M2M Network Design: IP Addressing, Network Analysis and Security
VerifiedAdded on 2020/02/24
|12
|1877
|384
Project
AI Summary
This project presents a comprehensive M2M (Machine-to-Machine) network design, focusing on IP addressing, network analysis, and security implementation. The design utilizes a TCP/IP solution with a private IP addressing scheme (10.0.0.0), employing VLSM (Variable Length Subnet Masking) for efficient subnetting across various departments, including IT, Finance, Transport, Research, Head Office, and Sales. The network architecture includes routers, switches, and access points to connect workstations, with an emphasis on the IT department's substantial IP address requirements. Network analysis is crucial, with a focus on network analyzers like Wireshark for monitoring, troubleshooting, and security purposes. The project emphasizes the importance of network security and timely reporting to prevent unauthorized access and ensure network stability. References to key networking concepts and tools are provided throughout the project.

Running header: M2M NETWORK DESIGN
1
THE NETWORK DESIGN FOR M2M
1
THE NETWORK DESIGN FOR M2M
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

2
M2M NETWORK DESIGN
Executive summary
A TCP/IP solution best suits M2M. The network will have six routers, each located at every site
in Sydney and main office. The network will adopt the 10.0.0.0 private IP. Every department will
have a subnet connecting with the headquarter. All subnets will adopt the 10.0.0.0 private IP
therefore, all data and information will be sent from the subnet only after NAT (Postel, January
1980). All sub-networks will have switches and AP in each subnet to allow all the work station
connect to the primary router. The count of switches and AP will be dependent on the physical
count of workstations and the capacity of the workstations. Some of the departments will have
the users centered in one area where an AP will serve them while in other departments, users will
be widespread in a workstation thus the AP will not be able to cater for their needs efficiently.
Class A IP addressing scheme will be factored which will help account for the entire
workstations and give space for expansion as the firm may continue to experience growth
(Comer, 2000).
The First Task
The analyses, design and addressing of IP
The network needs us to subnet the network into individual networks which are unequal.
The IT department requires a sizeable subnet to accommodate 520 workstations and allow room
for expansion as the sales department requires a smaller subnet to handle the 40 workstations.
The workstations will be interconnected by the Access points for all the devices that can
access wireless internet and there will be a main switch from the main router from where all the
M2M NETWORK DESIGN
Executive summary
A TCP/IP solution best suits M2M. The network will have six routers, each located at every site
in Sydney and main office. The network will adopt the 10.0.0.0 private IP. Every department will
have a subnet connecting with the headquarter. All subnets will adopt the 10.0.0.0 private IP
therefore, all data and information will be sent from the subnet only after NAT (Postel, January
1980). All sub-networks will have switches and AP in each subnet to allow all the work station
connect to the primary router. The count of switches and AP will be dependent on the physical
count of workstations and the capacity of the workstations. Some of the departments will have
the users centered in one area where an AP will serve them while in other departments, users will
be widespread in a workstation thus the AP will not be able to cater for their needs efficiently.
Class A IP addressing scheme will be factored which will help account for the entire
workstations and give space for expansion as the firm may continue to experience growth
(Comer, 2000).
The First Task
The analyses, design and addressing of IP
The network needs us to subnet the network into individual networks which are unequal.
The IT department requires a sizeable subnet to accommodate 520 workstations and allow room
for expansion as the sales department requires a smaller subnet to handle the 40 workstations.
The workstations will be interconnected by the Access points for all the devices that can
access wireless internet and there will be a main switch from the main router from where all the

3
M2M NETWORK DESIGN
other switches will be connected. All the other workstations will be connected via Ethernet
cables because they are more reliable than the wireless network and less prone to errors and
hitches.
For more efficiency in the implementation of the addressing space, using VLSMs is
recommended to allow the use of different masks for every subnet (Moran, 2010). The VLSMs
will assist in the creation of subnets large enough and with more than 255 addresses for the host.
