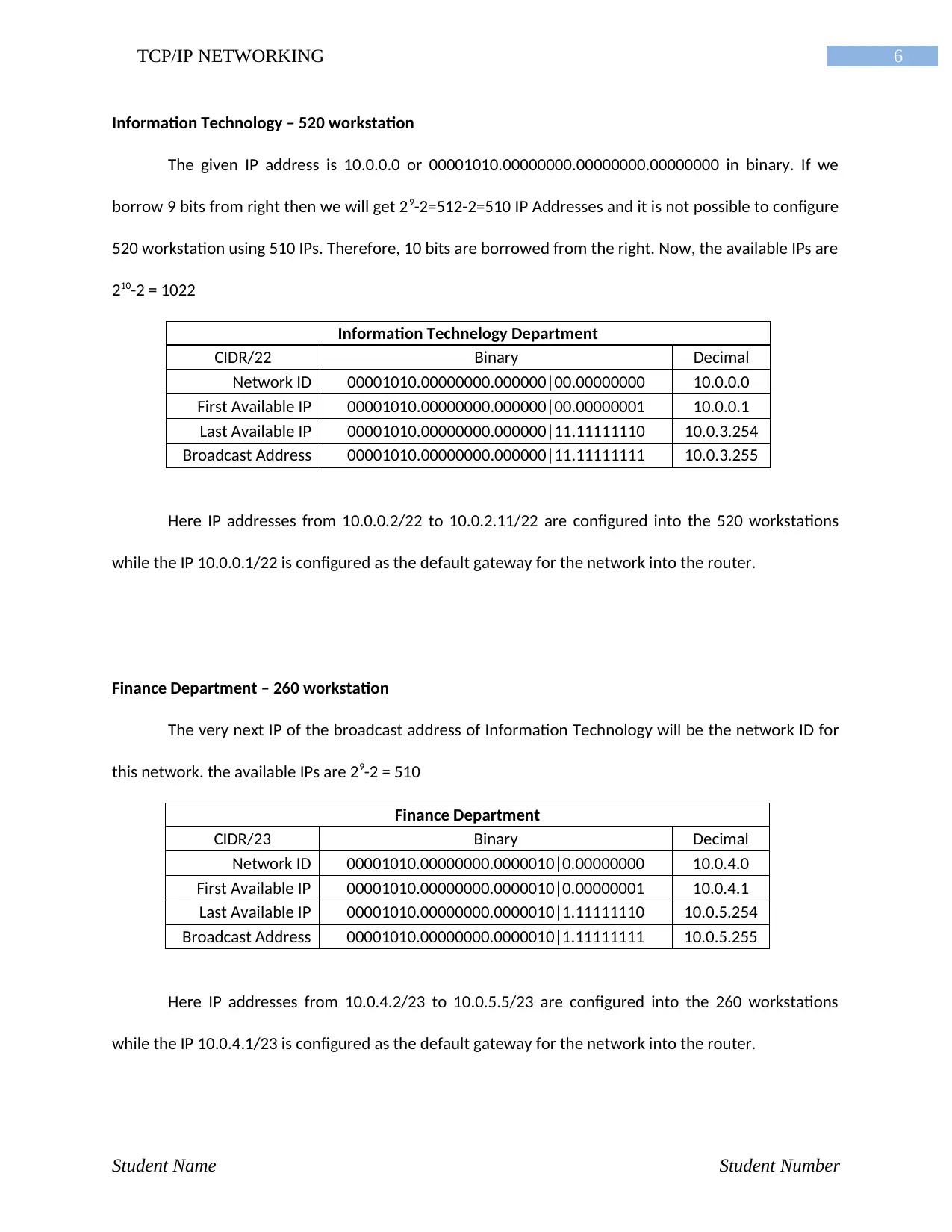
6TCP/IP NETWORKING
Information Technology – 520 workstation
The given IP address is 10.0.0.0 or 00001010.00000000.00000000.00000000 in binary. If we
borrow 9 bits from right then we will get 29-2=512-2=510 IP Addresses and it is not possible to configure
520 workstation using 510 IPs. Therefore, 10 bits are borrowed from the right. Now, the available IPs are
210-2 = 1022
Information Technelogy Department
CIDR/22 Binary Decimal
Network ID 00001010.00000000.000000|00.00000000 10.0.0.0
First Available IP 00001010.00000000.000000|00.00000001 10.0.0.1
Last Available IP 00001010.00000000.000000|11.11111110 10.0.3.254
Broadcast Address 00001010.00000000.000000|11.11111111 10.0.3.255
Here IP addresses from 10.0.0.2/22 to 10.0.2.11/22 are configured into the 520 workstations
while the IP 10.0.0.1/22 is configured as the default gateway for the network into the router.
