Comprehensive Report on M2M Network Addressing and Analyzer Tools
VerifiedAdded on 2020/03/07
|17
|2878
|167
Report
AI Summary
This report details the network infrastructure for M2M, encompassing addressing solutions, network protocols, and network analyzer tools. It begins by outlining the addressing scheme for M2M's six buildings, including subnetting details, IP ranges, and CIDR notations for each building's network. The report then explores communication protocols, emphasizing the role of TCP/IP and routing protocols like OSPF. It discusses the use of network analyzers, such as Wireshark and vector network analyzers, for monitoring and troubleshooting network performance. The report provides a cost analysis for hardware and software tools and concludes with recommendations for network administration, emphasizing the importance of both hardware and software solutions for maintaining a robust network. The report is a comprehensive guide to network design, implementation, and maintenance, offering practical insights for optimizing network performance and security.

Running Head: TCP/IP NETWORKING
TCP/IP NETWORKING
[Name of the student]
[Name of the University]
TCP/IP NETWORKING
[Name of the student]
[Name of the University]
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

1TCP/IP NETWORKING
Table of Contents
Introduction 2
Task 1.A. Addressing solution 2
Task 1. B. Explanation 6
Task 2. A. Communication protocol & Role of network analyzers 7
Task 2. B. Network analyzer tools 10
Benefits and Usability 10
Associated costs 10
Recommendation 11
Conclusion 12
References 13
Table of Contents
Introduction 2
Task 1.A. Addressing solution 2
Task 1. B. Explanation 6
Task 2. A. Communication protocol & Role of network analyzers 7
Task 2. B. Network analyzer tools 10
Benefits and Usability 10
Associated costs 10
Recommendation 11
Conclusion 12
References 13

2TCP/IP NETWORKING
Introduction
The M2M solution is going to implement a network architecture for their six buildings.
They initially have a private internet protocol, which is being distributed among these six
buildings. In this report, this IP distribution is specified along with the network address
distribution diagram according to the requested scenario (Bredel et al., 2014). However, the
M2M solution has approximately 1200 workstation in a total of their all sites. A network
diagram is prepared in this paper, where all network sites are defining as a building and showing
the internet connectivity.
Introduction
The M2M solution is going to implement a network architecture for their six buildings.
They initially have a private internet protocol, which is being distributed among these six
buildings. In this report, this IP distribution is specified along with the network address
distribution diagram according to the requested scenario (Bredel et al., 2014). However, the
M2M solution has approximately 1200 workstation in a total of their all sites. A network
diagram is prepared in this paper, where all network sites are defining as a building and showing
the internet connectivity.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
3TCP/IP NETWORKING
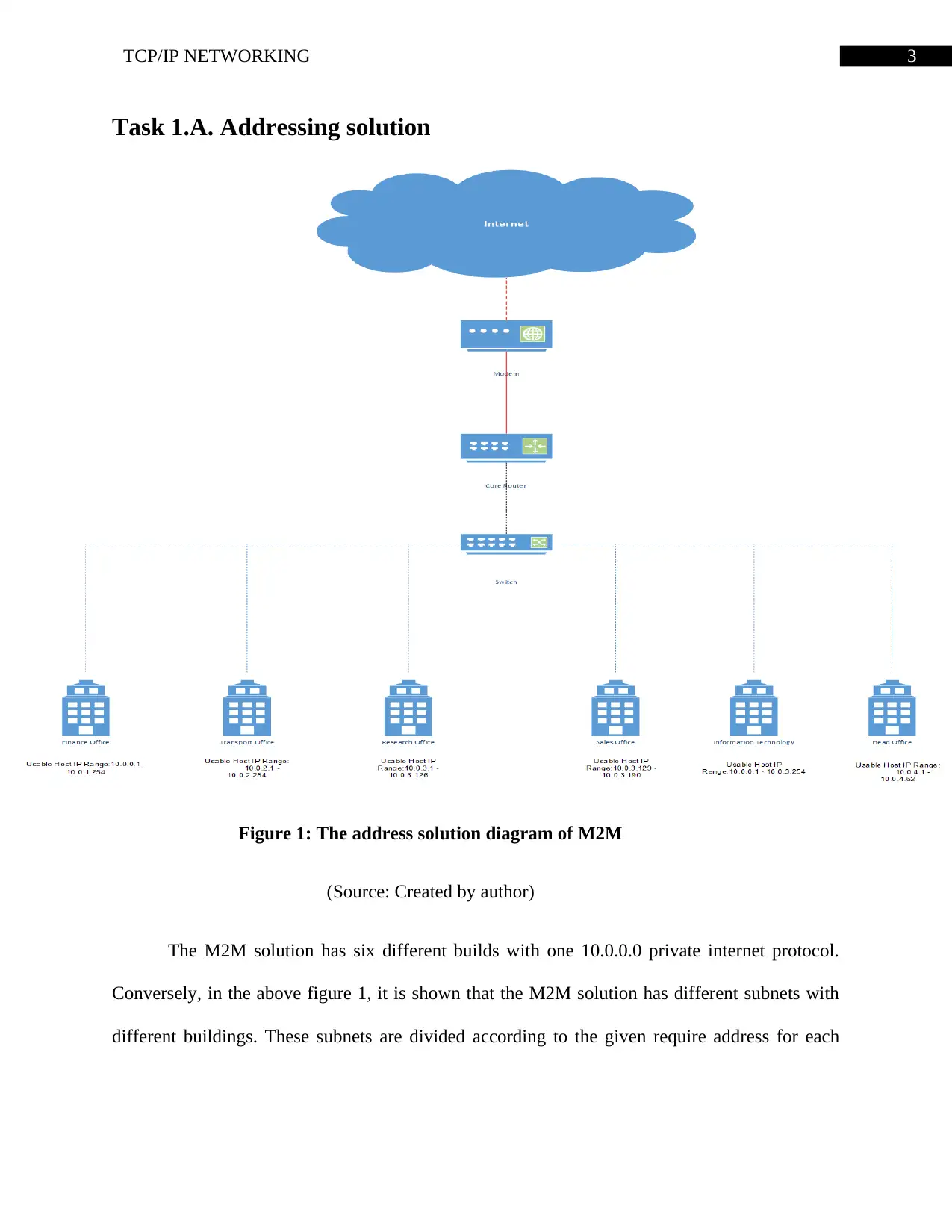
Task 1.A. Addressing solution
Figure 1: The address solution diagram of M2M
(Source: Created by author)
The M2M solution has six different builds with one 10.0.0.0 private internet protocol.