Use of the VLSM will enable us to assign IP addresses with a minimal number of IP addresses
wastage thereby leaving a surplus.
Figure 1 The network diagram of the Head Office
All units will consist of a setup like the one shown below. The primary router will
interconnect each unit to the main office. The router will connect to the main switch which will
be connected to other switches that will connected to the end devices. The access point will have
connected to the main router and some devices will connect to the network via the access point.
The router will be connected to the modem which will allow it to access internet and
connect to the other routers from the other offices. All the routers will be connected to the
internet via the virtual private network so that their IP addresses will not visible to other devices
on the internet but not in the company’s private network.
M2M NETWORK DESIGN
other switches will be connected. All the other workstations will be connected via Ethernet
cables because they are more reliable than the wireless network and less prone to errors and
hitches.
For more efficiency in the implementation of the addressing space, using VLSMs is
recommended to allow the use of different masks for every subnet (Moran, 2010). The VLSMs
will assist in the creation of subnets large enough and with more than 255 addresses for the host.
Use of the VLSM will enable us to assign IP addresses with a minimal number of IP addresses
wastage thereby leaving a surplus.
Figure 1 The network diagram of the Head Office
All units will consist of a setup like the one shown below. The primary router will
interconnect each unit to the main office. The router will connect to the main switch which will
be connected to other switches that will connected to the end devices. The access point will have
connected to the main router and some devices will connect to the network via the access point.
The router will be connected to the modem which will allow it to access internet and
connect to the other routers from the other offices. All the routers will be connected to the
internet via the virtual private network so that their IP addresses will not visible to other devices
on the internet but not in the company’s private network.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
4
M2M NETWORK DESIGN
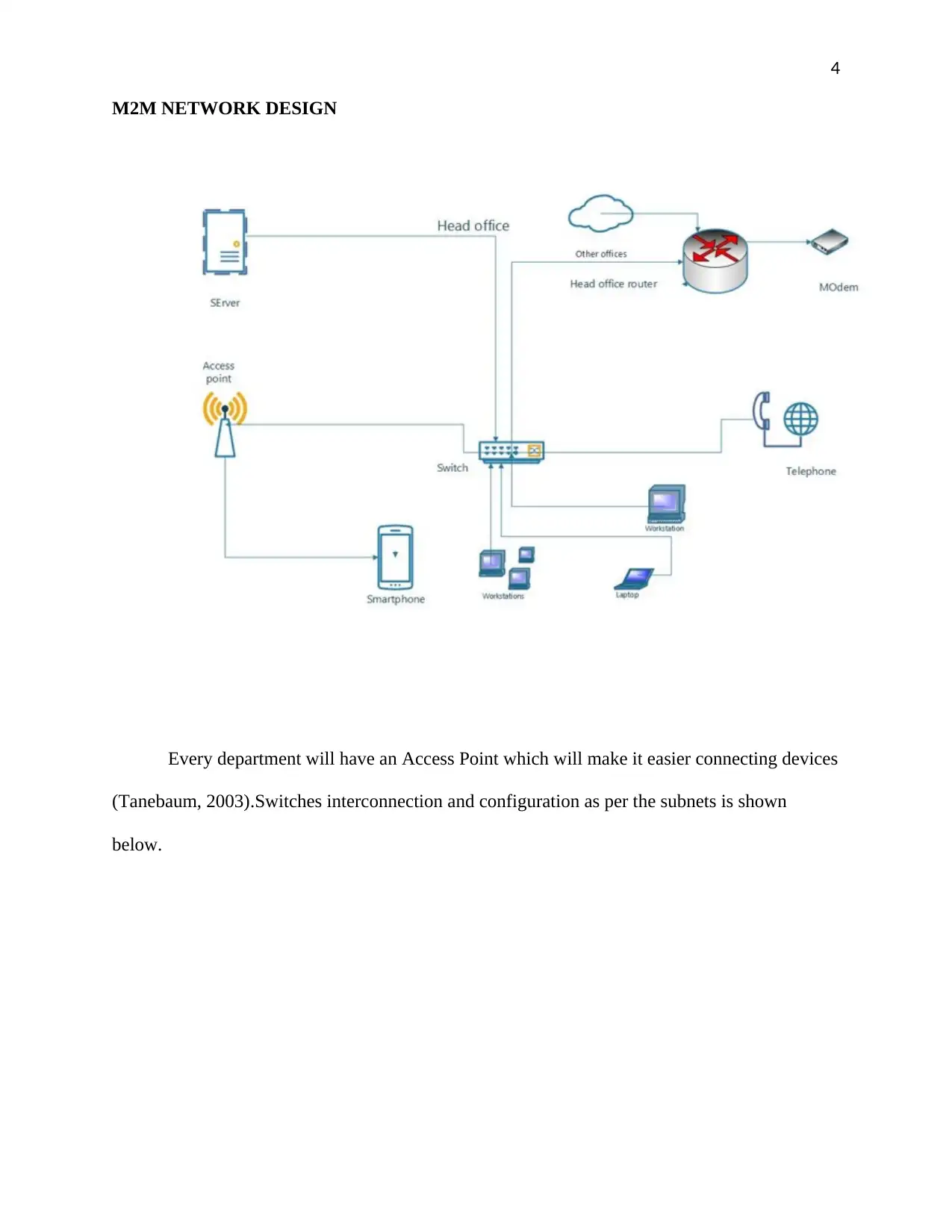
Every department will have an Access Point which will make it easier connecting devices
(Tanebaum, 2003).Switches interconnection and configuration as per the subnets is shown
below.
M2M NETWORK DESIGN
Every department will have an Access Point which will make it easier connecting devices
(Tanebaum, 2003).Switches interconnection and configuration as per the subnets is shown
below.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
5
M2M NETWORK DESIGN
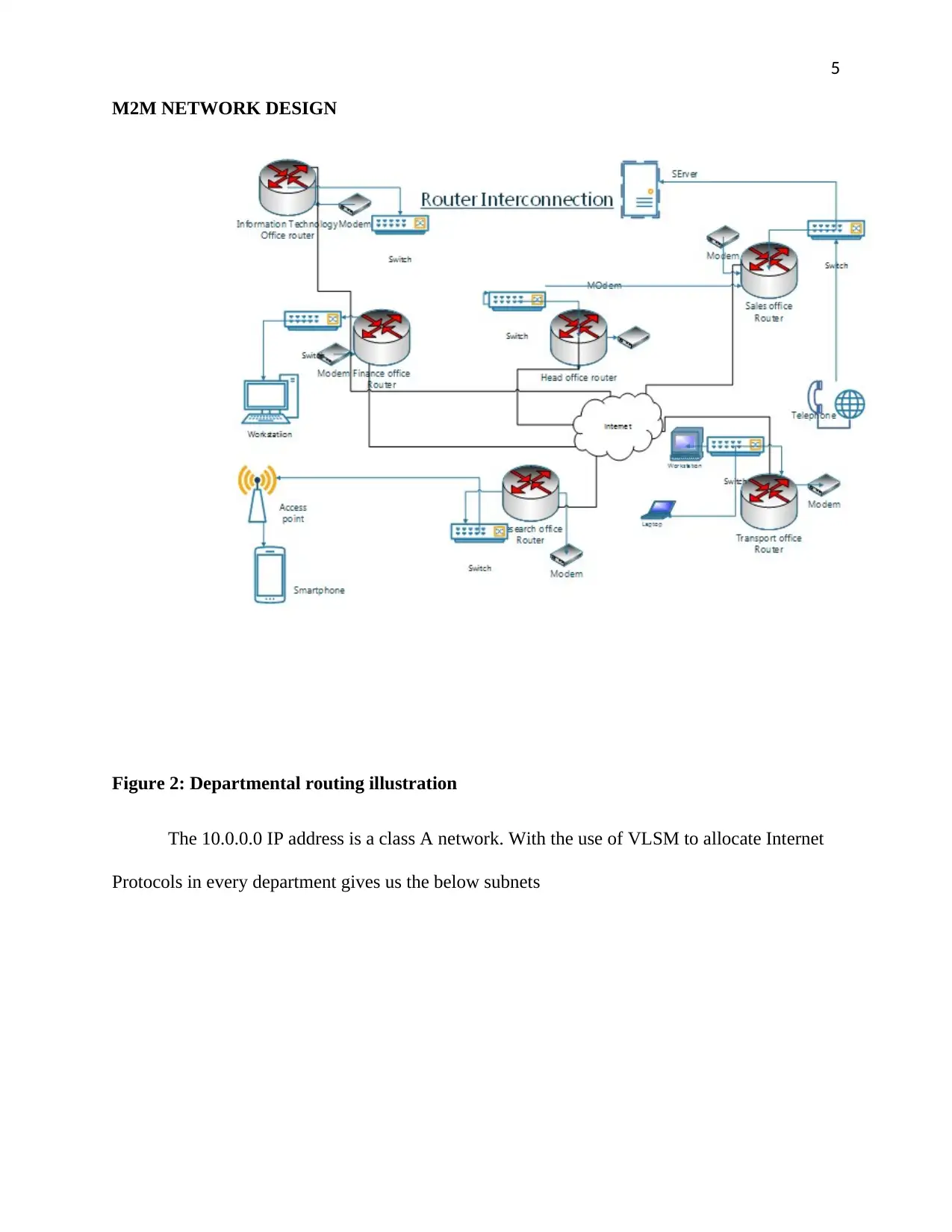
Figure 2: Departmental routing illustration
The 10.0.0.0 IP address is a class A network. With the use of VLSM to allocate Internet
Protocols in every department gives us the below subnets
M2M NETWORK DESIGN
Figure 2: Departmental routing illustration
The 10.0.0.0 IP address is a class A network. With the use of VLSM to allocate Internet
Protocols in every department gives us the below subnets