Finance Department – 260 workstation
The very next IP of the broadcast address of Information Technology will be the network ID for
this network. the available IPs are 29-2 = 510
Finance Department
CIDR/23 Binary Decimal
Network ID 00001010.00000000.0000010|0.00000000 10.0.4.0
First Available IP 00001010.00000000.0000010|0.00000001 10.0.4.1
Last Available IP 00001010.00000000.0000010|1.11111110 10.0.5.254
Broadcast Address 00001010.00000000.0000010|1.11111111 10.0.5.255
Here IP addresses from 10.0.4.2/23 to 10.0.5.5/23 are configured into the 260 workstations
while the IP 10.0.4.1/23 is configured as the default gateway for the network into the router.
Student Name Student Number
Information Technology – 520 workstation
The given IP address is 10.0.0.0 or 00001010.00000000.00000000.00000000 in binary. If we
borrow 9 bits from right then we will get 29-2=512-2=510 IP Addresses and it is not possible to configure
520 workstation using 510 IPs. Therefore, 10 bits are borrowed from the right. Now, the available IPs are
210-2 = 1022
Information Technelogy Department
CIDR/22 Binary Decimal
Network ID 00001010.00000000.000000|00.00000000 10.0.0.0
First Available IP 00001010.00000000.000000|00.00000001 10.0.0.1
Last Available IP 00001010.00000000.000000|11.11111110 10.0.3.254
Broadcast Address 00001010.00000000.000000|11.11111111 10.0.3.255
Here IP addresses from 10.0.0.2/22 to 10.0.2.11/22 are configured into the 520 workstations
while the IP 10.0.0.1/22 is configured as the default gateway for the network into the router.
Finance Department – 260 workstation
The very next IP of the broadcast address of Information Technology will be the network ID for
this network. the available IPs are 29-2 = 510
Finance Department
CIDR/23 Binary Decimal
Network ID 00001010.00000000.0000010|0.00000000 10.0.4.0
First Available IP 00001010.00000000.0000010|0.00000001 10.0.4.1
Last Available IP 00001010.00000000.0000010|1.11111110 10.0.5.254
Broadcast Address 00001010.00000000.0000010|1.11111111 10.0.5.255
Here IP addresses from 10.0.4.2/23 to 10.0.5.5/23 are configured into the 260 workstations
while the IP 10.0.4.1/23 is configured as the default gateway for the network into the router.