Conversely, in the above figure 1, it is shown that the M2M solution has different subnets with
different buildings. These subnets are divided according to the given require address for each
Task 1.A. Addressing solution
Figure 1: The address solution diagram of M2M
(Source: Created by author)
The M2M solution has six different builds with one 10.0.0.0 private internet protocol.
Conversely, in the above figure 1, it is shown that the M2M solution has different subnets with
different buildings. These subnets are divided according to the given require address for each
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
4TCP/IP NETWORKING
building. However, each of these subnets shown in the above figure 1 is provided with more
details underneath.
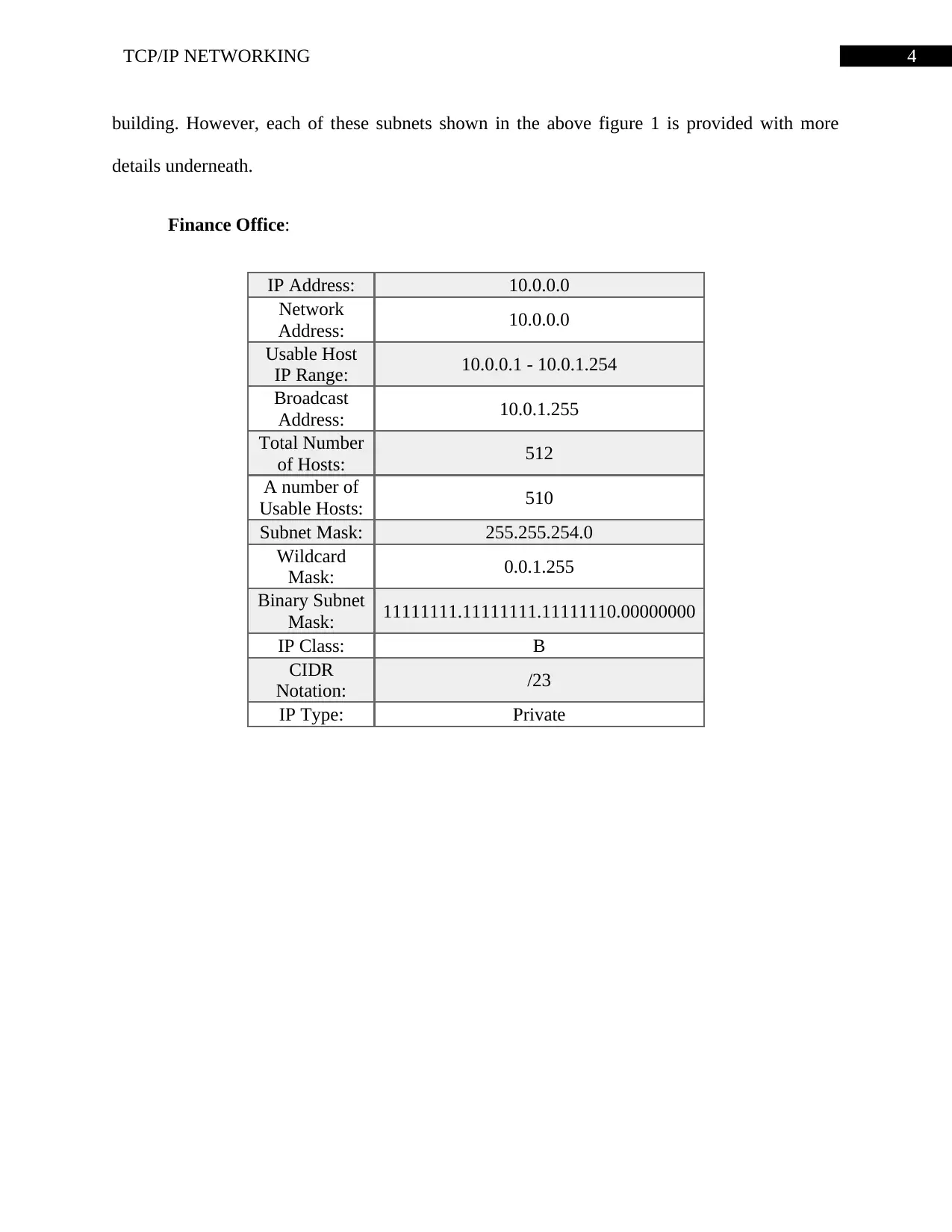
Finance Office:
IP Address: 10.0.0.0
Network
Address: 10.0.0.0
Usable Host
IP Range: 10.0.0.1 - 10.0.1.254
Broadcast
Address: 10.0.1.255
Total Number
of Hosts: 512
A number of
Usable Hosts: 510
Subnet Mask: 255.255.254.0
Wildcard
Mask: 0.0.1.255
Binary Subnet
Mask: 11111111.11111111.11111110.00000000
IP Class: B
CIDR
Notation: /23
IP Type: Private
building. However, each of these subnets shown in the above figure 1 is provided with more
details underneath.