6
M2M NETWORK DESIGN
The IT department needs the biggest range of IP addresses (Press). We shall, therefore,
assign a high range of IP addresses as per the high usage requirements. It will, therefore, adopt
subnet mask 255.255.252.0 and 10.0.0.0/22. The start IP address should be 10.0.0.1 and end IP
M2M NETWORK DESIGN
The IT department needs the biggest range of IP addresses (Press). We shall, therefore,
assign a high range of IP addresses as per the high usage requirements. It will, therefore, adopt
subnet mask 255.255.252.0 and 10.0.0.0/22. The start IP address should be 10.0.0.1 and end IP
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

7
M2M NETWORK DESIGN
10.0.3.254 (Mogul & J., August 1985). Compared to the departmental demands, the subnet mask
used will be the best in terms of wastage of IP addresses and allowing room for expansion.
The Office of Finance is 2nd in the IP address needs. Using a subnet mask of
255.255.254.0, the IP address will be 10.0.0.0/23. The start IP host address will be 10.0.0.1 and
end with 10.0.1.254.
The Office of Transport and logistics is third in IP requirements and will consist of a
subnet mask of 255.255.255.0 and an IP address with 10.0.0.0/24. The beginning IP address will
be 10.0.0.1 and end in 10.0.0.254.
The research office is holding approximate 120 workstations will fall under the
255.255.255.128 subnet mask. It will take a 25-subnet mask IP address of 10.0.0.0/25. Beginning
IP address will be 10.0.0.1 and end IP will be 10.0.0.126. It will allow 125 host workstation
which is the best fit for our research office department.