Student Name Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
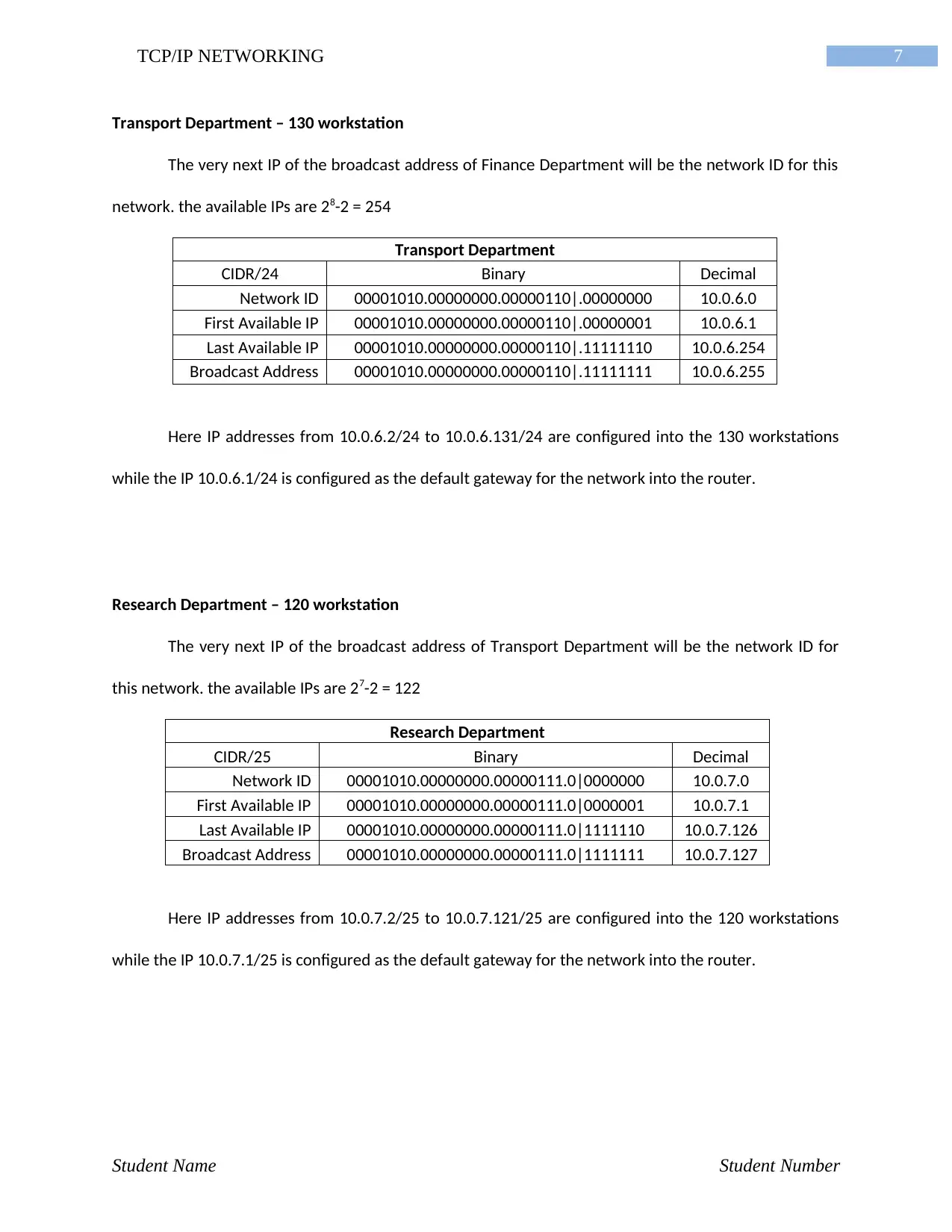
7TCP/IP NETWORKING
Transport Department – 130 workstation
The very next IP of the broadcast address of Finance Department will be the network ID for this
network. the available IPs are 28-2 = 254
Transport Department
CIDR/24 Binary Decimal
Network ID 00001010.00000000.00000110|.00000000 10.0.6.0
First Available IP 00001010.00000000.00000110|.00000001 10.0.6.1
Last Available IP 00001010.00000000.00000110|.11111110 10.0.6.254
Broadcast Address 00001010.00000000.00000110|.11111111 10.0.6.255
Here IP addresses from 10.0.6.2/24 to 10.0.6.131/24 are configured into the 130 workstations
while the IP 10.0.6.1/24 is configured as the default gateway for the network into the router.
Research Department – 120 workstation
The very next IP of the broadcast address of Transport Department will be the network ID for
this network. the available IPs are 27-2 = 122
Research Department
CIDR/25 Binary Decimal
Network ID 00001010.00000000.00000111.0|0000000 10.0.7.0
First Available IP 00001010.00000000.00000111.0|0000001 10.0.7.1
Last Available IP 00001010.00000000.00000111.0|1111110 10.0.7.126
Broadcast Address 00001010.00000000.00000111.0|1111111 10.0.7.127
Here IP addresses from 10.0.7.2/25 to 10.0.7.121/25 are configured into the 120 workstations
while the IP 10.0.7.1/25 is configured as the default gateway for the network into the router.