Finance Office:
IP Address: 10.0.0.0
Network
Address: 10.0.0.0
Usable Host
IP Range: 10.0.0.1 - 10.0.1.254
Broadcast
Address: 10.0.1.255
Total Number
of Hosts: 512
A number of
Usable Hosts: 510
Subnet Mask: 255.255.254.0
Wildcard
Mask: 0.0.1.255
Binary Subnet
Mask: 11111111.11111111.11111110.00000000
IP Class: B
CIDR
Notation: /23
IP Type: Private
5TCP/IP NETWORKING
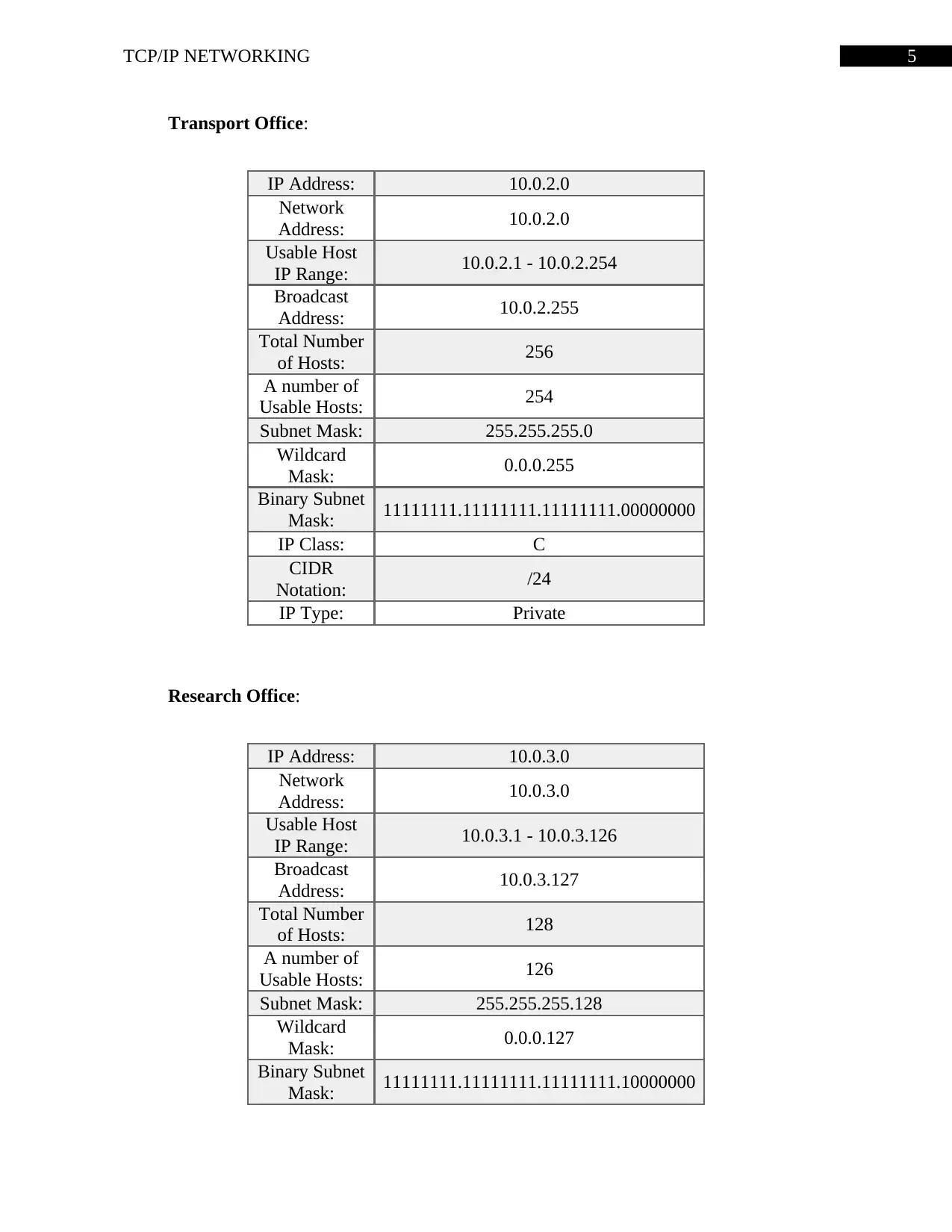
Transport Office:
IP Address: 10.0.2.0
Network
Address: 10.0.2.0
Usable Host
IP Range: 10.0.2.1 - 10.0.2.254
Broadcast
Address: 10.0.2.255
Total Number
of Hosts: 256
A number of
Usable Hosts: 254
Subnet Mask: 255.255.255.0
Wildcard
Mask: 0.0.0.255
Binary Subnet
Mask: 11111111.11111111.11111111.00000000
IP Class: C
CIDR
Notation: /24
IP Type: Private
Research Office:
IP Address: 10.0.3.0
Network
Address: 10.0.3.0
Usable Host
IP Range: 10.0.3.1 - 10.0.3.126
Broadcast
Address: 10.0.3.127
Total Number
of Hosts: 128
A number of
Usable Hosts: 126
Subnet Mask: 255.255.255.128
Wildcard
Mask: 0.0.0.127
Binary Subnet
Mask: 11111111.11111111.11111111.10000000
Transport Office:
IP Address: 10.0.2.0
Network
Address: 10.0.2.0
Usable Host
IP Range: 10.0.2.1 - 10.0.2.254
Broadcast
Address: 10.0.2.255
Total Number
of Hosts: 256
A number of
Usable Hosts: 254
Subnet Mask: 255.255.255.0
Wildcard
Mask: 0.0.0.255
Binary Subnet
Mask: 11111111.11111111.11111111.00000000
IP Class: C
CIDR
Notation: /24
IP Type: Private
Research Office:
IP Address: 10.0.3.0
Network
Address: 10.0.3.0
Usable Host
IP Range: 10.0.3.1 - 10.0.3.126
Broadcast
Address: 10.0.3.127
Total Number
of Hosts: 128
A number of
Usable Hosts: 126
Subnet Mask: 255.255.255.128
Wildcard
Mask: 0.0.0.127
Binary Subnet
Mask: 11111111.11111111.11111111.10000000
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
6TCP/IP NETWORKING
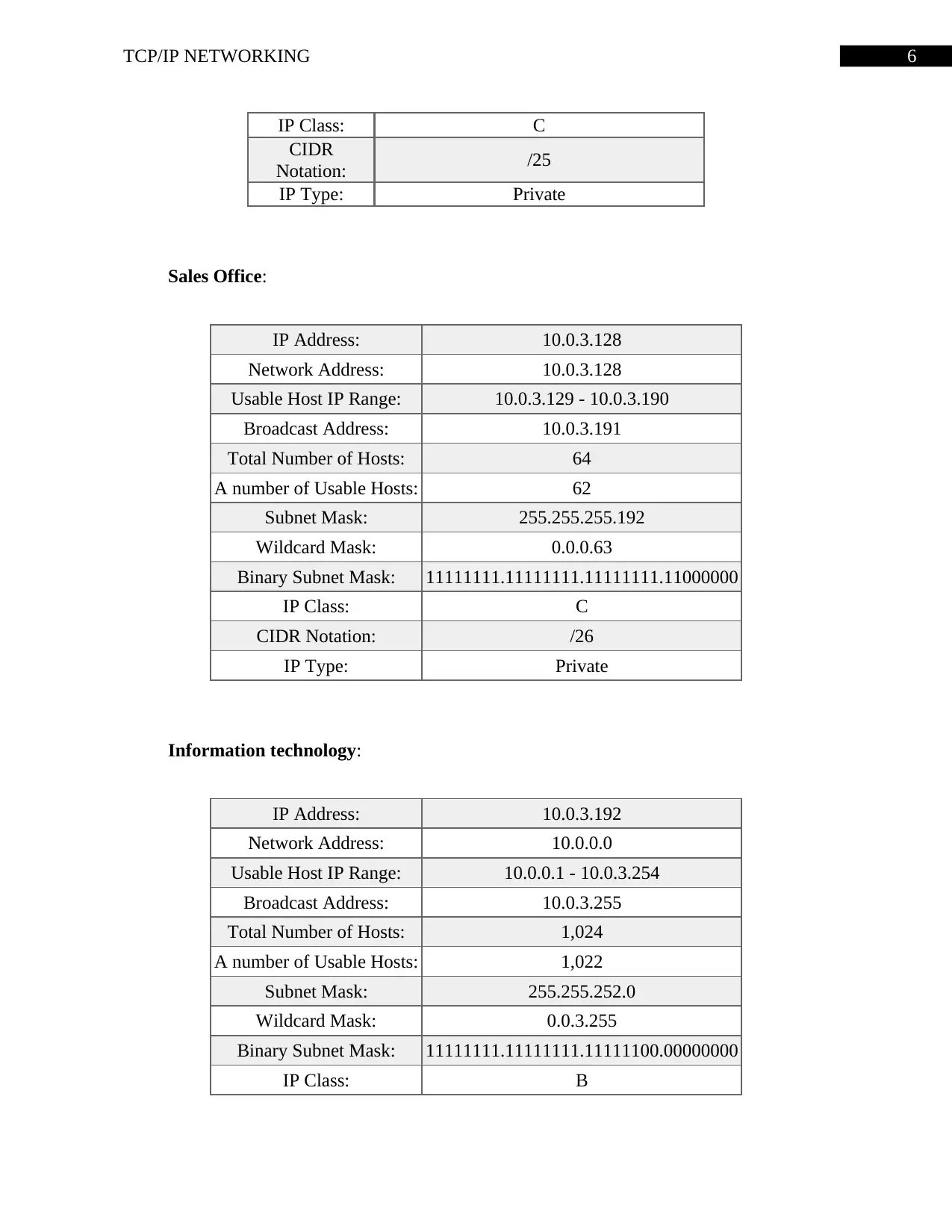
IP Class: C
CIDR
Notation: /25
IP Type: Private
Sales Office:
IP Address: 10.0.3.128
Network Address: 10.0.3.128
Usable Host IP Range: 10.0.3.129 - 10.0.3.190
Broadcast Address: 10.0.3.191
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Information technology:
IP Address: 10.0.3.192
Network Address: 10.0.0.0
Usable Host IP Range: 10.0.0.1 - 10.0.3.254
Broadcast Address: 10.0.3.255
Total Number of Hosts: 1,024
A number of Usable Hosts: 1,022
Subnet Mask: 255.255.252.0
Wildcard Mask: 0.0.3.255
Binary Subnet Mask: 11111111.11111111.11111100.00000000
IP Class: B
IP Class: C
CIDR
Notation: /25
IP Type: Private
Sales Office:
IP Address: 10.0.3.128
Network Address: 10.0.3.128
Usable Host IP Range: 10.0.3.129 - 10.0.3.190
Broadcast Address: 10.0.3.191
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Information technology:
IP Address: 10.0.3.192
Network Address: 10.0.0.0
Usable Host IP Range: 10.0.0.1 - 10.0.3.254
Broadcast Address: 10.0.3.255
Total Number of Hosts: 1,024
A number of Usable Hosts: 1,022
Subnet Mask: 255.255.252.0
Wildcard Mask: 0.0.3.255
Binary Subnet Mask: 11111111.11111111.11111100.00000000
IP Class: B
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
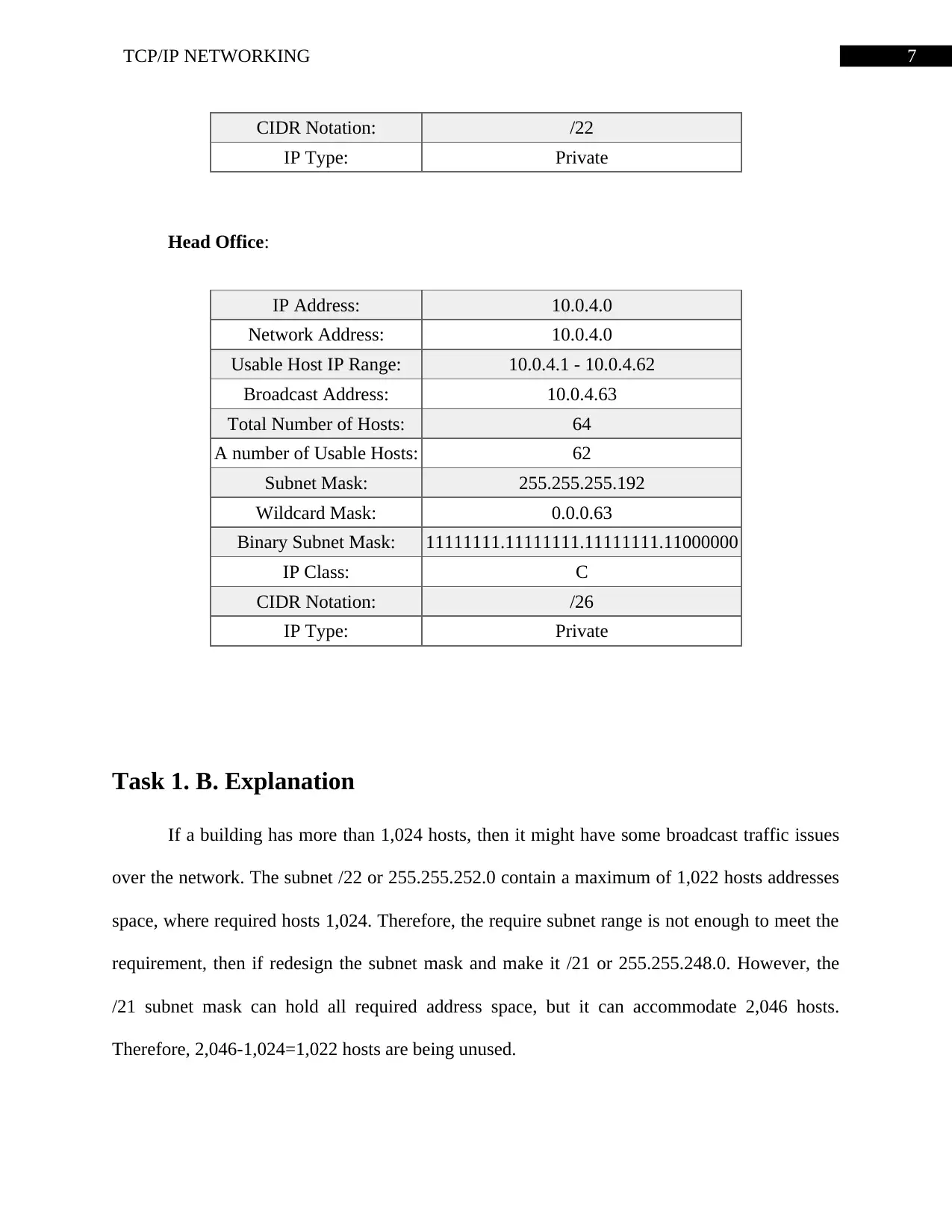
7TCP/IP NETWORKING
CIDR Notation: /22
IP Type: Private
Head Office:
IP Address: 10.0.4.0
Network Address: 10.0.4.0
Usable Host IP Range: 10.0.4.1 - 10.0.4.62
Broadcast Address: 10.0.4.63
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Task 1. B. Explanation
If a building has more than 1,024 hosts, then it might have some broadcast traffic issues
over the network. The subnet /22 or 255.255.252.0 contain a maximum of 1,022 hosts addresses
space, where required hosts 1,024. Therefore, the require subnet range is not enough to meet the
requirement, then if redesign the subnet mask and make it /21 or 255.255.248.0. However, the
/21 subnet mask can hold all required address space, but it can accommodate 2,046 hosts.
Therefore, 2,046-1,024=1,022 hosts are being unused.
CIDR Notation: /22
IP Type: Private
Head Office:
IP Address: 10.0.4.0
Network Address: 10.0.4.0
Usable Host IP Range: 10.0.4.1 - 10.0.4.62
Broadcast Address: 10.0.4.63
Total Number of Hosts: 64
A number of Usable Hosts: 62
Subnet Mask: 255.255.255.192
Wildcard Mask: 0.0.0.63