The head office has 60 workstations. It will, therefore, have a subnet mask of
255.255.255.192 with an IP address with 26 subnet mask bits of 10.0.0.0/26. Beginning IP
address will be 10.0.0.1 and end with 10.0.0.62. This will be the best fit for our head office
having sixty-one host IP addresses available.
The sales office has an approximate of 40 workstations. It will adopt a subnet mask of
255.255.255.192. It will have an IP address with 26 subnet masks of 10.0.0.0/26. Beginning IP
address will be 10.0.0.1 and end IP will be 10.0.0.62.
The addressing solution leaves enough space for expansion within the departments and
makes sure of minimal IP address wastage (Institute). With the research office having ten
M2M NETWORK DESIGN
10.0.3.254 (Mogul & J., August 1985). Compared to the departmental demands, the subnet mask
used will be the best in terms of wastage of IP addresses and allowing room for expansion.
The Office of Finance is 2nd in the IP address needs. Using a subnet mask of
255.255.254.0, the IP address will be 10.0.0.0/23. The start IP host address will be 10.0.0.1 and
end with 10.0.1.254.
The Office of Transport and logistics is third in IP requirements and will consist of a
subnet mask of 255.255.255.0 and an IP address with 10.0.0.0/24. The beginning IP address will
be 10.0.0.1 and end in 10.0.0.254.
The research office is holding approximate 120 workstations will fall under the
255.255.255.128 subnet mask. It will take a 25-subnet mask IP address of 10.0.0.0/25. Beginning
IP address will be 10.0.0.1 and end IP will be 10.0.0.126. It will allow 125 host workstation
which is the best fit for our research office department.
The head office has 60 workstations. It will, therefore, have a subnet mask of
255.255.255.192 with an IP address with 26 subnet mask bits of 10.0.0.0/26. Beginning IP
address will be 10.0.0.1 and end with 10.0.0.62. This will be the best fit for our head office
having sixty-one host IP addresses available.
The sales office has an approximate of 40 workstations. It will adopt a subnet mask of
255.255.255.192. It will have an IP address with 26 subnet masks of 10.0.0.0/26. Beginning IP
address will be 10.0.0.1 and end IP will be 10.0.0.62.
The addressing solution leaves enough space for expansion within the departments and
makes sure of minimal IP address wastage (Institute). With the research office having ten
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser

8
M2M NETWORK DESIGN
workstations, it is at a needful point with a subnet of 126 hosts. Further expansion of the office
will require reviewing the entire addressing scheme.
The Head Office too is needful, with 60 workstations and a 62-host subnet. Loss of IP
address is minimized by having two free addresses in the subnet. In case the office expands with
an extra two workstations, the entire addressing scheme should be reviewed.
The offices will be interconnected as displayed below:
Figure 3: Offices Interconnection
M2M NETWORK DESIGN
workstations, it is at a needful point with a subnet of 126 hosts. Further expansion of the office
will require reviewing the entire addressing scheme.
The Head Office too is needful, with 60 workstations and a 62-host subnet. Loss of IP
address is minimized by having two free addresses in the subnet. In case the office expands with
an extra two workstations, the entire addressing scheme should be reviewed.
The offices will be interconnected as displayed below:
Figure 3: Offices Interconnection

9
M2M NETWORK DESIGN
Using the VLSM addressing procedure fits well for the subnets since some are as large as
255 hosts like the IT department subnet. It should, therefore, be addressed a manner that will
allow future expansion. It is also necessary to have small subnets to avoid loss of addresses.
Using the method ensures there is minimal loss thus allowing room for growth.
The Second Task
The role of Network analyzers
The network requires close monitoring to ensure they are running correctly and that all
devices in the workstations never experience down times (Press., 2004). It is important to
monitor the network security to keep off intruders who might penetrates the system and to ensure
no unauthorized personnel gets access to information he/she is not supposed to get.
The network administrator should give timely reports about the network. It's however
hard for a network admin to continuously diagnose and detect operational and configurational
problems in an expanding environment (Dye, McDonald, & Rufi, 2007).