Student Name Student Number
Transport Department – 130 workstation
The very next IP of the broadcast address of Finance Department will be the network ID for this
network. the available IPs are 28-2 = 254
Transport Department
CIDR/24 Binary Decimal
Network ID 00001010.00000000.00000110|.00000000 10.0.6.0
First Available IP 00001010.00000000.00000110|.00000001 10.0.6.1
Last Available IP 00001010.00000000.00000110|.11111110 10.0.6.254
Broadcast Address 00001010.00000000.00000110|.11111111 10.0.6.255
Here IP addresses from 10.0.6.2/24 to 10.0.6.131/24 are configured into the 130 workstations
while the IP 10.0.6.1/24 is configured as the default gateway for the network into the router.
Research Department – 120 workstation
The very next IP of the broadcast address of Transport Department will be the network ID for
this network. the available IPs are 27-2 = 122
Research Department
CIDR/25 Binary Decimal
Network ID 00001010.00000000.00000111.0|0000000 10.0.7.0
First Available IP 00001010.00000000.00000111.0|0000001 10.0.7.1
Last Available IP 00001010.00000000.00000111.0|1111110 10.0.7.126
Broadcast Address 00001010.00000000.00000111.0|1111111 10.0.7.127
Here IP addresses from 10.0.7.2/25 to 10.0.7.121/25 are configured into the 120 workstations
while the IP 10.0.7.1/25 is configured as the default gateway for the network into the router.
Student Name Student Number
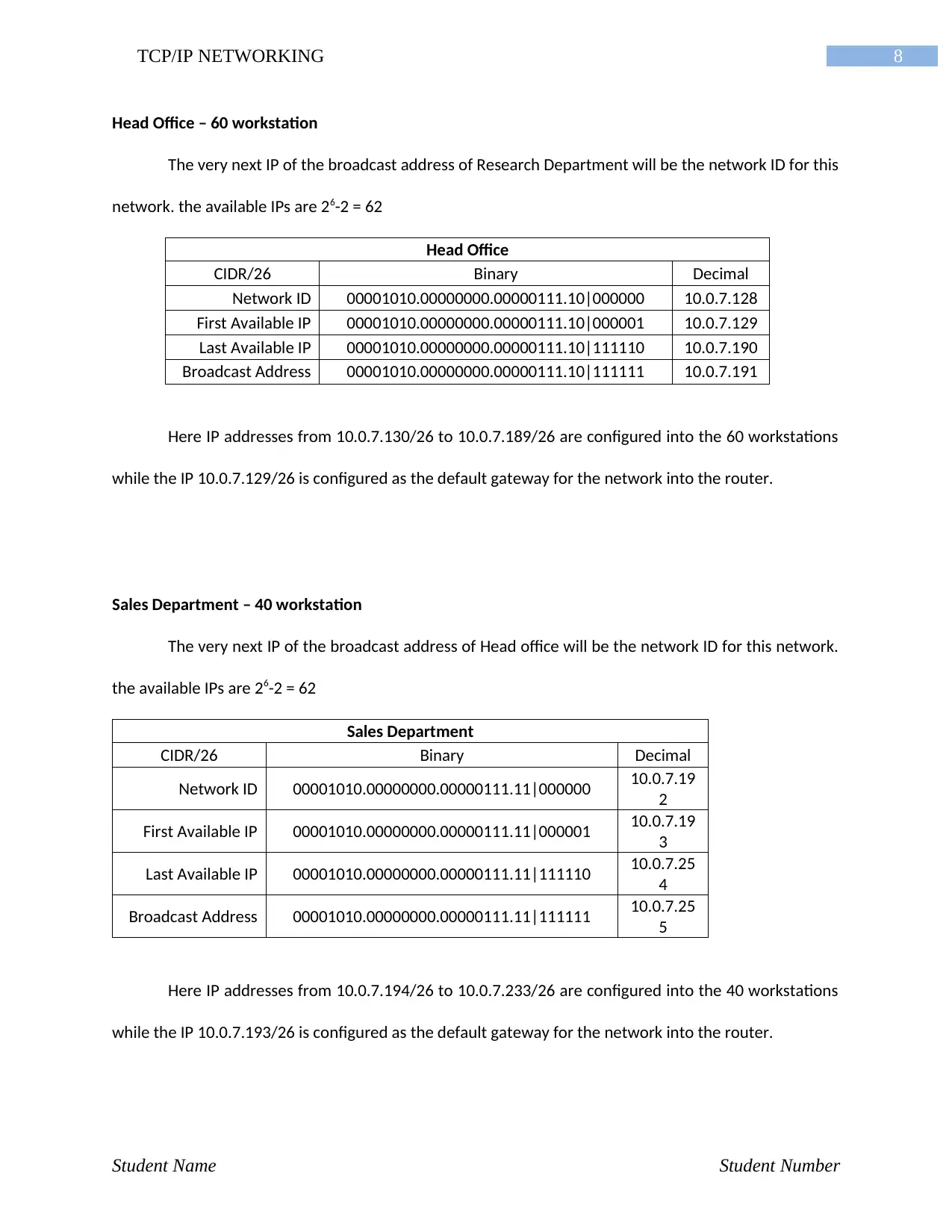
8TCP/IP NETWORKING
Head Office – 60 workstation
The very next IP of the broadcast address of Research Department will be the network ID for this
network. the available IPs are 26-2 = 62
Head Office
CIDR/26 Binary Decimal
Network ID 00001010.00000000.00000111.10|000000 10.0.7.128
First Available IP 00001010.00000000.00000111.10|000001 10.0.7.129
Last Available IP 00001010.00000000.00000111.10|111110 10.0.7.190
Broadcast Address 00001010.00000000.00000111.10|111111 10.0.7.191
Here IP addresses from 10.0.7.130/26 to 10.0.7.189/26 are configured into the 60 workstations