Binary Subnet Mask: 11111111.11111111.11111111.11000000
IP Class: C
CIDR Notation: /26
IP Type: Private
Task 1. B. Explanation
If a building has more than 1,024 hosts, then it might have some broadcast traffic issues
over the network. The subnet /22 or 255.255.252.0 contain a maximum of 1,022 hosts addresses
space, where required hosts 1,024. Therefore, the require subnet range is not enough to meet the
requirement, then if redesign the subnet mask and make it /21 or 255.255.248.0. However, the
/21 subnet mask can hold all required address space, but it can accommodate 2,046 hosts.
Therefore, 2,046-1,024=1,022 hosts are being unused.

8TCP/IP NETWORKING
Task 2. A. Communication protocol & Role of network analyzers
A network protocol defines a set of rules as well as it conveys a communication channel
between two or more network devices. The M2M solution has around 1200 hosts in their six
sites. Therefore, they need to used appropriate mechanisms for devices to identify as well as
make the connection between each other (Chen, Yuan & Muntean, 2013). These protocols are
also responsible for formatting rules that can specify how the data obtained from network
devices as well as sent over the network. However, network protocol mechanism also useful to
enhance the performance of the network by data compression and message acknowledgement.
The M2M has a reserved private internet protocol 10.0.0.0 to connect all buildings.
Therefore, it must use modern protocols for networking, which conveys packet switching
techniques to receive and send a message in the form of packets. A packet is part of an amount of
original data, which is subdivided into pieces that are re-assembled at their destination device
(Demmer, Ott & Perreault, 2014). However, in networking, there is two level of protocols
available, such as high level protocol (TCP, UDP, HTTP as well as FTP) and low-level protocol.
In generally, high level protocols interact with applications like web browsers while a lower
level protocols interact with network adapters as well as other required network devices.