The roles of a network analyzer
According to (Cerf, 1974), analyzers play a significant role in assisting the network
administrator in diagnosing and troubleshooting.
The M2M network administrator will have an easy task of troubleshooting and
diagnosing the network if a need arises. The analyzer provides the required data source for
monitoring and managing the system. They monitor the WAN and LAN status, statistics and
security of endpoints. Having a continuous update of the network requires the admin to have an
M2M NETWORK DESIGN
Using the VLSM addressing procedure fits well for the subnets since some are as large as
255 hosts like the IT department subnet. It should, therefore, be addressed a manner that will
allow future expansion. It is also necessary to have small subnets to avoid loss of addresses.
Using the method ensures there is minimal loss thus allowing room for growth.
The Second Task
The role of Network analyzers
The network requires close monitoring to ensure they are running correctly and that all
devices in the workstations never experience down times (Press., 2004). It is important to
monitor the network security to keep off intruders who might penetrates the system and to ensure
no unauthorized personnel gets access to information he/she is not supposed to get.
The network administrator should give timely reports about the network. It's however
hard for a network admin to continuously diagnose and detect operational and configurational
problems in an expanding environment (Dye, McDonald, & Rufi, 2007).
The roles of a network analyzer
According to (Cerf, 1974), analyzers play a significant role in assisting the network
administrator in diagnosing and troubleshooting.
The M2M network administrator will have an easy task of troubleshooting and
diagnosing the network if a need arises. The analyzer provides the required data source for
monitoring and managing the system. They monitor the WAN and LAN status, statistics and
security of endpoints. Having a continuous update of the network requires the admin to have an
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide

10
M2M NETWORK DESIGN
analyzer so that it identifies any upcoming issue in case a workstation is unable to transmit
statistics (Abbate, 2000).
The analyzer will help in monitoring transmitted and received data packets by the nodes
thus making it possible to filter and block malicious content from the network (Cerf, Vinton G.,
Kahn Robert E., 1979). They also verify any unusual change in the network, working with filters,
proxies and firewalls.
Why we need a network analyzer in M2M
The entire network is secure if a network analyzer is adopted. The network consists of six
subnets using a private IP network. It is therefore necessary to adopt a focal point in the
diagnoses and troubleshooting of the network. (C., 2016).
Network analyzer tools analysis
There exist various network analyzers in the market of software developers. They only
differ in the manner they intercept and log traffic on the network (James F. Kurose, 2008).
Wireshark is among the best analyzers. It runs well on Unix and Windows platforms. It can view
TCP sessions across all the protocols. Other network analyzers are based on consoles, but in
Wireshark, the console is inclusive.
Wireshark should be kept up to date to minimize vulnerabilities and ensure the system
remains bug-free and stable.
M2M NETWORK DESIGN
analyzer so that it identifies any upcoming issue in case a workstation is unable to transmit
statistics (Abbate, 2000).
The analyzer will help in monitoring transmitted and received data packets by the nodes
thus making it possible to filter and block malicious content from the network (Cerf, Vinton G.,
Kahn Robert E., 1979). They also verify any unusual change in the network, working with filters,
proxies and firewalls.
Why we need a network analyzer in M2M
The entire network is secure if a network analyzer is adopted. The network consists of six
subnets using a private IP network. It is therefore necessary to adopt a focal point in the
diagnoses and troubleshooting of the network. (C., 2016).
Network analyzer tools analysis
There exist various network analyzers in the market of software developers. They only
differ in the manner they intercept and log traffic on the network (James F. Kurose, 2008).
Wireshark is among the best analyzers. It runs well on Unix and Windows platforms. It can view
TCP sessions across all the protocols. Other network analyzers are based on consoles, but in
Wireshark, the console is inclusive.
Wireshark should be kept up to date to minimize vulnerabilities and ensure the system
remains bug-free and stable.