while the IP 10.0.7.129/26 is configured as the default gateway for the network into the router.
Sales Department – 40 workstation
The very next IP of the broadcast address of Head office will be the network ID for this network.
the available IPs are 26-2 = 62
Sales Department
CIDR/26 Binary Decimal
Network ID 00001010.00000000.00000111.11|000000 10.0.7.19
2
First Available IP 00001010.00000000.00000111.11|000001 10.0.7.19
3
Last Available IP 00001010.00000000.00000111.11|111110 10.0.7.25
4
Broadcast Address 00001010.00000000.00000111.11|111111 10.0.7.25
5
Here IP addresses from 10.0.7.194/26 to 10.0.7.233/26 are configured into the 40 workstations
while the IP 10.0.7.193/26 is configured as the default gateway for the network into the router.
Student Name Student Number
Head Office – 60 workstation
The very next IP of the broadcast address of Research Department will be the network ID for this
network. the available IPs are 26-2 = 62
Head Office
CIDR/26 Binary Decimal
Network ID 00001010.00000000.00000111.10|000000 10.0.7.128
First Available IP 00001010.00000000.00000111.10|000001 10.0.7.129
Last Available IP 00001010.00000000.00000111.10|111110 10.0.7.190
Broadcast Address 00001010.00000000.00000111.10|111111 10.0.7.191
Here IP addresses from 10.0.7.130/26 to 10.0.7.189/26 are configured into the 60 workstations
while the IP 10.0.7.129/26 is configured as the default gateway for the network into the router.
Sales Department – 40 workstation
The very next IP of the broadcast address of Head office will be the network ID for this network.
the available IPs are 26-2 = 62
Sales Department
CIDR/26 Binary Decimal
Network ID 00001010.00000000.00000111.11|000000 10.0.7.19
2
First Available IP 00001010.00000000.00000111.11|000001 10.0.7.19
3
Last Available IP 00001010.00000000.00000111.11|111110 10.0.7.25
4
Broadcast Address 00001010.00000000.00000111.11|111111 10.0.7.25
5
Here IP addresses from 10.0.7.194/26 to 10.0.7.233/26 are configured into the 40 workstations
while the IP 10.0.7.193/26 is configured as the default gateway for the network into the router.