According to the M2M solution network, architecture routing protocols also required
identifying other routers in the network. Routing protocols are designed for used in the routers to
manage the pathway between source to a destination device (Goralski, 2017). There are few well
known routings protocols are EIGRP, BGP as well as OSPF. However, the M2M solution can
implement the OSPF routing protocols to connect their private networking sites with a core
router, as shown in the above figure 1.
Task 2. A. Communication protocol & Role of network analyzers
A network protocol defines a set of rules as well as it conveys a communication channel
between two or more network devices. The M2M solution has around 1200 hosts in their six
sites. Therefore, they need to used appropriate mechanisms for devices to identify as well as
make the connection between each other (Chen, Yuan & Muntean, 2013). These protocols are
also responsible for formatting rules that can specify how the data obtained from network
devices as well as sent over the network. However, network protocol mechanism also useful to
enhance the performance of the network by data compression and message acknowledgement.
The M2M has a reserved private internet protocol 10.0.0.0 to connect all buildings.
Therefore, it must use modern protocols for networking, which conveys packet switching
techniques to receive and send a message in the form of packets. A packet is part of an amount of
original data, which is subdivided into pieces that are re-assembled at their destination device
(Demmer, Ott & Perreault, 2014). However, in networking, there is two level of protocols
available, such as high level protocol (TCP, UDP, HTTP as well as FTP) and low-level protocol.
In generally, high level protocols interact with applications like web browsers while a lower
level protocols interact with network adapters as well as other required network devices.
According to the M2M solution network, architecture routing protocols also required
identifying other routers in the network. Routing protocols are designed for used in the routers to
manage the pathway between source to a destination device (Goralski, 2017). There are few well
known routings protocols are EIGRP, BGP as well as OSPF. However, the M2M solution can
implement the OSPF routing protocols to connect their private networking sites with a core
router, as shown in the above figure 1.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
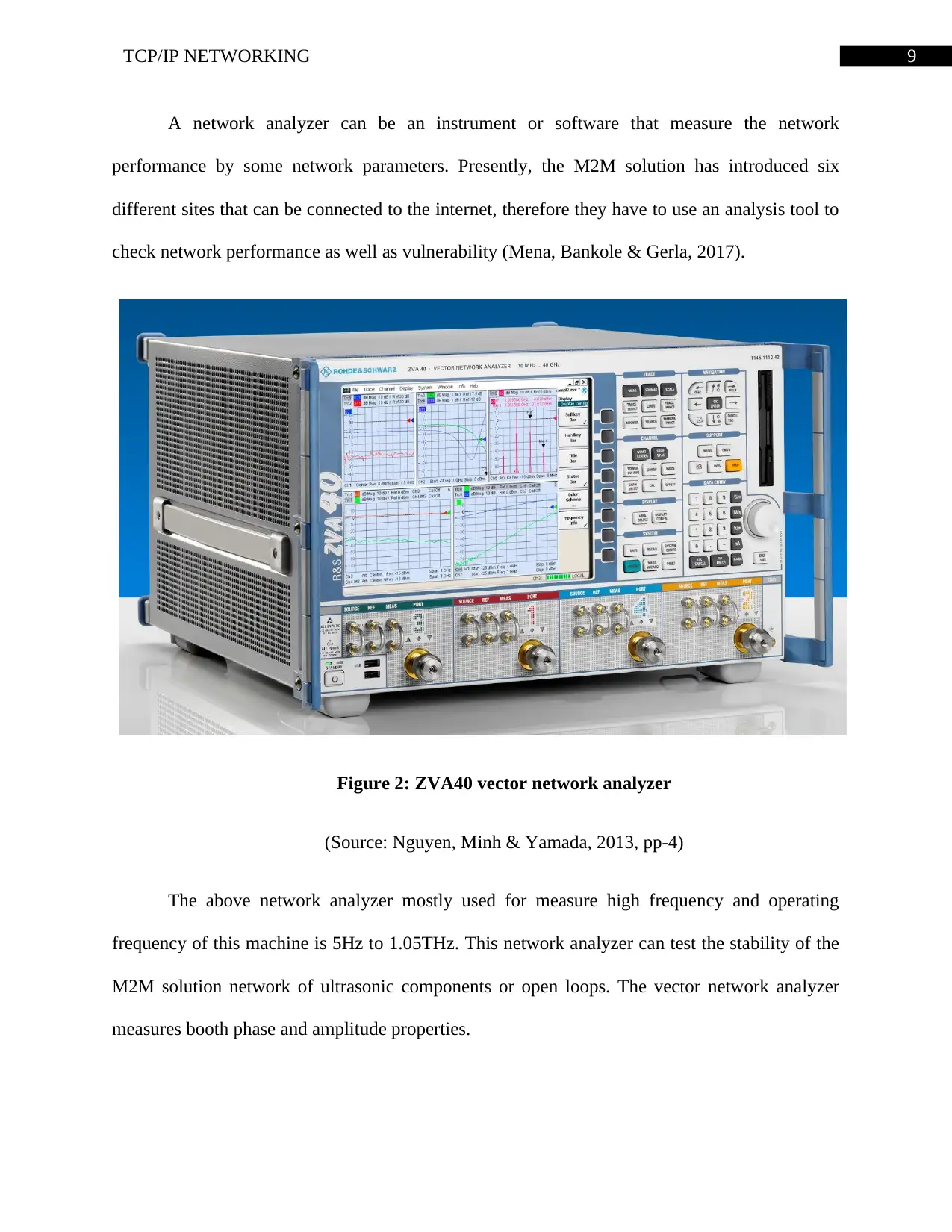
9TCP/IP NETWORKING
A network analyzer can be an instrument or software that measure the network
performance by some network parameters. Presently, the M2M solution has introduced six
different sites that can be connected to the internet, therefore they have to use an analysis tool to
check network performance as well as vulnerability (Mena, Bankole & Gerla, 2017).
Figure 2: ZVA40 vector network analyzer
(Source: Nguyen, Minh & Yamada, 2013, pp-4)
The above network analyzer mostly used for measure high frequency and operating
frequency of this machine is 5Hz to 1.05THz. This network analyzer can test the stability of the
M2M solution network of ultrasonic components or open loops. The vector network analyzer
measures booth phase and amplitude properties.