Paraphrase This Document
Need a fresh take? Get an instant paraphrase of this document with our AI Paraphraser
11
M2M NETWORK DESIGN
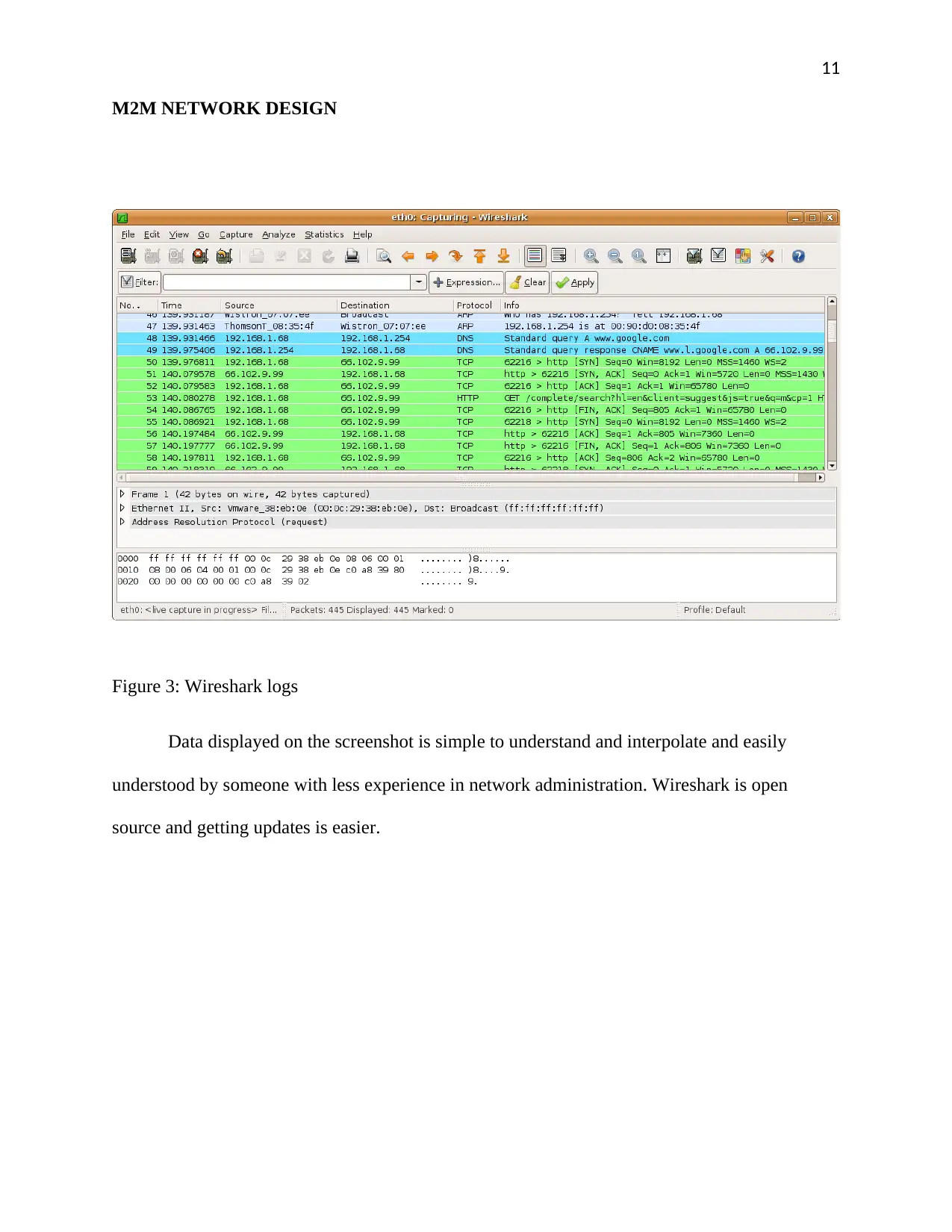
Figure 3: Wireshark logs
Data displayed on the screenshot is simple to understand and interpolate and easily
understood by someone with less experience in network administration. Wireshark is open
source and getting updates is easier.