Student Name Student Number
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
9TCP/IP NETWORKING
Router-to-Router Networks
IT Router - Finance Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000000|00 10.0.8.0
IT Router IP 00001010.00000000.00001000.000000|01 10.0.8.1
Finance Router IP 00001010.00000000.00001000.000000|10 10.0.8.2
Broadcast Address 00001010.00000000.00001000.000000|11 10.0.8.3
Finance Router - Transport Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000001|00 10.0.8.4
Finance Router IP 00001010.00000000.00001000.000001|01 10.0.8.5
Transport Router IP 00001010.00000000.00001000.000001|10 10.0.8.6
Broadcast Address 00001010.00000000.00001000.000001|11 10.0.8.7
Transport Router - Research Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000010|00 10.0.8.8
Transport RouterIP 00001010.00000000.00001000.000010|01 10.0.8.9
Research Router IP 00001010.00000000.00001000.000010|10 10.0.8.10
Broadcast Address 00001010.00000000.00001000.000010|11 10.0.8.11
Research Router - HeadOffice Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000011|00 10.0.8.12
Research RouterIP 00001010.00000000.00001000.000011|01 10.0.8.13
HeadOffice Router IP 00001010.00000000.00001000.000011|10 10.0.8.14
Broadcast Address 00001010.00000000.00001000.000011|11 10.0.8.15
HeadOffice Router - Sales Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000100|00 10.0.8.16
HeadOffice Router IP 00001010.00000000.00001000.000100|01 10.0.8.17
Sales Router IP 00001010.00000000.00001000.000100|10 10.0.8.18
Student Name Student Number
Router-to-Router Networks
IT Router - Finance Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000000|00 10.0.8.0
IT Router IP 00001010.00000000.00001000.000000|01 10.0.8.1
Finance Router IP 00001010.00000000.00001000.000000|10 10.0.8.2
Broadcast Address 00001010.00000000.00001000.000000|11 10.0.8.3
Finance Router - Transport Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000001|00 10.0.8.4
Finance Router IP 00001010.00000000.00001000.000001|01 10.0.8.5
Transport Router IP 00001010.00000000.00001000.000001|10 10.0.8.6
Broadcast Address 00001010.00000000.00001000.000001|11 10.0.8.7
Transport Router - Research Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000010|00 10.0.8.8