A network analyzer can be an instrument or software that measure the network
performance by some network parameters. Presently, the M2M solution has introduced six
different sites that can be connected to the internet, therefore they have to use an analysis tool to
check network performance as well as vulnerability (Mena, Bankole & Gerla, 2017).
Figure 2: ZVA40 vector network analyzer
(Source: Nguyen, Minh & Yamada, 2013, pp-4)
The above network analyzer mostly used for measure high frequency and operating
frequency of this machine is 5Hz to 1.05THz. This network analyzer can test the stability of the
M2M solution network of ultrasonic components or open loops. The vector network analyzer
measures booth phase and amplitude properties.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
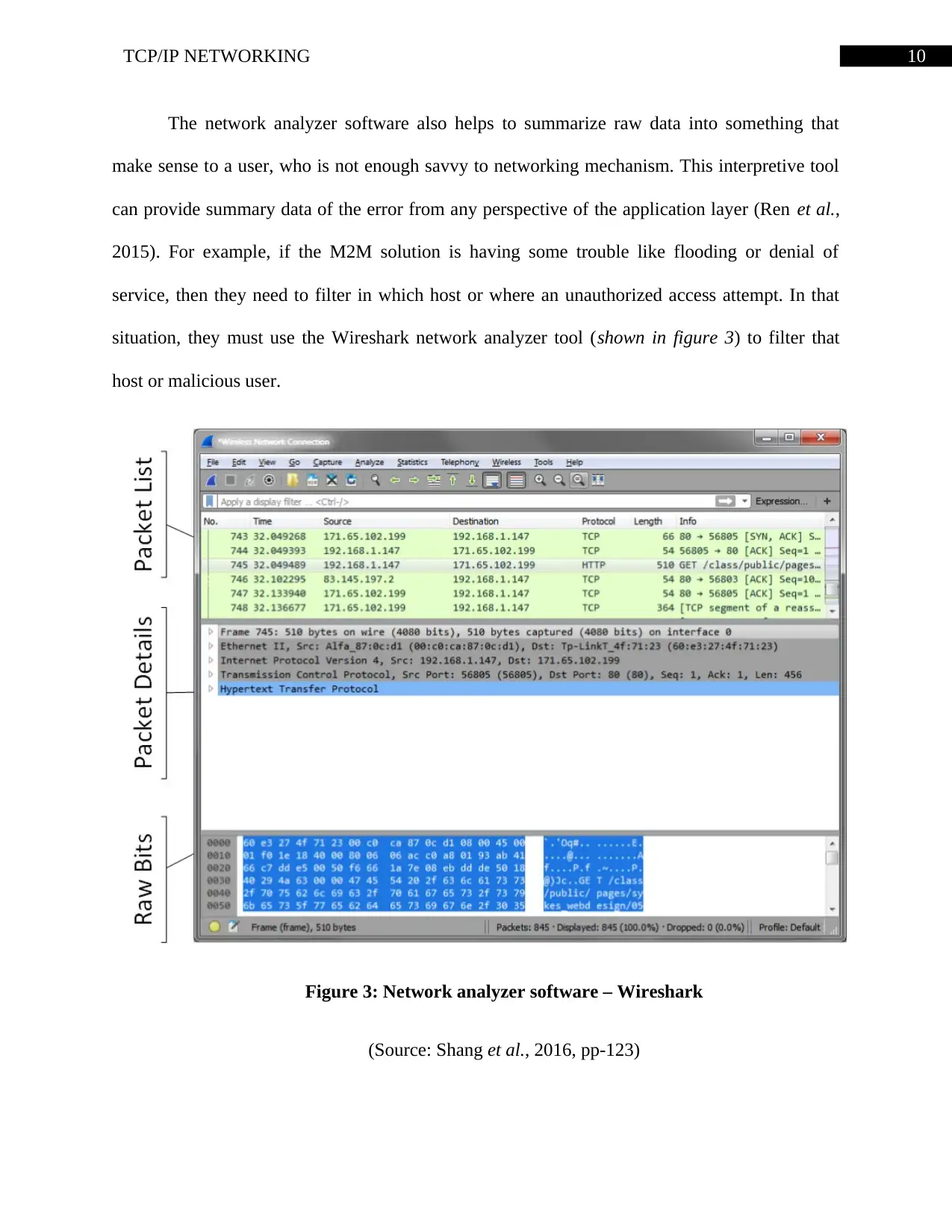
10TCP/IP NETWORKING
The network analyzer software also helps to summarize raw data into something that
make sense to a user, who is not enough savvy to networking mechanism. This interpretive tool
can provide summary data of the error from any perspective of the application layer (Ren et al.,
2015). For example, if the M2M solution is having some trouble like flooding or denial of
service, then they need to filter in which host or where an unauthorized access attempt. In that
situation, they must use the Wireshark network analyzer tool (shown in figure 3) to filter that
host or malicious user.
Figure 3: Network analyzer software – Wireshark
(Source: Shang et al., 2016, pp-123)
The network analyzer software also helps to summarize raw data into something that
make sense to a user, who is not enough savvy to networking mechanism. This interpretive tool
can provide summary data of the error from any perspective of the application layer (Ren et al.,
2015). For example, if the M2M solution is having some trouble like flooding or denial of
service, then they need to filter in which host or where an unauthorized access attempt. In that
situation, they must use the Wireshark network analyzer tool (shown in figure 3) to filter that
host or malicious user.