M2M NETWORK DESIGN
Figure 3: Wireshark logs
Data displayed on the screenshot is simple to understand and interpolate and easily
understood by someone with less experience in network administration. Wireshark is open
source and getting updates is easier.

12
M2M NETWORK DESIGN
References
Abbate, J. (2000). Inventing the Internet. Cambridge: MIT Press.
C., S. (2016). Network Security Architectures.
Cerf, V. G. (1974). A protocol for Packet Network Intercommunication.
Cerf, Vinton G., Kahn Robert E. (1979). The introduction of packet satellite communication.
Comer, D. (2000). Internetworking with TCP/IP Principles, protocols and architectures.
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration Companion
guide. Cisco Press.
Institute, I. S. (n.d.). Internet Protocol. Internet Program Protocol Specification. Retrieved from
www.tools.ietf.org/html/frc791#page-7
James F. Kurose, K. W. (2008). Computer Networking.
Mogul, J., & J., P. (August 1985). Internet Standard Subnetting Procedure.
Moran, J. (2010, September 1). Understanding and resolving IP Address conflict. Retrieved from
www.webopedia.com
Postel, J. (January 1980). Model of Operation. In I. S. Institute, DOD Standard Internet (p. 5).
Marina del Rey, California: University of California.
Press, C. (n.d.). IP addressing guide. . Retrieved from
www.cisco.com/web/about/ciscoitatwork/downloads/ciscoitatwork/pdf/
Cisco_IT_IP_Addressing_Best_Practices.pdf
Press., C. (2004). Network Security Architectures. General Design Considerations for Secure
Networks.
Tanebaum, A. S. (2003). Computer Networks.
M2M NETWORK DESIGN
References
Abbate, J. (2000). Inventing the Internet. Cambridge: MIT Press.
C., S. (2016). Network Security Architectures.
Cerf, V. G. (1974). A protocol for Packet Network Intercommunication.
Cerf, Vinton G., Kahn Robert E. (1979). The introduction of packet satellite communication.
Comer, D. (2000). Internetworking with TCP/IP Principles, protocols and architectures.
Dye, M., McDonald, R., & Rufi, A. (2007). Network Fundamentals, CCNA Exploration Companion
guide. Cisco Press.
Institute, I. S. (n.d.). Internet Protocol. Internet Program Protocol Specification. Retrieved from
www.tools.ietf.org/html/frc791#page-7
James F. Kurose, K. W. (2008). Computer Networking.
Mogul, J., & J., P. (August 1985). Internet Standard Subnetting Procedure.
Moran, J. (2010, September 1). Understanding and resolving IP Address conflict. Retrieved from
www.webopedia.com
Postel, J. (January 1980). Model of Operation. In I. S. Institute, DOD Standard Internet (p. 5).
Marina del Rey, California: University of California.
Press, C. (n.d.). IP addressing guide. . Retrieved from
www.cisco.com/web/about/ciscoitatwork/downloads/ciscoitatwork/pdf/
Cisco_IT_IP_Addressing_Best_Practices.pdf
Press., C. (2004). Network Security Architectures. General Design Considerations for Secure
Networks.
Tanebaum, A. S. (2003). Computer Networks.
⊘ This is a preview!⊘
Do you want full access?
Subscribe today to unlock all pages.

Trusted by 1+ million students worldwide
1 out of 12
Related Documents
Your All-in-One AI-Powered Toolkit for Academic Success.
+13062052269
info@desklib.com
Available 24*7 on WhatsApp / Email
![[object Object]](/_next/static/media/star-bottom.7253800d.svg)
Unlock your academic potential
Copyright © 2020–2026 A2Z Services. All Rights Reserved. Developed and managed by ZUCOL.