Transport RouterIP 00001010.00000000.00001000.000010|01 10.0.8.9
Research Router IP 00001010.00000000.00001000.000010|10 10.0.8.10
Broadcast Address 00001010.00000000.00001000.000010|11 10.0.8.11
Research Router - HeadOffice Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000011|00 10.0.8.12
Research RouterIP 00001010.00000000.00001000.000011|01 10.0.8.13
HeadOffice Router IP 00001010.00000000.00001000.000011|10 10.0.8.14
Broadcast Address 00001010.00000000.00001000.000011|11 10.0.8.15
HeadOffice Router - Sales Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000100|00 10.0.8.16
HeadOffice Router IP 00001010.00000000.00001000.000100|01 10.0.8.17
Sales Router IP 00001010.00000000.00001000.000100|10 10.0.8.18
Student Name Student Number
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
10TCP/IP NETWORKING
Broadcast Address 00001010.00000000.00001000.000100|11 10.0.8.19
Sales Router - IT Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000101|00 10.0.8.20
Sales Router IP 00001010.00000000.00001000.000101|01 10.0.8.21
IT Router IP 00001010.00000000.00001000.000101|10 10.0.8.22
Broadcast Address 00001010.00000000.00001000.000101|11 10.0.8.23
Finance Router - HeadOffice Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000110|00 10.0.8.24
Finance Router IP 00001010.00000000.00001000.000110|01 10.0.8.25
HeadOffice Router IP 00001010.00000000.00001000.000110|10 10.0.8.26
Broadcast Address 00001010.00000000.00001000.000110|11 10.0.8.27
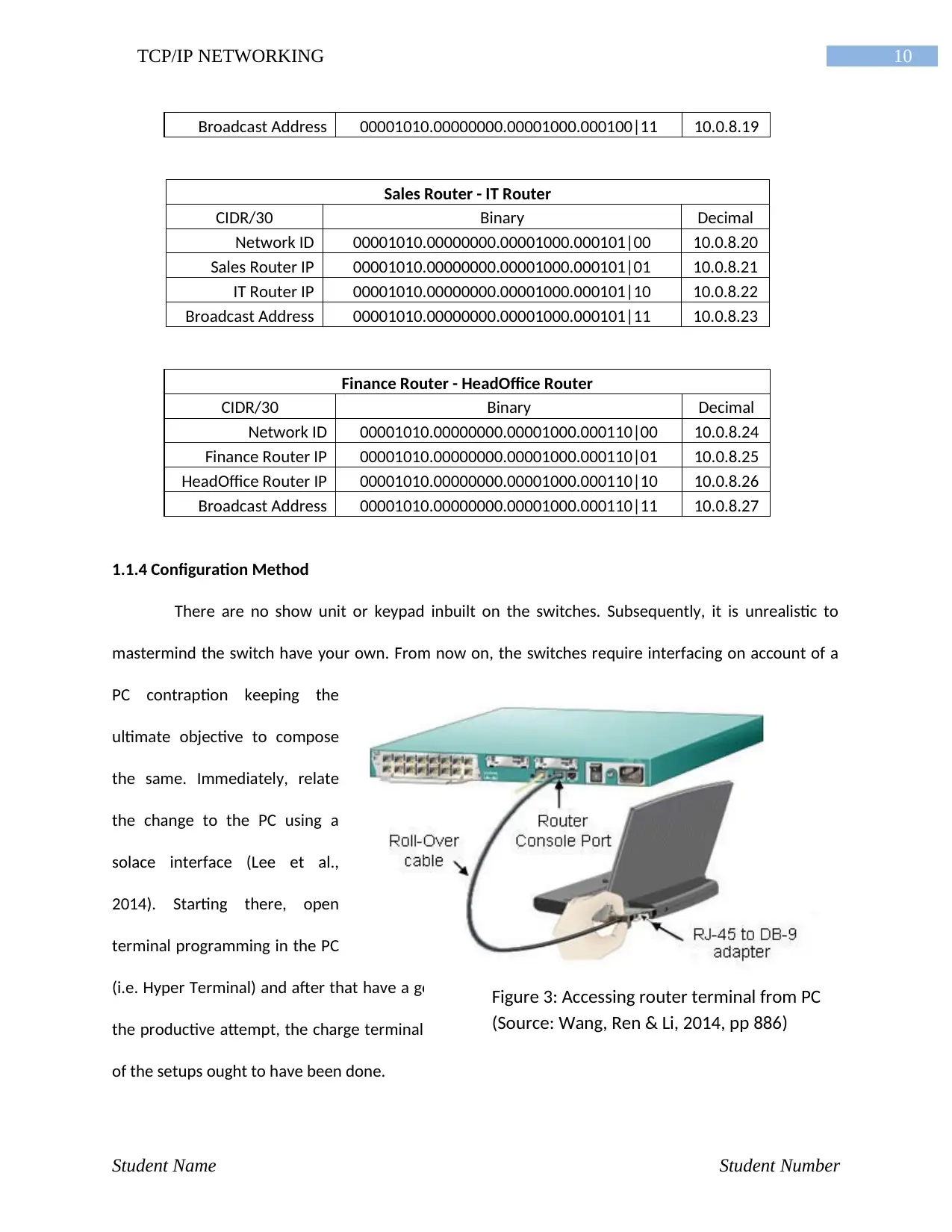
1.1.4 Configuration Method
There are no show unit or keypad inbuilt on the switches. Subsequently, it is unrealistic to
mastermind the switch have your own. From now on, the switches require interfacing on account of a
PC contraption keeping the
ultimate objective to compose
the same. Immediately, relate
the change to the PC using a
solace interface (Lee et al.,
2014). Starting there, open
terminal programming in the PC
(i.e. Hyper Terminal) and after that have a go at getting to the port in which the switch is related. After
the productive attempt, the charge terminal for the switch will open on the PC screen. There each one
of the setups ought to have been done.