Figure 3: Network analyzer software – Wireshark
(Source: Shang et al., 2016, pp-123)
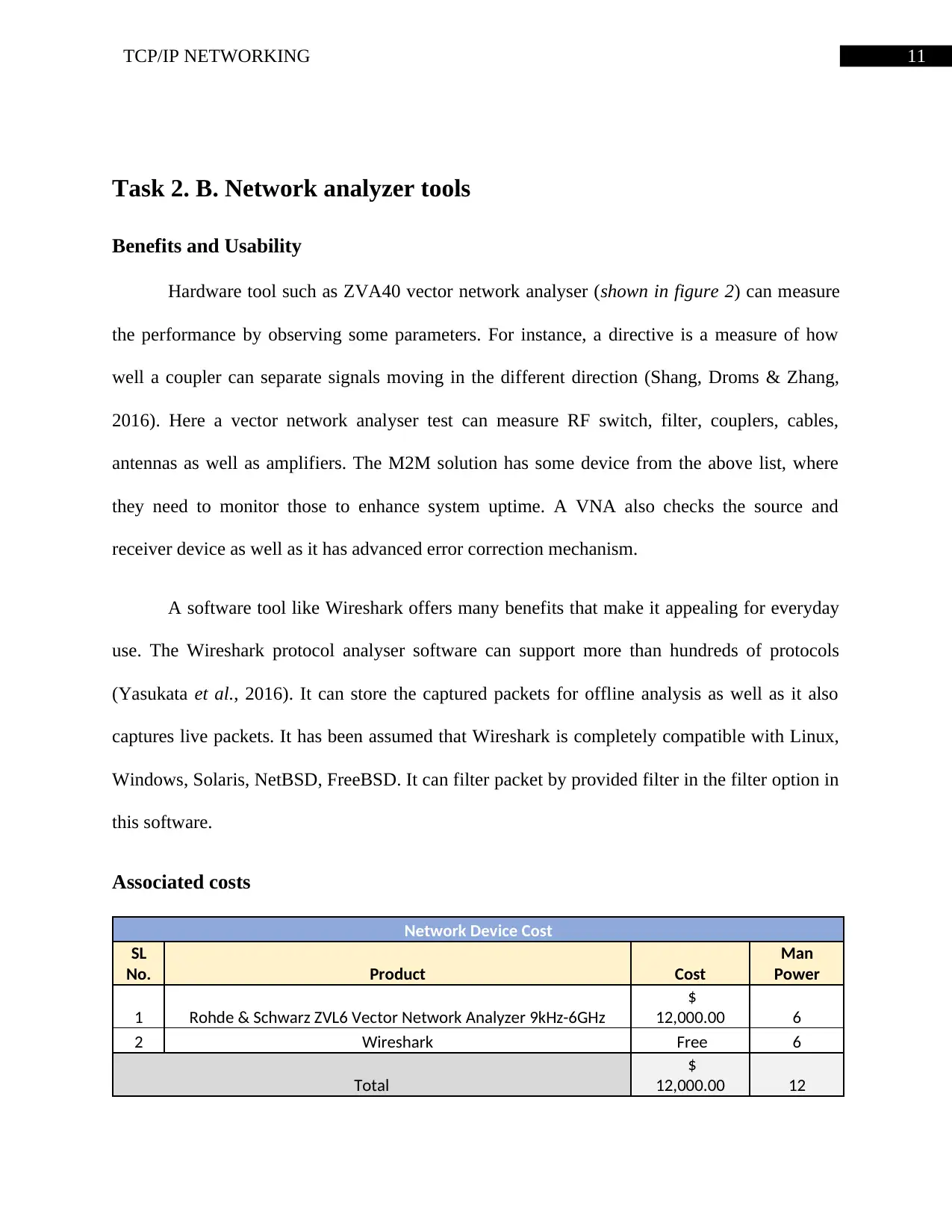
11TCP/IP NETWORKING
Task 2. B. Network analyzer tools
Benefits and Usability
Hardware tool such as ZVA40 vector network analyser (shown in figure 2) can measure
the performance by observing some parameters. For instance, a directive is a measure of how
well a coupler can separate signals moving in the different direction (Shang, Droms & Zhang,
2016). Here a vector network analyser test can measure RF switch, filter, couplers, cables,
antennas as well as amplifiers. The M2M solution has some device from the above list, where
they need to monitor those to enhance system uptime. A VNA also checks the source and
receiver device as well as it has advanced error correction mechanism.
A software tool like Wireshark offers many benefits that make it appealing for everyday
use. The Wireshark protocol analyser software can support more than hundreds of protocols
(Yasukata et al., 2016). It can store the captured packets for offline analysis as well as it also
captures live packets. It has been assumed that Wireshark is completely compatible with Linux,
Windows, Solaris, NetBSD, FreeBSD. It can filter packet by provided filter in the filter option in
this software.
Associated costs
Network Device Cost
SL
No. Product Cost
Man
Power
1 Rohde & Schwarz ZVL6 Vector Network Analyzer 9kHz-6GHz
$
12,000.00 6
2 Wireshark Free 6
Total
$
12,000.00 12
Task 2. B. Network analyzer tools
Benefits and Usability
Hardware tool such as ZVA40 vector network analyser (shown in figure 2) can measure
the performance by observing some parameters. For instance, a directive is a measure of how
well a coupler can separate signals moving in the different direction (Shang, Droms & Zhang,
2016). Here a vector network analyser test can measure RF switch, filter, couplers, cables,
antennas as well as amplifiers. The M2M solution has some device from the above list, where
they need to monitor those to enhance system uptime. A VNA also checks the source and
receiver device as well as it has advanced error correction mechanism.
A software tool like Wireshark offers many benefits that make it appealing for everyday
use. The Wireshark protocol analyser software can support more than hundreds of protocols
(Yasukata et al., 2016). It can store the captured packets for offline analysis as well as it also
captures live packets. It has been assumed that Wireshark is completely compatible with Linux,
Windows, Solaris, NetBSD, FreeBSD. It can filter packet by provided filter in the filter option in
this software.
Associated costs
Network Device Cost
SL
No. Product Cost
Man
Power
1 Rohde & Schwarz ZVL6 Vector Network Analyzer 9kHz-6GHz
$
12,000.00 6
2 Wireshark Free 6
Total
$
12,000.00 12
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 17
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