Student Name Student Number
Figure 3: Accessing router terminal from PC
(Source: Wang, Ren & Li, 2014, pp 886)
Broadcast Address 00001010.00000000.00001000.000100|11 10.0.8.19
Sales Router - IT Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000101|00 10.0.8.20
Sales Router IP 00001010.00000000.00001000.000101|01 10.0.8.21
IT Router IP 00001010.00000000.00001000.000101|10 10.0.8.22
Broadcast Address 00001010.00000000.00001000.000101|11 10.0.8.23
Finance Router - HeadOffice Router
CIDR/30 Binary Decimal
Network ID 00001010.00000000.00001000.000110|00 10.0.8.24
Finance Router IP 00001010.00000000.00001000.000110|01 10.0.8.25
HeadOffice Router IP 00001010.00000000.00001000.000110|10 10.0.8.26
Broadcast Address 00001010.00000000.00001000.000110|11 10.0.8.27
1.1.4 Configuration Method
There are no show unit or keypad inbuilt on the switches. Subsequently, it is unrealistic to
mastermind the switch have your own. From now on, the switches require interfacing on account of a
PC contraption keeping the
ultimate objective to compose
the same. Immediately, relate
the change to the PC using a
solace interface (Lee et al.,
2014). Starting there, open
terminal programming in the PC
(i.e. Hyper Terminal) and after that have a go at getting to the port in which the switch is related. After
the productive attempt, the charge terminal for the switch will open on the PC screen. There each one
of the setups ought to have been done.
Student Name Student Number
Figure 3: Accessing router terminal from PC
(Source: Wang, Ren & Li, 2014, pp 886)

11TCP/IP NETWORKING
1.2 What if host number increases over 1024 per department ?
The hosts are being utilised per working beginning at now is most outrageous 520 by
Information Technology division. There are 1022 IPs doled out to IT gather in which 520 IPs are being
utilised (Richards and Petras, 2015). Whatever is left of the workplaces are sub-gotten in a way that a
noteworthy bit of the IPs is utilised moving inconsequential IPs that are misused. Regardless, the present
diagram will in all probability confront dangerous conditions if the quantity of workstations
augmentations to more than 1024. The conceivable occasions are discussed as underneath:
1.2.1 Difficulties
The in all cases framework will wind up apparently out of expertise for the present framework
chief.
The frame will end up being more tangled, and it will wind up noticeably extreme to explore if
any breakdown happens.
The divisions are by and large orchestrated to use static controlling. The augmentation in have
number will impact the head gravely.
not a lone of the workplace has the available IPs offer to dispense them to those workstations.
On the off chance that the extra has shape another framework inside the different room, it will
end up being hard to mastermind VLANs to relate those workstations.
Student Name Student Number
1.2 What if host number increases over 1024 per department ?
The hosts are being utilised per working beginning at now is most outrageous 520 by
Information Technology division. There are 1022 IPs doled out to IT gather in which 520 IPs are being
utilised (Richards and Petras, 2015). Whatever is left of the workplaces are sub-gotten in a way that a
noteworthy bit of the IPs is utilised moving inconsequential IPs that are misused. Regardless, the present
diagram will in all probability confront dangerous conditions if the quantity of workstations
augmentations to more than 1024. The conceivable occasions are discussed as underneath:
1.2.1 Difficulties
The in all cases framework will wind up apparently out of expertise for the present framework
chief.
The frame will end up being more tangled, and it will wind up noticeably extreme to explore if
any breakdown happens.
The divisions are by and large orchestrated to use static controlling. The augmentation in have
number will impact the head gravely.
not a lone of the workplace has the available IPs offer to dispense them to those workstations.
On the off chance that the extra has shape another framework inside the different room, it will
end up being hard to mastermind VLANs to relate those workstations.
Student Name Student Number
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 21
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





